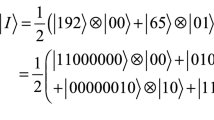Abstract
This paper presents a quantum image encryption algorithm based on Baker map and 2D logistic map. The encrypted image is represented with NEQR model and the presented scheme adopts the strategy of selective encryption. Given a threshold value T, when \(C^{\prime }_{YX}\geq T (C^{\prime }_{YX}< T)\), the proposed scheme performs U⊕k(U⊕A) on quantum state \(|I^{\prime }\rangle \). The final ciphertext quantum image is obtained through performing nine times quantum Baker map (QBM). The quantum circuits of encryption and decryption procedure are given. Multiple images were tested for security performance, including entropy, correlation coefficient (CC), Number of Pixel Change Rate (NPCR) and the Unified Averaged Changed Intensity (UACI). The best values of entropy, CC, NPCR and UACI are 7.9888, -0.0005, 99.58%, 33.17% respectively. Simulation results show that the proposed quantum image scheme has good performance in the aspect of security. By comparison with other schemes, the main indicators of the proposed scheme are roughly the same.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Feynman proposed the quantum computer model in 1982 [1]. The model uses the superposition and entanglement properties of quantum mechanics to store, process and transmit information. It has higher computing power compared to normal computers. Subsequently, Shor and Grover proposed quantum prime factorization algorithm [2] and quantum search algorithms [3] respectively. Therefore, the quantum computers began to appear in various fields of computer science. Such as quantum cryptography [4,5,6], quantum communication [7, 8], quantum image encryption and so on. Among them, quantum image encryption has become more and more important in recent years because it is more secure and efficient than traditional image encryption [9].
However, the digital image is converted into a quantum image before performing the quantum processing. Thus there are some quantum image representation methods are proposed. In 2003 Bose proposed the Qubit Lattice representation method [10]. The image is considered as a matrix and each qubit stores only one pixel. In 2010, a flexible representation of quantum images (FRQI) was proposed [11], an algorithm that represents color information as an angle. For an image of size 2n × 2n, its horizontal and vertical coordinates are expressed in n qubits. However, FRQI uses only one qubit to represent the color information, so it is not easy to perform some complex color manipulation. To address this problem, the novel enhanced quantum representation (NEQR) [12] was proposed in 2013. The total number of qubits required in NEQR is q + 2n for a gray range \(0\sim 2^{q}-1 \) image with size of 2n × 2n. Although it increases the use of qubits, it facilitates the handling of colors. It has also become a more widely used image representation model in quantum image processing. There are other quantum image representation models, such as the generalized quantum image representation (GNEQR) model [36], FRQIM [38] by slightly modifying FRQI, the normal arbitrary superposition state (NASS) model [13] and the multi-channel quantum image (MCQI) model [38], which improve the efficiency of specific applications.
According to the characteristics and convenience of various quantum image representation methods, NEQR and its improved method GNEQR are often used for time domain image encryption [15,16,17, 39], and FRQI and its improved method FRQIM are often used for frequency domain image encryption [19, 20, 40, 41]. Time-domain image encryption scheme generally encrypts images by scrambling pixel positions and changing pixel values. For example, in [15], a three-level quantum image encryption algorithm based on Arnold transform and logistic mapping is proposed, which performs block-level permutation, bit-level permutation and pixel-level diffusion respectively. The key space is increased by setting different block sizes as well as Arnold transform parameters. In 2019, Li et al. proposed a block image encryption algorithm based on GNEQR [16]. It is not only applicable to grey-scale and color images, but also can be used for rectangular images. The scheme uses both geometric and bit-plane transformations to change the position and pixel values of the image. Frequency-domain encryption are more complicated than the encryption algorithms over the time domain. Because they usually convert the image to the frequency domain for encryption while maintaining permutation and diffusion operations. There are some encryption schemes in frequency domain. For example, in [19], it proposes a quantum image encryption algorithm based on Arnold permutation and wavelet transform, which combines the time domain and frequency domain permutation to achieve good encryption results. The algorithm uses a modified FRQI model to represent the image. In [41], it uses Fibonacci transform and geometric transform to scramble the position and double random-phase encoding to encode the pixel information. There are some encryption schemes that only disturb the frequency domain characteristics of the image. For example, the algorithms in [18] use the double random phase encoding (DRPE) technique for quantum image encryption in the Fourier transform domain. Then the paper [18] is improved by Du, he makes the results of the double random phase coding as uniformly mixed as possible in [20].
In recent years, chaotic maps are often used to image encryption due to the features of sensitivity to initial values, a period and pseudo randomness [37]. Therefore, we propose a quantum image encryption method based on chaotic mapping and Fourier transform in time-frequency domain. Considering that most encryption operations are performed in the time domain, we choose NEQR as the representation method of quantum images. We incorporate the idea of selective encryption [24] into it to equalize histogram of cipher image. Selective encryption first to block the image. Then, different operations are performed on the image block according to whether the correlation coefficient in the block is greater than the threshold. The main advantages of this scheme as follows: (1) Associate the key with the plain image. It can effectively resist chosen-plaintext attack. (2) Equalize histogram of encrypted image. It can remarkably resist statistical attack. (3) The introduction of QFT increases the complexity of the encryption scheme.
The remainder of this paper is organised as follows. Section 2 presents some preliminary knowledges. The proposed encryption and decryption schemes are presented in Section 3. Section 4 presents simulations and security evaluations of the scheme. Finally, the conclusion is presented in Section 5.
2 Preliminary
Before introducing the background, we agree on some symbols in Table 1.
2.1 NEQR representation and quantum computation model
In [28], Zhang et al. presented the NEQR representation of quantum image. The digital image I can be stored into a normalized superposition state |I〉, that is, the proposed NEQR model stores the gray-scale and position information of the image using the superposition of the qubit sequences.
The NEQR model of a quantum image |I〉 for a 2n × 2n image can be written as
where the gray-scale value of the corresponding pixel (Y, X) is
While the vertical position Y and horizontal position X are represented with qubits |Y X〉. Thus, in the representation of NEQR, a quantum image with the gray-scale 2q and position information 2n × 2n consists of q + 2n qubits.
Next we introduce the quantum computation model. Quantum computation consists of a series of quantum logic gates and measurement results. It can accepts superposition states input and outputs corresponding superposition states. The special quantum computation model is as follow
where f is any function and Uf is a unitary operator [31].
2.2 Discrete Baker map (DBM) and quantum DBM
Baker mapping is a block scrambling method, and at the same time, selecting encryption requires dividing the image into blocks. That’s why Baker mapping was chosen for scrambling. The classical Baker map B(x, y), which maps the unit square 0 ≤ x, y ≤ 1 onto itself, is a special chaotic map in [29]. Classical Baker map B(x, y) is described as follows
where y ∈ [0,1]. In other words, as shown in Fig. 1, the classical Baker map maps the left rectangle of the square \([0, \frac {1}{2})\times [0,1)\) to rectangle \([0,1)\times [0, \frac {1}{2})\), and it transforms the right rectangle of the square \([\frac {1}{2},1)\times [0,1)\) to rectangle \([0,1)\times [\frac {1}{2},1)\).
The Baker map used for image encryption needs to be discretized because each image is composed of discrete pixel values. The Baker map can be discretized in the following.
Assume ni|N(i = 1, ⋯ , k) and n1 + n2 + ... + nk = N, N ∈ Z+. The discrete Baker Map is defined as follows. Firstly, it divides the image BN×N into N blocks, i.e.
where Bij is a matrix of \( \frac {N}{n_{i}} \) rows and ni columns, i = 1, ⋯ , k, j = 1, ⋯ , ni. Secondly, it performs matrix vec operator [30] on Bij to obtain B1N×N, i.e.
where B1ij is a matrix of 1 row and N columns. For example, let N = 4, n1 = 1, n2 = 2, n3 = 1, the discrete Baker Map is as shown in Fig. 2.
For an example with N = 4 in Fig. 2, we give a concrete quantum circuit of the quantum Baker map. The quantum analogy of classical image BN×N is |I〉, and its NEQR representation is expressed as
Apply the quantum Baker map on quantum image |I〉, and we obtain the new quantum image \(|I^{\prime }\rangle \). That is,
and its quantum circuit is shown in Fig. 3.
2.3 2D Logistic Map
The 2D Logistic Map [32] is defined as follows
where x1(n), x2(n) ∈ (0,1) and 2.75 < μ1 ≤ 3.4, 2.7 < μ2 ≤ 3.45, 0.15 < γ1 ≤ 0.21, 0.13 < γ2 ≤ 0.15. The 2D Logistic Map can ensure the keyspace larger and the encryption system more complex since there are two quadratic terms in the 2D Logistic Map.
3 Quantum image encryption scheme
In this section, the quantum image encryption scheme based on Baker map, 2D logistic map and quantum Fourier transform is presented in detail. The whole quantum image scheme has three main parts including key generation, encryption process and decryption process. More details can be introduced in the following subsections.
3.1 Key generation
Let the original classical image with size 28 × 28 be denoted as I. We use 2D logistic map to generate pseudo-random numbers with good cryptographic characteristics as the key. The specific steps are as follows.
Step 1. Caculate offset
a) Apply the discrete Baker map B(x, y) on classical image I, then it obtains a new image \(I^{\prime }\) denoted as \(I^{\prime }=B1_{N\times N}\) through equation (4).
b) Let B111 = (b11, ⋯ , b1N) be a vector from B1N×N, where b1k ∈ [0,255], k = 1, ⋯ , N. Apply operation dec2bin(⋅) on b1k of B111, and it has dec2bin(b1k) = (b1k)2 = (ek1, ⋯ , ekl)T, where ekl ∈{0,1} and l = 1, ⋯ , 8. Thus we obtain a 8 × N binary matrix \( BM=((b_{11})_{2}^{T},\cdots ,(b_{1N})_{2}^{T}) \).
c) Perform bitwise XOR operation on each row of BM, i.e., \( \alpha _{l}=\bigoplus _{k=1}^{N}e_{kl}, \alpha _{l}\in {{0,1}}, l=1,\dots ,8 \). Then, it obtains E = (α1, ⋯ , α8)T.
d) Perform bin2dec(⋅) operation on E, and it obtains bin2dec(E) = E10 = α7 × 27 + ⋯ + α1 × 20 and denotes E10 as the offset ∈ [0,255].
For example, let N = 8, the above calculation process of offset is shown in Fig. 4.
Step 2. Update the initial values of the 2D logistic map.
Suppose the initial values of the 2D logistic map are x1(0)′, x2(0)′. The offset that is obtain in Step 1 will be mapped to (0,1) by equation δ(s, offset). The δ(s, offset) is defined as follows
where symbol ⌊⋅⌋ is a floor function and s is a given value. In this paper, we convention s = 4.
Add the result of δ(s, offset) to x1(0)′, x2(0)′, and obtain the modified initial values x1(0), x2(0) i.e.,
where x1(0)′, x2(0)′ are given initial values and \( \left \lbrace x\right \rbrace \) is the fractional part of x.
Step 3. Generate key
Modified initial values will be used to generate the key. Substituting x1(0), x2(0) into equation (5), the equation yields two chaotic sequences x1 = (x1(1), ⋯ , x1(N/2)) and x2 = (x2(1), ⋯ , x2(N/2)). The chaotic sequences x1, x2 are mapped to \( \left [ 1,255\right ] \) using the equation as follows
where u ∈ (x1(1), ⋯ , x1(N/2), x2(1), ⋯ , x2(N/2)).
The mapped values g(u) are considered as
It shorted by \( k=(k_{1},\dots ,k_{N}) \).
Finally, after performing the dec2bin(⋅) function on k, we obtain the classical information k2 = dec2bin(k1) ⊕⋯ ⊕ dec2bin(kN) as the encryption key.
3.2 Encryption process
Alice and Bob secretly transmit image information using quantum technology. The encryption process involves the following steps.
Step 1. Let \(C_{Y^{\prime }X^{\prime }}\) be the corresponding discrete pixel values of image \(I^{\prime }\). Alice calculates \(A=floor(\frac {1}{N^{2}}{\sum }_{Y^{\prime }, X^{\prime }}C_{Y^{\prime }X^{\prime }})\) from \(I^{\prime }\) and selects a random number T ∈ [0,255]. Alice sends the binary sequence (k2, dec2bin(A)) to Bob through quantum key distribution protocol such as BB84 protocol.
Step 2. Initialization of the quantum state.
After performing the quantum Baker map (QBM) on I, and Alice obtains quantum image with size 28 × 28 denoted as \(|I^{\prime }\rangle \), and its NEQR representation is expressed as
Step 3. Alice computes \(C_{Y^{\prime } X^{\prime }}- T\) and stores the result on a auxiliary qubit |0〉a. If \(C_{Y^{\prime } X^{\prime }}\geq T (C_{Y^{\prime } X^{\prime }}<T)\), the auxiliary qubit |0〉a = |1〉(|0〉a = |0〉).
Step 4. If |0〉a = |1〉(|0〉a = |0〉), then Alice performs the unitary operation U⊕k(U⊕A) on quantum states \(|I^{\prime }\rangle \) and sequentially performs quantum Fourier transform (QFT) on it.
Step 5. Alice iterates the quantum Baker Map (QBM) nine times and obtains cipher image \(|C\rangle =|0\rangle _{a}|T\rangle |C^{\prime }_{YX}\rangle |YX\rangle \). After at least nine iterations, the original adjacent pixels will be distributed to the entire scrambled image [29]. That’s the reason for the nine iterations of QBM.
The flowchart of the proposed quantum image encryption is demonstrated in Fig. 5, and the corresponding quantum circuit in Fig. 6.
Note that the unitary operation U denotes as an inverse quantum adder operation in Fig. 6.
3.3 Decryption process
Step 1. Iterate discrete inverse quantum Baker Map (IQBM) on the entire cipher image |C〉 ten times, and the transformed image is still denoted as |C〉.
Step 2. Bob performs the inverse quantum Fourier transform (IQFT) on |C〉.
Step 3. Bob applies the control unitary operation C − U on plain image. If the control qubit is |1〉(|0〉), then the C − U is equivalent to C − U⊕k(C − U⊕A).
Step 4. Bob performs the inverse quantum Baker Map (IQBM) and obtains plain image I.
The flowchart of quantum image decryption is demonstrated in Fig. 7, and the corresponding quantum circuit in Fig. 8.
Note that the unitary operation U− 1 denotes as the quantum adder operation in Fig. 8.
4 Simulation Results
The experiments are performed on MATLAB R2018a. We use 256 × 256 images Cameraman, Peppers, Baboon, Lake and Lena to test the security performance of the encryption scheme. The security performance indicators include visual inspection, keyspace, entropy, encryption quality, histogram and differential analysis. The key of the encryption scheme is composed of (n1, ⋯ , nk;x1(0), x2(0), μ1, μ2, γ1, γ2). Set the key to (64, 32, 4, 8, 4, 16, 32, 64, 16, 16; 0.5, 0.5, 3, 3, 0.2, 0.14) during the experiment.
4.1 Visual Inspection
In evaluating the ciphered image, visual inspection is the easiest and most remarkable factor. The five original images and their corresponding encrypted images are shown in Fig. 9, there is a big difference between the original images and the ciphers. Thus the proposed scheme can hide the main information of the original images.
4.2 Keyspace
In the permutation stage, the key relies on the width (height) of the image to be encrypted due to the scrambling phenomenon of the chaotic Baker map. Thus, the keyspace of size 256 × 256 is equal to 1063 [23]. In the substitution stage, every parameter of the logistic map is a double precision number [23]. Thus, the keyspace in this stage is 1014 × 1014 × 1014 × 1014 × 1014 × 1014 = 1084. Such a large keyspace is enough to resist brute-force attacks.
4.3 Entropy
Entropy is an unpredictability measurement of structural characteristics for a cipher image x. The formula is defined as [22]
where N is the number of bits for the pixel value xi. In this paper, let N = 8. P(xi) is the proportion of pixel value xi ∈ [0,255] in the encrypted image x. To attach high-level security, the entropy E(x) should be close to 8. The entropy values of the cipher image corresponding to Cameraman, Peppers, Baboon, Lake and Lena are 7.983, 7.9854, 7.9812, 7.9888 and 7.9812 respectively as shown in Table 2. It shows that the proposed scheme has the unpredictability of structural characteristics.
4.4 Encryption Quality
In this section, correlation coefficient(CC), histogram deviation(HD), and irregular deviation(ID) have been calculated to evaluate the encryption quality.
CC is used to evaluate the correlation between plain image and cipher image. The value of CC is \( \left [ -1,1\right ] \). If the absolute value of CC equals to 1 that means the two images are the same. Thus, the lower absolute value of CC is, the better. The CC is measured by [22]
where \( E(x)=\frac {1}{N}{\sum }_{i=1}^{N}x_{i} \), N defines the pixel count in the image, and x, y are the pixel values of the plain image and encrypted image respectively.
The histogram deviation(HD) calculates the gap between the histogram of the original image and the histogram of the encrypted image and it can be defined as [22]
where W(Width) and H(Height) are the size of the image, and h1(i), h2(i) define the histogram of original image and enciphered image at value i respectively. The higher the HD value is, the better.
The histogram of an ideal encrypted image should keep each pixel level containing the same pixels. For example, for a 512 × 512 encrypted image, each pixel level should contain 512 × 512/256 = 1024 pixels. The irregular deviation(ID) measures the gap between the histogram of the cipher image and the histogram of the ideal encrypted image. The equation is [22]
where h(i) is enciphered image histogram at value i, and M is the average of an ideal enciphered image histogram. Given an image of size 256 × 256, M is set to 256. The smaller the ID value, the histogram of the encrypted image is closer to the histogram of the ideal encrypted image. Thus, the target is to attach the lower value of ID.
As shown in Table 3, the CC value of the encrypted Cameramen, Peppers, Baboon, Lake, Lena are 0.0025, -0.0005, -0.0024, -0.002 and -0.0061 respectively. It shows that the plain images and cipher images with a low correlation. The mean of HD is 0.8175. It shows that the difference between plain images and cipher images encrypted by the proposed scheme is large. The histograms of the cipher images are close to ideal histogram due to the ID values of five encrypted images are near to 0.1.
4.5 Histogram Analysis
The histograms of the plain images and cipher images are shown in Fig. 10. It proves that the histograms of the cipher images are different from the plain one. The cipher images have a uniformed histogram due to change the pixel value in time domain, which can resist statistical attacks better. The proposed scheme hides the histogram features well.
4.6 Differential Analysis
In order to resist differential attacks, a good encryption scheme should be sensitive to small changes in the key. There are two parameters used for differential analysis, namely Number of Pixel Change Rate (NPCR) and the Unified Averaged Changed Intensity (UACI), described as follows [22]
where E1 and E2 are two different cipher images of size W × H. If the pixel values of E1 and E2 at position (i, j) are different, that is, E1(i, j)≠E2(i, j), then D(i, j) = 1. There will be a big gap between E1 and E2 if the values of NPCR and UACI are big and it shows that the proposed scheme is sensitive to key. The original key is used to encrypt the original image to obtain cipher image E1. After that we exchange the position of the key n2 and n3, and keep other parameters unchanged. Then, the changed key is used to encrypt the original image to obtain cipher image E2.
The results of NPCR and UACI are shown in Table 4. We observe that the values of NPCR are above 90%. For a 256 gray level image, the expected UACI value is 33% and the UACI value of the Peppers is 33.17%. It means our scheme can resist differential attacks well.
4.7 Comparative Analysis
To verify the safety of the proposed scheme, various experiments have been carried out to compare the security based on entropy, CC, NPCR and UACI.
The comparative study between the proposed quantum image encryption scheme and other similar quantum image encryption schemes is performed based on the image Peppers. The values of entropy, CC, NPCR and UACI are listed in Table 5 for the proposed and other schemes in [15, 33,34,35]. One can see that the image encrypted by the proposed scheme has the lowest CC value, that is, the correlation of the encrypted image is the lowest. In addition, the results of the experiment indicate that the other key indicators are approximately comparable to those of other scheme.
5 Conclusion
This paper proposed an image encryption scheme based on QFT and two chaotic maps. The proposed cryptographic system use the selecting encryption method to equalize histogram. If \(C^{\prime }_{YX}\geq T (C^{\prime }_{YX}< T)\), it performs U⊕k(U⊕A) transformation, where the k and A are associated with the plain image. Then use QFT to transform the image to the frequency domain. Finally, we use a QBM to scramble the entire image. From the simulation results, the keyspace of two chaotic maps is enough to resist brute-force attacks. The mean values of CC, HD and ID are 0.0027, 0.8175, 0,1189, which have been demonstrated the security of the proposed scheme. Change the pixel values in the time domain makes the histogram uniform. The key related to the plain image can effectively resist plaintext attacks. The values of NRCR are all above 90%, and the highest is 99.58%. The values of UACI are all around 30%, and the highest is 33.17%. That shows the proposed scheme is sensitive to key. However, this scheme still has some shortcomings, that is, the histogram of the encrypted image is not balanced enough. In the future, the encryption scheme can be optimized to obtain a more evenly distributed histogram.
References
Feynman, R.P.: Simulating physics with computers. Int. J. Theor. Phys. 21(6), 467–488 (1982)
Shor, P.: Algorithms for quantum computation: discrete logarithms and factoring. Inproceedings of 35th Annual Symposium on the Foundations of Computer Science, IEEE Computer Society Press, Los Alamitos, CA, 124-134” (1994)
Grover, L.K.: A fast quantum mechanical algorithm for database search. Proceedings of the twenty-eighth annual ACM symposium on Theory of computing, pp 212–219 (1996)
Feng, H., Liu, B.J., Li, D., et al.: Traceable ring signatures: general framework and post-quantum security. Des. Codes Crypt., pp 1–35 (2021)
Wu, W.Q., Ma, X.X.: Quantum private comparison protocol without a third party. Int. J. Theor. Phys. 59(6), 1854–1865 (2020)
Wu, W.Q., Zhao, Y.X.: Quantum private comparison of size using d-level Bell states with a semi-honest third party. Quantum information process 20 (4), 155 (2021)
Song, S.Y., Wang, C.: Recent development in quantum communication. Chin. Sci. Bull. 57(36), 4694–4700 (2012)
Pirandola, S.: Bounds for multi-end communication over quantum networks. Quantum Science and Technology 4(4), 045006 (2019)
Wang, Z., Xu, M., Zhang, Y.: Review of quantum image processing. Archives of Computational Methods in Engineering, pp 1–25 (2021)
Venegas-Andr, S.E., Storing, B.S.: Processing, and retrieving an image using quantum mechanics. The International Society for Optical Engineering 5105, 137–147 (2003)
Le, P.Q., Iliyasu, A.M., Dong, F., et al.: A flexible representation of quantum images for polynomial preparation, image compression and processing operations. Quantum Inf. Process 10(1), 63–84 (2011)
Zhang, Y., Kai, L., Gao, Y., et al.: NEQR: A novel enhanced quantum representation of digital images. Quantum Inf. Process 12(8), 2833–2860 (2013)
Li, H.S., Zhu, Q., Zhou, R.G., et al.: Multi-dimensional color image storage and retrieval for a normal arbitrary quantum superposition state. Quantum Inf. Process 13(4), 991–1011 (2014)
Li, H.S., Song, S.X., Fan, P., et al.: Quantum vision representations and multi-dimensional quantum transforms. Inform. Sci. 502, 42–58 (2019)
Liu, X.B., Xiao, D., Liu, C.: Three-level quantum image encryption based on Arnold transform and logistic map. Quantum Inf. Process 20(1), 1–22 (2021)
Li, H.S., Chen, X., Song, S.X., et al.: A block-based quantum image scrambling for GNEQR. IEEE Access 7, 138233–138243 (2019)
Luo, Y.L., Tang, S.B., Liu, J.X., et al.: Image encryption scheme by combining the hyper-chaotic system with quantum coding. Opt. Lasers Eng. 124, 105836 (2020)
Yang, Y.G., Xia, J., Jia, X., et al.: Novel image encryption/decryption based on quantum Fourier transform and double phase encoding. Quantum Inf. Process 12(11), 3477–3493 (2013)
Hu, W.W., Zhou, R.G., et al.: Quantum image encryption algorithm based on Arnold scrambling and wavelet transforms. Quantum Inf. Process 19(3), 1–29 (2020)
Du, S.P., Qiu, D.W., Mateus, P., et al.: Enhanced double random phase encryption of quantum images. Results in Physics 13, 102161 (2019)
Musanna, F., Kumar, S.: Image encryption using quantum 3-D Baker map and generalized gray code coupled with fractional Chen’s chaotic system. Quantum Inf. Process 19(8), 220 (2020)
Allah, O., Afifi, A., ElShafai, W., et al.: Investigation of Chaotic Image Encryption in Spatial and frFT Domains for Cybersecurity Applications. IEEE Access 3(99), 195–208 (2020)
Ramadan, N., Ahmed, H., ElKhamy, S.E., et al.: Permutation-substitution image encryption scheme based on a modified chaotic map in transform domain. J. Cent. South Univ. 24(9), 2049–2057 (2017)
Sher, K.J., Jawad, A.: Chaos based efficient selective image encryption. Multidim. Syst. Sign. Process. 30, 943–961 (2019)
Fridrich, Jiri: Symmetric ciphers based on Two-Dimensional chaotic maps. International Journal of Bifurcation and Chaos 8(06), 1259–1284 (1998)
Wang, X., Crisis, S.h.i.Q.: New type hysteresis and fractal in coupled logistic map. Chinese Journal of Applied Mechanics 22, 501–506 (2005)
Henderson, H.V., Searle, S.R.: Vec and vech operators for matrices, with some uses in Jacobians and multivariate statistics. Canadian Journal of Statistics 7 (1), 65–81 (1979)
Zhang, Y., Kai, L., Gao, Y., et al.: NEQR: A novel enhanced quantum representation of digital images. Quantum Inf. Process 12(8), 2833–2860 (2013)
Jiri, F.: Symmetric ciphers based on two-dimensional chaotic maps. International Journal of Bifurcation and Chaos 8(06), 1259–1284 (1998)
Henderson, H.V., Searle, S.: Vec and vech operators for matrices, with some uses in jacobians and multivariate statistics. Canadian Journal of Statistics 7 (1), 65–81 (1979)
Kashefi, E., Kent, A., Vedral, V., et al.: A comparison of quantum oracles. Phys. Rev. A 65(5), 882–886 (2001)
Wang, X.Y., Shi, Q.J.: New type crisis: hysteresis and fractal in coupled logistic map. Chinese Journal of Applied Mechanics 22(4), 501–505 (2005)
Gong, L.H., He, X.T., Cheng, S., et al.: Quantum image encryption algorithm based on quantum image XOR operations. Int. J. Theor. Phys. 55, 3234–3250 (2016)
Liu, X.B., Xiao, D., Liu, C.: Quantum image encryption algorithm based on bit-plane permutation and sine logistic map. Quantum Inf. Process 19(8), 239 (2020)
Ye, G.D., Jiao, K.X., Huang, X.L., et al.: An image encryption scheme based on public key cryptosystem and quantum logistic map. Sci. Rep. 10, 21044 (2020)
Li, H.S., Ping, F., Xia, H.Y., et al.: Quantum implementation circuits of quantum signal representation and type conversion. IEEE Transactions on Circuits Systems I Regular Papers 1, 1–14 (2018)
Wang, X, Zhang, J, Cao, G: An image encryption algorithm based on ZigZag transform and LL compound chaotic system Optics Laser Technology, 119:105581-105591 (2019)
Li, H.S., Song, S.X., Ping, F., et al.: Quantum vision representations and multi-dimensional quantum transforms. Inform. Sci. 502, 42–58 (2019)
Liu, X.B., Xiao, D., Xiang, Y.P.: Quantum image encryption using intra and inter bit permutation based on logistic map. IEEE Access 7, 6937–6946 (2018)
Zhou, N.R., Hua, T.X., Gong, L.H., et al.: Quantum image encryption based on generalized Arnold transform and double random-phase encoding. Quantum Inf. Process 14, 1193–1213 (2015)
Wang, H., Wang, J., Geng, Y.C.: Quantum image encryption based on iterative framework of frequency-spatial domain transforms. Int. J. Theor. Phys. 56, 3029–3049 (2017)
Acknowledgements
The authors are supported by the Science and Technology Research Project of Higher Education of Hebei Province Nos. ZD2021011.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Rights and permissions
About this article
Cite this article
Wu, W., Wang, Q. Quantum Image Encryption Based on Baker Map and 2D Logistic Map. Int J Theor Phys 61, 64 (2022). https://doi.org/10.1007/s10773-022-04979-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-022-04979-1