Abstract
Quantum watermarking technology protects copyright by embedding an invisible quantum signal in quantum multimedia data. This paper proposes a two-bit superposition method which embeds a watermark image (or secret information) into a carrier image. Firstly, the bit-plane is used to encrypt the watermark image. At the same time, the quantum expansion method is used to extend the watermark image to the same size with the carrier image, and then the image is encrypted through the Fibonacci scramble method again. Secondly, the first proposed method is the two bits of the watermark image which is embedded into the carrier image in accordance with the order of the high and lowest qubit, and the second proposed method which is the high bit of the watermark image is embedded to the lowest bit. Then the lowest bit of the watermark image is embedded in carrier image. Third, the watermark image is extracted through 1-CNOT and swap gates, and the watermark image is restored by inverse Fibonacci scramble, inverse expansion method and inverse bit-plane scramble method. Finally, for the validation of the proposed scheme, the signal-to-noise ratio (PSNR), the image histogram and the robustness of the two watermarking methods are analyzed.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In recent years, the development of quantum information processing shows that the development of quantum computer systems has a tremendous impact on the field of computer science. The fundamental reason is that quantum computers are beyond the reach of traditional computers [1,2,3]. One of the goals of quantum computers is to solve complex problems that cannot be solved even in supercomputers. Therefore, because of the remarkable nature of quantum computers, many innovative ideas have emerged in all related fields such as quantum image processing. However, the use of quantum computers to accelerate certain deterministic signal processing tasks still not be achieved. Similarly, quantum computers also have some potential roles in some areas. For example, running a new type of quantum Fourier transform [4], wavelet transform and discrete cosine transform [5] and so on. However, quantum image processing in quantum computing still faces a large number of fundamental issues, such as the storage and presentation of quantum images.
Although there are many fundamental problems in quantum image processing, many methods that presentation of a quantum image was proposed in recent years. For example, the quantum logarithmic polar representation (QUALPI) proposed in Ref. [6], a novel quantum color digital image representation (NCQI [7]), and so on. Under these quantum representations, quantum watermarking has appeared many research results, such as watermarking scheme based on the Quantum Fourier Transform [8], watermarking scheme based on wavelet transform [9] and the Hadamard gate transform [10] proposed by Song et al. Jiang propose the quantum watermarking scheme based on LSB and the encryption algorithm based on quantum LSB [11]. A simple small-scale quantum circuit watermarking scheme was proposed [12]. In 2016, the quantum least significant bit algorithm based on the NCQI representation [13] was proposed. In 2018, the least significant bit algorithm based on the INEQR was proposed [14]. Similarly, there are some achievements in the sub-directions in image processing. In 2017, quantum space value domain filtering was proposed [15]. In 2018, Li proposed an improved frequency domain filtering method based on quantum color images [16]. For 2015 years, Mario proposed a quantum logic image denoising method [17]. Hua proposed a quantum image encryption algorithm based on image correlation decomposition [18]. Song proposed a method based on constrained geometry and color transformed quantum image encryption algorithm [19]. Zhou proposed an encryption scheme based on quantum iterative Arnold transform and quantum image shift operation [20]. In summary, although there are some problems in the current stage of quantum image processing, these not stop the rapid development trend.
In this paper, a double embedded watermarking scheme is proposed. Firstly, the watermark image is scrambled by the bit-plane scrambling method. Secondly, the watermark image is expanded by the quantum expansion circuit. Thirdly, utilizes the Fibonacci scrambling method to scramble the expanded image. Finally, the watermark image is embedded in the carrier image.
The rest of the paper is organized as follows. A brief basic theoretic knowledge is given in Section 2. In Section 3 a new quantum embedded watermarking scheme is proposed. Section 4 is devoted to the simulation-based experiments and analysis. Finally, the conclusion is drawn in Section 5.
2 Basic Knowledge
2.1 The Novel Enhanced Quantum Representation (NEQR)
The NEQR was first proposed in 2013 [21]. It uses q quantum bits to store the color values of each pixel [22], which is more convenient for the operation of image colors. According to NEQR this Eq. (1) is shown.
Where the binary sequence \( \mid {C}_{YX}^0\left\rangle \mid {C}_{YX}^1\right\rangle \dots \mid {C}_{YX}^{q-2}\left\rangle \mid {C}_{YX}^{q-1}\right\rangle \)encodes the color value, and the gray range is2n, ∣YX〉 = ∣ yn − 1yn − 2…y1y0〉 ∣ xn − 1xn − 2…x1x0〉, ∣ ylxl〉 ∈ {0, 1}encodes the vertical and horizontal coordinates information. Therefore, NEQR needs q + 2n qubits to represent an 2n × 2n image with gray range2n.
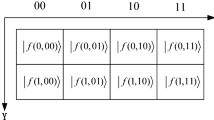
An example of 2 × 2 pixels image is shown in Fig. 1. In this example, the gray value ranges from 0 to 255, so the 8 qubits are needed to store this color information.
2.2 Fibonacci Image Scrambling
When the Fibonacci scrambling [23] acts on a digital classical image sized2n × 2n,this transformation can be defined as follows Eq. (3):
i.e.,
(xF, yF) is the coordinates of the scrambled image.
The inverse Fibonacci transformation is defined as follows:
i.e.,
As shown in Eq. (4), the adder modulo plays an important role in the Fibonacci Scrambling, and its quantum circuit proposed in Ref. [23] is given as follows Fig. 3.
Plain adder network shown in Fig. 2 consists of basic sum circuit and carries circuit. Based on Plain adder, Ref. [23] designed a ADDER-MOD module as shown in Fig. 3.
The reversible sum and reversible carries circuit proposed in Ref. [23] is shown in Fig. 4.
3 Watermarking Scheme
At present, the implemented watermarking scheme usually uses the least significant bit algorithm. However, the embedded capacity is only a qubit. This paper proposes two kinds of watermarking scheme. One method is to embed the two bits of the watermark image into the image of the carrier image through the overlay method. Another method is to embed the two-qubit of the watermark image by itself, and then the operated watermark image is embedded into the carrier image. Next, the two kinds of watermarking methods are introduced.
3.1 Image Preprocessing
3.1.1 Image Bit-Plane Scramble
In 2015, the quantum image gray-code and bit-plane scrambling [24] was proposed by Zhou et al. Inspired by this article, this paper utilizes a similar pixel bit-plane algorithm. The bit-plane scramble circuit is shown in Fig. 5.
Generally, an image has 8-pixel bit-plane. When the digital watermark image is transformed into a quantum watermark image through the NEQR, the digital bit-plane of the image becomes a qubit-plane. Next, watermark image is scrambled by a bit-plane scramble. Firstly, in accordance with the order of “0–4”, “1–5”, “2–6”, and “3–7”, these bit planes are exchanged through quantum swap gates. After the exchange is completed, if the quantum state of the pixel bit-plane in the original order “4567” is ∣1〉, 1-CNOT is used to change the other bit-plane pixel bit stream. Go through this operation, watermark image’s bit-plane order is changed and some bit-plane pixel’s bit stream is changed. Finally, the watermark image scramble is completed by means of the simple bit-plane scramble algorithm. Utilizes the scrambling circuit, the watermark image can be scrambled so as to achieve the scrambling effect in Fig. 6.
In Fig. 6, (a) is original watermark image, (b) scrambled watermark image. The grey-value image becomes chaotic after bit-plane scramble is executed. And then the scrambled image can’t be recognized.
3.1.2 Image Expand Method
The first step of the watermark image preprocessing has been completed. Next, utilizes the quantum expansion circuit to expand the scrambled watermark image, in order to gain the same size as carrier image. This expansion circuit is shown in Fig. 7.
Via the quantum expansion circuit, watermark image is expanded in accord with the order the clock-wise direction. Suppose there are a watermark image with the size of 1 × 1, and a carrier image with the size of4 × 4.Because of the original watermark image coordinate is [0, 0], expanded watermark image coordinate is [0, 0][0, 1][1, 0][1, 1]. Thus, utilizes the auxiliary qubits ∣0〉 record the expanded watermark image coordinate information and pixel bit-plane distribution information in Fig. 7. On account of the expand watermark image dependence the clock-wise direction, that’s the corresponding coordinates after the bit-plane expansion is “(0, 1) − [0, 0]”, “(2, 3) − [0, 1]”, “(4, 5) − [1, 1]”, “(6, 7) − [1, 0]”. Finally, the eight bit-plane is distributed and new watermark image is obtained. In the Fig. 7, \( \mid {C}_{xy}^0\cdots {C}_{xy}^7\Big\rangle \) represent the original watermark image bit-plane pixel value, auxiliary qubits ∣0〉 represent the coordinates and temporary memory pixel information, ∣x0⋯xn − 1〉 ∣ y0⋯yn − 1〉 represent original image coordinates information.
3.1.3 Image Fibonacci Scramble
Referring to the Fibonacci scramble formula (3) in Section 2.2, the expanded image can be encrypted through the scramble circuit in the Fig. 8.
In Fig. 8, X and Y represent the expanded image’s coordinate information,XFand YF represent the scramble expanded image’s coordinate information. Through the scramble circuit, expanded watermark image is scrambled. However, expanded watermark image is sightless, so that the watermark image has an additional layer of protection and attacker cannot recognize the scrambled image.
3.2 Watermark Embedded Scheme
Through image preprocessing, the watermark image and the carrier image have the same size. All preparations have been completed. Next, the watermark image is need to be embedded in the carrier image. The entire embedded procedure is shown in Fig. 9.
Observe the Fig. 9, the watermark image is embedded in the carrier image after multiple operations. The first operation of the watermark image has been introduced in section 3.1. Next, the operation which the watermarking image is embedded, is shown in the following steps.
-
Step 1:
Watermark and carrier images are transformed into the quantum image ∣W〉and∣C〉through the NEQR.
-
Step 2:
Quantum watermark image is scrambled through the bit-plane scramble algorithm. The scrambled watermark image is disordered and chaotized, and then detail operation procedure is described in section 3.1.1. In the end, the scrambled watermark image ∣PW〉 is obtained.
-
Step 3:
The scrambled quantum watermark image is unable to embedded in the carrier, because of watermark image size is not the same as carrier image. Next, scrambled watermark image need to be expanded, so that watermark has the same size as carrier image. However, there is a problem that how to expand watermark image. In order to solve this problem, quantum expansion circuit is proposed in Fig. 7. Through quantum expansion circuit, watermark image ∣EPW〉 have the same size as carrier image and a detailed description of the expand procedure is shown in section 3.1.2.
According to the image preprocessing procedure, the extended watermark image needs to be re-encrypted by means of a Fibonacci scramble, so that the watermark image is less easily cracked by the attacker. This procedure is described in section 3.1.3.
-
Step 4:
In this step, the extended watermark image is embedded into the carrier image by two kinds of embedding methods. The descriptions of the two kinds of embedding methods are given in section 3.2.1 and 3.2.2.
3.2.1 Self-Embedded Watermark Scheme
In the previous section, the watermark was embedded into the carrier image, but it is not described that how to embed in carrier image. This section will introduce the first watermark embedding method in detail. a detailed embedded circuit is shown in Fig. 10.
In the Fig. 10, ∣K1〉 represent the least bit that the carrier image. Specific NEQR presentment is given in Eq. (5).
Firstly, if the \( \mid {C}_{xy}^0\Big\rangle \) and \( \mid FEP{W}_{xy}^1\Big\rangle \) are equal, control swap gate is not performed. If the \( \mid {C}_{xy}^0\Big\rangle \) and \( \mid FEP{W}_{xy}^1\Big\rangle \) are not equal, this information is recorded through auxiliary qubit ∣0〉, and then \( \mid FEP{W}_{xy}^1\Big\rangle \) is embedded in \( \mid {C}_{xy}^0\Big\rangle \) through the control swap gates. Secondly, utilizes the ∣K1〉 record the recent carrier image \( \mid {C}_{xy}^0\Big\rangle \). Thirdly, if the \( \mid {C}_{xy}^0\Big\rangle \)and \( \mid FEP{W}_{xy}^0\Big\rangle \) are not equal, utilizes the auxiliary qubit∣0〉record this inequality information, and then auxiliary qubit state is ∣1〉when the \( \mid {C}_{xy}^0\Big\rangle \)and \( \mid FEP{W}_{xy}^0\Big\rangle \) are not equal, the carrier information is exchanged by the 1-CONT. In the end, quantum image ∣CW〉,∣K1〉and∣K2〉are obtained.
3.2.2 Superimposed Embedded Watermark Scheme
The first method of watermark image embedded scheme is introduced in section 3.2.1. Thus, the other method is introduced in this section and the detailed embedded circuit is shown in Fig. 11.
Among them, ∣K1〉 represents an image with only one bit-plane, which is shown in Eq. (5),∣K2〉represents the key image that stores the original carrier image \( \mid {C}_{xy}^0\Big\rangle \)information. In this embedded circuit, firstly, utilizes the 1-CNOT record and store the \( \mid FEP{W}_{xy}^0\Big\rangle \) information. Secondly, if the state of the two bit-plane contained in the quantum image∣FEPW〉is not the same, the upper bit bit-plane is embedded in the low order through 1-CNOT. Finally, if the state of changed \( \mid FEP{W}_{xy}^0\Big\rangle \) and \( \mid {C}_{xy}^0\Big\rangle \)are not equal, this qubit is exchanged through the control swap gates. In the end, three quantum images ∣CW〉,∣K1〉and∣K2〉are obtained, and the quantum image ∣CW〉is the most important of the copyright businessman.
3.3 Watermark Extraction Scheme
The watermark image has been embedded in the carrier image through. However, if copyright businessman wants to get the embedded information that contained in the cover image, the extracting circuit is needed. Thus, the entire extracting circuit is introduced. The extract framework is shown in Fig. 12.
In this figure, the quantum images ∣CW〉,∣K1〉and∣K2〉 are needed.
In Fig. 12, quantum images ∣CW〉,∣K1〉and∣K2〉 are obtained through NEQR, and then scrambled expanded watermark image is gained by quantum extract circuit. In the end, the original watermark image is restored through a set of reversible quantum circuits. The concrete operation can be divided into the following several steps.
-
Step 1:
A classical image that contained hidden information is loaded, next those relative key images are processed by NEQR quantum presentation.
-
Step 2:
After those relative images has been prepared, the carrier image that hidden secret information, and the key image is operated through the quantum extract circuit. Finally, the scrambled watermark image is gained. But due to the quantum extract circuit contain two kinds of watermark method, the watermark extract method is described in section 3.3.1and 3.3.2.
-
Step 3:
Quantum extract operation has been completed, but there gets a chaotic and unrecognized image that rooted in the carrier image. Next, reversible Fibonacci scramble is used to get the expanded watermark image. According to the Eq. (4), the chaotic and unrecognized image is restored, so that expanded watermark image is gotten. However, this image is not recognized, next the quantum restored circuit that shown in Fig. 13 is utilized to restore the watermark image.
In the Fig. 13, ∣y0⋯yn〉 and ∣x0⋯xn〉 represents the expanded watermark’s coordinates information, ∣y0⋯yn − 1〉 and ∣x0⋯xn − 1〉represents the restored watermark’s coordinates information, \( \mid {C}_{xy}^0\cdots {C}_{xy}^7\Big\rangle \) represent the restored watermark’s bit-plane pixel information. Firstly, utilizes the quantum state ∣x0〉 and ∣y0〉 are used to express the expanded coordinates. Secondly, according to the relative coordinates, the original watermark image bit-plane pixels is assigned in new quantum coordinates. Finally, this image is restored through N-CNOT. However, this image is chaotic, so that watermark image is not recognized. On the basis of image preprocessing, reversible bit-plane is used to restore the original watermark image. According to the Fig. 5 bit-plane scramble circuit, reversible scramble circuit is shown in Fig. 14.
In Fig. 14, the scrambled image bit-plane is exchanged in accord with order “0–4”, “1–5”, “2–6”, “3–7”. And then 1-CNOT is utilized when the “0123” bit-plane quantum state is∣1〉.
-
Step 4:
the original watermark image is retrieved through quantum measurement.
3.3.1 Self-Embedded Extract Method
According to the step2, we will introduce the first method. This circuit is shown in Fig. 15.
Firstly, the watermarked carrier image \( \mid C{W}_{xy}^0\Big\rangle \) is recorded through auxiliary qubit ∣0〉, which represented the watermark least qubit\( \mid {W}_{xy}^0\Big\rangle \). Secondly, utilizes swap gates to restore carrier image, then the carrier image is restored. Finally, the key image ∣K1〉 is recorded through auxiliary qubit ∣0〉, which represented the watermark image qubit\( \mid {W}_{xy}^1\Big\rangle \). In the end, the watermark image is extracted.
3.3.2 Superimposed Embedded Extract Method
Compared with the first one self-embedded extract method, the other superimposed embedded extract method is simple and easy to implement. The detailed circuit is shown in Fig. 16.
In the Fig. 16, firstly, the original carrier image\( \mid C{W}_{xy}^0\Big\rangle \) is recorded through auxiliary qubit∣0〉, which represented the watermark qubit\( \mid {W}_{xy}^1\Big\rangle \). Secondly, the carrier image is restored by swap gates. Finally, the watermark image least qubit \( \mid {W}_{xy}^0\Big\rangle \) is restored through 1-CNOT recorded the key image ∣K1〉, so that encrypted watermark image is obtained. In the end, the original carrier image is restored while the encrypted watermark image is also acquired.
4 Experiments and Analysis
At present, quantum computers are in the theoretical stage and there is no available quantum computer to analyze this method. Thus, this article utilizes MATLAB2014b to simulate this experiment on a classical computer. So, this section gives the simulation experiment results of the proposed watermarking scheme [25]. The simulations are built on linear algebraic constructions. The quantum states and the quantum operations are simulated by complex vectors and unitary matrices [25]. In this experiment, we use bridge image [26], cameraman image, Barbara image and baboon image and so on to verify this idea. The watermark image size is256 × 256and carrier image size is512 × 512.
4.1 Robust Analysis
The robustness of the watermark, is the watermark information must be difficult to remove, or any attempt to destroy the watermark will result in a serious degradation of the image quality. Therefore, salt and pepper noise are added to the watermarked carrier image in this paper, and the robustness of the proposed scheme is obtained. as a rule, the PSNR is utilized to observe the watermark-image’s visually effect. If the visually effect is higher, the robustness of watermark is stronger. The PSNR as defined in the following Eq. (6). The robustness of the self-embedded method is shown in Table 1. The robustness of the superimposed embedded method is shown in Table 2.
In Table 1, it is seen that the comparison result between the extracted watermarked image and the original watermarked image. But the watermark image under this self-embedded method has a few missing, the robustness of self-embedded method is about 38db. Meanwhile, the robustness of superimposed embedded method is as same as the self-embedded method. In Table 2, the robustness of superimposed method is about 37db.
4.2 Visual Analysis
The peak-signal-to-noise ratio(PSNR), being one of the most used quantity in classical for comparing the fidelity of a watermarked image with its original version, will be used as our embedded carrier image evaluation quantity by transforming the quantum images into classical forms [26]. PSNR as defined in the following eq. (6). The more the watermarked image resembles its carrier image, the more the value of PSNR increases.
Therein, MAXIis the maximum possible gray-level value of the image. MSE is the mean squared error for two gray-scale images, a carrier image (or watermark) I and its watermarked version (or extracted watermark) O, as defined in the following Eq. (7).
The experiment result is shown in Fig. 17.
In the Fig. 17, (a) represent the carrier image, (b) represent the original watermark image, (c) represent the watermarked carrier image, (d) represent the extracted watermark image. In order to detect watermarked carrier image visual quality, the peak-signal-to-noise ratio is given in Tables 3 and 4.
Observe the peak signal-to-noise ratios of carrier image in the two watermarking embedded methods in Tables 3 and 4. The two watermark methods proposed in this paper have similar peak-to-noise ratios as same as others watermarking scheme. However, the two watermarking embedded methods in this paper have some other advantages. First, the embedding capacity is embedded 2-qubit information bit in the carrier image least significant qubit. Second, the circuit are simpler and more convenient in this paper.
4.3 Image Grey-Value Analysis
Now, there is another tool to evaluate the fidelity of the watermarking image, which is the histogram of the image. The images’ histogram is the frequency used to display the pixel intensity values. In the images’ histogram, the x-axis shows the grayscale intensity, and the y-axis shows the frequencies of these intensities. The histogram of the image has many applications in image processing. One of the applications is image analysis [27]. By looking at the histogram of the image, we can compare the grayscale and intensity of the image after the watermarked of the image. In order to further test the results of the experiment, a histogram of the three original carrier images and the embedded watermarked carrier image in Fig. 18. According to Fig. 18, the histogram of the watermarked image is very consistent with the histogram of the carrier image.
5 Conclusion
In this article, two superimposed watermarking methods have been proposed. The watermark and carrier image sizes are used in this paper are 256 × 256 and 512 × 512, respectively.
In the paper, the two of the watermarking methods is proposed. Firstly, the watermark image and the carrier image are transformed into the quantum images by NEQR. Secondly, the watermark image is encrypted for the first time utilizes a new bit-plane scramble algorithm. Thirdly, the watermark image is extended to the same image as the carrier through the quantum expansion circuit. Fourthly, utilizes the Fibonacci scramble to encrypt the watermark image again. After the fourth operation has been completed, the watermark image will be embedded in the carrier image. The first self-embedded method is to separate all of the watermark image qubit planes, and then the qubit planes are respectively embedded in the least significant bits of the carrier image. Control swap gates and 1-CNOT gates is employed to complete this operation. The other superposition embedding method is to embed the high qubits of the watermark image in the least qubits of the watermark image, and then the operated lowest bits is embedded in the carrier image. Finally, a watermarked carrier image is obtained.
Next, the extraction of the watermark image is introduced. Firstly, the classical image is converted into a quantum image by NEQR. Secondly, the watermark image is extracted through detailed extract circuit, which is divided into two kinds of cases. The extracting method is similar, which is utilizes 1-CNOT and swap gate to accomplish this operation. Thirdly, the extracted watermark image is converted into the original watermark image by inverse Fibonacci, inverse extension and inverse qubit-plane scramble. Finally, the watermark image is restored.
References
N, X., Zhu, J., D, L., et al.: Quantum factorization of 143 on a dipolar-coupling nuclear magnetic resonance system. Phys. Rev. Lett. 108(13), 130501 (2012)
Van d, S.T., Wang, Z.H., Blok, M.S., et al.: Decoherence-protected quantum gates for a hybrid solid-state spin register. Nature. 484(7392), 82–86 (2012)
Pla, J.J., Tan, K.Y., Dehollain, J.P., Lim, W.H., Morton, J.J.L., Jamieson, D.N., Dzurak, A.S., Morello, A.: A single-atom electron spin qubit in silicon. Nature. 489(7417), 541–545 (2012)
Fijany, A., Williams, C.P.: Quantum wavelet transforms: fast algorithms and complete circuits. Lect. Notes Comput. Sci. 1509, 10–33 (1998)
Tseng C C., Hwang T M.: Quantum circuit design of 8×8 discrete cosine transform using its fast computation flow graph// IEEE International Symposium on Circuits and Systems. IEEE. 1, 828-831(2005)
Zhang, Y., Lu, K., Gao, Y., Xu, K.: A novel quantum representation for log-polar images. Quantum Inf. Process. 12(9), 3103–3126 (2013)
Sang, J., Wang, S., Li, Q.: A novel quantum representation of color digital images. Quantum Inf. Process. 16(2), 16–42 (2017)
Yang, Y.G., Jia, X., Xu, P., et al.: Analysis and improvement of the watermark strategy for quantum images based on quantum Fourier transform. Quantum Inf. Process. 12(2), 793–803 (2013)
Song, X.H., Wang, S., Liu, S., Abd el-Latif, A.A., Niu, X.M.: A dynamic watermarking scheme for quantum images using quantum wavelet transform. Quantum Inf. Process. 12(12), 3689–3706 (2013)
Song, X., Wang, S., El-Latif, A.A.A., et al.: Dynamic watermarking scheme for quantum images based on Hadamard transform. Multimedia Systems. 22(2), 273–274 (2016)
Jiang, N., Zhao, N., Wang, L.: LSB based quantum image steganography algorithm. Int. J. Theor. Phys. 55(1), 107–123 (2016)
Miyake, S., Nakamae, K.: A quantum watermarking scheme using simple and small-scale quantum circuits. Quantum Inf Process. 15(5), 1849–1864 (2016)
Sang, J., Wang, S., Li, Q.: Least significant qubit algorithm for quantum images. Quantum Inf. Process. 15(11), 4441–4460 (2016)
Zhou, R.G., Zhou, Y., Zhu, C., Wei, L., Zhang, X., Ian, H.: Quantum watermarking scheme based on INEQR. Int. J. Theor. Phys. 57(4), 1120–1131 (2018)
Yuan, S., Mao, X., Zhou, J., Wang, X.: Quantum image filtering in the spatial domain. Int. J. Theor. Phys. 56(8), 2495–2511 (2017)
Li, P., Xiao, H.: An improved filtering method for quantum color image in frequency domain. Int. J. Theor. Phys. 57(1), 258–278 (2018)
Mastriani, M.: Quantum Boolean image denoising. Quantum Inf. Process. 14(5), 1647–1673 (2015)
Hua, T., Chen, J., Pei, D., Zhang, W., Zhou, N.: Quantum image encryption algorithm based on image correlation decomposition. Int. J. Theor. Phys. 54(2), 526–537 (2015)
Song, X.H., Wang, S., El-Latif, A.A.A., et al.: Quantum image encryption based on restricted geometric and color transformations. Quantum Inf. Process. 13(8), 1765–1787 (2014)
Zhou, N., Hu, Y., Gong, L., et al.: Quantum image encryption scheme with iterative generalized Arnold transforms and quantum image cycle shift operations. Quantum Inf. Process. 16(6), 1–23 (2017)
Zhang, Y., Lu, K., Gao, Y., Wang, M.: A novel enhanced quantum representation of digital images. Quantum Inf. Process. 12(8), 2833–2860 (2013)
Ping, F., Zhou, R.-G., Jing, N., Li, H.-S.: Geometric transformations of multidimensional color images based on NASS. Inf Sci. 340–341 (2016)
Jiang, N., Wang, L.: Analysis and improvement of the quantum Arnold image scrambling. Quantum Inf. Process. 13(7), 1545–1551 (2014)
Ri-gui, Z., Ya Juan, S., Fan, P.: Quantum image gray-code and bit-plane scrambling. Quantum Inf Process. 14(5), 1717–1734 (2015)
Ri-Gui, Z., Wenwen, H., Ping, F.: Quantum watermarking scheme through Arnold scrambling and LSB steganography. Quantum Inf. Process. 16(9), 212–233 (2017)
Jianzhi, S., Shen, W., Qiong, L.: Least significant qubit algorithm for quantum images. Quantum Inf. Process. 15(11), 4441–4460 (2016)
Caraiman, S., Vasile, M.: Histogram-based segmentationof quantum image. Theor. Comput. Sci. 529, 46–60 (2014)
Acknowledgements
This work is supported by the National Natural Science Foundation of China under Grant No. 61463016, “Science and technology innovation action plan” of Shanghai in 2017 under Grant No. 17510740300, and the advantages of scientific and technological innovation team of Nanchang City under Grant No. 2015CXTD003;
Author information
Authors and Affiliations
Corresponding author
Additional information
Yang Zhou and Ri-Gui Zhou are co-first authors.
Rights and permissions
About this article
Cite this article
Zhou, Y., Zhou, RG., Liu, X. et al. A Quantum Image Watermarking Scheme Based on Two-Bit Superposition. Int J Theor Phys 58, 950–968 (2019). https://doi.org/10.1007/s10773-018-3987-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-018-3987-9