Abstract
In this paper, a theoretical scheme for tripartite quantum controlled teleportation is presented using the entanglement property of seven-qubit cluster state. This means that Alice wants to transmit a entangled state of particle a to Bob, Charlie wants to transmit a entangled state of particle b to David and Edison wants to transmit a entangled state of particle c to Ford via the control of the supervisor. In the end, we compared the aspects of quantum resource consumption, operation complexity, classical resource consumption, quantum information bits transmitted, success probability and efficiency with other schemes.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Entanglement is considered as the central resource for quantum information and computation, the multi-mode entanglement works have been studied experimentally and theoretically [1–4]. Since the first creation of quantum teleportation (QT) protocol by Bennett [5], research on quantum teleportation has been attracting much attention both in theoretical and experimental aspects, such as quantum teleportation (QT) [5–11], quantum secure direct communication (QSDC) [12–18], quantum secret sharing (QSS) [19–22], quantum key distribution (QKD) [23–25], and so on. In 2000, Lo [26] presented an RSP protocol to fulfill the same goal. However, there are several differences between QT and RSP. In RSP, the sender must know the prepared state completely. Since then, many researchers have studied RSP from different aspects, including low-entanglement RSP [27], optimal RSP [28], generalized RSP [29], continuous variable RSP [30], etc. Recently, some researchers have paid close attention to controlled remote state preparation (CRSP) [31–33]. Unlike common RSP protocol, CRSP can be completed if and only if the supervisor participates during the implementation of the protocol. Latter, another effective method of information processing, so-called joint remote state preparation (JRSP), has been explored [34–49]. In JRSP, all senders share the information of the prepared state, the senders perform proper measurements on their particles according to their knowledge of the prepared state. The original state can be prepared by performing corresponding unitary operation on the receivers particle according to all the senders measurement results and the entangled state shared in advance. This feature is highly needed in confidential communication between agencies.
In 2005, Deng et al. introduced a symmetric multiparty controlled teleportation scheme for an arbitrary two particle entangled state [50]. In particular, in 2013, Zha et al. presented the first bidirectional quantum controlled teleportation (BQCT) protocol by employing five-qubit cluster state as the quantum channel [51]. Recently Cao Thi Bich. put forward a seven-qubit cluster state [52]. According to this inspiration, we present the tripartute quantum controlled teleporattion.
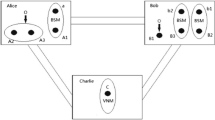
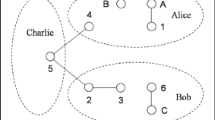
In this paper, in order to present a scheme of tripartute quantum controlled teleportation, we utilize the seven-qubit entangled state in which a seven-qubit cluster state quantum channel initially shared by the three sender Alice, Charlie, and Edison and three receiver Bob, David, Ford and supervisor Tom. Suppose Alice has particle a in an unknown state, she wants to transmit the state of particle a to Bob; while, Charlie has particle b in an unknown state, he wants to transmit the state of particle b to David. As same as two senders, Edison has particle c in an unknown state, he wants to transmit the state of particle c to Ford under the control of Tom. We display that if the senders make a Bell state measurement and receiver operate a felicitous unitary transformation on the receivers side with the cooperation of the supervisor Tom, the original state of each qubit will be restored by the receiver. At the same time, we will reveal the advantages of tripartute quantum controlled teleportation from the quantum resource consumption, operation complexity, classical resource consumption, success probability and efficiency.
2 Tripartite Quantum Controlled Teleportation via Seven-Qubit Cluster State
Let us assume that the quantum channel during the three senders (Alice, Charlie, and Edison), the three receivers (Bob, David, and Ford ), and the supervisor Tom, is a one-dimensional seven-qubit cluster state, which has the form [52]:
Suppose that particle a which Alice has, is in an uncharted state:
Charlie has particle b in an unknown state:
And that Edison has particle c in an unknown state:
Alice wants to transmit the state of particle a to Bob, Charlie wants to transmit the state of particle b to David and Edison wants to transmit the state of particle c to Ford.
The system state of the ten particles can be expressed as:
For the sake of realizing quantum state swapping, Alice has to perform Bell state measurement on her qubit pairs (A,a), and
Without loss of generality, if Alice’s measurement results is |φ 1〉, then the other particles are collapsed into the state
Subsequently, Charlie has to perform Bell state measurement on his qubit pairs (b,C), and
if Charlie’s measurement results is |φ 1〉 b C , then the other particles c,T,B,D,E and F is collapsed into the state
Third, Edison has to performs Bell state measurement on his qubit pairs (c,E) and
if Edison’s measurement results is |φ 1〉 c E , then the other particles TBDF is collapsed into the state
Finally, Tom have to perform Von Neumann measurement on his qubit T, with measurement base
For example, if David’s measurements result is |+〉 T , the corresponding collapsed state of
The tripartite quantum controlled teleportation is successfully realized. Analogously, for other cases, According to measurement result by Alice,Charlie, Edison and Tom, Bob, David, Ford can operate an appropriate unitary transformation; the tripartite quantum controlled teleportation is realized easily.
3 Discussions and Comparisons
As a communication protocol, we should briefly discuss our scheme from security. Before the implementation of our protocol, the Cluster state should be securely shared among Alice, Charlie, Edison, Bob, David, Ford, and supervisor Tom. Without loss of generality, suppose that Alice prepares the Cluster state |ψ〉 T A B C D E F and sends particle(s) T(B C D E F) to Tom (Bob, Charlie, David, Edison, Ford). When sending the particles, the Alice inserts respectively a certain number of decoy-state particles which are randomly in one of four states |0〉,|1〉,|+〉,|−〉. After be confirmed that both Tom, Charlie, Edison, Bob, David and Ford have received the particles respectively, Alice announces the positions and measurement basis of the decoy particles. Then Tom, Charlie, Edison, Bob, David and Ford measure these particles under the given basis and announce the results. Next, Alice compares the measurement results with the initial states of the decoy particles. Because every eavesdroppers has a trace in the outcomes of the decoy sampling photons [53]. Several kinds of attacks from the outside attacker Eve, such as intercept-resend arrack, measurement-resend attack, entanglement-measure attack and denial-of-service (DOS) attack will be detected with nonzero probability during the security checking process. Obviously, this checking method is derived from the idea of the BB84 QKD protocol, which has been proven to be unconditionally secure by several groups [54].
let us make a comparisons between our scheme and other schemes [31, 46]. Comparisons are carried out from the five aspects: the quantum resource consumption. the necessary-operation complexity which include the operation difficulty and intensity, the classical resource consumption, transmitted quantum information bits, success probability and the intrinsic efficiency. And we will be summarized in Table 1.
From the Table 1, one can see that, the quantum and classical resource consumption in our scheme are most. The operation complexities are almost same in the three schemes. Except for this, our scheme is overall better than the L and B schemes. In particular, comparison with the B and L schemes, our scheme transmit more quantum information bits and possess higher intrinsic efficiency. In a word, our scheme is more optimal and economic.
4 Conclusion
In summary, we have proposed a scheme for tripartite quantum controlled teleportation by seven cluster state. Namely, Alice, Charlie, and Edison can transmit their own particle a, b,c in an unknown state in cyclic via the control of the supervisor Tom. The three unknown states can be exchanged as long as sender make a Bell state measurement and receiver operate an appropriate unitary transformation on the receiver’s side with the cooperation of the supervisor Tom. However, if one agent does not cooperate, the receiver can not fully recover the original state of each qubit. Finally, we have compared the scheme with other schemes on quantum and classical resource consumption, operation complexities, quantum information bits transmitted, success probabilities and efficiencies. By the comparison, we think our scheme has more superior than others.
References
Zheng, H.B., Zhang, X., Zhang, Z.Y., Tian, Y.L., Chen, H., Li, C.B., Zhang, Y.P.: Sci. Rep. 3, 1885 (2013)
Chen, H.X., Zhang, X., Zhu, D.Y., Yang, C., Jiang, T., Zheng, H.B., Zhang, Y.P.: Phys. Rev. A 90, 043846 (2014)
Chen, H.X., Zhang, Y.Q., Yao, X., Wu, Z.K., Zhang, X., Zhang, Y.P., Xiao, M.: Sci. Rep. 4, 3619 (2014)
Zhang, Z.Y., Wen, F., Che, J.L., Zhang, D., Li, C.B., Zhang, Y.P., Xiao, M.: Sci. Rep. 5, 15058 (2015)
Bennett, C.H., Brassard, G., Crpeau C., et al.: Phys. Rev. Lett. 70, 1895–1899 (1993)
Deng, F.G., Li, X.H., Li, C.Y.: Eur. Phys. J. D 39, 459–464 (2006)
Cardoso, W., Avelar, A., Baseia, B., Almeida, N.G.: Phys. Rev. A. 72, 045802 (2005)
Bouwmeester, D., Pan, J.W., Mattle, K.: Nature 390, 575–579 (1997)
Barrett, M.D., Chiaverini, J., Schaetz, T., et al.: Nature 429, 737–739 (2004)
Yeo, Y., Chua, W.K.: Phys. Rev. Lett. 96, 1060502 (2006)
Zhang, D., Zha, X.W., Duan, Y.J.: Int. J. Theor. Phys. 54, 1711–1719 (2015)
Deng, F.G., Long, G.L.: Phys. Rev. A 69, 052319 (2004)
Long, G.L., Deng, F.G., Wang, C.: Front. Phys. China 2, 251–272 (2007)
Xiu, X.M., Li, D., Gao, Y.J., Chi, F.: Commun. Theor. Phys. 52, 60–62 (2009)
Yan, C., Xu, C.X., Zhang, S.B.: Chin. Sci. Bull. 59, 2541–2546 (2014)
Zhang, Q.N., Li, C.C., Li, Y.H.: Int. J. Theor. Phys. 52, 22–27 (2013)
Jin, X.R., Ji, X., Zhang, Y.Q., et al.: Phys. Lett. A. 354, 67–70 (2006)
Xu, J.S., Li, C.F.: Science Bulletin 60, 141–142 (2015)
Zhang, Z.J., Man, Z.X.: Phys. Rev. A 72, 022303 (2005)
Markham, D., Sanders, B.C.: Phys. Rev. A 78, 042309 (2008)
Karimipour, V., Bahraminasab, A., Bagherinezhad, S.: Phys. Rev. A 65, 042320 (2002)
Zhang, Z.J., Li, Y., Man, Z.X.: Phys. Rev. A 71, 044301 (2005)
Li, H.W., Yin, Z.Q., Wang, S.: Chin. Phys. 20, 100306 (2011)
Zhu, J., He, G.Q., Zeng, G.H.: Chin. Phys. B 16, 1364–1369 (2007)
Yang, Y.G., Wen, Q.Y., Zhu, F.C.: Chin. Phys. B 16, 910–914 (2007)
Lo, H.K.: Phys. Rev. A 62, 012313 (2000)
Devetak, I., Berger, T.: Phys. Rev. Lett. 87, 197901 (2001)
Berry, D.W., Sanders, B.C.: Phys. Rev. Lett. 90, 057901 (2003)
Abeyesinghe, A., Hayden, P.: Phys. Rev. A 68, 062319 (2003)
Kurucz, Z., Adam, P., Kis, Z., Janszky, J.: Phys. Rev. A 72, 052315 (2005)
Liu, L.L., Tzonelih, H.: Quantum Inf. Process 13, 1639–1650 (2014)
Wang, C., Zeng, Z., Li, X.H.: Quantum Inf. Process 14, 1077–1089 (2015)
Wang, D., Ye, L.: Quantum Inf. Process 12, 3223–3237 (2013)
Xia, Y., Song, J., Song, H.S.: J. Phys. B At Mol. Opt. Phys. 40, 3719–3724 (2007)
Zha, X.W., Song, H.Y.: Opt.Commun 284, 1472–1474 (2011)
Hou, K., Li, Y.B., Liu, G.H., Sheng, S.Q.: J. Phys. A: Math. Theor 44, 255304 (2011)
Xiao, X.Q., Liu, J.M., Zeng, G.H.: J. Phys. B At. Mol. Opt. Phys 44, 075501 (2011)
Chen, Q.Q., Xia, Y., An, N.B.: Opt. Commun 284, 2617–2621 (2011)
Yang, K.Y., Xia, Y.: Int. J. Theor. Phys 51, 1647–1654 (2012)
Luo, M.X., Chen, X.B., Ma, S.Y.: Opt. Commun 283, 4796–4801 (2010)
Wang, D., Ye, L.: Int. J. Theor. Phys 51, 3376–3386 (2012)
Zhan, Y.B., Hu, B.L., Ma, P.C.: J. Phys. B. At. Mol. Opt. Phys 44, 095501 (2011)
Yeo, Y., Chua, W.K.: Phys. Rev. Lett. 96, 1060502 (2006)
Zhou, P., Li, H.W., Long, L.R.: Int. J. Theor. Phys 52, 849–861 (2013)
Ai, L.T., Li, N., Zhou, P.: Int. J. Theor. Phys 53, 159–168 (2014)
Binary, S., Choudhury, A.D.: Quantum Inf. Process 14, 373–379 (2015)
Zhou, N.R., Cheng, H.L., Tao, X.Y.: Quantum Inf. Process 13, 513–526 (2014)
Liao, Y.M., Zhou, P., Qin, X.C.: Quantum Inf. Process 13, 615–627 (2014)
Long, L.R., Zhou, P., Li, Z., Yin, C.L.: Int. J. Theor. Phys. 51, 2438–2446 (2012)
Deng, F.G., Li, C.Y., Li, Y.S., et al.: Phys. Rev. A 72, 022338 (2005)
Zha, X.W., Zou, Z.C., Qi, J.X., Song, H.Y.: Int. J. Theor. Phys 52, 1740–1744 (2013)
Bich, C.T.: Int. J. Theor. Phys 54, 139–152 (2015)
Wang, T.Y., Wen, Q.Y., Chen, X.B.: Opt. Commun 281, 6130–6134 (2008)
Shor, P.W., Preskill, J.: Phys. Rev. Lett. 85, 441–444 (2000)
Yuan, H., et al.: J. Phys. B 41, 145506 (2008)
Acknowledgments
This work was supported by the foundation of Shannxi provincial Educational Department under Contract No. 15JK1668 and the Natural Science Foundation of Shannxi provincial of China Grant No. 2015JM6263 and No. 2013JM1009.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Li, W., Zha, XW. & Qi, JX. Tripartite Quantum Controlled Teleportation via Seven-Qubit Cluster State. Int J Theor Phys 55, 3927–3933 (2016). https://doi.org/10.1007/s10773-016-3022-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-016-3022-y