Abstract
By introducing a sinusoidal function into a three-dimensional map, a hyperchaotic map with three positive Lyapunov exponents is derived. The map has two amplitude controllers, a total controller, and a partial controller. The hyperchaotic map shares a unique structure of two-leaf and three-leaf attractors under united Lyapunov exponents. Furthermore, homogenous multistability is found in the 3-D map, where the initial data determine the attractor structure combined with the distance between any two leaves. Experimental hardware based on STM32 is built to prove the numerical findings. The hyperchaotic map is introduced for color image encryption. The analysis of key space, histogram, information entropy, correlation, and antinoise infection shows its powerful performance in encryption and security.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Chaos plays an important role in image encryption [1,2,3,4,5], secure communication [6,7,8,9], computer engineering [10], and even other fields [11,12,13,14]. The discrete chaotic map shows its potential power as a continuous chaotic system. Amplitude control and polarity adjustment of the chaotic sequence obtain much flexibility for chaos-based applications and therefore introduce much more value in information engineering [15,16,17,18,19]. Although the amplitude and offset control of continuous chaotic systems have been systematically explored and reported [20, 21], the geometric control of discrete chaotic maps is still in the beginning stages. The nonlinearity of the trigonometric function leaves a chance for chaos producing [22], but it also increases the difficulty of amplitude control and poses a great risk for multistability [23,24,25,26,27]. It is of great theoretical significance and engineering values to design chaotic maps based on trigonometric function nonlinearity and study their controllability. A couple of 2-D chaotic maps with trigonometric functions have been studied [28,29,30,31], with abundant dynamics for multistability. However, we cannot find any single knob for amplitude control. Amplitude control along with offset boosting seems to be well addressed in continuous chaotic systems [32], but all chaotic systems ignore the nonlinearity of the trigonometric function. Continuous chaotic systems have been investigated, mainly focusing on polarity balance and attractor self-reproduction [33, 34], generalized synchronization [35, 36], or attractor growing [37, 38] rather than amplitude control. Amplitude control in chaotic maps seems much more difficult to design since the coefficient for variable rescaling has a broader distribution on the right side of the map; therefore, the control of chaotic maps has not received enough attention in the field of nonlinear dynamics. Additionally, homogenous multistability plays an important role in amplitude control, where an initial condition can be selected for easy variable rescaling.
Aiming to design a chaotic map with amplitude control and rich dynamics, in this paper, a three-dimensional (3-D) hyperchaotic map is created by resorting to sinusoidal feedback. As a result, the map is gifted with two independent knobs for total and partial amplitude control. In Sect. 2, the hyperchaotic model is constructed, and the dynamic development is discussed, including fixed points and bifurcation analysis. In Sect. 3, the principle of amplitude control is explained. In Sect. 4, the special homogenous multistability is demonstrated, where two-leaf and three-leaf attractors are selected by the initial condition under a set of unified Lyapunov exponents. In Sect. 5, a digital platform based on STM32 is set up for experimental verification. In Sect. 6, the hyperchaotic sequence is applied to image encryption, where the performance of encryption affected by amplitude control and homogenous multistability is exhaustively explored. The conclusions are presented in the last section.
2 A 3-D hyperchaotic map and its basic dynamics
2.1 Map model
Based on the continuous jerk system, a new 3-D discrete chaotic map is derived by introducing a sinusoidal function,
where xn, yn, zn (n = 0, 1, 2, …) are discrete sequences, and map parameters a, b, c are not equal to 0. The fixed points S = (x*, y*, z*) of map (1) is solved by Eq. (2),
Therefore, the fixed points are,
where m is an integer.
When a = 0.9, b = 1, and c = − 2, the Jacobian matrix of the discrete map at the fixed point (x *, y *, z *) = (− 3mπ/2, mπ, mπ) (m = 0,1,2, …) can be described as
The Jacobian characteristic equation satisfies λ3 = 1+2.7mπcos(mπ) (m = 0, 1, 2, …). For m = 0, 1, 2…, |1 + 2.7mπcos(mπ)| ≥ 1, so |λ1,2,3| < 1, it cannot be satisfied at the same time. The map has unstable fixed points.
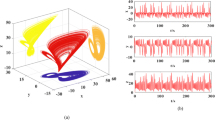
When a = 0.9, b = , c = − 2, and IC = (− 0.1, − 0.1, 0.1), map (1) exhibits hyperchaos with three positive Lyapunov exponents, LE1 = 0.095, LE2 = 0.057, and LE3 = 0.011. The corresponding hyperchaotic sequences and attractors are shown in Fig. 1.
Hyperchaotic sequences and attractor of map (1) with a = 0.9, b = 1, c = − 2, IC = (− 0.1, − 0.1, 0.1): a x(n), b y(n), c z(n), and d phase portrait in the x–y plane
2.2 Bifurcation analysis
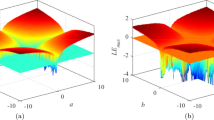
For map (1) with b = 1 and c = − 2, IC = (− 0.1, − 0.1, 0.1), and a varies in [0.85, 0.95], the dynamical behavior can be indicated by the Lyapunov exponent spectrum and corresponding bifurcation as displayed in Fig. 2. When a ∈ [0.85, 0.862] and a = 0.95, all Lyapunov exponents are negative, and the map is periodic. The typical x–y plane phase portraits are shown in Fig. 3a, d. When a ∈ [0.863, 0.868], map (1) has one positive Lyapunov exponent showing its chaotic state. The typical x–y plane phase portraits are shown in Fig. 3b. When a ∈ [0.9, 0.94] and a ∈ [1, 1.02], three Lyapunov exponents are all positive indicating that map (1) is hyperchaotic, corresponding phase portraits are demonstrated in Fig. 3c (Table 1).
Dynamical analysis of map (1) when b = 1, c = − 2, and IC = (− 0.1, − 0.1, 0.1): a Lyapunov exponent spectrum and b bifurcation evolvement
Typical phase portraits of map (1) with b = 1, c = − 2, IC = (− 0.1, − 0.1, 0.1) under given parameters: a a = 0.86, b a = 0.866, c a = 0.9, and d a = 0.95
3 Amplitude control analysis
3.1 Total amplitude control
Theorem 1
In map (1), b is a total amplitude controller.
Proof 1
Let un+1 = xn+1/b, vn+1 = yn+1/b and wn+1 = zn+1/b, the resulting map is.
which is identical to Eq. (1) with b = 1. Therefore, the parameter b adjusts the amplitude of all sequences of x, y, and z according to 1/b, which means that b is a total amplitude controller.
Here the parameter b controls the amplitude of all variables, and therefore b is a non-bifurcation parameter, as shown in Fig. 4, the attractor projection in all plane is rescaled by b in inverse proportion. In map (1), a = 0.9, c = − 2, and IC = (− 0.1, − 0.1, 0.1).
Rescaled phase portraits of map (1) with a = 0.9, c = − 2, and IC = (− 0.1, − 0.1, 0.1), where parameter b takes different values: a x–y plane and b y–z plane
Further verification can be seen in Fig. 5, where the averages of the absolute values of x, y, and z decrease with the parameter b but almost without revising the Lyapunov exponents. Unrevised Lyapunov exponents prove that the frequency of the sequence in map (1) remains independent with the parameter b.
Amplitude control in map (1) with a = 0.9, c = − 2, and IC = (− 0.1, − 0.1, 0.1): a almost invariable Lyapunov exponents, b bifurcation diagram, and c average absolute value of the sequences
3.2 Partial amplitude control
Theorem 2
The c in map (1) is a partial amplitude controller.
Proof 2
Let un+1 = xn+1/c, vn+1 = yn+1, and wn+1 = zn+1 the resulting map is.
Therefore, the parameter c controls the amplitude of the sequence of x according to 1/c without changing the other two series of y and z. Therefore, parameter c is a non-bifurcation partial amplitude controller for the variable x.
As shown in Fig. 6b, the amplitude of the x signal is controlled under different c. When c = − 2, the amplitude of x is larger, and when c = − 20, the amplitude is greatly reduced. Further verification can be seen in Fig. 6c, where the average of the |x(n)| increases with parameter c but almost without revising the Lyapunov exponents. This also further proves that the frequency of the sequence in map (1) is not affected by parameter c.
Amplitude control in map (1) with a = 0.9, b = 1, and IC = (− 0.1, − 0.1, 0.1): a Lyapunov exponents spectrum, b bifurcation diagram of x(n), c average value of |x(n)|, and d rescaled phase portraits under different c
4 Homogeneous multistability
Different initial conditions in chaotic systems may lead to different attractors with the same shape (sometimes with different amplitudes and/or frequencies or offsets). This special multistability is defined as homogeneous multistability.
To show the complex dynamics of map (1) with infinitely many attractors, a bifurcation diagram under the initial value is plotted in Fig. 7 where a = 0.9, b = 1, c = − 1, and IC = (− 1, y0, 1). It proves that the map displays homogeneous multistability indicated by almost unchanged Lyapunov exponents and gap-enlarged bifurcation.
Dynamical transition controlled by the initial condition of map (1) with a = 0.9, b = 1, c = − 1, and IC = (− 1, y0, 1): a Lyapunov exponents and b bifurcation diagram
Set to a = 0.9, b = 1, c = − 1, and IC = (− 1, y0, 1) in map (1), and rescaled coexisting two-leaf and three-leaf attractors are plotted in Fig. 8. Map (1) has infinite coexisting attractors with unified Lyapunov exponents.
Rescaled coexisting two-leaf and three-leaf attractors of map (1) with a = 0.9, b = 1, c = − 1, IC = (− 1, y0, 1) under different initial conditions of y0
The dynamical behavior can be further observed by setting a = 0.9, b = 1, c = − 1, and IC = (− 1, − 1, z0), corresponding Lyapunov exponent spectrum and bifurcation diagram of the signal y are plotted in Fig. 9. Rescaled coexisting two-leaf and three-leaf hyperchaotic attractors share the same set of unified Lyapunov exponents. Moreover, the discrete periodic points are scattered between any two hyperchaotic states. To the best of our knowledge, this is a brand new phenomenon in nonlinear mapping. Also with the increase of z0 in the 3-D map, two-leaf and three-leaf attractors with different leaf distances are born. More strikingly, the initial data modifies the distance between any two leaves in a positive correlation. Figure 10 shows the typical coexisting phase portraits of map (1) accordingly. Note that the homogeneous multistability found here shows the characteristic of coexisting attractors with enlarged distance, which is close to the regime of megamultistability [39, 40].
Dynamical development of map (1) with a = 0.9, b = 1, c = − 1, and IC = (− 1, − 1, z0): a Lyapunov exponent spectrum and b rescaled bifurcation
Rescaled coexisting two-leaf and three-leaf attractors of map (1) with a = 0.9, b = 1, c = − 1, IC = (− 1, − 1, z0) under different initial conditions of z
5 Hardware implementation based on STM32
An experimental test can be given for further demonstration. In this work, the MCU development suite was used for experimental exploration. Here the electronic platform and components mainly include STM32F103 MCU and TLV5618, 12-bit DAC modules. To meet the requirement of the precision, here we select ∆T = 1 and the TLV5618 is applied for giving two separate sequences. The phase trajectories of map (1) are captured in the oscilloscope which is displayed in Fig. 11. The experimental process is shown in Fig. 12.
Phase portraits of map (1) displayed in the oscilloscope when a = 0.9, b = 1, c = − 1, and IC = (− 1, y0, 1): a y0 = 1 + 3π and b y0 = 1
6 Application of the hyperchaotic map in image encryption
Hyperchaotic systems provide a larger key space and higher complexity and therefore become more applicable for encryption and secure communication. In the following, the image encryption is studied based on the above-proposed hyperchaotic map. Furthermore, the amplitude control and coexisting two-leaf or three-leaf hyperchaotic sequences are applied as shown later that in fact the information entropy of the three-channel encrypted image does not change dramatically.
6.1 Algorithm design
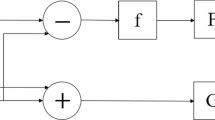
Here, DNA coding is applied in hyperchaotic mapping (1) for image encryption. Compared with other algorithms, the encryption key space becomes larger with stronger sensitivity, showing robustness to attacks. The main encryption flowchart is shown in Fig. 13: First, the image is encrypted by a logistic map, then encrypted by the hyperchaotic sequence combining with the DNA coding.
The specific encryption process can be described as follows:
-
Step 1: Add the horizontal and vertical pixels with M0 = 0 and N0 = 0, so that they are divisible by the block size S.
-
Step 2: Given the initial condition of x0 and the variable μ of the logistic map, discrete signals {Pi}(i = 2001, 2002, …, M × N + 2000) with the length of M × N + 2000 is obtained.
-
Step 3: All the numbers in the discrete signals are transformed to [0, 255] and then randomly formed into a 2-D matrix R of M × N.
-
Step 4: Set S = 4, and correspondingly the size of each block of the matrix R and the image are S × S.
-
Step 5: Given the initial conditions X0, Y0, Z0 and the values of a and b in map (1), three discrete time series {xi}, {yi}, and {zi} can be obtained (i = 4002, 4003, …, 4001 + M/S + N/S).
-
Step 6: The DNA coding pattern of each image matrix and a stochastic matrix is determined by the sequences {xi} and {yi}, respectively. Taking image matrix as an example, this process of encoding mode is defined as follows,
$$ x_{i} = \bmod (round(x_{i} \times 10^{4} ),8) + 1 $$(7)Transform the grayscale values of all image elements into the binary numbers and get DNA coding pattern according to the value of xi.
-
Step 7: DNA coding between random matrix and image matrix according to {zi}. The conversion of {zi} is as follows,
$$ z_{i} = \bmod (round(z_{i} \times 10^{4} ),4) $$(8)when zi = 0, the random matrix block and the corresponding elements in the image matrix block execute DNA addition, and when zi = 1, subtraction, zi = 2, exclusive or (XOR), and zi = 3, the equivalence gate (XNOR) operation.
-
Step 8: The encryption performance can be optimized by adding a diffusion algorithm. {zi} also determines the relationship between two adjacent image blocks after encryption. In the case of zi = 0, the encryption results ci can be expressed:
$$ c_{i} = c_{{i - 1}} + I_{i} + R_{i} $$(9)The process of decryption and encryption are inverse to each other. The operation mode of random matrix and DNA encoding can be obtained by the keys shown below.
6.2 Chaotic encryption with DNA coding
In the following, we test with a standard RGB image, as displayed in Fig. 14. The initial value x0 is 0.5475 and the parameter μ of Logistic map is 3.999. Set the parameters of hyperchaotic map (1) as a = 0.9, b = 1, c = − 1 along with the initial condition: X0 = − 1, Y0 = − 1, Z0 = 1, and therefore, the coding rule of DNA is determined randomly by the corresponding hyperchaotic sequence. As shown in Table 2, the selected keys of M0 and N0 during the encryption process are given; k1 and k2 are the average gray levels of the B channel and G channel in the unencrypted image, respectively. The encrypted image is shown in Fig. 14b, where the information disappears and shows nothing. Figure 14c shows the decrypted image which is the same as the unencrypted image.
6.3 Safety performance analysis
Security is the essential requirement of the encryption system. Generally, the encryption system requires a large key space, a reversible encryption process, and strong anti-attack property. Detailed analysis of the hyperchaotic encryption algorithm is given from the following five aspects.
6.3.1 Key space analysis
An excellent encryption method typically obtains its high performance by its large key space in order to against strong attack. In the above encryption algorithm, the initial conditions of the 3-D hyperchaotic map are applied as the keys, where the accuracy reaches 10–16, and therefore the key space is 10160. Furthermore, the logistic chaotic map is used for the key generation. Its initial value and parameter are also be introduced as a part of the key. By this means, the key space is enlarged for resisting attacks more effectively.
6.3.2 Histogram analysis
The R, G, B components are extracted from the original color image and its encrypted image, and their histograms are shown in Fig. 15. It can be easily observed from Fig. 15 that the histograms of the R, G, B are completely changed when they are encrypted.
6.3.3 Information entropy analysis
The uncertainty of image information can be analyzed by information entropy. The size of information entropy is proportional to the strength of randomness. To ensure the random distribution of pixel values, we use the following method,
where N is the number of gray levels, xi is a gray level of the image, and P(xi) is the frequency of the grayscale. Generally speaking, the pixel value of a completely random gray image is scattered between [0, 255], p(xi) = 1/256, i ∈ [0, 255], and the entropy is computed to be of 8 bits. Therefore, for the information entropy of the encrypted image, the value closer to 8 wins the better encoding performance. The information entropy of the three channels of the image before and after encryption is displayed in Table 3. The information entropy calculated by our method is higher than that in reference [8] indicating better image encryption performance.
Figure 16 shows the information entropy of the encrypted image of the amplitude-controllable map under different scales. Figure 17 shows the information entropy of three channels of encrypted images under multistable hyperchaotic sequences.
Information entropy of encrypted image in the R, G, and B channels by the sequences from map (1) with a = 0.9, b = 1, and IC = (− 1, − 1, 1)
Information entropy of the three-channel encrypted image by the multistable sequences from map (1) with a = 0.9, b = 1, c = − 1 and IC = (− 1, y0, 1)
6.3.4 Correlation analysis of images before and after encryption
The degree of correlation between adjacent pixels is directly proportional to its correlation coefficient, and security is inversely proportional. To calculate the correlation between the pixels next to each other of the image before and after encryption, N pairs of adjacent pixels are stochastically picked to analyze in vertical, horizontal, and diagonal directions.
where cov(x, y) is the correlation function and D(x) means square error. Table 4 shows that all the pixels of the encrypted image are distributed with high dispersion.
6.3.5 Analysis of resistance to noise
In the application of communication engineering, encrypted image will be inevitably disturbed in the channel. The most common disturb is the salt-and-pepper noise. Figure 18 shows the decrypted image in the R channel with different intensities of salt-and-pepper noise. Although there is some distortion in the decrypted image, it does not affect the access to valid information.
7 Conclusion
In this paper, a class of three-dimensional maps with homogenous multistability and amplitude control is proposed. A set of united positive Lyapunov exponents is well maintained in attractors with two-leaf and three-leaf even when they stand at different distances. The complex dynamical properties of the 3-D map are studied by Lyapunov exponents and bifurcation diagrams. The proposed hyperchaotic map can be freely controlled in one dimension or all three dimensions by a single coefficient. These two isolated amplitude controllers provide a quick passage for hyperchaotic sequence rescaling, which is generally a great challenge for typical chaotic systems.
Furthermore, the newly found hyperchaotic map with a sinusoidal function has an infinite number of coexisting attractors with united Lyapunov exponents, in which the special phenomenon called homogeneous multistability is found. Experimental results verify the findings from the numerical simulations. A typical application of image encryption is analyzed in detail. Applying the hyperchaotic sequence generated by the map, a color image can be easily encrypted and decrypted in the key space. The lack of correlation between the histograms and the pixels next to each other proves that the hyperchaotic map shows high performance for image encryption.
Data availability
The data that support the findings of this study are available from the corresponding author upon reasonable request.
References
Chen, X., Qian, S., Yu, F., Zhang, Z., Shen, H., Huang, Y., Cai, S., Deng, Z., L, Y., Du, S. : Pseudorandom number generator based on three kinds of four-wing memristive hyperchaotic system and its application in image encryption. Complexity 2020, 1–17 (2020)
Peng, G., Min, F.: Multistability analysis, circuit implementations and application in image encryption of a novel memristive chaotic circuit. Nonlinear Dyn. 90(3), 1607–1625 (2017)
Liu, Z., Xia, T., Wang, J.: Image encryption technique based on new two-dimensional fractional-order discrete chaotic map and Menezes–Vanstone elliptic curve cryptosystem. Chin. Phys. B 27(3), 030502 (2018)
Deng, J., Zhou, M., Wang, C., Wang, S., Xu, C.: Image segmentation encryption algorithm with chaotic sequence generation participated by cipher and multi-feedback loops. Multimed. Tools Appl. 80, 13821–13840 (2021)
Zeng, J., Wang, C.: A novel hyperchaotic image encryption system based on particle swarm optimization algorithm and cellular automata. Secur. Commun. Netw. 2021(5), 1–15 (2021)
Cheng, G., Wang, C., Chen, H.: A novel color image encryption algorithm based on hyperchaotic system and permutation-diffusion architecture. Int. J. Bifurc. Chaos 29(9), 1950115 (2019)
Gan, Z.H., Chai, X.L., Han, D.J., Chen, Y.R.: A chaotic image encryption algorithm based on 3-D bit-plane permutation. Neural Comput. Appl. 31(11), 7111–7130 (2019)
Chai, X., Fu, X., Gan, Z., Lu, Y., Chen, Y.: A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process. 155, 44–62 (2019)
Shi, Z., Bi, S., Zhang, H., Lu, R., Shen, X.: Improved auxiliary particle filter-based synchronization of chaotic Colpitts circuit and its application to secure communication. Wirel. Commun. Mob. Comput. 15(10), 1456–1470 (2015)
Min, F., Li, C., Zhang, L., Li, C.: Initial value-related dynamical analysis of the memristor-based system with reduced dimensions and its chaotic synchronization via adaptive sliding mode control method. Chin. J. Phys. 58, 117–131 (2019)
Liu, J., Liu, S., Yuan, C.: Adaptive complex modified projective synchronization of complex chaotic (hyperchaotic) systems with uncertain complex parameters. Nonlinear Dyn. 79(2), 1035–1047 (2015)
Liu, J., Liu, S., Sprott, J.C.: Adaptive complex modified hybrid function projective synchronization of different dimensional complex chaos with uncertain complex parameters. Nonlinear Dyn. 83(1), 1109–1121 (2016)
Liu, T., Yan, H., Banerjee, S., Mou, J.: A fractional-order chaotic system with hidden attractor and self-excited attractor and its DSP implementation. Chaos Solitons Fractals 145, 110791 (2021)
Liu, T., Banerjee, S., Yan, H., Mou, J.: Dynamical analysis of the improper fractional-order 2D-SCLMM and its DSP implementation. Eur. Phys. J. Plus 136(5), 1–17 (2021)
Zhang, L.P., Liu, Y., Wei, Z.C., Jiang, H.B., Bi, Q.S.: A novel class of two-dimensional chaotic maps with infinitely many coexisting attractors. Chin. Phys. B 29(6), 060501 (2020)
Bao, B.C., Li, H.Z., Zhu, L., Zhang, X., Chen, M.: Initial-switched boosting bifurcations in 2D hyperchaotic map. Chaos 30(3), 033107 (2020)
Yu, F., Qian, S., Chen, X., Huang, Y., Cai, S., Jin, J., Du, S.: Chaos-based engineering applications with a 6D memristive multistable hyperchaotic system and a 2D SF-SIMM hyperchaotic map. Complexity 2021(1), 1–21 (2021)
Li, C., Sprott, J.C.: Finding coexisting attractors using amplitude control. Nonlinear Dyn. 78(3), 2059–2064 (2014)
Li, C., Sprott, J.C., Akgul, A., Iu, H.H., Zhao, Y.: A new chaotic oscillator with free control. Chaos 27(8), 083101 (2017)
Li, C., Wang, X., Chen, G.: Diagnosing multistability by offset boosting. Nonlinear Dyn. 90(2), 1335–1341 (2017)
Li, C., Sprott, J.C.: Amplitude control approach for chaotic signals. Nonlinear Dyn. 73, 1335–1341 (2013)
Li, H., Bao, H., Zhu, L., Bao, B., Chen, M.: Extreme multistability in simple area-preserving map. IEEE Access. 8, 175972–175980 (2020)
Pisarchik, A.N., Feudel, U.: Control of multistability. Phys. Rep. 540(4), 167–218 (2014)
Han, X., Xia, F., Zhang, C., Yu, Y.: Origin of mixed-mode oscillations through speed escape of attractors in a Rayleigh equation with multiple-frequency excitations. Nonlinear Dyn. 88(4), 2693–2703 (2017)
Zhou, W., Wang, G., Shen, Y., Yuan, F., Yu, S.: Hidden coexisting attractors in a chaotic system without equilibrium point. Int. J. Bifurc. Chaos 28(10), 1830033 (2018)
Pham, V.T., Volos, C., Jafari, S., Kapitaniak, T.: Coexistence of hidden chaotic attractors in a novel no-equilibrium system. Nonlinear Dyn. 87(3), 2001–2010 (2017)
Ojoniyi, O.S., Njah, A.N.: A 5D hyperchaotic Sprott B system with coexisting hidden attractors. Chaos Solitons Fractals 87, 172–181 (2016)
Xu, L., Li, Z., Li, J., Hua, W.: A novel bit-level image encryption algorithm based on chaotic maps. Opt. Lasers Eng. 78, 17–25 (2016)
Bao, H., Hua, Z., Wang, N., Zhu, L., Chen, M., Bao, B.: Initials-boosted coexisting chaos in a 2-D sine map and its hardware implementation. IEEE Trans. Ind. Inform. 17(2), 1132–1140 (2020)
Hadjabi, F., Ouannas, A., Shawagfeh, N., Khennaoui, A.A., Grassi, G.: On two-dimensional fractional chaotic maps with symmetries. Symmetry 12(5), 756 (2020)
Huang, H., He, Y., Yang, S., Ye, R.: Chaotic image encryption based on bidimensional empirical mode decomposition and double random phase encoding. IET Image Proc. 79(37), 28065–28078 (2020)
Zhang, S., Zeng, Y., Li, Z., Zhou, C.: Hidden extreme multistability, antimonotonicity and offset boosting control in a novel fractional-order hyperchaotic system without equilibrium. Int. J. Bifurc. Chaos 28(13), 1850167 (2018)
Li, C., Sun, J., Lu, T., Sprott, J.C., Liu, Z.: Polarity balance for attractor self-reproducing. Int. J. Bifurc. Chaos 30(6), 063144 (2020)
Yuan, F., Jin, Y., Li, Y.: Self-reproducing chaos and bursting oscillation analysis in a meminductor-based conservative system. Int. J. Nonlinear Science. Chaos 30(5), 053127 (2020)
Liu, J., Chen, G., Zhao, X.: Generalized synchronization and parameters identification of different-dimensional chaotic systems in the complex field. Fractals 29(4), 1–13 (2021)
Zhao, X., Liu, J., Mou, J., Ma, C., Yang, F.: Characteristics of a laser system in complex field and its complex self-synchronization. Eur. Phys. J. Plus 135(6), 1–17 (2020)
Gu, J., Li, C., Chen, Y., Iu, H.H., Lei, T.: A conditional symmetric memristive system with infinitely many chaotic attractors. IEEE Access 8, 12394–12401 (2020)
Kuptsov, P.V., Kuznetsov, S.P.: Route to hyperbolic hyperchaos in a nonautonomous time-delay system. Nonlinear Sci. Chaos 30(11), 113113 (2020)
Leutcho, G.D., Khalaf, A.J.M., Njitacke Tabekoueng, Z., Fozin, T.F., Kengne, J., Jafari, S., Hussain, I.: A new oscillator with mega-stability and its Hamilton energy: infinite coexisting hidden and self-excited attractors. Chaos 30(3), 033112 (2020)
Sun, J., Li, C., Lu, T., Akgul, A., Min, F.: A memristive chaotic system with hypermultistability and its application in image encryption. IEEE Access 8, 139289–139298 (2020)
Acknowledgements
This work was supported financially by the National Natural Science Foundation of China (Grant No.: 61871230), the Natural Science Foundation of Jiangsu Province (Grant No.: BK20181410), and the Provincial Key Training Programs of Innovation and Entrepreneurship for Undergraduates (Grant No.: 201910300053Z). We thank Dr. Jun Mou for his enlightening suggestion.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
We declare that we have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhou, X., Li, C., Li, Y. et al. An amplitude-controllable 3-D hyperchaotic map with homogenous multistability. Nonlinear Dyn 105, 1843–1857 (2021). https://doi.org/10.1007/s11071-021-06654-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-021-06654-2