Abstract
Performing a comprehensive risk analysis is primordial to ensure a reliable and sustainable water supply. Though the general framework of risk analysis is well established, specific adaptation seems needed for systems such as water distribution networks (WDN). Understanding of vulnerabilities of WDN against deliberate contamination and consumers’ sensitivity against contaminated water use is very vital to inform decision-maker. This paper presents an innovative step-by-step methodology for developing comprehensive indicators to perform sensitivity, vulnerability and criticality analyses in case of absence of early warning system (EWS). The assessment and the aggregation of these indicators with specific fuzzy operators allow identifying the most critical points in a WDN. Intentional intrusion of contaminants at these points can potentially harm both the consumers as well as water infrastructure. The implementation of the developed methodology has been demonstrated through a case study of a French WDN unequipped with sensors.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Water distribution networks (WDN) are considered as core public infrastructures because of their relevance to social and economic activities. Unfortunately, WDN are vulnerable against various sources of accidental and intentional contaminations (US EPA 2003). Accidental contamination can be generally due to compromise in water quality caused by external factors such as dysfunction of devices, human errors and aging infrastructure etc. Intentional contamination is due to malicious attacks through deliberated injection of contaminants into water supply system (Nilsson et al. 2005; Clark et al. 2008; Copeland 2010).
According to Di Nardo et al. (2014), a malicious act involves deliberately introducing chemical, biochemical or radioactive contaminants. Recently, Islam et al. (2015) conduct a comprehensive literature review on existing decision models addressing risk analysis in case of contamination intrusion. The awareness on the need of risk assessment methodology for potential malevolent attack for water systems has increased to counter potential bioterrorism acts.
Di Nardo et al. (2013) consider the intentional contamination of water network as a major risk for society. For authors contamination can occur by the introduction of biological or chemical contaminant in simple way as backflow attack for example. According to authors, contamination risk is not exclusively technical but is also due to managerial complexity, the characteristics of contaminant and the difficulty of describing the phenomenon of contaminant propagation. One of the key points is the ability of developing an Early Warning Systems (EWS) that ensures an early detection of the contamination by monitoring the water quality through some significant parameters such as pH, turbidity. 2 Main actions can be carried out: (1) alert the population and (2) to close contaminated area when it’s possible to limit the propagation. Other approaches are based on the optimal location of measurement devices in order to identify source of contamination. It seems that Water Network Partitioning (WNP) which consists in dividing the water network in permanent subnetworks called District Meter Area (DMA) are capable of protecting water network from attacks by isolating infected areas and stopping contaminant propagation without decreasing the performance of the entire network. Di Nardo et al. (2013) assess the impact of isolation of DMA few hours after a chemical contamination (potassium cyanide) of a water network unequipped with EWS.
Hart and Murray (2010) describe EWS and review several works around this topic. Authors realise a significant literature review concerning the problematic of optimal placement of sensors. It appears that sensors placement is one of the critical aspects of the design of EWS.
Hall et al. (2007) discuss recent initiatives of investigating how changes in some water quality parameters can potentially indicate contamination. Interrogations concern the set of parameters to consider and the appropriate sensors for on-line monitoring to detect potential contamination. Authors lists programs and set of parameters such as pH, free chlorine, oxidation reduction potential (ORP), dissolved oxygen, conductance, turbidity, total organic carbon (TOC), chloride, ammonia and nitrate. Sensors could be discriminated according to the type of monitored parameters, technology or manufacturer and their cost. Authors test several sensors by using a pilot scale distribution system simulator. They inject various types of contaminant and use several types of sensors in order to check the response of sensors to the injected contaminants and how quality parameters change. For authors the use of online monitors may increase water quality and constitutes a complimentary source of other monitoring data that could help to protect water network against contamination. Authors conclude that no single sensor responded to all contaminants but some of them respond to a large number of contaminants.
Murray et al. (2010) deals with spatiotemporal model for health risk distribution in case of contamination events of drinking water network. Authors develop a model that links flow and transport model to dynamic models for disease in order to estimate the spatial distribution of health risks due to ingestion of contaminated water. They discussed the effectiveness of early warning system on water quality sensors for reducing the risks of intentional contamination of water systems.
The effectiveness of sensors can also depend on its location and its capacity to be close to vulnerable area of the network. Ailamaki et al. (2003) describe a distribution and operation protocol for the location and the utilisation of in situ sensors. Developed approach is based on the combination of a new algorithm for spatiotemporal data mining and a new modelisation of water quality and security dynamics. Authors assume that effective early detection requires an extensive monitoring coupled with modelling of the link between varying distribution conditions, loading of pathogens and their persistence in the system. Responses issued from sensors is not enough, they require specific data evaluation and treatment for decision making.
The main focus of this paper is to present decision aiding tools allowing a better preparedness against an intentional contamination of WDN that could be implemented independently or as part of an EWS. Proposed model is referred as WARNING (Water Analysis Risks for Networks Incidents and uNexpected events Guidance) SMaRT-OnlineWDN. It has been adapted from the RAMCAP framework (Risk Analysis and Management for Critical Asset Protection) (ASME 2006), which has been used by the U.S. Department of Homeland Security to improve the risk analysis practice among various industrial sectors.
Proposed methodology employs multi-criteria decision analysis and fuzzy logic approaches. It involves both theoretical and practical knowledge around two main elements of the WDN: (1) consumers and (2) physical assets. Complexity of risk analysis framework depends on the level of knowledge of these components and how a contamination could possibly impact them. Developed methodology intends to improve the understanding of the sensitivity of consumers and the intrinsic vulnerability of the physical assets against contamination events. This paper investigates the appropriate scale for analysis. It will identify potential risk locations that could correspond to a consumption place or a WDN asset based on the concept of “Criticality”.
In this paper, we build specific criteria to identify sensitive consumers and vulnerable assets in order to estimate the criticality of a WDN unequipped with sensors and where EWS does not exist. Following are the key points that will be addressed by the our methodology:
-
Intentional contamination: contaminated water in the WDN is the result of an intentional attack.
-
Intrusion of contaminant in the distribution network: a specific analysis of WDN components is required in order to determine if they could constitute a potential intrusion point.
-
Chemical or microbiological contaminants: analysis is restricted to only chemical or microbiological contaminants. The radioactive compounds or other derived substances are excluded from the analysis.
-
Implementation of sensitivity analysis and vulnerability analysis in order to match most critical areas of WDN.
The paper is divided into 4 sections. A general description of the developed methodology is presented in the next section, which provides details on the sensitivity analysis, vulnerability analysis and related criteria. Section 3 illustrates an implementation of proposed methodology and discusses main results. Final section provides the conclusions and highlights possible improvements.
2 Materials and methods
Scope of this paper does not include production and storage systems as a potential source of the contamination event. Likewise, the vulnerability of the water resource(s) will not be considered in the risk analysis approach (i.e., the efficiency of the water treatment system will not be addressed.
The context of “intentional contamination” of a dynamic system delivering consumers implies adapting of the “first-order” risk definitionFootnote 1 introduced by the RAMCAP framework. Hence, the Eq. (1) defines the risk caused by the intrusion of contaminant in the WDN as the combination of following three components:
The consequences of the water contamination will be evaluated for two main categories of impacts regarding to the water utility: (1) impacts on the water utility and (2) impacts on third party that comprise impacts on human health and socio-economic activities.
The RAMCAP framework (ASME 2006) defines the Threat as “the likelihood of a specific attack scenario directed toward a specific asset”. It seems hard to estimate the likelihood of particular scenarios. In general, risk is analyzed as a conditional risk with a maximal probability of occurrence (equal to 1). Thus, we assume that the occurrence of an attack is certain. This assumption leads to the simplification of the Eq. (1).
Estimating how vulnerable is the WDN in front of a contamination scenario requires the consideration of 2 sub-levels: (1) the intrinsic vulnerability of WDN components—asset level—that could be considered as potential intrusion points (target); (2) the magnitude of the spread of contamination from the intrusion point to the water users, the network level. We define the Criticality of the WDN component (asset) as the combination of the intrinsic vulnerability of the component with the magnitude of the contaminant spread within the WDN.
The Intrinsic Vulnerability estimates the possibility of introducing contaminant into the WDN from a specific and predetermined point. To assess susceptibility of intrusion both technical characteristics and the environment of the intrusion point are analyzed. The Magnitude of the contaminant Spread from a determined intrusion point describes the water flow patterns within the WDN. This magnitude corresponds to the spatial dispatching of contaminant into the system. As the Contaminant Spread depends on hydraulics, a simulation model can be used to predict the propagation of the contaminant throughout the WDN as recommended by Nilsson et al. (2005).
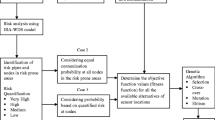
Proposed risk analysis methodology enables to link three components of the risk equation, i.e., consequence, intrinsic vulnerability and contaminant spread magnitude. It appears that the risk assessment in case of intentional contamination of the WDN requires the pairing of intrusion and consumption points in terms of time and space scales. Developed methodology follows 4 main steps: (1) users’ sensitivity analysis, (2) WDN vulnerability analysis, (3) consequences analysis and (4) risk assessment. The calculation of risk factors for risk assessment requires the aggregation of numerous sub-results derived from each step. Figure 1 proposes a conceptual framework for risk analysis. It consists of 3 levels of aggregation that successively enables estimating contaminant spread magnitude, criticality of the WDN components, and finally estimating the risk for the intentional intrusion of contaminant. Specific fuzzy membership functions and knowledge bases (KB) fitted according to the decision maker preferences are used for successive aggregation levels. The use of fuzzy logic approach concerns a wide range of problematics related to water systems. Panigrahi and Mujumdar (2000) develop a fuzzy rule based model for the operation of reservoir. Authors details the use of fuzzy approach by explaining the construction of membership functions for the inflow, storage, demand and the release. They also define fuzzy operator and defuzzification method. Developed model had been applied to the Malaprabha irrigation reservoir in Karnataka, India. It appears that fuzzy approach avoids complex optimization procedures and allows easy operation of system based on linguistic statements. Sadiq et al. (2007) address risk of water quality failure in distribution network. Authors develop a methodology based on aggregative risk analysis approach where each basic risk item that assesses a risk source is expressed by triangular fuzzy number. Tchórzewska-Cieslak (2011) implements a failure risk approach based on fuzzy logic. Author defines 3 criteria as components of the risk and use specific membership functions to modelise each criterion. All steps of the implantation of fuzzy logic approach are detailed in pedagogic way. The fuzzy risk of failure of water pipes is assessed according to specific inference rules. In our case, fuzzy logic is used to achieve the vulnerability analysis and to aggregate sub-results obtained from each analysis steps as shown by Fig. 1.
Factors in shaded boxes are the direct results of hydraulic simulations that are conducted as recommended by Nilsson et al. (2005). Simulations are performed during peak period by considering a specific mass loading of contaminant and according to demand characteristic. The combination of these parameters defines a contamination scenario as mentioned in Rasekh and Brumbelow (2013).
The first level of aggregation, “Inference 1”, evaluates the contaminant spread magnitude. In addition, the location of existing sensors in the WDN could help to better designate contamination location. We assume that the average time of detection corresponds to the elapsed time between the contaminant intrusion and its detection by sensors (if they exist) or by a positive concentration of the contaminant into nodes obtained by a hydraulic simulation in case of absence of sensors. This delay is taken into consideration to assess the contaminant spread magnitude in combination with the percentage of sensitive users exposed to the contaminant.
The second level, “Inference 2”, involves the assessment of the WDN components criticality based on spread magnitude and WDN intrinsic vulnerability. The third level of aggregation is done to perform risk assessment based on criticality and consequences. It can also be noted that several types of risks can be measured depending on the type of retained consequences (economic, environmental, social and sanitary). The following sections highlight the methodology to conduct each level of analysis.
2.1 Sensitivity analysis
This section aims at better understanding of the concept of sensitivity and more precisely the sensitivity of consumers against a potential contamination of water. The sensitivity of the WDN users can be defined both in terms of water quality and quantity regarding to their uses or potential consequences on health or usual activities. It depends on the typology of water uses and the intrinsic characteristics of consumers. For more clarity, we distinguish between sensitivity of consumers and vulnerability of WDN. One of the goal of this step is to explain the main dimensions of sensitivity in order to build consistent and reliable criteria that are able to sort or rank users. In order to be exhaustive and transparent, a multi-criteria analysis (MCA) Bernard and Bouyssou (1993) approach is implemented. Each step of the method is validated and amended by decision makers. Sensitivity analysis should be conducted through following steps as illustrated by Fig. 2.
It is crucial at this step of the analysis to observe water consumers according to their water uses and locations. In order to take into account potential water uses, consumers are sorted into 4 categories: (1) Water for human consumption corresponding to the domestic use of water: drinking water, water for food and hygiene. Users included in this group (domestic users, office employees, schoolboys, hotel client…) are human beings (contrary to companies, shops, factories…) (2) Water for medical purposes corresponds to water used within the health facilities and the specific case of home-based patients of dialysis for example, (3) Water for recreational activities concerns all locations where the water is the object of recreational activities. This type of use has to be associated with places as aquatic park, swimming pool and municipal bath but also water jets and public fountains and (4) water for professional uses which concerns water used for industrial or service activities. In this case, the water user could be an organization or an institution (firm, company or shop).
Because water use differs from category to another, sensitivity analysis is based on the comparison of users belonging to the same category. Comparison is achieved based on exhaustive and non-redundant criteria and sub-criteria that handle potential dimensionalities of sensitivity with regard to the decision maker preferences. Because the users of the groups 1, 2 and 3 are individuals, user sensitivity of these 3 groups will be analyzed with the same criteria. Evaluation of each criterion is done by specific mathematical function called performance function.
Because the group 4 is composed by companies, factories or firms other criteria were defined. The retained criteria and their respective performance functions are summarized in Tables 1 and 2.
Once criteria are defined and evaluated, the relative importance of each criterion has to be determined based on the decision makers’ preferences. Many approaches exist for the criteria weighting but it does not exist a real consensus in the literature concerning the most appropriate one. In order to ensure transparency and reproducibility of the process, we preconize the use of very simple procedure developed by (Simos 1990) and revised by Figueira and Roy (2002). It offers the advantages to be: (1) very easy to implement and to understand (2) non-focused on the scale of the criterion evaluation, (3) involves ex aequo. Simos’ procedure consists in assigning card for each criterion and ranking them with regard to decision maker’s preferences. Once the cards are ranked, relative criteria weights are computed.
In order to conduct reliable risk analysis, it seems suitable to involve multiple perceptions of decision makers in order to achieve an exhaustive analysis. So, several stakeholders with different background and expertise can be involved in the weighting process. The use of Simos’ procedure in this situation is not enough because it leads to a variety of weight sets, one for each involved decider. In order to obtain a compromise set of weights, the use of Ordered Weighted Average Operators (OWA) introduced by (Yager 1998) seems relevant. The OWA-based approach has a number of important benefits because it offers the possibility to involve multiple decision-makers context. The OWA procedure can be implemented in 3 main steps: (1) Reordering the performance value of criteria in descending order, (2) Determining the weightsFootnote 2 associated with the OWA operators and generate the OWA weights with an appropriate probability density function as suggested by Tesfamariam and Sadiq (2006), (3) aggregating process based on OWA weights. Concerning the generation of OWA weights (Xu 2005) proposed the probability distribution function which the heights represent OWA weights. The λ parameter—i.e., quantile—corresponds to the location of the maximum weights. The normal distribution is obtained for λ = 0.5. It provides compromising OWA weight distribution. Yager (1998) introduced the concept of orness α which characterizes the type of aggregation being performed for a particular value of OWA weighting vector.
The last step of sensitivity analysis is the aggregation of criteria in order to estimate the sensitivity of each user. This step consists in choosing the most appropriate aggregation methods considering a ranking problem in order to sort consumers and match the most sensitive. Let’s consider C 1, …,C n criteria, weighted respectively by w 1, …, w n and evaluated by g i (C i ) performance function. The sensitivity of consumer node j is assessed by the function S w (j) obtained by the Eq. (1):
For practical reasons, the weighted sum seems the most adapted method because of its simplicity of implementation.
In order to assess the magnitude spread of contaminant, the identification of the most contaminant locations from where contaminant can be introduced and potentially harm sensitive users must be done. A specific inverse model is implemented in order to identify the potential sources of contamination based on backtracking algorithm developed by Ung et al. (2013).
Considering that velocities in the network are known in an extended period simulation, the inverse model is done by resolving the adjoint problem of transport on the graph obtained from the water network. The equation of classical 1D transport model is:
Considering S is the scalar value (the concentration), v the velocity, x the position. We use a conservative law to be in the worst case and a complete and perfect mixing at junctions. The adjoint equations give a solution to reach possible source for a contamination P:
where \(\uptau = {\text{T}}_{0} - {\text{t}}\;{\text{and}}\;\upchi = {\text{X}}_{0} - {\text{x}}.\) This can be interpreted as “turn the clock back”. The problem is solved by a Lagrangian characteristic method as described in (Ung 2016) initialized by value of P equals to 1 at the user’s node to be contaminated.
(Ung 2016) builds an input/output matrix to show if a node is contaminated from a potential source nodes as illustrated by Fig. 3.
Input/output matrix of contamination, blue points are non-zero (Ung 2016)
Each line of the matrix shows a node with sensitive user, each column potential sources. The points aligned as diagonals show the duration of contamination from sources to surveyed node.
Backtracking matches the paths of contaminant spread between sensitive users’ locations and potential intrusion points.
Inverse transport model is faster than standard hydraulic simulation. As shown in Fig. 4, it matches the most frequent contaminant nodes for the most sensitive users. This sub-result combined with the intrinsic vulnerability enables the selection of vulnerable nodes that could constitute potential injection points of contaminants. The preselection of intrusion points allows generating more realistic contamination scenarios and simulating most probable situations based on the hydraulic operation of the WDN. So backtracking enables to link sensitivity analysis with the next section dealing with the vulnerability of WDN components.
2.2 Vulnerability analysis
Vulnerability analysis estimates the relative preparedness of WDN components to potential attack. Ezell et al. (2000) develop an interesting approach by assigning “access” and “exposure” fuzzy factors. “Access” corresponds to the degree of protection of the device and “exposure” corresponds to its degree of visibility or accessibility. Ezell et al. (2000) assume that the total vulnerability is the product of access and exposure. Torres et al. (2009) implement this approach for risk screening in order to sort WDN nodes that require more attention and to be analyzed in depth. Authors conduct a vulnerability analysis with the help of Geographic Information System (GIS) on virtual city, “Micropolis”. We adapt and build specific criteria to deal with the axiom defined by Ezell et al. (2000), even if the basis is quite similar, our approach seems more practical. It improves the understanding and the estimation of vulnerability by crossing information concerning the network and its environment.
The vulnerability analysis is carried out at the scale of each device or asset. It is based on the assessment of an intrinsic vulnerability index obtained from Fuzzy Rule Base (FRB) aggregation scheme of two dimensions of vulnerability, i.e., (1) structural vulnerability and (2) vulnerability linked with the environment of the intrusion site. Each component of WDN represents a potential intrusion site of contaminant. Under the assumption of intentional contamination, the injection device produces the driving force (i.e., pressure) needed to introduce the contaminant, it could be a pump and fittings to connect it to existing paddle clamp or socket clamp. The contaminant to be injected is assumed in a liquid state or contained in a liquid. In order to measure asset’s vulnerability, a classification of intrusion sites is done based on the following characteristics: (1) control structures equipped with a by-pass system, (2) WDN components connected to the pipe through a paddle clamp, (3) fire-fighting equipment, (4) unburied and unprotected pipes.
The Intrinsic Vulnerability describes the level of protection of WDN devices against contaminant intrusion. It corresponds to the combination of the structural vulnerability and the vulnerability linked to the environment of the intrusion point.
The structural vulnerability depends on the technical characteristics of the intrusion site. It could be estimated based on the combination of the following criteria: (1) ease of physical access to the intrusion site according to its immediate environment and (2) level of surveillance according to existing devices or observers.
The aggregation of proposed non-commensurate criteria is performed by an uncertainty index-based approach using the Fuzzy Inference System (FIS) developed by Francisque et al. (2009). It combines 3 inference engines as illustrated in Fig. 5.
The three Inference Engines will be supplied respectively by three knowledge bases (KB) as explained in appendix.
In order to combine the 3 inference engines and implement the Fuzzy Inference Systems, an open source library for fuzzy systems called jFuzzyLogic and developed by Cingolani and Alcala-Fdez (2012) was used. The outputs of the inference engines 1 and 2—outputs which are crisp values—are then partitioned into 3 levels (Low/Medium/High) and represented by triangular fuzzy set mapped into a relative scale as described for the inputs. These outputs correspond to the input fuzzy sets used by the inference engine 3.
The results of this third inference engine are represented by a triangular fuzzy set partitioned and mapped in the same way as outputs of the inference engine 1 and 2. This last triangular fuzzy set is then defuzzified into a single crisp value; the intrinsic vulnerability index.
Remember that the scale of analysis corresponds to a node in hydraulic model that could represent a group of consumers or potential intrusion point. So even if vulnerability analysis deals with assets, the intrinsic vulnerability index has to be affected to the nearest consumption node of the intrusion point. The estimation of criticality is also achieved at nodes level, it is obtained by crossing two assessments, the spread magnitude of contaminant which is output of sensitivity analysis and the intrinsic vulnerability index.
3 Case study
The proposed methodology was applied on an urban WDN delivering about 400 000 inhabitants along 1082 km of pipes. WDN operation was modelled with help of hydraulic model computed by Porteau® 4.0 (Porteau 2016) of about 9200 consumption nodes, 11000 pipes and around 2300 loops. The Hydraulic model is mainly used for simulating contaminant spread into the network.
3.1 Sensitivity analysis using multi-criteria approach
The following section details the implementation of the analysis to the water users belonging to the groups 1, 2 and 3 (persons) and the group 4 (organizations). The first step consists in building GIS users database. In order to create the group of users, the water users and their characteristics have been associated with the location where the water is used or consumed. Two different geo-referenced databases have been used for the creation of the GIS user database: (1) the postal address database and (2) the “Sirene®”Footnote 3 database. The structures of these 2 databases have been modified in order to be aggregated into a single database of 49162 users belonging to the group 1, 2 and 3, representing persons and 9180 users belonging to group 4 representing organizations on the territory of considered WDN (see Table 3).
As explained in Sect. 2, specific criteria were defined for each category of user. For group 1, 2 and 3 users, weighting procedure of criteria is based on “Simos” procedure. The following spider plots illustrate weights attributed to the group 1, 2 and 3 criteria by 8 employees—representing stakeholders—from the water quality department of the concerned utility.
The Fig. 6 shows preferences of each decision makers according to their position and role in the operation and the management of the WDN. In order to take into account the 8 decision makers preferences, OWA (Ordered Weighting Averaging) for aggregation operator weights were generated using standard normal distribution (n = 8) with λ = 0.5. The weight vector, W is obtained as follow: W = (0.059, 0.104, 0.152, 0.184, 0.184, 0.152, 0.104, 0.059).
The aggregating results using the Normal distribution are summarized in Table 4 and are plotted in Fig. 6.
The value of orness (that measures the degree of disjunction) α is 0.5 as expected. Regarding the dispersion the high value close to maximum value of ln(8) ≈ 2.08 indicates that the OWA weights generated using Normal distribution use information from “most” of the arguments. This situation indicates that OWA aggregating results tends to a trade-off solution regarding to decision maker answers. Table 5 describes in details the utility functions, which have been used to evaluate the performance of the criteria according to normalized scale between 0 and 1 as shown by Fig. 7.
For each consumption node a weighted sum is calculated based on defined utility functions. The obtained value serves for nodes sorting in order to identify the most sensitive nodes. Figure 8 illustrates some of them in a part of the WDN.
Results analysis indicates a relatively homogenous geographical distribution of the most sensitive users. It should however be noted a slightly higher density of sensitive users in downtown. The sensitive users’ distribution highlights clusters, which are located in different parts of the WDN. The Groups 1, 2 and 3 most sensitive users are mostly composed by hospitals; residential care activities for elderly; collective housing; and governmental buildings.
As for groups 1, 2 and 3, the normal distribution has been used in order to aggregate the preferences of 8 decision makers for the group 4. The aggregating results are summarized in the Table 6.
Table 7 describes in details the utility functions, which have been used to evaluate the performance of the criteria (Fig. 9).
It seems that a higher density of users from group 4 is in downtown. This finding is consistent with sensitivity criterion definition and weighting which provide a higher sensitivity score to catering, restaurant and food production (Tables 8, 9).
3.2 Vulnerability analysis
The following section describes how the GIS WDN asset database has been built and used for the inference engine which enables to aggregate the vulnerability criteria for assessing vulnerability index.
In order to define as exhaustively as possible the potential intrusion points, several geo-referenced information layers have been collected.
Seven different layers have been combined: private connection (49162 items), fire hydrant (4824 items), underground hydrant (4824 items), flow rate measuring station (83 items), sampling point pit (261 items), air bleeding (141 items) and valves box (382 items). As a result, 58 299 intrusion points among which more than 84% are private connections constitute the GIS WDN asset database.
As a reminder, the intrinsic vulnerability is the combination of the structural vulnerability and the vulnerability linked to the environment of the intrusion point. Four criteria for vulnerability analysis Cv i have been defined as follow:
-
Ease of installation and implementation of the contamination device (Cv 1)
-
Level of protection of the intrusion site (Cv 2)
-
Ease of physical access to the intrusion site (Cv 3)
-
Level of surveillance of the intrusion site (Cv 4)
The evaluation of criteria Cv 1 and Cv 2 has been done according to a specific study related to characteristics of hydraulic devices.
The evaluation of criteria Cv 3 and Cv 4 takes into consideration the environment of the asset. To describe this aspect, the presence of road (primary and secondary) and green spaces (as a public place) has been superimposed on the intrusion point database. Furthermore, the additional information provided by the item itself (private or public) completes the analysis. As a result, the following normalized scores have been applied for the evaluation of criteria.
Thanks to these scores, the vulnerability of each intrusion point is calculated. The list of intrusion points is recorded into an MS excel file and is scanned by a fuzzy logic java program which calculate the intrinsic vulnerability using inference engine. As explained before, even if vulnerability analysis is conducted on WDN asset, results should be attached to consumption node in order to be able to link both sensitivity and vulnerability analysis.
It appears that the number of consumption nodes (14889) is 5 times less than potential intrusion points (58299), which means that several WDN assets are connected to the same node after transfer. So, the retained vulnerability value to be assigned to a given node is the maximum value of vulnerability among the WDN assets connected to the node. Finally 8632 model nodes are assigned with a value of intrinsic vulnerability strictly greater than zero. Among these vulnerable nodes 28.5% (2458 nodes) have a maximum value of intrinsic vulnerability.
In order to finalize the vulnerability analysis, it is necessary to assess the contaminant spread magnitude into the WDN. This step uses a specific module in Porteau® software based on an inverse transport module. In our approach this inverse simulation starts from the most sensitive users and enables us to identify the contaminant nodes. The proposed methodology assumes that the correspondence between existing users and consumption nodes as represented by the hydraulic model is obtained by gathering several users in a given node with the help of specific transfer ratio. This ratio is equal to 50 for users group 1, 2 and 3 and it is equal to 10 for the group 4. This grouping procedure leads to obtain 7458 model nodes with a value of sensitivity strictly greater than zero. For practical reasons, the 1% most sensitive nodes (75) are selected to be considered as potential targets.
The expected results are the potential sources of contamination of these 75 nodes across a defined elapsed time window. In order to take into account the worst-case scenario, two contamination-time periods have been defined, each time period matching with the two daily water consumption peak periods: (1) from 6 to 9 am and (2) from 6 to 8 pm. As a result and represented in yellow in Fig. 10, 43% of total nodes have been identified as potential sources of contamination of the 1% most sensitive users.
3.3 Criticality analysis
Criticality analysis prioritizes the most contaminant and vulnerable consumption nodes derived from vulnerability analysis.
Among potential sources of contamination obtained by backtracking, 56% of contaminant nodes are assigned with a value of intrinsic vulnerability strictly greater than zero. By assuming that a critical node is both contaminant and vulnerable, vulnerable nodes have been sorted according to their frequency of occurrence as contaminant nodes. On that basis, nodes that occur more than one hundred times are considered as the most frequent vulnerable contaminant nodes. At the end, 483 nodes are retained as pathways for the contaminant intrusion and define the set of critical nodes from where an attack could harm severely WDN consumers. The Fig. 11 shows some of critical nodes.
The set of critical intrusion points constitute a prerequisite for mitigating the capacity of attackers to contaminate WDN. The assessment of possible pathways is not enough, even if potential actions to secure WDN are not addressed in the current paper, they constitute one of the goals of criticality analysis, the assessment itself is not sufficient. Specific actions should be planned and implemented to secure WDN. The efficacy of these corrective actions can be measured by re-implementing criticality analysis in order to check if the number of critical points for example decreases. It appears that criticality analysis is a continuous process of improvement. Criticality analysis provides relevant intermediate results for risk assessment by defining the potential intrusion points that should be handled in the simulation of contamination scenarios in order to assess potential consequences of an intentional contamination.
4 Conclusions
The developed methodology allows enhancing the knowledge of WDN manager against the capacity of attackers to harm WDN unequipped with EWS. The main added value of presented work concerns the achievement of innovative and integrated analysis by matching both consumption nodes, considered as location of consumption and assets considered as potential targets of an attack. The criticality analysis is based on the understanding of sensitivity of consumer according to their uses and the vulnerability of WDN unequipped with sensors and without EWS against potential attacks. For both analysis, the decision maker preference is taken into account by the co-built of specific criteria, evaluation functions and fuzzy membership functions. So the effective improvement is on the methodological and practical point of view. A detailed panorama for both methodology and its implementation is presented. One of the main backgrounds of the current work concerns the possible distortion between the conceptual model and reality. Data availability, the existence of hydraulic model and WDN asset GIS are required to conduct a reliable criticality analysis. Many adaptations and modifications of existing data are required in order to implement the proposed methodology. The implementation is not automated; the link between steps is done manually. All these aspects could render the methodology complex but don't constitue a shortfall. Despite possible improvements of WARNING methodology, it offers the possibility to WDN manager to conduct a risk analysis in structured and reproducible way. It allows identifying the most critical points that could constitute potential pathways for intentional contamination and possible locations to install sensors for water quality as a part of an EWS.
The step after consists in proceeding risk analysis by generating contamination scenario based on matched critical points to assess the potential consequences both on consumers and WDN assets. Risk analysis deals with the type of potential risks (economic, health, environmental, social, etc.) and how they could be measured. These aspects will be addressed in a following paper.
Notes
Risk = Consequences × Threat × Vulnerability.
We will talk further about OWA weights in order to avoid confusion with the weights assigned to the sensitivity criteria by the decision makers.
«Système Informatisé du Répertoire National des Entreprises et des Établissements» Governmental database of all French public and private organisations.
References
Ailamaki A, Faloutos C, Fischbeck PS, Small MJ, VanBriesen J (2003) An environmental sensor network to determine drinking water quality and security. ACM SIGMOD Rec 32(4):47–52
American Society for Mechanical Engineering (ASME) (2006) RAMCAP: the framework (version 2.0). ASME Innovative Technologies Institute, LLC
Augeraud P, Touaty M (2002) Consommation d’eau par les secteurs industriels. Planistat France. Rapport final
Bernard R, Bouyssou D (1993) Aide multicritère à la décision: Méthodes et cas, Paris, Economica, ISBN 2-7178-2473-1
Cingolani P, Alcala-Fdez J (2012) jFuzzyLogic: a robust and flexible fuzzy-logic inference system language implementation. In: FUZZ-IEEE, pp 1–8. Citeseer. http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.415.3325&rep=rep1&type=pdf. Accessed 31 Aug 2015
Clark R, Chandrasekaran L, Buchberger S (2008) Modeling the propagation of waterborne disease in water distribution systems: results from a case study. 8th water distribution systems analysis symposium 2006, Cincinnati, USA, pp 1–20. doi:10.1061/40941(247)71
Copeland C (2010) Terrorism and security issues facing the water infrastructure sector. In: Report for congress, congressional research service, order code RS21026, Washington, DC, USA. https://www.fas.org/sgp/crs/terror/RL32189.pdf. Accessed May 10 2016
Di Nardo A, Di Natale M, Guida M, Musmarra D (2013) Water network protection from intentional contamination by sectorization. Water Resour Manag 27(6):1837–1850
Di Nardo A, Di Natale M, Musmarra D, Santonastaso GF, Tzatchkov V, Alcocer-Yamanaka V-H (2014) A district sectorization for water network protection from intentional contamination. 12th international conference on computing and control for the water industry, CCWI2013. Procedia Engineering, vol 70, pp 515–524. doi:10.1016/j.proeng.2014.02.057
Ezell BC, Farr J, Wiese I (2000) Infrastructure risk analysis of municipal water distribution system. J Infrastruct Syst 6(3):118–122
Figueira J, Roy B (2002) Determining the weights of criteria in the ELECTRE type methods with a revised Simos procedure. Eur J Oper Res 139(2):317–326
Francisque A, Rodriguez MJ, Sadiq R, Miranda LF, Proulx F (2009) Prioritizing monitoring locations in a water distribution network: a fuzzy risk approach. J Water Suppl Res Technol AQUA 58(7):488–509
Hall J, Zaffiro AD, Marx RB, Kefauver PC, Krishnan ER, Herrmann JG (2007) Online water quality parameters as indicators of distribution system contamination. J Am Water Works Assoc 99(1):66–77
Hart WE, Murray R (2010) Review of sensor placement strategies for contamination warning systems in drinking water distribution systems. J Water Resour Plan Manag 136(6):611–619
Islam N, Farahat A, Al-Zahrani MAM, Rodriguez MJ, Sadiq R (2015) Contaminant intrusion in water distribution networks: review and proposal of an integrated model for decision making. Environ Rev 23(3):337–352
Murray RE, Grayman WM, Savic DA, Farmani R (2010) Effects of DMA redesign on water distribution system performance. Integrating water systems—Boxall & Maksimovíc (eds)© 2010Taylor & Francis Group, London, ISBN 978-0-415-54851-9
Nilsson KA, Buchberger SG, Clark RM (2005) Simulating exposures to deliberate intrusions into water distribution systems. J Water Resour Plan Manag 131(3):228–236
Panigrahi DP, Mujumdar PP (2000) Reservoir operation modeling with fuzzy logic. Water Res Manag 14:89–109
Porteau (2016) Porteau 4.0, Logiciel de modélisation hydraulique. http://porteau.irstea.fr/. Accessed May 10, 2016
Rasekh A, Brumbelow K (2013) Probabilistic analysis and optimization to characterize critical water distribution system contamination scenarios. J Water Res Plan Manag 139(2):191–199
Sadiq R, Kleiner Y, Rajani B (2007) Water quality failures in distribution networks—risk analysis using fuzzy logic and evidential reasoning. Risk Anal 27(5):1381–1394
Simos J (1990) L’évaluation Environnementale: Un Processus Cognitif Négocié. Thèse de doctorat. DGF-Lausanne, Suisse
SMaRT-onlineWDN (2015) http://www.smart-onlinewdn.eu/. Last visit on 5 Oct 2015
Tchórzewska-Cieślak B (2011) Fuzzy failure risk analysis in drinking water technical system. Reliab Theory Appl 1(20):138–148
Tesfamariam S, Sadiq R (2006) Risk-based environmental decision-making using fuzzy analytic hierarchy process (F-AHP). Stoch Environ Res Risk Assess 21(1):35–50
Torres JM, Brumbelow K, Guikema SD (2009) Risk classification and uncertainty propagation for virtual water distribution systems. Reliab Eng Syst Saf 94(8):1259–1273
Ung H (2016) Quasi real-time model for security of water distribution network. Modeling and simulation. Université de Bordeaux, PhD Thesis. https://tel.archives-ouvertes.fr/tel-01310849/. Accessed Mar 2017
Ung H, Piller O, Gilbert D, Mortazavi I (2013) Inverse transport method for determination of potential contamination sources with a stochastic framework. In: World environmental and water resources congress, ASCE, pp 798–812. http://ascelibrary.org/doi/abs/10.1061/9780784412947.077. Accessed 28 Aug 2015
US EPA (2003) Response protocol toolbox: planning for and responding to drinking water contamination threats and incidents. http://www.epa.gov/safewater/watersecurity/pubs/guide_response_overview.pdf. Accessed 28 Aug 2015
Xu Z (2005) An overview of methods for determining OWA weights. Int J Intell Syst 20(8):843–865
Yager RR (1998) New modes of OWA information fusion. Int J Intell Syst 13(7):661–681
Acknowledgements
The work presented in the paper is part of the French-German collaborative research project SMart-OnlineWDN that is funded by the French National Research Agency (ANR Project: ANR-11-SECU-006) and the German Federal Ministry of Education and Research (BMBF; Project: 13N12180).
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
The first inference engine concerns the assessment of structural vulnerability index as illustrated in the Fig. 12.
Table 10 illustrates the rule base for inference 1 in order to estimate the structural vulnerability. IF Level of protection is “P” AND Ease of installation of the injection device is “I” THEN Structural vulnerability is “SV”.
The second inference engine aims at assessing the vulnerability of intrusion point linked to its environment as illustrated by Fig. 13.
Table 11 illustrates the rule base for inference 2 to estimate the intrinsic vulnerability linked to the environment. IF Level of surveillance is “S” AND Ease of physical access is “A” THEN Vulnerability linked with the environment is “VE”.
The last inference engine concerns the assessment of intrinsic vulnerability index based on the aggregation of previous indexes. The knowledge-base of inference 3 is illustrated by the Fig. 14.
The Table 6 illustrates the rule base for inference 3 to estimate the intrinsic vulnerability linked to the environment. IF Vulnerability linked with the environment of the intrusion site (VE) is “SE” AND Structural Vulnerability is SV” THEN Intrinsic Vulnerability is “IV” (Fig. 14).
Rights and permissions
About this article
Cite this article
Nafi, A., Crastes, E., Sadiq, R. et al. Intentional contamination of water distribution networks: developing indicators for sensitivity and vulnerability assessments. Stoch Environ Res Risk Assess 32, 527–544 (2018). https://doi.org/10.1007/s00477-017-1415-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00477-017-1415-y