Abstract
Human iris being the most stable biometric modality suffers from presentation attacks like colored textured contact lenses and print attacks that obfuscate the natural iris texture. The paper presents discrete orthogonal moment-based invariant feature-set comprising of Tchebichef, Krawtchouk and Dual-Hahn moments which are extracted at localized iris regions to capture local intensity distributions of the iris texture. The orthogonal moment-based feature-set is made rotation, translation and scale-invariant in order to accommodate for geometric transformations when images are acquired in uncontrolled environment. The performance of the proposed techniques is evaluated using four publicly available iris spoofing databases: IIITD-Contact Lens Iris, IIITD Iris Spoofing, Clarkson LivDet 2015 and Warsaw LivDet 2015. The textured contact lens detection rate of 100% for IIITD-CLI and 99.48% for Clarkson datasets is achieved, respectively. Similarly, print+scan and print+capture attacks are detected with 99% and 98.93% accuracy for IIS datasets, respectively. The print attacks are detected with 99.63% and 98.89% accuracy for Clarkson and Warsaw datasets, respectively. The proposed techniques thus, prove to be effective in terms of contact lens and print attacks detection when acquired using multiple sensors.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Human iris identification is being used in various large-scale security applications like the Aadhar project in India [49] and in UAE border crossing [46]. Iris being the most stable biometric modality [17] because of its unique texture still suffers from presentation attacks where an imposter impersonates a genuine user. Iris texture was proposed as a biometric modality for the first time in 1987 by Flom and Safir [5]. After that, Daugman made first commercial biometric algorithm based on iris recognition which is still widely used in many commercial systems [3]. Iris is affected by various covariates like usage of colored textured contact lenses [51], consumption of alcohol [1] and pupil dilation [14]. However, the presence of textured contact lenses is more prevalent for Presentation Attack Detection (PAD) with the increase of 3–5% in the number of contact lens wearers worldwide [37]. They are used to obfuscate the natural iris texture by superimposing the pattern and color of the textured contact lens onto the natural iris which affects the overall iris recognition accuracy of the system. However, soft transparent contact lenses do not tamper the natural iris pattern. Other than this, print attacks are another way to iris spoofing where a printed iris image is presented to the biometric system for impersonating an already enrolled user [11, 25]. In this, either the iris pattern is first printed by a high-quality printer and then scanned which is called print+scan or the photo is captured by a scanner which is called print+capture [11]. Detection of iris spoofing is the first step to improve the reliability of an iris recognition system.
The manuscript deals with an important and challenging issue of Presentation Attack Detection (PAD) method for iris recognition. In today’s scenario, biometric systems are being used in high-surveillance applications where security is the main concern. PAD is a challenge that researchers are working on these days to have more secure biometric systems. Recent research revealed that there are no existing methods that can significantly reduce spoofing attacks. Very few researchers have provided effective techniques which work for both iris spoofing attacks i.e. contact lenses and print attacks acquired using multiple sensors.
The manuscript deals with cross-sensor iris spoofing problem via contact lenses and print attacks when acquired using multiple sensors. Acquisition of iris images using multiple sensors also affects the overall performance of the iris recognition system. The first motive of the paper is thus, to develop a robust method that can detect any kind of iris spoofing attacks using different sensors. Thus, the focus of the paper is on iris spoofing detection acquired with multiple sensors using discrete orthogonal moment-based features which are invariant to noise and rotation. The paper introduces a novel method of constructing an orthogonal feature-set consisting of Krawtchouk, Tchebichef and Dual-Hahn moments extracted on localized 32 × 32 normalized iris texture regions. An orthogonal feature-set is deployed as these provide minimum information redundancy with sufficient number of features to discriminate between large number of subjects. For this, adequate number of features have been selected which can best represent the iris textural pattern. A critical analysis is done regarding the optimum selection of moment order and the number of features that can give best classification results.
With iris recognition systems being affected by various covariates like colored textured contact lenses and print attacks, there is a need of robust algorithms that can easily detect presentation attacks so as to make the system more reliable for use in large-scale applications. Acquiring iris samples using different sensors also affects the overall performance of the biometric system where samples acquired from one sensor are matched against another. Thus, the key motivation of the paper is to develop an effective technique that can easily detect presentation attacks acquired using different sensors. The main objectives of the paper are as follows:
- (1)
The paper proposes a robust method that can easily detect colored textured contact lenses as well as print attacks acquired using multiple sensors.
- (2)
The paper introduces a novel method of constructing an orthogonal feature-set consisting of Krawtchouk, Tchebichef and Dual-Hahn moments extracted on localized 32 × 32 normalized iris texture regions. An orthogonal feature-set is deployed as these provide minimum information redundancy with sufficient number of features to discriminate between large number of subjects used in this work. For this, adequate number of features have been selected which can best represent the iris textural pattern. A critical analysis is done regarding the optimum selection of moment order and the number of features that can give best results. A feature-set constructed from discrete orthogonal moments can effectively represent local intensity variations which prove to be useful for iris spoofing attack classification. To the best of our knowledge, this is the first paper to exploit the property of developing a feature-set which is orthogonal, has invariance properties and represents local intensity variations that works best with iris texture patterns which is characterized by high-degree of randomness and irregularities.
- (3)
This feature-set has been made invariant to rotation, scale and translation as iris spoofed samples undergo geometric variations when acquired.
- (4)
The proposed method is evaluated using performance metrics namely Correct Classification Rate (CCR), Attack Presentation Classification Error Rate (APCER), Bonafide Presentation Classification Error Rate (BPCER), Average Classification Error Rate (ACER), DET (Decision Error Threshold) Curve and Detection Equal Error Rate (D-EER) and the performance is validated by comparing it with recently proposed algorithms available in the literature.
The paper has been organized as follows: Section II summarizes the research work done till date on iris spoofing. Section III discusses the details on the introduction of the discrete orthogonal moment-based polynomials along with the proposed technique used in the manuscript for detecting iris spoofing attacks. Section IV demonstrates experiments performed by taking various spoofed samples from multiple sensors using proposed methodology and a comparison is drawn with the techniques available in the literature. Section V concludes the manuscript along with possible future scope to make the proposed system more reliable and secure.
2 Related work
In 2003, Daugman introduced Fourier spectrum of the printed iris pattern which gave periodic iris pattern that occurs in dot matrix printing. These days the dot matrix printing is not used, thus making Fourier transform less reliable for PAD [2]. Recently, many researchers have implemented algorithms for iris spoofing detection. Yadav et al. proposed modified LBP (Local Binary Pattern) with SVM (Support Vector Machine) classification for textured contact lens detection using IIITD-Contact Lens Iris (IIITD-CLI) and Notre Dame Contact Lens databases. The textured contact lenses were detected with an accuracy of 95% and it was concluded that the removal and detection of contact lenses improves the reliability of the iris recognition system [51]. Hu et al. implemented regional features based on spatial pyramid for iris liveness detection on contact lens and print attack iris spoofing databases. The proposed methods gave minimum error rates when compared with other state-of-the-art methods [16]. Gupta et al. proposed LBP, HOG (Histogram of Oriented Gradients) and GIST with SVM classification for detection of iris spoofing via print attacks [11]. LBP was found to perform best giving PAD rate of above 95%. Kohli et al. implemented multi-order Zernike and LBP with variance for iris spoofing detection via contact lens and print attacks. The proposed method resulted in detection rate of 82.20% using combined iris spoofing database [31]. Kohli et al. analysed that colour cosmetic lenses degrade the performance of a biometric system with increase in false rejection using VeriEye. It was concluded that lens detection helps maintain the performance of the iris recognition system [30]. Menotti et al. proposed deep representation via convolutional networks and back-propagation for iris spoofing detection [34]. Silva et al. implemented deep representation through convolutional network with softmax regression for classification on IIITD-CLI database thus, achieving 30% performance gain as compared to other approaches [45]. Gragnaniello et al. proposed local descriptors based on microtextural features for iris liveness detection [9]. Nalla et al. proposed bi-spectral iris recognition which acquired both visible and near infrared with pixel-to-pixel correspondences. The Domain Adaption- Naïve Bayes Nearest Neighbor (DA-NBNN) with real-valued log-gabor phase features were extracted on IIITD-CLI database obtaining 89.92% accuracy [36]. Pala et al. implemented triplet convolutional network along with relative distance matching which proved to be effective for both photo-based and contact lens attacks [38]. Raghavendra et al. implemented deep convolutional neural network with fifteen layers for three-class classification of normal, soft and textured contact lenses on IIITD-CLI database. It showed an improvement of more than 10% in correct classification rate when compared to other state-of-the-art approaches [42]. Doyle et al. implemented modified LBP method which was applied to different iris regions at multiple scales for classifying no lens, soft lens and textured contact lens. Results gave 98% of textured contact lens detection rate on Notre Dame Contact Lens Database (NDCLD12) [4]. Sequeira et al. implemented a set of five features for liveness detection in a mobile scenario. These features included high frequency power, local contrast, global contrast, adapted frequency distribution rates and statistical texture analysis. The best features were selected using Sequential Forward Floating Selection (SFFS) which were classified using SVM, k-Nearest Neighbor (k-NN) and Discriminant Analysis (DA). The experiments were conducted on Biosec, Clarkson, NotreDame, MobBIOfake and Warsaw databases out of which Biosec gave best classification error of 2.0% using SVM [44]. Galbally et al. implemented 25 general image quality features to distinguish between fake and real iris images. The classification was done using Quadratic Discriminant Analysis (QDA). The experimental results were conducted on real images of CASIA-Iris V1 and WVU-Synthetic Iris databases along with self-developed ATVS-Fir database which consisted of 800 fake and 800 genuine iris samples. For ATVS-Fir database, 97% of samples were correctly classified. The synthetic iris samples gave False Fake Rate (FFR) of 4.2, False Genuine Rate (FGR) of 0.8 and Half Total Error Rate (HTER) of 2.1 [7]. Table 1 summarizes recent literature survey of promising algorithms for iris spoofing attack detection.
3 Proposed methodology
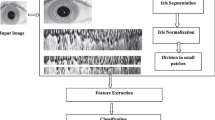
An iris recognition system has the following steps: 1) Image Acquisition 2) Iris Segmentation 3) Iris Normalization 4) Feature Extraction 5) Classification. The acquired iris sample is matched against the enrolled users resulting in either acceptance or rejection. The proposed methodology has been illustrated in Fig. 1.
3.1 Iris segmentation
The first step of iris recognition is to detect iris-pupil and iris-sclera boundary. For this, Circular Hough Transform (CHT) has been deployed which detects circles in an image and is insensitive towards noise [33].
where, (xi, yi), i = 1,2,3…..n are all edge points in an image. A binary edge map of the image is generated using Canny edge detector where each edge point is treated as the centre of the circle with varying radii. Iris being the largest circle with maximum number of edges is detected using CHT. The circumferential pixels are stored in an accumulator. CHT (xc, yc, r) = 1 is stored in accumulator, when CHT (xi, yi) lies on the perimeter of the circle else, CHT (xc, yc, r) = 0 is stored. The highest value stored in the accumulator corresponds to centre co-ordinates of iris.
3.2 Iris normalization
The segmented iris samples are transformed into fixed dimensions due to variations in illumination and acquisition of samples at varying distances. For normalizing segmented iris samples Daugman’s homogeneous rubber sheet model [3] is employed which transforms iris segmented image F (x, y) into polar co-ordinates (r, θ), where r ϵ [0, 1] and θ ϵ [0,2π]:
xp,yp and xI, yI are the pupil and iris co-ordinates, respectively. The normalized iris samples are shown in Fig. 2.
3.3 Feature extraction
Moments have been widely used by many researchers for applications like face recognition [43], gesture recognition [20,21,22,23, 40] and watermarking [48]. Hu for the first time proposed seven moment invariants for recognition [15]. Because of their non-orthogonal nature, there was maximum information redundancy which affected recognition performance. Teague introduced continuous orthogonal moments namely Zernike and Legendre which were rotation-invariant and orthogonal in nature but had numerical instabilities at higher orders [27, 28, 47]. To overcome this, discrete orthogonal moments like Tchebichef [23, 24, 26, 35] Krawtchouk [20,21,22,23,24, 26, 29, 53] and Dual-Hahn [23, 24, 26, 54] moments were introduced which worked in image co-ordinate space with no discretization errors and minimum information redundancy.
3.3.1 Tchebichef moments
These are derived from Tchebichef polynomials and can extract global features in an image by varying moment order. These are made translation and scale invariant [35].
The Tchebichef polynomial is defined as:
To avoid numerical instabilities, normalized Tchebichef moments are derived [35]:
For an image intensity function f (i,j) of size X × Y, the Tchebichef moments of order (r, q) is [35]:
where, \( {{}_3F}_2\left(m,m,o;p,q;r\right)={\sum}_{k=0}^{\infty}\frac{(m)_k{(n)}_k{(o)}_k{r}^k}{(p)_k{(q)}_k\left(k!\right)} \) is a hypergeometric function.where, (m)k is pochhammer symbol:
where, \( \rho \left(r;X\right)-(2r)!\left(\begin{array}{c}X+r\\ {}2r+1\end{array}\right) \)
3.3.2 Krawchouk moments
These are obtained from Krawtchouk polynomials associated with binomial functions. These are used to extract local features from a specific ROI in an image. These are made rotation, scale and translation invariant [53].
The rth order classical Krawtchouk polynomial is given by [53]:
where, i, r = 0, 1, 2……X, X ≥ 0, pϵ(0, 1), ak, r, p are Krawtchouk polynomial coefficients.
Here, 2F1 is a hypergeometric function which is given by:
where (m)k is a pochhammer symbol given by:
The normalized Krawtchouk polynomials are given by [53]:
The weighted Krawtchouk polynomials are given by:
The weight function is given by [53]:
The weighted Krawtchouk polynomials were derived in order to overcome numerical instabilities at higher orders.
The Krawtchouk moments of order (r + q) for an image intensity function f(i,j) is given by:
where, f(i,j) is of size X × Y and these are substituted for X-1 and Y-1. p1 and p2 are used for varying ROI in an image [53].
‘p1’ and ‘p2’ are used for ROI variation in horizontal and vertical directions. For p1 > 0.5, ROI shifts towards positive x-direction and for p1 < 0.5, it shifts towards negative x-direction. With p2 > 0.5, shifting occurs towards negative y-direction and with p2 < 0.5 it takes place towards positive y-direction. In this paper, ‘p1’ and ‘p2’ have been taken to be 0.5 so that the focus of the moment invariants is towards the centre of the image.
3.3.3 Dual-Hahn moments
Dual-Hahn moments can extract global as well as local features with rotation, scale and translation invariance as opposed to Tchebichef moments that extract global features and Krawtchouk moments that extract local features from a specific ROI of the image [54].
where, r = 0, 1, 2…. R − 1, p = a, a + 1……. b − 1
To avoid numerical fluctuations at higher orders, the Dual-Hahn polynomials are scaled using a weighted function which is given by [54]:
where,
For an image intensity function f (p,u) the Dual-Hahn moments with order (r,q) are calculated as [54]:
where,−0.5 < a < b, ∣ v ∣ < 1 + a, b = a + R, r, q = 0, 1……. . R − 1 and f(p,u) is R × R.
Feature Extraction is carried out using moment invariants which include discrete orthogonal moments i.e. Tchebichef (TM), Krawtchouk (KM) and Dual-Hahn moments (DM). In case of orthogonal moments, the image is projected onto a set of pair-wise orthogonal axes which minimize information redundancy and gives compact description of the image. The images are described in terms of moment-based orthogonal kernels which are real-values that represent features of a particular image. Based upon the moment order, different features are extracted for different orders. As the moment order increase, the features get added up which helps in discriminating between different classes.
3.3.4 Iris spoofed sample
Figure 3 shows the top views of discrete orthogonal basis polynomials for different moment orders. Visualization of the moment basis functions in the spatial domain. These basis functions are projected onto the image to give numerical values that represent features of an image. As the moment order increases, the number of zero-crossings increase which enhances the ability of the moments to represent the image. Dual-Hahn, Krawtchouk and Tchebichef polynomials behave as multi-frequency filter banks with polynomials having increased oscillations (zero-crossings) at higher orders. For both cases, horizontal and vertical edges are preserved at lower orders. However, Tchebichef moments have wider supports in terms of polynomial oscillations, thus capturing global information. But as the order increases, the polynomial oscillations become compact with local information capturing. In case of Krawtchouk moments the polynomials have wider supports at higher orders, thus capturing global information and compact support at lower orders, thus capturing local information. The Dual-Hahn moments act as Krawtchouk moments and Tchebichef moments, depending on its tuning parameters which are discussed in detail in this section. Further, it is seen that the enhancement is achieved up to a certain moment order, after which the recognition accuracy saturates. For discrete orthogonal feature-set, the recognition accuracy increases till 15th order after which it saturates. Also, to extract local information, the discrete orthogonal moment set is extracted for sub-images (32 equal sized (32 × 32 iris normalized sub-images).
The purpose is to extract sufficient number of features which can best represent different classes. Table 2 illustrates the feature-set based on moment-based methods. Tchebichef moments based on Tchebichef polynomials also act as global feature descriptors defined in the image co-ordinate space, are extracted till 15th order, thus representing details of the entire image for further classification. In case of Krawtchouk moments, local description pertaining to a specific ROI is preserved in an image. For this, the ROI is localized at the centre of the image (using ‘p1’ = ‘p2’ = 0.5) and features are extracted till 15th order representing the image in terms of discrete Krawtchouk polynomials. Dual-Hahn moments extract both global and local features depending on tuning parameters ‘a’ and ‘v’ through which ROI can be varied using eq. (20). In order to accommodate for geometric transformation and scale changes in iris images during acquisition, the discrete orthogonal moment feature-set is made rotation, scale and translation invariant [6].
With ‘a’,‘v’ > 0, local information is captured from a specific ROI. As the values of ‘a’ and ‘v’ increase, the ROI starts shifting from top-right to bottom-right corner of the image. Thus, by tuning ‘a’ = ‘v’ = 18 at 15th order the ROI is focused to the centre of the image. However, for global feature extraction of the entire image, the parameters are set to ‘a’ = ‘v’ = 0.
The normalized iris samples of size 512 × 64 are partitioned into non-overlapping 32 equal sub-regions each of size 32 × 32. At each patch, the feature-set till 15th order comes out to be 32 localized regions × 255 features till 15th order = 8160 features. However, in case of Dual-Hahn moments the feature-set is a fusion of 8160 local and 8160 global features [18, 19].


3.4 Classification
For classification, k-Nearest Neighbor (k-NN) is used which works best with large databases. It is based on the principle that the instances belonging to the same class are closer to each other. Manhattan distance [12] is calculated between the training and the testing samples. Based on majority voting, the testing samples are classified into their respective classes. Moment-based techniques contain features which are highly correlated with the same class and uncorrelated with a different class. Thus, k-NN works best with moment-based features for discriminating between different classes. The best recognition accuracy results for all the databases are shown by Manhattan distance at ‘k’ = 1. Thus, experiments have been performed using these parameters.
4 Results and discussions
The experiments have been conducted on MATLAB R2014a using Intel(R) Pentium(R) laptop with windows 7, 32-bit operating system at 2GHz with 4GB RAM memory using four publicly available iris spoofing databases: IIITD Contact Lens Iris (IITD-CLI) (consists of 6570 images from 101 subjects captured using Cogent dual iris sensor (CIS 202) and VistaFA2E single iris sensor) [30, 51], IIITD Iris Spoofing (IIS) (contains 4848 images acquired from 101 subjects with two types of print attacks: print+scan and print+capture) [11, 31], Clarkson LivDet 2015 (consists of 828 genuine images for 45 subjects, 1152 fake images from 7 subjects using 20 contact lenses and 1746 printed iris images) [52] and Warsaw LivDet 2015 (The testing set contains 2002 genuine and 3890 fake printed samples while the training set consists of 852 genuine and 815 printed fake images) [52].
4.1 Performance evaluation of the proposed technique
The proposed technique is evaluated on four publicly available presentation attack databases using performance indices: APCER, BPCER, ACER and D-EER. APCER incorrectly classifies spoofed images as normal images and BPCER misclassifies normal images as spoofed images. ACER gives the average of APCER and BPCER. D-EER is a point where both BPCER and APCER are equal. The lower the D-EER value, better will be the performance of the system.
For fair comparative analysis of the proposed approach with other techniques available in the literature, the databases have been divided using the same training-testing protocol as done by existing approaches.
The problem of PAD via contact lenses and print attacks has been approached through 3-class classification i.e. no lens, soft lens and textured lens for contact lenses and original, print+capture and print+scan for print attacks. Correct classification rate has been evaluated on four publicly available presentation attack databases. These include inter-sensor, intra-sensor and multi-sensor classification also.
4.1.1 Intra-sensor
In this case, the training as well as testing sets have been evaluated using the same type of sensors. By fusing discrete moments best recognition accuracy is observed. For IIITD-Cogent, 89.20% normal, 100% textured and 99.99% soft lenses are correctly detected. In case of IIITD-Vista, 87.90% normal, 100% textured and 99.98% soft lenses are correctly classified. For IIS (Print+Scan) Cogent, 89.60% normal, 96.56% textured and 90.43% transparent lenses are correctly detected. In case of IIS (Print+Scan) Vista, 92.70% normal, 96.67% textured and 89.67% transparent lenses are correctly classified. For IIS (Print+Capture) Cogent, 56.98% normal, 98.50% textured and 99.32% transparent lenses are correctly detected. In case of IIS (Print+Capture) Vista, 85.89% normal, 92.60% textured and 89.78% transparent lenses are correctly classified. For Clarkson LG, the average CCR has resulted in 98.48% with patterned contact lens and printed detection rate of 100% and 98.56%, respectively. For Clarkson Dalsa, the average CCR is 99.39% with patterned contact lens and printed detection rate of 100% and 99.42%, respectively. In case of Warsaw, CCR obtained is 99.39% with fake iris printout detection rate of 100%. The results are summarized in Tables 3 and 5 with moment-based method achieving superior results in comparison to other approaches.
4.1.2 Inter-sensor
In this, database trained on one sensor is tested on another sensor to evaluate cross-sensor performance of the proposed system. Tables 4 and 6 show the proposed moment-based techniques outperform existing techniques for cross-sensor iris recognition problem. When models trained on IIITD Cogent were tested on IIITD Vista, the average CCR was observed to be 99.20% with 100% of textured contact lenses correctly detected. In case of models trained on IIITD Vista and tested on IIITD Cogent, the average CCR improved to 99.06% with contact lens detection accuracy of 100%. When models trained on IIS (Print+Scan) Cogent were tested on IIS (Print+Scan) Vista, the average CCR obtained is 93.60% with an accuracy of 93.60% contact lens detection. In case of models trained on IIS (Print+Scan) Vista and tested on IIS (Print+Scan) Cogent, the average CCR is 91.80% with contact lens detection accuracy of 93.78%. Similarly, in case of Print+Capture attack, models trained on Cogent and tested on Vista showed CCR of 93.35% with contact lens detection accuracy of 95.94%. When trained on Vista and tested on Cogent, the average CCR dropped to 92.57% with contact lens detection accuracy 93.89%. When models trained on Clarkson LG were tested on Clarkson Dalsa, the average CCR obtained is 99.81% with an accuracy of 100% of contact lens and print attack detection. In case of models trained on Clarkson Dalsa and tested on Clarkson LG, the average CCR is 99.98% with contact lens and print attack detection accuracy of 100%.
4.1.3 Multi-sensor
The inter-sensor and intra-sensor results indicate that the proposed system performs well for cross-sensor iris recognition system. In case of multi-sensor classification, the training dataset contains images from multiple sensors and the testing dataset contains images from the same set of multiple sensors. Tables 4 and 6 indicate that a high CCR is obtained even when database consists of images from multiple sensors. In case of IIITD combined database, fusion of discrete moments gives an average CCR of 99.89% and contact lens detection accuracy of 100%. For IIS combined database, average CCR of 95.45% with contact lens detection accuracy of 94.75% is obtained. For Clarkson combined database, the detection rate of patterned contact lenses and print attacks obtained is 99.74% and 98.46%, respectively. For a 3-class classification problem results of all the iris spoofing databases are summarized in Table 6. In case of IIITD and IIS combined databases, the textured contact lens can be easily detected with 98.90% and 96% accuracy, respectively. Both Print+Scan and Print+Capture attacks can be easily detected with 99% and 98.93% accuracy, respectively thus giving competent results. The patterned contact lenses and printed fake images in case of Clarkson database give recognition accuracy of 99.48% and 99.63%, respectively (Table 7).
Fake printouts of iris images in Warsaw dataset are detected with 98.89% accuracy. Tables 8 and 9 illustrate that the ACER value of 4.15% and 1.11% for Clarkson Dalsa and LG, respectively outperforms other algorithms submitted for LivDet-Iris 2015 competition. For Warsaw dataset, ACER value of 0% is obtained. In case of IIITD and IIS databases, the results obtained are encouraging when compared to other approaches with ACER as low as 1.27% for IIITD Vista and 1.20% for IIS Vista. Table 10 compares D-EER values of presentation attack databases with other state-of-the-art techniques with proposed technique achieving lower D-EER values for all the databases. Figure 4 indicates the performance of the proposed system using DET curve by plotting APCER and BPCER with performance curves closer to lower left corner of the graph showing minimum errors for all the datasets. However, by fusing moment-based features, a superior performance is observed.
The results provided by existing research papers using SIFT, LBP and HOG do not provide invariant features and have redundant information involved in the features which results in poor accuracy. The redundancy in the feature-set results in overfitting thus, decreasing the accuracy performance. Also, these features have a large computation time.
However, in case of moment-based feature-set the image is projected onto a set of pair-wise orthogonal axes which minimize information redundancy and gives compact description of the image. This feature-set is further made invariant to rotation, scale and translation because of image scale variations and geometrical transformations that are embedded in iris images when acquired. Iris spoofed texture contains irregular and random patterns for which features capturing local intensity variations prove to be more effective than those which extract features from the entire image that work well with well-defined shape-based applications.
The orthogonal moment-based features provide compact description with invariance properties of rotation, scale and translation which are extracted from localized iris textural patterns emphasizing on local intensity distributions of the random and irregular iris spoofed texture. Table 11 compares the performance of the existing approaches which are applied using the proposed methodology with the proposed moment-based feature-set. Experimental results reveal that the proposed moment-based feature-set proves to be robust in presentation attack detection as it achieves superior performance results when compared with existing algorithms available in the literature.
5 Conclusions and future scope
The paper discusses iris spoofing attacks by which an imposter impersonates a genuine user. Thus, detection if iris spoofing attacks would make the system secure for practical applications. In this paper, discrete orthogonal moment-based invariant feature-set comprising of Tchebichef, Krawtchouk and Dual-Hahn moments is extracted at localized iris regions till 15th order. Results demonstrate that the features show textured contact lens detection rate of 100% for IIITD-CLI and 99.48% for Clarkson datasets, respectively. Similarly, print+scan and print+capture attacks are detected with 99% and 98.93% accuracy for IIS datasets, respectively. The print attacks were detected with 99.63% and 98.89% accuracy for Clarkson and Warsaw datasets, respectively. Experiments suggest that iris spoofing detection improves the reliability of the biometric system.
However, various possible future directions can be explored to make the system more secure and reliable. The performance of the iris spoof attack detection can be further improved by using deep convolutional neural networks for learning complex patterns more deeply when working on different spoofed samples. Also, the performance of the iris biometric system degrades when an unknown spoofing attack is encountered. This limits its application for real world when the nature of attacks is unpredictable. Therefore, effective and generalized algorithms need to be proposed that can detect unpredictable or unseen spoofing attacks by designing mathematical models of spoofs characterized by different materials and techniques like an artificial eye ball, a printed or video image and an eye removed from the authenticated user. Real world applications require a robust iris scanning system that uses surveillance cameras that can track the activities and identify individuals from a distance. Developing effective iris scanning systems that can scan multiple moving individuals at a distance of several feet is also an interesting future research direction. In addition to this, the biometric templates can be exploited to create synthetic spoofing databases. This threat can be addressed by using cancelable biometrics which means a non-invertible mathematical transformation is applied and only the transformed biometric template is stored through which biometric trait cannot be procured. Another solution could be using cryptographic keys for biometric templates to protect the user’s privacy.
References
Arora SS, Vatsa M, Singh R, Jain A (2012) Iris recognition under alcohol influence: A preliminary study”, 5th IEEE IAPR International Conference on Biometrics (ICB), pp. 336–341
Daugman J (2003) Demodulation by complex-valued wavelets for stochastic pattern recognition. Int J Wavelets Multiresolution Inf Process 1(1):1–17
Daugman J (2004) How iris recognition works. IEEE Transactions on Circuits and Systems for Video Technology 14(1):21–30
Doyle JS, Flynn PJ, Bowyer KW (2013) Automated classification of contact lens type in iris images. International Conference on Biometrics (ICB):1–6
Flom L, Safir A (1987) Iris recognition system. U.S. Patent 4 641 349
Flusser J, Suk T, Zitová B (2016) 3D Moment Invariants to translation, rotation, and scaling. 2D and 3D Image Analysis by Moments 96
Galbally J, Marcel S, Fierrez J, J. (2014) Image quality assessment for fake biometric detection: Application to iris, fingerprint, and face recognition. IEEE Trans Image Process 23(2):710–724
Gan J, Liang Y (2005) Applications of wavelet packets decomposition in iris recognition. Advances in Biometrics. Berlin, Germany: Springer-Verlag:443–449
Gragnaniello D, Poggi G, Sansone C, Verdoliva L (2015) An investigation of local descriptors for biometric spoofing detection. IEEE Transactions on Information Forensics and Security 10(4):849–863
Gragnaniello D, Poggi G, Sansone C, Verdoliva L (2015) Local contrast phase descriptor for fingerprint liveness detection. Pattern Recogn 48(4):1050–1058
Gupta P, Behera S, Vatsa M, Singh R (2014) On iris spoofing using print attack. 22nd IEEE International Conference on Pattern Recognition:1681–1686
Han M, Pei J (2011) Data Mining: Concepts and Techniques, 3rd edn. Morgan Kaufmann Publishers, San Francisco
He X, An S, Shi P (2007) Statistical texture analysis-based approach for fake Iris detection using support vector machines. Proc IAPR Int Conf Biometrics:540–546
Hollingsworth K, Bowyer KW, Flynn PJ (2009) Pupil dilation degrades iris biometric performance. Comput Vis Image Underst 113(1):150–157
Hu MK (1962) Visual Pattern Recognition by Moment Invariants. IRE Transactions on Information Theory 8(2):179–187
Hu Y, Sirlantzis K, Howells G (2016) Iris liveness detection using regional features. Pattern Recogn Lett 82(2):242–250
Jain AK, Ross AA, Nandakumar K (2011) Introduction to biometrics. Springer Science & Business Media, Berlin
Kaur B (2019) Discrete Orthogonal Moments for iris recognition https://www.mathworks.com/matlabcentral/fileexchange/72412-discrete-orthogonal-moments-for-iris-recognition. MATLAB Central File Exchange. Retrieved August 15, 2019
Kaur B (2019). Dual-Hahn mOMENTS. https://www.mathworks.com/matlabcentral/fileexchange/72413-dual-hahn-moments. MATLAB Central File Exchange. Retrieved August 15, 2019
Kaur B, Joshi G (2016) Lower Order Krawtchouk Moment-Based Feature-Set for Hand Gesture Recognition. Advances in Human-Computer Interaction, Hindawi Publications 2016(2016):1–10
Kaur B, Joshi G, Vig R (2015) Analysis of shape recognition capability of Krawtchouk moments. IEEE International Conference on Computing, Communication and Automation:1085–1090
Kaur B, Joshi G, Vig R (2017) Indian sign language recognition using Krawtchouk moment-based local features. The Imaging Science Journal 65(3):171–179
Kaur B, Joshi G, Vig R (2017) Identification of ISL alphabets using discrete orthogonal moments. Wirel Pers Commun 95(4):4823–4845
Kaur B, Singh S, Kumar J (2018) Robust Iris Recognition using Moment Invariants. Wirel Pers Commun 99(2):799–828
Kaur B, Singh S, Kumar J (2018) A Study on Fake Iris Detection under Spoofing Attacks. J Eng Appl Sci 13(8):2049–2056
Kaur B, Singh S, Kumar J (2018) Fusing Iris and Periocular Recognition using Discrete Orthogonal Moment-based Invariant Feature-set. International Journal of Biometrics 10(4):352–367
Kaur B, Singh S, Kumar J (2018) Iris Recognition using Zernike Moments and Polar Harmonic Transforms. Arab J Sci Eng 43(12):7209–7218
Kaur B, Singh S, Kumar J (2019) Cross- Sensor Iris Spoofing Detection using Orthogonal Features. Comput Electr Eng 73:279–288
Kaur B, Singh S, Kumar J (2019) Orthogonal rotation invariant features for iris and periocular recognition. International Journal of Biometrics 11(2):160–176
Kohli N, Yadav D, Vatsa M, Singh R (2013) Revisiting Iris Recognition with Color Cosmetic Contact Lenses. Proc. 6th IAPR, pp. 1–5
Kohli N, Yadav D, Vatsa M, Singh R, Noore A (2016) Detecting medley of iris spoofing attacks using DESIST. IEEE 8th International Conference on Biometrics Theory, Applications and Systems:1–6
Ma L, Tan T, Wang Y, Zhang D (2003) Personal identification based on iris texture analysis. IEEE Trans Pattern Anal Mach Intell 25(12):1519–1533
Masek L (2003) Recognition of human iris patterns for biometric identification, pp. 1–7. http://www.csse.uwa.edu.au/opk/student projects/labor
Menotti D, Chiachia G, Pinto A, Schwartz WR, Pedrini H, Falcao AX, Rocha A (2015) Deep representations for iris, face, and fingerprint spoofing detection. IEEE Transactions on Information Forensics and Security 10(4):864–879
Mukundan R, Lee PA (2001) Image Analysis by Tchebichef Moments. IEEE Trans Image Process 10(9):1357–1364
Nalla PR, Kumar A (2017) Toward More Accurate Iris Recognition Using Cross-Spectral Matching. IEEE Trans Image Process 26(1):208–221
Nichols JJ (2012) Annual Report: Contact Lenses. Available:http://www.clspectrum.com/articleviewer.aspx?articleID=107853, accessed 26 June 2017
Pala F, Bhanu B (2017) Iris Liveness Detection by Relative Distance Comparisons. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops:162–169
Pillai JK, Puertas M, Chellappa R (2014) Cross-sensor iris recognition through kernel learning. IEEE Trans Pattern Anal Mach Intell 36(1):73–85
Priyal SP, Bora PK (2013) A Robust Static Hand Gesture Recognition System using Geometry based Normalizations and Krawtchouk Moments. Pattern Recogn Lett 46(8):2202–2219
Raghavendra R, Raja KB, Busch C (2014) Ensemble of statistically independent filters for robust contact lens detection in iris images. ACM Proceedings of the 2014 Indian Conference on Computer Vision Graphics and Image Processing, pp. 24:1–24:7
Raghavendra R, Raja KB, Busch C (2017) ContlensNet: Robust Iris Contact Lens Detection Using Deep Convolutional Neural Networks. IEEE Winter Conference on Applications of Computer Vision:1160–1167
Rahman SM, Howlader T, Hatzinakos D (2016) On the selection of 2D Krawtchouk moments for face recognition. Pattern Recogn 54:83–93
Sequeira AF, Murari J, Cardoso JS (2014) Iris liveness detection methods in the mobile biometrics scenario. International Joint Conference on Neural Networks (IJCNN):3002–3008
Silva P, Luz E, Baeta R, Pedrini H, Falcao AX, Menotti D (2015) An approach to iris contact lens detection based on deep image representations. 28th IEEEE SIBGRAPI Conference on Graphics, Patterns and Images:157–164
Tan CW, Kumar A (2013) Adaptive and localized iris weight map for accurate iris recognition under less constrained environments. Proc IEEE 6th Int Conf Biometrics, Theory Appl Syst (BTAS):1–7
Teague MR (1980) Image Analysis via the General Theory of Moments. J Opt Soc Am 70(8):920–930
Tsougenis ED, Papakostas GA, Koulouriotis DE, Tourassis VD (2012) Performance Evaluation of Moment-based Watermarking Methods: A Review. J Syst Softw 85(8):1864–1884
UID Authority of India (2012) Role of biometric technology in Aadhaar enrollments. Available : http://uidai.gov.in/images/FrontPageUpdates/role_of_biometric_technology_in_aadhaar_jan21_2012.pdf. accessed 26 June, 2017
Wei Z, Qiu X, Sun Z, Tan T (2008) Counterfeit Iris detection based on texture analysis. Proc 18th Int Conf Pattern Recognit:1–4
Yadav D, Kohli N, Doyle J, Singh R, Vatsa M, Bowyer K (2014) Unraveling the Effect of Textured Contact Lenses on Iris Recognition. IEEE Transaction on Information Forensics and Security 9(5):851–862
Yambay D, Walczak B, Schuckers S, Czajka A (2017) LivDet-Iris 2015 - Iris Liveness Detection. IEEE International Conference on Identity, Security and Behavior Analysis:1–6
Yap PT, Raveendran P, Ong SH (2003) Image analysis by Krawtchouk moments. IEEE Trans Image Process 12(11):1367–1377
Yap PT, Raveendran P, Ong SH (2007) Image analysis using Hahn moments. IEEE Trans Pattern Anal Mach Intell 29(11):2057–2062
Zhang H, Sun Z, Tan T (2010) Contact lens detection based on weighted LBP. Proc 20th Int Conf Pattern Recognit:4279–4282
Acknowledgments
The authors would like to acknowledge Indraprastha Institute of Information and Technology, Delhi (IIITD), Clarkson University, USA and Warsaw University of Technology, Poland for providing IIITD-CLI, IIS, Clarkson and Warsaw iris spoofing databases used in this work.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kaur, B. Iris spoofing detection using discrete orthogonal moments. Multimed Tools Appl 79, 6623–6647 (2020). https://doi.org/10.1007/s11042-019-08281-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08281-x