Abstract
In the modern era of computing, the iris-based biometric systems are gaining significant attention for secured and automatic human authentication. However, past decades have witnessed numerous spoofing assaults on these iris-based recognition systems where an attacker impersonates an exact replica of biometrical information of the genuine user. Particularly, these direct attacks are targeted on the iris sensor module of the biometric system by presenting the fake artefacts of a bonafide iris trait. With the emergence of data-driven paradigm (i.e. handcrafted feature learners such as support vector machine (SVM), decision tree (DT), k-nearest neighbor (KNN), ensembles, etc. or automatic image features extraction-based classifiers such as convolutional neural networks (CNN), generative adversial networks (GAN)), mitigating these iris spoof attacks has become comparatively an easier and accurate task of computer vision. An iris spoof detector (ISD) is a mechanism through which the vitality of a presented iris trait is measured intelligently by classifying it as genuine or counterfeit. In this study, we explicate a taxonomy-based comparative analysis of state-of-the-art (SOTA) ISDs that employ machine learning or deep learning-based approaches. We expound a novel taxonomy for classifying ISDs based on underlying criterion such as feature type, learning algorithm, pre-trained models, data augmentation, hybrid, etc. Furthermore, we investigate and analyze various benchmark datasets employed in the various data-driven iris spoof detectors (D2ISD). We also illustrate prominent performance evaluation protocols that are widely adopted in the SOTA approaches. Though, pioneer contributions related to D2ISD is reported in the literature, but several potential open research problems still exist, that requisite a futuristic attention of the investigators in this active field of research.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
In today’s era of digitization, biometric-based recognition systems [70] are replacing traditional methods of human authentication. These systems recognize human on the basis of single biometrical modalities such as gait, palm print, fingerprint, voice, face, iris, etc. or fusion of multiple biometric traits [80]. Fig. 1 illustrates a historical evolution of various biometrical traits that are deployed for human recognition over the decades. The prominent biometrical characteristics [46, 47] are widely used as these possess certain properties such as uniqueness, universality, acceptability, measurability and reliability. Among all, iris recognition [45] has become one of the most reliable techniques for human authentication due to its exceptional features as it offers in terms of accuracy, performance, and processing speed. Iris spoof detection is a significant image classification [7,8,9,10,11,12,13] problem that is very prevalent now a days. The iris’ visual texture forms during fetal development and stabilizes over the first two years of life; however, the pigmentation changes over time. These complex iris textures carry unique information that can assist in personal identification.
Further, visible light or near infrared (NIR) illuminated sensors could be used to capture a high-contrast image of an individual’s iris to pick up distinctive patterns that are not visible to the naked eyes. Daugman [24] proposed the first pioneer commercial tool thorough investigation of the iris in the field of biometric identification, which is extensively applied in many real-time systems. Iris codes are proven to be unique not just across unrelated persons but also between the twins and the right and left irises of the same person. Due to its measurability and accuracy, iris-based recognition systems have called forth its wide-scale deployment for applications areas such as airport security, border control, smart phones authentication, forensic investigations, and national identification projects. However, despite of numerous advantages, iris biometric systems are susceptible to a variety of attacks. In a typical biometric-based system, Ratha et al. in 2001 [67] identified eight vulnerable spots. Among all, spoof or presentation attacks are most widely and easier attempted at the sensor level to various types that can degrades the overall performance of system. To countermeasure these attacks on various biometric recognition systems (i.e., fingerprint, face, iris, etc.) a variety of solutions are available [1, 15, 30, 33, 44, 48, 58, 72, 73, 75,76,77, 86] that may be generally classified as: hardware or data-driven based approaches. For the hardware-based methods to distinguish between a real and counterfeit iris trait, we utilize an extra sensing device. Due to its limited capabilities to tackle different types of iris spoof attacks and additional cost of extra hardware device, these approaches are not widely used.
With the emergence of machine learning algorithms and contemporary paradigms shift to deep learning-based CNN models, a more accurate as well as robust solution for iris spoof detection is possible. Figure 2 depicts the developments of various iris spoof detection mechanisms during last couple of years. It can be seen that significant contributions in the field of ISDs has led to a clear paradigm shift from traditional feature descriptors and classifiers to the most recent deep CNNs. The literature exhibits a significant growth in this active field of research where the pioneer contributions from several investigators are reported. Earlier, Czajka and Bowyer [21] (2018) presented a well-structured study that cover a review of various aspects of iris attacks, iris anti-spoofing datasets and software-based solutions. However, this study covers many key domains but limited attention has been put forward to latest deep learning (DL)-based approaches and it includes SOTA approaches up to 2017. In another study, Agarwal and Jalal [2] (2020) presented a brief analysis of iris attacks, datasets and hardware-based as well as software-based approaches. It may be analysed that some of the significant aspects related to data-driven approaches are missing in this study. As majority of the approaches in recent times rely on two important characteristics i.e., robustness of the features and classifiers, a more detailed analysis of recent SOTA ISD is requisite.
Therefore, to address these gaps in the existing review studies, our work aims to present an in-depth and a systematic investigation of D2ISD SOTA approaches through the proposed taxonomy. The goal of our analysis is to compliment the aforementioned existing studies by including more recent aspects that are related to data-driven approaches (i.e., recent benchmark datasets, handcrafted features-based detectors, deep learning-based models, transfer learning, hybrid methods, evaluation protocols, etc.).
The foremost contributions of this article may be stated as follows:
-
We present a taxonomy for the classification of various iris spoof detection approaches.
-
We expound an in-depth study and analysis of SOTA data-driven based iris anti-spoofing mechanisms.
-
A summary of several benchmark iris anti-spoofing datasets that are frequently used for evaluating the presentation attack detection (PAD) algorithms is presented.
-
We present a comparative analysis of some most recent iris SOTA mechanisms through various standard evaluation metrics.
-
At last, we identify several open research challenges from this study and suggest some viable solutions that may provide future directions to the researchers.
The remainder of the article is structured as per the roadmap shown in Fig. 3. Section 2 introduces the study’s scope and coverage. A brief overview of iris presentation attack instruments is provided in Section 3. A detailed review and analysis of D2ISD approaches as well as our proposed taxonomy is presented in Section 4. Performance evaluation protocols and a comparative analysis of recent SOTA approaches are put forward under Section 5. Section 6 includes the overall analysis of D2ISD approaches. The major identified open problems along with suggested remediation are provided in Section 7. Section 8 provides concluding remarks and the future direction of this investigation. Some symbols and acronyms used in the article are listed in Table 8 under Appendix section.
2 Scope and coverage
The key motivation behind this study is to present a thorough analysis of recent SOTA iris anti-spoofing algorithms from 2010 to 2022. Henceforth, we explored more than 150 articles from reputed repositories such as: IEEExplore, Scopus, Web of science, ResearchGate, etc. Thereafter, an intense examination of the literature, led us to finally select a total of 97 articles that are consequently included in the study. Our survey is based on the most recent literature that is advocated by Fig. 4a, where it is meticulously seen that majority of the articles are selected from the period between 2018 to 2022. It is also observed that the pioneer contributions in the field of iris anti-spoofing mechanisms are published in the top-rated transactions or journals that are supported by Fig. 4b, where articles type distribution of the study is depicted. Figure 4c indicate that the majority of the reviewed iris spoof detection approaches are based on static features extraction-based mechanisms. The publisher wise distribution of the selected articles for our analysis is depicted in Fig. 4d.
3 Iris spoof attacks
A spoof attack, as well-defined by ISO/IEC 30107 [16], is a presentation to a biometric model’s sensor that aims to influence these systems to make false identification determinations. The process is used to subvert an iris-based biometric system by presenting a genuine biometric artefact of the legitimate user to the sensor to obtain an illegitimate access to data, either by imitating a verified user or by obscuring the identity of attackers. Fig. 5 illustrates a broad categorization of these attacks. Usually, contact lenses (CL), paper printouts (PP) and plastic artefacts are used to subvert the iris recognition systems. Thus, the relevance of effective security measures against these invasions become paramount. In the succeeding subsection, we briefly deliberate some common spoof attacks on iris biometrics [37].
3.1 Zero effort attacks
Generally, these attacks are carried out by the attacker’s own iris. Hence, no artefacts or knowledge about the legitimate user under assault is required. The success of an attack is determined by the false match rate (FMR), which is computed as the percentage of times the attacker’s iris pattern is successfully matched with that of a valid user. The FMR is associated to the false non-match rate (FNMR), which occurs when the system rejects legitimate users. The higher the FMR, the more vulnerable the system is to this attack. As most of the iris recognition systems have a low FMR, impact of these attacks is expected to be minimal.
3.2 Paper printout attacks
A legitimate iris is directly presented to the iris recognition system’s sensor via a printed photo or digital image. Paper printout attacks are the easiest to spoof as it is moderately easier to access an iris image from the headshots of users on social networking sites (e.g., Twitter, Instagram, Picasa web, and etc.), and it is comparatively easier to print superior quality iris photographs using cameras and ink printers. A sample depiction of paper printout attack is shown in Fig. 6a.
3.3 Video or display attacks
Video assaults make it possible to imitate both the dynamic information as well as its static patterns of an iris. Figure 6b illustrates an iris spoof attack via replaying a video. The expected impact of these attacks is considerably more as high-quality graphic may reproduce digital images and videos. Therefore, it enables iris spoof attacks based on visible spectrum imaging a challenging task but not as much in case of NIR sensors in commercial systems.
3.4 Contact lense attacks
The contact lenses such as textured, patterned or soft could be used for two different types of attacks. The first is an impostor attack, in which the iris pattern of a valid user is imitated. The information required for these attacks is the iris pattern of a genuine user. The masquerade attack, often known as identity concealing, is the second type of attack, where the information of the user is not required. Figure 6c depicts a sample image of textured contact lens of a genuine user. These attacks demand a significant effort for either automatic iris spoof detection or human visual examination.
3.5 Prosthetic eyes attacks
The synthetically generated eyes (SYN) are exploited to imitate the characteristics of real eyes. Figure 6d illustrate a sample iris image of prosthetic eye. These techniques are extensively used for medical purposes ever since the twentieth century, and recent technologies for prosthetic fabrication allow for realistic replication of key characteristics of real eye. These attacks are rarely used by the adversaries and their detection by iris spoof detection methods based on image features is comparatively difficult.
3.6 Cadavers attacks
These attacks are carried out by presenting a deceased person’s iris to a human authentication system’s sensor. It is feasible to attain the post-mortem iris images using commercial iris sensor, and obtain a correct match rate between the samples even upto 30 days after death. However, there isn’t any stated effective attack on the iris authentication systems employing cadaver eye.
4 State-of-the-art iris spoof detection mechanisms
In the previous section, we contemplated that iris recognition systems are vulnerable to a range of spoof attacks at the sensor level. These attacks make the sensor module incompetent of discriminating an authentic or a spoofed biometrical trait. An anti-spoofing mechanism [34] is essential to safeguard sensors from such assaults. Therefore, in this section we explore various countermeasures to presentation attacks (PAs) in iris recognition systems. We have proposed a taxonomy as shown in Fig. 7 that clearly classifies the PAD mechanism into two broad categories i.e., hardware-based and data-driven based approaches. In the following subsections, we examine the existing PAD approaches, including their key concepts, datasets deployed and performance measures.
4.1 Hardware-based approaches
Hardware-based approaches [26, 42, 63] are also called as sensor-based approaches, these may use an extra sensing device in count to the standard iris sensor to measure the physical (e.g., density of the eye tissues) and biological traits (e.g., textural pattern of iris) of the eye. The methods like multispectral imaging, 3D imaging, and electrooculography are used in this approach.
Although hardware-based approaches [20, 43, 53, 64] perform better in a known environment scenario but with an additional cost of further sensor that differentiate between live and fake iris images. As these methods mainly rely on some live characteristics (i.e., impedance, temperature, blood cells, image quality) of an iris image, therefore these approaches have been proved to be comparatively less robust to perform well in unknown environment scenario.
4.2 Data-driven-based approaches
To overcome the confines of contemporary hardware-based iris anti-spoofing techniques, a viable solution is to make use of machine learning-based algorithm. These approaches are mainly based on learning a model by using a variety of handcrafted features from iris images. As these methods, requires training samples to build an iris anti-spoofing model, therefore these are called as data-driven approaches. In the case of data-driven based approaches, there are two significant notions namely: a classifier and a training dataset. One of the major concerns is the quality and diversity in the datasets (higher inter-class and low intra-class diversity) that are being provided to the system for training and testing purpose. The more the inter-class diversity and higher the quality, the better classification decision a system will be able to make. The process to understand the deployment of data-driven-based ISDs in human authentication system is shown in Fig. 8. Based upon the type of method used to extract features from iris images, data-driven approaches may be broadly classified in two categories: manually or automatic crafted features. In the following sub-sections, we present a detailed study and analysis of SOTA iris anti-spoofing methods that employ hand-crafted or automatic feature engineering process.
4.2.1 Handcrafted features extraction-based approaches
In these methods, distinctive features are extracted from iris images to train a classifier for building an iris anti-spoofing model. These may include some image characteristics, micro-textural, color, and statistical features. Among all, micro-textural features of iris images have been explored by majority of the researchers, mainly due to its capability to discriminate between both classes in more efficient manner. Another key aspect is to decide upon the number of samples acquired to build an anti-spoofing model. Hence, these approaches are further classified as static (a single image is used) or dynamic (multiple samples or a small video of iris trait is captured). Fig. 9 illustrates a generic framework for handcrafted features-based ISDs.
Static features-based approaches
These approaches only rely on features extracted from static images of the training dataset. The image features such as micro-textural properties, shape, color features and image quality are frequently explored by the researchers to learn a classifier that discriminate a given image to live or fake. The effectiveness of these iris spoof detection approaches relies on the appropriate robust feature set and a strong learner. Fig. 10 shows a timeline for various feature descriptors deployed in iris spoof detection mechanisms. In the following paragraphs, we present an investigation of various static software-based ISDs.
Earlier, Zhang et al. [94] propounded an iris spoof detection mechanism using scale-invariant feature transform (SIFT) and weighted-local binary patterns (W-LBP) feature descriptors. An SVM classifier is used to discriminate the genuine and artefact iris traits. Though, the experimental results in known attack scenario shows an excellent correct classification rate (CCR) of 99.14%, but the accuracy rate in unknown attack scenario is relatively low. Another solution for iris spoof detection is put forward by Zhang et al. [95] using SIFT descriptor for feature extraction and hierarchical visual codebook (HVC) with SVM for classification purpose. To translate the distinct and robust texture primitives of genuine and counterfeit iris images, the HVC approach uses both LLC and vocabulary tree techniques. This approach lowers the vocabulary tree’s dependence on upper-level coding and achieves low quantization error, sparsity, and capturing salient patterns. Other handcrafted features extraction-based PAD approaches using local binary patterns (LBP) as a feature extractor and SVM as a classifier have been deliberated by Kohli et al. [51] and Gragnaniello et al. [35]. Both the approaches show promising results in terms of accurately classifying the given iris image in two classes but a limited robustness of handcrafted features is observed in these mechanisms.
The concept of quadratic discriminant analysis (QDA) for classification is adopted by Galbally et al. [31]. Performance of the proposed technique is evaluated on ATVS-Fir, CASIA-IrisV1 and, WVU- synthetic iris database and analyzed a half total error rate (HTER) of 2.2% on iris-spoof and 2.1% on iris-synthetic. Another work by Raghavendra & Busch [62] utilize the capabilities of binarized statistical image features (BSIF) for statistical feature extraction and 2D cepstrum analysis for cepstral feature extraction. In this approach, a linear SVM classifier is used for classifying the iris images as real or fake. The suggested iris spoof detection mechanism has an exceptional average classification error rate (ACER) of 0% on ATVS-FIr dataset. Unravelling the effect on textured contact lens on iris recognition system Yadav et al. [89] proposed an approach using modified LBP with an ensemble learning. Whereas, Gupta et al. [38] introduced an iris spoof detection method using three different descriptors namely; LBP, Histogram of Oriented Gradient (HoG), global image descriptor (GIST) and an SVM is employed for classification.
Gragnaniello et al. [36] also addressed a generalized approach to counter liveness detection using LBP, SIFT, BSIF, scale invariant descriptor (SID), local contrast-phase descriptor (LCPD) and multi-resolution LBP descriptors to extract the features from a presented iris image and build a model using an SVM as classifier. The proposed approach achieves a comparable accuracy in most cases except when analyzed on IITD dataset. Meanwhile, Bhogal et al. [14] used non-reference image quality measures (NF-IQM) consisting of NIQE, BLIINDS-II, BIQAA, BRISQUE, DIIVINE, BIQI and a KNN learner is used in the proposed work and classification accuracy of 85.81% on best IQM combinations is achieved. Yang et al. [40] deliberated an iris vitality detection through regional features. These regional features seek the dispersal of the low-level features extracted from neighboring regions and high-level feature distribution that provides profound insight into the distribution in a different region. The proposed approach uses two models i.e., spatial pyramid and relational measure to construct regional features that seek the feature distributions in a region with varying size and shape respectively. Then fusing the outcomes, of the two models at the score level and using an SVM classifier it is decided whether it is a live or a counterfeit iris image. The proposed method is evaluated on four benchmark iris anti-spoofing datasets i.e., Warsaw, Clarkson, MobBIOfake and Notre Dame consisting of live iris images and fake iris that are captured by simulating two different attacks on iris recognition i.e., contact lenses and printout attacks in NIR illumination and visible light. The approach demonstrates that regional features attain analogous performance to SOTA features with precise iris localization and a appropriate pre-processing with reliable feature selection but this approach resulted in a high error rate.
Another robust scheme using Multi-scale BSIF and linear SVM is adopted by Raghavendra and Busch [65], using a novel comparatively significant Visible Spectrum Iris Artefact (VSIA) database consisting of real and counterfeit samples captured by simulating five diverse range of attacks on iris recognition system. Extensive experimentation is carried out in this work and concludes that the proposed PAD scheme has an ACER of 0.29%. Similarly, using orthogonal features a cross-sensor iris spoof detection technique is proposed by kaur et al. [50]. A rotational-invariant feature-set encompassing of polar harmonic transforms and Zernike moments that extracts local intensity variations for detection of iris presentation attacks is introduced. The KNN classifier is used for discriminating genuine and fake iris images. The presented system’s performance is assessed using four publicly accessible iris spoofing datasets: IITD-CLI, IIS, Clarkson LivDet-Iris 2015, and Warsaw LivDet-Iris 2015. The detailed experiments show that proposed system detects iris spoofing assaults with an ease, even when multiple sensors are deployed, making the scheme ideal for commercial real-time applications. Another work on iris spoof detection using combination of KNN classifier and discrete orthogonal moments-based invariant feature-set comprising of Dual-Hahn, Tchebichef, Krawtchouk moments to capture local intensity distribution of the iris texture is adopted by Kaur [49]. To accommodate geometric alterations when images are taken in an uncontrolled environment, the orthogonal moment-based feature-set is made translation, rotation, and scale-invariant. The proposed method’s performance is assessed using four publicly accessible databases: IIITD-Contact Lens Iris, IIITD Iris Spoofing, Clarkson LivDet 2015, and Warsaw LivDet 2015. Their results demonstrate that detecting iris spoofing improves the biometric system’s reliability but the performance degrades when unknown spoofing attack is encountered.
Also, Ahmadi et al. [5] proposed an iris recognition method based on extracting the iris tissue features in 3 steps by using two dimensional Gabor kernel step filtering and polynomial filtering methods. A combination of radial basis function neural network (RBFNN) with genetic algorithm (GA) classifier is applied on iris feature vector for classification purpose. The proposed model is implemented on CASIS-Iris V3, UBIRIs V1 and UCI machine learning datasets. The two-performance metric, receiver operating characteristic (ROC) curve and equal error rate (EER) are used to access the proposed model and result show that the method is able to determine subsets of feature with superior classification accuracy, but it require a large memory space and is a complex approach. Agarwal et al. [4] and Agarwal et al. [3] propounded new descriptors namely; Local binary hexagonal extrema pattern (LBHxEP) and Enhanced binary hexagonal extrema pattern (EBHxEP) respectively. An SVM classifier has been used in both of these approaches and their performance is evaluated on IIITD-CLI, ATVS-Fir datasets and it is inferred that EBHxEP has lower average error rate (AER) as compared to LBHxEP. Recently, Dronky et al. [25] bring forward a method where 8-bit BSIF with an SVM learner is applied for liveness detection. In order to determine if the segmentation stage in liveness detection may be eliminated for a better applicability in real-life scenarios, the method’s effectiveness is evaluated on four distinct datasets in both segmented and un-segmented modes. The outcomes demonstrated that the technique was capable of accurately identifying various assaults. In both techniques of employing NIR datasets, the classification rate for assaults like plastic, synthetic, and print is approximately 100%, however using the entire image improves the ability to identify print attacks in datasets using visible light.
Dynamic features-based approaches
In comparison to static approaches, the dynamic features-based mechanisms utilize multiple image samples of a user acquired during different intervals of time (i.e., a video). Thereafter, features are extracted from multiple image samples to train the anti-spoofing model. However, these methods are comparatively better in accuracy but are computational inefficient due to enlarged training overhead. Few studies have explored the notion of dynamic iris detection that are discussed in the succeeding paragraph.
Raja et al. [66] suggested an approach based on decomposing the images into Laplacian pyramid of various scale and the obtain frequency response in different orientations. The extracted features in the proposed approach are classified using SVM in addition to a polynomial kernel. The proposed technique is further extended with majority voting to classify the artefact for video-based iris recognition systems. Performance of the proposed method is measured on presentation attack video iris database (PAVID) and LivDet Iris 2013 warsaw dataset. And, ACER of 0.64% and 1.37% is measured on PAVID and LivDet Iris 2013 warsaw respectively. Whereas, Rigas and Komogortsev [69] propounded a methodology relying on eye movement traits for the extraction of features indicating iris presentation attack. Due to the artificial nature of the iris paper prints, the devised system is capable of statistically modelling the basic distortions occurring in the eye movement signals during iris print assaults. The suggested technique employs an SVM classifier with a rbf kernel, and it is evaluated using a database of eye movement signals from 200 participants that includes both genuine eye movement signals and signals from the print attack. With an average classification rate (ACR) of 96.5% and an error rate (EER) of 3.4%, the recommended approach also offers strong detection performance. The subjects’ heads are gently stabilized by the use of a headrest, and the trials are conducted in a controlled setting with no outside factors. However, more recent methods of remote eye monitoring provide a different level of head movement. Additionally, some physical, behavioral, and physiological factors (such as weariness) have an effect on the observed eye movements, resulting in fixational signals that are more positionally variable than usual. Recently, Fang et al. [28] put forward a robust iris PAD method that combines 2D (textural) and 3D (shape) information. The convexity of the observed iris surface is next assessed using the normal vector map to determine whether or not the subject is wearing textured contact lenses. The extensive testing with the NDCLD’15 and NDIris3D datasets shows that the proposed method outperforms the existing iris PAD methods in various open set testing scenarios.
From the comparative analysis of handcrafted features-based approaches as specified in Table 1 it can be inferred that there is a limited robustness in the handcrafted features and in the pioneer contributions the LBP descriptor is used may be because of its computational simplicity or its robustness to monotonic grey-scale changes. It may also be analyzed that SVM is one of the most widely used classifier as it works relatively well in most cases and is more effective in high dimensional spaces. Moreover, IIITD-CLI is one of the extensively used dataset in this approach with an accuracy ranging from 72.96% to 99.8%.
4.2.2 Automatic features extraction-based approaches
Manual feature extraction is exploited in handcrafted feature-based approaches, where image descriptors such as BSIF and LBP are used to represent discriminating characteristics. The extraction procedure becomes challenging due to variations in the collected iris images, and there is an inherent issue in these techniques to pre-fix the number of features. The automated feature-based approaches help to address some of these issues. These approaches are also known as deep feature engineering; it constructs new features from the existing data that are used to train the model. Newer DL methods typically use automated feature extraction as they require a large training sample to achieve the high detection accuracy. The concepts of data augmentation and transfer learning could be used to generate larger datasets.
Deep convolution neural network (DCNN)-based approaches
The emergence of deep neural networks, facilitates the task of computer vision, is comparatively easier than traditional handcrafted feature-based mechanisms. The DL-based approaches are frequently employed for counter measuring iris spoofing attacks since the year 2014. A series of benchmark DCNN models such as Inception [81], VGG-16 [79], EfficientNet [82], ResNet50 [39], etc. have been developed that are trained on millions of images from ImageNet dataset. A DCNN model may be viewed as a stacked layered architecture of alternating sequence of convolutional, pooling and drop out layers. A generic architecture of DCNN model employed for iris anti-spoofing is depicted in Fig. 11.
The first N-1 layers of the model extract deep level features and the last layer perform the task of classification. As DL-based models have been proved as a powerful tool for image classification, therefore these models are recently explored to countermeasure iris spoof attacks. The further analysis are focused on the analysis of DL-based ISDs. Earlier, Silva et al. [78] propounded an approach to detect three-class iris contact lens detection i.e., textured lens, soft contact lens and no lenses based on deep image representations by means of learning weights named as CLDNet. Additionally, a CNN model with a fully connected layer is used to build deep image representation with softmax regression to classify the images. The proposed method is evaluated on Notre Dame 2013 and IIIT-Delhi iris databases for contact lens detection. The stated experimentation validates that the proposed method can achieve a 30% performance gain over SOTA on the 2013 Notre Dame and comparable results on IIIT-Delhi database, but this approach does not allow pre-processing, segmenting and localization of the iris. A similar deep CNN-based approach using architectural and filter optimization is followed by Menotti et al. [59]. This approach is evaluated on Warsaw, Biosec and, MobBIOfake datasets of iris images. It can be inferred that Warsaw achieved a lowest HTER rate of 0.16% compared to other datasets. Utilizing the capabilities of deep convolution generative adversarial networks and iris quality metrics Kohli et al. [52] proposed a framework, iris deep convolutional generative adversarial network (iDCGAN) for the generation of realistic appearing synthetic iris images.
The effectiveness of a PDA framework called DESIST to distinguish between artificially generated and genuine iris images is examined. The multi-order Zernike moments and local binary pattern with variance (LBPV) are deployed for feature extraction from these iris images. Accuracy rate achieved by DESIST to classify iris image generated by iDCGAN is 85.95%. Furthermore, it is observed that the synthetically generated iris image from the iDCGAN framework is more challenging to be detected by DESIST compared to the existing synthetic iris database. Pala and Bhanu [61] adopted a deep TripletNet embedding network for iris recognition. The proposed approach makes use of euclidean distance to match the input iris image features with the already stored features. This approach can work in real-time scenario and has comparable accuracy on two benchmarking datasets. A different approach to avoid losing useful information while discarding the parts of input image beyond the boundary of iris that are influenced by noises is bring forward by Liu et al. [56]. The approach is based on fuzzifying the region beyond the boundary of iris to improve the signal-to-noise ratio by using the triangular fuzzy average and triangular fuzzy median smoothing filters to pre-process the iris images. The improved images are then used to train deep learning systems using fuzzy operations that speeded up the convergence process while simultaneously increasing identification accuracy. The fuzzified image filters are also proven to make images more informative for deep learning and the suggested fuzzy image operation provided a robust approach for many additional deep-learning image processing, analysis, and prediction applications.
Similarly, Long. and Zeng [57] also proposed an iris liveliness detection approach by batch normalized CNN to evade the issue of overfitting and gradient disappearing during the training process. The results after evaluation shows that the suggested technique can effectively extract micro features from an image and can provide high accuracy. Hu et al. [41] suggested an end-to-end deep neural network for iris authentication model based on EfficientNet-b0. The designed model is evaluated on hybrid iris databases composed of CASIA thousand and Mmu2. The evaluation resulted into a low valid loss of 0.41% as compared to the previously proposed mixnet_I, resnext50d, resnet50, seresnext and, Senet154 models. In analogy to that, a micro stripe analyses (MSA) solution to sense spoof attack is given by Fang et al. [29]. The MSA focus on the difference of the image dynamics around the iris border area. For classification, decision multiple overlapping stripes is fused by the majority vote. Although this MSA method outperforms the present SOTA, it does not show the problem of confounding genuine clear lenses with assault textured ones.
As per the comparisons among the illustrated SOTA DCNN features extraction-based approaches as stated in Table 2, it can be analyzed that various CNN-based frameworks have been put forward and majority of these approaches are evaluated on well-known IIT-Delhi and CASIS iris datasets in known environment. But limited evaluation of DCNN approaches in unknown environment is done where the accuracy ranges from 69.47% to 91.77%.
Fully connected network (FCN)-based approaches
As per the above-mentioned CNN-based technique, it may be inferred that giving an entire iris image as an input to the model is inefficient. Since the pixels are lying on the outside iris region are not considered, thus we can take into consideration small iris patches to the learning classifiers for efficient training purpose. The FCN model [55, 83] is a deep learning-based network relying on conventional CNN model without a fully connected layer and it combines expression and prior-knowledge similarities as the input. In the subsequent paragraph, we analyze the locally supervised FCN-based iris spoof detection approaches. Varkarakis et al. propose a deep learning strategy for segmentation of deformed iris areas using FCN in head mounted display. [88]. The proposed network offers a good accuracy of 99.34% and 99.12% on datasets namely; CASIA thousand and Bath-800 respectively. Another robust iris segmentation technique using FCN with dilated convolution is suggested by Yang et al. [93]. The suggested model does not require any pre-processing of the input iris images and provides end-to-end prediction.
Tobji et al. [87] propounded an FMnet algorithm using FCN for manual segmentation and multi-scale convolutional neural network (MCNN) for feature extraction and classification purpose. The performance is evaluated on three datasets i.e., CASIA-Iris-Thousand, UBIRIS.v2 and, LG2200 where the recognition accuracy reported for CASIA-Iris-Thousand is 95.63%, UBIRIS.v2 is 99.41% and, LG2200 is 93.17%. Zhao and Kumar [96] developed a framework using FCN which generates spatial consistent iris feature descriptors. Also, an extended triplet loss (ETL) function is used to integrate bit-shifting and non-iris masking. By extending the work done in 2019 a DL-based unified framework for iris spoof detection, segmentation and recognition is propound by Zhao and Kumar [97]. The proposed framework UniNet.v2 consists of three modules: Mask R-CNN for image localization and segmentation using optimized FCN, normalized layer and FeatNet for feature learning and matching.
While comparing various FCN-based iris spoof detection methods reported in Table 3, it can be inferred that in most of the approaches a fully connected network is used for segmentation. It may be because of its structure agnostic property and a CNN framework with some modification that is used for classification task. Moreover, to evaluate the performance, the majority of these approaches have used the CASIA V4 iris datasets with an accuracy rate of 95.63% to 99.34%.
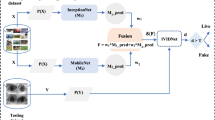
Transfer learning-based approaches
One of the critical issues in the CNN-based approaches is to extract deep level features to design a robust ISD that perform well in unknown attacking scenario. To tackle these problems, a recent paradigm in deep learning is to utilize the knowledge of the pre-trained models in a specific domain that can be effectively transferred to build an efficient ISD. The transfer learning offers numerous advantages such as reduced training time, improved performance (in most cases), also it doesn’t require a huge amount of data. The conception of transfer learning that is used to effectively import the knowledge from source domain to the target domain for building an efficient ISD is illustrated in Fig. 12. In a recent study, Ribeiro et al. [68] investigated the texture transfer learning for super resolution that is applied to low resolution images. The designed approach is evaluated on the subset of CASIA iris image dataset and the best performance of EER 6.07% in factor 2 is achieved when describable texture dataset (DTD) is used. The fusion between the best datasets with the enrolment results is not explored in this work. Chen and Ross [18] proposed multi-task PAD system inspired by an object detection method. The suggested method is computationally effective and can be used in real-time environment. But the technique is not investigated in the scenarios where the training and test datasets have different attacks.
Gautam and Mukhopadhyay [32] presented a transfer learning technique relied on (AlexNet) pre-trained DCNN for feature extraction followed by principal component analysis (PCA) for dimensionality reduction. Cubic SVM (cSVM) based on error-correcting output code (ECOC) multi-class model is further used for classification purpose. For multi-sensor evaluation the CCR of 81.40% and 86.33% is achieved for IIITD and ND dataset respectively. Efficient comprehension and exploitation of hybrid classifiers as well as powerful feature extraction techniques in combination with deep image representation are still open issues to be addressed in this work. The conception of transfer learning that is used to effectively import the knowledge from. An effective iris authentication system based on transfer learning with CNN is suggested by Alaslani and Elrefaei [6]. To adopt this strategy, a pre-trained VGG-16 model for feature extraction and classification is tuned. Thereafter, the IITD, CASIA-Iris-V1, CASIA-Iris-thousand, and CASIA-Iris-Interval public datasets are used to assess the performance of the iris recognition system. The findings reveal that the suggested approach has a very high accuracy rate of 100% in case of IIITD. A deep learning framework fine-tuned on pre-trained CNN model (ImageNet) is put forward by Minaee and Abdolrashidi [60]. The performance of the technique is assessed using IITD dataset and the accuracy rate of 95.5% is obtained. A novel densely connected contact lens detection network (DCLNet) based on DCNN with addition of SVM on top for classification is proposed by Choudhary et al. [19]. The DCLNet is a densely connected convolutional network with fewer layers and learning parameters than other networks. It learns more significant iris traits due to the dense connections between layers. The experimental results reaffirm that the proposed approach improves the CCR up to 4% as compared to the SOTA. However, it can be inferred that normalization can cause degradation in the model’s accuracy in majority of the cases.
Depending on the architecture of a deep learning model for images of a person’s left and right irises, a multimodal biometric real-time technique IrisConvNet is adopted by Therar et al. [85]. The feature extraction and classification task are dependent on CNN and transfer learning techniques to generate special features that are supplied to a multi-class SVM algorithm. The performance of IrisConvNet is measured on two publicly available datasets IITD and CASIA-Iris-V3. The accuracy rate of IITD is 99% for both left and right iris and CASIA-Iris-V3 is 94% and 93% for the left and right iris respectively. Sardar et al. [71] introduced an interactive variant of Unet i.e., deep Interactive Squeeze Expand Unet (ISqEUNet) model with interactive learning to lower the training time while improving the storage efficiency by reducing the number of involved parameters. The performance being evaluated on three publicly available dataset shows that NICE. I has a mean true positive rate (mTRP) of 0.983% and mean error rate (MER) of 0.261%. Another ISD solution based on multi-layer fusion is propounded by Fang M. et al. [27]. Two level fusion i.e. feature level and score level is done on the feature extracted from the last several convolution layers. Although, result shows that multi-layer fusion technique performs better as compare to the best single layer feature extractor using pre-trained VGG-16 but while trained from scratch this technique perform well only on larger dataset such as the IIITD-WVU database in comparison to the Notre Dame database. Recently, Tapia J. et al. [84] deliberated a two-stage serial framework for PAD focused on detecting bonafide images. For this approach the largest iris PA database by combining several other databases is developed and model is tested when trained from scratch and using fine-tuning. Although comparable results are obtained in known environment the performance of proposed two stage networks is not measured in unknown attack scenarios.
From the comparative analysis of various transfer learning-based iris spoof detection approaches as discussed in Table 4, it can be inferred that in most of the techniques a pre-trained model on ImageNet is used. The reason behind this is, it consists of over 14 million images of roughly 20,000 categories and training a new model using this may reduce the overall training time. Moreover, IITD iris anti-spoofing dataset is widely used in these approaches. Besides, the accuracy rate for IITD dataset in transfer learning-based approaches ranges from 81.40% to 100%.
4.2.3 Hybrid features extraction-based approaches
The handcrafted ISDs have shown promising performance in known attack scenarios but exhibits limited generalization capabilities in unknown attacking environments. Hence, to overcome these problems the DL-based iris spoof detection approaches have proved to be of worth in unknown scenarios, however with an additional training overhead. Our analysis presented in the previous sections indicates a trade-off among design and performance parameters of anti-spoofing mechanisms. Therefore, an alternative solution is to explore the approaches that employ the pros of both handcrafted and DL-based ISDs. These mechanisms may utilize the highly discriminatory feature sets generated by CNN models followed by a traditional classifier such as: SVM, KNN, DT, etc. A generic illustration of hybrid features extraction-based approach is shown in Fig. 13.
The most recent studies as hybrid iris spoof detection is presented by Czajka et al. [22] in 2017 to countermeasure the spoofing attacks generated by rotating the iris image or the sensor during acquisition and correctly recognizing the left / right (L/R) and upright / upside-down (U/D) orientation of the iris images. Two approaches namely feature engineering (using SVM) and feature learning (using CNN) are compared and evaluated on the proprietary iris dataset by both same-sensor and cross sensor tests. The CCR achieved in case of SVM for L/R is 99.8% and for U/D is 97.3% and in case of CNN is nearly 100% in both the cases (in known environment). It has been observed that CNN-based approach performed better for same-sensor, and presented slightly worse to unknown sensors experiments when compared to an SVM classifier. An ensemble of multi-view-CNN for cross domain iris PAD is proposed by Kuehlkamp et al. [54]. Capabilities of BSIF feature descriptors is utilized and the performance measured by meta-fusing (via SVM) on four benchmark datasets shows that the lowest HTER is in case of Warsaw (0.44% & 0.79%) in known environment and unknown environment. But in test unknown partitions scenario this approach achieves HTER of 20.92% that is higher as compare to others. Another contribution using discrete wavelet transform (DWT) for feature extraction and modified deep residual neural network for spoof detection is done by Chatterjee et al. [17]. Although, the classification accuracy of DWT + modified ResNet for ATVS-FIr and CASIS outperforms the previously implemented modified VGG Net and DWT + modified VGG Net. But, comparatively lesser detection accuracy is achieved when modified ResNet classification technique is employed.
Analyzing the illustrated hybrid iris spoof detection approaches as stated in Table 5 that combines the pros of both handcrafted and deep learning-based approaches it can be deduced that majority of these techniques are evaluated on publicly available datasets with an accuracy ranging from 82.4% to 92.57%.
5 Performance evaluation protocols
The effectiveness and correctness of D2ISD mechanisms is measured through widely accepted evaluation protocols such as anti-spoofing datasets and performance measuring metrics. In this section, we present an evaluation protocols-based analysis of various approaches.
5.1 Benchmark iris anti-spoofing datasets analysis
An iris anti-spoofing database signifies the well-organized collection of iris data that is primarily used for developing and evaluating the iris spoof detection algorithms. A sufficient size of database consistent to diverse iris sensing approaches and fabrication components are required to evaluate these algorithms. Figure 14 shows few samples of iris images from the benchmark iris anti-spoofing datasets. In this section, we present a review of several existing iris anti-spoofing databases that are widely used in the literature of iris spoof detection mechanisms. The most prominent databases are from publicly available Liveness detection competition series: LivDet-2020 [23], LivDet-2017 [92], LivDet-2015 [91], LivDet-2013 [90], MobBIOfake [74], etc. The details of ISDs datasets are listed in Table 6 along with the sensor technology used for capturing iris images at various resolution and image sizes.
After assessment, two imperative assumptions may be drawn from the benchmark iris anti-spoofing datasets given in Table 6. First indicate that the most prominently used dataset for performance evaluation of iris spoof detection approaches is IIITD-CLI, and the second is the size of datasets used for iris spoof detection techniques consists of only few thousands iris images, that is inadequate for learning an effective DL-based iris spoof detector (DISD). CASIS-IrisV3 is the largest of all consisting of 22,035 images.
5.2 ISDs evaluation metrics
The well-known performance metrics are used to assess the extent to which possible mechanisms, solutions, or D2ISD models are able to meet the expectations through extents of their performance, limitations, and trade-off. The standard metrics for evaluating the effectiveness of an iris PAD are defined by the International Standard Organization (ISO/IEC 30107–3:2017) and is summarized in Table 7.
The analysis of the evaluation metrics that are employed for iris spoof detection approaches as illustrated in Table 7, it may be observed that the FRR is the most widely used protocol for evaluating the performance of anti-spoofing mechanisms.
6 Overall analysis
With the thorough investigations and analysis of D2ISD approaches, certain broad inferences can be drawn as an outcome of the study. Figure 15 depicts the overall outcomes of the comparative analysis particularly based on the descriptors used, learning algorithms, spoofing attack types, etc. Our analysis from Fig. 15a indicate that LBP and its variants are most widely deployed image descriptors in handcrafted features-based ISD methods.
One of the reasons behind this is the robustness and ability of LBP descriptors to tackle the inconsistences in iris images that include rotational, scale and illumination variations. Another image BSIF descriptor that extracts robust features from iris images is also a popular choice to the designers of ISDs. The classification is a vital task of any ISD that discriminate a given iris image as live or fake. From the Fig. 15b, the literature witnesses the use of SVM in majority of the handcrafted features-based ISDs. In comparison to other classifiers, the SVM discriminate between the bonafide and fake samples via a hyperplane with maximum margin. Moreover, SVM is efficient in terms of training overhead and it supports its utilization in majority of the traditional approaches. On the other hand, in the contemporary ISDs, the deep CNN with additional notion of data augmentation or pre-trained models is a prevailing scenario. Apart from this, Fig. 15c shows that pre-trained models such as MobileNet, VGGNet, and ResNet are also being used for developing efficient ISD approaches. Counter measuring iris attacks are also an important design issue for a potent ISD. Our analysis from Fig. 15d shows a comparison among the type of iris attacks tackled by existing ISDs. Moreover, the study infers that most of the ISDs countermeasures paper printout and contact lens attacks. Only a few mechanisms have been developed that may prevent the sensor module from video, prosthetic eye, and cadavers’ attacks. From the overall analysis it is also inferred that the benchmark IIIT Delhi and LivDet 2013 are the most widely used iris anti-spoofing datasets to evaluate the performance of model as demonstrated in Fig. 15e. In the last, a comparison based on the performance evaluation protocols is presented in Fig. 15f. The ACER and ROC curve are the frequently used metrics to compute the performance of an ISD.
7 Open research challenges and future directions
The critical investigation and study in the previous sections has led to identification of several open research issues that need futuristic exploration in the future research. In this section, we deliberate various research problems and opportunities for further study to tackle PAs in the iris biometric systems. The major open problems and the viable opportunities that have emerged from our overall analysis are explained as follows.
i. Open research problem. Limited robustness of handcrafted features: The majority of iris spoof detection methods have used a single descriptor for image classification ([2,3,4, 16, 20, 26, 31, 34,35,36,37,38, 42, 43, 51, 53, 62,63,64,65, 89, 94, 95] and [25]) that results in low discrimination power for accurately discriminating an image to be a real or fake iris traits. Therefore, a challenge is to build a model that can efficiently extract robust feature sets from iris images that may accurately classify a given iris image into a real or fake label.
Future directions: To build more accurate ISD, the future direction orient towards exploring a novel combination of multiple features. The compatibility and upper limit on the number of features need a thorough analysis for avoiding the curse-of-dimensionality issues. The choice of features sets is dependent upon the discrimination power to accurately classify a given iris image as real or fake. The design of novel methods for feature or decision level fusion of multiple image features is another future scope for the researchers. Another design issue for multi-features-based ISD methods is to select appropriate classification algorithms. |
ii. Open research problem. Requirement of robust learner: Our analysis clearly indicate that majority of the existing handcrafted features-based ISD’s used a single classifier such as: SVM or KNN ([3, 4, 14, 25, 31, 35, 36, 38, 50, 94] and [69]). In some cases, these alone classifiers may not perform well to tackle the problem of imbalanced datasets or the model does not offer the desired performance, hence results in overfitting the ISD model. Moreover, the decision capabilities of various classifiers vary in different environmental conditions as well as inconsistences in the training datasets.
Future directions: One of the viable solutions that is least explored is to employ the notion of ensemble learning [89], where the decision of multiple weak classifiers is consolidated to result in the final outcome. Additionally, these approaches are particularly significant in the case when the ISD is built on multiple handcrafted-features. A diverse range of simple (e.g. majority voting, weighted sum, etc.) as well as complex (e.g. bagging, AdaBoost, etc.) ensembles are available that may be explored in designing more robust learners for iris spoof detection. |
iii. Open research problem. Limited performance of handcrafted approaches in unknown attack scenario: One of the utmost attributes of an ISD is to perform excellently well in known as well as unknown attack scenario such as (i.e. cross-sensor, cross-database and cross-material). From our analysis, it is observed that only few existing approaches ([49,50,51, 94, 95] and [28]) are evaluated in unknown attacking scenario. Moreover, these approaches offer limited performance to tackle the problems of unknown attacks.
Future directions: The future research should be oriented towards developing robust handcrafted features-based ISDs that are well trained on iris images of diverse range of variations covering samples from different sensors, datasets and iris spoof materials. |
iv. Open research problem. Adversial attacks on CNN models: A recent paradigm has shifted to deep-level features via CNN for building an accurate iris spoof detection network. However, these models are also vulnerable to attacks that may be hosted by an adversary, where the underline architecture of the CNN model is altered. In this manner, the knowledge learned by an CNN-based ISD model accumulated as model weights may be either completely stolen or altered.
Future directions: As a future research, the secured CNN models can be developed to overcome the different types of adversial attacks. Alternatively, the effective mechanisms can be explored to counter the attacks on CNN-based ISD models. |
v. Open research problem. Limited performance of CNN-based methods in unknown attack scenario: Though, CNN-based iris spoof detection approaches demonstrates excellent performance in known environment, but our study examined that limited work has focused on unknown attack scenarios [29]. Surprisingly, these approaches are only evaluated on cross-dataset scenarios.
Future directions: To further boost up performance of CNN-based ISDs, the models should be trained on iris images captured from different sensors as well as spoofed artefacts created from various materials. To anticipate, the artefact created from unknown materials the iris spoof detection model should actively learn from previously misclassified fakes. |
vi. Open research problem. Inadequate dataset for DL-based iris spoof detector: One of the critical design issues for DISD is the requirement of appropriate and adequate size of iris anti-spoofing datasets. In other words, the DL-based approaches are most effective when the model is trained on millions of images. From our investigations it may be seen that the existing benchmark anti-spoofing datasets are comprised of only few thousands iris images [23, 74, 90,91,92], that is inadequate for learning an effective DISD.
Future directions: One of the solutions is to develop a large-scale dataset covering millions of iris images acquired in different environmental conditions. However, this is time consuming and tedious mechanism, therefore an alternative is to explore data augmentation to enlarge the size of existing datasets. Another mechanism may explore the concept of transfer learning that use the power of well-known pre-trained CNN models on millions of images. |
vii. Open research problem. Lack of lightweight DL-enabled ISD models: An iris anti-spoofing method may be viewed as a simple binary classification problem to categorize an input image as either real or fake. The existing DL-based models that employ deeper architectures (higher number of layers) result in larger training overhead due to millions of trainable parameters.
Future directions: An alternative and efficient approach is to develop novel architecture that is comprised of comparatively lesser number of layers. However, to tackle this problem the concept of domain adaptation may be adopted where the knowledge of source domain may be transferred for learning lightweight DISD. |
viii. Open research problem. Need of hybrid approaches for efficient models: The overall analysis from the presented study draws a clear inference that there exists a trade-off between classical handcrafted features and contemporary DL-based iris spoof detection approaches. Both the mechanisms exhibit conciliation between accuracy and training overhead as well as performance in unknown attack scenarios. Although, some studies are available in literature that are based on hybrid iris spoof detection mechanisms ([22, 54] and [17]), but the further improvements in this field is requisite.
Future directions: To offer viable and efficient iris anti-spoofing solutions, the futuristic approaches can exploit the pros of both the classical as well as modern iris spoof detection approaches. Therefore, the DL-based ISD can integrate some of the initial layers as handcrafted features followed by convolutional, pooling, drop out and fully connected layers. |
8 Conclusions
In this study, we presented an in-depth review of SOTA iris anti-spoofing approaches. Our study has analyzed several ISDs that make use of different types of image features along with a diverse range of classification algorithms. However, handcrafted features and DL-based ISDs show their respective merits and demerits but a clear trade-off between these methods is a major investigation of the presented study. It has led researchers to explore new hybrid ISD mechanisms that complement the pros of both the schemes. Apart from this, evaluation protocols-based analysis of D2ISD approaches offers a clear futuristic perspective for designing improved anti-spoofing mechanisms. Among all, one of the critical issues is to build an appropriate anti-spoofing iris dataset as the data-driven approaches are heavily dependent on the quality as well as quantity of the training dataset. Moreover, the choice of a strong classifier is an imperative design issue in the classical approaches that employs multiple image features. Our study clearly infers that the modern paradigm has shifted towards DL-based ISD approaches, hence the training overhead due to the requirement of larger dataset led to additional challenge. The future research can be oriented towards designing robust and lightweight iris spoof detectors via transfer learning or active learning. The expansion of benchmark anti-spoofing iris datasets covering broader perspectives may help to tackle the problem of unknown attacks scenarios. The analysis presented in this study, infers that majority of the work has focused on counter measuring photo or cosmetic lens attacks. Therefore, the future work may target preventing from other iris attacks such as display, prosthetic eye, etc. It is also observed that SOTA iris spoof detectors demonstrate superb performance in known attack environments while results in satisfactory accuracy in unseen attacks. In future, robust ISD mechanisms can be explored that performs well in unseen attack scenarios (i.e. cross-database, cross-sensor, and cross-materials).
Data availability
The datasets used/generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
References
Abdellatef E, Ismail NA, Abd Elrahman SESE, Ismail KN, Rihan M, Abd el-Samie FE (2019) Cancelable multi - biometric recognition system based on deep learning. Vis Comput 36(0123456789):1097–1109. https://doi.org/10.1007/s00371-019-01715-5
Agarwal R and Jalal AS (2021) “Presentation attack detection system for fake Iris: a review,” Multimed. Tools Appl, https://doi.org/10.1007/s11042-020-10378-7.
Agarwal R, Jalal AS, Arya KV (2020) Enhanced binary hexagonal Extrema pattern (EBHXEP) descriptor for Iris liveness detection. Wirel Pers Commun 115(3):2627–2643. https://doi.org/10.1007/s11277-020-07700-9
Agarwal R, Jalal AS, Arya KV (2021) Local binary hexagonal Extrema pattern (LBHXEP): a new feature descriptor for fake iris detection. Vis Comput 37(6):1357–1368. https://doi.org/10.1007/s00371-020-01870-0
Ahmadi N, Nilashi M, Samad S, Rashid TA, Ahmadi H (2019) An intelligent method for iris recognition using supervised machine learning techniques. Opt Laser Technol 120(December 2018):105701. https://doi.org/10.1016/j.optlastec.2019.105701
Alaslni MG, Elrefaei LA (2019) Transfer learning with convolutional neural networks for IRIS recognition. Int J Artif Intell Appl 10(5):49–66. https://doi.org/10.5121/ijaia.2019.10505
Bakkouri I, Afdel K (2020) Computer-aided diagnosis (CAD) system based on multi-layer feature fusion network for skin lesion recognition in dermoscopy images. Multimed Tools Appl 79(29–30):20483–20518. https://doi.org/10.1007/s11042-019-07988-1
Bakkouri I, Afdel K, Benois-Pineau J, Catheline G, For the Alzheimer’s Disease Neuroimaging Initiativ (2022) BG-3DM2F: Bidirectional gated 3D multi-scale feature fusion for Alzheimer’s disease diagnosis, vol. 81, no. 8
Bhatti UA, Huang M, Wang H, Zhang Y, Mehmood A, Di W (2018) Recommendation system for immunization coverage and monitoring. Hum Vaccines Immunother 14(1):165–171. https://doi.org/10.1080/21645515.2017.1379639
Bhatti UA, Huang M, Wu D, Zhang Y, Mehmood A, Han H (2019) Recommendation system using feature extraction and pattern recognition in clinical care systems. Enterp Inf Syst 13(3):329–351. https://doi.org/10.1080/17517575.2018.1557256
Bhatti UA, Yu Z, Li J, Nawaz SA, Mehmood A, Zhang K, Yuan L (2020) Hybrid watermarking algorithm using Clifford algebra with Arnold scrambling and chaotic encryption. IEEE Access 8:76386–76398. https://doi.org/10.1109/ACCESS.2020.2988298
Bhatti UA, Zeeshan Z, Nizamani MM, Bazai S, Yu Z, Yuan L (2022) Assessing the change of ambient air quality patterns in Jiangsu Province of China pre-to post-COVID-19. Chemosphere 288(2):132569. https://doi.org/10.1016/j.chemosphere.2021.132569
Bhatti UA et al (2022) Local Similarity-Based Spatial–Spectral Fusion Hyperspectral Image Classification With Deep CNN and Gabor Filtering. IEEE Trans Geosci Remote Sens 60. https://doi.org/10.1109/TGRS.2021.3090410
Bhogal APS, Sollinger D, Trung P, Uhl A (2017) Non-reference image quality assessment for biometric presentation attack detection. Proc - 2017 5th Int Work Biometrics Forensics, IWBF 2017. https://doi.org/10.1109/IWBF.2017.7935080
Boulkenafet Z, Komulainen J, Hadid A (2018) On the generalization of color texture-based face anti-spoofing. Image Vis Comput 77:1–9. https://doi.org/10.1016/j.imavis.2018.04.007
Busch C (2017) “The ISO/IEC standards for testing of Presentation Attack Detection,”, [Online]. Available: https://christoph-busch.de/files/Busch-PAD-standards-170329.pdf.
Chatterjee P, Yalchin A, Shelton J, Roy K, Yuan X, Edoh KD (2019) Presentation attack detection using wavelet transform and deep residual neural net, vol 11637. Springer International Publishing, LNCS
Chen C, Ross A (2018) “A Multi-Task Convolutional Neural Network for Joint Iris Detection and Presentation Attack Detection,” no. March
Choudhary M, Tiwari V, Venkanna U (2019) An approach for iris contact lens detection and classification using ensemble of customized DenseNet and SVM. Futur Gener Comput Syst 101:1259–1270. https://doi.org/10.1016/j.future.2019.07.003
Czajka A (2015) Pupil dynamics for iris liveness detection. IEEE Trans Inf Forensics Secur 10(4):726–735. https://doi.org/10.1109/TIFS.2015.2398815
Czajka A, Bowyer KW (2018) Presentation attack detection for iris recognition: An assessment of the state-of-the-art. ACM Comput Surv 51(4). https://doi.org/10.1145/3232849
Czajka A, Bowyer KW, Krumdick M, Vidalmata RG (2017) Recognition of image-orientation-based Iris spoofing. IEEE Trans Inf Forensics Secur 12(9):2184–2196. https://doi.org/10.1109/TIFS.2017.2701332
Das P et al. (2020) “Iris Liveness Detection Competition (LivDet-Iris) - The 2020 Edition,” IJCB 2020 - IEEE/IAPR Int. Jt. Conf. Biometrics, https://doi.org/10.1109/IJCB48548.2020.9304941.
Daugman J (1994) “Biometric Personal Identification System Based on Iris Analysis,” no. 19
Dronky MR, Khalifa W, Roushdy M (2021) Using residual images with BSIF for iris liveness detection. Expert Syst Appl 182(March 2020):115266. https://doi.org/10.1016/j.eswa.2021.115266
“FAKE IRIS DETECTION USING STRUCTURED LIGHT Connell J, N Ratha, James Gentile, Ruud Bolle (2013) Yorktown Heights , NY 10598 { jconnell , ratha } @ us . ibm . com,” pp. 8692–8696
Fang M, Damer N, Boutros F, Kirchbuchner F, Kuijper A (2020) “Deep learning multi-layer fusion for an accurate iris presentation attack detection,” Proc. 2020 23rd Int. Conf. Inf. Fusion, FUSION 2020, https://doi.org/10.23919/FUSION45008.2020.9190424.
Fang Z, Czajka A, Bowyer KW (2021) Robust iris presentation attack detection fusing 2D and 3D information. IEEE Trans Inf Forensics Secur 16:510–520. https://doi.org/10.1109/TIFS.2020.3015547
Fang M, Damer N, Boutros F, Kirchbuchner F, Kuijper A (2021) Cross-database and cross-attack Iris presentation attack detection using micro stripes analyses. Image Vis Comput 105:104057. https://doi.org/10.1016/j.imavis.2020.104057
Farmanbar M, Toygar Ö (2017) Spoof detection on face and palmprint biometrics. Signal, Image Video Process 11(7):1253–1260. https://doi.org/10.1007/s11760-017-1082-y
Galbally J, Marcel S, Fierrez J (2014) Image quality assessment for fake biometric detection: application to Iris, fingerprint, and face recognition. IEEE Trans Image Process 23(2):710–724. https://doi.org/10.1109/TIP.2013.2292332
Gautam G, Mukhopadhyay S (2018) “Contact Lens Detection using Transfer Learning with Deep Representations,” Proc. Int. Jt. Conf. Neural Networks, vol. 2018-July, pp. 1–8, https://doi.org/10.1109/IJCNN.2018.8489590.
Gomez-Barrero M, Rathgeb C, Li G, Ramachandra R, Galbally J, Busch C (2018) Multi-biometric template protection based on bloom filters. Inf Fusion 42:37–50. https://doi.org/10.1016/j.inffus.2017.10.003
Goshtasby AAA (2012) Advances in computer vision and pattern recognition
Gragnaniello D, Sansone C, Verdoliva L (2015) Iris liveness detection for mobile devices based on local descriptors. Pattern Recogn Lett 57:81–87. https://doi.org/10.1016/j.patrec.2014.10.018
Gragnaniello D, Poggi G, Sansone C, Verdoliva L (2015) An investigation of local descriptors for biometric spoofing detection. IEEE Trans Inf Forensics Secur 10(4):849–863. https://doi.org/10.1109/TIFS.2015.2404294
Gupta R, Sehgal P (2016) A survey of attacks on iris biometric systems. Int J Biometeorol 8(2):145–178. https://doi.org/10.1504/IJBM.2016.077833
Gupta P, Behera S, Vatsa M, Singh R (2014) On iris spoofing using print attack. Proc - Int Conf Pattern Recognit:1681–1686. https://doi.org/10.1109/ICPR.2014.296
He K, Zhang X, Ren S, Sun J (2016) “Deep residual learning for image recognition,” Proc. IEEE Comput. Soc. Conf. Comput. Vis. Pattern Recognit., vol. 2016-Decem, pp. 770–778, https://doi.org/10.1109/CVPR.2016.90
Hu Y, Sirlantzis K, Howells G (2016) Iris liveness detection using regional features. Pattern Recogn Lett 82:242–250. https://doi.org/10.1016/j.patrec.2015.10.010
Hu Q, Yin S, Ni H, Huang Y (2020) An end to end deep neural network for Iris recognition. Procedia Comput Sci 174(2019):505–517. https://doi.org/10.1016/j.procs.2020.06.118
Huang X, Ti C, Hou QZ, Tokuta A, Yang R (2013) An experimental study of pupil constriction for liveness detection. Proc IEEE Work Appl Comput Vis:252–258. https://doi.org/10.1109/WACV.2013.6475026
Hughes K, Bowyer KW (2013) Detection of contact-lens-based iris biometric spoofs using stereo imaging. Proc Annu Hawaii Int Conf Syst Sci:1763–1772. https://doi.org/10.1109/HICSS.2013.172
Ishfaq DSR, Selwal A (2021) “Fingerprint Spoofing Attacks and their Deep Learning-enabled Remediation: State-of-the-art, Taxonomy, and Future Directions,” pp. 22–28
Jain AK, Ross A, Prabhakar S (2004) An introduction to biometric recognition. IEEE Trans Circuits Syst Video Technol 14(1):4–20. https://doi.org/10.1109/TCSVT.2003.818349
Jain AK, Flynn P, Ross AA (2007) Handbook of biometrics
Jamdar SD et al (2017) Biometrics: A Tool for Information Security Anil. IEEE Trans Inf Forensics Secur 1(Iccmc):125–143
Kapur PK, Singh G, Klochkov YS, Kumar U (2020) Decision analytics applications in industry.
Kaur B (2020) Iris spoofing detection using discrete orthogonal moments. Multimed Tools Appl 79(9–10):6623–6647. https://doi.org/10.1007/s11042-019-08281-x
Kaur B, Singh S, Kumar J (2019) Cross-sensor iris spoofing detection using orthogonal features. Comput Electr Eng 73:279–288. https://doi.org/10.1016/j.compeleceng.2018.12.002
Kohli N, Yadav D, Vatsa M, Singh R (2013) Revisiting iris recognition with color cosmetic contact lenses. Proc - 2013 Int Conf Biometrics, ICB 2013 1. https://doi.org/10.1109/ICB.2013.6613021
Kohli N, Yadav D, Vatsa M, Singh R, Noore A (2018) “Synthetic iris presentation attack using iDCGAN,” IEEE Int. Jt. Conf. Biometrics, IJCB 2017, vol. 2018-Janua, pp. 674–680 https://doi.org/10.1109/BTAS.2017.8272756.
O. V Komogortsev, S. Marcos, A. Karpov, and S. Marcos (2013) “Liveness Detection via Oculomotor Plant Characteristics : Attack of Mechanical Replicas”
Kuehlkamp A, Pinto A, Rocha A, Bowyer KW, Czajka A (2019) Ensemble of Multi-View Learning Classifiers for cross-domain Iris presentation attack detection. IEEE Trans Inf Forensics Secur 14(6):1419–1431. https://doi.org/10.1109/TIFS.2018.2878542
Liu N, Li H, Zhang M, Liu J, Sun Z, Tan T (2016) Accurate iris segmentation in non-cooperative environments using fully convolutional networks. 2016 Int Conf Biometrics, ICB:2016. https://doi.org/10.1109/ICB.2016.7550055
Liu M, Zhou Z, Shang P, Xu D (2020) Fuzzified image enhancement for deep learning in Iris recognition. IEEE Trans Fuzzy Syst 28(1):92–99. https://doi.org/10.1109/TFUZZ.2019.2912576
Long M, Zeng Y (2019) “Detecting Iris Liveness with Batch Normalized Convolutional Neural Network,” vol. 58, no. 2, pp. 493–504, https://doi.org/10.32604/cmc.2019.04378.
Mehmood R, Selwal A (2020) Polynomial based fuzzy vault technique for template security in fingerprint biometrics. Int Arab J Inf Technol 17(6):926–934. https://doi.org/10.34028/iajit/17/6/11
Menotti D, Chiachia G, Pinto A, Robson Schwartz W, Pedrini H, Xavier Falcao A, Rocha A (2015) Deep representations for Iris, face, and fingerprint spoofing detection. IEEE Trans Inf Forensics Secur 10(4):864–879. https://doi.org/10.1109/TIFS.2015.2398817
Minaee S, Abdolrashidi A (2019) “DeepIris: Iris Recognition Using A Deep Learning Approach,” [Online]. Available: http://arxiv.org/abs/1907.09380.
Pala F Bhanu B (2017) “Iris Liveness Detection by Relative Distance Comparisons,” IEEE Comput. Soc. Conf. Comput. Vis. Pattern Recognit. Work., vol. 2017-July, pp. 664–671 https://doi.org/10.1109/CVPRW.2017.95.
“Presentation attack detection algorithm for face and iris biometrics” (2014) pp. 1387–1391
Puhan NB, Sudha N, Hegde S (2011) A new iris liveness detection method against contact lens spoofing. Proc Int Symp Consum Electron ISCE:71–74. https://doi.org/10.1109/ISCE.2011.5973786
Raghavendra R, Busch C (2014) Presentation attack detection on visible spectrum iris recognition by exploring inherent characteristics of Light Field Camera. IJCB 2014–2014 IEEE/IAPR Int Jt Conf Biometrics. https://doi.org/10.1109/BTAS.2014.6996226
Raghavendra R, Busch C (2015) Robust scheme for iris presentation attack detection using multiscale binarized statistical image features. IEEE Trans Inf Forensics Secur 10(4):703–715. https://doi.org/10.1109/TIFS.2015.2400393
Raja KB, Raghavendra R, Busch C (2015) “Presentation attack detection using Laplacian decomposed frequency response for visible spectrum and Near-Infra-Red iris systems,” 2015 IEEE 7th Int. Conf. Biometrics Theory, Appl. Syst. BTAS 2015, https://doi.org/10.1109/BTAS.2015.7358790.
Ratha NK, Connell JH, Bolle RM (2001) An analysis of minutiae matching strength. Lect Notes Comput Sci (including Subser Lect Notes Artif Intell Lect Notes Bioinformatics) 2091 LNCS(2015):223–228. https://doi.org/10.1007/3-540-45344-x_32
Ribeiro E, Uhl A (2017) Exploring Texture Transfer Learning via Convolutional Neural Networks for Iris Super Resolution. Lect Notes Informatics (LNI), Proc - Ser Gesellschaft fur Inform (00736):0–4. https://doi.org/10.23919/BIOSIG.2017.8053505
Rigas I, Komogortsev OV (2015) Eye movement-driven defense against iris print-attacks. Pattern Recogn Lett 68:316–326. https://doi.org/10.1016/j.patrec.2015.06.011
Rui Z, Yan Z (2019) A survey on biometric authentication: toward secure and privacy-preserving identification. IEEE Access 7(c):5994–6009. https://doi.org/10.1109/ACCESS.2018.2889996
Sardar M, Banerjee S, Mitra S (2020) Iris segmentation using interactive deep learning. IEEE Access 8:219322–219330. https://doi.org/10.1109/ACCESS.2020.3041519
Selwal A, Gupta S, Kumar S (2016) A Scheme for Template Security At Feature Fusion Level in Multimodal Biometric System. Adv Sci Technol Res J 10(31):23–30. https://doi.org/10.12913/22998624/64062
Selwal A, Gupta SK, Surender (2017) Low overhead octet indexed template security scheme for multi-modal biometric system. J Intell Fuzzy Syst 32(5):3325–3337. https://doi.org/10.3233/JIFS-169274
Sequeira AF, Oliveira HP, Monteiro JC, Monteiro JP, Cardoso JS (2014) “MobILive 2014 - Mobile Iris Liveness Detection Competition,” IJCB 2014–2014 IEEE/IAPR Int. Jt. Conf. Biometrics, https://doi.org/10.1109/BTAS.2014.6996290.
Sharma D, Selwal A (2021) An intelligent approach for fingerprint presentation attack detection using ensemble learning with improved local image features, no. 0123456789. Springer US.
Sharma D, Selwal A (2021) FinPAD: State-of-the-art of fingerprint presentation attack detection mechanisms, taxonomy and future perspectives. Pattern Recogn Lett 152(March 2005):225–252. https://doi.org/10.1016/j.patrec.2021.10.013
Sharma D, Selwal A (2021) HyFiPAD : a hybrid approach for fingerprint presentation attack detection using local and adaptive image features. Vis Comput 38(0123456789):2999–3025. https://doi.org/10.1007/s00371-021-02173-8
Silva P, Luz E, Baeta R, Pedrini H, Falcao AX, Menotti D (2015) “An Approach to Iris Contact Lens Detection Based on Deep Image Representations,” Brazilian Symp. Comput. Graph. Image Process., vol. 2015-Octob, pp. 157–164https://doi.org/10.1109/SIBGRAPI.2015.16.
Simonyan K, Zisserman A (2015) “Very deep convolutional networks for large-scale image recognition,” 3rd Int. Conf. Learn. Represent. ICLR 2015 - Conf. Track Proc., pp. 1–14
Singh M, Singh R, Ross A (2019) A comprehensive overview of biometric fusion. Inf Fusion 52:187–205. https://doi.org/10.1016/j.inffus.2018.12.003
Szegedy C, Vanhoucke V, Ioffe S, Shlens J, Wojna Z (2016) Rethinking the Inception Architecture for Computer Vision. Proc IEEE Comput Soc Conf Comput Vis Pattern Recognit 2016:2818–2826. https://doi.org/10.1109/CVPR.2016.308
Tan M, Le QV (2019) “EfficientNet: Rethinking model scaling for convolutional neural networks,” 36th Int. Conf. Mach. Learn. ICML 2019, vol. 2019-June, pp. 10691–10700
Tann H, Zhao H, Reda S (2019) A resource-efficient embedded iris recognition system using fully convolutional networks. ACM J Emerg Technol Comput Syst 16(1):1–23. https://doi.org/10.1145/3357796
Tapia JE, Gonzalez S, Busch C (2022) Iris liveness detection using a Cascade of dedicated deep learning networks. IEEE Trans Inf Forensics Secur 17:42–52. https://doi.org/10.1109/TIFS.2021.3132582
Therar HM, Mohammed LDEA, Ali APDAJ (2021) “Multibiometric System for Iris Recognition Based Convolutional Neural Network and Transfer Learning,” IOP Conf. Ser. Mater. Sci. Eng., vol. 1105, no. 1, p. 012032, https://doi.org/10.1088/1757-899x/1105/1/012032.
Tirunagari S, Poh N, Windridge D, Iorliam A, Suki N, Ho ATS (2015) Detection of face spoofing using visual dynamics. IEEE Trans Inf Forensics Secur 10(4):762–777. https://doi.org/10.1109/TIFS.2015.2406533
Tobji R, Di W, Ayoub N (2019) FMnet: Iris segmentation and recognition by using fully and multi-scale CNN for biometric security. Appl Sci 9(10):1–17. https://doi.org/10.3390/app9102042
Varkarakis V, Bazrafkan S, Corcoran P (2018) “A deep learning approach to segmentation of distorted iris regions in head-mounted displays,” 2018 IEEE Games, Entertain. Media Conf. GEM 2018, pp. 402–406 https://doi.org/10.1109/GEM.2018.8516446
Yadav D, Kohli N, Doyle JS, Singh R, Vatsa M, Bowyer KW (2014) Unraveling the effect of textured contact lenses on iris recognition. IEEE Trans Inf Forensics Secur 9(5):851–862. https://doi.org/10.1109/TIFS.2014.2313025
Yambay D, Doyle JS, Bowyer KW, Czajka A, Schuckers S (2014) “LivDet-iris 2013 - Iris Liveness Detection Competition 2013,” IJCB 2014–2014 IEEE/IAPR Int. Jt. Conf. Biometrics, https://doi.org/10.1109/BTAS.2014.6996283.
Yambay D, Czajka A, Ii F (2015) “LivDet-Iris 2015 – Iris liveness detection competition 2015 University of Naples”
Yambay D et al. (2018) “LivDet iris 2017 - Iris liveness detection competition 2017,” IEEE Int. Jt. Conf. Biometrics, IJCB 2017, vol. 2018-Janua, pp. 733–741, https://doi.org/10.1109/BTAS.2017.8272763.
Yang Y, Shen P, Chen C (2019) A robust iris segmentation using fully convolutional network with dilated convolutions. Proc - 2018 IEEE Int Symp Multimedia, ISM 2018:9–16. https://doi.org/10.1109/ISM.2018.00010
Zhang H, Sun Z, Tan T (2010) Contact lens detection based on weighted LBP. Proc - Int Conf Pattern Recognit:4279–4282. https://doi.org/10.1109/ICPR.2010.1040
Zhang H, Sun Z, Tan T, Wang J (2011) “Learning hierarchical visual codebook for Iris liveness detection”
Zhao Z, Kumar A (2017) “Towards More Accurate Iris Recognition Using Deeply Learned Spatially Corresponding Features,” Proc. IEEE Int. Conf. Comput. Vis., vol. 2017-Octob, pp. 3829–3838, https://doi.org/10.1109/ICCV.2017.411.
Zhao Z, Kumar A (2019) A deep learning based unified framework to detect, segment and recognize irises using spatially corresponding features. Pattern Recogn 93:546–557. https://doi.org/10.1016/j.patcog.2019.04.010
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
All the authors declare that they do not have any conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Verma, P., Selwal, A. & Sharma, D. A survey on data-driven iris spoof detectors: state-of-the-art, open issues and future perspectives. Multimed Tools Appl 82, 19745–19792 (2023). https://doi.org/10.1007/s11042-022-14014-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-14014-4