Abstract
The security in cognitive radio networks (CRNs) has been attracting continuously growing attention due to the open and dynamic nature of cognitive radio architecture. In this paper, we propose new relay selection schemes to improve the physical layer security in CRNs. A trusted decode-and-forward relay is selected to help the secondary user (SU) transmission and improve the secrecy rate in the presence of multiple eavesdroppers and multiple primary users (PUs). The secrecy rate of the SU is characterized under both its own transmit power constraint as well as a set of interference power constraints imposed at each PU, in order to preserve its quality of service. The performance of the proposed schemes is analyzed in terms of the achievable secrecy rate and the intercept probability. Closed form expressions for the asymptotic intercept probability at high source-relays channel variances are also derived. Moreover, new derivations of some existing traditional schemes are presented and compared. The performance comparison of the proposed schemes with the schemes proposed in the literature reveals the superior of the proposed schemes.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Cognitive radio (CR) is a technology that allows the unlicensed user to access the licensed channels dedicated to a primary user (PU) without causing interference to the PU. There are two main characteristics of cognitive radios. The first is cognitive capability, which refers to the ability of the radio technology to sense information from its radio environment. The second is re-configurability, which enables a user to change the transmitting channel quickly and adaptively according to the radio environment [1]. There are three main different approaches by which secondary user (SU) access spectrum without interfering with the PU. These approaches include underlay, overlay and interweave paradigms [2]. In the underlay paradigm, SUs are allowed to operate only if their interference to the PUs is below a certain threshold. While operating in the overlay paradigm, the SUs transmit their data simultaneously with the PUs but employ sophisticated techniques that maintain (or even improve) the performance of PUs. In the interweave, the SUs sense unused frequency bands called spectrum holes to communicate without disrupting primary transmissions.
Since CR system is open and dynamic in nature, where various unknown wireless devices are allowed to opportunistically access the licensed spectrum, this make them more vulnerable to attack. The traditional security is based on cryptographic approaches; these techniques rely on secret keys and introduce additional complexities due to the dynamic distribution and management of secret key. Physical layer security paradigm is used to prevent the eavesdropper attack and assure the secure communication by exploiting the physical characteristic of wireless channel. This work was first studied by Shannon in [3] and extended by Wyner in [4], where a so-called secrecy rate is defined as the rate at which information can be transmitted confidently from a source to its intended destination. The maximum achievable secrecy rate is named the secrecy capacity [5]. To improve the physical-layer security of wireless transmissions, some recent work was proposed by exploiting the multiple-input multiple-output (MIMO) techniques [6–8], and cooperative relays [9–11].
Although physical layer security in classic wireless networks has been studied for many years, security in the physical layer of CRNs has not been investigated until recently [12–19]. Many types of attacks have been addressed in the physical layer of CRNs; namely, PU emulation (PUE), spectrum sensing data falsification (SSDF), objective function attack (OFA), jamming attack and eavesdropping attack [12]. In [13] and [14], the two classes of attacks, PUE attack and OFA were studied. The achievable secrecy rates in CRNs with external eavesdroppers have been studied in [15] and [16]. In [17], the physical layer security against eavesdropping in the CRN was investigated by introducing the multiuser scheduling scheme to achieve multiuser diversity for improving the security level of cognitive transmissions with a PU quality of service (QoS) constraint. A relay selection scheme for secrecy-constrained CRNs was proposed in [18], which studied the maximization of the achievable secrecy rate that is subjected to the interference power constraints at the PUs for different numbers of eavesdroppers and PUs, under available channel state information (CSI) assumption. For relay selection schemes in [18], the source and relay nodes transmit at maximum power and the selection process depends on the QoS requirements of the PUs. This will affect the secrecy performance especially at high transmitted power values. Moreover, a unified manner with more general system model is required to improve the secrecy performance. Particularly, relay selection schemes with power scaling at the transmission side is required to compromise the achievable secrecy rate and at the same time satisfy the required QoS at the PU, which will be investigated in this paper.
In this paper, we study secure transmission in cooperative CRNs in the presence of multiple PUs, and multiple eavesdroppers, which attempt to intercept the signal transmitted from the SU to the legitimate receiver in the CRN. The contributions of the paper are summarized as follows. Firstly, we propose new relay selection schemes to improve the physical layer security of underlay cognitive transmission in presence of multiple eavesdroppers. The effect of the presence of multiple PUs is also investigated. The proposed selection schemes consider two power constraints; transmit power constraint at both the SU and the selected relay, and received interference power constraints at the PUs. The QoS at the PUs is considered by limiting the transmitted power of the SU and the selected relay such that the interference received at each PU does not exceed a predefined interference threshold. Decode and forward (DF) relying is assumed, where one relay is selected to help forward the decoded signal to the intended receiver. Two performance metrics are considered; the achievable secrecy rate and the intercept probability. We derive closed form expressions for the asymptotic intercept probability under the assumption of high source-relays channel variances at which all relays decode the transmitted message correctly. Secondly, we investigate the traditional relay selection schemes and the scheme proposed in [18] for the comparison purpose, and new expressions of the asymptotic intercept probability for some traditional schemes that are related to the proposed scheme are derived. The performance of the proposed schemes is compared with the conventional relay selection schemes and the relay selection scheme proposed in [18].
The remainder of this paper is organized as follows. In Sect. 2, the system and channel models are introduced. In Sect. 3, the performance analysis of the proposed relay selection schemes in terms of the achievable secrecy rate and intercept probability is presented; the asymptotic intercept probabilities are also derived. The conventional relay selection schemes and their performance analysis are presented in Sect. 4. Simulation and numerical results are presented and discussed in Sect. 5. Section 6 gives the concluding remarks.
Throughout the paper, the following notations are used. For the set \({\mathcal{A}}\), \(|{\mathcal{A}}|\) denotes the cardinality of this set. [x]+ = max (0, x). Furthermore, \(\underset{\raise0.3em\hbox{$\smash{\scriptscriptstyle-}$}}{X}\) denotes a lower bound for X, and ≜ denotes equals by definition. Finally, we use \(x \sim {\mathcal{C}\mathcal{N}}(0,\sigma^{2} )\) to denote a circularly symmetric complex Gaussian random variable with zero-mean and varianceσ 2.
2 System and channel models
We consider a CRN model as shown in Fig. 1, where a single-antenna SU transmitter (SU-TX) sends confidential information to a legitimate SU receiver (SU-RX), in the presence of K single-antenna PUs, L eavesdroppers, and a set of N relay nodes. For notational convenience, N relays, L eavesdroppers, and K PUs are denoted by the sets \({\mathcal{R} } = \left\{ {R_{i} |i = 1,2, \ldots ,N} \right\}\), \({\mathcal{E} } = \left\{ {E_{j} |j = 1,2, \ldots ,L} \right\}\), and \({\mathcal{P} } = \left\{ {p_{k} |i = 1,2, \ldots ,K} \right\}\), respectively. We also define the decoding set \({\mathcal{D}}\), which contains the relay nodes that have decoded correctly the received message from the source in the first phase. A cognitive network with underlay spectrum sharing which allows concurrent transmission from the PU and the SU simultaneously in the same spectrum band is assumed. We assume that the source has no direct link with the destination and eavesdroppers, i.e., the direct links are in deep shadowing, and the communication is carried out through a reactive DF relays [20, 21]. Moreover, considering the direct link from the source to the destination and eavesdroppers is straightforward extension of this system model, but our main concern here is to investigate the effect of relay selection in enhancing the secrecy performance. In addition, we consider the CSI of the main, primary, and eavesdropper links are available; this is a common assumption in the literature of information-theoretic physical layer security [9, 20]. A slow, flat, block Rayleigh fading is assumed, where the channel remains static for one coherence interval (one slot) and changes independently in different coherence intervals with a variance σ 2 ij = d -α ij where d -α i,j is the Euclidean distance between the nodes i and j, and α is the path loss exponent. The fading coefficienth ij between the nodes i and j is distributed as circularly symmetric complex Gaussian random variable with zero-mean and a variance σ 2 ij .
Based on the DF protocol, there are two phases in the transmission from the SU-TX to the SU-RX. In the first phase, the source broadcasts its message to the trusted relays. The received signal at the ith relay is given by
where P s is the transmitted power at the SU-TX and \(h_{{sr_{i} }}\) is the fading coefficient of the channel from the source to the ith relay. xdenotes the transmitted symbol from the source and \(z_{{r_{i} }} \sim {\mathcal{C}\mathcal{N}}(0,N_{{r_{i} }} )\) represents the additive white Gaussian noise (AWGN) at the ith relay. The received signal at the kth PU in the first phase is given by
where \(h_{{sp_{k} }}\) represents the fading coefficient of the channel from the source to the kth PU and \(z_{{p_{k} }} \sim {\mathcal{C}\mathcal{N}}(0,N_{{p_{k} }} )\) represents AWGN. In order to protect the PU, the interference received at the PU shall be guaranteed not to exceed the maximum threshold limit denoted by I. Therefore, the transmitted power P s should be varied according to the source-primary channel as will be described later.
In the second phase, one of the trusted relays that successfully decoded the message in the first phase is selected to retransmit the signal to the destination. The transmitted signal is also overheard by the eavesdropper due to wireless broadcasting. Considering that the ith relay is selected, the received signals at the destination and eavesdroppers are given by
where \(P_{{r_{i} }}\) denotes the transmitted power of the selected relay. \(h_{{r_{i} d}}\) and \(h_{{r_{i} e_{j} }}\) are the fading coefficients of the channels from selected relay to the destination (the main channel), and from selected relay to the jth eavesdropper (the wiretap channel), respectively. \(z_{d} \sim {\mathcal{C}\mathcal{N}}(0,N_{d} )\) and \(z_{{e_{j} }} \sim {\mathcal{C}\mathcal{N}}(0,N_{{e_{j} }} )\) are AWGN at the destination and the jth eavesdroppers, respectively. The received signal at the kth PU is given by
where \(h_{{r_{i} p_{k} }}\) is the fading coefficient of the channel from the selected relay to the kth PU, and \(z_{{p_{k} }} \sim {\mathcal{C}\mathcal{N}}(0,N_{{p_{k} }} )\). It should be noted that in (1)–(5), both P s , and \(P_{{r_{i} }}\) should be adjusted in every transmitted block according to the channel condition between the SU and the PU.
3 The proposed relay selection schemes
In this section, we present the proposed relay selection schemes to improve the physical-layer security of CRNs and analyze their performance in terms of the achievable secrecy rate and intercept probability with single and multi-eavesdroppers. Furthermore, we analyze their performance considering the presence of one and multiple PUs.
3.1 Proposed relay selection scheme with single eavesdropper (SE)
In this case, we consider single eavesdropper and single PU. The objective of the proposed selection scheme is to select the relay node that maximizes the achievable secrecy rate and at the same time keep the received interference power at the PU below a threshold level I. Therefore, we propose to limit the transmitted power at the source node in accordance to this allowed interference threshold as follows
where P is the maximum power budget at the SU-TX and h sp is the fading coefficient from the source to the PU. Note that the transmitted power is a random variable but is limited by the maximum transmitted power P. Using (6), the received interference at the PU can be ensured not to exceed I. Without loss of generality, we assume that the maximum transmitted power at any relay node is P. Therefore, the transmitted power of the relay R i is given by
The instantaneous achievable secrecy rate when the ith relay is selected is defined as [20]
where, \(\gamma_{{r_{i} d}} \triangleq \frac{{P_{{r_{i} }} \left| {h_{{r_{i} d}} } \right|^{2} }}{{N_{d} }}\) and \(\gamma_{{r_{i} e}} \triangleq \frac{{P_{{r_{i} }} |h_{{r_{i} e}} |^{2} }}{{N_{e} }}\) represent the signal to noise ratios (SNRs) at the SU-RX and eavesdropper, respectively. The objective is to select a relay from the decoding set \({\mathcal{D}}\) that maximizes the secrecy rate given in (8) as follows
Hence, the achievable secrecy rate of the proposed scheme is given as
Finding closed form expression of the ergodic achievable secrecy rate for (10) requires solving high dimensional integrals, which is cumbersome. However, the ergodic achievable secrecy rate can be solved easily using computer simulation.
3.1.1 Asymptotic intercept probability analysis
We introduce the intercept probability as another performance metric for the proposed schemes. The intercept probability is defined as the probability that the secrecy rate is less than zero [10, 17]. In other words, the intercept event occurs when the wiretap link is better than that the main link (i.e. when the achievable secrecy rate becomes negative). Therefore, the intercept probability in this case is given as [20]
where C prop S,SE is the rate given in (10). For simplicity of analysis, we drive an asymptotic intercept probability under the assumption that all relay nodes decode the received signals correctly in the first phase.Footnote 1 As the transmit power is a random variable, we assume high source-relays channel variances to ensure correct decoding of all relays. In this case, all relays are assumed to decode the signal that is transmitted from SU-TX correctly so that \(\Pr \left\{ {|{\mathcal{D}}| = N} \right\} = 1\), and hence, the intercept probability in (11) becomes \(P_{{\text{int} ,SE}}^{prop} = \Pr \{ C_{S,SE}^{prop} < 0\}\). Considering (9) and (10) and assuming that N d = N e , the asymptotic intercept probability of the proposed scheme for one realization of the rate C S,SE (R i ) given in (8), which correspond to the ith relay is given as
Note that the intercept probability does not depend on the transmitted power. Define \(X_{1} \triangleq |h_{{r_{i} d}} |^{2}\), and \(X_{2} \triangleq |h_{{r_{i} e}} |^{2}\). Note that both X 1and X 2 are independent exponentially distributed random variables, with means \(\sigma_{{r_{i} d}}^{2}\), and \(\sigma_{{r_{i} e}}^{2}\), respectively. Therefore, (12) is given as
Using the order statistics [22], for the N independent realizations of the random variables C S,SE (R i ), i = 1, 2, …, N, the asymptotic intercept probability is given as
3.2 Proposed relay selection with multiple eavesdroppers (ME)
In this case, we consider L eavesdroppers that try to decode the information intended for the SU independently, without cooperation between them. The worst case, which represents choosing the eavesdropper that can achieve the maximum rate, is considered. Therefore, the overall rate of the wiretap links is the maximum of individual rates achieved at Leavesdroppers. Hence, the instantaneous achievable secrecy rate when selecting the relay R i is given as
where \(\gamma_{{r_{i} e_{j} }}\) is the SNR at the jth eavesdropper. The objective is to select the relay that maximizes the rate given in (15) as follows
Hence, the achievable secrecy rate of the proposed scheme with multiple eavesdroppers is given by
The achievable ergodic secrecy rate of (17) can be obtained through computer simulations.
3.2.1 Asymptotic intercept probability analysis
We drive an asymptotic intercept probability when multiple eavesdroppers try to decode the message. Following similar assumptions in the previous subsection, the intercept probability of the rate given in (15) is given by
The random variable \(|h_{{r_{i} d}} |^{2}\) is exponential distributed with mean \(\sigma_{{r_{i} d}}^{2}\) . Define \(X \triangleq \mathop {\hbox{max} }\limits_{{E_{j} \in {\mathcal{E}}}} |h_{{r_{i} e_{j} }} |^{2}\); the cumulative distribution function (CDF) and the probability density function (PDF) of the random variable X, considering order statistics, are given as
So, the intercept probability in (18) is calculated by averaging the CDF of \(|h_{{r_{i} d}} |^{2}\) over the PDF of X, given in (20), as follows
The product term in (21) can be expanded using the binomial theorem as
where, \({\mathcal{E}}_{k}\) is the kth nonempty subset of L eavesdroppers, excluding the subset when k = j, and \(\left| {{\mathcal{E}}_{k} } \right|\) represents the cardinality of set \({\mathcal{E}}_{k}\). Substituting (22) into (21) and performing the integration by changing the order of summations and integration, it can easily be shown that
The intercept probability of the rate given in (17) can be obtained using the order of statistics as
Note that for L = 1, (24) reduces to (14) for the case of single eavesdropper.
3.3 Proposed relay selection with multiple primary users (MP)
In this case, K PUs and one eavesdropper are considered. The objective is to investigate the effect of the presence of multiple PUs on the achievable secrecy rate and the intercept probability. Presence of multiple PUs will certainly add more constraints on the transmitted power at the SU-TX and the selected relay. Therefore, in order to limit the transmitted power at SU-TX in accordance to the allowed interference threshold I at each PU, the transmitted power at SU-X, and the ith selected relay will be
respectively. The instantaneous achievable secrecy rate with the relay R i is given as
where \(\gamma_{{r_{i} d}} = \frac{{P_{{r_{i} ,MP}} |h_{{r_{i} d}} |^{2} }}{{N_{d} }}\), and \(\gamma_{{r_{i} e}} = \frac{{P_{{r_{i} ,MP}} |h_{{r_{i} e}} |^{2} }}{{N_{e} }}\) represent the SNRs at the destination and eavesdropper, respectively. The objective is to select the relay that maximizes the rate given in (27) as follows
Hence, the achievable secrecy rate of the proposed scheme with multiple PUs is given as
3.3.1 Asymptotic intercept probability analysis
We derive an asymptotic approximation of the intercept probability when multiple PUs are considered. The PUs are protected from the interference through limiting the transmitted power at the SU-TX and relays as in (25) and (26). Considering the same assumptions mentioned before, the intercept probability of one realization of the achievable secrecy rate corresponding to the ith relay is given by
which is the same as (12). So, the intercept probability of the multiple PUs case is given as
Interestingly, the asymptotic intercept probabilities of the proposed scheme with single and multi PUs are the same. This can be interpreted as follows. In our system model, the performance enhancement is due to the selection process. In the asymptotic case, all relays decode the received signals correctly and hence belong to the decoding set, and the performance start to saturates either for the secrecy rate or the intercept probability as will be shown in Sect. 5. Therefore, the presence of multiple PUs will only limit the transmitted power. As the asymptotic intercept probability does not depend on the transmitted power, its performance with single and multiple PUs is the same. This will also be confirmed in Sect. 5 via simulations.
4 The conventional relay selection schemes
In this section, for the comparison purpose, we analyze the performance of the conventional relay selection schemes. However, we drive new closed-form expressions for the asymptotic intercept probability of these schemes.
4.1 Conventional selection (CS1) with single eavesdropper (SE)
In this scheme, the objective is to select the relay R i that maximizes the achievable rate of the main link without considering the existence of the eavesdropper as follows
In this case, the achievable secrecy rate of this scheme, which is denoted as CS1, is given as
As before, we assume that N d = N e . Also, all relays are assumed to decode the signal that is transmitted from source correctly so that \(\Pr \left\{ {|{\mathcal{D}}| = n} \right\} = 1\). Therefore, the asymptotic intercept probability is given by
A closed form solution for the intercept probability in (34) is difficult. Therefore, a numerical intercept probability is done through computer simulation. However, a lower bound on the intercept probability can be obtained by performing the maximization in the left-hand side of the inequality in (34) only over the random variables \(|h_{{r_{i} d}} |^{2}\),i = 1, 2, …, N. In this way, we obtain a lower bound on the asymptotic intercept probability as follows
Using the binomial expansion theorem, the product term in (35) is expressed as
where \({\mathcal{R}}_{n}\) is the nth non-empty subset of N relays. Substituting (36) into (35) and performing the integration yield
4.2 Conventional selection (CS1) with multi eavesdroppers (ME)
With multiple eavesdroppers, the conventional scheme selects the relay that maximize the SNR at SU-RX regardless of the presence of the eavesdroppers as in (32). Regarding the wiretap link, the eavesdropper that achieves the maximum rate is considered. As a result, the achievable secrecy rate is given as
Note that the maximization over the SNRs of the wiretap links in (38) is reduced to the maximization over the channel coefficients \(|h_{{r_{i} e_{j} }} |^{2} ,\,j = 1,2, \ldots ,L\), because a relay is already selected to maximize the main link and the maximization here is over the eavesdroppers that achieve the maximum rate from the selected relay. As in the case of single eavesdropper, a lower bound on the asymptotic intercept probability in this case can be obtained as
Define \(X \triangleq \mathop {\hbox{max} }\limits_{{E_{j} \in {\mathcal{E}}}} |h_{{r_{i} e_{j} }} |^{2}\), and \(Y \triangleq \mathop {\hbox{max} }\limits_{{R_{i} \in {\mathcal{D}}}} |h_{{r_{i} d}} |^{2}\); The CDF and PDF of both the random variables X and Y are given in (19), and (20), respectively. Therefore, the lower bound of the asymptotic intercept probability given in (39) is calculated as
Substituting the binomial expansions, given in (22) and (36), instead of the product terms in (40), and changing the orders of integrations and summations, it can be shown that
4.3 Conventional selection scheme (CS1) with multi primary users(MP)
In this case, we consider K PUs and one eavesdropper. The transmitted power at SU-TX and the ith relay are given in (25) and (26). Hence, the achievable secrecy rate in this case is given as
Following the same assumptions as in the previous subsections, the asymptotic intercept probability in this case is given by
A closed form solution for the intercept probability in (43) is cumbersome. However, a lower bound on the intercept probability can be obtained by maximizing over the relay-eavesdroppers channels, i. e, \(\mathop {\hbox{max} }\limits_{{R_{i} \in {\mathcal{D}}}} |h_{{r_{i} d}} |^{2}\), as
which is reduced to the problem in (35) with the case of single PU. So, the asymptotic intercept probability is given by
4.4 The selection scheme proposed in [18]
For the comparison purpose, we briefly introduce the selection scheme proposed in [18] which we denote as Scheme2. The achievable secrecy rate of this scheme with single eavesdropper and single PU is given as
where, INT is the interference received at the PU and expressed as \(INT = N_{p} + P|h_{sp} |^{2} + P|h_{{r_{i} p}} |^{2}\). Note that this scheme transmits with the maximum power P that is available at the SU-TX and the relay. The relay is selected subject to the constraint INT ≤ I; in the proposed scheme, a relay is always selected and the transmitted power is controlled according to the channel characteristics to the PU so that the interference received at the PU is always less than I. When L eavesdroppers is considered, the selection criteria (46) is used after replacing \(|h_{{r_{i} e}} |^{2}\) with \(\mathop {\hbox{max} }\limits_{{E_{j} \in {\mathcal{E}}}} |h_{{r_{i} e_{j} }} |^{2}\). In the case of multiple PUs and one eavesdropper, the selection criteria for this scheme is given as in (46) but with the constraint \(\mathop {\hbox{max} }\limits_{{p_{k} \in {\mathcal{P}}}} INT_{{p_{k} }} \le I\); where \(INT_{{p_{k} }} = N_{{p_{k} }} + P|h_{{sp_{k} }} |^{2} + P|h_{{r_{i} p_{k} }} |^{2}\). The intercept probability for this scheme is defined as [18]
where \(\tilde{C}_{S,SE}^{Scheme2}\) is the rate given in (46) without enforcing the rate to be more or equal to zero. When multiple eavesdroppers or multiple PUs are considered, (47) is modified according to the constrains discussed above.
5 Simulation results
In this section, we investigate the effectiveness of the proposed relay selection schemes via computer simulations that also validate the analytical results. We follow the system model shown in Fig. 1, and perform Monte Carlo simulation consisting of 40,000 independent trials to obtain the average result. The system parameters are as follows:
The SU-TX, N = 4relays, SU-RX, and L = {1, 2} eavesdroppers are deployed in a two-dimensional unit-square area. The locations of SU-TX, and SU-RX are {X, Y} = {0, 0.5} and {1, 0.5}, respectively. The locations of the eavesdroppers are {1, 0} in case of single eavesdropper, and {1, 0}, {1, 1} in case of two eavesdroppers. The relays are located at {0.5, 0.2}, {0.5, 0.4}, {0.5, 0.6}, {0.5, 0.8}. Moreover, the PU is located at {1, 3} in case of single PU. In the case of two PUs, i.e. K = 2, we distinguish between two cases: (1) the second PU is farther than the first, located at {1, 4} and (2) the second PU is closer than the first, located at {1, 2}.
The total interference temperature limit \(I = - 3\,{\text{dB}}\). The path loss exponent α = 3. The transmission rate R 0 = 2bits/s/Hz, which represent the transmission rate of the SU-TX. A relay \(R_{i} \in {\mathcal{D}}\) if its channel capacity with the SU-TX is larger than R 0. In all simulations, the maximum transmitted power at each relay is set at 10 dB.
Figure 2 shows the achievable ergodic secrecy rate versus the transmitted power budget Pat the SU-TX for the proposed scheme, the conventional scheme CS1, the scheme proposed in [18] which we denote as Scheme2, and the conventional scheme CS2, which also presented in [18] for the comparison purpose with Scheme2. It can be seen from the figure that the proposed scheme gives the best performance over the range of P. The case of multi-eavesdroppers is also shown on the figure. The achievable ergodic secrecy rate of the proposed scheme and CS1 scheme gradually increases with P before it saturates. Saturation occurs at high Pdue to one of the following reasoning: (1) at high transmitted power, all the relays may decode the signal correctly and more power will not further enhance the performance. (2) As the actual transmitted power are given in (6), (7), small values of the interference threshold I will restrict he transmitted power by the average value of the random variable I/|h sp |2 and the achievable rate saturate, although some of the relays do not belong to the decoding set. Note that with Scheme2, which transmit at the maximum power, the achievable ergodic secrecy rate starts to increase with Pbut further increase in the transmitted power will affect the selection process because the interference power at the PU increases. Therefore, the secrecy rate starts to decrease until it reaches zero at \(P = 30\,{\text{dB}}\). We also note that with L = 2, the achievable ergodic secrecy rate is degraded compared with one eavesdropper.
Figure 3 shows the intercept probability for the different schemes versus P. As shown, the proposed scheme gives the minimum intercept probability over all values of P. For Scheme2 and CS2, the intercept probability starts to decrease at low transmit power; however, further power increase will affect the selection process due to high interference at the PU. Therefore, the intercept probability starts to increase until it reaches 1 at \(P = 30\,{\text{dB}}\).
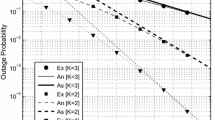
In order to investigate the asymptotic secrecy performance, where all the relays decodes the signal correctly, we plot the intercept probability against source-relays variances in Fig. 4 with \(P = 10\,{\text{dB}}\). The exact expressions of the asymptotic intercept probabilities for the different schemes are also shown in the figure . It can be seen that the analytical results matches well the simulation results. Note that the performance of Scheme2 and CS2 saturates at high source-relays channel variances with fixed transmit power, but at lower values compared to the proposed schemes.
Figure 5 shows the effect of the presence of two PUs located at {1, 3}, and {1, 4} on the achievable secrecy rate. The dotted lines represent the case of one PU located at {1, 3}. In this case, where the second PU is father than the first one, we note that the secrecy rate with one PU is slightly smaller than the case of two PUs. This is because the power that causes the maximum allowed interference at the PUs is given according to (25) and (26). As the first PU is nearer to the SU-TX and the selected relay, it is more likely to be the dominant factor in selecting the transmitted power. In Fig. 6, the second PU is located at {1, 2}, closer to the SU-TX and the selected relay than the first PU located at {1, 3}. The achievable secrecy rate is lower than that with one PU as shown on the figure. The minimum transmitted power is selected to protect both PUs from interference and because the second is located closer than the first, It will be dominant PU and therefore, the secrecy rate decreases.
Finally, we plot the intercept probability for the different schemes versus the source-relays variances in cases of one and two PUs as shown in Fig. 7. The two PUs are located at {1, 3}, {1, 2} and the transmitted power is set at \(P = 10\,\,{\text{dB}}\). It can be seen that at high source-relays variances, meaning that the SU-TX is very close to the relays and hence all relays are assumed to belong to the decoding set, the intercept probability with one and two PUs are the same. This confirms the analytical results derived in Sect. 3, which also shown on the figure.
6 Conclusions
In this paper, we have studied the physical layer security in cooperative CRNs. We have proposed relay selection schemes to improve the physical layer security in CRNs against the presence of multiple eavesdroppers, and at the same time taking into account the QoS constraints of the PUs in the network. The DF relaying is used, where a relay is selected from the decoding set to help the source transmission and also maximize the secrecy rate. Two performance metrics are considered; namely, achievable ergodic secrecy rate and intercept probability. We have shown that the proposed selection schemes outperform the conventional and other schemes proposed in the literature over all the range of the transmitted power in terms of both the achievable ergodic secrecy rate and the intercept probability. Also, it has be shown that presence of multiple eavesdroppers or PUs in the network degrade both the achievable secrecy rate and the intercept probability. However, in the asymptotic case, the intercept probability with multiple PUs is the same as that with single PU. Furthermore, we have derived closed form expressions of the asymptotic intercept probability of the proposed schemes, and tight lower bounds for the asymptotic intercept probability of the conventional schemes.
Notes
It should be noted that in [9] and [10] all relays are assumed to decode correctly , and the derived expressions of the intercept probability are considered exact . Our case is more general as we consider \(|{\mathcal{D}}| = N\) an asymptotic case. So, the derived expressions are considered asymptotic according to this assumption.
References
Akyildiz, I. F., Lee, W. Y., Vuran, M. C., & Mohanty, S. (2006). Next generation/dynamic spectrum access/cognitive radio wireless networks: A survey. Computer Networks, 50(13), 2127–2159.
Biglieri, E., Goldsmith, A. J., Greenstein, L. J., Mandayam, N. B., & Poor, H. V. (2013) Principles of cognitive radio. Cambridge: Cambridge University Press.
Shannon, C. E. (1949). Communication theory of secrecy systems. Bell System Technical Journal, 28(4), 656–715.
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54(8), 1355–1387.
Barros, J., & Rodrigues, M. R. D. (2006, July). Secrecy capacity of wireless channels. In Proceedings of IEEE international symposium information theory (pp. 356–360).
Li, Z., Trappe, W., & Yates, R. (2007, March). Secret communication via multi-antenna transmission. In Proceedings of 41st conference on information sciences systems, Baltimore, MD.
Khisti, A., Womell, G., Wiesel, A., & Eldar, Y. (2007, June). On the Gaussian MIMO wiretap channel. In Proceedings of IEEE international symposium on information theory, Nice, France.
Oggier, F., & Hassibi, B. (2007). The secrecy capacity of the MIMO wiretap channel. IEEE Transactions on Information Theory, 57(8), 4961–4972.
Zou, Y., Wang, X., & Shen, W. (2013). Optimal relay selection for physical layer security in cooperative wireless networks. IEEE Journal on Selected Areas in Communications, 31(10), 2099–2111.
Zou, Y., Wang, X., & Shen, W. (2013, June). Intercept probability analysis of cooperative wireless networks with best relay selection in the presence of eavesdropping attack. In Proceedings of IEEE international conference on communicaitons (ICC 2013) (pp. 1–5).
Al-nahari, A., Krikidis, I., Ibrahim, A. S., Dessouky, M. I., & El-Samie, F. A. (2012). Relaying techniques for enhancing the physical layer secrecy in cooperative networks with multiple eavesdroppers. Transactions on Emerging Telecommunications Technologies (ETT), 25(4), 445–460.
Shu, Z., Qian, Y., & Ci, S. (2013). On physical layer security for cognitive radio networks. IEEE Networks, 27(3), 28–32.
Leon, O., Serrano, J. H., & Soriano, M. (2010). Securing cognitive radio networks. International Journal of Communications Systems, 23(5), 633–652.
El-Hajj, W., Safa, H., & Guizani, M. (2011). Survey of security issues in cognitive radio networks. Journal of Internet Technology, 12(2), 25–37.
Anand, S., & Chandramouli, R. (2008, May). On the secrecy capacity of fading cognitive wireless networks. In Proceedings IEEE CrownCom.
Pei, Y., Liang, Y., Zhang, L., Teh, K. C., & Li, K. H. (2010). Secure communication over MISO cognitive radio channels. IEEE Transactions on Wireless Communications, 9(4), 1494–1592.
Zou, Y., Wang, X., & Shen, W. (2013). Physical layer security with multiuser scheduling in cognitive radio networks. In IEEE Transactions on Communications, 61(12), 5103–5113.
Sakran, H., Nasr, O., Shokair, M., El-Rabaie, E., & El-Azm, A. (2012). Proposed relay selection scheme for physical layer security in cognitive radio networks. IET Communications, 6(16), 2676–2687.
Al-Jamali, M., Al-nahari, A., & Al-Khawlani, M. (2015). Relay selection scheme for improving the physical layer security in cognitive radio networks. In Proceedings of 23rd IEEE signal processing and communications applications, Malatya, 16–19 May 2015.
Krikidis, I. (2010). Opportunistic relay selection for cooperative networks with secrecy constraints. IET Communications, 4(15), 1787–1791.
Zou, Y., Wang, X., & Shen, W. (2013). Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE Journal on Selected Areas in Communications, 31(10), 1787–1791.
Miller, S., & Childers, D. (2004). Probability and random processes with applications to signal processing and communications. San Diego: Elsevier Academic Press.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Al-jamali, M., Al-nahari, A. & AlKhawlani, M. Relay selection schemes for secure transmission in cognitive radio networks. Wireless Netw 24, 911–923 (2018). https://doi.org/10.1007/s11276-016-1378-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-016-1378-9