Abstract
In this paper, the benefit of distinguishable diversity order within a co-operative relay system is exploited to overcome the problem of secure communication in an underlay wiretap cognitive radio network. This network is in a coexistence with a primary transceiver network and it is subjected to multiple eavesdropping attacks which employ a specific interception strategy. To improve the physical layer security, simple relay selection schemes will be proposed that aims at maximizing the minimum of the dual hop communication secrecy rates under primary network constraints. For Rayleigh fading channels, exact and asymptotic closed form expressions will be derived for the secondary system outage and secrecy rate. Furthermore, based on the network topology, tight inner and outer bounds will subsequently be derived on the system secrecy outage probability. By employing analytical and simulation results, the gain of the system diversity order is obviously investigated and emphasized.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Cognitive radio network (CR) is a useful tool for solving the problem of scarcity of spectral resources and to provide a spectral efficiency by licensed/unlicensed spectrum sharing [1]. In cognitive radio networks, it is permissible to unlicensed secondary users (SUs) to access the spectrum of licensed primary users (PUs) without interfere the PUs. To preserve a certain quality of service (QoS) for unlicensed/secondary users while leveraging a limited (uninfluenced) interference to licensed/primary users, the assistance of co-operative relays in cognitive radio networks were utilized extensively [2].
Mainly, co-operative relays were proposed to promote the system performance and obtain signaling and diversity gains. This paradigm was devoted to get rid of the problem of extending the coverage of wireless networks [3,4,5,6,7,8]. Specifically, promising relay protocols had been studied to forward the secondary source message in a cognitive radio system to the destination [9,10,11,12,13,14]. However, due to wireless broadcasting, the physical layer security (PLS) is vulnerable to illegitimate benefits. Securing and protecting issues of the physical layer against eavesdroppers were extensively investigated [15,16,17,18,19,20].
In fact, cognitive radio networks may be classified with respect to spectrum sharing or access techniques into: (1) overlay CR [21], [22] and (2) underlay CR.
In an overlay CR, the SUs have to detect the spectrum holes to maintain their own communication which can be hardly performed in the dense areas due to the lack of empty resources.
Alternatively, underlay cognitive radio network is a crucial network topology for both the academicals and industrial network designers as it provides concurrent cognitive/non-cognitive communications [23, 24]. To achieve secure and reliable communication within such a network, conflict objectives of interest should be maintained:
-
1.
Making the secondary network coverage as large as possible while protecting both primary and secondary networks from interference.
-
2.
Satisfying adoptable (QoS) requirements for both primary and secondary users.
-
3.
Preventing external attackers from overhearing secure and confidential information.
Anywhere, there exist some recent researches in the context of secure underlay CR that aims at enhancing the secrecy performance by exploiting the statistical characteristics of the wireless channels regarding interference constraint requirements [25,26,27,28,29]. For instance, in [25] the authors derived a closed form expression of some performance metrics, i.e., outage probability and secrecy outage probability, for multicasting system in the presence of multiple eavesdroppers. In [26] single and multi-relay selection schemes were investigated where security and reliability tradeoff issues were examined. In [27] the case of unknown channel state information CSI about the attackers (sub-optimal relay selection) was assumed. Regenerative multi-relay system was introduced in [28]. Reference [29] investigated licensed/unlicensed users with dual sources of interference in both directions. Unfortunately, it did not consider the security issue.
Very recently, in [30] the authors considered a secure dual-hop communication where an eavesdropper can overhear the transmission from both the direct and the relayed links. Thus, the eavesdropper performs maximal radio combining (MRC) or selection combining (SC) of the signals. Still, this has not been discussed in terms of secure underlay cognitive radio networks. In [31] the authors proposed three relay selection schemes to improve PLS in an underlay CR in the presence of multiple PUs. Unfortunately, they did not consider the effect of interference from the PUs to SUs.
To the best of our knowledge, in all of the above mentioned works (and the references therein) the mutual interference between PUs and SUs have not been highlighted especially in the presence of multiple secondary eavesdroppers. In particular, the impact of joint constraints of interference and security on the performance of both primary and secondary networks involves a tradeoff. Motivated by these considerations, a novel secure secondary communication system that incorporates cooperative diversity will be investigated. In particular, the fading characteristics will be exploited to provide useful insights regarding the main factors that regulate the secrecy performance when both direct and relayed links are overheard under all possible interference constraints. The contributions of this paper are summarized as follows:
-
We propose relay selection criteria for the per-hop and the dual-hop communications to improve the PLS under the primary/secondary interference constraints.
-
We evaluate the secrecy performance and derive new closed form expressions for some important metrics, i.e., achievable secrecy rate, outage probability and asymptotic outage probability.
-
The impact of cooperative diversity of relay selection is characterized when perfect or statistical CSI of eavesdroppers are known.
-
Thereafter, system inner and outer bounds are also derived. Those bounds become tight at high transmitted signal to interference noise ratio (SINR) in the considered system.
The rest of the paper is organized as follows. In Section II the system analysis and the optimal relay selection conditions are statistically investigated. Also, the effect of the primary user’s constraints and impact of diversity order are clarified. In Section III we evaluate the performance metrics. Simulation results are depicted in Section IV. Section V concludes the paper.
2 System and Channel Models
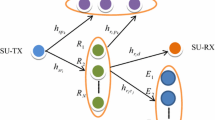
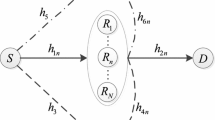
Here, we consider a wiretap cognitive radio network. It is a dual-hop decode and forward relay assisted network. It consists of the following nodes; one secondary user source, \( S \), set of \( N \) decode and forward (DF) relays, (\( R_{i} , 1 \le i \le N \)), one secondary user destination, \( D \), one primary user transmitter, \( P_{Tx} \), one primary user receiver, \( P_{Rx} \), and multiple \( M \) eavesdroppers, (\( E_{j} , 1 \le j \le M \)). All nodes are equipped with a single antenna.
2.1 The System Model
We rely on a worse-case model, where the secondary source transmitter transmits a confidential information to the secondary receiver in the presence of multiple eavesdroppers with the aid of \( N \) trusted DF relays, while the eavesdroppers try to overhear and attack all of the communication paths between the secondary source, \( S \), and destination, \( D \).
Such an underlay spectrum sharing cognitive radio network in coexistence with a primary user network is shown in Fig. 1. It is assumed that the secondary network communication follows an interference power constraint condition which represents the maximum allowable transmit power of both the secondary source and relays. Thus, the interference power does not exceed a threshold limit \( P \) at the primary receiver end.
It is further assumed that all of the receiving nodes are confirmed to know global channel state information (CSI) and either instantaneous information about eavesdroppers or statistical CSI is available at the end of the secondary user source, \( S \).Footnote 1 Moreover, the secondary user destination, \( D \), and relays are subjected to interference signals from the primary transmitter, \( P_{Tx} \). All communication channels are quasi-static and flat fading Rayleigh channels. No direct path from \( S \) to \( D \) is found due to deep fading conditions. Communication takes place in a half duplex mode through two phases.
In the first phase S transmits a power constraint signal while the relays listen, type of non-colluding eavesdroppers,Footnote 2 i.e., multiple or co-operative eavesdroppers, try to overhear through wiretap channels.
In the second phase, the relays listen in a co-operative scheme. Then, one potential relay node is selected out of the set that successfully decodes the source message to forward the re-encoded messages toward the destination such that this relay satisfies a certain optimization condition. However, the eavesdroppers’ system tries to again overhear the second path through another dedicated wiretap channel.
A co-operative communication method based on optimal selection scheme is proposed to select the relay that has the best maximum to forward the source message to the destination.
2.2 The Communication Channels
Since it is assumed that all communication channels follow Rayleigh fading distributions, let us generally define that the fading coefficients \( \gamma_{q,r} = \left| {h_{q,r} } \right|^{2} ,q,r \in \left\{ {s,i,p, j, d} \right\} \) satisfy Rayleigh fading conditions and undergo independent exponential distributions, i.e., be exponential random variables (exponential R.V.s) \( with\;means\;\lambda_{q,r} \), where their cumulative density functions and probability density functions, i.e., CDF and PDF, can be expressed by
In the first phase, \( S \) sends its message signal to \( R_{i} \) with the constraint power
Where \( h_{s,p} \) is the \( S - P \) channel fading coefficient and \( P \) is the constraint power at \( P_{Rx} \). In the vicinity of \( R_{i} \), the received signal can be expressed as
Where \( h_{s,i} \) is the \( S - R_{i} \) channel fading coefficient and \( x_{s,i} \) is the \( S \) transmitted symbol of the \( S - R_{i} \) link, \( h_{p,i} \) is the channel fading coefficient of the \( P_{Tx} - R_{i} \) interference signal, \( x_{p,i} \) is the corresponding transmitted interference symbol with power \( P_{p} \) and \( n_{i} \sim\,CN\left( {0,N_{0} } \right) \) is an additive white Gaussian noise (AWGN) signal.
In the second phase, \( R_{i} \) forwards its signal to D after successful decodingFootnote 3 with the constraint power
Where \( h_{i,p} \) is the \( R_{i} - P \) channel fading coefficient. The received signal at \( D \) can be expressed as
Where \( h_{i,d} \) is the \( R_{i} - D \) channel fading coefficient and \( x_{i,d} \) is the transmitted relay, \( R_{i} \), symbol of the \( R_{i} - D \) link with power \( P_{i} \), \( h_{p,d} \) is the channel fading coefficient of the \( P_{Tx} - D \) interference signal, \( P_{p} \) is the primary transmitted interference power and \( n_{d} \sim\,CN\left( {0,N_{0} } \right) \) is an additive white Gaussian noise (AWGN) signal.
Considering the worst-case scenario, eavesdropper \( j \) can recover the interference from the primary user and the received signals in the first and the second phases can be given by
Where \( h_{\mu ,j} , \mu \in \left\{ {s,i} \right\} \), is the channel fading coefficient of the overheard signals from both \( S \) and \( R_{i} \) to \( E_{j} \), \( x_{\mu ,j} \) is the corresponding overheard symbol and \( n_{j} \sim\,CN\left( {0,N_{0} } \right) \) is an AWGN with respect to the jth eavesdropper end.
2.3 The Secrecy Capacity
Let us first define the concept of maximum achievable secrecy rate (secrecy capacity) as [32]
Where \( \left[ x \right]^{ + } \) represents \( max\left( {0,x} \right) \), \( C_{M} = \frac{1}{2}\log_{2} \left( {1 + \gamma_{M} } \right) \),Footnote 4\( C_{E} = \frac{1}{2}\log_{2} \left( {1 + \gamma_{E} } \right) \), \( \gamma_{M} \), \( \gamma_{E} \) are the capacity of the main channel, the capacity of the wiretap channel, the SINR of the main channel and the SINR of the wiretap channel, respectively.
Hence, the achievable transmission rate of the \( S - R_{i} \) and \( R_{i} - D \) channels can be given by
Where \( \gamma_{s,i} \) and \( \gamma_{i,d} \) can be formulated as
Correspondingly, the achievable wiretap transmission rate of the \( S - E \) and \( R_{i} - E \) channels (intercepted by the eavesdropping system \( J \)) can be given by
Where \( \gamma_{s,j} \) and \( \gamma_{i,J} \) can be formulated as
Comparatively, the achievable secrecy rate which is intercepted by the eavesdropping system \( J \) can be rewritten for the two communication phases as
Where \( \gamma_{{E_{J} }} \), \( E_{J} \in \left\{ {\left( {s,J} \right),\left( {i,J} \right)} \right\} \), is the SINR at the eavesdropping system \( J \), the superscript \( \omega \), \( \omega \in \left\{ 1 \right\}\;{\text{or}}\;\omega \in \left\{ 2 \right\} \), denotes the first phase or the second phase, \( Z_{1,\omega } = \frac{P}{{N_{0} }}\psi_{1,\omega } \), \( Z_{2,\omega } = \frac{{P_{p} }}{{N_{0} }}\psi_{2,\omega } + 1 \), \( Z_{3,\omega } = \frac{P}{{N_{0} }}\psi_{3,\omega } \), \( Z_{4,\omega } = \psi_{4,\omega } \), \( \psi_{1,1} \sim \left| {h_{s,i} } \right|^{2} , \psi_{1,2} \sim \left| {h_{i,d} } \right|^{2} \), \( \psi_{2,1} \sim \left| {h_{p,i} } \right|^{2} ,\psi_{2,2} \sim \left| {h_{p,d} } \right|^{2} \), \( \psi_{3,1} \sim \left| {h_{s,J} } \right|^{2} ,\psi_{3,2} \sim \left| {h_{i,J} } \right|^{2} \), \( \psi_{4,1} \sim \left| {h_{s,p} } \right|^{2} \;and\;\psi_{4,2} \sim \left| {h_{i,p} } \right|^{2} \) of the first phase or the second phase, respectively.
In the following, we derive formulas for the cumulative and probability density functions, i.e., CDF and PDF, of the SINR of the two communication phases, considering the proposed selection schemes and the interception strategies, then, we use them to obtain closed form expressions for important performance metrics such as the secrecy outage probability and the non-zero achievable secrecy rate.
3 Relay Selection Schemes and Performance Metrics
Our analysis will be started with the per-hop relay selection scheme. It is remarkable that the per-hop selection may replace the dual-hop one, if perfect CSI information about the location of the eavesdropping system indicates that the eavesdroppers reside within one of the two communication phases.
3.1 Per-hop Relay Selection Schemes
In this sub-section, we propose per-hop relay selection schemes regarding one side of the secondary network transmission. If it is confirmed that the eavesdropping system reside within one of the two communication phases, it is better to derive the cooperative relay to select the one that maximizes the secrecy rate within the phase of the eavesdroppers’ residence. Let the per-hop relay selection be defined as
Where \( i_{per - hop} \) is the index of the selected relay.
3.1.1 Relay Selection Scheme at the First Phase Side
At this side, the selected relay depends only on the SINR of the main channel where \( C_{sj,1}^{{}} = \frac{1}{2}\log_{2} \left( {\frac{{1 + \gamma_{M} }}{{1 + \gamma_{{E_{J} }} }}} \right) \), \( M \in \left\{ {\left( {s,i} \right)} \right\} \), \( E_{J} \in \left\{ {\left( {s,J} \right)} \right\} \), as investigated by the following theorem.
Theorem 1
The relay selection rule according to (16) is determined statistically by selecting\( i \)that maximizes The CDF of the achievable secrecy rate\( \left( {i.e. C_{sJ,1}^{{}} } \right) \)of the first communication phase as,
where\( \Omega _{p,i} = \left( {\lambda_{p,i} \frac{{P_{p} }}{{N_{0} }}} \right)^{ - 1} ,\Omega _{s,i} = \left( {\lambda_{s,i} \frac{P}{{N_{0} }}} \right)^{ - 1} , \)and\( \gamma \)is the threshold SINR.
Proof
Let \( h_{s,i} \) and \( h_{p,i} \) be Rayleigh R.V. s, then, the PDF and the CDF of \( X_{s,i} = \frac{P}{{N_{0} }}\left| {h_{s,i} } \right|^{2} \) will take the forms
respectively, and after some algebraic manipulation the PDF of \( Y_{p,i} = \frac{{P_{p} }}{{N_{0} }}\left| {h_{p,i} } \right|^{2} + 1 \) can be expressed as
Thus, the CDF of the R.V. \( Z_{i} = \frac{{{\text{X}}_{s,i} }}{{Y_{p,i} }} \) is given by
where the previous Eq. follows after applying the following integral
Consequently, (17) immediately follows after some algebraic manipulations by using
It can be concluded that, this relay selection is briefly a conventional selection rule.□
3.1.2 Relay Selection Scheme at the Second Phase Side
At the second phase side, the selected relay depends on \( C_{sJ,2}^{{}} = \frac{1}{2}\log_{2} \left( {\frac{{1 + \gamma_{M} }}{{1 + \gamma_{{E_{J} }} }}} \right) \), \( M \in \left\{ {\left( {i,d} \right)} \right\} \), \( E_{J} \in \left\{ {\left( {i,J} \right)} \right\} \), where the \( R_{i} - E_{J} \) channel fading coefficient has a great impact on the decision of the relay selection. Thus, two applicable cases of eavesdropping are adopted and investigated as follows.
Case 1: Maximum of the eavesdroppers:
In this case, the strongest attacker is picked up. Thus, the group SINR is considered by the one that has the highest SINR and is given by,
Let \( \left| {h_{i,j} } \right|^{2} \) be an exponential R.V., then, the CDF of \( Z_{3,2} = \frac{P}{{N_{0} }}\left| {h_{i,J} } \right|^{2} \) can be denoted as follows
Where \( \Omega_{i,j} = \left( {\lambda_{i,j} \frac{P}{{N_{0} }}} \right)^{ - 1} \). By using (23) the CDF of \( Z_{3,2} \) will take the form
By applying following relation
Then, the PDF of can be expressed as
Theorem 2
The relay selection rule according to (16) is determined statistically by selecting\( i \)that maximizes The CDF of the achievable secrecy rate\( \left( {i.e. C_{sJ,2}^{{}} } \right) \)of the second communication phase can be derived as,
where
where\( \Omega _{\text{i,p}} = \left( {\uplambda_{\text{i,p}} } \right)^{ - 1} ,\Omega _{\text{i,d}} = \left( {\uplambda_{\text{i,d}} \frac{{{\text{P}}_{{{\text{R}}_{\text{p}} }} }}{{{\text{N}}_{0} }}} \right)^{ - 1} \)and\( \upgamma \)is the threshold SINR.
Proof
For the second communication phase, one can innovate in (15) that the relay selection relies again only on \( i \) which is independent of \( Z_{2,2} \).
Firstly, the CDF of the R.V. \( \sigma_{i} = \frac{{1 + Z_{1,2} \text{ / }Z_{4,2} }}{{1 + Z_{3,2} \text{ / }Z_{4,2} }} \to F_{{\sigma_{i} }} \left( \sigma \right) = Pr\left( {\sigma_{i} \le \sigma } \right) \) can be derived as follows
Let the CDF of \( Z_{1,2} \) takes the forms
By using (28) and after some algebraic manipulations, the PDF \( \sigma Z_{3,2} \) of can be expressed as
For simplicity, a decomposed form can be denoted as
The PDF of the R.V. \( \left( {\sigma - 1} \right)Z_{4,2} \) is given by
Then, the PDF of \( Y_{i} = \sigma Z_{3,2} + \left( {\sigma - 1} \right)Z_{4,2} \) can be computed as
By applying the integral
Hence, \( F_{{\sigma_{i} }} \left( \sigma \right) \) can be given by
Where the following integral is solved for \( x = 1 \) as
Consequently, (29) immediately follows after some algebraic manipulations by using a similar form as (23).□
Case 2: Co-operative eavesdroppers:
In this case, the group SINR is given by,
where the eavesdroppers cooperate the MRC reception. Thus, the CDF of the R.V. \( Z_{3,2} \) can be computed as follows
where the subscripts \( \sum\nolimits_{j = 1}^{\epsilon } {\left| {h_{i,j} } \right|^{2} } \) of E represent the computation of the mean under the PDF of the R.V. \( \sum\nolimits_{j = 1}^{\epsilon } {\left| {h_{i,j} } \right|^{2} } , \in is\;an\;integer. \)
Applying recursive calculus, the CDF of \( Z_{3,2} \) will take the form,
where \( \Omega_{\text{iJ}} = {\text{aver}}_{j} \Omega_{i,j} \), the PDF (Chi square distribution) of the R.V. \( Z_{3,2} \) is determined directly by differentiating (41) by \( x \) as follows,
Theorem 3
The relay selection rule according to (16) and (42) is determined statistically by selecting\( i \)that maximizes the CDF of the achievable secrecy rate\( \left( {i.e. C_{sJ,2}^{{}} } \right) \)whose CDF can be derived as,
Proof
Applying similar steps as Theorem 2, it is necessary to compute the PDF of \( Y_{i} = \sigma Z_{3,2} + \left( {\sigma - 1} \right)Z_{4,2} \), in this case, which is given by
where the integral (36) is utilized. Consequently, \( F_{{\sigma_{i} }} \left( \sigma \right) \) is given by,
where the integral (38) is solved for \( x = 1 \) (see [ [33], Eq. (3.351.1)]). Then, (43) follows after some algebraic manipulations by using a similar form as (23).□
3.2 The Optimal Relay Selection Schemes
In the previous analysis, we state the statistical conditions of relay selection schemes for the two per-hop communication, individually. However, the relay selected to achieve maximum secrecy rate at one hop, can severely interrupt the reception security at the other.
To investigate the corresponding diversity analysis and propose a relay selection scheme to maintain secure and reliable communication, it suffices to check in and deal with the relay index dependent coefficients of dual hop communication phases.
Thus, in order to guarantee that neither of the separate secrecy rates falls down to a low level (i.e., which implies a security degradation), a low complexity overall relay selection scheme is adopted to select a relay, i.e., or more, out of N relays in the co-operative system that maximizes the minimum of the dual secrecy rates as follows.
3.2.1 Optimal Relay Selection in Global CSI Availability
Let \( C_{sJ,\omega }^{{}} , \omega \in \left\{ {1,2} \right\} \) denote the achievable secrecy rates at the first and the second communication phases, respectively. The optimal relay \( R_{i}^{*} \) can be formulated by maximizing the relation
Where \( C_{sJ,1,2}^{{}} = min\left( {C_{sJ,1}^{{}} , C_{sJ,2}^{{}} } \right) \). Therefore, the CDF of \( C_{sJ,1,2} \) leads directly to
Where \( \gamma = 2^{\tau } - 1 \) is the threshold capacity, \( F_{{C_{sJ,1} }} \left( \tau \right) and F_{{C_{sJ,2} }} \left( \tau \right) \) are the CDFs of \( C_{sJ,1} and C_{sJ,2} \). The CDF of \( C_{sJ,1} \) is sufficiently given by (17) and the CDF of \( C_{sJ,2} \) can be given by \( F_{{\sigma_{i} }} \left( \gamma \right) \) in (29) and (43), respectively.
The assumption of spatial independence can be exclusively deduced from the uncorrelated ordering concept where the CDF of the selected ith relay for each path satisfies
Where \( C_{sJ,1,2} \left( i \right) \) denote the achievable secrecy R.V.s of the ith relay index. For simplicity, it is assumed that for each communication phase, the order statistics of the best relay selection in (48) is independent of \( \tau \), the threshold capacity as
Thus, to evaluate (48), we have exclusively to determine \( C_{sJ,1,2} \left( i \right) \) and the diversity order statistics of the best relay selection for the system relies only on the joint order statistics of the two combined communication phases, as it will be investigated.
Let us consider that the cooperative relay system will select the same relay to interconnect the secondary source, \( S \), to the destination, \( D \), for a certain, \( r \triangleq number of selected relays \), an optimal relay selection expression can be derived from the equivalent permanent order statistics (see [34]) represented by
Where \( \sum\nolimits_{{\Im }} \triangleq \) represents the sum over all \( N! \) permutations \( \left( {i_{1} ,i_{2} ,i_{3} , \ldots i_{N} } \right)\;of\;\left( {1,2,3, \ldots N} \right) \). Let \( \gamma_{i\omega } ,\omega \in \left\{ {1,2} \right\} \), represent the SINR within the first and the second phases, respectively, where \( \gamma_{i1} = \frac{{1 + \gamma_{M} }}{{1 + \gamma_{{E_{J} }} }} \), \( M \in \left\{ {\left( {s,i} \right)} \right\} \), \( E_{J} \in \left\{ {\left( {s,J} \right)} \right\} \), \( \gamma_{i2} = \frac{{1 + \gamma_{M} }}{{1 + \gamma_{{E_{J} }} }} \), \( M \in \left\{ {\left( {i,d} \right)} \right\} \), \( E_{J} \in \left\{ {\left( {i,J} \right)} \right\} \) and \( \gamma_{i} = \mathop {\hbox{min} }\limits_{{}} \left( {\gamma_{i1} ,\gamma_{i2} } \right) \), then, \( C_{sJ,1,2} \left( i \right) \) can be replaced by \( \gamma_{i} \), by substituting \( F_{{C_{{i_{l} }} }} \left( \tau \right) = F_{{\gamma_{i} \left| {i = i_{l} } \right.}} \left( \gamma \right)\,in\,\left( {47} \right), i_{1} < i_{2} \ldots i_{N} \), the CDF of the achievable rate of the ith selected relay that has the order \( l \) can be formulated.
Finally, the optimal relay, i.e., \( R_{{i|i = i^{*} }}^{*} ,\,r = 1 \), is selected based on a robust form of (50) as
\( where\;\sum\nolimits_{{{\Im }_{l} }} \triangleq \;represents\;the\;sum\;over\;all\;permutations\;\left( {i_{1} ,i_{2} ,i_{3} , \ldots i_{N} } \right)\;of\;\left( {1,2,3, \ldots N} \right)\;that\;includes\;\left( {\begin{array}{*{20}c} N \\ l \\ \end{array} } \right)\;terms\;instade\;of\;N!terms\;in\;\left( {50} \right),\,i_{1} < i_{2} \ldots i_{N} . \)
3.2.2 Optimal Relay Selection in Statistical CSI Availability
In this subsection, we rely on the statistical data of the global CSI of all links where it is confirmed that the small and large scale computations of the channels’ characteristics do not vary drastically over a long period of time. Thus, it is sufficient to compute and test a specific performance metric such as the secrecy outage probability to decide which relay will be selected.
The secrecy outage probability is defined as the probability that the achievable secrecy rate (e.g., correspondingly SINR) falls below a desired secrecy rate (e.g., correspondingly a desired level).
Let the desired threshold levels \( \gamma_{out1} \) and \( \gamma_{out2} \) for the first and the second phases, respectively. The secrecy outage probability may be computed equivalently as
where \( \alpha \) indicates the joint probability and the last two terms follow from the fact that they are two disjoint events.
Hence, the optimal relay selection can be formulated by selecting \( R_{i}^{*} \) that minimizing the statistical secrecy outage probability by satisfying
In the next section, we are going to derive expressions for the secrecy outage probability and some other performance metrics such as non-zero achievable secrecy rate and asymptotic secrecy outage probability.
3.3 Performance Metrics
In the concerned system, one feasible method to ensure a confidential data security and reliability against eavesdropping is to transmit the data with a rate that is less than its dedicated channel capacity (i.e., from the source to destination) while maintain the difference between the transmitted and the confidential data rates larger than the channel capacity dedicated for the eavesdropping system. This guarantees that any transmitted data rate will become beyond the reliable illegal interception.
3.3.1 The Exact Secrecy Outage Probability
A special case of (52) when the communication channel requires one desired or predefined SINR level, \( \gamma \). In such a case, \( P_{{out_{i} }} \left( \gamma \right) \) of the ith relay is given by
Unlike the relay selection scheme, closed form expressions for \( P_{{out_{i} }} \left( \gamma \right) \) can be derived in terms of \( \gamma_{i1}^{{}} \) and \( \gamma_{i2}^{{}} \) as shown in the following theorems.
Let \( \upgamma_{{{\text{i}}\upomega}} = \frac{{1 + {\raise0.7ex\hbox{${\frac{{Z_{{1,\upomega}} }}{{Z_{{2,\upomega}} }}}$} \!\mathord{\left/ {\vphantom {{\frac{{Z_{{1,\upomega}} }}{{Z_{{2,\upomega}} }}} {Z_{{4,\upomega}} }}}\right.\kern-0pt} \!\lower0.7ex\hbox{${Z_{{4,\upomega}} }$}}}}{{1 + {\raise0.7ex\hbox{${Z_{{3,\upomega}} }$} \!\mathord{\left/ {\vphantom {{Z_{{3,\upomega}} } {Z_{{4,\upomega}} }}}\right.\kern-0pt} \!\lower0.7ex\hbox{${Z_{{4,\upomega}} }$}}}} \), \( \omega \in \left\{ {1,2} \right\} \), be the SINRs of the first and the second communication phases, then, we have the following cases.
Case 1: Maximum of the eavesdroppers:
Theorem 4
The CDF of the SINR \( \upgamma_{{{\text{i}}\upomega}} \), \( \upomega \in \left\{ {1,2} \right\} \), according to (28) can be derived statistically as
where
where\( \upzeta_{{1,{\text{j}}}} \in \left\{ {\upzeta_{{{\text{s}},{\text{j}}}} } \right\},\upzeta_{{2,{\text{j}}}} \in \left\{ {\upzeta_{{{\text{i}},{\text{j}}}} } \right\} \), \( \upalpha_{\text{j}} = \frac{{\Omega_{{{\text{Z}}_{{2,\upomega}} }}\upzeta_{{\upomega,{\text{j}}}} }}{{\Omega_{{{\text{Z}}_{{1,\upomega}} }} }},\quad \forall {\text{j}} = 1, \ldots {\text{M}},\quad\upbeta = \frac{{\Omega_{{{\text{Z}}_{{2,\upomega}} }} \Omega_{{{\text{Z}}_{{4,\upomega}} }} }}{{\Omega_{{{\text{Z}}_{{1,\upomega}} }} }} \), \( \left| {{ \arg }\left( {\frac{{ \Omega_{{{\text{Z}}_{{2,\upomega}} }} }}{{\Omega_{{{\text{Z}}_{{1,\upomega}} }} }}} \right)} \right| \le\uppi \)and\( \upgamma \)is the SINR threshold.
Proof
Applying similar steps as Theorem 2, the CDF of the R.V. \( \gamma_{i\omega } \) can be derived as follows
First, we have to compute the CDF of \( Z_{i\omega } = \frac{{Z_{1,\omega } }}{{Z_{2,\omega } }} \), which can be computed in a similar form as (21) using (22) as
Then, it is necessary to compute the PDF of \( Y_{i\omega } = \sigma Z_{3,\omega } + \left( {\sigma - 1} \right)Z_{4,\omega } \) in that case, in a similar way to (36)
Utilizing a similar integral as (38) (see [33, Eq. (3.353.5)]) and some algebraic manipulations the CDF of the R.V. \( \gamma_{i\omega } \) can be derived in part as
and (55) follows after rearranging the terms.□
Case 2: Co-operative eavesdroppers:
Theorem 5
The CDF of the SINR\( \gamma_{i\omega } \) (42), \( \upomega \in \left\{ {1,2} \right\} \), can be derived statistically as
Where\( \Omega _{{{\text{Z}}_{3,1} }} \in \left\{ {\Omega _{\text{sJ}} \triangleq {\text{aver}}_{\text{j}} \left( {\Omega _{{{\text{s}},{\text{j}}}} } \right)} \right\} \), \( \Omega _{{{\text{Z}}_{3,2} }} \in \left\{ {\Omega _{\text{iJ}} \triangleq {\text{aver}}_{\text{j}} \left( {\Omega _{{{\text{i}},{\text{j}}}} } \right)} \right\},\;\forall {\text{j}} = 1, \ldots {\text{M}} \), \( \upalpha = \frac{{\Omega _{{{\text{Z}}_{{2,\upomega}} }}\Omega _{{{\text{Z}}_{{3,\upomega}} }} }}{{\Omega _{{{\text{Z}}_{{1,\upomega}} }} }} \), \( \upbeta = \frac{{\Omega _{{{\text{Z}}_{{2,\upomega}} }}\Omega _{{{\text{Z}}_{{4,\upomega}} }} }}{{\Omega _{{{\text{Z}}_{{1,\upomega}} }} }} \), \( \Omega _{{\upalpha \upbeta }} =\uplambda_{\text{i}} \frac{{\Omega _{{{\text{Z}}_{{2,\upomega}} }} }}{{\Omega _{{{\text{Z}}_{{1,\upomega}} }} }} \), \( \left| {{ \arg }\left( {\frac{{ \Omega _{{{\text{Z}}_{{2,\upomega}} }} }}{{\Omega _{{{\text{Z}}_{{1,\upomega}} }} }}} \right)} \right| \le\uppi\;{\text{and}}\;\upsigma \)is the SINR threshold.
Proof
Applying similar steps as Theorem 3, the CDF of the R.V. \( \gamma_{i\omega } \) can be derived as follows
The CDF of \( Z_{i\omega } = \frac{{Z_{1,\omega } }}{{Z_{2,\omega } }} \) is given by (57). Then, the PDF of \( Y_{i\omega } = \sigma Z_{3,\omega } + \left( {\sigma - 1} \right)Z_{4,\omega } \) in that case, which is directly given as (36) by
Utilizing a similar integral as (38) (see [33, Eq. (3.353.5)]) and some algebraic manipulations the CDF of the R.V. \( \gamma_{i\omega } \) or (60) follow after rearranging the terms.□
Hence, the secrecy outage probability can be expressed by substituting in (54) and its related form of the optimal relay selection which can be likely written without order statistics as
3.3.2 The Non-zero Achievable Secrecy Rate
By employing the fact that \( \forall \epsilon \in \Re , \left( {\log_{2} \epsilon } \right) > 0\mathop \to \limits^{yields} \epsilon > 1 \), it is obtained from (56) and (61) by substituting for \( \sigma = 1 \) as in the following forms.
Let \( P_{secrecy} \) be the optimal achievable non-zero secrecy probability which occurs when there exists a non-zero secrecy capacity for the secondary communication network, namely
Where \( i^{*} \) represents the optimal relay, by considering the cases of eavesdropping \( P_{{out_{i} }} \left( 1 \right) \) can be determined as follows:
Case 1: Maximum of the eavesdroppers:
Plugging (33) and (57) into (56), solving for \( \sigma = 1 \) and using a similar integral as (36), \( F_{{\gamma_{i\omega } }} \left( 1 \right) \) is given by,
Where \( \alpha_{j} = \frac{{\Omega _{{{\text{Z}}_{{2,\upomega}} }}\upzeta_{{\upomega,{\text{j}}}} }}{{\Omega _{{{\text{Z}}_{{1,\upomega}} }} }}, \forall j = 1, \ldots M\;and\;\left| {arg\left( {\frac{{ \Omega _{{Z_{{2,\upomega}} }} }}{{\Omega _{{Z_{{1,\upomega}} }} }}} \right)} \right| \le \pi \), by substituting in (54) for \( \omega = 1\;{\text{or}}\;2 \), \( P_{{out_{i} }} \left( 1 \right) \) follows directly.
Case 2: Co-operative eavesdroppers:
Plugging (42) and (57) into (61), solving for \( \sigma = 1 \) and using a similar integral as (36), \( F_{{\gamma_{i\omega } }} \left( 1 \right) \) is given by
Where \( \left| {arg\left( {\frac{{ \Omega _{{Z_{2,\omega } }} }}{{\Omega _{{Z_{1,\omega } }} }}} \right)} \right| \le \pi \), by substituting in (54) for \( \omega = 1\;{\text{or}}\;2 \), \( P_{{out_{i} }} \left( 1 \right) \) follows directly.
3.3.3 Inner and Outer System Bounds for the Secrecy Outage Probability
As a reference relay selection scheme, system bounds can be considered by assuming that the cooperative system can possess the buffering capability [37] at the relay nodes. Therefore, the cooperative system has the option to store data for the next phase and select the two relays of the strongest secrecy rates for the two phases yielding the lowest secrecy outage probability. Thus, we can define an inner (lower) bound for the secrecy outage probability when the minimum secrecy outage probability of a dual-hop communication itself for a certain selected relay is indeed the minimum outage amongst the entire relays, namely
In contrary, the system outer (upper) bound is defined by
In this case, the maximum secrecy outage probability of a dual-hop communication itself for a certain selected relay is indeed the maximum outage amongst the entire relays.
3.4 The Asymptotic Outage Probability
Exact expressions are too complicated to interpret conceptually the impact of interference and eavesdropping for high SINR regime which represents the main agent that identifies and controls the network behavior. In the following, the effect of increasing the SINR statistically on all network parameters will be studied.
If the transmit SINR is abruptly increased toward the received nodes to enhance the system performance within the secondary network, the CDF of \( Z_{1,\omega } \) can be approximated to its first order term, simply
Upon this fact, let the other R.V. s be dependently unchanged, then, by applying similar statistical analysis the system asymptotic optimal secrecy outage probability can be expressed in a generalized form as
Where the impact of diversity order (gain) \( \eta \) will be emphasized here,Footnote 5 (e.g., it can be enhanced by using relays with distinguishable parameters). The diversity gain can be defined as the negative exponent of the average symbol error probability SEP in a log–log scale when SINR goes to infinity [35, 36] and related to the secrecy outage probability by (70), \( \kappa \) is the coding gain parameter, \( i^{*} \) is the optimal relay and \( SINR_{system} \) is the overall system SINR.
To investigate the impact of the diversity order, system high SINR and coding gain, \( P_{{out_{{i^{*} }} }}^{\infty } \) should be computed and coincided with (70), then, by extracting comparative relations for \( \kappa , SINR_{system} \;{\text{and}}\;\eta \), one can study a unified framework for the effect of those system communication metrics and build up relay selection strategies.
Accordingly, we have to compute \( P_{{out_{i} }}^{\infty } \;{\text{of}}\;{\text{relay}}\;R_{i} \) in terms of the CDF of the corresponding SINR as in (54).
Theorem 6
By considering (70) the CDF of\( \gamma_{i\omega } \)may be generally derived as
Where \( \phi_{i\omega } \) is expressed as follows:
Case of max. of eavesdroppers
where
Case of cooperative eavesdroppers
Proof
From (70), the CDF of \( Z_{i\omega } = \frac{{Z_{1,\omega } }}{{Z_{2,\omega } }} \) is given easily by
The CDF of the R.V. \( \gamma_{i\omega } \) which is given by (56) and (61) of the considerable cases can be derived here after computing the PDF of \( Y_{i\omega } \) in these cases, which are directly given by (58) and (62), respectively.
Applying similar steps as the above theorems, after utilizing a similar integral as (38) (see [33, Eq. (3.351.1–3)]), some algebraic manipulations and rearranging the terms, the CDF of the R.V. \( \gamma_{i\omega } \) (71) follows.□
Therefore, \( P_{{out_{i} }}^{\infty } of relay R_{i} \) can be expressed by substituting in (54) which leads to
By inserting (75) into a similar form of (51), it can be found that it perfectly matches (70) to the extent of
Where \( P_{{out_{{r^{*} :N}} }}^{\infty } \) represents the asymptotic secrecy outage probability of optimal rth out of \( N \) relays, C is an arbitrary constant, \( C \triangleq f\left( {\phi_{i1} ,\phi_{i2} } \right),{\rm O}\left( \gamma \right) \) are the higher order terms of \( \gamma \) and (a): follows after algebraic manipulations, equating powers and inserting
The diversity order of the system can be extracted by equating lowest order exponent of SINR to (70), this shows that the achievable diversity can be of the order of \( N - r + 1 \).
4 Simulation Results
In this section, the analytical derivations are verified to be in consistent with simulation results as well as the impact of the system parameters on the security performance will be studied. This is confirmed by performing Monte Carlo simulations with \( 10^{6} \) experimental trials.
From the previous analysis, one can find that the impact of relay interference is more severe with respect to the primary network than the source and destination and consequently, it dominates. However, we are interested in the impact of diversity gain that can be enhanced to approach \( N,N \triangleq number\;of\;relays, \) in optimal relay selection. In general, the simulation is carried assuming equal values of fading coefficients (\( \Omega_{q,r} = \Omega = 0.3\;{\text{dB}},q,r \in \left\{ {s,i,p, j, d} \right\} \)).
Figure 2 illustrates the exact curves between the outage probability and a relay transmit power while fixing the source power, i.e., relay transmitters are the dominant interfere sources of power, with different number of co-operative relays. This figure indicates a local minimum value of outage which represents the optimal value of the relay power for security interference trade off. This value can be verified by plugging the inequality of arithmetic and geometric means together, i.e., \( \prod\nolimits_{i = 1}^{N} {P_{{out_{i} }} \le \left( {\frac{1}{N}\sum\nolimits_{i = 1}^{N} {P_{{out_{i} }} } } \right)^{N} } \), into (63) and solving for the equality. This figure also compares our exposed eavesdropping models. It is obvious that the co-operative eavesdropping scheme exhibits worse performance than the maximum of eavesdroppers scheme due to its robust overhearing procedure. Increasing the number of relays adds a quite degree of freedom that improves the system performance.
For low transmitted power the outage probability begins to deteriorate until it reaches its minimum value, then, it again begins to increase by increasing the transmitted power due to primary network constraints.
In Fig. 3 a statistical CSI knowledge about the primary network i.e., \( \Omega _{p,i} ,\Omega _{i,p} ,\Omega _{s,p} \;{\text{and}}\;\Omega _{p,d} \) is considered where constraint sources of power are maintained. The performance of the secrecy outage probability against the increasing in SINR is highlighted, i.e., when \( \Omega _{s,i} =\Omega _{i,d} \). Moreover, the impact of increasing the number of relays, the inner and outer bounds are included in this figure. It is cleared that case of the maximum of eavesdroppers scheme outperforms the case of co-operative eavesdropping scheme. It is notable that the outage probability drops down when the SINR increases. The asymptotic responses and bounds approximate the exact ones to the extent that asymptotic, outer bound and exact curves are tightly compromised at high SINR. Finally, parallel slops for different values of \( N,N \triangleq number\;of\;relays \), reflect the equality of the diversity gain.Footnote 6 There exists a successful agreement between the theoretical and simulation results which justifies our derivations.
In Fig. 4, it is anticipated that the secrecy outage probability increases when moving towards the decreased order statistics of the optimal relay selection, i.e., towards the optimal rth order relay selection, given the number of active relays in the co-operative relay system. It is also worthwhile to see that the asymptotic curve exhibits wider divergence from the exact curve at low SINR, when higher order statistics relay is selected. This verifies the impact of diversity order on the system performance. However, at high SINR the asymptotic curve perfectly fits the exact one. Moreover, it is evident that the asymptotic curve is plotted using (76) by substituting \( C \triangleq f\left( {\gamma_{i1} ,\gamma_{i2} } \right) = \gamma_{i1} + \gamma_{i2} \) and neglecting the higher order terms.
An illustration for the maximum achievable secrecy rate versus the average SINR (\( \Omega_{s,i} = \Omega_{i,d} = \Omega \)) is shown in Fig. 5. Using the proposed optimal selection and constraint power sources, one can observe that there is a limited maximum capacity values “upper floor” [25] after which the secrecy rate will collapse unless the constraints are preserved. This means that at high SINR the secrecy rate is approximately fixed.
As depicted in Fig. 6, the secrecy rate decreases when the overhearing nodes “\( M \)” increase. With a target rate of the secondary network of 0.5 bits/s/Hz, \( P_{Tx} \) power of 6 dB and \( S \) power of 2 dB, it can be shown that, increasing the number of eavesdroppers causes significant degradation in the secrecy rate. For \( M \gg 1 \), the performance curve over the co-operative eavesdropping scheme or the maximum of eavesdroppers scheme is asymptotically the same.
For a selected optimal relay \( i^{*} \), our results are compared with [38, Fig. 3] where we use the same system parameters, i.e., the channel coefficients are modeled as \( \Omega_{q,r} = \left( {\frac{1}{{d_{q,r} }}} \right)^{\updelta} \), = 3, where is the path loss exponent and \( d_{q,r} \) is the distance between the node and the node . Thus, the following parameters are assumed: \( d_{{s,i^{*} }} = d_{{i^{*} ,d}} = 1 \), \( d_{s,J} = d_{s,p} = d_{{i^{*} ,p}} = 6 \), \( d_{{i^{*} ,J}} = 4 \), \( P = \vartheta P_{p} \); where \( 0 \le \vartheta < 1 \) is an arbitrary constant, \( N_{0} = 1 \) and a target secrecy rate of 0.5 bits/s/Hz. The secrecy outage probability is plotted against the secondary constraint power \( \frac{P}{{\left| {h_{s,p} } \right|^{2} }} \) as shown in Fig. 7, where for the comparison we consider MRC at the eavesdropping system (e.g., as in [38] and our cooperative eavesdropper scheme with two eavesdroppers). Different from the results in [38], it is observed that the relaxation of the constraint power by increasing the \( P_{Tx} \) transmit power can cause severe interference at the secondary networks. In [38], the secrecy outage first decreases with increase in the constraint power and later exhibits a floor because of increasing in parallel the ability of overhearing by the eavesdropping system. However, in our case, the interference of the primary network increases significantly the secrecy outage probability.
5 Conclusions
In this paper, relay selection schemes have been proposed and investigated to maintain secure communications in relay assisted underlay cognitive radio networks in the presence of multiple eavesdroppers. To evaluate the system performance, some important metrics have been computed such as secrecy outage probability and achievable secrecy rate to give an account on security and reliability trade-off parameters. Analytical expressions have been derived upon the exposed model to verify the impact of mutual interferences, sources of power and target rates of both the primary and the secondary networks in order to optimize the communication quality. Some system bounds have also been derived where the impact of their tightness at high SINR was demonstrated. Co-operative diversity adds another degree of freedom especially when the instantaneous CSI of the eavesdroppers is known. It is worth mentioning that the dual-hop secrecy optimization has replaced the per-hop one in order to jointly enhance the secrecy performance via exploiting the diversity gain. Simulation results were in accordance with the analytical ones. In the future work, we will examine the situation when the eavesdropping system realizes the same benefit of diversity order.
Notes
This assumption is reasonable when the well-known user represents a legitimate user for some applications and an eavesdropper for others.
It is nonsense considering a colluding system as it reduces the opportunity to occupy a legitimate channel.
It is supposed that all relay nodes decode the source message correctly.
The term \( \frac{1}{2} \) indicates the dual split communication protocol (the time slot is divided into two fractions of communication sub-slots).
The diversity gain can be improved to approach \( N, N \triangleq number of relays \), in this simple model by utilizing optimal relay selection and/or optimal combining.
It is noted that we simply plot one case for inner bound, outer bound and asymptotic curves so that the graphics do not interfere so as to be more visible.
References
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23, 201–220.
Liu, K. J. R., Sadek, A. K., Su, W., & Kwasinski, A. (2008). Cooperative communications and networking. Cambridge: Cambridge University Press.
Amarasuriya, G., Ardakani, M., & Tellambura, C. (2010). Output-Threshold multiple relay selection scheme for cooperative wireless networks. IEEE Transactions on Vehicular Technology, 59(6), 3091–3097.
Ikki, S. S., & Ahmed, M. H. (2009). On the performance of amplify-and forward cooperative diversity with the nth best-relay selection scheme. In Proceedings of 2009 IEEE international conference on communications (ICC’09) (pp. 1–6).
Duy, T. T., An, B., & Kong, H.-Y. (2010). A novel cooperative-aided transmission in multi-hop wireless networks. IEICE Transactions on Communications, E93.B(3), 716–720.
Laneman, J. N., Tse, D. N. C., & Wornell, G. W. (2004). Cooperative diversity in wireless networks: Efficient protocols and outage behavior. IEEE Transactions on Information Theory, 50(12), 3062–3080.
Bletsas, A., Khisti, A., Reed, D. P., & Lippman, A. (2006). A simple cooperative diversity method based on network path selection. IEEE Journal on Selected Areas in Communications, 24(3), 659–672.
Cuba, F. G., Cacheda, R. A., & Castaño, F. J. G. (2012). A survey on cooperative diversity for wireless networks. IEEE Communications Surveys & Tutorials, 14(3), 822–835.
Hasna, M. O., & Alouini, M. S. (2003). End-to-end performance of transmission systems with relays over Rayleigh-fading channels. IEEE Transactions on Wireless Communications, 2(6), 1126–1131.
Ikki, S., & Ahmed, M. H. (2009), Performance analysis of decode-and-forward incremental relaying cooperative diversity networks over Rayleigh fading channels. In Proceedings of IEEE VTC spring, Barcelona, April 2009 (pp. 1–6).
Ikki, S., Uysal, M., & Ahmed, M. H. (2009). Performance analysis of incremental-best-relay amplify-and-forward technique. In Proceedings of IEEE GLOBECOM, Honolulu, Hawaii, November 30–December 4 (pp. 1–6).
Krikidis, I., Thompson, J., McLaughlin, S., & Goertz, N. (2008). Amplify-and forward with partial relay selection. IEEE Communications Letters, 12(4), 235–237.
Suraweera, H. A., Michalopoulos, D. S., & Karagiannidis, G. K. (2009). Semi blind amplify-and-forward with partial relay selection. Electronics Letters, 45(6), 317–319.
Duy, T. T., & Kong, H.-Y. (2013). Performance analysis of incremental amplify-and-forward relaying protocols with nth best partial relay selection under interference constraint. Wireless Personal Communications, 71(4), 2741–2757.
Gopala, P. K., Lai, L., & Gamal, H. E. (2008). On the secrecy capacity of fading channels. IEEE Transactions on Information Theory, 54(10), 4687–4698.
Dong, L., Han, Z., Petropulu, A. P., & Poor, H. V. (2010). Improving wireless physical layer security via cooperating relays. IEEE Transactions on Signal Processing, 58(3), 1875–1888.
Mo, J., Tao, M., & Liu, Y. (2012). Relay placement for physical layer security: A secure connection perspective. IEEE Communications Letters, 16(6), 878–881.
Zou, Y., Wang, X., & Shen, W. (2013). Optimal relay selection for physical layer security in cooperative wireless networks. IEEE Journal on Selected Areas in Communications, 31(10), 2099–2111.
Sakran, H., Shokair, M., Nasr, O., El-Rabaie, S., & El-Azm, A. A. (2012). Proposed relay selection scheme for physical layer security in cognitive radio networks. IET Communications, 6(16), 2676–2687.
Mukherjee, A., Fakoorian, S. A. A., Huang, J., & Swindlehurst, A. L. (2014). Principles of physical layer security in multiuser wireless networks: A survey. IEEE Communications Surveys and Tutorials, 16(3), 1550–1573.
Srinivasa, S., & Jafar, S. A. (2007). Cognitive radios for dynamic spectrum access-the throughput potential of cognitive radio: A theoretical perspective. IEEE Communications Magazine, 45(5), 73–79.
Akyildiz, I. F., et al. (2008). A survey on spectrum management in cognitive radio networks. IEEE Communications Magazine, 46(4), 40–48.
Goldsmith, A., Jafar, S. A., Maric, I., & Srinivasa, S. (2009). Breaking spectrum gridlock with cognitive radios: An information theoretic perspective. Proceedings of the IEEE, 97(5), 894–914.
Tourki, K., Qaraqe, K. A., & Alouini, M. S. (2013). Outage analysis for underlay cognitive networks using incremental regenerative relaying. IEEE Transactions on Vehicular Technology, 62(2), 721–734.
Bao, V. N. Q., Trung, N. L., & Debbah, M. (2013). Relay selection schemes for dual-hop networks under security constraints with multiple eavesdroppers. IEEE Transactions on Wireless Communications, 12(12), 6067–6085.
Zou, Y., Champagne, B., Zhu, W. P., & Hanzo, L. (2015). Relay-selection improves the security-reliability trade-off in cognitive radio systems. IEEE Transactions on Communications, 63(1), 215–228.
Jindal, A., Kundu, C., & Bose, R. (2014). Secrecy outage of dual-hop AF relay system with relay selection without eavesdropper’s CSI. IEEE Communications Letters, 18(10), 1759–1762.
Kundu, C., Ghose, S., & Bose, R. (2015). Secrecy outage of dual-hop regenerative multi-relay system with relay selection. IEEE Transactions on Wireless Communications, 14(8), 4614–4625.
Salhab, A., & Zummo, S. (2014). Cognitive DF generalized order relay selection networks with imperfect channel estimation and interference from primary user. In 2014 IEEE global communications conference.
Ghose, S., Kundu, C., & Bose, R. (2016). Secrecy performance of dual-hop decode-and-forward relay system with diversity combining at the eavesdropper. IET Communications, 10(8), 904–914.
Dan Ngoc, P. T., Duy, T. T., Bao, V. N. Q., & Nhat, N. L. (2016). Security-reliability analysis for underlay cognitive radio networks with relay selection methods under impact of hardware noises. In 2016 International conference on advanced technologies for communications (ATC), Hanoi (pp. 174–179).
Bloch, M., Barros, J., Rodrigues, M. R. D., & McLaughlin, S. W. (2008). Wireless information-theoretic security. IEEE Transactions on Information Theory, 54(6), 2515–2534.
Gradshteyn, I. S., & Ryzhik, I. M. (2007). Table of integrals, series and products (7th ed.). San Diego, CA: Academic.
Vaughan, R. J., & Venables, W. N. (1972). Permanent expressions for order statistics densities. Journal of the Royal Statistical Society Series B, 34(2), 308–310.
Simon, M. K., & Alouini, M.-S. (2005). Digital communication over fading channels (2nd ed.). New York: Wiley.
Ding, H., Ge, J., da Costa, D. B., & Jiang, Z. (2011). Asymptotic analysis of cooperative diversity systems with relay selection in a spectrum-sharing scenario. IEEE Transactions on Vehicular Technology, 60, 457–472.
Ikhlef, A., Michalopoulos, D. S., & Schober, R. (2011). Buffers improve the performance of relay selection. In Proceedings of 2011 IEEE global communications conference (pp. 1–6).
Chakraborty, P., & Prakriya, S. (2017). Secrecy outage performance of a cooperative cognitive relay network. IEEE Communications Letters, 21(2), 326–329.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Saad, W., Shokair, M. & Ibraheem, S.M. On the Security of Relay Assisted Cognitive Radio Networks in the Presence of Primary Transceiver Network. Wireless Pers Commun 104, 949–977 (2019). https://doi.org/10.1007/s11277-018-6062-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-6062-1