Abstract
A new protocol of bidirectional quantum teleportation (BQT) is proposed in which the users can transmit a class of n-qubit state to each other simultaneously, by using (2n + 2)-qubit entangled states as quantum channel. The state of the art approaches can only transmit two-qubit states in each round. This scheme is based on control-not operation, single-qubit measurements and appropriate single-qubit unitary operations. It is shown that the protocol is secure in preparation phase.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Quantum science has been attracting much attention in recent years. Quantum teleportation (QT) [1] is one of the most important protocols of quantum information theory. QT is a type of quantum communication, where by using entanglement and classical information, one of the users from one place teleport an unknown quantum state to the other user in the other place. This kind of protocol was presented in 1993. Bennett et al. [2] proposed the first protocol of QT by using Einstein-Podolsky-Rosen (EPR) pair. Since 1993, several QT schemes have been proposed so far [3,4,5,6,7,8,9,10,11] by using other entangled states as a quantum channel including Greenberger—Horne—Zeilinger (GHZ) state, W state, GHZ-like state, and etc, where the only difference among these protocols is the quantum channel.
A different kind of QT protocols was proposed in 1998 by Karlsson and Bourennane [12]. This type of QT is a controlled quantum teleportation (CQT), in which the sender transmits an unknown state to a remote receiver under the control of the supervisor. After that, several CQT protocols have been proposed [13,14,15,16,17] by using one or more than one controller. In these protocols the third person controls the qubits of users by applying measurement on his qubits.
Several experiments have been performed for realizing quantum teleportation. In pioneering work the teleportation protocol was implemented with single photons [18] over lab-scale distances and later also over km-scale distances in free space [19,20,21,22].
One of the most important subfields of QT is bidirectional quantum teleportation (BQT). In BQT, two users can teleport qubits to each other and two users play sender role and receiver role, simultaneously. In 2013, the first CBQT was proposed by Zha et al. [23]. After that, several BCQT protocols have been proposed [24,25,26,27,28]. Yan [24] and Sun et al. [25] proposed two protocols of BQCT by using six-qubit cluster state and six-qubit maximally-entangled state as a quantum channel, respectively. Li and Nie [26] presented a protocol of BQCT via five-qubit composite GHZ-Bell state as a quantum channel but Shukla et al. [27] showed that the Li’s protocol [26] is not a BQCT scheme. Then, Li et al. [28] proposed a protocol via five-qubit entangled state. All of those protocols were proposed in 2013.
In 2014, Fu et al. [29] presented a BQT scheme by using a four-qubit cluster state as a quantum channel. In this scheme, users can simultaneously exchange their single-qubit states by applying Hadamard operation. In the same year, Chen [30], Duan et al. [31] and Duan and Zha [32], proposed new schemes of BCQT by using five-qubit entangled state, seven-qubit entangled state, and six-qubit entangled state, as a quantum channel, respectively. In Duan et al.’s scheme [31], Charlie improves the security of the protocol by performing single-qubit measurements three times. In the next study, Duan and Zha [32] improved the security of their protocol by applying two single-qubit measurements.
In 2015, different schemes of BCQT by using six-qubit genuine state [33], GHZ-type state [34], eight-qubit entangled state [35], and six-qubit entangled state [36] as a quantum channel were proposed. The scheme in [35] is better than the previous ones in terms of quantum resource consumptions. In Hassanpour’s scheme [36], the quantum channel is easier to prepare.
In all mentioned protocols, Alice and Bob can only teleport an arbitrary single-qubit state to each other. In 2016, two different protocols of BCQT by using seven-qubit entangled state as a quantum channel were proposed, that Alice can teleport an arbitrary single-qubit state to Bob and Bob can teleport an arbitrary two-qubit state to Alice [37, 38]. The same year in February, a BQT protocol by using six-qubit entangled state as a quantum channel was presented [39]. In this protocol, Alice and Bob can teleport a pure EPR state to each other. Then a BCQT protocol was proposed by using nine-qubit entangled state as a quantum channel, where Alice and Bob can teleport an arbitrary two-qubit state to each other [40]. In June 2016, a BCQT protocol by using six-qubit cluster state as a quantum channel was proposed [41]. In this protocol, Alice can teleport an arbitrary two-qubit state to Bob and Bob can teleport an arbitrary single-qubit state to Alice. In [42], a new scheme of bidirectional quantum teleportation (BQT) making use of an eight-qubit entangled state as the quantum channel is presented, where Alice and Bob can teleport two-qubit states to each other simultaneously.
In this study, for the first time, a BQT protocol is presented by which n-qubit states (as (1) and (2) shows) can be teleported simultaneously. This protocol utilizes (2n + 2)-qubit entangled state as a channel. In this protocol, each user applies one CNOT gate and (n + 1) single-qubit unitary gates as well as performing n measurements in X basis.
The rest of the paper is organized as follows. In Section 2, the proposed protocol is explained. Section 3, includes summary and analysis of previous research. Conclusion and future work are presented in Section 4.
2 Description of the Presented Protocol
The proposed scheme is a BQT protocol, where Alice and Bob as two legitimate users want to teleport an n-qubit state as (1) and (2) to each other. (It should be noted that EPR and GHZ states are examples of states in (1) and (2).)
where |α 0|2 +|α 1|2 = 1, |β 0|2 +|β 1|2 = 1 and q 1 q 2…q n ∈ {0,1} and q bar is the flipped state of q.
2.1 Preparation Phase
In this protocol, two users teleport their qubits by using (2n + 2)-qubit entangled state as a quantum channel,
Alice generates the N states described in (3). She keeps qubits a 1…a n+1 for herself and sends the qubits b 1…b n+1 to Bob.
2.2 Security Checking Phase
For making sure that qubits of (3) are shared without eavesdropping, Alice selects randomly enough states of sequence as checking qubits. The remaining qubits are used as teleporting qubits. To measure the checking qubits, she randomly selects one of the Z or X bases for each checking qubits. Then she announces the orders and the bases of the checking qubits to her Bob. Bob measures the corresponding qubits under the same measuring bases. Then, he announces their measurement results to Alice.
If there is no Eve interference and the channel is secure, the measurement results must be correlated. As an example suppose q 1 = q 2 = ⋯ = q n = 0.
Table 1 shows the correlation of Alice and Bob measurement results where n − indicates the number of the qubits that are collapsed to |−〉 when measured in X basis. It should be noted that:
If the error rate is more than the threshold, they discard and abort the communication; otherwise they continue the communication and execute the next phase.
2.3 Main Protocol
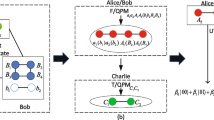
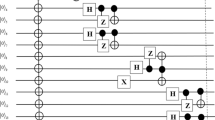
In this subsection the steps of the protocol is described. Figure 1 illustrates the protocol.
-
Step 1.
After Alice and Bob share a (2n + 2)-qubit entangled state as (3), as a quantum channel, the initial state of the whole system can be expressed as (4),
$$ \left|\varphi \right\rangle_{a_{1} b_{1} {\ldots} b_{n} a_{2} {\ldots} a_{n+1} b_{n+1} A_{1} {\ldots} A_{n} B_{1} {\ldots} B_{n}} \!\,=\,\left|G\right\rangle_{a_{1} b_{1} {\ldots} b_{n} a_{2} {\ldots} a_{n+1} b_{n+1}} \otimes \left|\emptyset \right\rangle_{A_{1} {\ldots} A_{n}} \otimes \left|\emptyset \right\rangle_{B_{1} {\ldots} B_{n}} , $$(4)where the qubits a 1…a n+1 and A 1…A n belong to Alice and qubits b 1…b n+1 and B 1…B n belong to Bob, respectively.
-
Step 2.
In this step, Alice and Bob apply a controlled-not operation with A 1 and B 1 as control qubits and qubits a 1 and b n+1 as target respectively. Now the state will be in the form of (5) (without loss of generality suppose q 1 = 0).
$$\begin{array}{@{}rcl@{}} &&\left|\varphi_{1} \right\rangle_{a_{1} b_{1} {\ldots} b_{n} a_{2} \ldots a_{n+1} b_{n+1} A_{1} {\ldots} A_{n} B_{1} {\ldots} B_{n}} \\ &=&\frac{1}{2}\left[\vphantom{\left|\overline{q}_{1}\right.} {\alpha_{0} \beta_{0}} \right.\left|0q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} 0\right\rangle \left|q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle\\ &&+\alpha_{0} \beta_{0} \left|0q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} 1\right\rangle \left|q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle \\ &&+\alpha_{0} \beta_{0} \left|1\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} 0\right\rangle \left| q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle\\ && +\alpha_{0} \beta_{0} \left|1\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} 1\right\rangle \left|q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle \\ &&+\alpha_{0} \beta_{1} \left|0q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} 1\right\rangle \left|q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle\\ &&+\alpha_{0} \beta_{1} \left|0q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} 0\right\rangle \left|q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle \\ &&+\alpha_{0} \beta_{1} \left|1\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} 1\right\rangle \left| {q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n}} \right\rangle\\ && +\alpha_{0} \beta_{1} \left|1\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} 0\right\rangle \left|q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle \\ &&+\alpha_{1} \beta_{0} \left|1q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} 0\right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle\\ &&+\alpha_{1} \beta_{0} \left|1q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} 1\right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle \\ &&+\alpha_{1} \beta_{0} \left|0\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} 0\right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle\\ && +\alpha_{1} \beta_{0} \left|0\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} 1\right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle \\ &&+\alpha_{1} \beta_{1} \left|1q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} 1\right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} \ldots \overline{q}_{n} \right\rangle\\ && +\alpha_{1} \beta_{1} \left|1q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} \ldots q_{n} 0\right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle \\ &&+\alpha_{1} \beta_{1} \left|0\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} 1\right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle\\ &&\left. +\alpha_{1} \beta_{1} \left|0\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} 0\right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle \right]. \end{array} $$(5) -
Step 3.
In this step, Alice and Bob perform a single-qubit measurement in the Z-basis on qubits a 1 and b n+1 respectively. According to Table 2, the remaining particles may collapse into one of the 4 possible states with 25% probability.
-
Step 4.
After Alice and Bob tell their measurement results to each other, they apply suitable unitary operation as is shown in Table 3.
After users applied unitary operation on their qubits, all of the 4 states will be in the form of (6).
$$\begin{array}{@{}rcl@{}} &&\left( \alpha_{0} \beta_{0} \left| q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n}\right\rangle \left|q_{1} q_{2} {\ldots} q_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle\right.\\ &&~\left.+\alpha_{0} \beta_{1} \left|q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} \ldots \overline{q}_{n} \right\rangle\left|q_{1} q_{2} {\ldots} q_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle\right.\\ &&~\left.+\alpha_{1} \beta_{0} \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} q_{1} q_{2} {\ldots} q_{n} \right\rangle\right.\\ &&~\left.+\alpha_{1} \beta_{1} \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle \left|\overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \overline{q}_{1} \overline{q}_{2} {\ldots} \overline{q}_{n} \right\rangle\right)_{b_{1} {\ldots} b_{n} a_{2} {\ldots} a_{n+1} A_{1} {\ldots} A_{n} B_{1} {\ldots} B_{n}}.\\ \end{array} $$(6) -
Step 5.
In this step, Alice and Bob perform n single-qubit measurement in the X-basis on qubits A 1…A n and B 1…B n respectively. The remaining particles may collapse into one of the 2n possible states with the same probability as described in Table 4, where n − and m − are the numbers of |−〉 in the collapsed state after the Alice’s measurement and Bob’s measurement respectively.
-
Step 6.
In this step, Alice and Bob can reconstruct the n-qubit state by applying suitable unitary operation as shown in Table 5.
Table 2 The (Z-basis) measurement results of users and the corresponding collapsed state Table 3 Applying suitale unitary operations Table 4 The (X-Basis) measurement results of users and the corresponding collapsed state Table 5 Required unitary operations
After applying the unitary operators in Table 5, the state will be as below:
Now, Alice and Bob reconstruct the n-qubit state, and the bidirectional teleportation is successfully finished which is shown in (8) and (9).
Considering that the protocol is based on quantum teleportation and no qubit is transmitted in the channel, the protocol is secure against attacks such as intercept-resend.
3 Comparison
The most important advantage of the proposed protocol is that Alice and Bob can simultaneously teleport an n-qubit state in the form of (1) and (2) to each other. In the best approach previously proposed [40], the users can transmit only two-qubit states while in the proposed protocol in this paper, the users can teleport as many qubits as they desire through the bidirectional quantum teleportation.
Consider m u the number of transmitted qubits, q k the number of used qubits in the channel and b k the number of transmitted bits, the efficiency is calculated as the following relation:
By setting the values of these parameters, we will have:
which implies that by increasing the value of n, the efficiency of this protocol gets closer to one.
4 Conclusions
The advantage of this protocol is that users can simultaneously teleport an n-qubit state to each other. In the best case of previous protocols the users can only teleport a two-qubit state simultaneously. In this protocol, only single-qubit measurements are required so it is more simple and feasible in experiment. As a future work, this protocol can be extended to transmitting an arbitrary n-qubit state. Further, the effects of the amplitude-damping noise and the phase-damping noise for BQT process could be investigated. The other direction for a future work is to include a third party as a controller in the protocol, where without controller’s cooperation Alice and Bob cannot recover the teleported quantum states.
References
Nielsen, M.A., Chuang, I.L.: Quantum Computation and Quantum Information. Cambridge University Press, Cambridge (2002)
Bennett, C.H., et al.: Teleporting an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels. Phys. Rev. Lett. 70(13), 1895 (1993)
Cardoso, W.B.: Teleportation of GHZ-states in QED-cavities without the explicit Bell-state measurement. Int. J. Theor. Phys. 47(4), 977–982 (2008)
Shi, B.-S., Tomita, A.: Teleportation of an unknown state by W state. Phys. Lett. A 296(4), 161–164 (2002)
Yang, K., et al.: Quantum teleportation via GHZ-like state. Int. J. Theor. Phys. 48(2), 516–521 (2009)
Tian, D.P., Tao, Y.J., Qin, M.: Teleportation of an arbitrary two-qudit state based on the non-maximally four-qudit cluster state. Sci. China Ser. G Phys. Mech. Astron. 51(10), 1523–1528 (2008)
Tang, S.-Q., Shan, C.-J., Zhang, X.-X.: Quantum teleportation of an unknown two-atom entangled state using four-atom cluster state. Int. J. Theor. Phys. 49(8), 1899–1903 (2010)
Agrawal, P., Pati, A.: Perfect teleportation and superdense coding with W states. Phys. Rev. A 74(6), 062320 (2006)
Nie, Y.-y., et al.: Perfect teleportation of an arbitrary three-qubit state by using W-class states. Int. J. Theor. Phys. 50(10), 3225–3229 (2011)
Tsai, C.-W., Hwang, T.: Teleportation of a pure EPR state via GHZ-like state. Int. J. Theor. Phys. 49(8), 1969–1975 (2010)
Nandi, K., Mazumdar, C.: Quantum teleportation of a two qubit state using GHZ-like state. Int. J. Theor. Phys. 53(4), 1322–1324 (2014)
Karlsson, A., Bourennane, M.: Quantum teleportation using three-particle entanglement. Phys. Rev. A 58(6), 4394 (1998)
Yang, C.-P., Han, S.: A scheme for the teleportation of multiqubit quantum information via the control of many agents in a network. Phys. Lett. A 343(4), 267–273 (2005)
Deng, F.-G., et al.: Symmetric multiparty-controlled teleportation of an arbitrary two-particle entanglement. Phys. Rev. A 72(2), 022338 (2005)
Wang, Y.-H., Song, H.-S.: Preparation of partially entangled W state and deterministic multi-controlled teleportation. Opt. Commun. 281(3), 489–493 (2008)
Wang, X.-W., Su, Y.-H., Yang, G.-J.: Controlled teleportation against uncooperation of part of supervisors. Quantum Inf. Process. 8(4), 319–330 (2009)
Wang, T.-Y., Wen, Q.-Y.: Controlled quantum teleportation with Bell states. Chin. Phys. B 20(4), 040307 (2011)
Bouwmeester, D., et al.: Experimental quantum teleportation. Nature 390 (6660), 575–579 (1997)
Marcikic, I., de Riedmatten, H., Tittel, W., Zbinden, H., Gisin, N.: Long-distance teleportation of qubits at telecommunication wavelengths. Nature 421, 509–513 (2003)
Yin, J., et al.: Quantum teleportation and entanglement distribution over 100-kilometre free-space channels. Nature 488, 185–188 (2012)
Ma, X.-S., et al.: Quantum teleportation over 143 kilometres using active feed-forward. Nature 489(7415), 269–273 (2012)
Sun, Q.C., et al.: Quantum teleportation with independent sources over an optical fibre network. Nat. Photonics 10, 671–675 (2016)
Zha, X.-W., et al.: Bidirectional quantum controlled teleportation via five-qubit cluster state. Int. J. Theor. Phys. 52(6), 1740–1744 (2013)
Yan, A.: Bidirectional controlled teleportation via six-qubit cluster state. Int. J. Theor. Phys. 52(11), 3870–3873 (2013)
Sun, X.M., Zha, X.W.: A scheme of bidirectional quantum controlled teleportation via six-qubit maximally entangled state. Acta Photonica Sin. 48, 1052–1056 (2013)
Li, Y.-H., Nie, L.-P.: Bidirectional controlled teleportation by using a five-qubit composite GHZ-Bell state. Int. J. Theor. Phys. 52(5), 1630–1634 (2013)
Shukla, C., Banerjee, A., Pathak, A.: Bidirectional controlled teleportation by using 5-qubit states: a generalized view. Int. J. Theor. Phys. 52(10), 3790–3796 (2013)
Li, Y.-H., et al.: Bidirectional controlled quantum teleportation and secure direct communication using five-qubit entangled state. Quantum Inf. Process. 12(12), 3835–3844 (2013)
Fu, H.-Z., Tian, X.-L., Hu, Y.: A general method of selecting quantum channel for bidirectional quantum teleportation. Int. J. Theor. Phys. 53(6), 1840–1847 (2014)
Chen, Y.: Bidirectional controlled quantum teleportation by using five-qubit entangled state. Int. J. Theor. Phys. 53(5), 1454–1458 (2014)
Duan, Y.-J., et al.: Bidirectional quantum controlled teleportation via a maximally seven-qubit entangled state. Int. J. Theor. Phys. 53(8), 2697–2707 (2014)
Duan, Y.-J., Zha, X.-W.: Bidirectional quantum controlled teleportation via a six-qubit entangled state. Int. J. Theor. Phys. 53(11), 3780–3786 (2014)
Chen, Y.: Bidirectional quantum controlled teleportation by using a genuine six-qubit entangled state. Int. J. Theor. Phys. 54(1), 269–272 (2015)
Wang, J.-W., Shu, L.: Bidirectional quantum controlled teleportation of qudit state via partially entangled GHZ-type states. Int. J. Mod. Phys. B 29(18), 1550122 (2015)
Zhang, D., et al.: Bidirectional and asymmetric quantum controlled teleportation via maximally eight-qubit entangled state. Quantum Inf. Process. 14(10), 3835–3844 (2015)
Hassanpour, S., Houshmand, M.: Bidirectional quantum controlled teleportation by using EPR states and entanglement swapping. In: 23th Iranian Conference on Electrical Engineering (ICEE) (2015)
Hong, W.: Asymmetric bidirectional controlled teleportation by using a seven-qubit entangled state. Int. J. Theor. Phys. 55(1), 384–387 (2016)
Sang, M.: Bidirectional quantum controlled teleportation by using a seven-qubit entangled state. Int. J. Theor. Phys. 55(1), 380–383 (2016)
Hassanpour, S., Houshmand, M.: Bidirectional teleportation of a pure EPR state by using GHZ states. Quantum Inf. Process. 15(2), 905–912 (2016)
Li, Y., Jin, X.: Bidirectional controlled teleportation by using nine-qubit entangled state in noisy environments. Quantum Inf. Process. 15(2), 929–945 (2016)
Li, Y., et al.: Asymmetric bidirectional controlled teleportation by using six-qubit cluster state. Int. J. Theor. Phys. 55(6), 3008–3016 (2016)
Zadeh, S., Sadegh, M., Houshmand, M., Aghababa, H.: Bidirectional teleportation of a two-qubit state by using eight-qubit entangled state as a quantum channel. Int. J. Theor. Phys. 56(7), 1–12 (2017)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zadeh, M.S.S., Houshmand, M. & Aghababa, H. Bidirectional Quantum Teleportation of a Class of n-Qubit States by Using (2n + 2)-Qubit Entangled States as Quantum Channel. Int J Theor Phys 57, 175–183 (2018). https://doi.org/10.1007/s10773-017-3551-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-017-3551-z