Abstract
Urban water supply systems (UWSS) are generally composed of water sources, transmission pipes, treatment plants, and distribution networks from source to tap and usually are exposed to variety of uncertain threatening hazards. These threats can be divided to three main groups of natural, human-made, and operational hazards which affect either water quantity or water quality. In order to evaluate the reliability of water supply systems, risk assessment tools must be used to identify threats, their probability, and consequences and vulnerabilities of each element of these systems against the hazards. Due to the complexity and uncertainties affecting water supply systems and threatening hazards, a comprehensive and effective risk assessment method is required. In this study, an integrated fuzzy hierarchical risk assessment model for water supply systems (IFHRA-WSS) is proposed to assess hazards in a complex UWSS using a systematic approach incorporating both water quantity and quality issues. This model uses a hierarchical framework for breaking down the UWSS infrastructures to their interrelated elements to reduce the overall complexity of the system. It also considers uncertainties using Fuzzy Logic approach. Effects of functional interdependencies between different components of the system have also been considered in the vulnerability analysis. IFHRA-WSS incorporates the contributions of urban water experts in a group risk assessment procedure in a way that they can be easily expressed in terms of the qualitative and quantitative risk measures. Efficiency of this model has been examined in a case study which includes a large part of a drinking water supply system in a major city in Iran. This system includes all the elements of the UWSS from the delivery point to the consumption point. In the case study, different components and subcomponents of this system have been ranked based on their estimated risk values. It is envisaged that the results of the proposed model can help the decision makers to plan for effective risk mitigation measures.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
UWSS consist of different strategic components each having different roles in delivering water to the consumers with acceptable quantity and quality. These roles can be well defined in the framework of “Water Safety” i.e. water supply that protects water availability and human health with a high degree of practical certainty. A water supply system is composed of different components and subcomponents. These components and their relative subcomponents are exposed to variety of uncertain natural, human related, and operational threats, mainly because most of them are spatially diverse and accessible. These threats can affect both water quantity and quality in different elements of UWSS. These effects can be quantified taking into account three parameters: probability of hazards, consequences of hazards, and vulnerabilities of the facilities against these hazards which can be evaluated through risk assessment approaches.
There are different definitions for risk assessment in the literature (Huang 2009; Aven 2011), but as it was mentioned earlier, in one of the important and useful definitions, risk measure is a function of specific hazard probability (likelihood) and also its attributed consequences which are usually proportional to the system vulnerabilities against the hazards (Torres et al. 2009; Huipeng 2007; Kaplan 1997). Likelihood represents the characteristics of a hazard or threat; consequence is a function of hazard intensity and system condition, and vulnerability shows the property of an asset that is influenced by the hazard or threat. Risk assessment of a water supply system should be initiated by defining a general objective of how to reduce the risk for the water utility. A clear scope of the analysis should be defined in order to calculate the hazard risk value in qualitative or quantitative scales.
Based on the definitions prepared by Huang (2009), there are two concepts of integrated “risk assessment” which refers to a holistic approach and “Integrated risk” assessment which indicates that the integration degree of a risk is not low. Integrated risk assessment requires contributions of stakeholders, owners, consumers, etc. Therefore, risk assessment procedure is a group evaluating and decision making procedure. Furthermore, due to the complexities of UWSS and uncertainties affecting them and the threatening hazards, effective risk assessment is hard to accomplish by using most of the available risk assessment tools. Some models can be found in the literature, which are still being used by water utilities for risk assessment. Among them Fault Tree Analysis (Mays 2004), Markov models (Tidwell et al. 2005), Monte Carlo simulation (Rausand and Høyland 2004), and Fuzzy risk assessment (Sadiq et al. 2004) have been used in different cases in recent years. Some useful guidelines have also been prepared for water supply system risk management such as Water Safety Plans (WHO 2004), Water Framework Directive (European Commission 2000), the Bonn Charter for Safe Drinking Water (IWA 2004), Primer for Design of Commercial Buildings to Mitigate Terrorist Attacks (FEMA 2003), RAMCAP (ASME 2006), etc.
In this part of the introduction, previous studies about risk assessment in the UWSS are briefly described and compared with the proposed approach in this paper. Sadiq et al. (2004) used fuzzy numbers to represent the likelihood and severity associated with water quality related risks in water distribution networks. They proposed an aggregative risk analysis procedure for the overall system. In their work, fuzzy numbers have been subjectively determined and then an aggregation method has been used to obtain the risks associated with water quality.
Tidwell et al. (2005) proposed a Markov Latent Effects modeling method, in which the Human caused threats in water supply systems were decomposed into the subsystems or decision elements. Each decision element represented a single factor influencing the likelihood that a threat yields its intended consequence. Lee et al. (2006) focused on drinking water quality issues and presented a model for cancer risk assessment using the statistical analysis, Monte Carlo simulation and sensitive analysis. They also applied this model in Taiwan as a part of decision making framework for drinking water safety plan. Huipeng (2007) presented a fuzzy hierarchical risk assessment method taking into account likelihood and severity of different hazards. Aggregative risk evaluation of UWSS from source to tap was carried out without considering the effect of different subcomponents vulnerabilities in risk assessment. Furthermore, Fuzzy Fault Tree Analysis (FTA) was used for cause–effect analysis of failure in water delivery to a specific node in a hypothetical water distribution network.
Sadiq et al. (2007a, b) extended their previous work on fuzzy risk assessment of water quality in water distribution networks by using Dempster–Shafer theory of evidence. Their main purpose was to combine various sources of information to update risk analysis. They used Exponential Ordered Weighted Average (E-OWA) operators for incorporating different qualitative risk attitudes to obtain the unique risk value in the decision-making process. Lindhe et al. (2009) presented a risk assessment method based on Fault Tree analysis in which three failure states for raw water, treatment plant, and distribution network were combined together to estimate a representative risk of UWSS failure in Götenborg city in Sweden. Their model was capable of incorporating effects of interdependencies between the three components in the risk assessment model while economic and social consequences of the hazards were not taken into account. Fares and Zayed (2010) designed a framework to evaluate the risk of water mains failure using Hierarchical Fuzzy Expert System (HFES) model. HFES defined fuzzy rules to quantify environmental, physical, operational failures as well as cost of repairs. Lee et al. (2009) presented a model in which fuzzy logic was used to assess potential contributing factors to water quality failures in a UWSS. The model was applied to a case study in North Battleford, Saskatchewan and sensitivity tests was carried out to demonstrate the model capability to assess individual contributing factors. Torres et al. (2009) presented a risk model developed by integration of GIS and EPANET model for risk analysis of water contamination due to external pollutant sources. It considered vulnerability as a function of accessibility and exposure of different demand nodes in water distribution networks. Cieślak (2011) applied a fuzzy logic based method for risk assessment of drinking water system by defining the fuzzy rules between likelihood of pipe failures, consequence of failure, and sensitivity of water mains (i.e. vulnerability).
Some of other works addressing the risk assessment in different main components of UWSS can be classified to studies focused on water resources (Weiler et al. 2000; Ostfeld 2001; Lund 2002; Salas et al. 2005; Qin 2012), water treatment plants (Haestad et al. 2003; Rahman and Zayed 2009) and transmission mains and water distribution networks (Clark and Deininger 2000; Sadiq et al. 2007a, b; Vairavamoorthy et al. 2007).
To summarize, it should be noted that most of the previous studies have either focused on specific components of water supply systems or some specific threatening hazards. In addition, they only consider water quality or water quantity aspects while both should be analyzed simultaneously in comprehensive urban water supply system risk assessment. Some methods that consider systems complexities, do not consider uncertainties and vice versa, while the level of uncertainty associated with a system is proportional to its complexity. Majority of previous researches have not used any expert based system or a certain database to elicit different parameters of risk and they have only used subjective fuzzy or crisp numbers. Another important issue in risk assessment process is consideration of functional and operational interdependencies between subcomponents in vulnerability analysis, which have not been addressed in most of the previous studies.
In this study, an Integrated Hierarchical Fuzzy Risk Assessment for Water Supply System (IHFRA-WSS) is introduced to assess risks in complex water supply systems based on Fuzzy approach. It considers both water quality and water quantity issues. This model not only uses a hierarchical structure to represent UWSS with less complexity, but also is able to consider functional interdependencies between subcomponents and their vulnerabilities. In different parts of the proposed risk assessment model, decision makers’ knowledge on urban water systems are incorporated systematically in order to have a flexible and expert based assessment. Using the aforementioned classification of Huang (2009), integrated “risk assessment” approach has been utilized in this study to propose a holistic approach for aggregation of risks from the lowest level of urban water hierarchical framework (i.e. hazards threatening water quantity and water quality) to the highest level (overall urban water system and its components and subcomponent). Furthermore, “Integrated risk” assessment approach has been utilized in this study to define risk item as a function of main factors (i.e. hazard probabilities, hazard consequences and vulnerabilities of components and subcomponents against these hazards) involving different related uncertainty sources. Efficiency of the proposed model has been examined in a large part of the drinking water system of Urmia City in northwest of Iran. The selected system consists of two water resources (surface and ground water), an old water treatment plant, and a large water distribution network. In Sects. 2 and 3 of this paper, general overview of hierarchical structure of complex water supply systems and different hazards which any UWSS might face, are described, respectively. In Sect. 4, proposed model (IHFRA-WSS) is presented in detail. The case study and attributed results are explained in Sect. 5 and further issues and conclusions are addressed in the final section.
2 Hierarchical structure and functional interdependencies
Each UWSS is unique and therefore detailed description of its components is an important part of risk analysis. The system description should include detailed knowledge of the following four main vulnerable components and their relative subcomponents (see Fig. 1):
-
1.
Water resources (e.g. rivers, wells, etc.)
-
2.
Main water transmission pipes or channels
-
3.
Water treatment plants
-
4.
Distribution network (including tanks, pumps, valves and pipes)
Most of the risk analysis models require some structured way to reasonably breakdown the system to different parts. A common way to break down a system for risk assessment is to define hierarchical model which reflects how the system is designed. The system should be broken down into components and subcomponents that can be handled effectively in the analysis (i.e. splitting Fig. 1 into subsystems such as water resource, treatment plants, and the distribution network). Hierarchical structures can also provide a possible framework for risk assessment. Within this hierarchy, risk levels of the urban water supply system are governed by the risk levels of its components as well as the hierarchical relationships among them. In this research, hazards form the lowest level of total hierarchical framework of risk assessment of water supply systems and subcomponents, components and UWSS constitute next levels of this framework from down to the top levels. Other issue which has not been addressed in the majority of researches on UWSS risk assessment is the functional interdependencies and cause–effect relationships between different subcomponents of UWSS. For example, in a typical UWSS, functionality of a treatment plant is directly dependent to the quality and quantity of water resources. In this study, the functional relationships between the system components have also been taken into account.
3 Threatening hazards
Another important step in the risk assessment is to identify hazardous events, in various parts of the system. A hazardous event is an event which can cause negative economical, environmental, and social effects on UWSS. There are different types of hazards that may increase the risk of reduced water quantity or water contamination. In this paper, the following three types of hazards have been considered that can adversely affect the performance of an UWSS:
-
1.
Natural hazards (i.e. earthquakes, floods, high speed winds, droughts and etc.)
-
2.
Human-caused hazards (i.e. chemical and biological terrorist attacks, sabotage and etc.)
-
3.
Operational hazards (i.e. natural deterioration of facilities, control failure, non-accurate monitoring, pipes leakage and non-accurate design related problems, etc.)
Each part of UWSS might face one or more of these failures depending on its operational, environmental, economical, social and geographical conditions. As it was mentioned before, in this paper, hazards are the lowest level of the hierarchical framework of risk assessment below the components and subcomponents levels of UWSS. Figure 2 shows an example of hazards that may threaten water quantity and quality in water treatment plants (WTP). Similar breakdown should be designed for other main components of UWSS.
4 Methodology
This study adopts hierarchical framework to represent the relationships between the components of water supply systems and to develop hierarchical structure of the risk assessment model considering capability of handling complexities, uncertainties, and interdependencies. Fuzzy Sets Theory (FST), evidence reasoning theory of Dempster–Shafer, Fuzzy Cognitive Map (FCM) and Fuzzy Integrated Vulnerability Assessment Model (FIVAM) are integrated with these hierarchies to generate quantitative risk measures for different levels of UWSS. The proposed risk assessment model (IFHRA-WSS) composed of three modules: module 1: Hierarchical levels, module 2: Risk assessment process and module 3: Tools and activities which are shown in Fig. 3. Tools and activities are described briefly in Sect. 4.1 and formulations of IFHRA-WSS model are presented in Sect. 4.2.
4.1 Mathematical tools
4.1.1 Fuzzy Set Theory (FST)
Since Fuzzy Inference System (FIS) plays an important role in the proposed risk assessment methodology, theoretical background of the theory, triangular fuzzy numbers (TFNs), linguistic variables, and fuzzy rules are briefly presented in this section. The notion of fuzzy sets was introduced by Zadeh (1965). Fuzzy sets are sets with boundaries that are not precise, in other words, the membership in a fuzzy set is not a matter of affirmation or denial, but rather a matter of a degree. For the sake of simplification, triangular and trapezoidal membership functions are the most in use (Sachs and Tiong 2009). Most of the hazards cannot be predicted with an acceptable degree of accuracy. In addition, experts’ knowledge about these hazards consists of high uncertainty. In order to deal with these issues, FST has been proposed as an alternative measure. For risk analysis of UWSS failure, the membership function class type t (TFN) formulated in Eq. (1), has been utilized in this research for probability, consequences, and vulnerability parameters of risks.
The parameters a 1, a 2, and a 3, denote the smallest possible value, the most promising value, and the largest possible value, respectively. The fuzzy sets can be transformed into non-fuzzy values (crisp values) by various defuzzification methods. In this study, the Centroid Of Area (COA) method has been used which is also one of the most common defuzzification methods (Lee 1990):
where Z is the defuzzified value of fuzzy number A and μ A (z) is fuzzy membership degree of z.
4.1.2 Fuzzy rule-based system
Fuzzy rules are linguistic IF–THEN-statements that have the general form of “IF A THEN B” where A and B are (collections of) propositions containing linguistic variables. A is called the premise and B is the consequence of the rule. The use of linguistic variables and fuzzy IF–THEN-rules exploits the tolerance for imprecision and uncertainty. Fuzzy logic mimics the crucial ability of the human mind to summarize data and its focus on the decision-relevant information. In a more explicit form, if there are I rules each with K premises in a system, the ith rule has the following form:
where s represents the crisp or fuzzy inputs to the rule and A and B are linguistic variables. The operator \( \Uptheta \) can be AND or OR. For example, in the case of UWSS, a rule can be: “If in a given water treatment plant, an earthquake with high probability is expected to take place and the consequences of the earthquake is medium and vulnerability of water treatment plant against the earthquake is low, then the risk of water shortage is high”. In this paper, in order to estimate some important parameters of risk such as consequences of hazards and vulnerabilities of the components and subcomponents in UWSS, fuzzy rule-based method has been utilized.
4.1.3 Dempster–Shafer Theory of evidence
Once the risks of hazards in a water supply system have been determined, a proper aggregation method is necessary for risk evaluations of subcomponents, components, and the whole UWSS. In aggregative risk assessment, determination of subcomponents risks is a process of aggregating risks from multiple hazards. Similarly, determination of system risks is a process of aggregating risks from its subcomponents and components. Also as it mentioned earlier in this paper, UWSS risk assessment is a multi-analyst and experts problem and applying a suitable aggregation method to combine their opinions is also required. Some aggregation techniques include arithmetic averages, geometric averages, harmonic averages, maximum values, etc. In this research, Dempster–Shafer theory has been chosen for this purpose. Dempster–Shafer theory was first developed by Dempster (1967) and later extended and refined by Shafer (1976). It offers an alternative to the traditional probabilistic theory for the mathematical representation of uncertainty. The significant innovation of this method is that it allows allocation of probabilities to sets. The Dempster–Shafer theory does not require an assumption regarding the probability of the individual constituents of a set or interval. This is potentially valuable for evaluating risk in engineering applications where it is not possible to obtain a precise measurement from experiments, or where knowledge is obtained from experts. One of the benefits of Dempster–Shafer theory is its combination rule by which evidences/information from different sources are combined to determine a degree of belief (also referred to as a mass). The mass m(A) of A, expresses the proportion of all relevant and available evidence that supports the claim that the actual state belongs to A but to no particular subset of A. The combination of two sources 1 and 2 (m 12) based on two sets of A and B is calculated from the aggregation of two basic probability assignments for given sources 1 and 2 (m 1(A), m 2(B)) in the following manner (Shafer 1976):
in which K is called the degree of conflict. It represents the basic probability associated with the two conflicting sources (i.e. sources 1 and 2). This is determined by summing the products of the basic probability assignments of all sources where the intersection is null. In application of this theory in this study, these sources can be considered as risk of hazards, subcomponents, component and also different experts’ opinions about them. In order to combine two mass distributions with fuzzy focal elements (low, medium, high, …), Ishizuka et al. (1982) extended Dempster rule by taking into account the degree of intersection of two sets, J(A, B):
where,
where A i and B j , represent predefined risk grades i and j, respectively. J(A i , B j ) represents the partial intersections between two adjacent predefined risk categories i and j; m 12(C) denotes the combined degree to each risk level from two sources 1 and 2; m 1(A i ) denotes degree to risk category A i from source 1; and m 2(B j ) denotes degree to risk category j from source 2. If A i and B j are normal fuzzy sets (i.e. \( \mu_{{\max \,A_{i} }} (x) = \mu_{{\max \,B_{j} }} (x) = 1 \)) then \( J(A_{i} ,B_{j} ) = \max_{x} \left[ {\mu_{{A_{i} \cap B_{j} }} (x)} \right] \). In this study, seven predefined risk grades have been considered \( (i = j = 1,2, \ldots ,7) \) that are introduced later in the paper.
In the real word, all of the sources do not have equal credibility. Yager (2004) indicated that a source importance in the aggregation process is related to its credibility and suggested a credibility transformation function, which discounts evidence with a credibility factor or weight (W) and distributes the remaining evidence (1 − W) equally among n elements (number of data sources) as follows:
This method is used in this research to aggregate decision makers’ opinions as a group decision making method and risk values in different levels of hierarchical structure in IFHRA-WSS model with their attributed importance (W). In the case study of this research, each hazard has an individual importance in calculating risks of subcomponents and each expert or decision maker has an individual importance in aggregative risk assessment model. The latter can be estimated base on the experience and executive power in UWSS decision making procedure.
4.1.4 Fuzzy Cognitive Map (FCM)
Ezell et al. (2000) showed that an important component of risk assessment is to determine the vulnerability of a system. Vulnerability is defined as a measure of susceptibility to threat scenario(s). Vulnerability of urban water supply systems has not been adequately addressed in the literature. Ezell (2007) presented the Critical Infrastructure Vulnerability Assessment Model (I-VAM) for vulnerability assessment of drinking water systems against terrorist attacks by introducing some specific criteria. As it was mentioned earlier, an important issue in vulnerability assessment of infrastructures such as water supply systems is consideration of functional dependencies. For example, operation of water treatment plants has direct effects on water distribution networks because occurrence of any incident in this component can lead to widespread problems in water distribution networks. So it can be considered as a hidden vulnerability for water treatment plants and it should be added to the initial vulnerability of this component. Hence applying the vulnerability assessment model which is able to consider these interdependencies and estimate these hidden vulnerabilities, is necessary.
In this paper, FCM has been used to model the interdependencies between component and subcomponents, which was used previously by Akgun et al. (2010) to develop a model called Fuzzy Integrated Vulnerability Assessment Model (FIVAM). FIVAM can assess vulnerability of critical facilities. Akgun et al. (2010) used SMART method (Edwards 1971) as one of the useful Multi-Criteria Decision Making (MCDM) methods to estimate initial vulnerabilities based on aggregation of some vulnerability criteria. In this research, all of the initial vulnerabilities have been calculated by the fuzzy rule-based system.
FCMs are used to represent and to model the knowledge on the examining system. Existing knowledge on the behavior of the system is stored in the structure of nodes and interconnections of the map. Kosko (1986) was the first to associate cognitive maps to fuzzy logic by incorporating qualitative knowledge as fuzzy causal functions. Thus, FCM is a cognitive map where relationships among the elements derived from a given mental map, with their relative importance representing the magnitude of the functional causality of such elements. The graphical illustration of an FCM is a signed fuzzy graph with feedback, consisting of nodes and weighted interconnections (Fig. 4). Signed and weighted arcs connect various nodes representing the causal relationships that exist among concepts.
A typical formula for calculating the values of concepts of FCM is:
in which, C t i is the value of concept C i at step t. w ji is the weighted arc from C j to C i and f is a threshold function. w ji > 0 represents a positive causality, where an increase in the value of the ith concept causes an increase in the value of the jth concept. w ji < 0 represents a negative causality, where an increase in the value of the ith concept causes a decrease in the value of the jth concept. w ji = 0 illustrates the case that no causal relationship between the ith and jth concepts exists.
Two threshold functions are usually used. The unipolar sigmoid function (\( f(x) = \frac{1}{{(1 + e^{ - \lambda x} )}} \)) in which, λ > 0 determines the steepness of the continuous function. This function is used when the values of the concept lie in [0, 1]. When concepts can be negative and their values belong to the interval [−1, 1], tangent hyperbolic function (\( f(x) = \tan \,h(x) \)) is used. The initial values of the concepts in the input vector and the weighted arcs are set to specific values based on the expert’s believes. Afterwards, the system is free to interact. This interaction continues until the model reaches equilibrium at a fixed point. Previously, some researchers such as Akgun et al. (2010) presented fuzzy linguistic variable to describe the influence values (functional interdependency relationships). In this paper, a linguistic variable showing the degree of influence value among system functions has been defined. The classification of this linguistic variable is elicited by consulting with different experts. It should be noted that in this research, as it can be seen in Table 1 and Fig. 5, seven basic categories (i.e. extremely low, very low, slightly low, medium, slightly high, very high, and extremely high) are introduced to represent different uncertain parameters (e.g. functional interdependency, probability, vulnerability…).
4.1.5 Weighting approach
In different modules of the proposed risk assessment model (Fig. 3), determination of weights of some parameters representing their relative importance is necessary. These weights, defined by experts, are used for combining assessments in different levels of UWSS. For example, to estimate the overall risk of hazards which threaten water treatment plants, a set of weights should be assigned to hazards with respect to their importance in the risk assessment procedure. The general fuzzy linguistic variable (Table 1) has also been selected by experts. For the case of group decision making (multi-experts), different weights can be combined by application of Dempster–Shafer theory (W in Eq. 7).
4.2 IFHRA-WSS model
IFHRA-WSS is an expert and data based risk assessment model which aggregates FST, fuzzy rule-based systems, FCM methodology and Dempster–Shafer theory in a group decision making environment. Different stages of IFHRA-WSS are elaborated in the following sections.
4.2.1 Step 1: Formation of expert groups and data gathering
Basic data consisting of locations of facilitates, demand points, high risk points, and general and detailed characteristics of UWSS should be collected to generate the database which is required for risk assessment. Different groups of experts with enough knowledge and experience about different elements of the water supply systems should be formed. For each main component of the UWSS, sufficient number of persons should be gathered with acceptable technical and operational knowledge about the system. The minimum group size has been suggested as five persons in the literature (Yetton and Botter 1983). Also for different stages of the risk model, several questionnaires are designed to elicit the decision makers’ engineering judgments.
4.2.2 Step 2: Hazard identification
Different hazards which have affected each part of the UWSS should be listed as well as hazards which are foreseen to affect the operation of the system in the future. The latter can be extracted by interview using questioners. In this paper, Delphi methodology has been used to collect this information from experts and decision makers. Delphi method is a structured communication technique originally developed as a systematic and interactive forecasting method which relies on a panel of experts (Linstone and Turoff 1975).
4.2.3 Step 3: Characterization the UWSS in a hierarchical framework
To begin the risk assessment procedure, the hierarchical framework of the UWSS, which was described earlier, has to be constructed. Hierarchical structure analysis is one of the promising methods for risk analysis level by level from the lowest (hazards) to the highest levels (UWSS). Also the middle levels (layers) of this framework are components and subcomponent. The generic hierarchical framework is illustrated in Fig. 6.
4.2.4 Step 4: Estimation of the hazard probabilities
As it was explained earlier, risk can be defined as the cumulative effects of probability, consequences of a hazard/threat and also vulnerabilities of components and subcomponents against them. Probability is the frequency of natural, human-related, and operational hazards that sometimes can be estimated based on historical data and some times only evaluated based on experts’ judgments. In this paper, probabilities are described in terms of fuzzy linguistic variables (Table 1). This approach allows both quantitative and qualitative descriptions of risk terms.
4.2.5 Step 5: Estimation of the hazard consequences
In this research, consequence is the total negative economical, social, and environmental effects of a hazard which will take place in a given sub-component, component, and the whole UWSS infrastructure, if assumed they are completely vulnerable. Generally, consequences of a hazard in an UWSS can affect the quantity and/or quality of water, as well as general sanitation and safety issues in a community. Consequences are usually estimated based on the number of users influenced by a specific hazard. It is necessary to define specific criteria to evaluate consequences. In this paper, the following four general criteria are aggregated to find consequences of each hazard which may happen due to a component, a group of components, or the whole UWSS disruption:
-
1.
Inadequate or unsafe water supply (depends on water quality and or quantity) (Cs1)
-
2.
Economical losses (Cs2)
-
3.
Social negative impacts (Cs3)
-
4.
Human losses (Cs4)
The next stage is aggregation of these criteria to calculate the overall consequence of each hazard in each part of the UWSS. For this purpose, fuzzy rule-based method proposed by Fares and Zayed (2010) is also applied in this study. The only difference is that Fares and Zayed (2010) used 5 fuzzy linguistic variables while 7 variables are used in this study to reduce the level of uncertainty in the assessment. The following steps have been taken to estimate the consequences of hazards based on four criteria defined for consequences evaluation:
-
1.
Defining all of the possible fuzzy rules between inputs (four criteria) and outputs (consequence of a given hazard) such as the following rule:
In this study, for a given hazard which threatens a subcomponent, 74 rules can be defined (7 linguistic variables shown in Table 1 for 4 criteria).
-
2.
The weights for each criterion are estimated using fuzzy numbers in Table 1 (W i ) and through interview with experts and literature review.
-
3.
Fuzzy value of each input is converted to crisp value using Fig. 7. The values shown on this figure are calculated by defuzzifying the membership functions presented in Fig. 5.
-
4.
The general equivalent combined impact (EI) for each rule is calculated for each set of inputs using the following formula:
\( \overline{{{\text{Cs}}_{i} }} \) is the ith criterion which has been converted to crisp number using Fig. 7.
-
5.
The equivalent impact for each rule is converted to a fuzzy value using the scale shown in Fig. 8.
-
6.
In the final step, fuzzy values of criteria (which have been obtained by aggregation of experts’ opinions) are inserted to the fuzzy rule-based system (Sect. 4.1.2) and output of the system is then defuzzified and considered as the consequence of a hazard in a specific subcomponent. This process should be repeated for all of the hazards in each subcomponent.
4.2.6 Step 6: Vulnerability assessment
This step can be regarded as the main part of risk evaluation. In many cases, decision makers have not enough information about probability or expected consequences of hazards but they can assess the vulnerability of UWSS based on the existing design related documents and their experiences. Same as the consequence analysis, some criteria should be determined by experts to assess the UWSS vulnerability against different natural, human caused and operational hazards. In this study, the following four main criteria are suggested to be used for vulnerability assessment:
-
1.
Insufficient physical means to detect, delay and respond to the threat in place (V1)
-
2.
Insufficient design redundancy (additional sources of supply readily available) (V2)
-
3.
Structural and non-structural vulnerability against hazards (V3)
-
4.
Ability of recovery in a short time after hazards occurrence (V4)
Similar to the probability and consequence parameters, Table 1 is used by experts to describe these four vulnerability criteria. Then similar procedure which was adopted for consequence estimation in the previous step, could be implemented to find the vulnerability value. These outputs are the initial vulnerabilities (V I j ) for subcomponent j. Further analysis is required to calculate the hidden vulnerability of subcomponent due to the interdependencies between subcomponents. Since the vulnerability of a component is a function of its subcomponents vulnerabilities, these hidden values are calculated only based on interdependencies between subcomponents. As it is illustrated before, FCM and FIVAM methods are used for this purpose in this paper. The hidden vulnerability value of a system in each iteration is calculated using Eqs. (10) to (12) as follows:
where V e j is the functional vulnerability value of subcomponent j (i.e. value of concept in Eq. 8) obtained when the FCM model reaches equilibrium at a fixed point after some iterations (V t+1 j in Eq. 10). V H j is the crisp hidden vulnerability of subcomponent j. w jm is the crisp influence value of subcomponent j on subcomponent m that is determined by defuzzifying the fuzzy influence value (\( \tilde{r}_{jm} \)) based on Table 1 and using Eq. (2). Finally, the real vulnerability value of subcomponent j(V R j ) is calculated as the summation of the initial and hidden vulnerabilities base on Eq. (12). This procedure is repeated for all of the subcomponents and for all of the hazards. It should also be noted that the initial values of the concepts in Eq. 10 (V t=0 j ) are set to the specific values based on existing UWSS condition and experts’ judgments.
4.2.7 Step 7: Converting crisp values of consequence and vulnerability parameters to the fuzzy variables
Firstly, a triangular membership functions for the consequence or vulnerability is formulated. The COA of this membership function is the estimated crisp value of consequence or vulnerability. Using the following similarity function proposed by Chen (1998), these fuzzy numbers can be converted to one of the seven linguistic variables shown in Table 1:
where \( S(\tilde{A},\tilde{B}) \) is the similarity value between estimated fuzzy numbers \( \tilde{A}(a_{1} ,a_{2} ,a_{3} ) \) and seven predefined fuzzy linguistic variables \( \tilde{B}(b_{1} ,b_{2} ,b_{3} ) \) (as described in Eq. 1).
4.2.8 Step 8: Estimation of risk in the subcomponent level
In the following three steps, different terms of risk (probability, consequence, and vulnerability) have to be combined together.
4.2.8.1 Step 8.1
For each subcomponent \( j(j = 1,2, \ldots ,J) \) and each hazard \( h(h = 1,2, \ldots ,H) \), fuzzy risk \( (\tilde{R}_{jh} ) \) is calculated based on fuzzy probability \( (\tilde{L}_{jh} ) \), fuzzy consequence \( (\tilde{C}_{jh} ) \) and fuzzy vulnerability \( (\tilde{V}_{jh} ) \):
4.2.8.2 Step 8.2
The total risk of subcomponent j \( (\tilde{R}_{j} ) \) regarding all of threatening hazards is estimated using Eq. (15) and Dempster–Shafer Theory as an aggregative function \( (f(.)) \) of hazards.
All of the hazards can be combined together based on their weight (relative importance) which is obtained from experts using Table 1.
4.2.8.3 Step 8.3
Each evaluated risk of hazard can be represented with a single fuzzy number \( (\tilde{R}_{j} ) \). These calculated risks can be compared with different standard risk grades to obtain relative risk levels (or risk distributions). In this paper, risk grades (levels) are shown by seven predefined risk grades from extremely low (EL) to extremely high (EH). The values associated with each risk grade indicate the degree to which the risk item belongs (Fig. 9). It means that model user can have the results in each level of UWSS (hazards, subcomponents, components and total system) in terms of \( \left( {\frac{a}{EL},\,\frac{b}{VL},\,\frac{c}{SL},\,\frac{d}{M},\,\frac{e}{SH},\,\frac{f}{VH},\,\frac{g}{EH}} \right) \), where a, b, …, g are the calculated risks belonging to the seven predefined risk grades. These predefined risk grades have been calculated multiplying the probability, consequence and vulnerability using Table 1. In order to determine the intersection between them, Weighted Overlap Area Method (WOAM) (Huipeng 2007) is used to determine the intersecting degrees between two fuzzy numbers. The overlap area between a calculated risk and a predefined risk, as a fraction of the total area of the calculated risk, can represent the degree of their intersections:
where C A,B is the weighted intersecting degree between fuzzy numbers of the predefined risk (A) (as shown in Fig. 9) and the calculated risk (B); a α L , a α R , b α L and b α R are the right and left bounds of α-cuts of A and B, respectively. α is also used as a weighting factor in this equation. Thus, degree of the calculated risk belonging to a risk grade \( m\,(m = 1,2, \ldots ,7) \) can be obtained by Eq. (17):
where \( C_{{R_{m} ,R_{n} }} \) denote the degrees of intersection between calculated risk and each of the seven predefined risk grades. r mn indicates the degree to which the calculated risk n belongs to the risk grade m. (Note that r mn is considered as the basic probability assignment in Dempster–Shafer Theory).
4.2.9 Step 9: Estimation of the risk in the components level
The risk of component level can be derived using the following equation:
\( \tilde{R}_{i} \) is the total fuzzy risk of component \( i\,(j = 1,2, \ldots ,I) \) and is calculated similarly based on aggregation of the risk grades of its constitutive subcomponents using the Dempster–Shafer theory. In this part of the model, these risks are aggregated based on the vulnerability of component i due to the failure of its relative subcomponents. In other word, each expert assigns the importance (W in Eq. 7) to each subcomponent with respect to the vulnerability of that component to the failure of its constitutive subcomponents based on Table 1 and finally these weights are aggregated together and applied in Eq. (18).
4.2.10 Step 10: Estimation of risk in the system level (UWSS)
Finally, risk at the system level (UWSS) is calculated by Eq. (19):
where \( \tilde{R}_{\text{UWSS}} \) is the total fuzzy risk of urban water supply system. Similar to step 9, in Eq. (19), each component has a relative importance in total risk of system with respect to the vulnerability of UWSS to its failure.
4.2.11 Step 11: Prioritization of critical points of UWSS based on the results of risk assessment model
The described procedure is repeated until the final risk grades of the total system (\( \tilde{R}_{\text{UWSS}} \)) are estimated. Proper method should be applied to better represent the calculated risks in all of hierarchical risk levels as this can be the most important output of the model for decision makers to apply it in risk management practices. Decision makers can expect to have the risk values in terms of qualitative or quantitative representations. The former group is suitable for decision makers who prefer linguistic expression of risks. These decision makers can focus on final risk grades which are obtained in each level of the IFHRA-WSS as \( \left( {\frac{a}{EL},\,\frac{b}{VL},\,\frac{c}{SL},\,\frac{d}{M},\,\frac{e}{SH},\,\frac{f}{VH},\,\frac{g}{EH}} \right) \) and select the risk grades with the maximum fuzzy membership values as the status of UWSS and its components. About the latter one, there are some simple methods such as estimation of average value of the final risk grades (Lee 1996) and some advanced methods such as Ordered Weighted Averaging (OWA) (Sadiq et al. 2007a, b). By these methods, the attitude of the decision-maker in defuzzifying the final risk value can be considered. In this research, an effective method of risk quantification is introduced which is optimization based. In this method, the following simple problem can be solved to find the non fuzzy values of risk in the proposed model:
where \( R_{\text{UWSS}} \) is the total defuzzified risk value that can be obtained for total system, each component, and subcomponent. \( {\text{L}}_{{{\text{G}}_{r} }} \) is the representing centroid values of 7 linguistic risk \( (r = 1,2, \ldots ,7) \) grades and \( \mu_{r} \) is their attributed fuzzy membership value computed by the IFHRA-WSS model. In fact, in this objective function, it has been tried to minimize the weighted difference between total risk (\( R_{\text{UWSS}} \)) and each predefined fuzzy risk grade centroid. Assigned weight \( \left( {{{\mu_{r} \cdot L_{{G_{r} }} } \mathord{\left/ {\vphantom {{\mu_{r} \cdot L_{{G_{r} }} } {\sum\nolimits_{i = 1}^{7} {L_{{G_{r} }} } }}} \right. \kern-\nulldelimiterspace} {\sum\nolimits_{i = 1}^{7} {L_{{G_{r} }} } }}} \right) \) is function of each grade centroid value and also fuzzy membership value which indicates calculated risks belonging to seven predefined risk grades. It means higher risk grades such as VH or EH has more effects than other risk grades in the total risk value. Some similar optimization methods presented by Lu et al. (2008) and Li et al. (2008) can be applied in this step of the risk assessment model.
5 Case study
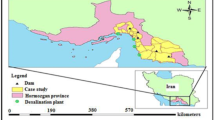
In this research, an urban water supply system in Urmia City in Iran has been selected to evaluate the proposed risk assessment method. Urmia is the center of the West Azerbaijan Province, located in northwest of Iran, near border of Iran and Turkey. It has a population of 577,307 and area of 5,250 km2 (Census of the Islamic Republic of Iran 2006) and is situated on the western side of the Lake Urmia. The city lies on an altitude of 1,330 m above sea level and its climate is semi-arid with moderately cold winters, mild springs, hot and dry summers and crisp autumns. Precipitation is heavily concentrated in late autumn, winter, and especially spring, while summer precipitation is very scarce. The geographical location of this city in Iran and schematic of its UWSS consisting of water sources, water transmission mains, water treatment plants and water distribution system are illustrated in Fig. 10.
There are two main water resources from which water is supplied to this city: Shahr Chay River and Urmia Plain aquifer. Surface water is supplied to the city through direct withdrawal from the river and regulated water from Shahr Chay Dam. Ground water is extracted from 39 wells. The transferred raw water from these sources is treated in two main water treatment plants. The first one (WTP1) has been the main water treatment infrastructure since 1962. Surface water is transferred to WTP1 directly from the river by an old gravity type open channel.
After treatment, it is mixed with the water extracted from groundwater, chlorinated and delivered to some tanks to be distributed in some large part of water distribution network of the city. The same process has been designed in the new water treatment plant (WTP2), but its raw water is supplied through Shahr Chay dam. WTP2 has a limited treatment capacity due its uncompleted construction.
15 water tanks exist in different points of this city that distribute the mixed surface and groundwater in the network as well as some limited wells that inject water directly to the pipes system. Currently, the average water consumption of Urmia City is about 1,900 l/s from which the contribution of water treatment plants WTP1 and WTP2 and wells in delivering water to the water distribution system is about 500, 200 and 1,200 l/s, respectively. It is foreseen that the operational capacity of the WTP2 will be increased in the near future. Also WTP2 has a better structural design and monitoring system against natural and unnatural hazards in this treatment plant.
A part of Urmia UWSS (Fig. 10) has been selected for risk assessment in this study. This part of system comprises of WTP1, its water resources (direct withdrawal from the river), Water Transmission Main No.1 (WTM1), one of the main water tanks (Tank A) with 10,000 m3 volume, that receives water from this water treatment plant and 6 wells, and finally a medium water distribution system (“Daneshkade” zone) which its total area and total length of pipes are 1.9 km2 and 700 km, respectively. This network delivers water to more than 8,500 water consumer units. More than 95 % of the pipe materials are asbestos and their diameter varies between 100 and 400 mm. Because of the following important reasons, this part of the Urmia UWSS has been selected and evaluated by IFHRA-WSS model in this paper:
-
1.
There is not any recorded and available data about WTP2 due to its new construction.
-
2.
WTP1 is still the main safe water supplier in this city and has a lot of operational problems due to the aging and some initial design problems. It is important to mention that this treatment plant has been rehabilitated and repaired several times in the last 40 years because of various operational problems.
-
3.
Urmia water distribution network area is too large and required data are only available for this chosen part of the network.
-
4.
Based on the experts’ opinions, threatening hazards of water supplied from Shahr Chay Dam is less than other resources.
Therefore, this paper focuses on wells, direct water withdrawal from the river and WTM1. The following two main decision making organizations are responsible for UWSS management in this city:
-
DM1: West Azarbayejan Regional Water Authority is responsible for planning and management of operation of surface and groundwater resources and also water transmission mains to the treatment plants. Supplying water to other water users is also responsibility of this organization.
-
DM2: West Azerbaijan Province Water and Wastewater Company operates all of the treatment plants, wells, tanks and water distribution facilities.
In most of the design and management issues related to water supply to Urmia city, these two organizations cooperate together while they both work under the supervision of the Iranian Ministry of Energy.
5.1 Gathered data in the selected area
Water quality and quantity risk assessment are addressed separately in this research based on the proposed methodology. Hazards may lead to both quantitative and qualitative problems while some can only cause water shortage or water contamination problems. A few questioners were designed and distributed between 20 persons (10 people from each of the aforementioned decision making organizations) to gather engineering judgments about associated risks with different components and subcomponents of the system. Then, this information was merged with the available engineering reports to find the most threatening hazards. The outputs of this analysis as well as a short description about each component are presented in the following sections:
5.1.1 Water resources (WR)
The risk identification results show that for the Shahr Chay River, flood has been found as the most effective hazard on water quantity. Severe flood conditions can contaminate the water transmitted to WTP1 and because of the limited capacity of this treatment plant it may subsequently interrupt clean water delivery to the consumers. It worth mentioning that this type of hazard has happened before and specially for the case of low frequency floods has caused serious water contaminations. Another hazard influencing water transfer from Shahr Chay River is drought. In the past 10 years, the average monthly inflow of this river has decreased due to severe and frequent droughts. From water quality point of view, terrorist attacks, floods, sewage discharge to this river, lack of online monitoring system to monitor water quality have been recognized as the main hazards threatening water transferred from Shar Chay River. For wells, the only water quantity related hazard is drought while for water quality; two main concerns are probable sabotage for water contaminating and also chemical threats (Reports are available about observations of high amount of nitrates in groundwater samples collected).
5.1.2 Water Transmission Main No. 1 (WTM1)
Only water transmission main in this case study is a very old gravity stone channel (WTM1) which directly transfers water to WTP1 from the river point which is shown in Fig. 10. The main concern of decision makers about this channel is deterioration in the future (aging), initial design problems and vulnerability against earthquake and probable external loads like corrosion. Furthermore, human related threats such as bombing are important and should be incorporated in the comprehensive risk assessment of this component.
5.1.3 Water Treatment Plant No. 1 (WTP1)
Potential hazards threatening WTP1 are identified based on available historical records of operation and management issues in this plant in the past 2 years, experts’ experiences and some existing reports about previous rehabilitations of this plant. These factors include flood impacts on the treatment process, earthquake, bombing and sabotage, equipment aging, and initial design and operational related problems. In this study, water treatment plant has been considered as a unique component without any subcomponent.
5.1.4 Water distribution network (WDN)
Three subcomponents have been found as the most vulnerable points in “Daneshkade” zone: Tank A, existing pumps and distribution pipes. For Tank A, earth movement and bombing are the main threats to water quantity while insufficient monitoring system and chemical/biological problems are the major threats for water quality. The pump station in the WDN is potentially influenced by various types of hazards according to its historical records and experts’ experiences. Aging of the equipments and weakness of the existing monitoring system and also earthquake as the critical natural hazard can result in reduction of the pumped water. But there is no evidence of any threat to water quality in this subcomponent. Due to the surrounding conditions of the pipes and historical records, earth movement, sewer leakage, and external loads are identified by the experts as potential hazardous factors that may disable the normal function of the pipes. Over burden and external loads on the pipes, including earth weight and vehicle weight, is a possible reason to cause longitudinal cracks on the pipes and it can lead to leakage or big bursts in them. Also from water quality point of view, surrounding soil can be contaminated by sewer leakage from open drains and hence has negative effects to the under buried pipes. Another cause would be the low pressure condition in the system which can lead to intrusion of contamination to the pipes in junctions and leakage points. Moreover, leaching of chemicals and corrosive materials from system components into the water, make some chemical/biological problems. In this paper, all pipes have been evaluated under assumption of occurrence of these hazards, but weight of each pipe in the risk assessment process has been calculated based on their water carrying capacity rather than experts judgments. Moreover, 2 years of historical data of failure rates and their attributed failure reasons have been applied for risk analysis.
Based on these descriptions and expert opinions, the final hierarchical risk assessment framework consisting functional interdependencies in subcomponent level is shown in Fig. 11a, b. The numbers on these figures indicate the deffuzified functional dependency values (w jm ). As it can be seen, there are direct and indirect relations between different subcomponents in WR, WT, WTP and WDN based on functional dependency values to each other. For example disruption of river or channel leads to non-functionality of WT; because no water can be transmitted to WTP. An important component is WDN, because the other components have the effect on this component and its constitutive subcomponents especially the pipes. It not only shows that WDN is not most vulnerable because of these effects, but also means that other components especially WR has higher hidden vulnerability because of the functional dependencies of other components to this component and it increases the importance of water resources in risk management.
It should be mentioned that if there is another permanent water resources or even temporary alternative to supply water in emergency conditions, other components dependencies to water resources can be reduced and subsequently, WR will have a smaller hidden vulnerability. Similar relations can be found between pipes, tank and pumps, river and wells as the main subcomponents of the UWSS. In both water quality and water quantity risk assessment scenarios, the river and wells are dependent to each other. Because every change in water quantity or quality in the river due to some hazards such as drought, can affect water withdrawal program from groundwater and vice versa.
5.2 Model parameters
5.2.1 Decision makers’ importance
For aggregation of decision makers’ opinions about different parameters discussed in this paper, relative importance of two groups of decision makers in the risk assessment procedure has to be considered. It should represent their executive responsibility for each component of the system. These fuzzy values have been chosen and shown in Table 2 based on the fuzzy variables in Table 1. For example, it can be seen that DM2 has the main responsibility for the water distribution network while, DM1 has no control over this part of the system. After that, these weights can be normalized for using in the next steps of the model.
5.2.2 Weights of components, sub-components and hazards
According to different risks scenarios (i.e. water quality or water quantity), weights are assigned by all of the experts for pipe network, pump, water treatment plant, transmission main, channel, river, reservoir, wells, etc. and then they are aggregated based on DMs’ importance (Sect. 5.2.1) using Dempster–Shafer theory. Weighting procedure consists of the following steps:
-
For each decision maker, a questionnaire form is provided including some information about risk assessment methodology and information about different components and subcomponents in a hierarchical form.
-
Each decision maker provides a weight to each component based on its vulnerability to the failure of its subcomponents in the lower level. The questioner is designed in a way to provide enough flexibility for gathering decision maker opinions in qualitative or quantitative manners.
-
These values are aggregated using Dempster–Shafer theory and final weights are obtained after normalizing the deffuzified values of these aggregated weights.
For instance, the final crisp weights for water quality risk category is shown in Table 3.
5.2.3 Functional interdependencies between the subcomponents
The linguistic variables (Table 1) and their respective fuzzy numbers for DMs are used to define the functional interdependency values among the subcomponents of Urmia UWSS. These fuzzy values are aggregated by using Dempster–Shafer theory and crisp influence fuzzy matrix is constructed for the FCM simulation. Different functional interdependency values between subcomponents can be observed in Fig. 11.
5.2.4 Risk term definition (probability, consequence and vulnerability)
This part of the study has a complicated procedure due to the uncertainties of probability, consequence and vulnerability parameters. Although information about some hazards and their consequences are not available and they have not been experienced in Urmia UWSS yet, it has been tried to score the parameters based on the current condition of the system.
As it was described in Sect. 4.2, some criteria have been defined to generate the fuzzy rules in order to assess the consequence and vulnerability of hazards. Table 4 presents the relative defuzzified weights used in the analysis for each of these criteria based on experts’ judgments. Totally 13,720 consequence rules and 96,040 vulnerability rules have been defined in this study for both scenarios of water quality and water quantity risk assessment. All risk terms have been estimated by the method which was introduced in steps 5 and 6 of the methodology and applied in the final step of the model to estimate the risks. Note that there are some limited numbers of hazards such as flood and earthquake for which data analysis has been carried out to extract their probabilities of occurrence. For these cases, their crisp values or fuzzy values are directly used in the model and eliciting the required data through the questionnaire and other methods has not been necessary.
5.3 Results and discussion
IFHRA-WSS model has been coded with Visual Basic program and MATLAB software in this research. The fuzzy rules are constructed in MATLAB and the results are used as the input to the main risk assessment model in Visual Basic domain. After running the model, quantitative results of the aggregative risk assessment have been obtained and discussed while different components and subcomponents of Urmia UWSS are also prioritized with respect to the results of the risk assessment model.
5.3.1 Risk assessment at subcomponent level
Using characteristics of hazards and other model parameters in IFHRA-WSS framework, risk values are obtained for different subcomponents in the selected water supply system in Urmia City, which includes Shahr Chay River, wells, WTM1, WTP1, pumps, Tank A and pipe network in “Daneshkade” zone. These results are shown in Tables 5 and 6 with consideration of functional dependencies between subcomponents to show the effects of hidden vulnerability in risk analysis. Italicized numbers show the highest risk grade for each subcomponent. Even though some details of the results could not be presented in this paper, some of the important findings related to water quantity risk assessment are as follows:
-
Among the two water resources, risk associated with the river is higher than wells. Since the functional interdependencies have been considered in the risk assessment model and also river has the highest levels of effects on other subcomponents (Fig. 11a), its risk grade is SH and it is ranked as the second critical subcomponent in this urban water supply system.
-
Water treatment plant has the highest total risk between all of the subcomponents and has SH risk followed by VH and M. Also among the contributing hazards, flood has the highest effects on its risk value from reduction of water quantity point of view.
-
In the water distribution network, the most critical subcomponents are pipes with SH degree of risk followed by M and SL due to their considerable failure rate.
-
The highest and lowest water quantity risks in the subcomponent level belong to WTP1 and pumps, respectively.
The results of water quality risk assessment can also be summarized as follows:
-
River and WTP1 are the first and the second rank based on water quality risk assessment with risk grade of SH.
-
Risk of pipes is SL, which is the lowest risk between subcomponents and followed by VL and M as well. This finding was expected because they are not prone to the water contamination related problems in “Daneshkade” Zone.
-
Total risk of Tank A is low but its relative fuzzy risk is medium and should be considered as an important point in the risk management procedure to decrease the negative effects of threatening hazards.
5.3.2 Risk assessment at component level
After determination of risk levels at subcomponents based on group decision making, it is simple to obtain risk levels of the main components by aggregating these risks along the hierarchical structure. The results are presented in Tables 7 and 8 for water quantity and quality scenarios, respectively. Firstly, contributing components to reduced water quantity risk are WS, WTP1, WTM1 (channel) and WDN. The results of this aggregation can be summarized as follows:
-
The risk level of water resources is M and varies from EL to EH which indicates the high uncertainty in the calculated risk.
-
The risk level of WTP1 belongs to four risk grades of SL to VH and also has the highest priority for risk management.
-
The risk of water distribution network is determined by repeating the risk aggregation on the pipes, Tank A and the pumps. As it can be seen, the total risk has the highest grade of M varying from EL to VH.
The contributing sources to the risk of water contamination are WS, WTP1 and WDN. Their attributed risk assessment results are as follows:
-
The most vulnerable component of the selected UWSS is WTP1 followed by WR and WDN and their highest risk grades are SH, SH and M, respectively.
-
For the “Daneshkade” zone, risk of contamination is evaluated by aggregating the risks of pipes and tanks. As it is mentioned in Table 8, WDN has the lowest risk value among other subcomponents.
-
The risk of pumps has not considered in this assessment, because these subcomponents are only vulnerable to the water quantity problems.
Also as an example, results of FCM simulation for water quality risk assessment are shown in Fig. 12. As it can be seen, FCM reaches an equilibrium state (i.e. no change in activation levels is observed in two consecutive iterations) approximately after 7 iterations. After that these values have been used to obtain hidden vulnerability and total vulnerability using Eqs. (11) and (12).
5.3.3 Risk assessment at system level (UWSS)
Finally, the risk of overall water supply system can be obtained by aggregation of components risks and their contribution in overall system based on Eq. 19. Figure 13 shows different risk grades of the system. Furthermore, using Eq. 20 defuuzified total risk value for water quality and water quantity risk assessment scenario have been obtained as 0.259 and 0.232, respectively incorporating the effects of all of the threatening hazards.
Some important results obtained in this phase of the risk assessment are:
-
Risk aggregation of different components shows that the highest risk grade for both water quantity and water quantity scenarios is medium, which indicates importance of monitoring risks and further efforts for developing long term risk mitigation plan.
-
Among the contributing components, WTP1 is the most important point in the Urmia UWSS. In addition, water distribution network and water resources have contribution in increasing the risk level of the system with respect to both water quantity and quality issues, respectively.
-
Four uncertainty sources have been considered in this case study:
-
1.
Uncertainty in decision makers’ opinions in preparing the information about hazard consequences and component and subcomponent’s vulnerabilities and other necessary parameters. It can be considered as technical uncertainties.
-
2.
Uncertainty in estimation of hazard probabilities especially for natural hazards (random uncertainties).
-
3.
Technical uncertainty in parameters of IFHRA-WSS model including weights of risk items and probabilities, vulnerabilities and consequences.
-
4.
Physical uncertainties in available and reported data about characteristics of the urban water system and its components.
-
1.
-
As it was mentioned in different parts of this paper, the model gives a way for ranking components and subcomponents in terms of their risk grades and values. If decision makers have their acceptance level for each risk grade or have a risk threshold for total risk, this model can explicitly show whether the risk in each level is acceptable or not. Based on these judgments, they can choose some risk mitigation measures and determine which one is the most effective measure by evaluating the risk in each level.
-
As it was also stated by Tesfamariam and Sadiq (2006), the selection of different mitigating or preventive alternatives often involve competing and conflicting criteria, which requires sophisticated multi-criteria decision-making (MCDM) methods. One of the best ways to design the effective risk management scenarios is to apply a multi-criteria decision-making method involving risk reduction ability of each measure (output of IFHRA-WSS model) and other criteria such as cost, environmental, and social effects. By this way, not only they can decrease the risk of hazards, but also decision makers’ management related concerns are included in the decision making process.
6 Conclusion
Management of UWSS is becoming more sophisticated as the subsystems face several uncertain threats and conditions. This study presented an effective risk evaluation model for UWSS from source to tap with the ability of incorporating uncertainties. The most important characteristics of IFHRA-WSS model could be summarized as follows:
-
Covers complexities in UWSS by hierarchical approach.
-
Evaluates risks by considering multiple hazards that are represented in varied forms.
-
Covers different sources of uncertainties.
-
Involves experts in a group decision making procedure.
-
Uses a new approach for evaluating consequence and vulnerability as the main parameters of risk item considering the most effective criteria.
-
Considers the functional interdependencies among the subcomponents to effectively assess their vulnerabilities against the hazards.
-
Incorporates the social and economical aspects in the risk assessment procedure.
-
Handles both qualitative and quantitative forms of risk values in different levels of UWSS.
-
Can be applied to water quality and water quantity risk assessment scenarios.
-
Can be updated by incorporating newly observed data.
-
Using its results can reduce the probability of loss before it becomes a real threat and will minimize the magnitude of damages.
The results of the case study showed that the total risk status of Urmia urban water system is medium and the most contributing component in increasing the system risk level is old water treatment plant (WTP1) for which some structural and nonstructural risk mitigation measures should be adopted. Alternatively, increasing the operational capacity of new water treatment plant (WTP2) can be a good solution in the future. The water distribution network and Shahr Chay River are the next candidates for water quantity and quality risk management. Cost-effective rehabilitation and renewal strategies can be an effective way to reduce the failure risks of pipes in water distribution network. Permanent inspection of water tank by installation of proper means to detect, delay and respond to the external threats is one of the methods which should be applied in water distribution networks especially for water Tank A. Moreover for the case of the river, since the most water quality threatening hazards are flood and chemical/biological hazards, construction of settling basins on Shahr Chay river for decreasing the water contamination in flood conditions and setting up a water quality monitoring system to control the chemical/biological status of the surface water, are the applicable examples of risk management alternatives for this system which need further studies. Future works can be dedicated to:
-
Extending the IFHRA-WSS model to determine the contribution degree of various components, subcomponents and hazards in deriving the overall risk of urban water systems.
-
Sensitivity analysis for evaluation of the effects of technical, random or physical uncertainties on model efficiency by using different forms of Fuzzy membership functions for representation of uncertain parameters comparing the results of using MCDM techniques (e.g. OWAFootnote 1 and FSAW,Footnote 2 etc.) instead of Dempster–Shafer theory for risk aggregation in different levels of the urban water system.
-
Developing a methodology for designing risk mitigation measures based on the results of IFHRA-WSS
-
The risk value obtained from IFHRA-WSS model is usually the basis for defining risk management scenarios. MCDM techniques can be used for ranking these scenarios based on diverse criteria such as cost and social satisfaction.
Similar flexible hierarchical frameworks can be easily used in risk assessment of other water utilities by considering their individual characteristics. This model could be the main part of a decision support system for comprehensive risk management and proper selection of risk reduction measures with minimum costs and maximum reliability.
Notes
Ordered Weighted Averaging.
Fuzzy Simple Additive Weighting.
References
Akgun I, Kandakoglu A, Ozok AF (2010) Fuzzy integrated vulnerability assessment model for critical facilities in combating the terrorism. J Expert Syst Appl 37(5):3561–3573
ASME Innovative Technologies Institute, LLC (2006) Risk analysis and management for critical asset protection-RAMCAP, Version 2.0
Aven T (2011) On some recent definitions and analysis frameworks for risk, vulnerability and resilience. J Risk Anal 31(4):515–522
Census of the Islamic Republic of Iran (2006) Statistical center of Iran http://www.amar.org.ir
Chen SM (1998) Aggregating fuzzy opinions in the group decision making environment. Int J Cybern Syst 29(4):363–376
Cieślak BT (2011) Fuzzy failure risk analysis in drinking water technical system. RT&A 1(20):138–148
Clark RM, Deininger RA (2000) Protecting the nation’s critical infrastructure: the vulnerability of U.S. water supply systems. J Conting Crisis Manag 8(2):73–80
Dempster AP (1967) Upper and lower probabilities induced by a multi-valued mapping. Annu Math Stat 38(2):325–339
Edwards W (1971) Social utilities. Eng Econ Summer Symp Ser 6:119–129
European Commission (EC) (2000) Directive 2000/60/EC of the European Parliament and of the council of 23 October 2000 establishing a framework for Community action in the field of water policy. Official J Eur Commun, L327/1, European Union
Ezell BC (2007) Infrastructure vulnerability assessment model (I-VAM). J Risk Anal 27(3):571–583
Ezell BC, Farr JV, Wiese I (2000) Infrastructure risk analysis model. J Infrastructure Syst ASCE 6(3):114–117
Fares H, Zayed T (2010) Hierarchical fuzzy expert system for risk of failure of water mains. J Pipeline Syst Eng Pract 1(1):53–62
Federal Emergency Management America (FEMA) (2003) Primer for design of commercial buildings to mitigate terrorist attacks. Risk Management Series
Haestad M, Walski TM, Chase DV, Savic DA, Grayman W, Backwith S, Koelle E (2003) Advanced water distribution modeling and management. Haestad Press, Waterbury
Huang C (2009) Integration degree of risk in terms of scene and application. Stoch Env Res Risk Assess 23:473–484
Huipeng L (2007) Hierarchical risk assessment of water supply systems. PhD Thesis, Loughborough University
Ishizuka M, Fu KS, Yao JTP (1982) Inference procedures and uncertainty for the problem-reduction method. J Inform Sci 28(3):179–206
IWA (2004) The Bonn Charter for Safe Drinking Water, http://www.iwahq.org/cm. International Water Association
Kaplan S (1997) The words of risk analysis. J Risk Anal 17(4):407–417
Kosko B (1986) Fuzzy cognitive maps. Int J Man Machine Stud 24(1):65–75
Lee CC (1990) Fuzzy logic in control systems: fuzzy logic controller, Part I and II. IEEE Trans Syst Man Cybern 20(2):404–435
Lee HM (1996) Applying fuzzy set theory to evaluate the rate of aggregative risk in software development. Int J Fuzzy Sets Syst 79(3):323–336
Lee HK, Yeh YY, Chen WM (2006) Cancer risk analysis and assessment of trihalomethanes in drinking water. Stoch Env Res Risk Assess 21(1):1–13
Lee M, McBean E, Ghazali M, Schuster C, Huang J (2009) Fuzzy-logic modeling of risk assessment for a small drinking-water supply system. J Water Resour Plan Manag 135(6):547–552
Li YP, Huang GH, Yang ZF, Nie SL (2008) IFMP: interval-fuzzy multistage programming for water resources management under uncertainty. Resour Conserv Recycl 52(5):800–812
Lindhe A, Rosén L, Norberg T, Bergstedt O (2009) Fault tree analysis for integrated and probabilistic risk analysis of drinking water systems. J Water Res 43(6):1641–1653
Linstone HA, Turoff M (1975) The Delphi method: techniques and applications. Adison-Wesley, Reading, ISBN 9780201042948
Lu HW, Huang GH, Zeng GM, Maqsood I, He L (2008) An inexact two-stage fuzzy-stochastic programming model for water resources management. Water Resour Manag 22(8):991–1016
Lund JR (2002) Floodplain planning with risk-based optimization. J Water Resour Plann Manag 128(3):202–207
Mays LW (2004) Urban water supply management tools. McGraw-Hill Engineering Reference, New York
Ostfeld A (2001) Reliability analysis of regional water distribution systems. J Urban Water 3(4):253–260
Qin XS (2012) Assessing environmental risks through fuzzy parameterized probabilistic analysis. Stoch Env Res Risk Assess 26:43–58
Rahman S, Zayed T (2009) Condition assessment of water treatment plant components. J Perform Constr Facil 23(4):276–287
Rausand M, Høyland A (2004) System reliability theory. Models, statistical methods, and applications. Wiley, New Jersey
Sachs T, Tiong R (2009) Quantifying qualitative information on risks: development of the QQIR method. J Constr Eng Manag 135(1):56–71
Sadiq R, Kleiner Y, Rajani B (2004) Aggregative risk analysis for water quality failure in distribution networks. J Water Supply Res Technol 53(4):241–261
Sadiq R, Rodriguez MG, Imran SA, Najjaran H (2007a) Communicating human health risks associated with disinfection by-products in drinking water supplies: a fuzzy-based approach. Stoch Env Res Risk Assess 21:341–351
Sadiq R, Kleiner Y, Rajani B (2007b) Water quality failures in distribution networks—risk analysis using fuzzy logic and evidential reasoning. J Risk Anal 27(5):1381–1394
Salas JD, Fu C, Cancelliers A, Dustin D, Bode D, Pineda A, Vincent E (2005) Characterizing the severity and risk of drought in the Poudre River, Colorado. J Water Resour Plan Manag 131(5):383–393
Shafer G (1976) A mathematical theory of evidence. Princeton University Press, Princeton
Tesfamariam S, Sadiq R (2006) Risk-based environmental decision-making using fuzzy analytic hierarchy process (F-AHP). Stoch Env Res Risk Assess 21:35–50
Tidwell VC, Cooper JA, Silva CJ (2005) Threat assessment of water supply systems using markov latent effects modeling. J Water Resour Plan Manag 131(3):218–227
Torres J, Brumbelow K, Guikema S (2009) Risk classification and uncertainty propagation for virtual water distribution systems. J Reliab Eng Syst Safety 94(8):1259–1273
Vairavamoorthy K, Yan J, Gagale HM, Gorantiwar SD (2007) IRA-WDS: a GIS-based risk analysis tool for water distribution systems. J Environ Model Softw 22(7):951–965
Weiler K, Walter MT, Walter MF et al (2000) Seasonal risk analysis for floodplains in the Delaware River Basin. J Water Resour Plan Manag 125(5):320–329
World Health Organization (WHO) (2004) Guidelines for drinking-water quality, 3rd edn
Yager RR (2004) On the determination of strength of belief for decision support under uncertainty—Part II: fusing strengths of belief. Int J Fuzzy Sets Syst 142(1):129–142
Yetton P, Bottger P (1983) The relationships among group size, member ability, social decision schemes, and performance. J Organ Behav Human Perform 32(2):145–159
Zadeh LA (1965) Fuzzy sets. J Inf Control 8(3):129–142
Acknowledgments
The authors would like to acknowledge valuable contributions of the staff of the West Azerbaijan Water Authority and West Azerbaijan Water & Waste Water Company specially Mr. A. Shirzad in preparation of the data and filling the questionnaires in different stages of this research.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Roozbahani, A., Zahraie, B. & Tabesh, M. Integrated risk assessment of urban water supply systems from source to tap. Stoch Environ Res Risk Assess 27, 923–944 (2013). https://doi.org/10.1007/s00477-012-0614-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00477-012-0614-9