Abstract
The finite step length (FSL) method is extensively used for structural reliability analysis due to its robustness and efficiency compared with traditional Hasofer–Lind and Rackwitz–Fiessler (HL-RF) method. However, it may generate a large computational effort when it faces some complex nonlinear limit state functions. This study explains the basic reason of inefficiency of the FSL method and proposes an enhanced finite step length (EFSL) method to improve the ability for solving complex nonlinear problems, and then apply it to reliability-based design optimization (RBDO). The tactic is to present an iterative control criterion to compensate for the deficiency of the FSL method in the oscillation amplitude criterion, which solves the problem of large computational effort caused by unchanged step length during the iterative process. Then, a comprehensive step length adjustment formula is presented, which can adaptively adjust the step length to achieve fast convergence for limit state functions with different degrees of nonlinearity. Following that, the proposed method is combined with the double loop method (DLM) to improve the efficiency and robustness for solving complex RBDO problems. The robustness and efficiency of the proposed method compared to other commonly used first-order reliability analysis methods are demonstrated by five numerical examples. In addition, four design problems are used to validate the proposed EFSL-based DLM which is effective for solving complex nonlinear RBDO problems.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Uncertainties widely present in the material parameters, geometries, external loads, and other aspects, which have important implications for structural reliability (Jiang et al. 2020; Schueller and Pradlwarter 2007). To assess the impact of uncertainties on engineering structures, structural reliability analysis methods have been constantly evolving over the past decades. Generally, these methods can be classified into five categories: sampling methods (Hu and Du 2013), expansion methods (Keshavarzzadeh et al. 2016), surrogate-based methods (Yang et al. 2021), integration methods (Xu and Dang 2019), most probable point (MPP)-based methods including the first-order reliability method (FORM) (Hasofer and Lind 1974; Rackwitz and Flessler 1978) and the second-order reliability method (SORM) (Wang et al. 2020). Among them, FORM is one of the most important methods for assessing the structural reliability, which was recommended to use by the Joint Committee of Structural Safety.
When performing reliability analysis by FORM, the calculation of reliability index becomes a problem of finding the optimum solution in a constrained optimization problem. So far, the approaches for solving the constrained optimization problems are categorized as optimization scheme and iterative algorithm. The optimization scheme generally solves the problem well, but the solution process may require to use Hessian matrix or inverse matrix, which leads to a complex solution process (Gong and Yi 2011). Unlike optimization scheme, iterative algorithm has the advantage of being simple and efficient. Typically, the HL-RF method is one of the most used iterative algorithm, which was presented by Hasofer and Lind (1974) and complemented by Rackwitz and Fiessler (1978). Due to the simplicity and efficiency of the HL-RF method, it is extensively used for structural reliability analysis. For weakly nonlinear limit state functions, the HL-RF method can quickly obtain a convergent result. But, for highly nonlinear limit state functions, the HL-RF method may converge slowly or even show a phenomenon of non-convergence, such as bifurcation, chaos, and periodic oscillation (Yang 2010; Zhang et al. 2021a).
To improve the numerical stability of the HL-RF method, several methods have been developed. Through introducing merit function, iHL-RF (Liu and Kiureghian 1991) increases the robustness of the HL-RF method by using Armijo rule to select an appropriate step length. According to the chaos control principle (Keshtegar 2016), the stability transformation method (STM) (Yang 2010), the adaptive stability transformation method (ASTM) (Meng et al. 2018), and the directional stability transformation method (DSTM) (Meng et al. 2017) were developed to enhance their capability in solving nonlinear limit state functions. Yang et al. (2020) reduced the risk of periodic oscillations, bifurcations, and chaos by modifying the search direction during the iterative process and establishing a new step length adjustment formula. Gong and Yi (2011) derived a new finite step length (FSL) method using adjustment formula to accelerate the convergence process and improve the robustness of algorithm. Roudak et al. (2017) proposed to introduce two adjusting parameters in the HL-RF method to adaptively adjust step length during the iterative process, preserving the simplicity property while improving its convergence performance. Keshtegar and Meng (2017) presented a hybrid relaxed HL-RF method considering the impact of relaxed factor to accelerate the convergence process.
It is worth noting that FORM not only can be used to assess structural reliability, but can also be applied into RBDO that seeks a compromise between safety and cost (Yang et al. 2022). Usually, RBDO is categorized into three types: double loop method (DLM) (Chiralaksanakul and Mahadevan 2005; Youn and Choi 2004; Zhu et al. 2021), decoupled method (Chen et al. 2013b; Du and Chen 2004; Yu and Wang 2019), and single loop method (Biswas and Sharma 2021; Lind and Olsson 2019). Among them, DLM theoretically has better robustness, which consists of an internal reliability constraint loop and an external optimization loop. DLM includes reliability index approach-based DLM (RIA-based DLM) and performance measure approach-based DLM (PMA-based DLM) (Aoues and Chateauneuf 2010). For RIA-based DLM, the FSL method is applied in reliability constraint loop due to its simplicity and efficiency. However, DLM combined with FSL may suffer from the problem of poor convergence performance when facing complex nonlinear limit state functions.
In this study, an EFSL method is proposed to enhance the efficiency and robustness for complex limit state functions. The major contributions of the proposed method are summarized as follows. Firstly, employing a state parameter to make up for the deficiencies of the FSL method in the oscillation amplitude criterion and solving the problem of large computational effort due to the unchanged step length. Secondly, developing a comprehensive step length adjustment formula to accelerate the iterative convergence process by adaptively adjusting the step length for limit state functions with different degrees of nonlinearity. Finally, the proposed EFSL method is combined with DLM to improve the efficiency and robustness for solving complex nonlinear RBDO problems.
The rest of this paper is organized as follows. In Sect. 2, four traditional FORM iterative methods are simply introduced. In Sect. 3, the EFSL method is developed and a comprehensive step length adjustment formula is proposed. In Sect. 4, five examples are used to verify the efficiency and robustness of the proposed EFSL method. In Sect. 5, four RBDO design problems are solved using the proposed EFSL method combined with DLM. In Sect. 6, conclusions are given.
2 Review of FORM iterative algorithm
The purpose of FORM is to acquire reliability index and calculate structural failure probability (Koduru and Haukaas 2010). The reliability index can be calculated through obtaining the most probable point (MPP), which is the closest distance from origin to limit state surface in the standard normal space (U-space). According to the reliability index, the failure probability is defined as
where \(P_{f}\) denotes the failure probability; \(\Phi\) stands for the cumulative distribution function (CDF); \(\beta\) represents the reliability index; and \({\mathbf{U}}^{\ast }\) is a vector of MPP coordinates in the U-space.
The solution of the reliability index \(\beta\) can be transformed into a constrained optimization problem, which can be expressed as
In the following, four traditional FORM iterative algorithms are briefly reviewed. For convenience of description, the limit state function can be expressed as
where \({\mathbf{X}}\) denotes a vector comprised by random variables.
When \({\mathbf{X}}\) obeys independently normal distribution, it should satisfy \({\mathbf{X}} = {{\varvec{\upmu}}} + {\mathbf{\sigma U}}\). The vectors \({{\varvec{\upmu}}}\) and \({{\varvec{\upsigma}}}\) are the mean and standard deviation of random variable \({\mathbf{X}}\). When the correlated random variables are involved, the random variables should be transformed into independent standard normal variables by Rosenblatt or Nataf transformation (Liu and Kiureghian 1986; Rackwitz and Flessler 1978).
2.1 HL-RF iterative algorithm
The formulation of the HL-RF (Hasofer and Lind 1974; Rackwitz and Flessler 1978) method can be expressed as
where k refers to the iterative number; \({\mathbf{U}}^{k}\) and \({\mathbf{U}}^{{k{ + }1}}\) are the random variable vectors at the kth and (k + 1)th iterative steps in the U-space, respectively; \(g\left( {{\mathbf{U}}^{k} } \right)\) represents the value of limit state function at \({\mathbf{U}}^{k}\). \(\nabla g\left( {{\mathbf{U}}^{k} } \right)\) denotes the gradient vector and \({\mathbf{n}}^{k}\) stands for the vector of normalized search direction at \({\mathbf{U}}^{k}\), which is represented as
2.2 Stability transformation method
The iterative formulation of the stability transformation method (STM) (Yang 2010) is formulated as
where \(\zeta\) refers to the chaos control factor, whose value ranges from 0 to 1 (Meng et al. 2017). \({\mathbf{C}}\) denotes an involutory matrix; \({\mathbf{f}}\) represents a function vector of random variable.
2.3 Directional stability transformation method
The iterative formula of the directional stability transformation method (DSTM) (Meng et al. 2017) is defined as
where \({\mathbf{n}}^{k}\) represents the current normalized search direction vector. The search direction can be divided into circumferential and radial directions, while DSTM only controls the iteration step length in circumferential direction, reducing the computational effort of STM.
2.4 Finite step length method
The basic formula of the FSL method (Gong and Yi 2011) can be expressed as
where \({{\varvec{\upalpha}}}^{k + 1}\) refers to a finite sensitivity vector at point \({\mathbf{U}}^{k}\); \(\lambda\) is the step length, which should satisfy greater than 0 (Gong and Yi 2011).
When \(\lambda \to \infty\), the iterative formula of the FSL method is identical to that of the HL-RF method. It implies that the HL-RF method is a particular form of the FSL method when \(\lambda \to \infty\). During the iterative process, the update of step length is determined by the following criterion
When Eq. (14) is satisfied, one can set \(\lambda^{k + 1} = \lambda^{k} /c\). Herein, \(c\) is a step length adjusting coefficient, which is usually taken between 1.2 and 1.5 (Gong and Yi 2011).
3 The proposed method
3.1 Derivatives of the enhanced finite step length method
The robustness and effectiveness of the FSL method was verified, but it still has two problems need to be overcome. The first problem is that when facing complex nonlinear limit state functions, the oscillation amplitude in each iteration gradually decreases throughout the iterative process, and the step length updated criterion Eq. (14) does not work. The consequence is that the step length \(\lambda\) does not change during the iterative process, although the oscillation exists, leading to a larger computational effort. Since the criterion in Eq. (14) is closely related to the oscillation amplitude, which is called as oscillation amplitude criterion. The second problem is that when the criterion in Eq. (14) works during the iterative process, the single step length adjustment formula of the FSL method and the unpredictable degree of nonlinear limit state functions lead to inability to adaptively adjust step length.
To solve the above-mentioned problems, a new step length updated strategy is proposed for the FSL method to enhance the capability for solving complex nonlinear problems. Herein, the proposed method is referred to as an EFSL method.
For the first problem, the purpose is to overcome the shortcomings of the oscillation amplitude criterion. Inspired by previous work in Jiang et al. (2017), a state parameter is adopted as criterion to prevent this situation, which is represented as
where \(M\) represents a state parameter, which is initially set to zero. \(M^{t}\) is a target state parameter, which is recommended to set as 2.
During each step of the iteration, the state parameter \(M\) will be added by 1 when Eq. (14) is not satisfied, and \(\lambda\) does not change at this time. Conversely, the state parameter \(M\) becomes 0 when Eq. (14) is satisfied. The step length \(\lambda\) will be adjusted at this time and the step length adjustment formula is given subsequently. When Eq. (15) is satisfied, whether or not the criterion in Eq. (14) is satisfied at this time, the step length \(\lambda\) will be adjusted. After the step length adjustment, the state parameter \(M\) is changed to zero again. The reason for the recommended value of target state parameter \(M^{t}\) in Eq. (15) is that when the criterion \(M{ = }M^{t}\) is satisfied, the step length \(\lambda\) should be updated to resolve such problem that the oscillation exists but the step length \(\lambda\) keeps fixed value. Therefore, the value of \(M^{t}\) should be set neither too large nor too small. If the value of \(M^{t}\) takes too large or too small, it is not conducive to adjust the step length \(\lambda\). According to the test experiences, taking 2 is an appropriate choice.
For the second problem, a comprehensive step length adjustment formula is developed, and the step length \(\lambda\) is adaptively adjusted in the face of different degrees of nonlinearity limit state functions. The step length \(\lambda\) is large for the weakly nonlinear limit state functions and the step length \(\lambda\) is small for the highly nonlinear limit state functions. The proposed comprehensive compensation adjustment formula consists of two parts, whether the criterion in Eq. (14) is satisfied or not.
When the criterion in Eq. (14) is satisfied, a new step length adjustment formula is developed, which is expressed as
where \(n\) represents a chaotic number, which satisfies \(n \in \left( {0,1} \right)\); \(c\) is a control parameter, which satisfies \(0 < c < 4\). The chaotic number \(n\) and control parameter \(c\) in Eq. (16) play an important role to adjust the step length. To reduce the step length \(\lambda\), the chaotic number \(n\) and control parameter \(c\) should satisfy the following criterion
where \(n\) satisfies \(n \in \left( {0,1} \right)\) and \(c\) satisfies \(0 < c < 4\). In theory, all the possible combinations of n and c satisfying the above criterion can be used. However, the recommended values of these two parameters are given as \(n = 0.05\) and \(c = 2\) according to the experience.
When the step length is updated, the state parameter \(M\) becomes zero. To ensure smooth convergence, a new criterion is defined as
When Eq. (18) is satisfied, the adjustment formula of \(\lambda\) is expressed as
When the criterion in Eq. (14) is not satisfied, the state parameter \(M\) will be added by 1. When the state parameter \(M\) satisfies Eq. (15), a new step length adjustment is presented, which is defined as
This equation can effectively balance the adaptive adjustment of the step length \(\lambda\) when facing weakly and highly nonlinear limit state functions. It should be noted that when updating the step length using Eq. (20), the state parameter \(M\) will become zero again, and then move to the next iteration.
Since the nonlinear degree of limit state functions cannot be predicted in advance, the initial value of \(\lambda\) should be relatively large. The initial value of \(\lambda^{0}\) is shown as
3.2 Step and flowchart of the proposed EFSL method
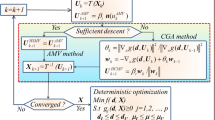
The detailed algorithm steps of the proposed EFSL method are summarized in Table 1. The flowchart of the proposed EFSL method is shown in Fig. 1.
4 Illustrative examples of structural reliability analysis
In this section, some nonlinear numerical examples are solved with the proposed EFSL method. The reliability analysis results are compared in terms of accuracy, efficiency, and robustness to those by other methods, which include HL-RF method (Hasofer and Lind 1974; Rackwitz and Flessler 1978), STM (Yang 2010), DSTM (Meng et al. 2017), and FSL method (Gong and Yi 2011). The control factors \(\zeta\) of STM and DSTM are taken as 0.10 and 0.05. The mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) and two additional different points are, respectively, selected as the initial points for different reliability analysis methods in the following examples. The involutory matrix \({\mathbf{C}}\) is considered as a unit matrix, which is applied to STM and DSTM. The convergence criterion for all these iterative algorithms is \(\left\| {{\mathbf{X}}^{k + 1} - {\mathbf{X}}^{k} } \right\|/\left\| {{\mathbf{X}}^{k + 1} } \right\| < 10^{ - 6}\). The Monte Carlo simulation (MCS) method (Xiao et al. 2020) with \(1 \times 10^{7}\) samples is used for calculating \(\beta^{{{\text{MCS}}}}\) to validate the accuracy of the proposed method. To illustrate that the \(\beta^{{{\text{MCS}}}}\) used in the examples is sufficiently accurate, the plots of the number of sampling points versus \(\beta^{{{\text{MCS}}}}\) are provided to show the convergence, which are given in Figs. 2, 4, 6, 8, and 10. The number of sampling points is taken as \(10^{5}\), \(5 \times 10^{5}\), \(10^{6}\), \(5 \times 10^{6}\), \(10^{7}\), \(5 \times 10^{7}\) and \(10^{8}\), respectively.
The plot of the number of different sampling points versus \(\beta^{{{\text{MCS}}}}\) in Example 1
The statistical data of limit state functions for Examples 1–5 are shown in Table 2. In addition, the reliability analysis results of different methods, including calculation of MPP (\({\mathbf{X}}^{\ast }\)), iteration number, number of function evaluations (F-evaluations), and calculation of reliability index \(\beta\) are given in Tables 3, 4, 5, 6, 7, 8, 9, 10, 11, and 12. The number of F-evaluations is the sum of the number of performance function \(g\) call and the number of gradient function \(\nabla g\) call. Herein, the sensitivity analysis is evaluated by the analytical method. The iterative histories of the comparative methods are illustrated in Figs. 3, 5, 7, 9, and 11.
Example 1
The limit state function of the first example is highly nonlinear and includes two independent random variables in normal distribution (Gong et al. 2014). As illustrated in Table 3, all the comparative methods with the exception of HL-RF method can converge. The proposed EFSL method obtains the MPP \({\mathbf{X}}^{\ast} = \left( {0.3093,4.0401} \right)\) and yields the reliability index \(\beta = 4.0519\), which are approximately similar to the results in Gong et al. (2014). The plot of the number of different sampling points versus \(\beta^{{{\text{MCS}}}}\) is shown in Fig. 2. The reliability index calculated by the MCS method with \(10^{7}\) samples is \(\beta^{{{\text{MCS}}}} = 3.7031\). In terms of the accuracy and robustness of these methods, when the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) is selected as the initial points, the proposed EFSL method has similar accuracy with STM, DSTM, and FSL method for the same convergence criteria. When point (1, 1) and point (‒1, ‒1) are chosen as initial points, DSTM yields different MPPs and reliability indices compared to other methods. This reflects that the DSTM is sensitive to the choice of initial point and less robust, and inversely demonstrates the high accuracy and robustness of the proposed EFSL method.
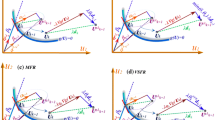
In terms of the efficiency of these methods, the proposed EFSL method has the fewest average number of iterations and number of F-evaluations. The average convergence speed of the proposed EFSL method is approximately three times higher than that of the FSL method. The STM, FSL, and proposed EFSL method are robust, but the proposed EFSL method is more efficient. When the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) is selected as the initial points, the detailed iterative histories of these comparative methods are shown in Fig. 3, which can be obviously found that the proposed EFSL method has the highest efficiency compared to other methods.
Example 2
The limit state function of the second example is a nonlinear exponential function, which includes two independent random variables in normal distribution (Meng et al. 2017). As illustrated in Table 5, when the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) and two additional different points are selected as the initial points, all the comparative methods with the exception of the HL-RF method can converge and yield the reliability index \(\beta = 2.8873\). These results are consistent with the results in Jiang et al. (2015). The plot of the number of different sampling points versus \(\beta^{{{\text{MCS}}}}\) in this example is shown in Fig. 4. The reliability index calculated by the MCS method with \(10^{7}\) samples is \(\beta^{{{\text{MCS}}}} = 3.0687\). In terms of accuracy, the proposed EFSL method has similar accuracy with STM, DSTM, and FSL method for the same convergence criteria.
In terms of the robustness and efficiency of these methods, from the average number of iterations and number of F-evaluations shown in Tables 5 and 6, the proposed EFSL method generates the fewest iteration number and F-evaluations number. Therefore, the proposed EFSL method has the highest convergence speed compared with other methods. Similarly, the STM, DSTM, and FSL method are all robust, but the proposed EFSL method is more efficient. When the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) is selected as the initial points, the detailed iterative histories of these comparative methods are shown in Fig. 5 to verify the high efficiency of the proposed EFSL method.
Example 3
The third example is also a nonlinear problem, which includes three independent random variables in normal distribution (Gong et al. 2014). From Table 7, when the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) and two additional different points are selected as the initial points, all the comparative methods with the exception of the HL-RF method can converge successfully. The proposed EFSL method obtains the MPP \({\mathbf{X}}^{\ast} = \left( {0.8344, - 0.7324, - 3.5348} \right)\) and yields the reliability index \(\beta = 3.7050\), which are consistent with the results in Yang et al. (2020). The plot of the number of different sampling points versus \(\beta^{{{\text{MCS}}}}\) is shown in Fig. 6. The reliability index calculated by the MCS method with \(10^{7}\) samples is \(\beta^{{{\text{MCS}}}} = 3.7236\). In terms of accuracy, the proposed EFSL method has similar accuracy with STM, DSTM, and FSL method for the same convergence criteria.
In terms of the efficiency and robustness of these comparative methods, the proposed EFSL method has the fewest average number of iterations and number of F-evaluations. The proposed EFSL has the highest convergence speed compared with other methods. The STM, DSTM, and FSL method are robust, but the proposed EFSL method is more efficient. When the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) is selected as the initial points, the detailed iterative histories of these comparative methods are shown in Fig. 7, which can be obviously found that the proposed EFSL method has the highest efficiency compared to other methods.
Example 4
This example is a complex limit state function including seven independent random variables with three different distributions (Gong et al. 2014). From Table 9, when the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) is selected as the initial points, all the comparative methods can successfully find MPP and yield the reliability index \(\beta = 2.7471\). These results are consistent with the results in Gong and Yi (2011). The plot of the number of different sampling points versus \(\beta^{{{\text{MCS}}}}\) is shown in Fig. 8. The reliability index calculated by the MCS method with \(10^{7}\) samples is \(\beta^{{{\text{MCS}}}} = 3.3985\). Although the reliability index changes slightly at different initial points, the same reliability index is obtained for all reliability analysis methods at the same initial point. Therefore, in terms of accuracy, all the comparative methods have similar accuracy for the same convergence criteria.
In terms of the robustness and efficiency of these methods, from the average number of iterations and number of F-evaluations as shown in Tables 9 and 10, the HL-RF method has a high efficiency in this problem compared to STM, DSTM, and FSL method, but the proposed EFSL method has the fewest average number of iterations and number of F-evaluations. The average convergence speed of the proposed EFSL method is about eleven times higher than that of the FSL method. The proposed EFSL method has the advantage of being as simple and efficient as the HL-RF method, while ensuring the robustness. When the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) is selected as the initial points, the detailed iterative histories of these comparative methods are shown in Fig. 9, which can be obviously found that the proposed EFSL method has the highest convergence speed compared to other methods.
Example 5
The limit state function of the final example is complex and highly nonlinear, which includes ten independent random variables in normal distribution (Roudak et al. 2017). From Table 11, when the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) and two additional different points are selected as the initial points, HL-RF method cannot converge and other methods except STM with \(\zeta = 0.05\) obtain the reliability index \(\beta = 3.7515\). These results are consistent with the results in Yang et al. (2020). The plot of the number of different sampling points versus \(\beta^{{{\text{MCS}}}}\) is shown in Fig. 10. It can be seen from Fig. 10 that the \(\beta^{{{\text{MCS}}}}\) with \(10^{5}\) samples is not converged. The reliability index calculated by the MCS method with \(10^{7}\) is \(\beta^{{{\text{MCS}}}} = 4.5336\). Since this limit state function is highly nonlinear, there are some errors in these comparative methods. In terms of accuracy, the proposed EFSL method has similar accuracy with DSTM, STM, and FSL method for the same convergence criteria.
In terms of the robustness and efficiency of these methods, the proposed EFSL method has the fewest average number of iterations and number of F-evaluations, and the average convergence speed is about six times higher than that of the FSL method. The STM, DSTM, and FSL method are robust, but the proposed EFSL method is more efficient. When the mean vector \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) is selected as the initial points, the iterative histories of these comparative methods are shown in Fig. 11, which can be obviously found that the proposed EFSL method has the highest convergence speed compared to those of other methods in this study.
5 The proposed method in combination with RBDO
This section introduces the typical formulation of RBDO and DLM, and then the proposed EFSL method is combined with DLM. The EFSL-based DLM is compared with the conventional optimization method through four nonlinear RBDO examples to verify the efficiency and robustness of the EFSL-based DLM. The comparison methods used in this study are chaos control (CC) method-based DLM (DLM/CC) (Yang and Yi 2009), modified chaos control (MCC) method-based DLM (DLM/MCC) (Meng et al. 2015), hybrid mean value (HMV) method-based DLM (DLM/HMV) (Du and Choi 2008), and FSL method-based DLM (DLM/FSL) (Gong and Yi 2011). The proposed EFSL-based DLM is abbreviated as DLM/EFSL.
5.1 Typical RBDO formulation
The RBDO mathematical model is defined as (Chen et al. 2013a; Yang et al. 2020)
where \(f\left( {{\mathbf{d}},{{\varvec{\upmu}}}_{{\mathbf{X}}} ,{{\varvec{\upmu}}}_{{\mathbf{P}}} } \right)\) stands for an objective function; \({\mathbf{d}}\) refers to a vector of deterministic design variable; \({{\varvec{\upmu}}}_{{\mathbf{X}}}\) denotes the mean of random variable vector \({\mathbf{X}}\); \({{\varvec{\upmu}}}_{{\mathbf{P}}}\) indicates the mean of random parameter vector \({\mathbf{P}}\); \({\text{Prob}}\left( \cdot \right)\) is the failure probability operator; performance function \(g_{i} \left( {{\mathbf{d}},{\mathbf{X}},{\mathbf{P}}} \right) \le 0\) is defined as a failure event; the probabilistic constraint is defined as failure probability less than or equal to the maximum permissible target failure probability \(P_{{f_{i} }}^{t}\); \({\mathbf{d}}^{L}\) and \({\mathbf{d}}^{U}\) are the lower and upper bounds of \({\mathbf{d}}\); \({{\varvec{\upmu}}}_{{\mathbf{X}}}^{L}\) and \({{\varvec{\upmu}}}_{{\mathbf{X}}}^{U}\) are the lower and upper bounds of \({\mathbf{X}}\).
5.2 Double loop method
Due to the uncertainty of \({\mathbf{X}}\) and \({\mathbf{P}}\), the response of performance function is also uncertain. The structural failure probability can be defined as (Youn and Choi 2004)
where \(f_{{{\mathbf{X}},{\mathbf{P}}}} \left( {{\mathbf{X}},{\mathbf{P}}} \right)\) represents the joint probability density function. The multidimensional integral of Eq. (23) is computationally expensive and difficult to solve (Aoues and Chateauneuf 2010). To avoid direct integration of Eq. (23), two representative methods were developed including reliability index approach (RIA) (Zhu et al. 2021) and performance measure approach (PMA) (Hamza et al. 2020; Lee et al. 2008).
5.2.1 Reliability index approach
Reliability index approach replaces the probabilistic constraints in Eq. (22) with reliability indices as constraints, which can be transformed into the following form (Zhu et al. 2021)
where \(\beta_{i}^{t}\) denotes the target reliability index of the ith constraint.
Then, the reliability index \(\beta_{i}\) can be computed by the following optimization problem
where the most probable point \({\mathbf{U}}_{{^{{{\text{MPP}}}} }}\;\) in U-space is obtained from Eq. (25), and \(\beta_{i} { = }\left\| {{\mathbf{U}}_{{{\text{MPP}}}} } \right\|\).
5.2.2 Performance measure approach
Performance measure approach transforms the probabilistic constraints in Eq. (22) to performance measures as constraints (Hamza et al. 2020):
where \(g_{i}\) denotes the probabilistic performance measure of the ith probabilistic constraint.
The minimum performance target point \({\mathbf{U}}_{{{\text{MPTP}}}}\) can be computed by inverse reliability analysis, which can be expressed by the following formula (Hamza et al. 2020)
The study shows that PMA is more robust compared to RIA and is not susceptible to the value of reliability index (Aoues and Chateauneuf 2010).
5.3 Integration of the EFSL method with DLM
It is verified that the proposed EFSL method has a good ability for solving nonlinear limit state functions in Sect. 4. Therefore, the proposed EFSL method is considered to be combined with DLM to improve the ability of DLM for solving complex RBDO problems. The proposed DLM/EFSL can be expressed as
5.4 Illustrative examples of RBDO
The robustness and efficiency of the proposed DLM/EFSL method are demonstrated by four design problems including numerical and structural examples. The optimizer “fmincon” is used as a tool to perform the optimization loop. The convergence criterion is set as \(\left\| {{\mathbf{X}}^{k + 1} - {\mathbf{X}}^{k} } \right\|/\left\| {{\mathbf{X}}^{k + 1} } \right\| < 10^{ - 6}\) for the inner loop, and the convergence criterion is set as \(\left\| {{\mathbf{d}}^{k + 1} - {\mathbf{d}}^{k} } \right\|/\left\| {{\mathbf{d}}^{k + 1} } \right\| < 10^{ - 3}\) for the outer loop. The efficiency of the optimization method depends mainly on the number of function call, which includes the number of constraint function call and the number of objective function call. In addition, the number of constraint function call is the sum of the number of performance function call and the number of gradient function call. Since sensitivity analysis is evaluated by using the analytical method in this study, the evaluation of sensitivity is counted as one function call. Therefore, the evaluation of a constraint function and its sensitivity is counted as two function calls. The reliability index of the performance function is calculated by the MCS method at the obtained optimal design point and compared with the target reliability index to evaluate error of the proposed DLM/EFSL.
5.4.1 Design problem 1
This nonlinear benchmark example, which is extracted from Aoues and Chateauneuf (2010), includes two independent random variables \(X_{1}\) and \(X_{2}\) with normal distribution \(X_{i} \sim N\left( {\mu_{{X_{i} }} ,0.3^{2} } \right)\) and three nonlinear performance function constraints. The target reliability indices for three constraint functions are \(\beta_{i}^{t} = 3 \, \left( {i = 1,2,3} \right)\) and the initial point is set as \({\kern 1pt} {{\varvec{\upmu}}}_{{\mathbf{X}}}^{0} = \left[ {5.0,5.0} \right]^{{\text{T}}}\). The RBDO problem is formulated as
The optimization results of the comparative methods are summarized in Table 13, in which all the methods can successfully converge to the same optimum \({{\varvec{\upmu}}}_{{\mathbf{X}}} = \left( {3.4391,3.2866} \right)\) except for DLM/CC. These results are consistent with the results in Aoues and Chateauneuf (2010). In terms of the accuracy, the proposed DLM/EFSL is more accurate than DLM/CC. For efficiency, DLM/EFSL generates the lowest number of function calls of 978, which proves that DLM/EFSL is more efficient than the comparative methods.
The reliability indices of the constraint function calculated by the MCS method at the optimal point are \(\beta_{i}^{{{\text{MCS}}}}\). From Table 13, all the methods except DLM/CC have same error (− 0.0278, 0.0541,\(\infty\)). It means that the proposed DLM/EFSL improves the computational efficiency while retaining a high level of accuracy.
5.4.2 Design problem 2
This nonlinear mathematical problem, which is extracted from Lee and Song (2011), includes two independent random variables \(X_{1}\) and \(X_{2}\), which obey normal distribution \(X_{i} \sim N\left( {\mu_{{X_{i} }} ,0.2^{2} } \right)\) and three highly nonlinear performance function. The target reliability indices for three probabilistic constraints are set as 2 and the initial point is \({{\varvec{\upmu}}}_{{\mathbf{X}}}^{0} = \left[ {1.0,1.0} \right]^{{\text{T}}}\). The RBDO problem is defined as
The optimization results of the comparative methods are summarized in Table 14. From Table 14, all the methods can successfully converge and these methods can obtain the same optimal solution \({{\varvec{\upmu}}}_{{\mathbf{X}}} = \left( {0.5000,2.3619} \right)\) except for DLM/CC, which is approximately similar to the result in Jiang et al. (2017). In terms of accuracy, all the comparative methods have similar accuracy for the same convergence criteria. From the number of function calls, except for the DLM/HMV, the proposed DLM/EFSL generates the lowest number of function calls of 1878. It proves that DLM/EFSL has accurate and efficient characteristics.
The reliability indices of the three probabilistic constraints calculated by the MCS method at the optimal point are \(\beta_{i}^{{{\text{MCS}}}}\). From Table 14, all the methods except DLM/CC have the same error (0.0567, 0.2847, 1.5113). It means that the proposed DLM/EFSL improves computational efficiency while retaining a high level of accuracy.
5.4.3 Cantilever beam design problem
This example is a vertical and lateral bending problem of cantilever beam extracted from Shan and Wang (2008), which includes two highly nonlinear performance functions, two independent design variables, and four random parameters. The tip of this beam is subjected to lateral and vertical loads of Z and Y. The random design variables are the width w and thickness t of the cross-section. The physical significance of the objective function is to minimize the weight of the cantilever beam. The length L is 100 in and the cantilever beam under lateral and vertical loads is shown in Fig. 12.
There are two failure modes for this cantilever beam. One failure mode refers to yielding at the fixed end of the cantilever, i.e., the combined force of these two forces produces the stress M greater than the yield strength S; another is the tip displacement D exceeding the permissible value \(D_{0} = 2.5^{\prime \prime }\). Two random variables and four random parameters obey normal distribution, as shown in Table 15.
The target reliability indices for two probabilistic constraints are set as \(\beta_{i}^{t} = 3, \, i = 1,2\) and the initial point is \({\mathbf{d}}^{0} { = }\left[ {2.5,2.5} \right]^{{\text{T}}}\). The RBDO problem is described as
where stress M and tip displacement D can be formulated as
The optimization results of the comparative methods are summarized in Table 16. From Table 16, all the methods with the exception of DLM/CC obtain the same objective function value 9.5202, corresponding to the same optimum point (2.4460, 3.8922). These results are consistent with the results in Yang and Gu (2004). It means that the DLM/EFSL has a high degree of accuracy. Regarding the number of function call, DLM/EFSL generates the lowest function call number of 351 and the highest convergence speed. This example indicates that DLM/EFSL performs well in terms of both convergence performance and computational efficiency.
5.4.4 Vehicle side impact problem
Vehicle impacts occur frequently in traffic accidents. Because the mechanical properties of the body on both sides of the vehicle are relatively weak, improving the degree of side impact resistance of the vehicle is of great importance to the safety of passengers. Hence, the proposed DLM/EFSL is now applied to the vehicle side impact design. The finite element analysis model (Youn et al. 2004; Zhang et al. 2021b), which consists of 85,941 shell elements and 96,122 nodes, is shown in Fig. 13. In the vehicle side impact finite element simulation, the barrier impacts the side of the vehicle at a velocity of 49.89 kph. One simulation of this finite element model using the RADIOSS software on SGI Origin 2000 takes about 20 h. This study uses the European Enhanced Vehicle-Safety Committee (EEVC) side impact criteria to enable the vehicle to meet the specified internal and regulatory side impact requirements. The EEVC side impact criteria, which is shown in Table 17, include abdomen load, rib deflections, VC’s (viscous criteria), pubic symphysis force, and Head Injury Criterion (HIC). In addition, the velocity of the front door at the B-pillar and the velocity of the B-pillar at the middle point need to be considered in the side impact design.
Schematic of vehicle side impact model (Zhang et al. 2021b)
To achieve the goal of reducing weight of vehicle while ensuring the safety of personnel, an optimal model for the side impact of vehicle considering ten safety constraints is developed. The RBDO problem is formulated as
The optimal model includes seven random variables X1–X7 and four random parameters X8–X11, and their statistical characteristics are given in Table 18. They are independent and normally distributed. The mean values of \(X_{8}\) and \(X_{9}\) are set as 0.345. The target reliability indices for ten probabilistic constraints are set as \(\beta_{{}}^{t} = 3\), corresponding to the target reliability of 99.8650%. The initial point is \({{\varvec{\upmu}}}_{{\mathbf{X}}}^{0} { = }\left[ {1.0,0.9,1.0,1.0,1.75,0.8,0.8} \right]^{{\text{T}}}\).
The optimization results of the comparative methods and the constraint functions at the optimal point, which are verified against the MCS method, are listed in Tables 19 and 20, respectively. From Table 19, DLM/HMV, DLM/FSL, and DLM/EFSL obtain the same objective function value 29.5578, but DLM/CC and DLM/MCC converge to objective function value 29.5567 and 29.5564. These results are approximately similar to the results in Yang and Gu (2004). It means that these comparative methods have similar degree of accuracy. In terms of efficiency, DLM/EFSL generates the lowest number of function calls compared to other comparative methods in the vehicle side impact problem, which demonstrates the superior computational efficiency of DLM/EFSL.
The reliability indices of constraint functions at the optimal point are shown in Table 20. From Table 20, the DLM/HMV, DLM/FSL, and DLM/EFSL have the same error (\(\infty\), 0.0017, 1.3502, 0.0001, \(\infty\), \(\infty\), \(\infty\), − 0.5677,1.9354, 0.2029). It means that DLM/EFSL improves efficiency while retaining a high level of computational accuracy.
6 Conclusions
Although the FSL method has achieved some improvement in robustness and effectiveness compared with improved HL-RF method, it cannot compensate for the deficiency of the FSL method in the oscillation amplitude criterion and adaptively adjust the step length for limit state functions with different degrees of nonlinearity. As a result, the FSL method may result in generating larger computational effort and lower efficiency gains.
In this study, an EFSL method is proposed to overcome the shortcomings of the FSL method. The efficiency and robustness of the proposed EFSL method compared to other commonly used methods like HL-RF, STM, DSTM, and FSL method are verified by five examples. Considering that the proposed method has good capability for solving nonlinear reliability analysis problems, the proposed EFSL method is combined with the DLM to enhance the efficiency for solving complex RBDO problems. Four design problems are employed to verify the computational performance of DLM/EFSL, compared with methods, such as DLM/CC, DLM/MCC, DLM/HMV, and DLM/FSL. It is found that in design problem 2, DLM/EFSL is less computationally efficient than DLM/HMV but higher than DLM/CC, DLM/MCC, and DLM/FSL, while DLM/EFSL has the highest computational efficiency in other three design problems.
In conclusion, the proposed EFSL method improves the efficiency and robustness by adopting a new iterative control criterion and a comprehensive step length adjustment formula, which allow adaptive step length adjustment for different degrees of nonlinear limit state functions. Furthermore, DLM/EFSL is also a robust and efficient RIA-based DLM. To some extent, it has positive significance for structural reliability analysis and RBDO problems.
References
Aoues Y, Chateauneuf A (2010) Benchmark study of numerical methods for reliability-based design optimization. Struct Multidisc Optim 41:277–294. https://doi.org/10.1007/s00158-009-0412-2
Biswas R, Sharma D (2021) An approximate single-loop chaos control method for reliability based design optimization using conjugate gradient search directions. Eng Optim. https://doi.org/10.1080/0305215x.2021.2007242
Chen Z, Qiu H, Gao L, Li P (2013a) An optimal shifting vector approach for efficient probabilistic design. Struct Multidisc Optim 47:905–920. https://doi.org/10.1007/s00158-012-0873-6
Chen Z, Qiu H, Gao L, Su L, Li P (2013b) An adaptive decoupling approach for reliability-based design optimization. Comput Struct 117:58–66. https://doi.org/10.1016/j.compstruc.2012.12.001
Chiralaksanakul A, Mahadevan S (2005) First-order approximation methods in reliability-based design optimization. J Mech Des 127:851–857. https://doi.org/10.1115/1.1899691
Du X, Chen W (2004) Sequential optimization and reliability assessment method for efficient probabilistic design. J Mech Des 126:225–233. https://doi.org/10.1115/1.1649968
Du L, Choi KK (2008) An inverse analysis method for design optimization with both statistical and fuzzy uncertainties. Struct Multidisc Optim 37:107–119. https://doi.org/10.1007/s00158-007-0225-0
Gong J, Yi P (2011) A robust iterative algorithm for structural reliability analysis. Struct Multidisc Optim 43:519–527. https://doi.org/10.1007/s00158-010-0582-y
Gong J, Yi P, Zhao N (2014) Non-gradient-based algorithm for structural reliability analysis. J Eng Mech. https://doi.org/10.1061/(asce)em.1943-7889.0000722
Hamza F, Ferhat D, Abderazek H, Dahane M (2020) A new efficient hybrid approach for reliability-based design optimization problems. Engineering with Computers. https://doi.org/10.1007/s00366-020-01187-5
Hasofer AM, Lind NC (1974) Exact and invariant second-moment code format. J Eng Mech Div 100:111–121. https://doi.org/10.1016/S0022-460X(74)80150-1
Hu Z, Du X (2013) A sampling approach to extreme value distribution for time-dependent reliability analysis. Journal of Mechanical Design. https://doi.org/10.1115/1.4023925
Jiang C, Han S, Ji M, Han X (2015) A new method to solve the structural reliability index based on homotopy analysis. Acta Mech 226:1067–1083. https://doi.org/10.1007/s00707-014-1226-x
Jiang C, Qiu H, Gao L, Cai X, Li P (2017) An adaptive hybrid single-loop method for reliability-based design optimization using iterative control strategy. Struct Multidisc Optim 56:1271–1286. https://doi.org/10.1007/s00158-017-1719-z
Jiang C, Hu Z, Liu Y, Mourelatos ZP, Gorsich D, Jayakumar P (2020) A sequential calibration and validation framework for model uncertainty quantification and reduction. Comput Methods Appl Mech Eng 368:113172. https://doi.org/10.1016/j.cma.2020.113172
Keshavarzzadeh V, Meidani H, Tortorelli DA (2016) Gradient based design optimization under uncertainty via stochastic expansion methods. Comput Methods Appl Mech Eng 306:47–76. https://doi.org/10.1016/j.cma.2016.03.046
Keshtegar B (2016) Chaotic conjugate stability transformation method for structural reliability analysis. Comput Methods Appl Mech Eng 310:866–885. https://doi.org/10.1016/j.cma.2016.07.046
Keshtegar B, Meng Z (2017) A hybrid relaxed first-order reliability method for efficient structural reliability analysis. Struct Saf 66:84–93. https://doi.org/10.1016/j.strusafe.2017.02.005
Koduru SD, Haukaas T (2010) Feasibility of FORM in finite element reliability analysis. Struct Saf 32:145–153. https://doi.org/10.1016/j.strusafe.2009.10.001
Lee J, Song CY (2011) Role of conservative moving least squares methods in reliability based design optimization: a mathematical foundation. Journal of Mechanical Design. https://doi.org/10.1115/1.4005235
Lee I, Choi KK, Du L, Gorsich D (2008) Inverse analysis method using MPP-based dimension reduction for reliability-based design optimization of nonlinear and multi-dimensional systems. Comput Methods Appl Mech Eng 198:14–27. https://doi.org/10.1016/j.cma.2008.03.004
Lind PN, Olsson M (2019) Augmented single loop single vector algorithm using nonlinear approximations of constraints in reliability-based design optimization. J Mech Des 141:9. https://doi.org/10.1115/1.4043679
Liu P-L, Kiureghian AD (1986) Multivariate distribution models with prescribed marginals and covariances. Probab Eng Mech 1:105–112. https://doi.org/10.1016/0266-8920(86)90033-0
Liu P-L, Kiureghian AD (1991) Optimization algorithms for structural reliability. Struct Saf 9:161–177. https://doi.org/10.1016/0167-4730(91)90041-7
Meng Z, Li G, Wang BP, Hao P (2015) A hybrid chaos control approach of the performance measure functions for reliability-based design optimization. Comput Struct 146:32–43. https://doi.org/10.1016/j.compstruc.2014.08.011
Meng Z, Li G, Yang D, Zhan L (2017) A new directional stability transformation method of chaos control for first order reliability analysis. Struct Multidisc Optim 55:601–612. https://doi.org/10.1007/s00158-016-1525-z
Meng Z, Pu Y, Zhou H (2018) Adaptive stability transformation method of chaos control for first order reliability method. Engineering with Computers 34:671–683. https://doi.org/10.1007/s00366-017-0566-2
Rackwitz R, Flessler B (1978) Structural reliability under combined random load sequences. Computers Structures 9:489–494. https://doi.org/10.1016/0045-7949(78)90046-9
Roudak MA, Shayanfar MA, Barkhordari MA, Karamloo M (2017) A robust approximation method for nonlinear cases of structural reliability analysis. Int J Mech Sci 133:11–20. https://doi.org/10.1016/j.ijmecsci.2017.08.038
Schueller GI, Pradlwarter HJ (2007) Benchmark study on reliability estimation in higher dimensions of structural systems - An overview. Struct Saf 29:167–182. https://doi.org/10.1016/j.strusafe.2006.07.010
Shan S, Wang GG (2008) Reliable design space and complete single-loop reliability-based design optimization. Reliab Eng Syst Saf 93:1218–1230. https://doi.org/10.1016/j.ress.2007.07.006
Wang Y, Hao P, Yang H, Wang B, Gao Q (2020) A confidence-based reliability optimization with single loop strategy and second-order reliability method. Comput Methods Appl Mech Eng 372:21. https://doi.org/10.1016/j.cma.2020.113436
Xiao N-C, Zhan H, Yuan K (2020) A new reliability method for small failure probability problems by combining the adaptive importance sampling and surrogate models. Comput Methods Appl Mech Eng 372:113336. https://doi.org/10.1016/j.cma.2020.113336
Xu J, Dang C (2019) A new bivariate dimension reduction method for efficient structural reliability analysis. Mech Syst Signal Proc 115:281–300. https://doi.org/10.1016/j.ymssp.2018.05.046
Yang D (2010) Chaos control for numerical instability of first order reliability method. Communications in Nonlinear Science Numerical Simulation 15:3131–3141. https://doi.org/10.1016/j.cnsns.2009.10.018
Yang RJ, Gu L (2004) Experience with approximate reliability-based optimization methods. Struct Multidisc Optim 26:152–159. https://doi.org/10.1007/s00158-003-0319-2
Yang D, Yi P (2009) Chaos control of performance measure approach for evaluation of probabilistic constraints. Struct Multidisc Optim 38:83–92. https://doi.org/10.1007/s00158-008-0270-3
Yang M, Zhang D, Han X (2020) New efficient and robust method for structural reliability analysis and its application in reliability-based design optimization. Comput Methods Appl Mech Eng. https://doi.org/10.1016/j.cma.2020.113018
Yang X, Cheng X, Liu Z, Wang T (2021) A novel active learning method for profust reliability analysis based on the Kriging model. Engineering with Computers. https://doi.org/10.1007/s00366-021-01447-y
Yang M, Zhang D, Wang F, Han X (2022) Efficient local adaptive Kriging approximation method with single-loop strategy for reliability-based design optimization. Comput Methods Appl Mech Eng 390:114462. https://doi.org/10.1016/j.cma.2021.114462
Youn BD, Choi KK (2004) An investigation of nonlinearity of reliability-based design optimization approaches. J Mech Des 126:403–411. https://doi.org/10.1115/1.1701880
Youn BD, Choi KK, Yang RJ, Gu L (2004) Reliability-based design optimization for crashworthiness of vehicle side impact. Struct Multidisc Optim 26:272–283. https://doi.org/10.1007/s00158-003-0345-0
Yu S, Wang Z (2019) A general decoupling approach for time- and space-variant system reliability-based design optimization. Comput Methods Appl Mech Eng 357:23. https://doi.org/10.1016/j.cma.2019.112608
Zhang D, Zhang N, Ye N, Fang J, Han X (2021a) Hybrid learning algorithm of radial basis function networks for reliability analysis. IEEE Trans Reliab 70:887–900. https://doi.org/10.1109/tr.2020.3001232
Zhang Z, Deng W, Jiang C (2021b) A PDF-based performance shift approach for reliability-based design optimization. Comput Methods Appl Mech Eng. https://doi.org/10.1016/j.cma.2020.113610
Zhu S-P, Keshtegar B, Trung N-T, Yaseen ZM, Bui DT (2021) Reliability-based structural design optimization: hybridized conjugate mean value approach. Engineering with Computers 37:381–394. https://doi.org/10.1007/s00366-019-00829-7
Funding
The authors would like to acknowledge the financial support from the National Natural Science Foundation of China (Grant No. 51905146), the Key R&D Plan Program of Hebei Province (Grant No. 19211808D), the Natural Science Foundation of Hebei Province (Grant No. E2020202066, No. A2021202006), and the State Key Laboratory of Reliability and Intelligence of Electrical Equipment (Grant No. EERI_OY2020005).
Author information
Authors and Affiliations
Contributions
DZ and JZ wrote the original manuscript. MY (yangmeide@hnu.edu.cn) and RW supervised the project, and they are co-corresponding authors of this paper. ZW reviewed and edited the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Replication of results
The code and data for producing the presented results will be made available by request.
Additional information
Responsible Editor: Yoojeong Noh
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhang, D., Zhang, J., Yang, M. et al. An enhanced finite step length method for structural reliability analysis and reliability-based design optimization. Struct Multidisc Optim 65, 231 (2022). https://doi.org/10.1007/s00158-022-03294-x
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s00158-022-03294-x