Abstract
This paper presents a quantum private comparison (QPC) protocol based on Bell states. The proposed QPC protocol can secretly compare information of the two participants without the help of a third party (TP). The proposed protocol employs some decoy state photons and quantum SWAP gates to resist various outside attacks and internal attacks. This paper compares the presented quantum private comparison (QPC) protocol with other schemes in terms of different indicators. The results show that the proposed protocol has some advantages different from previous protocols.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Ever since quantum mechanics was introduced into the cryptography field, numerous quantum cryptographic applications have been proposed, such as quantum secure direct communication (QSDC) [1, 2], quantum secret sharing (QSS) [3, 4], quantum public key cryptosystem (QPKC) [5, 6].
Recently, quantum private comparison (QPC) becomes an important branch of quantum cryptography, which can privately compare two parties’ undisclosed information for equality. In 2009 the first QPC protocol was presented by Yang and Wen based on Bell states and a hash function [7]. Since then numerous QPC protocols have been proposed to improve both the security and the qubit efficiency in [8,9,10,11,12,13,14,15,16], etc. Thus far, these protocols have accomplished the comparison work with the help of a semi-honest third party (TP). But a semi-honest TP might try to steal the players private inputs, while he cannot be corrupted by the adversary.
Although Lo (1997) pointed that a QPC may not be securely evaluated with a two-party scenario under the technology of that time in [17]. With the advance in quantum entanglement swapping, many papers reconstructed the two-party QPC protocols without the help of a TP. In 2014 Lin et al. presented a QPC without a TP based on entanglement swapping and a hash function [18]. In 2016 He proposed a QPC with two parties only based on single photon sequences and hash function [19]. Soon afterwards, He proposed the device-independent version of the QPC protocol [20]. One common feature of these protocols is that they require the help of hash functions to complete the comparison in [18,19,20].
Quantum private comparisons without third-party help are rare. In addition, publishing more efficient and safer protocols are necessary. For the above reasons, this paper present a new QPC protocol without a third party via using the Bell states and quantum SWAP gates. The paper is organized as follows. Section 2 introduces some basic concepts. Section 3 presents a QPC protocol. Section 4 analyzes the security of the QPC protocol. Section 5 concludes the paper.
2 Background
2.1 Permutation Operation
We summarize some basic concepts about permutations. By definition, a permutation of set A = {1,⋯ ,n} is simply a bijection \(\pi : A\rightarrow A\). We usually write a permutation π by writing its values as a finite sequence π = (i1,⋯ ,in), where π(j) = ij and j = 1,⋯ ,n. We denote all permutations of the set A on Sn. For example, let A = {1,2,3}, then S3 = {(1,2,3),(1,3,2),(2,1,3),(2,3,1),(3,1,2),(3,2,1)}.
A transposition is a special permutation that fixes all but two integers, which are interchanged. For example, the following are some of the transpositions in S3: (1,3,2),(3,2,1),(2,1,3). We define the special notation [s,t] to denote the transposition in Sn that interchanges s and t. For example, with n = 3, (1,3,2) = [2,3],(3,2,1) = [1,3],(2,1,3) = [1,2].
There are two basic facts about permutations. One is that every permutation can be written as the composition of transpositions. For example, with n = 3, (3,1,2) = [2,3][1,2]. Another is that a representation of a permutation as a composition of transpositions is not unique. For example, with n = 3, (3,1,2) = [2,3][1,2] = [1,3][2,3]. There are more details in [21].
Next we define a special permutation operation called N-level permutation by iterating the cyclic shift operation several times. Details as below.
Let πk be a cyclic left-shift operation (shorted by \(\lll k\)) defined as πk(i) = i + k mod r, that is
where non-negative integer k < r. Another cyclic right-shift operation has the same definition.
Let S = {a(1,⋯ ,1,1,1),⋯ ,a(1,⋯ ,1,1,r),a(1,⋯ ,1,2,1),⋯ ,a(1,⋯ ,1,2,r),⋯ ,a(r,⋯ ,r,1),⋯ , \( a_{(\underbrace {r, \cdots , r, r}_{N})}\}\) be a rN-dimension set, where r,N ≥ 2. By (1), the cyclic left-shift operation \(\pi ^{(j)}_{k_{j}}\) on set S is defined as
where 1 ≤ j ≤ N,1 ≤ kj ≤ r.
Example 1
With N = 2,r = 3,kj = 2,j = 2, it follows that
So the mathematical description of N-level permutation is
where ∘ means the compound of operation and \(\pi ^{(j)}_{k_{j}}\) is the cyclic left-shift operation in (2).
Example 2
With N = 2,r = 3,k1 = 2,k2 = 2, it performs \(\pi =\pi ^{(2)}_{k_{2}}\circ \pi ^{(1)}_{k_{1}}\) operation and obtains
Now we define an induction operation of π as follows
Next we discuss the commutativity of N-level permutation. By the (2), (3) and (4), it directly fields the Proposition 1 as follows.
Proposition 1
Let πA and πB be two N-level permutations, \(\overline {\pi _{A}}\) and \(\overline {\pi _{B}}\) are induction operation of πA and πB respectively, then \(\pi _{A}\circ \overline {\pi _{B}}=\pi _{B}\circ \overline {\pi _{A}}\).
Proof
The proof is easy. Let \(\pi _{A}=\pi ^{(N)}_{k_{N}}\circ {\cdots } \circ \pi ^{(1)}_{k_{1}}\) and \(\pi _{B}=\pi ^{(N)}_{s_{N}}\circ {\cdots } \circ \pi ^{(1)}_{s_{1}}\) be two N-level permutations. Then it has
and
It is clear that \(\pi _{A}\circ \overline {\pi _{B}}=\pi _{B}\circ \overline {\pi _{A}}\). Thus it holds. □
Example 3
For N = 2,r = 2, let \(\pi _{A}=\pi ^{(2)}_{1}\circ \pi ^{(1)}_{2}\) and \(\pi _{B}=\pi ^{(2)}_{2}\circ \pi ^{(1)}_{1}\) be two 2-level permutations, then it has
and
It is clear that \(\pi _{A}\circ \overline {\pi _{B}}=\pi _{B}\circ \overline {\pi _{A}}\).
2.2 General Quantum SWAP Gates
In this subsection we introduce a quantum SWAP gate. The SWAP gate is seen as an important component in theory of quantum computation. For a n-qubit quantum systems |c1,⋯ ,cn〉, the general quantum SWAP gate in [22] will act as:
where a permutation π = (i1,⋯ ,in).
Let π be a permutation, then π = π1 ∘⋯ ∘ πm, where πi is also a transposition, 1 ≤ i ≤ n. Since every permutation can be written as the composition of transpositions. By (5), we have
For example, in 3-qubit system, SWAP(3,1,2)|c1,c2,c3〉 = SWAP[2,3]SWAP[1,2]|c1,c2,c3〉 = |c3,c1,c2〉. Thus, it directly fields the following Proposition 2.
Proposition 2
Let πA and πB be two N-level permutations, \(\overline {\pi _{A}}\) and \(\overline {\pi _{B}}\) are induction operation of πA and πB respectively, then \(SWAP_{\pi _{A}\circ \overline {\pi _{B}}}=SWAP_{\pi _{B}\circ \overline {\pi _{A}}}\) for n-qubit quantum system.
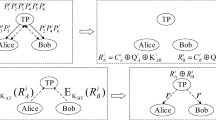
3 The Proposed Two-Party QPC Protocol
3.1 A Description of QPC Protocol
Alice and Bob are two parties who want to compare the equality of their secret messages with same bit-length, a,b ∈{0,1}∗, respectively. They agree that the two Bell states \(|\phi ^{0}\rangle =\frac {1}{\sqrt {2}}(|00\rangle +|11\rangle ), |\phi ^{1}\rangle =\frac {1}{\sqrt {2}}(|01\rangle +|10\rangle )\) represent the classical bits 0, 1, respectively. The proposed protocol can be depicted in steps as following.
Alice divides the secret message a into m groups, which are
If |Xm− 1|≠r2, Alice fills in the data alternately 0 and 1 after Xm− 1.
Bob does the same things for the secret message b and obtains
where a(i,j),b(i,j) ∈{0,1},i,j = 1,⋯ ,r2, as,bs ∈{0,1},s = 1,⋯ ,mr2 and r ∈ Z+.
- Step 1.:
-
Alice (Bob) selects two transpositions \(\pi ^{(1)}_{k_{1}}, \pi ^{(2)}_{k_{2}}(\pi ^{(1)}_{s_{1}}, \pi ^{(2)}_{s_{2}})\) in (4). Then Alice (Bob) computes
$$\overline{\pi_{A}}(X_{0})=\overline{\pi_{A}}(a_{(1,1)}, \cdots, a_{(1,r)}, \cdots, a_{(r,1)}, \cdots, a_{(r,r)})=(a_{\overline{\pi_{A}}(1)}, \cdots, a_{\overline{\pi_{A}}(r^{2})})$$$$ (\overline{\pi_{B}}(Y_{0})=\overline{\pi_{B}}(b_{(1,1)}, \cdots, b_{(1,r)}, \cdots, b_{(r,1)}, \cdots, b_{(r,r)})=(b_{\overline{\pi_{B}}(1)}, \cdots, b_{\overline{\pi_{B}}(r^{2})}))$$for first group X0(Y0), where \(\overline {\pi _{A}}=\pi ^{(1)}_{k_{1}}\circ \pi ^{(2)}_{k_{2}} (\overline {\pi _{B}}=\pi ^{(1)}_{s_{1}}\circ \pi ^{(2)}_{s_{2}} )\).
- Step 2.:
-
Alice (Bob) encodes each bit of \(\overline {\pi _{A}}(X_{0}) (\overline {\pi _{B}}(Y_{0}))\) and prepares r2 Bell states as initial states. Alice (Bob) records these initial states as
$$S_{A}=\{|\phi^{a_{\overline{\pi_{A}}(1)}}\rangle_{1}, \cdots, |\phi^{a_{\overline{\pi_{A}}(r^{2})}}\rangle_{r^{2}}\} ~~~~(S_{B}=\{|\phi^{b_{\overline{\pi_{B}}(1)}}\rangle_{1}, \cdots, |\phi^{b_{\overline{\pi_{B}}(r^{2})}}\rangle_{r^{2}}\}),$$where \(|\phi ^{a_{\overline {\pi _{A}}(i)}}\rangle _{i}, |\phi ^{b_{\overline {\pi _{B}}(i)}}\rangle _{i}\in \{|\phi ^{0}\rangle , |\phi ^{1}\rangle \}, i=1, \cdots , r^{2}\). Further, Alice (Bob) divides them into two ordered sequences \(S_{A_{1}}\) and \(S_{A_{2}} (S_{B_{1}}\) and \(S_{B_{2}})\) composed of the 1st and 2nd particles of each Bell state respectively, that is
$$ S_{A_{1}}=\{|\phi_{1}^{a_{\overline{\pi_{A}}(1)}}\rangle_{1}, \cdots, |\phi_{1}^{a_{\overline{\pi_{A}}(r^{2})}}\rangle_{r^{2}}\} ~~~~(S_{B_{1}}=\{|\phi_{1}^{b_{\overline{\pi_{B}}(1)}}\rangle_{1}, \cdots, |\phi_{1}^{b_{\overline{\pi_{B}}(r^{2})}}\rangle_{r^{2}}\}), $$$$ S_{A_{2}}=\{|\phi_{2}^{a_{\overline{\pi_{A}}(1)}}\rangle_{1}, \cdots, |\phi_{2}^{a_{\overline{\pi_{A}}(r^{2})}}\rangle_{r^{2}}\} ~~~~(S_{B_{2}}=\{|\phi_{2}^{b_{\overline{\pi_{B}}(1)}}\rangle_{1}, \cdots, |\phi_{2}^{b_{\overline{\pi_{B}}(r^{2})}}\rangle_{r^{2}}\}). $$ - Step 3.:
-
Alice (Bob) randomly prepares decoy photons \(\otimes {D^{A}_{j}} (\otimes {D^{B}_{j}})\), where \(|{D_{j}^{A}} \rangle \)\( (|{D^{B}_{j}}\rangle )\in \{|0\rangle , |1\rangle ,\)\((|0\rangle +|1\rangle )/\sqrt {2}, (|0\rangle -|1\rangle )/\sqrt {2}\} (j=1, 2, \cdots , k)\). Then Alice (Bob) randomly inserts \(\otimes {D^{A}_{j}} (\otimes {D^{B}_{j}})\) in \(S_{A_{1}}(S_{B_{1}})\) to form a new sequence \(S^{\prime }_{A_{1}}(S^{\prime }_{B_{1}})\), and sends it to Bob (Alice).
- Step 4.:
-
After confirming that Bob (Alice) has received the quantum sequence \(S^{\prime }_{A_{1}}(S^{\prime }_{B_{1}})\), Alice (Bob) informs the positions and the measurement bases of \(\otimes {D^{A}_{j}} (\otimes {D^{B}_{j}})\) to Bob (Alice). Subsequently, Bob (Alice) extracts the particles in \(\otimes {D^{A}_{j}} (\otimes {D^{B}_{j}})\) from \(S^{\prime }_{A_{1}}(S^{\prime }_{B_{1}})\), and gets the sequence \(S_{A_{1}}(S_{B_{1}})\). Thereafter, Alice and Bob can check the existence of an Eve by a predetermined threshold of error rate. If the error rate is limited in a predetermined threshold, there is no eve and the protocol continues. Otherwise, Alice and Bob abort the protocol and restart from Step 1.
- Step 5.:
-
Bob (Alice) performs quantum swapping gate \(SWAP_{\pi _{B}} (SWAP_{\pi _{A}})\) on quantum particle sequence \(S_{A_{1}}(S_{B_{1}})\) and obtains
$$ S^{\prime\prime}_{A_{1}} = \{|\phi_{1}^{a_{\overline{\pi_{A}}(1)}}\rangle_{\pi_{B}(1)}, \cdots, |\phi_{1}^{a_{\overline{\pi_{A}}(r^{2})}}\rangle_{\pi_{B}(r^{2})}\} ~~(S^{\prime\prime}_{B_{1}}\! = \{|\phi_{1}^{b_{\overline{\pi_{B}}(1)}}\rangle_{\pi_{A}(1)}, \cdots, |\phi_{1}^{b_{\overline{\pi_{B}}(r^{2})}}\rangle_{\pi_{A}(r^{2})}\}). $$ - Step 6.:
-
Bob (Alice) selects a binary random sequences \(e^{B}=({e^{B}_{1}}, {e^{B}_{2}}, \cdots , e^{B}_{r^{2}})\in \{0, 1\}^{r^{2}}\)\((e^{A}=({e^{A}_{1}}, {e^{A}_{2}}, \cdots , e^{A}_{r^{2}})\in \{0, 1\}^{r^{2}}\)). Bob (Alice) performs unitary operation U on quantum particle sequence \(S^{\prime \prime }_{A_{1}} (S^{\prime \prime }_{B_{1}})\) and obtains a new quantum particle sequence \(\widetilde {S}^{\prime \prime }_{A_{1}} (\widetilde {S}^{\prime \prime }_{B_{1}})\), where U = I if \({e^{B}_{i}}=0\)\(({e^{A}_{i}}=0)\) and U is X-gate if \({e^{B}_{i}}=1\)\(({e^{A}_{i}}=1)\).
- Step 7.:
-
Bob (Alice) randomly inserts \(\otimes D^{\prime A}_{j} (\otimes D^{\prime B}_{j})\) in \(\widetilde {S}^{\prime \prime }_{A_{1}}\) and \(S_{B_{2}} (\widetilde {S}^{\prime \prime }_{B_{1}}\) and \(S_{A_{2}})\) to form a new sequence \(S^{\prime \prime \prime }_{A_{1}}(S^{\prime \prime \prime }_{B_{1}})\) and \(S^{\prime }_{B_{2}} (S^{\prime }_{A_{2}})\), where \(|D^{\prime A}_{j} \rangle (|D^{\prime B}_{j}\rangle )\in \{|0\rangle , |1\rangle , (|0\rangle +|1\rangle )/\sqrt {2}, (|0\rangle -|1\rangle )/\sqrt {2}\} (j=1, 2, \cdots , k)\). Then Bob (Alice) sends sequences \(S^{\prime \prime \prime }_{A_{1}}(S^{\prime \prime \prime }_{B_{1}})\) and \(S^{\prime }_{B_{2}} (S^{\prime }_{A_{2}})\) to Alice (Bob).
- Step 8.:
-
Alice and Bob check the existence of an Eve just as Step 4 introduced, and obtains \(\widetilde {S}^{\prime \prime }_{A_{1}}, S_{B_{2}}\) and \(\widetilde {S}^{\prime \prime }_{B_{1}}, S_{A_{2}}\) respectively.
- Step 9.:
-
Bob (Alice) performs quantum swapping gate \(SWAP_{\pi _{B}} (SWAP_{\pi _{A}})\) on quantum particle sequence \(S_{A_{2}}(S_{B_{2}})\), and obtains
$$ S^{\prime\prime}_{A_{2}} = \{|\phi_{2}^{a_{\overline{\pi_{A}}(1)}}\rangle_{\pi_{B}(1)}, \cdots, |\phi_{2}^{a_{\overline{\pi_{A}}(r^{2})}}\rangle_{\pi_{B}(r^{2})}\} ~~(S^{\prime\prime}_{B_{2}}\! = \{|\phi_{2}^{b_{\overline{\pi_{B}}(1)}}\rangle_{\pi_{A}(1)}, \cdots, |\phi_{2}^{b_{\overline{\pi_{B}}(r^{2})}}\rangle_{\pi_{A}(r^{2})}\}). $$ - Step 10.:
-
Alice (Bob) obtains the sequence of classical results \(\{a^{A_{1}}_{1}\oplus {e^{B}_{1}}, \cdots , a^{A_{1}}_{r^{2}}\oplus e^{B}_{r^{2}}, b^{B_{2}}_{1}, \cdots , b^{B_{2}}_{r^{2}}\}, (\{b^{B_{1}}_{1}\oplus {e^{A}_{1}}, \cdots , b^{B_{1}}_{r^{2}}\oplus e^{A}_{r^{2}}, a^{A_{2}}_{1}, \cdots , a^{A_{2}}_{r^{2}}\})\) from quantum particles \(\widetilde {S}^{\prime \prime }_{A_{1}}S^{\prime \prime }_{B_{2}} (\widetilde {S}^{\prime \prime }_{B_{1}}S^{\prime \prime }_{A_{2}})\) after the |0〉,|1〉 basis measurement. Alice (Bob) computes the \({t^{A}_{i}}=a^{A_{1}}_{i}\oplus {e^{B}_{i}}\oplus b^{B_{2}}_{i}\oplus {e^{A}_{i}}\) (\({t^{B}_{i}}=b^{B_{1}}_{i}\oplus {e^{A}_{i}}\oplus a^{A_{2}}_{i}\oplus {e^{B}_{i}}\)), and obtains result \(t^{A}=\{{t^{A}_{i}}, i=1, \cdots , r^{2}\}\) (\(t^{B}=\{{t^{B}_{i}}, i=1, \cdots , r^{2}\}\)). Alice and Bob publish the tA and tB respectively. If tA = tB, then they announce the compared secret information X0 and Y0 are identical, and perform the protocol for the next group Xj and Yj,j = 1,⋯ ,m − 1. Otherwise, they announce the comparison are regarded as different.
3.2 An Example
Next, we taken an example when N = 2,r = 2. Suppose that Alice’s and Bob’s secret inputs are a = a(1,1)a(1,2)a(2,1)a(2,2) = 1001,b = b(1,1)b(1,2)b(2,1)b(2,2) = 1001.
- Step 1.:
-
Alice selects two integers k1 = 1,k2 = 2 and computes
$$ \begin{array}{@{}rcl@{}} \overline{\pi_{A}}(a_{(1, 1)}, a_{(1, 2)}, a_{(2, 1)}, a_{(2, 2)}) &=&\pi^{(1)}_{k_{1}}\circ\pi^{(2)}_{k_{2}}(a_{(1, 1)}, a_{(1, 2)}, a_{(2, 1)}, a_{(2, 2)})\\ &=&(a_{(2, 1)}, a_{(2, 2)}, a_{(1, 1)}, a_{(1, 2)})=0110. \end{array} $$Bob selects two integers s1 = 1,s2 = 1 and computes
$$ \begin{array}{@{}rcl@{}} \overline{\pi_{B}}(b_{(1, 1)}, b_{(1, 2)}, b_{(2, 1)}, b_{(2, 2)}) &=&\pi^{(1)}_{s_{1}}\circ\pi^{(2)}_{s_{2}}(b_{(1, 1)}, b_{(1, 2)}, b_{(2, 1)}, b_{(2, 2)})\\ &=&(a_{(2, 2)}, a_{(2, 1)}, a_{(1, 2)}, a_{(1, 1)})=1001. \end{array} $$ - Step 2.:
-
Alice (Bob) encodes each bit and prepares 4 Bell states as initial states. Alice (Bob) records these initial states as
$$S_{A}=\{|\phi^{0}\rangle_{1}, |\phi^{1}\rangle_{2}, |\phi^{1}\rangle_{3}, |\phi^{0}\rangle_{4}\} ~~~~(S_{B}=\{|\phi^{1}\rangle_{1}, |\phi^{0}\rangle_{2}, |\phi^{0}\rangle_{3}, |\phi^{1}\rangle_{4}\}.$$Further, Alice (Bob) divides them into two ordered sequences \(S_{A_{1}}\) and \(S_{A_{2}} (S_{B_{1}}\) and \(S_{B_{2}})\) composed of the 1st and 2nd particles of each Bell state respectively, that is
$$ S_{A_{1}}=\{|{\phi_{1}^{0}}\rangle_{1}, |{\phi_{1}^{1}}\rangle_{2}, |{\phi_{1}^{1}}\rangle_{3}, |{\phi_{1}^{0}}\rangle_{4}\} ~~~~(S_{B_{1}}=\{|{\phi_{1}^{1}}\rangle_{1}, |{\phi_{1}^{0}}\rangle_{2}, |{\phi_{1}^{0}}\rangle_{3}, |{\phi_{1}^{1}}\rangle_{4}\}), $$$$ S_{A_{2}}=\{|{\phi_{2}^{0}}\rangle_{1}, |{\phi_{2}^{1}}\rangle_{2}, |{\phi_{2}^{1}}\rangle_{3}, |{\phi_{2}^{0}}\rangle_{4}\} ~~~~(S_{B_{2}}=\{|{\phi_{1}^{1}}\rangle_{1}, |{\phi_{1}^{0}}\rangle_{2}, |{\phi_{2}^{0}}\rangle_{3}, |{\phi_{1}^{1}}\rangle_{4}\}). $$ - Step 3.:
-
Alice (Bob) randomly inserts decoy photons in \(S_{A_{1}}(S_{B_{1}})\) to form a new sequence \(S^{\prime }_{A_{1}}(S^{\prime }_{B_{1}})\), and sends it to Bob (Alice).
- Step 4.:
-
Alice and Bob check the presence of an Eve. There is no an Eve and the protocol continues. Otherwise, Alice and Bob abort the protocol and restart from Step 1.
- Step 5.:
-
Bob (Alice) performs quantum swapping gate \(SWAP_{\pi _{B}} (SWAP_{\pi _{A}})\) on quantum particle sequence \(S_{A_{1}}(S_{B_{1}})\) and obtains
$$ S^{\prime\prime}_{A_{1}}=\{|{\phi_{1}^{0}}\rangle_{4}, |{\phi_{1}^{1}}\rangle_{3}, |{\phi_{1}^{1}}\rangle_{2}, |{\phi_{1}^{0}}\rangle_{1}\} ~~~~(S^{\prime\prime}_{B_{1}}=\{|{\phi_{1}^{0}}\rangle_{3}, |{\phi_{1}^{1}}\rangle_{4}, |{\phi_{1}^{1}}\rangle_{1}, |{\phi_{1}^{0}}\rangle_{2}\}). $$ - Step 6.:
-
Bob (Alice) selects a binary random sequences eB = (0,0,1,1)(eA = (1,1,0,0)). Bob (Alice) performs unitary operation U on quantum particle sequence \(S^{\prime \prime }_{A_{1}} (S^{\prime \prime }_{B_{1}})\) and obtains a new quantum particle sequence \(\widetilde {S}^{\prime \prime }_{A_{1}} (\widetilde {S}^{\prime \prime }_{B_{1}})\), where U = I if \({e^{B}_{i}}=0\)\(({e^{A}_{i}}=0)\) and U is X-gate if \({e^{B}_{i}}=1\)\(({e^{A}_{i}}=1)\).
- Step 7.:
-
Alice (Bob) randomly inserts decoy photons in \(\widetilde {S}^{\prime \prime }_{A_{1}}\) and \(S_{B_{2}} (\widetilde {S}^{\prime \prime }_{B_{1}}\) and \(S_{A_{2}})\) to form a new sequence \(S^{\prime \prime \prime }_{A_{1}}(S^{\prime \prime \prime }_{B_{1}})\) and \(S^{\prime }_{B_{2}} (S^{\prime }_{A_{2}})\), and sends them to Bob (Alice).
- Step 8.:
-
Alice and Bob check the existence of an Eve just as Step 4 introduced, and obtains \(\widetilde {S}^{\prime \prime }_{A_{1}}, S_{B_{2}}\) and \(\widetilde {S}^{\prime \prime }_{B_{1}}, S_{A_{2}}\) respectively.
- Step 9.:
-
Bob (Alice) performs quantum swapping gate \(SWAP_{\pi _{B}} (SWAP_{\pi _{A}})\) on quantum particle sequence \(S_{A_{2}}(S_{B_{2}})\), and obtains
$$ S^{\prime\prime}_{A_{2}}=\{|{\phi_{2}^{0}}\rangle_{4}, |{\phi_{2}^{1}}\rangle_{3}, |{\phi_{2}^{1}}\rangle_{2}, |{\phi_{2}^{0}}\rangle_{1}\} ~~~~(S^{\prime\prime}_{B_{2}}=\{|{\phi_{2}^{0}}\rangle_{3}, |{\phi_{2}^{1}}\rangle_{4}, |{\phi_{2}^{1}}\rangle_{1}, |{\phi_{2}^{0}}\rangle_{2}\}). $$ - Step 10.:
-
Alice (Bob) obtains the sequence of classical results {0,1,0,1,1,1,0,0}, ({0,1,1,0,0,0,0,0) from quantum particles \(\widetilde {S}^{\prime \prime }_{A_{1}}S^{\prime \prime }_{B_{2}} (\widetilde {S}^{\prime \prime }_{B_{1}}S^{\prime \prime }_{A_{2}})\) after the |0〉,|1〉 basis measurement. Alice (Bob) computes the tA = {0,1,0,1} (tB = {0,1,0,1}). Alice and Bob publish the tA and tB respectively. The tA = tB, then they announce the compared secret information a and b are identical.
4 Analysis
4.1 Correctness
Alice and Bob use the N-level permutation to process secret information. They encode secret information and insert decoy states randomly. Then they send the first sequence of quantum particles to each other. Alice and Bob check the presence of an Eve. They use the quantum swapping gate \(SWAP_{\pi _{B}}\) and \(SWAP_{\pi _{A}}\) to process the sequence of quantum particles received separately. Before sending, Alice and Bob perform some unitary operations U on quantum particle sequences according to the random number sequences selected. Then they insert the decoy states in the sequence of quantum particles, and return to each other. After checking the presence of an Eve, they respectively obtain the sequence of quantum particles \(\widetilde {S}^{\prime \prime }_{A_{1}}, S_{B_{2}}\) and \(\widetilde {S}^{\prime \prime }_{B_{1}}, S_{A_{2}}\) from each other. Furthermore, they perform quantum swapping gate \(SWAP_{\pi _{A}}\) and \(SWAP_{\pi _{B}}\) on quantum particle sequence \(S_{B_{2}}\) and \(S_{A_{2}}\), separately. After the measurement, Alice and Bob obtain some corresponding encoding information respectively. That is, after performing 0, 1 basis measurement, Alice and Bob obtain the \(a_{i}^{A_{1}}\oplus {e^{B}_{i}}, b^{B_{2}}_{i}\) and \(b^{B_{1}}_{i}\oplus {e^{A}_{i}}, a^{A_{2}}_{i}\), respectively. Since Proposition 1, \(\pi _{B}\circ \overline {\pi _{A}}=\pi _{A}\circ \overline {\pi _{B}}\) holds. From Table 1 we observe that when the secret information is the same, that is ai = bi, there is always \({t^{A}_{i}}\oplus {t^{B}_{i}}=0\). Otherwise, when ai ≠ bi, there is always \({t^{A}_{i}}\oplus {t^{B}_{i}}=1\). So our protocol is correctness.
4.2 Outsider Attack
In presented protocol, Alice and Bob exchange compared secret information under insecure channels. In order to ensure the security of information, all parties publicly check for the existence of an Eve. There are two steps need to detect the presence of an Eve in presented protocol.
Since the Eve doesn’t know the measuring bases, and the positions of all decoy photons in \(S^{\prime }_{A_{1}}\) and \(S^{\prime }_{B_{1}}\). Eve will lead to an error to each decoy photon with a probability of \(\frac {1}{4}\). Thus, let n be the number of decoy photons, if n is large enough, then the probability of detecting Eve’s attack from the public discussion \(1-(\frac {3}{4})^{n}\) is close to 1. In addition, in step 8, Alice and Bob check the existence of an Eve just as Step 4 introduced. Hence, the presented protocol can withstand some known outsider attacks, such as entanglement-measure attack, measurement-resend attack, and intercept-resend [23,24,25,26,27].
4.3 Insider Attack
In general, dishonest participant can learn the secret of other party’s partial information without being detected. This congenital advantage for any participants should be limited such that it doesn’t threaten the security of the presented protocol.
The presented protocol is symmetric, Alice and Bob can execute the same attack strategy. Without loss of generality, we consider the case that Bob learns the Alice’s secret.
For comparing private information a, Alice divides the secret information into some groups, rearranges them according to a cyclic left-shift operation πA and encoding the new secret information using the Bell states on Step 1 and Step 2. At Step 3, Alice randomly inserts some decoy photons in \(S_{A_{1}}\) and sends the quantum sequences to Bob. After checking the existence of an Eve, Bob can obtain the sequences of quantum particles \(S_{A_{1}}\).
So Bob can distinguish between aj = 0 and aj = 1,j = πA(i) if Bob can distinguish between the two states \(\frac {|00\rangle +|11\rangle }{\sqrt {2}}\) and \(\frac {|01\rangle +|10\rangle }{\sqrt {2}}\). Bob needs to distinguish between the density matrices
and
It is clear that ρA = σA. Then Bob cann’t distinguish the Alice’s initial Bell states by measuring the first photon of the j-th state.
In Step 8, Bob can obtain the quantum particle sequence \(S_{A_{2}}\). But Bob only knows the πB and doesn’t know the πA. The probability of obtaining another correct πA is \(\frac {1}{r^{2}}\), that is the order \(\pi _{A}\overline {\pi _{B}}\) is secret for Bob. Through the particle sequences \(S_{A_{1}}\) and \(S_{A_{2}}\), Bob only guesses the correct Bell state or the corresponding message X0 with a probability of \(\frac {1}{r^{2}}\).
In addition, in Step 8, Bob obtains other quantum particle sequence \(\widetilde {S}^{\prime \prime }_{B_{1}}\). Bob doesn’t obtain Alice’s secret information. The reason is that Bob does not know random number sequence eA except eB. So Bob only guesses the correct random numbers with \(\frac {1}{2^{r^{2}}}\) successful probability. Furthermore, the presented protocol can resist the inside attacks.
4.4 Comparison
In this subsection, the comparisons of Lin et al.’s protocol [18], He’s protocol [19], and the proposed scheme is described in the following Table 2. The qubit efficiency η is defined as \(\eta =\frac {\eta _{c}}{\eta _{q}}\), where ηc denotes the classical bits that can be employed, and ηq denotes the total photons.
Lin et al. use Bell states to design their QPC protocol, in which two qubits can compare one bit of information. However, the qubit efficiency can be computed as 50%. In He’s protocol, single photon states are used to construct the QPC, in which one photons can compare one bit of information among two parties. Therefore, its qubit efficiency is 100%. Comparing these protocol, the presented protocol also uses the Bell states to construct the new QPC, It leads to the qubit efficiency of 50%.
Lin et al.’s and He’s scheme need more quantum devices such as quantum operations, and quantum measurement to perform the comparison. For Lin et al.’s and He’s scheme, both users have to perform one-to-one hash operation to encode the hash code of their information in advance, and encode each bit to the corresponding quantum states. In the proposed scheme, it does not require hash coding in advance.
In addition, in Lin et al.’s QPC, it need Bell-basis measurement to accomplish the comparison phase. In He’s scheme, it requires single photon measurements. In the proposed scheme, the two players only need to perform the {0,1}-basis measure to retrieve their own result of comparison. Thus, the proposed scheme is more efficient and practical.
5 Conclusion
In this paper, we described a protocol to compare the quantum secrets without a third party based on the Bell states and quantum SWAP gates. The proposed protocol has adopted quantum transmission strategy and the decoy state photons to prevent various types of eve attacks. In addition, Bob (Alice) only knows the πB(πA), and doesn’t know the πA(πB). Thus they have only the same order of information arrangement, but the \(\pi _{A}\overline {\pi _{B}}=\overline {\pi _{A}}\pi _{B}\) is secret for two parties. The participants’ encoded secrets are protected by the entanglement of Bell states. So, it provides security for inside attackers. In summary, through the security analysis, the presented protocol is demonstrated to be secure against outsider attack and insider attack.
References
Zhang, W., Ding, D.S., Sheng, Y.B., et al.: Quantum secure direct communication with quantum memory. Phys. Rev. Lett. 118(22), 220501 (2017)
He, Y.F., Ma, W. P.: Three-party quantum secure direct communication against collective noise. Quantum Inf. Process 16(10), 252 (2017)
Xu, T.T., Li, Z.H., Bai, C.M., et al.: A new improving quantum secret sharing scheme. Int. J. Theor. Phys. 56, 1–10 (2017)
Bai, C.M., Li, Z.H., Xu, T.T., et al.: Quantum secret sharing using the d-dimensional GHZ state. Quantum Inf. Process 16(3), 59 (2017)
Wu, W.Q., Cai, Q.Y., Zhang, H.G., et al.: Quantum public key cryptosystem based on bell states. Int. J. Theor. Phys. 56(11), 3431–3440 (2017)
Wu, W.Q., Cai, Q.Y., Zhang, H.G., et al.: Bit-oriented quantum public-key cryptosystem based on bell states. Int. J. Theor. Phys. 57(12), 1–11 (2018)
Yang, Y.G., Cao, W.F., Wen, Q.Y.: Secure quantum private comparison. Physica Scripta 80(6), 065002 (2009)
Ye, T.Y., Ji, Z.X.: Two-party quantum private comparison with five-qubit entangled states. Int. J. Theor. Phys. 56(5), 1517–1529 (2017)
Pan, H.M.: Quantum private comparison based on x-type entangled states. Int. J. Theor. Phys. 56(10), 3340–3347 (2017)
Ji, Z.X., Ye, T.Y.: Multi-party quantum private comparison based on the entanglement swapping of d-level cat states and d-level Bell states. Quantum Inf. Process 16(7), 177 (2017)
Xu, L., Zhao, Z.: A robust and efficient quantum private comparison of equality based on the entangled swapping of GHZ-like state and χ+ state. Int. J. Theor. Phys. 56(8), 2671–2685 (2017)
Xu, L., Zhao, Z.: Quantum private comparison protocol based on the entanglement swapping between (χ+) state and W-Class state. Quantum Inf. Process. 16(12), 302 (2017)
Zhou, M.K.: Improvements of quantum private comparison protocol based on cluster states. Int. J. Theo. Phys. 2, 1–6 (2017)
Wu, W.Q., Cai, Q.Y, Wu, S.M., et al.: Cryptanalysis and improvement of Ye et al’s quantum private comparison protocol. Int. J. Theor. Phys. 58(6), 1892–1900 (2019)
Hung, S.M., Hwang, S.L., Hwang, T., et al.: Multiparty quantum private comparison with almost dishonest third parties for strangers. Quantum Inf. Process. 16(2), 36 (2017)
Wu, W.Q., Cai, Q.Y., Wu, S.M., et al.: Cryptanalysis of He’s quantum private comparison protocol and a new protocol. Int. J. Quantum Inf. 17(3), 1950026 (2019)
Lo, H.K.: Insecurity of quantum secure computations. Phys. Rev. A 56(2), 1154–1162 (1998)
Lin, J., Yang, C.W., Hwang, T.: Quantum private comparison of equality protocol without a third party. Quantum Inf. Process. 13(2), 157 (2013)
He, G.P.: Quantum private comparison protocol without a third party. Int. J. Quantum Inf. 15(2), 1750014 (2016)
He, G.P: Device-independent quantum private comparison protocol without a third party. arXiv:1710.05051
Gockenbach, M.S.: Finite-dimensional linear algebra. CRC Press, Boca Raton (2010)
Wilmott, C., Wild, P.: On a generalized quantum SWAP gate. Int. J. Quantum Inf. 10(03), 1250034 (2008)
Wang, T.Y., Wen, Q.Y., Zhu, F. C.: Cryptanalysis of multiparty quantum secret sharing with Bell states and Bell measurements. Optics Communications 284(6), 1711–1713 (2011)
Wang, W., Cao, H.: An Improved Multiparty Quantum Secret Sharing with Bell States and Bell Measurement. Int. J. Theor. Phys. 52(6), 2099–2111 (2013)
Lin, J., Hwang, T.: An enhancement on Shi others.’s multiparty quantum secret sharing protocol. Opt. Commun. 284(5), 1468–1471 (2011)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 11(2), 373–384 (2012)
Zhou, M.K.: Improvements of quantum private comparison protocol based on cluster states. Int. J. Theor. Phys. 2, 1–6 (2017)
Acknowledgments
The authors are supported by the Natural Science Foundation of HeBei Province Nos. F2017201199.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wu, W., Ma, X. Quantum Private Comparison Protocol without a Third Party. Int J Theor Phys 59, 1854–1865 (2020). https://doi.org/10.1007/s10773-020-04453-w
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-020-04453-w