Abstract
Quantum watermarking is a technique which embeds the invisible quantum signal such as the owners identification into quantum multimedia data (such as audio, video and image) for copyright protection. In this paper, using a quantum representation of digital images a new quantum watermarking protocol including quantum image scrambling based on Least Significant Bit (LSB) is proposed. In this protocol, by using m-bit embedding key K 1 and m-bit extracting key K 2 a m-pixel gray scale image is watermarked in a m-pixel carrier image by the original owner of the carrier image. For validation of the presented scheme the peak-signal-to-noise ratio (PSNR) and histogram graphs of the images are analyzed.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Since the presentation of the first quantum key distribution protocol by Bennett and Brassard in 1984 [1], quantum information and quantum computation have spurred a number of theoretical and practical research. Recent research on quantum computation and quantum information allowed to use it in applications related to information security in real life [2–14].
New improvements in the field make it possible to represent and processes classical media using quantum point of view [15–33].
In 2011, a Flexible Representation for Quantum Images (FRQI) was proposed by Phuc, Fangyan Dong and Kaoru Hirota [24]. The FRQI, is similar to the pixel representation for images on traditional computers, it captures the essential information about the colors as well as the corresponding positions of every point in an image and integrates them into a quantum state. In 2013, Zhang, Lu, Gao and Wang proposed a novel enhanced quantum representation (NEQR) for digital images using the basis state of a qubit sequence to store the gray scale value of every pixel instead of an angle encoded in a qubit in the FRQI method [25]. Therefore, to store the digital image in NEQR scheme, two entangled qubit sequences are used to store the whole image, which represent the gray scale and positional information of all the pixels.
Due to advances in Information and Communications Technology (ICT), most of information is kept electronically. Digital representation of media facilitates access and potentially improves the portability, efficiency, and accuracy of the information presented. Undesirable effects of facile data access include an increased opportunity for violation of copyright and tampering with or modification of content, Consequently, the security of information has become a fundamental issue. Generally, information hiding, i.e., watermarking and steganography can be considered as efficient tools for protecting digital information from above mentioned undesirable effects. Up to now there are many quantum data hiding and quantum watermarking schemes presented [34–42].
In 2010 Z.G. Qu et al. proposed a novel quantum steganography protocol based on quantum secure direct communication where, employing entanglement swapping of Bell states, secret messages are transmitted in a hidden channel within the improved Ping-Pong protocol [34]. Quantum steganography protocols with noisy quantum channels where proposed by B. A. Shaw et al. [35], where two types of protocols were considered. In the first one the hidden quantum information was stored locally in the codeword, and in the second type of protocols the hidden quantum information was embedded in the space of error syndromes. In 2012, N. Fatahi and M. Naseri [36] proposed a secure quantum watermarking using entanglement swapping is proposed. In [36] using the entanglement swapping a hidden layer of secure message under the conventional first layer of secure information sequence is build up. Later, in 2013, a quantum images watermarking strategy is proposed based on flexible representation for quantum images (FRQI) [37]. Also another quantum image watermarking strategy was proposed by W .W. Zhang et al., in 2013. In the protocol proposed by W. W. Zhang et al., watermark image is embedded into the fourier coefficients of the quantum carrier image, in which the carrier images will not be visually affected by the watermark images [38]. Afterwards, X. Song et al. proposed a dynamic watermarking scheme for quantum images based on Hadamard transform [39]. Recently, a novel multi-party quantum steganography protocol based on quantum secret sharing is proposed by L. Liu et al. [40]. Very Recently, a blind LSB steganography in the form of quantum circuits have been proposed by N. Jiang et al. [41]. The proposed LSB based quantum steganography algorithms are based on the novel enhanced quantum representation (NEQR) for quantum images. The first algorithm is plain LSB in which the pixels LSB are substituted by message bits directly. The second algorithm is block LSB in which a message bit is embedded into a number of pixels that belong to one image block [41].
In this paper a novel LSB based quantum watermarking protocol is proposed. In the presented scheme using a quantum representation of digital images, a m-bit embedding key K 1 and m-bit extracting key K 2 a m-pixel gray scale image is embedded in and extracted from a m-pixel carrier image. This paper is organized as follows: The next section introduces the novel enhanced quantum representation of digital images (NEQR protocol) proposed by and LSB based quantum image steganography algorithm. Our proposed protocol for quantum watermark is presented in Section 3. Section 4 presents the software simulation of the protocol. Finally, a short conclusion is given in Section 5.
2 The Least Significant Bit (LSB) Based Quantum Image Steganography Algorithm
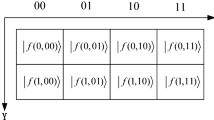
A Novel Enhanced Quantum Representation of digital images (NEQR protocol) was proposed in 2013 [23]. According to the NEQR protocol, a quantum image can be represented as follows:
The two parts in the NEQR protocol, |c i 〉 and |i〉 encode information about the color and their corresponding positions in the image, respectively. In this view, the size of the quantum image is 2n×2n. Where, the location information |i〉 includes two parts: the vertical and the horizontal parts,
It encodes the first n-qubit |y n−1〉,|y n−2〉,...,|y 0〉 along the vertical location and the second n-qubit |x n−1〉,|x n−2〉,...,|x 0〉 along the horizontal axis. Therefore, NEQR needs q + 2n qubits to represent a 2n×2n image with gray range 2q.
Based on NEQR protocol, a least significant bit (LSB) based quantum image steganography algorithm has been recently proposed Nan Jiang et al., [11], where by using a LSB embedding circuit a binary 2n×2n image message |M〉 is embedded in a 2n×2n cover image |I〉 with gray range 2r. Also, a extracting circuit has been presented for extracting the embedded image.
The NEQR representation of the cover image |I〉 and the message image |M〉 can be written as below:
In the circuit of plain LSB embedding, 2n CNOT gates are used to test whether the position information of |I〉 and |M〉 is the same. If they are equal, the least significant bit \(|{c_{i}^{0}}\rangle \) of |I〉 and the message bit |m i 〉 will be swaped to get the stego image.
In the extracting circuit 2n Hadamard gates are employed to turn the initial all |0〉 state to an empty binary image. Afterwards, using 2n CNOT gates, if the position information of |I〉 and |M〉 is equal, the least significant bit \(|{c_{i}^{0}}\rangle \) of |I〉 and the message bit |m i 〉 will be swaped to get the message [20].
3 A Novel Quantum Watermark Based on LSB
Considering the least significant bit (LSB) based quantum image steganography algorithm, a protocol for quantum LSB based quantum watermarking is proposed, where, for the aim of copyright prove, a watermark image |W〉 is embedded into a carrier image |C〉. Now let us present the protocol for LSB quantum based watermarking.
According to NEQR scheme, the carrier image |C〉 and the watermark image |W〉 can be written as below:
where:
The LSB quantum based watermarking protocol includes two procedures, the embedding Procedure and the extracting one. A simple outline for the embedding procedure and the extracting procedure in our schema is given in Fig. 1a and b respectively.
In the proposed protocol, two image key: |K1〉 and |K2〉 is considered as embedding key and extracting key respectively, i.e., |K1〉 is a 2n×2n binary image embedding key that the embedder used this for watermarking. while |K2〉 is an other 2n×2n binary image extracting key that is generated during the embedding procedure. In NEQR view, |K1〉 and |K2〉 can be represented as follows:
where:
The embedding procedure and the extracting procedure can be presented as follows:
3.1 The Embedding Procedure
The embedding procedure of the proposed protocol can be accomplished in two steps:
-
1.
Preparation step:
-
(a)
If the size of watermark image is less than that of carrier image, it should be polished to the size of carrier image. i.e., the watermark image is covered by the carrier one. In other terms, the area in watermark image corresponding to the exposed region in carrier image is filled out with the corresponding pixels in the carrier image; by doing so, the watermark image would be the same size as the carrier image.
-
(b)
In the proposed protocol, to improve the power to resist invalid attack and accordingly enhance the security, prior to the embedding procedure, the watermark image has to be scrambled [the image scrambling transforms a meaningful image into a meaningless or disordered image].
Suppose that the watermark image is binary 2n×2n with color range 21. This means colors in watermark image are 0 or 1 (white or black). In the NEQR representation, the watermark image is represented as below:
$$|W\rangle=\frac{1}{2^{n}}\sum\limits^{2^{2n}-1}_{i=0}|w_{i}\rangle\otimes|i\rangle, w_{i}\in\{0,1\}, i=0, 1, ..., 2^{2n}-1, $$$$ |i\rangle=|y\rangle|x\rangle=|y_{n-1},y_{n-2}...y_{0}\rangle|x_{n-1},x_{n-2}...x_{0}\rangle, y_{j}, x_{j}\in\{0,1\}, $$(8)where, |w i 〉 is color information in position |i〉. Here the image-scrambling method renders the image content unintelligible based on the keys only known to the operator.Consider a 2n×2n image, and two 2n-bit keys M={M(1),M(2),...,M(2n)} and N={N(1),N(2),...,N(2n)}. For scrambling, assume M(i) and N(j) are the ith and jth bits of M, N keys respectively. If \(M(i)\bigoplus N(j)=1\), then the color value at position (i,j) of watermark image is applied by the I operation; otherwise, the color value at position (i,j) of watermark image is applied by the X operation, where,
$$I=\left( \begin{array}{cc} 1 & 0 \\ 0 & 1 \\ \end{array} \right), X= \left( \begin{array}{cc} 0 & 1 \\ 1 & 0 \\ \end{array} \right). $$(9)Take 4×4 image for as an example. Let M=1,0,1,0 and N=0,0,1,1, then the scrambled image is shown in Fig. 2, from which we can see that a meaningful image is scrambled into a meaningless one. The quantum circuit corresponding to the scrambling is shown in Fig. 3.
The inverse image-scrambling procedure is similar to that of the scrambling procedure with the scrambled image as the input. The gates used in the inverse image-scrambling procedure is the same as the circuit for image-scrambling, but the order is inverse. Thus the resulted image is the original image.According to the quantum image scrambling mentioned above, the resized watermark image is scrambled by the embedder.
-
(a)
-
2.
Embedding step:
After preparation step, for embedding, the embedder produces a 2n×2n binary image embedding key K1 . This key will be used to determine the position that the watermark pixels will be embedded in and is only known to the embedder. Then, each position in watermark image |W〉 will be compared with the positions in carrier image |C〉.
-
–
If the positions are equal, then the corresponding color values will be compared.
-
–
If the color value |W i 〉 and the color value \(|{C^{0}_{i}}\rangle \) are equal, no changes will be made.
-
–
If the color value |W i 〉 and the color value \(|{C^{0}_{i}}\rangle \) are not equal, then:
-
if the color value |K1 i 〉=0 then the color value |W i 〉 will be embedded in \(|{C^{0}_{i}}\rangle \) (it means, a not gate is applied to the LSB of |C i 〉 ). Simultaneously, the color value |K2 i 〉 is set to 1.
-
if color value |K1 i 〉=1, then no change is needed. Simultaneously, the color value |K2 i 〉 is set to 1.
-
-
–
By doing so, the watermark image is embedded into the carrier image.
-
–
3.2 Quantum Watermark Images Extracting Procedure
Here, it will be shown how the copyright owner can extract watermark image from the carrier Image using |K1〉 and |K2〉. Prior to the extraction, an empty 2n×2n binary image, i.e., W o u t is prepared by the embedder, where,
On the other hands, all of the color values in |W o u t 〉 is set to 0. The extracting procedure can be done in the following steps:
For(i:0 to i:22n−1),
-
if(K2 i =1) then
-
if (K1 i =0) then \(w^{i}_{out}={c^{0}_{i}},\) else if (K1 i =1) then \(w^{i}_{out}={c^{0}_{i}}\oplus 1.\)
-
By completing the extraction procedure, one can see that the original scrambled polished watermark image could be extracted. Quantum circuit for the watermarking procedure is presented in Figs. 4a and 4b. Finally, by applying inverse image scrambling algorithm, the original polished watermark image will be simply extracted.
Needless to say that in the protocol, a quantum comparator circuit is needed for comparing procedure. Wang et al. [3] proposed a quantum comparator circuit presented in Fig. 5. The comparator compares a and b, where |a〉=|a n−1...a 1 a 0〉 and |b〉=|b n−1...b 1 b 0〉, a i ,b i ∈0,1,i = n−1,...,1,0. Qubits |c 1〉 and |c 0〉 are outputs.
-
If c 1 c 0=10, then a>b
-
If c 1 c 0=01, then a<b
-
If c 1 c 0=00, then a = b
In Fig. 4, the embedding circuit and the extracting circuit are shown as block diagrams. The comparator block, the embedding block and the extracting blocks are shown in Figs. 5, 6a and b. respectively.
4 Simulations of Quantum Watermark Embedding and Extracting Procedure
To execute the protocol more convincingly, it is simulated using a classical computer with Intel(R) Core(TM) 2 Duo CPU E7300 2.66 GHz, 2.00 GB Ram equipped with the MATLAB 2009 environment.
The peak-signal-to-noise ratio (PSNR), is one of the most used quantity in classical image processing for comparing the fidelity of a watermarked image with its original version. Here the PSNR is considered as our embedded carrier image evaluation quantity by transforming the quantum images into classical forms. It is most easily defined via the mean squared error (MSE), which for two m×n monochrome images (the original carrier image I and its watermarked version K) is defined as
The PSNR is defined by
where, M A X I is the maximum pixel value of image I. In our scheme, I and J correspond to the original image and the watermark image respectively. All of the gray-carrier images used in our simulations are shown in Fig. 7, and their corresponding PSNR values with different watermark images are presented in Table 1. According to Fig. 7 and Table 1, it can be seen that the watermark image’s embedding doesn’t affect the carrier images visual effect. And the PSNR is acceptable for use.
Another tool for evaluating of the fidelity of a watermarked image with its original version of an image is the image’s histogram. An image histogram, shows frequency of pixels intensity values. In an image histogram, the x axis shows the gray level intensities and the y axis shows the frequency of these intensities. Histograms has many uses in image processing. One of the applications is the analysis of the image [42]. By just looking at an image’s histogram histogram, one can predict important data about an image. By comparing the histogram graphs of two images one can find in what content the images are match. For more convince following in Fig. 8 the histogram graphs of the six original images and the histogram graphs of their corresponded watermarked images where the camera image is considered as a watermark image is presented. According to the Fig. 8 the histogram of the watermarked images are in good agreement with the original ones.
Finally for comparing the results of the proposed scheme with the previous one, the presented LSB based quantum watermarking is compared with Nan Jiangs algorithm [42] in Table 2. Although the steganography and the watermarking are two different kinds of data hiding methods with different objectives, since the Nan Jiang’s algorithm for quantum steganography and our proposed protocol for image watermarking are following the same method in data hiding (LSB method), comparing the (PSNR) of the two protocols would be a useful tool for comparing the fidelity of a watermarked/stegano image with its original version. According to Table 2, one can see that comparing with the previous Nan Jiang’s algorithm for quantum steganography, in the proposed LSB based quantum watermarking scheme about six percent improvement is achieved for PSNR quantity.
5 Conclusion
The essential goal of watermarking is to resist not only the geometric distortion attack but also the signal processing attack. The performance of a watermarking method is depended on various parameters to be considered. In classical information there is no watermarking procedure resists all types of attack. But, still many researchers are working on finding better technique which will give more robust. In this paper, a novel LSB based quantum watermarking protocol is presented in which through m-bit embedding key K 1 and m-bit extracting key K 2, a m-pixel gray scale image is watermarked in a m-pixel carrier image by the original owner of the carrier image. In this scheme to represent quantum images, the Novel Enhanced Quantum Representation of digital images (NEQR protocol) presented by Zhang, Yi, et al. in 2013 [23] is employed. A close inspection of the presented LSB based quantum watermarking algorithm indicates that only the legal owner of the original carrier image knows the extracting key K 2, no attacker can reach the watermarked secret image, so the presented watermarking is a robust watermark protocol. Furthermore, by analyzing the histogram graphs one can see that the histogram graphs of the original images and their corresponding watermarked images are in a good agreement and the original cover image and the watermarked signal are perceptually indistinguishable, so the protocol is imperceptible. Finally, compare with the Nan Jiang’s LSB based quantum steganography algorithm [42], in the presented LSB based quantum watermarking about six percent improvement is observed in the PSNR.
References
Bennett, C.H., Brassard, G.. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India (IEEE, New York, 1984), p 175
Zhang, Y.S., Li, C.F., Guo, G.C.: Quantum key distribution via quantum encryption. Phys. Rev. A 64, 024302 (2001)
Zhou, N., Zeng, G., Zeng, W., Zhu, F.: Cross-center quantum identification scheme based on teleportation and entanglement swapping. Opt. Commun. 254, 380 (2005)
Zhou, N., Liu, Y., Zeng, G., Xiong, J., Zhu, F.: Novel qubit block encryption algorithm with hybrid keys. Phys. A 375, 693 (2007)
Naseri, M.: Eavesdropping on secure quantum telephone protocol with dishonest server. Opt. Commun. 282, 278–282 (2009)
Zhou, N.R., Wang, L.J., Ding, J., Gong, L.H.: Quantum deterministic key distribution protocols based on the authenticated entanglement channel. Phys. Scr. 81, 045009 (2010)
Naseri, M.: A weak blind signature based on quantum cryptography. Int. J. Phys. Sci. 6, 5051 (2011)
Gao, G., Fang, M., Yang, R.M.: Quantum Secure Direct Communication by Swapping Entanglements of 3×3−Dimensional Bell States. Int. J. Theor. Phys. 50, 882–887 (2011)
Liu, D., Chen, J. L., Jiang, W.: High-capacity quantum secure direct communication with single photons in both polarization and spatial-mode degrees of freedom. Int. J. Theor. Phys. 51, 2923–2929 (2012)
Sun, Z.W., Du, R.G., Long, D.Y.: Quantum secure direct communication with Two-Photon Four-Qubit cluster states. Int. J. Theor. Phys. 51, 1946–1952 (2012)
Ren, B.C., etal: Photonic spatial Bell-state analysis for robust quantum secure direct communication using quantum dot-cavity systems. Eur. Phys. J. D 67, 30 (2013)
Gu, B., etal: Robust quantum secure communication with spatial quantum states of single photons. Int. J. Theor. Phys. 52, 4461–4469 (2013)
Zhang, Q.N., Li, C.C., Li, Y.H., Nie, Y.Y.: Quantum secure direct communication based on Four-Qubit cluster states. Int. J. Theor. Phys. 52, 22–27 (2013)
Naseri, M., et al.: A scheme for secure quantum communication network with authentication using GHZ-like states and cluster states controlled teleportation. Quantum Inf. Process 14, 4279–4295 (2015)
Venegas-Andraca, S.E., Bose, S.: Storing, processing and retrieving an image using quantum mechanics. Proceeding of the SPIE conference quantum information and computation (2003)
Venegas-Andraca, S.E., Ball, J.L.: Processing images in entangled quantum systems. Quantum Inform. Process 9, 1–11 (2010)
Le, P.Q., Iliyasu, A.M., Dong, F., Hirota, K.: Fast geometric transformations on quantum images. Int. J. Appl. Math. 40(3), 113–123 (2010)
Iliyasu, A.M., Le, P.Q., Dong, F., Hirota, K.: Watermarking and authentication of quantum images based on restricted geometric transformations. Inf. Sci. 186, 126–149 (2011)
Le, P.Q., Doyng, F., Hirota, K.: A flexible representation of quantum images for polynomial preparation. Quantum Inf. Process. 10(1), 6384 (2011)
Zhou, R.G., Wu, Q., Zhang, M.Q., Shen, C.Y.: Quantum image encryption and decryption algorithms based on quantum imagegeometric transformations. Int. J. Theor. Phys. 52(6), 1802–1817 (2013)
El-Latif, A.A.A., Li, L., Wang, N., Han, Q., Niu, X.: A new approach to chaotic image encryption based on quantum chaotic system, exploiting color spaces. Signal Process. 93(11), 2986–3000 (2013)
Yang, Y.G., Jia, X., Xu, P., Tian, J.: Analysis and improvement of the watermark strategy for quantum images based on quantum Fourier transform. Quantum Inf. Process 12(8), 2765–2769 (2013)
Zhang, Y., Lu, K., Gao, Y.H., Wang, M.: NEQR: A novel enhanced quantum representation of digital images. Quantum Inf. Process 12(12), 2833–2860 (2013)
Song, X.H., Wang, S., Liu, S., Abd El-Latif, A.A., Niu, X.M.: A dynamic watermarking scheme for quantum images using quantum wavelet transform. Quantum Inf. Process 12(12), 3689–3706 (2013)
Yuan, S., Mao, X., Chen, L., Xuke, Y.: Quantum digital image processing algorithms based on quantum measurement. Optik 124(23), 6386–6390 (2013)
Song, X.H., Wang, S., Liu, S., Abd El-Latif, A.A., Niu, X.M.: Dynamic watermarking scheme for quantum images based on Hadamard transform. Multimedia Systems 20(4), 379–388 (2014)
Zhang, Y., Lu, K., Gao, Y.H., Sobel, Q.: A novel quantum image edge extraction algorithm. Sci. China Inf. Sci. 58(1), 1–13 (2014)
Jiang, N., Wang, L., Wu, W.Y.: Quantum Hilbert image scrambling. Int. J. Theor. Phys. 53(7), 2463–2484 (2014)
Zhou, R.G., Sun, Y.J., Fan, P.: Quantum image Gray-code and bit-plane scrambling. Quantum Inf. Process 14(5), 1717–1734 (2015)
Zhou, N.R., Hua, T.X., Gong, L.H., Pei, D.J., Liao, Q.H.: Quantum image encryption based on generalized Arnold transform and double random phase encoding. Quantum Inf. Process 14(4), 1193–1213 (2015)
Hua, T., Chen, J., Pei, D., Zhang, W., Zhou, N.R.: Quantum image encryption algorithm based on image correlation decomposition. Int. J. Theor. Phys. 54(2), 526–537 (2015)
Zhang, Y., Lu, K., Xu, K., Gao, Y., Wilson, R.: Local feature point extraction for quantum images. Quantum Inf. Process 14(5), 1573–1588 (2015)
Zhou, R.G., Sun, Y.J.: Quantum multidimensional color images similarity comparison. Quantum Inf. Process 14(5), 1605–1624 (2015)
Qu, Z.G., Chen, X.B., Zhou, X.J., Niu, X.X., Yang, Y.X.: Novel quantum steganography with large payload. Opt. Commun. 283(23), 47824786 (2010)
Shaw, B.A., Brun, T.A.: Quantum steganography with noisy quantum channels. Phys. Rev. A 83, 022310 (2011)
Fatahi, N., Naseri, M.: Quantum watermarking using entanglement swapping. Int. J. Theor. Phys. 51, 20942100 (2012)
Zhang, W.W., Gao, F., Liu, B., Jia, H., Wen, Q.Y., Chen, H.: A quantum watermark protocol. Int. J. Theor. Phys. 52, 504–513 (2013)
Zhang, W.W., Gao, F., Liu, B., Wen, Q.Y., Chen, H.: A watermark strategy for quantum images based on quantum Fourier transform. Quantum Inf. Process 12(4), 793–803 (2013)
Song, X., Wang, S., El-Latif, A.A.A., Niu, X.: Dynamic watermarking scheme for quantum images based on Hadamard transform. Multimedia Systems 20, 379–388 (2014)
Liu, L., Tang, G.M., Sun, Y.F., Yan, S.F.: Quantum steganography for multi-party covert communication. Int. J. Theor. Phys. 55, 191201 (2016)
Jiang, N., Zhao, N., Wang, L.: LSB Based Quantum Image Steganography Algorithm. Int. J. Theor. Phys. 55, 107123 (2016)
Caraiman, S., Vasile, M.: Histogram-based segmentationof quantum image. Theor. Comput. Sci. 529, 46–60 (2014)
Acknowledgments
This work is supported by Kermanshah Branch, Islamic Azad University, Kermanshah, IRAN. Also the authors would like to thank Alimorad Ahmadi for his helpful comments and the final edition of the paper and Soheila Gholipour, Yasna Naseri and Viana Naseri for their interests in this work.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Heidari, S., Naseri, M. A Novel LSB Based Quantum Watermarking. Int J Theor Phys 55, 4205–4218 (2016). https://doi.org/10.1007/s10773-016-3046-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-016-3046-3