Abstract
A novel quantum gray-level image encryption and decryption algorithm based on image correlation decomposition is proposed. The correlation among image pixels is established by utilizing the superposition and measurement principle of quantum states. And a whole quantum image is divided into a series of sub-images. These sub-images are stored into a complete binary tree array constructed previously and then randomly performed by one of the operations of quantum random-phase gate, quantum revolving gate and Hadamard transform. The encrypted image can be obtained by superimposing the resulting sub-images with the superposition principle of quantum states. For the encryption algorithm, the keys are the parameters of random phase gate, rotation angle, binary sequence and orthonormal basis states. The security and the computational complexity of the proposed algorithm are analyzed. The proposed encryption algorithm can resist brute force attack due to its very large key space and has lower computational complexity than its classical counterparts.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Information security has become an important topic during the processing on information storage and transmission. Images are one of the most important information representation models and widely used in modern communications. Some random-phase operations and transforms have been introduced to design encryption algorithms, such as random phase encoding [1–3], Hadamard transform [4, 5], fractional Mellin transform [6] and ect. However, with the development of cryptanalysis and computer technology, ingenious methods for breaking the existing image encryption algorithms are presented successively [7–10], which threaten the existing traditional encryption systems.
Quantum computation has been applied in many fields of information sciences [11]. With the development of quantum computation, classical image processing is naturally extended to quantum scenario. Some methods for representing quantum images have been proposed [12–25]. The quantum image can be represented by color. i.e., a quantum state detected from monochromatic electromagnetic waves through special machines and position, and the storing unit was named Qubit Lattice [12, 13]. By mapping pixels into the real ket of Hilbert space, Latorre proposed a new method to complete image compression combined with pixel states [14]. The image color and position can be encoded into one quantum state by a flexible representation of quantum image (FRQI) [15], which keeps the classical properties of color and position. Then color transformation [16, 17], simple geometric transformation [18, 19], and image watermarking [20] were proposed based on FRQI. A 3D feature space was proposed by Le PQ et al to represent visual complexity of images based on structure, noise and diversity (SND) features extracted from the images [21]. Their method provided a rich understanding of the complexity of visual image, and has important applications to determine the capacity and the feasibility of image processing tasks. Ledesma S et al. proposed an optical analogy of quantum entanglement by means of classical image [22], which showed how to interpret some non-local features of the joint measurement by the bidimensional encoding of two-qubit states. A novel enhanced quantum image representation (NEQR) for digital images was invented, which uses the basis state of a qubit sequence to store the gray-scale value of each pixel in the image for the first time [23]. A quantum image representation for log-polar image (QUALPI) was proposed for the storage and processing of images sampled in the log-polar coordinates, which achieves high efficiency of the new quantum image registration algorithm [24]. Moreover, a method for quantum image processing on image storage, retrieval, compression and segmentation in a quantum system was proposed [25].
Consequently, some new quantum algorithms were developed as new theoretical tools for the security of quantum images. Since dissipative quantum maps can be characterized by sensitive dependence on initial conditions, an image encryption scheme based on quantum logistic map is proposed [26], which pointed out a clear direction for image security with quantum maps. In 2013, Zhou RG et al. proposed the quantum gray-scale image encryption and decryption algorithms based on quantum image geometric transformations, and it unfortunately involves repeated quantum image storages [27]. A robust watermark algorithm for quantum images was also proposed, where the watermark image is embedded into the Fourier coefficients of the quantum carrier image [28]. Akhshani A et al. proposed a new color image encryption scheme based on quantum chaotic systems [29]. Yang YG et al. proposed a novel gray image encryption/decryption scheme based on quantum Fourier transform and double random-phase encoding technique, which is enlightening for introducing more optical information processing techniques into quantum scenario [30]. In 2014, a novel dynamic watermarking scheme for quantum images using Hadamard transform and FRQI was proposed [31]. The existing quantum image security algorithms provide references for follow-up study in different aspects.
In this paper, the image correlation decomposition is applied in the field of quantum image encryption. At the same time, quantum random-phase gate, quantum revolving gate and Hadamard transform are used to encode color information of quantum images. A detailed theoretical security analysis is given.
The rest of this paper is organized as follows. In Section 2, quantum gray-scale image representation, quantum image correlation decomposition, quantum revolving gate, Hadamard transform and quantum image superposition are introduced. The proposed quantum image encryption and decryption algorithm is given in Section 3. Section 4 is devoted to the theoretical security analysis and the computational complexity analysis. A brief conclusion is drawn in Section 5.
2 Quantum Image Representation and Transformation
2.1 Quantum Gray-Scale Image Representation
Classical image is represented by a matrix with the same size of the image, i.e. the number of pixels. In classical gray image, the pixel value of each point represents the gray-scale value and the position information. For a quantum image, the gray value and the position information of each pixel are stored into the corresponding quantum states, respectively. Therefore, the quantum image is a quantum system composed of quantum states. Figure 1 depicts the workflow of preparing a new quantum image model from the classical image representation. Suppose M is a classical image of size 2n × 2n, |M〉 is the storage of the whole quantum states for a gray-scale image, the quantum image representation can be expressed as:
where \(\theta \mbox {=}\left ({\theta _{0} ,\theta _{1} ,{\cdots } ,\theta _{2^{2n}-1} } \right )\) is the vector of angles encoding colors, |g(y, x)〉 encodes the color information of quantum image, |i〉 = |yx〉 = |y〉 |x〉 = |y n−1 y n−2 ⋯ y 0〉 |x n−1 x n−2 ⋯ x 0〉 encodes the corresponding positions of the quantum images, |y n − 1 y n − 2 ⋯ y 0〉 encodes the first n-qubit along the vertical location information while |x n − 1 x n − 2 ⋯ x 0〉 encodes the second n-qubit along the horizontal location information, n is the number of quantum bits required for encoding. As a consequence, the unfolded representation for the 2 × 2 gray-scale image in Fig. 2 can be written as:
2.2 Quantum Image Correlation Decomposition
According to the representation of quantum image in (1), we suppose that the locations of k pixels are in the states |y〉 |x + 1〉, |y〉|x + 2〉, ⋯ , |y〉 |x + k〉 , respectively. Thus, the gray values of k pixels are represented by |g(y, x + 1)〉, |g(y, x + 2)〉, ⋯ , |g(y, x + k)〉 , which can be simply rewritten as: |g y, x + 1〉, |g y, x + 2〉,⋯,|g y, x + k 〉, respectively. The k-qubit system composed of k pixels of quantum image can be represented as:
where state vector \(\left |b_{k-1^{\cdots }}b_{1}b_{0}\right \rangle \) is denoted by |i〉, i represents binary number b k − 1⋅⋅⋅b 1 b 0 corresponding to decimal number. w i is the probability amplitude of |i〉 which satisfies the normalization condition \(\sum \limits _{i=0}^{N-1} {{w_{i}^{2}} } =1\). \(\left |g_{y,x+1}g_{y,x+2^{\cdots }}g_{y,x+k}\right \rangle \) is called quantum image correlation decomposition. The above quantum system is an N-dimensional Hilbert space, and the probability amplitude of any one-dimensional state vector can be constructed by a sub-image of corresponding superposition state. According to (3), the probability amplitude w i represents the cosine value of the angle θ y x with the sub-image and the quantum image |M〉 is divided into N sub-images. Obviously, the original image can be restored by the color information of these sub-images.
2.3 Quantum Revolving Gate and Hadamard Transform
Quantum revolving gate is defined as
Suppose \(\left |\phi \right \rangle =\left [ {{\begin {array}{*{20}c} {\cos \theta _{0} } \hfill \\ {\sin \theta _{0} } \hfill \\ \end {array} }} \right ]\), then \(R\left (\theta \right )\left |\phi \right \rangle =\left [ {{\begin {array}{*{20}c} {\cos \left ({\theta _{0} +\theta } \right )} \hfill \\ {\sin \left ({\theta _{0} +\theta } \right )} \hfill \\ \end {array} }} \right ]\).
The single qubit Hadamard transformation H is a unitary transformation.
Hadamard transformation applied on n qubits can be expressed as
2.4 Superposition of Quantum Images
In quantum mechanics, the quantum state of microcosmic particles is described by using the wave function, which can be fully described by a unit vector in Hilbert space. If |ψ 1〉 and |ψ 2〉 are two vectors in a Hilbert space, then
|ψ〉 is also a Hilbert space vector, where c 1, c 2 are two complex numbers which satisfy the condition |c 1|2 + |c 2|2 = 1. Assume that images M A and M B are stored in states |M A 〉 and |M B 〉, respectively. According to the principle of quantum states superposition, if |M A 〉 and |M A 〉 are two vectors in a Hilbert space, the definition of quantum image superposition is:
where |M c 〉 is a superposition image, α and β are the image superposing coefficients which should satisfy the normalization condition |α|2 + |β|2 = 1.
3 Quantum Image Encryption and Decryption Algorithm
3.1 Encryption Algorithm
As the encrypting object is a quantum gray-scale image, the corresponding plain-text and cipher-text will also be quantum images. Assume that plaintext quantum image is
i = y x = 0, 1, … , 22n − 1. The proposed image encryption algorithm consists of the following steps:
-
Step 1.
|M〉 is divided into a series of characteristic sub-images |M 0〉, |M 1〉, ⋯ |M N − 1〉 by utilizing quantum image correlation decomposition.
-
Step 2.
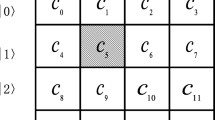
The array of a complete binary tree is constructed by an integer sequence 0, 1, ⋯ , N − 1, as shown in Fig. 3. After the array of the complete binary tree is performed preorder traversal, the sub-images are stored into the array of the complete binary tree. |M i 〉 corresponds to the ith node of the complete binary tree.
-
Step 3.
To encode color information of quantum image, quantum random phase gate, quantum revolving gate and Hadamard transform are randomly performed on these sub-images. For the ith node of the complete binary tree, if i mod 3 = 0, perform random phase gate U k on |M i 〉. Random phase gate is used to construct a 2n + 1 qubits-based unitary transform C k .
$$\begin{array}{@{}rcl@{}} C_{k} =\left( {I\otimes \sum\limits_{y=0}^{2^{n}-1} {\sum\limits_{\begin{array}{l} x=0 \\ yx\ne k \\ \end{array}}^{2^{n}-1} {\left|yx \right\rangle \left\langle {yx} \right|} } } \right)+U_{k} \otimes \left|k \right\rangle \left\langle k \right| \end{array} $$(10)$$\begin{array}{@{}rcl@{}} U_{k} =\left[ {{\begin{array}{*{20}c} 1 & 0 \\ 0 & {e^{\mathrm{j}2{\pi }\varphi_{k} }} \\ \end{array} }} \right] \end{array} $$(11)where φ k is a real number and distributed uniformly between 0 and 1. The controlled phase matrix C k is a unitary matrix since \(C_{k} C_{k}^{\dag } \mbox {=}I^{\otimes 2n+1}\). Applying a 2n + 1 qubits unitary transform C on quantum image |M i 〉, one obtains:
$$\begin{array}{@{}rcl@{}} {\begin{array}{l} C\left( \left|M_{i} \right\rangle \right) =\prod\limits_{y=0}^{2^n-1} \prod\limits_{x=0}^{2^n-1} C_{yx} \left|\right.M_{i}\rangle \\ =\frac{1}{2^{n}}\sum\limits^{2^{n-1}}_{y=0}\sum\limits^{2^{n-1}}_{x=0}\left(\text{cos} \theta_{yx}\left|0\right\rangle +e^{\text{j}2\pi\phi_{k}} sin \theta_{yx}\left|\right.1\rangle\right)\left|\right.yx\rangle\\ =\left|\right.f_{i}\rangle \end{array}} \end{array} $$(12)
If i mod 3 = 1, perform quantum revolving gate on |M i 〉. Quantum revolving gate R(ϕ j ) is used to construct a unitary transform R j .
where ϕ j indicates the rotation angle, and ϕ j is uniformly distributed from 0 to 2π. The controlled rotation matrix R j is a unitary matrix since \(R_{j} R_{j}^{\dag } =I^{\otimes 2n+1}\). Applying a 2n + 1 qubits unitary transform R on quantum image |M i 〉, one obtains:
If i mod 3=2, perform Hadamard transform operation on |M i 〉. Unitary transform T is controlled by a binary key K 1, where K 1 = k 1 k 2⋯k 2n + 1, k 1 = 1, k i ∈ {0, 1}, i = 2,3,⋯,2n + 1.
where \(T=H\mathop \otimes \limits _{i=2}^{2n+1} H^{k_{i} },H^{k_{i} }= \left \{\begin {array}{cc} H, & k_{i} = 1\\ I, & k_{i} = 0\\ \end {array}\right .,i=2,3,{\cdots } ,2n+1\), H is a Hadamard matrix and I is a 2-D identity matrix. The new images |f 0〉, |f 1〉, ⋯ ,|f N − 1〉 are obtained by implementing different transform operations in each node according to the residue of i divided by 3.
-
Step 4.
To achieve the final quantum cipher-text image |f〉, one encrypts all of quantum images |f i 〉 into the superposition.
$$ \left|f \right\rangle =\eta_{0} \left|f_{0} \right\rangle +\eta_{1}\left|f_{1}\right\rangle+\cdots+\eta_{N-1}\left|f_{N-1}\right\rangle\\ $$(17)where η = (η 0,η 1,⋯,η N − 1) and \({\eta _{0}^{2}} +{\eta _{1}^{2}} +{\cdots } +\eta _{N-1}^{2} =1\).
-
Step 5.
To obtain the orthonormal basis states |Q i 〉, one applies Schmidt decomposition to cipher-text image |f〉.
$$ \left|f \right\rangle =\sum\limits^{N-1}_{i=0} \beta_{i} \left|Q_{i} \right\rangle $$(18)where β i is a non-negative real number satisfying \(\sum \limits _{i=0}^{N-1} {{\beta _{i}^{2}} } =1\).
The quantum image encryption procedure is shown in Fig. 4. The encryption algorithm is composed of quantum image correlation decomposition, three transforms and superposition operation.
3.2 Decryption Algorithm
In the encryption algorithm, random phase gate U k , quantum revolving gate R(ϕ j ) and binary sequence K 1 are used to control quantum random-phase operation, quantum revolving operation and Hadamard transform, respectively. The keys involve the parameter φ k of random phase gate, rotation angle ϕ j , binary sequence K 1 = k 1 k 2⋯k 2n + 1, and orthonormal basis states K 2 = {|Q i 〉,i = 0,1⋯ , N − 1}. The decryption process is as follows.
-
Step 1.
The cipher-text image |f〉 is obtained by making measurements on the received quantum images |f i 〉. Applying K 2 = {|Q i 〉, i = 0, 1, ⋯ , N − 1} as the project operators to perform the projective measurements, i.e.,
$$ P=\sum\limits^{N-1}_{i=0}P_{i}\left|Q_{i}\right\rangle\langle Q_\textit{i}\left|\right. $$(19)$$ p_{i} =\frac{t_{i} }{t-t_{i} } $$(20)where t represents the total number of the measurements, t i is the number of the measurements coincided with the results of |f i 〉.
-
Step 2.
According to the array of the complete binary tree, different inverse transforms are executed to get the sub-images |M 0〉, |M 1〉,⋯ ,|M N − 1〉. For the node i of the complete binary tree, if i mod 3 = 0, the decryption operation is performed on |f i 〉 with the key φ k .
$$ {\begin{array}{l} C^{-1}\left( \left|f_{i}\right\rangle \right)=\prod\limits_{y=0}^{2^{n}-1} \prod\limits_{x=0}^{2^{n}-1} C_{yx}^\dag \left( \left|f_{i} \right\rangle \right) \\=\prod\limits_{y=0}^{2^{n}-1} \prod\limits_{x=0}^{2^{n}-1} C_{yx}^\dag \left(\frac{1}{2^{n}}\sum\limits^{2^{n}-1}_{y=0}\sum\limits^{2^{n}-1}_{x=0}(\cos\theta_{yx}\left|0\right\rangle+e^{\mathrm{j}2\pi\varphi_{yx}}\sin\theta_{yx}\left|1\right\rangle)\left|yx\right\rangle \right)\\=\left|M_{i}\right\rangle \end{array}} $$(21)where \(C_{yx}^{\dag } \) is the Hermitian conjugate of C y x . If i mod 3=1, perform the decryption operation on |f i 〉 with the key ϕ j .
$$ {\begin{array}{l} R^{-1}\left( \left|f_{i} \right\rangle \right)=\prod\limits_{y=0}^{2^{n}-1} \prod\limits_{x=0}^{2^{n}-1} R^{\dag}_{yx}(\left|f_{i}\right\rangle)\\ =\prod\limits_{y=0}^{2^{n}-1} \prod\limits_{x=0}^{2^{n}-1} R^{\dag}_{yx}\frac{1}{2^{n}}\sum\limits^{2^{n}-1}_{y=0}\sum\limits^{2^{n}-1}_{x=0}R(\phi_{yx})\left|g(x,y)\right\rangle\left|yx\right\rangle\\ =\frac{1}{2^{n}}\sum\limits^{2^{n}-1}_{y=0}\sum\limits^{2^{n}-1}_{x=0}\left|g(y,x)\right\rangle\left|yx\right\rangle\\ =\left|M_{i}\right\rangle \end{array}} $$(22)
If i mod 3 = 2, execute the decryption operation on |f i 〉 with the key K 1, where T −1 is the inverse operator of T.
-
Step 3.
According to the nature of quantum image correlation decomposition, the color information of the original image is rebuilt by these sub-images.
4 Algorithm Analyses
Since a practical and useful quantum computer is unavailable, there is lack of quantum hardware to simulate the quantum image encryption algorithm. Thus the proposed algorithm is limited to the theoretical analyses on key space, security and computational complexity.
4.1 Key Space
The key space of a good image encryption algorithm should be large enough to make brute-force attack infeasible. It is recommended in Ref.[32] that the ideal key space should be larger than 2100 while considering the current computation speed of a general computer. In the proposed algorithm, random phase gate U k , quantum revolving gate R(ϕ j ) and binary sequence K 1 are used to control quantum random-phase operation, quantum revolving operation and Hadamard transform, respectively. The keys are composed of the parameter φ k of random phase gate, rotation angle ϕ j , binary sequence K 1, and orthonormal basis states K 2. Here, φ k is a real number and distributed uniformly between 0 and 1, ϕ j is uniformly distributed from 0 to 2π, k i ∈ {0, 1}, i = 2, 3, ⋯ , 2n + 1. φ k , ϕ j imply a very large key space, and the key space of K 1 is 22n. The total key space is a very huge number, thus the proposed algorithm can resist brute-force attack.
4.2 Security
The encrypted image is stored and transmitted in the form of quantum states. Since the quantum no-cloning theorem and quantum uncertainty principle, the process of exactly replicating any unknown quantum state can not be realized in quantum mechanics. If the attacker wants to obtain the information about the quantum state, he has to measure it, which will make the quantum state collapse randomly into an eigenstate of the measurement operators irreversibly. Therefore, the legitimate users can detect whether the quantum information has suffered from attacks or not. So the proposed quantum encryption algorithm has provable security and will immune from the interception with unlimited computing power of eavesdroppers due to the principles of quantum mechanics. Zhou RG et al.’s scheme realized quantum image encryption by utilizing quantum image geometric transformations. Unfortunately, it involves repeated quantum image storage and the adversary can get plaintext image as long as he decrypts a quantum image from the full-binary-tree array. However, the proposed encryption algorithm successfully solved these drawbacks. In the proposed algorithm, the whole quantum image is divided into a series of sub-images, and these sub-images are encrypted by utilizing quantum random-phase gate, quantum revolving gate and Hadamard transform. The receiver has to decrypt all quantum images from the array of the complete binary tree to obtain the sub-images, and then recover the plaintext image under quantum information theory. The proposed quantum image encryption algorithm increased the decryption difficulty. Moreover, the quantum state measurements are the most essential decryption operations. Therefore, the proposed algorithm can greatly improve the security of image encryption and decryption.
4.3 Computational Complexity
Assume that M is a 2n × 2n original image. There are 22n pixels in the original image. For quantum image encryption algorithm, due to the properties of quantum parallel computation, the use of quantum transforms speeds up the image encryption and decryption. The computational complexity of the proposed encryption algorithm depends on quantum random-phase operation, quantum revolving operation and Hadamard transform. The complexity of quantum random-phase operation for a quantum image is O(n). Since the computational complexity is the same as quantum random-phase operation, revolving operation and Hadamard transform, and the encryption algorithm needs to perform encryption operation on N sub-images at the same time. So the total computational complexity is O(N n). By analyzing the corresponding classical image encryption algorithm, random-phase operation is performed on the image by using 22n multiplication operations, so the computational complexity is O(22n). The computational complexity is the same as random-phase operation, revolving operation and Hadamard transform. Thus, the total computational complexity is O(N22n). Therefore, the computational complexity of the proposed encryption algorithm is lower than its classical counterparts.
5 Conclusion
We utilized the superposition and measurement principle of quantum states to establish the correlation among image pixels and proposed a novel quantum image encryption and decryption algorithm based on image correlation decomposition. The encryption algorithm is realized by combining quantum image correlation decomposition, three transforms with superposition operation. Quantum random-phase operation, quantum revolving operation and Hadamard transform are used to encode color information of these sub-images, which increases the decryption difficulty. The encrypted image can be obtained by superimposing the resulting sub-images. A detailed theoretical security and computational complexity analysis of the encryption algorithm is given. The proposed encryption algorithm can resist brute-force attack due to its very large key space. Moreover, the proposed algorithm has lower computational complexity than its classical counterparts. It implements quantum image encryption by combining quantum information theory with classical image encryption technology, which introduces a new theoretical tool for image encryption.
References
Javidi, B., Zhang, G., Li, J.: Opt. Eng. 35, 2506 (1996)
Peng, X., Zhang, P., Wei, H., Yu, B.: Opt. Lett. 31, 1044 (2006)
Tao, R., Xin, Y., Wang, Y.: Opt. Express 15, 16067 (2007)
Maity, S.P., Kundu, M.K.: Inform. Sci. 181, 450 (2011)
Aung, A., Ng, B.P., Rahardja, S.: J. Signal Process. Sys. 64, 319 (2011)
Zhou, N.R., Wang, Y.X., Gong, L.H.: Opt. Commun. 284, 3234 (2011)
Solak, E., Rhouma, R., Belghith, S.: Opt. Commun. 283, 232 (2010)
Rhouma, R., Solak, E., Belghith, S.: Commun. Nonlinear Sci. Numer. Simulat. 15, 1887 (2010)
Zhang, Y., Xiao, D.: Nonlinear Dynam. 72, 751 (2013)
Li, C., Liu, Y., Zhang, L.Y., Chen, M.Z.: Int. J. Bifurcat. Chaos 23, 1350075 (2013)
Nielsen, M.A., Chuang, I.L.: Cambridge University Press (2010)
Venegas-Andraca, S.E., Bose, S.: Conference on Quantum Information and Computation, Orlando. Fl. 5105, 137 (2003)
Venegas-Andraca, S.E., Ball, J.L.: Quantum Inf. Process. 9, 1 (2010)
Latorre, J.I.: Quantum Phys. 0510031 (2005)
Le, P.Q., Dong, F.Y., Hirota, K.: Quantum Inf. Process. 10, 63 (2011)
Le, P.Q., Iliyasu, A.M., Dong, F.Y., Hirota, K.I.: JACIII 15, 698 (2011)
Sun, B., Le, P.Q., Iliyasu, A.M., Yan, F., Garcia, J.A., Dong, F., Hirota, K.: Intelligent Signal Processing (WISP), 2011 IEEE 7th International Symposium on. Floriana 1 (2011)
Le, P.Q., Iliyasu, A.M., Dong, F.Y., Hirota, K.: IAENG Int. J. Apl. Math. 40, 113 (2010)
Le, P.Q., Iliyasu, A.M., Dong, F.Y., Hirota, K.: Theor. Comput. Sci. 412, 1406 (2011)
Iliyasu, A.M., Le, P.Q., Dong, F.Y., Hirota, K.: Inform. Sci. 186, 126 (2012)
Le, P.Q., Iliyasu, A.M., Garcia, J.A., Dong, F., Hirota, K.: JACIII 16, 631 (2012)
Goldin, M.A., Francisco, D., Ledesma, S.: Opt. Commun. 284, 2089 (2011)
Zhang, Y., Lu, K., Gao, Y.H., Wang, M.: Quantum Inf. Process. 12, 2833 (2013)
Zhang, Y., Lu, K., Gao, Y.H., Xu, K.: Quantum Inf. Process. 12, 3101 (2013)
Li, H.S., Zhu, Q.X., Song, L., Shen, C.Y., Zhou, R.G., Mo, J.: Quantum Inf. Process. 12, 2269 (2013)
Akhshani, A., Akhavan, A., Lim, S.C., Hassan, Z.: Commun. Nonlinear Sci. Numer. Simulat. 17, 4653 (2012)
Zhou, R.G., Wu, Q., Zhang, M.Q., Shen, C.Y.: Int. J. Theor. Phys. 52, 1802 (2013)
Zhang, W.W., Gao, F., Liu, B., Wen, Q.Y., Chen, H.: Quantum Inf. Process. 12, 793 (2013)
Abd El-Latif, A.A., Li, L., Wang, N., Han, Q., Niu, X.M.: Sig. Process. 93, 2986 (2013)
Yang, Y.G., Xia, J., Jia, X., Zhang, H.: Quantum Inf. Process. 12, 3477 (2013)
Song, X.H., Wang, S., Abd El-Latif, A.A., Niu, X.M.: Multimedia Syst. 20, 379 (2014)
Alvarez, G., Li, S.J.: Int. J. Bifurcat. Chaos 16, 2129 (2006)
Acknowledgments
This work is supported by the National Natural Science Foundation of China (grant no. 61262084), the Natural Science Foundation of Jiangxi Province, China (grant no. 20122BAB201031), the Foundation for Young Scientists of Jiangxi Province (Jinggang Star) (grant no. 20122BCB23002), the Research Foundation of the Education Department of Jiangxi Province (grant nos. GJJ14138 and GJJ13057), the Open Project of Key Laboratory of Photoeletronics & Telecommunication of Jiangxi Province (grant no. 2013003), and the Innovation Project of Jiangxi Graduate Education (grant no. YC2012-S009).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hua, T., Chen, J., Pei, D. et al. Quantum Image Encryption Algorithm Based on Image Correlation Decomposition. Int J Theor Phys 54, 526–537 (2015). https://doi.org/10.1007/s10773-014-2245-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-014-2245-z