Abstract
Telecare medicine information system (TMIS) has provided an efficient and convenient way for communications of patients at home and medical staffs at clinical centers. To make these communications secure, user authentication by medical servers is considered as a crucial requirement. For this purpose, many user authentication and key agreement protocols have been put forwrad in order to fulfil this vital necessity. Recently, Arshad and Rasoolzadegan have revealed that not only the authentication and key agreement protocols suggested by Amin and Biswas and Giri et al. are defenseless against the replay attack and do not support the perfect forward secrecy, but also Amin and Biswas’s protocol is susceptible to the offline password guessing attack. Nonetheless, in this paper, we demonstrate that Arshad and Rasoolzadegan’s and the other existing schemes still fail to resist a well-known attack. Therefore, to cover this security gap, a new user authentication and session key agreement protocol is recommended that can be employed effectively for offering secure communication channels in TMIS. Our comparative security and performance analyses reveal that the proposed scheme can both solve the existing security drawback and, same as Arshad and Rasoolzadegan’s scheme, has low communication and computational overheads.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
The digital revolution has provided many opportunities in various fields and it has promoted the information technology. New devices, technologies, and manners of sharing information promise an easier and better life [1]. Amongst the recent technological advances, telecare medicine information system (TMISs) is considered as one the most well-known achievements [2]. The classic doctor-patient relationship model can be transformed into a new model with the assistance of electronic devices and Internet, as a channel for sharing information [3].
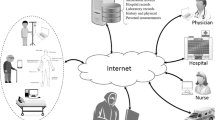
As illustrated in Fig. 1, the structure of the TMIS consists of four main parts: the patient, the doctor, the database, and the Internet. To be able to remotely access healthcare services through the Internet, a user must first register with the medical server. After the completion of the registration process, a smart card is issued for the user by the server for future communications. The usage of the smart card is mainly to verify the legitimacy of the patient and send login messages to the server over an insecure network. At the end, the user and server mutually authenticate each other and agree upon a session key [4]. Following, using the generated session key, secure gathering of patient information is done by means of sensor nodes, smartwatches, fitness bands, or even by measuring medical signs like heart rate or blood pressure and manually inputting the data into a smartphone or personal computer. The patient can also ask questions from the doctor. The collected information and/or questions are sent to the doctor through the Internet. The process of exchanging information between patients and doctors, which is mediated by electronic devices, leads to less face to face sessions and saves the patients’ time, effort, cost, and hassle of traversing to see the doctor for any small status report or simple question. With the help of the TMISs, a doctor can constantly review his/her patient’s vital signs and answer asked questions appropriately [5]. Occasionally, it is difficult for doctors to make a decision for a patient due to lack of sufficient knowledge of the patient’s past and health records. By the employment of the TMISs, the recorded information are stored in a database. Having the patient’s health records stored on a database, which can be accessed anywhere and at any time, doctors can make the best decision for the patient at any given time [6, 7].
Since the TMISs operate through the Internet and the Internet has an open architecture, a patient will not be willing to work with a medical center that cannot fulfil the security and privacy concerns. Furthermore, in a TMIS, confidential information of patients are stored in the database. Thus, security flaws in a TMIS can disclose the patients’ privacy and may have dire consequences [8, 9]. Finally yet significantly, feeding inaccurate data into a TMIS database could make the stored information valueless or even misleading and will cause misjudgements. Therefore, to protect the security and privacy of patients and prevent any illegal database access or manipulation, numerous security protocols, such as authentication and access control protocols, have been proposed for the TMISs [10,11,12,13,14]. In order to confirm patients’ authenticity and safeguarding the exchange of medical data, remote user authentication is highly contributed [15]. This process happens with the assistance of some authentication tokens like passwords, smart cards, or biometrics.
Recently, Arshad and Rasoolzadegan [16] have assessed the security of Giri et al.’s scheme [17] and found that their protocol cannot resist the replay attack and does not provide the perfect forward secrecy. Likewise, Arshad and Rasoolzadegan [16] have pointed out that the proposed protocol by Amin and Biswas [18] is insecure against the offline password guessing attack, replay attack, and does not support the perfect forward secrecy. As a result, Arshad and Rasoolzadegan [16] have introduced an enhanced authentication protocol for the TMISs and claimed that their new protocol can withstand the well-known attacks. Nevertheless, in this paper, we will indicate that the proposed protocol by Arshad and Rasoolzadegan [16] and also the presented ones by Giri et al. [17] and Amin and Biswas [18] are all vulnerable to key compromise impersonation attack. Hence, to cover this security challenge, this paper presents a novel elliptic curve cryptosystem (ECC) based user authentication and key agreement protocol for TMISs that has an acceptable level of performance.
Threat model
The widely-accepted and well-known Canetti and Krawczyk (CK) threat model [19] has been adopted in this article. In this model, the adversary can both control the communications by listening to, changing, deciding on, and injecting into the transferring information and can gain private information saved in the memory of parties via some explicit attacks. As a result, the security of the proposed protocol should guarantee that the leakage of secret values, like long-term or session ephemeral secrets, would have the least possible effect on the security of other sessions and other private credentials of participants.
Contribution
The main contributions of this paper are as follows.
-
(1)
This paper indicates that the proposed protocols by Giri et al. [17], Amin and Biswas [18], and Arshad and Rasoolzadegan [16] are all vulnerable to the key compromise impersonation attack.
-
(2)
This paper introduces a novel user authentication protocol that, in comparison to the related protocols, is the best in terms of security metrics.
-
(3)
The proposed protocol is simulated by the employment of the widely-accepted automated validation of internet security protocols and applications (AVISPA) simulator tool in order to demonstrate that it is safe.
-
(4)
This paper presents a comprehensive comparative study with 15 related protocols.
Organization of this article
The rest of this article is arranged as the following sections. In Section 2, we review the related authentication and key agreement protocols. We present the security analysis of three related works in Section 3. In Section 4, the proposed scheme is explained in details. The formal security verification of the proposed scheme with the AVISPA tool is discussed in Section 5 and informal discussion on security is presented in Section 6. The performance comparison of the suggested protocol with the other related schemes is given in Section 7. Finally, we conclude the paper in Section 8.
Literature review
Since the beginning of this millennium, a great number of authentication and key agreement protocols have been presented, among which many are verified to be insecure against many security attacks. Table 1 shows the limitations of the related works.
In 2000, Hwang and Li [20] suggested a remote user authentication protocol that does not require to maintain a password file or a verification table for users. Nevertheless, Sun [21] stated that the protocol of Hwang and Li [20] is not practical and efficient in terms of computation and communication costs. Accordingly, they presented an efficient and practical remote user authentication protocol by applying smart cards. This is because the password used in [21] is 64 bits while in the protocol of Hwang and Li [20], it is 1024 bits. Therefore, it is very hard for users to recall the password.
Following, many authentication protocols have been proposed to be employed in the context of the TMIS. In 2013, Tan [22] suggested an efficient biometric-based authentication protocol for TMISs and indicated that his proposed protocol is resistant to the well-known attacks and can accomplishe stronger level of security.
In 2014, Arshad and Nikooghadam [23] reviewed Tan’s authentication and key agreement protocol [24] and found that his protocol is vulnerable to the denial of service (DoS) and replay attacks. In order to solve these security weaknesses, an efficient privacy-preserving three-factor authentication and session key agreement proposed for TMISs by Arshad and Nikooghadam [23] . In addition, Das and Goswami [25] indicated that Awasthi and Srivastava’s protocol [26] is exposed to strong replay attack and cannot provide user anonymity. Hence, Das and Goswami [25] introduced a secure and improved biometric-based remote user authentication protocol, which supports user anonymity property and obtains additional vigorous features for an idle user authentication protocol in TMISs. Mishra et al. [27] introduced a biometric-based authentication protocol for TMISs, which has an efficient login and password change phases.
In 2015, Giri et al. [17] showed that Khan and Kumari’s protocol [28] is vulnerable to the offline password guessing attack. Afterwards, they presented an efficient and robust RSA-based remote user authentication and key agreement protocol for the TMISs. Amin and Biswas [18] analyzed Giri et al.’s protocol [17] and revealed that their protocol cannot withstand the privileged insider attack, offline password guessing attack, and cannot preserve anonymity. In order to fix these challenges, Amin and Biswas [18] suggested an improved RSA-based user authentication and key agreement protocol for TMISs. Chaudhry et al. [29] studied Islam and Khan’s protocol [30] and demonstrated that their protocol is not secure against the server and user impersonation attacks. To overcome these limitations, Chaudhry et al. [29] recommended an improved two-factor authentication protocol for TMISs. Arshad et al. [31] assessed Bin Muhaya’s protocol [32] and demonstrated that the protocol cannot withstand the offline password guessing attack and does not provide perfect forward secrecy. Moreover, an ECC-based authentication protocol for TMISs with anonymity preservation introduced by Arshad et al. [31]. Amin and Biswas [33] studied the security of both Xu et al.’s [34] and Mishra et al.’s [27] protocols and showed the security challenges of them. In order to fix the both protocols, Amin and Biswas [33] presented a secure three-factor authentication and key agreement protocol, which can offer the user anonymity in TMISs. Yet another ECC-based scheme is presented in [35], where careful assessment of their work reveals that in their scheme there exists no key confirmation and it cannot guarantee the message integrity.
In 2016, Chaudhry et al. [15] evaluated the security of the authentication scheme suggested by Amin et al. [36] and claimed that their scheme cannot withstand the stolen smart card and stolen verifier attacks, and has inefficient password recovery and password change phases. Therefore, Chaudhry et al. [15] proposed an enhanced biometric-based authentication scheme for TMIS using ECC. Arshad and Rasoolzadegan [16] analyzed the security of both Amin and Biswas [18] and Giri et al. [17] protocols. They showed that Amin and Biswas’s protocol [18] is exposed to the offline password guessing attack, replay attack, and does not provide perfect forward secrecy, while Giri et al.’s protocol [17] is vulnerable to the replay attack and lacks perfect forward secrecy. In order to solve the both protocols, Arshad and Rasoolzadegan [16] designed a privacy-preserving authentication and key agreement protocol to be employed in TMISs. Nonetheless, as we will show in the next section, not only Giri et al.’s [17] and Amin and Biswas’s [18] protocols, but also Arshad and Rasoolzadegan’s protocol [16] are susceptible to the key compromise impersonation attack.
In 2017, Zhang et al. [37] analysed the protocol of Mishra et al. [27] and proved that the protocol is susceptible to the offline identity guessing attack, replay attack, and man-in-the-middle attack, and does not support perfect forward secrecy. In order to cover these limitations, Zhang et al. [37] suggested a chaotic map-based three factor authenticated key agreement protocol for the TMISs. Jiang et al. [38] reviewed the improved three-factor authentication protocol proposed by Lu et al. [39] and found that the protocol is prone to the offline identity guessing, tracking, offline password guessing, user impersonation, server impersonation, and identity revelation attacks. Therefore, Jiang et al. [38] recommended an enhanced three-factor authentication protocol for the TMISs.
In 2018, Qiu et al. [40] studied Chaudhry et al.’s protocol [29] and showed that it is susceptible to the man-in-the-middle, user impersonation, server impersonation, and offline password guessing attacks. In order to eliminate these problems, Qiu et al. [40] presented a robust mutual authentication protocol based on ECC for TMISs, capable of reducing computational cost than the previous protocols. Li et al. [41] analysed a newly improved authentication protocol by Mohit et al. [42] and indicated that it is prone to the privileged insider attack.
Review and cryptonalysis of three related works
Brief review of Giri et al.’s protocol
In this section, we review and analyse Giri et al.’s protocol [17], which includes the following phases: initialization phase, registration phase, and login and authentication phase. The explanation of Giri et al.’s protocol [17] is given below.
Initialization phase
The server selects two large primes p and q, and calculates n = p × q, then, it keeps p and q as private parameters and publishes n as a public parameter. Next, it chooses two integers e and d, where e × d mod (p − 1) (q − 1) = 1, then, it considers d as the secret key and publishes e as the public key.
Registration phase
As shown in Fig. 2, a new user executes the following procedure to register with the server.
-
Step 1.
User → Server: {IDi, PWbi}
The user selects an identity IDi, a password PWi, and a random number bi. Then, he/she calculates PWbi = h(PWi || bi) and sends {IDi, PWbi} to the server via a secure channel.
-
Step 2.
Server → User: {IDi, Ai, Bi, Li, h(·)}
After receiving the request message {IDi, PWbi}, the server calculates Ri = h(IDi || d), Bi = (PWbi || Ri) e mod n, Ai = Ri ⊕ PWbi, and Li = h(Ri || PWbi). The server saves {IDi, Ai, Bi, Li, h(·)} in a smart card and sends it to the user via a secure channel.
-
Step 3.
User → Smart card: {IDi, Ai, Bi, Li, bi, h(·)}
Finally, the user saves random number bi into the memory of the smart card.
Login and authentication phase
In order for any registered user to access the information of server, this phase must be implemented through an insecure channel. The details are as the following steps and illustrated in Fig. 3.
-
Step 1.
User → Server: {IDi, Ci, Bi, Di}
The user inserts his/her smart card into the card reader and inputs his/her IDi* and PWi*. The smart card calculates PWbi* = h(PWi* || bi), Ri* = Ai ⊕ PWbi*, and Li* = h(Ri* || PWbi*). Then, the smart card validates whether the condition Li* = Li holds or not. If not, the smart card terminates the login phase; otherwise, the smart card chooses a random number N1 and calculates Ci = h(PWbi || N1 || Ri) and Di = PWbi ⊕ N1. At last, the smart card sends {IDi, Ci, Bi, Di} to the server through an insecure channel.
-
Step 2.
Server → User: {N3, Ki}
Upon receiving the message {IDi, Ci, Bi, Di}, the server checks whether the received IDi is valid or not. If it does not valid, the server terminates the session; otherwise, the server calculates Ri* = h(IDi* || d) and (Bi)d mod n = (PWbi* || Ri∗) and compares Ri∗ with Ri. If they are not equal, the server rejects the session; otherwise, the server calculates N1∗ = PWbi∗ ⊕ Di* and Ci* = h(PWbi∗ || N1∗ || Ri). Then, the server verifies whether the condition Ci* = Ci holds or not. If not, the server aborts this session; else, authenticates the user and chooses a random number N2. Afterwards, the server calculates N3 = N1∗ ⊕ N2 and Ki = h(Ri || N2). Ultimately, the server calculates the session key as SK = h(IDi || PWbi∗ || N1∗ || N2) and sends {N3, Ki} to the user through an insecure channel.
-
Step 3.
User gain session key
After receiving the message {N3, Ki}, the user calculates N2* = N3* ⊕ N1 and Ki* = h(Ri || N2∗). If Ki* ≠ Ki the smart card aborts the session; otherwise, the user authenticates the server and calculates the session key as SK = h (IDi || PWbi || N1 || N2). Doing so, both user and server agree upon a common session key.
The drawback of Giri et al.’s protocol
Recently, Arshad and Rasoolzadegan [16] pointed out that the protocol of Giri et al. [17] is vulnerable to the replay attack and does not provide the perfect forward secrecy. In the following subsection, we indicate that Giri et al.’s protocol [17] is also vulnerable to the key compromise impersonation attack. The details are as follows.
Key compromise impersonation attack
In order to withstand this attack, if the long-term secrets of server are disclosed, the adversary must not be able to impersonate the user and agree upon a common key with the server [43].
Assume the adversary eavesdrops the communication channel between the user and the server and achieves the values of {IDi, Ci, Bi, Di}. According to the assumption of key compromise impersonation attack, consider that the adversary has obtained the server’s private key, i.e., d. Then, he/she can impersonate a valid user and agree on the same session key with the server as follows.
-
Step 1.
Using the disclosed d, The adversary decrypts Bi and gains (PWbi ‖ Ri). Hence, the adversary gets PWbi.
-
Step 2.
Having IDi available on the insecure channel, the adversary computes Ri = h(IDi ‖ d).
-
Step 3.
As the public key of the server, e, is a common term, the adversary selects a random number N1 and computes Bi = (IDi || PWbi || N1)e mod n.
-
Step 4.
Afterwards, the adversary calculates Ci = h(PWbi || N1 || Ri) and Di = PWbi ⊕ N1. Then, he/she sends a valid request message {IDi, Ci, Bi, Di} to the server.
-
Step 5.
Upon receiving the message {IDi, Ci, Bi, Di}, the server checks Ri* = h(IDi* || d) and picks a random number N2. Then, the server calculates Ki = h(Ri || N2) and N3 = N1 ⊕ N2. Next, the server sends {N3, Ki} to the adversary.
-
Step 6.
Through the received N3, the adversary computes N2 = N1 ⊕ N3.
-
Step 7.
At the end, the adversary computes session key as SK = h(IDi || PWbi || N1 || N2).
As in Giri et al.’s protocol [17], the disclosure of the private key of the server allows the adversary to impersonate a legal user and agree on a session key, it can be deduced that, Giri et al.’s protocol [17] is vulnerable to the key compromise impersonation attack.
Review of Amin and Biswas’s protocol
In this subsection, we review Amin and Biswas’s authentication and key agreement protocol [18]. Amin and Biswas’s protocol [18] includes initialization phase, registration phase, and login and authentication phase. The initialization phase of Amin and Biswas’s protocol [18] is the same as Giri et al.’s protocol [17]. Therefore, we review only the registration and login and authentication phases.
Registration phase
As shown in Fig. 4, a new user executes the following steps to register with the server.
-
Step 1.
Step 1. User→ Server: {IDi, PWbi}
The user selects an identity IDi, a password PWi, and generates a random number bi. Next, the smart card calculates PWbi = h(PWi || bi) and sends {IDi, PWbi} to the server through a private channel.
-
Step 2.
Server → User: {Ai, Li, n, h(·)}
After receiving the request message {IDi, PWbi}, the server calculates Ri = h(IDi || d), Ai = Ri ⊕ h (PWbi || IDi), and Li = h (IDi ⊕ PWbi). Eventually, the server saves {Ai, Li, n, h(·)} into a smart card and sends it to the user through a private channel.
-
Step 3.
User → Smart card: {Ai, Li, DP, n, h(·)}
As soon as the user gets the smart card, he/she calculates DP = bi ⊕ h(IDi || PWi) and saves DP in the memory of the smart card.
Login and authentication phase
In order for any registered user to access the information of the server, this phase must be executed through an insecure channel. The details are as the following steps and illustrated in Fig. 5.
-
Step 1.
User → Server: {Ci, Bi, Di}
The user inserts his/her smart card into the card reader and inputs his/her IDi* and PWi*. The smart card calculates bi* = DP ⊕ h(IDi* || PWi*), PWbi* = h(PWi* || bi*), Li* = h(IDi* ⊕ PWbi*). Then, it verifies whether the condition Li* = Li holds or not. If not, the smart card aborts the session; otherwise, it generates a random number N1 and calculates Ri = Ai ⊕ h (PWbi || IDi), Ci = h(PWbi || N1 || Ri), Di = h(IDi || PWbi) ⊕ N1, and Bi = (IDi || PWbi || N1)e mod n. Finally, the smart card sends request message {Ci, Bi, Di} to the server through an insecure channel.
-
Step 2.
Server → User: {N3, Ki}
Based on the receiving request message {Ci, Bi, Di}, the server computes (Bi)d mod n = (IDi* || PWbi* || N1*) and N1* = h(IDi* || PWbi*) ⊕ Di*. Then, it validates whether the condition N1* = N1 holds or not. If not, the server rejects the session; else, it calculates Ri* = h(IDi* || d) and Ci* = h(PWbi* || N1 || Ri*). Next, the server validates whether the condition Ci* = Ci holds or not. If not, the server aborts the session; otherwise, it authenticates the user and generates a random number N2. Lastly, the server calculates N3 = N1 ⊕ N2 and Ki = h(Ri || N2), and sends response message {N3, Ki} to the user through an insecure channel.
-
Step 3.
User → Server: {SKV}
Upon receiving the response message, the smart card calculates N2* = N3* ⊕ N1, Ki* = h(Ri || N2*). Then, the smart card validates whether the condition Ki* = Ki holds or not. If not, the smart card terminates the session; else, it authenticates the server and calculates the session key as SK = h(IDi || PWbi || N1 || N2). Moreover, the smart card calculates SKV = h(SK || IDi) and sends {SKV} to the server through an insecure channel.
-
Step 4.
Server confirms session key
After receiving the message {SKV}, the server calculates the session key SK = h(IDi || PWbi || N1 || N2) and SKV* = h (SK || IDi). If SKV* ≠ SKV, the server rejects this connection; otherwise, it accepts the session key.
Weakness of Amin and Biswas’s protocol
Arshad and Rasoolzadegan [16] demonstrated that the protocol of Amin and Biswas [18] is susceptible to the offline password guessing and replay attacks and also does not support the perfect forward secrecy. In this section, we prove that the protocol of Amin and Biswas [18] also suffers from the key compromise impersonation attack. The details are as follows.
Key compromise impersonation attack
Assume an adversary eavesdrops the communication channel between the user and the server and reaches the values of {Ci, Bi, Di}. According to the assumption of the key compromise impersonation attack, consider that the adversary has access to the private key of the server, i.e., d, he/she can impersonate a legal user and agree on a same session key with the server as follows.
-
Step 1.
Using d, the adversary decrypts Bi and gains (IDi ‖ PWbi ‖ N1). Hence, the adversary finds IDi and PWbi.
-
Step 2.
The adversary obtains Ri as Ri = h(IDi ‖ d).
-
Step 3.
Since the public key of the server, e, is a common term, the adversary generates a random number N1 and computes Bi = (IDi || PWbi || N1)e mod n.
-
Step 4.
The adversary first calculates Ci = h(PWbi || N1 || Ri) and Di = h(IDi || PWbi) ⊕ N1. Then, he/she generates valid request message {Ci, Bi, Di} and submits it to the server.
-
Step 5.
When the server receives the message {Ci, Bi, Di}, it gets Ri* = h(IDi* || d) and chooses a random number N2. Then, the server calculates Ki = h(Ri || N2) and N3 = N1 ⊕ N2. Next, the server sends {N3, Ki} to the adversary.
-
Step 6.
Having the received N3, the adversary computes N2 = N1 ⊕ N3.
-
Step 7.
Eventually, the adversary calculates session key as SK = h(IDi || PWbi || N1 || N2).
As in Amin and Biswas’s protocol [18], the disclosure of the private key of the server can lead to the impersonation of legal users, we can conclude that their protocol cannot resist the key compromise impersonation attack.
Review of Arshad and Rasoolzadegan’s protocol
In this section, we review Arshad and Rasoolzadegan’s authentication and key agreement protocol [16], which includes initialization phase, registration phase, login and authentication phase, and password change phase. Since the password change phase of Arshad and Rasoolzadegan’s protocol [16] is not related to our cryptanalysis, we skip that.
Initialization phase
The server selects an elliptic curve E over a finite field Fp and chooses a base point P with a large order n. The server generates a random number s ∈ R Zp∗ as its private key and publishes {E, n, P} parameters.
Registration phase
As depicted in Fig. 6, a new user executes the following steps to register with the server.
-
Step 1.
User → Server: {IDi, PWbi}
The user selects his/her identity IDi, a password PWi, and a random number bi. The user calculates PWbi = h(PWi || bi) and sends {IDi, PWbi} to the server through a private channel.
-
Step 2.
Server → User: {Ai, CIDi, E, P, n, h(·)}
First of all, the server checks the existence of IDi in its database. If it exists, the server requests the user to selects another identity; otherwise, the server generates a random number r. Then, the server calculates Ri = h(IDi || s), Ai = Ri ⊕ h(IDi || PWbi), and CIDi = Es (IDi || r). Finally, the server saves IDi in its database and stores {Ai, CIDi, E, P, n, h(·)} into the memory of a smart card and sends it to the user via the private channel.
-
Step 3.
User → Smart card: {Ai, CIDi, bi, E, P, n, h(·)}
Upon receiving the smart card, the user saves the random number bi in the memory of the smart card.
Login and authentication phase
In order for any registered user to access the information of server, this phase must be executed through an insecure channel. The details are as the following steps and illustrated in Fig. 7.
-
Step 1.
User → Server: {CIDi, K1, V1, T1}
The user inserts his/her smart card into the card reader and inputs his/her identity IDi* and password PWi*. The smart card calculates PWbi* = h(PWi* ‖ bi) and Ri* = Ai ⊕ h(IDi* ‖ PWbi*). Then, the smart card validates whether the condition Ri* = Ri holds or not. If not, the smart card terminates the session; else, it chooses a random number k1 ∈ R Zp∗ and calculates K1 = k1P, Ri = Ai ⊕ h (IDi || h (PWi || bi)), and V1 = h(IDi || K1 || Ri || T1). Ultimately, the user sends request message {CIDi, K1, V1, T1} to the server through a secure channel.
-
Step 2.
Server → User: {K2, ECIDi, V2}
After getting the message {CIDi, K1, V1, T1}, first, the server checks the condition |T2 – T1| ≤ ∆T based on the current timestamp T2. Next, the server decrypts CIDi by its own private key as Ds (CIDi) = (IDi* || r*) and calculates V1* = h(IDi* || K1* || h (IDi* || s) || T1). The server validates whether the condition V1* = V1 holds or not. If not, the server rejects the session; otherwise, generates two random numbers rNew and k2 ∈ R Zp∗. Then, the server computes CIDiNew = Es (IDi || rNew), K2 = k2P, K = k2K1, ECIDi = h(K) ⊕ CIDiNew, and verifier V2 = h(K1 || h(IDi || s) || K2 || CIDiNew || K). Finally, the server sends response message {K2, ECIDi, V2} to the user through an insecure channel.
-
Step 3.
User → Server: {V3}
Upon getting the response message {K2, ECIDi, V2}, the user calculates K = k1K2, CIDiNew* = h(K) ⊕ ECIDi*, and V2* = h(K1 || Ri || K2* || CIDiNew* || K). Then, the user validates whether the condition V2* = V2 holds or not. If not, the smart card aborts the session; otherwise, he/she calculates V3 = h(Ri || V2 || K), replaces CIDi with CIDiNew in the memory of smart card, and sends {V3} to the server through an insecure channel. Furthermore, the user calculates the session key as SK = h (IDi || K || K1 || K2).
-
Step 4.
Server confirms session key
As soon as the server gets the message {V3}, it calculates V3* = h(h (IDi || s) || V2 || K). Then, it validates whether the condition V3* = V3 holds or not. If not, the server aborts the session; otherwise, it calculates the session key as SK = h(IDi || K || K1 || K2).
Weakness of Arshad and Rasoolzadegan’s protocol
Arshad and Rasoolzadegan [16] claimed that their protocol can withstand several security attacks. Nevertheless, in this section, we prove that their protocol is vulnerable to the key compromise impersonation attack. The details are as follows.
Key compromise impersonation attack
Assume an adversary eavesdrops the communication channel between the user and the server and reaches the values of {CIDi, K1, V1, T1}. According to the assumption of the key compromise impersonation attack, consider that the adversary has access to the private key of server, s, he/she can impersonate a legal user and agree on a same session key with the server as follows.
-
Step 1.
Having s, the adversary decrypts CIDi and obtains (IDi ‖ r).
-
Step 2.
Since P is the base point, the adversay generates a random number k1 and computes K1 = k1P.
-
Step 3.
The adversary gets Ri as Ri = h(IDi ‖ s).
-
Step 4.
The adversary computes V1 = h(IDi || K1 || Ri || T1) and generates a valid request message {CIDi, K1, V1, T1} and sends it to the server.
-
Step 5.
Based on the received message {CIDi, K1, V1, T1}, the server generates a new random number rNew and achieves CIDiNew = Es (IDi || rNew). Then, the server calculates K2 = k2P, K = k2K1, ECIDi = h(K) ⊕ CIDiNew, and V2 = h(K1 || h(IDi || s) || K2 || CIDiNew || K). At last, the server sends the response message {K2, ECIDi, V2} to the adversary.
-
Step 6.
Using the received K2, the adversary computes K = k1K2 = k1k2P.
-
Step 7.
Ultimately, the adversary computes session key as SK = h(IDi ‖ K ‖ K1 ‖ K2).
Since in Arshad and Rasoolzadegan’s protocol [16], the disclosure of the private key of the server leads to the impersonation of a legal user, we can conclude that Arshad and Rasoolzadegan’s protocol [16] cannot withstand the key compromise impersonation attack.
Proposed protocol
As proved in section 3, Giri et al.’s [17], Amin and Biswas’s [18], and Arshad and Rasoolzadegan’s [16] protocols fail to achieve the entire security objectives. This is because an adversary can execute a key compromise impersonation attack to impersonate a legal user and obtain the session key. As a result, in this section, we propose a novel user authentication and key agreement protocol, which can properly withstand this attack. The proposed protocol is composed of patient registration, login and authentication, and password change phases. The important notations of the proposed scheme have been listed in Table 2.
Patient registration phase
In this phase, each patient who intends to get services from the medical server performs the registration process. All the steps of this phase take place over a reliable channel. The detail of the registration phase is described as follows and demonstrated in Fig. 8.
-
Step 1.
Patient → Server: {IDp, IDm, OPWp, XPWp}
The patient first selects an identity IDp, a password PWp, and two random numbers rp and up. Subsequently, he/she computes OPWp = h0((IDm ⊕ IDp) ‖ rp ‖ PWp) and XPWp = h0(up ‖ PWp)P, where P is the base point, and sends the message {IDp, IDm, OPWp, XPWp} to the server through a reliable channel.
-
Step 2.
Server → Patient: {EIDp, Bp, Cp}
After receiving the registration message {IDp, IDm, OPWp, XPWp}, the server checks the existence of IDp and identity of mobile device IDm in its database. If it exists, the server requests the user to pick another identity. Otherwise, the server computes Ap = h0(IDm ‖ IDp ‖ s), Bp = OPWp ⊕ Ap, Cp = h1(OPWp) ⊕ sP, and Dp = h1(Ap) ⊕ XPWp. After that, it generates a random number rs and encrypts (IDp ‖ rs) by its own private key s as EIDp = Encs(IDp ‖ rs). Ultimately, the server stores <IDp, IDm, Empty, Dp > in its registration table and sends the message {EIDp, Bp, Cp} to the patient through a secure channel.
-
Step 3.
Patient → Mobile device: {EIDp, Bp, Cp, rp, up, Tokenppw}
After getting the message from the server, the user sets Tokenppw = 0 and stores the values <EIDp, Bp, Cp, rp, up, Tokenppw > in his/her mobile device and then finishes the registration process.
Login and authentication phase
After the successful completion of the patient registration phase, the patient can communicate with the medical server at any time using his/her mobile device. All the steps of this phase are presented below and illustrated in Fig. 9.
-
Step 1.
Patient → Server: {Tokenppw, EIDp, Xp, Vp, Vppw, Tp}
At the beginning, the patient inserts his/her identity IDp and password PWp. Then, the mobile device retrieves rp and Bp from its memory and calculates OPWp = h0((IDm ⊕ IDp) ‖ rp ‖ PWp), Ap = OPWp ⊕ Bp, and point Qs = sP = h1(OPWp) ⊕ Cp. Next, the mobile device generates a random number xp and computes Xp = h0(IDm ‖ IDp ‖ xp)P and captures its current time Tp. Finally, the mobile device computes verifier Vp = h0(Ap ‖ Xp ‖ Qs ‖ Tp ‖ Tokenppw). If Tokenppw > =1, it computes XPWp = h0(up ‖ PWp)P and Vppw = h0(Ap ‖ Xp ‖ Qs ‖ Tp ‖ XPWp ‖ Tokenppw) and submits the request message {Tokenppw, EIDp, Xp, Vp, Vppw, Tp} to the server over a public channel.
-
Step 2.
Server → Patient: {OEIDpnew, Xs, Vs}
After receiving the request message {Tokenppw, EIDp, Xp, Vp, Vppw, Tp}, the server checks the validity of Tp by checking the condition Tc − Tp? ≤ ∆T, where Tc is the time when the server receives the login request message {Tokenppw, EIDp, Xp, Vp, Vppw, Tp} and ∆T is the maximum transmission delay. If the time delay in message transmission is valid, it decrypts EIDp by its own private key s as (IDp ‖ rs) = Decs(EIDp). After decrypting EIDp, the server checks the existence of IDp in its database. If it exists, the server retrieves IDm and Dp corresponding to IDp and computes Ap = h0(IDm ‖ IDp ‖ s) and XPWp = h1(Ap) ⊕ Dp. If Tokenppw == 0, the server checks whether the received Vp is identical to h0(Ap ‖ Xp ‖ Qs ‖ Tp ‖ Tokenppw) or not. If Tokenppw > = 1, the server checks whether the received Vppw is identical to h0(Ap ‖ Xp ‖ Qs ‖ Tp ‖ XPWp ‖ Tokenppw) or not. If it is not identical, the server rejects the session. Otherwise, it computes XPWpold = h1(Ap) ⊕ Dpold and checks whether the received Vppw is equal to h0(Ap ‖ Xp ‖ Qs ‖ Tp ‖ XPWpold ‖ Tokenppw) or not. If it is not equal, the server aborts the login request. Else, it generates a random number xs and calculates Xs = h0(IDs ‖ xs)P, K = (s + h0(IDs ‖ xs))(XPWp + Xp), and the session key as SK = h2(Tp ‖ K). Following, the server generates a new random number rsnew and computes EIDpnew = Encs(IDp ‖ rsnew), OEIDpnew = EIDpnew ⊕ h3(SK), and verifier Vs = h0(Ap ‖ Xs ‖ EIDpnew ‖ SK). Eventually, the server sends the response message {OEIDpnew, Xs, Vs} to the patient through an insecure channel. Note that the server does not submit the value of EIDpnew in plaintext over the reliable channel. Thus, the proposed scheme supports the unlinkability.
-
Step 3.
Patient gains session key
Upon receiving the message {OEIDpnew, Xs, Vs}, the mobile device computes K = (h0(up ‖ PWp) + h0(IDm ‖ IDp ‖ xp))(Qs + Xs), session key as SK = h2(Tp ‖ K), and EIDpnew = OEIDpnew ⊕ h3(SK) and checks whether the received Vs matches to h0(Ap ‖ Xs ‖ EIDpnew ‖ SK) or not. If the verification succeeds, the server is authenticated and the session key is verified and also EIDp is substituted with EIDpnew. Finally, the mobile device sets Tokenppw = 0 for the next key agreement.
Password change phase
As illustrated in Fig. 10, a legal patient with a mobile device can change his/her password through the following steps.
-
Step 1.
Mobile device → Server: {Tokenppw, EIDp, XOPWpnew, Vp, Tp}
The patient inserts his/her identity IDp and password PWp. The mobile device retrieves rp and Bp from its memory and calculates OPWp = h0((IDm ⊕ IDp) ‖ rp ‖ PWp), Ap = OPWp ⊕ Bp, and XPWp = h0(up ‖ PWp)P. Then, the patient selects a new password PWpnew and new random numbers rpnew and upnew. The mobile device calculates OPWpnew = h0((IDm ⊕ IDp) ‖ rpnew ‖ PWpnew), XPWpnew = h0(upnew ‖ PWpnew)P, and XOPWpnew = (OPWpnew ‖ XPWpnew) ⊕ h1(Ap). Besides, the mobile device adds one to the token and sets Tokenppw = Tokenppw + 1. Next, the mobile device computes verifier Vp = h0(Ap ‖ XPWp ‖ OPWpnew ‖ XPWpnew ‖ Tp ‖ Tokenppw). Finally, the mobile device submits the change password request message {Tokenppw, EIDp, XOPWpnew, Vp, Tp} to the server through an unreliable channel.
-
Step 2.
Server → Mobile device: {OEIDpnew, XBpnew, Vs}
Upon receiving the request message {Tokenppw, EIDp, XOPWpnew, Vp, Tp}, the server checks the validity of Tp by checking the condition Tc − Tp? ≤ ∆T, where Tc is the time when the server receives the change password request message {Tokenppw, EIDp, XOPWpnew, Vp, Tp} and ∆T indicates the maximum transmission delay. If the condition does not hold, the server rejects the request message. Otherwise, it checks the Tokenppw. If Tokenppw == 1, the server decrypts EIDp by applying its own private key s as (IDp ‖ rs) = Decs(EIDp). Afterwards, the server retrieves IDm corresponding to IDp and computes Ap = h0(IDm ‖ IDp ‖ s), XPWp = h1(Ap) ⊕ Dp, and (OPWpnew ‖ XPWpnew) = XOPWpnew ⊕ h1(Ap). The server checks whether the received Vp is equal to h0(Ap ‖ XPWp ‖ OPWpnew ‖ XPWpnew ‖ Tp ‖ Tokenppw) or not. If it is not equal, the server aborts the request. Otherwise, it calculates Dpnew = h1(Ap) ⊕ XPWpnew. At last, the server updates <IDp, IDm, Empty, Dp > as <IDp, IDm, Dp, Dpnew > in its database and renames <IDp, IDm, Dp, Dpnew > as <IDp, IDm, Dpold, Dp>. If Tokenppw > 1, the server decrypts EIDp by its own private key s as (IDp ‖ rs) = Decs(EIDp). Then, the server retrieves IDm corresponding to IDp and calculates Ap = h0(IDm ‖ IDp ‖ s), XPWpold = h1(Ap) ⊕ Dpold, (OPWpnew ‖ XPWpnew) = XOPWpnew ⊕ h1(Ap). The server checks whether the received Vp is identical to h0(Ap ‖ XPWp ‖ OPWpnew ‖ XPWpnew ‖ Tp ‖ Tokenppw) or not. If they are not equal, the server terminates the request. Else, it computes Dpnew = h1(Ap) ⊕ XPWpnew. At last, the server updates <IDp, IDm, Dpold, Dp > as <IDp, IDm, Dpold, Dpnew > and renames <IDp, IDm, Dpold, Dpnew > as <IDp, IDm, Dpold, Dp>. Furthermore, the server calculates Bpnew = OPWpnew ⊕ Ap and XBpnew = Bpnew ⊕ h2(Ap). As a final point, the server selects a random number rsnew and calculates EIDpnew = Encs(IDp ‖ rsnew), computes OEIDpnew = EIDpnew ⊕ h3(Ap), and obtains verifier Vs = h0(Bpnew ‖ EIDpnew ‖ Tp). Over an insecure channel, the server sends the response message {OEIDpnew, XBpnew, Vs} to the mobile device.
-
Step 3.
Mobile device changes the password
After receiving the response message {OEIDpnew, XBpnew, Vs}, the mobile device computes Bpnew = XBpnew ⊕ h2(Ap) and EIDpnew = OEIDpnew ⊕ h3(Ap). Next, the mobile device checks whether the received Vs is identical to h0(Bpnew ‖ EIDpnew ‖ Tp) or not. If they are not equal, the mobile device aborts the session. Otherwise, it replaces <EIDp, Bp, rp, up > with < EIDpnew, Bpnew, rpnew, upnew >. Finally, the mobile device sets the Tokenppw = 0.
Formal security verification using the AVISPA simulation tool
The proposed protocol has been simulated using the AVISPA software. For the implementation of cryptographic protocols, the high level protocol specification language (HLPSL) is used and four checkers/back-ends called on-the-fly model-checker (OFMC), constraint-logic-based attack searcher (CL-AtSe), sat-based model-checker (SATMC), and tree automata-based protocol analyser (TA4SP) models are adopted for the simulation purposes and to analyse different security features like secrecy of keys, freshness, authentication, and resistance against the replay attack [44] [45].
The HLPSL is an expressive, modular, role-based, and formal language that describes each participant’s role, adversary models, composition rules for the illustration of basic roles control-flow patterns, and security properties. The structure of the AVISPA software [46] is depicted in Fig. 11 for the better understanding. Brief explanation of these model checkers is given below.
-
OFMC: This back-end constructs the infinite tree defined through the protocol analysis problem and implements diverse symbolic methods to search the state space in a demand-driven manner (i.e., on-the-fly). OFMC assists to discover the attacks and verifies the correctness of the protocol for a bounded number of sessions without limiting the number of messages that an intruder can produce.
-
CL-AtSe: This back-end is applied to discover the attacks on the protocol by applying a set of constraints that are gained by translating the security protocol specifications written in the intermediate format (IF). The discovery of attacks and the translation of protocol specifications, planned based on the adversary’s knowledge, are completely automated and internally achieved by CL-AtSe model checker.
-
SATMC: This back-end is applied to detect the state space through several symbolic methods. It is worth noting that it also detects attacks on protocols and confirms the security requirements for a bounded number of sessions.
-
TA4SP: This back-end guesses the intruder knowledge (over or under) applying unbounded number of sessions based on propositional formula and regular tree languages.
To verify the security of cryptographic protocols in the formal manner, the AVISPA tool is integrated with a graphical user interface, named security protocol animator (SPAN). The protocol specification in HLPSL has four sections, namely role, session, environment, and goal. To evaluate a cryptographic protocol on the AVISPA the following steps are performed: 1) the protocol is executed in HLPSL specification, 2) the AVISPA tool exchanges this specification into IF in an automatic manner through a built-in translator, named HLPSL2IF translator, and 3) the IF specification is given to the back-ends of the AVISPA tool to evaluate whether there exists any active or passive attack.
The IF is a low-level language containing some information about IF syntax for back-ends, the explanation of mathematical properties of operators (e.g., bitwise XOR, exponentiation etc.) and the intruder’s behaviour. After the implementation of IF, any model checker of AVISPA returns the simulation results of the protocol through analysing the output format (OF), which demonstrates that the given protocol is SAFE or UNSAFE against the intruders.
We have modelled the proposed protocol using the AVISPA tool by HLPSL and the role specifications of the patient and server are shown in Figs. 12 and 13.
Furthermore, as illustrated in Fig. 14, we have determined the HLPSL specification for the session.
role and have defined session of the scheme by describing the communications between the patient and the server. In Fig. 15, the environment role expresses a composition of one or more sessions and contains the intruder knowledge and the global constants. The intended security properties and goals have been specified as presented in Fig. 16.
In the patient role, the goal secrecy of sub1, the statement secret ({IDp, IDp}, sub1, {P,S}) means that the identity of patient IDp and mobile device IDp are kept furtive to the patient and server. In the same way, in the goal secrecy of sub2, where sub2 is a protocol id for the statement secret ({PWp, Rp, Up}, sub2, {P}), the patient only knows his/her generated password PWp and random numbers (Rp, Up). In the goal secrecy of sub3, where sub3 is a protocol id for the statement secret ({Xp’}, sub3, {P}), we state that the chosen random number Xp by the patient is kept secret to him/her. Likewise, in the goal secrecy of sub4, where sub4 is a protocol id for the statement secret ({SK’}, sub4, {P,S}), the session key SK is only identified by the patient and server.
In the server role, the goal secrecy of sub5, the statement secret ({Rs’, SS}, sub5, {S}) means that the random number generated by the server Rs and private key of the server SS are kept furtive to it. Similarly, in the goal secrecy of sub6, where sub6 is a protocol id for the statement secret ({Xs’}, sub6, {S}), the server only knows chosen random number Xs. The goal authentication_on patient_server_tp means that the patient captures a timestamp tp and the server authenticates the patient from the message of him/her.
Similarly, the goal authentication_on patient_server_xp points out that the patient chooses a random number xp and the server authenticates the patient when it receives xp from the patient. The goal authentication_on server_patient_xs indicates that the server selects a random number xs and the patient authenticates the server when it receives xs from the server.
Figures 17 and 18 are the simulation results of the proposed protocol for the OFMC and CL-AtSe back-ends. The results show that the proposed protocol is SAFE under the OFMC and CL-AtSe back-ends, meaning that the protocol meets the specified goals. Therefore, we confirmed that the proposed protocol meets the mutual authentication and privacy of the sensitive data, as specified in the environment role.
Informal security analysis of the proposed protocol
Offline password guessing attack
Assume an adversary steals or finds a patient’s mobile device and retrieves {EIDp, Bp, Cp, rp, up, Tokenppw} from its memory, where EIDp = Encs(IDp ‖ rs), Bp = OPWp ⊕ Ap, and Cp = h1(OPWp) ⊕ sP. Because the patient’s identity IDp is encrypted with the private key of server, s, the adversary cannot derive the IDp from EIDp. Moreover, the password of patient PWp is not saved directly in the mobile device and the adversary cannot guess the PWp from the stored information in the mobile device. Furthermore, because the adversary does not know the value of OPWp, he/she cannot guess the password using the equation OPWp = h0((IDm ⊕ IDp) ‖ rp ‖ PWp). Thus, the proposed protocol is secure against the offline password guessing attack.
Stolen smart card/mobile device attack
In general, since the patient uses low entropy identity and password, the adversary may try to guess them in polynomial time. Hence, the adversary tries to extract confidential information from the stolen mobile device. Here, it is assumed that the adversary can retrieve the {EIDp, Bp, Cp, rp, up, Tokenppw} saved in the mobile device. However, these values will not help the adversary to get the actual identity and password of patient. This is because the adversary does not know the private key s and EIDp is protected by the symmetric encryption. Therefore, the proposed protocol can resist this attack.
Replay attack
One of the challenging matters in cryptography is resisting against the replay attack. In the proposed protocol, the adversary may try to replay a previously-sent message {Tokenppw, EIDp, Xp, Vp, Vppw, Tp} or {OEIDpnew, Xs, Vs} transmitted between the patient and the server. The server can distinguish a replay attack by the examination of the freshness of the timestamp Tp as |Tc − Tp| ≤ ∆T, where Tc is the current time that the server gets the message and ∆T is the maximum transmission delay. In addition, the patient can filter a replayed message by checking the equality of h0(Ap ‖ Xs ‖ EIDpnew ‖ SK) =? Vs. Doing so, the Tp involved in the computation of the session key SK can properly make the resistance against this attack.
User and server impersonation attacks
In such attacks, usually by altering the communicating messages, an adversary may attempt to impersonate him/herself as a valid user or server. However, the proposed protocol can resist this attack according to the following justification.
-
Initially, the adversary attempts to obtain and send a legal login message {Tokenppw, EIDp, Xp, Vp, Vppw, Tp}. The adversary cannot calculate legal login parameter EIDp, because he/she is unaware of the patient’s identity IDp and the private key of the server s. Therefore, the presented protocol provides security on the login message.
-
It is assumed that the adversary traps communicating message {OEIDpnew, Xs, Vs} and tries to impersonate as a legitimate server to the patient. The adversary fails to calculate the message {OEIDpnew, Xs, Vs}, because he/she cannot calculate valid OEIDpnew and Vs due to the unknown parameters Xs and SK, where SK is the shared key only known to the server and patient.
Therefore, it is clear from the above discussion that no one can impersonate a legitimate patient or server and the proposed protocol can prevent both user and server impersonation attacks.
Privileged insider attack
In the patient registration phase, each patient sends {IDp, IDm, OPWp, XPWp} to the server, where OPWp = h0((IDm ⊕ IDp) ‖ rp ‖ PWp) and XPWp = h0(up ‖ PWp)P. Since an insider does not know the random numbers rp and up, he/she has no chance to acquire or guess the password of the patient PWp. As a result, the proposed protocol can provide the security against the privilege insider attack.
Key replicating attack
This attack is a form of the man-in-the-middle attack, where an adversary captures and modifies the transmitting messages between two parties in such a manner that he/she persuades both the parties to agree on a wrong session key, a key that both parties in fact do not want to agree on. Due to the proper usage of key confirmation in the proposed protocol, our scheme can withstand this attack. This is because computing the correct verifiers can only be done by the authentic communicating patient and server.
Known session-specific temporary information attack
In the proposed protocol, if the adversary gets access to the random numbers xp and xs and tries to calculate session key SK, where the session key is computed as SK = h2(Tp ‖ K), he/she will not succeed. It is worth noting that the SK not only depends on the session-specific random numbers xp and xs, but also relies on K = (h0(up ‖ PWp) + h0(IDm ‖ IDp ‖ xp))(Qs + Xs). Thus, because no one has access to the patient’s password PWp, the proposed protocol is secure against this attack.
Perfect forward secrecy
The session key SK is computed as SK = h2(Tp ‖ K), where, K = (h0(up ‖ PWp) + h0(IDm ‖ IDp ‖ xp))(Qs + Xs) or K = (s + h0(IDs ‖ xs))(XPWp + Xp). If the adversary acquires the patient’s password PWp and the server’s private key, s, he/she must also know the session-specific random number xp or xs to obtain the session key. However, according to the elliptic curve discrete logarithm problem (ECDLP), this is not feasible. Therefore, the proposed protocol can properly provide the perfect forward secrecy.
Patient’s anonymity and unlinkability
If an adversary tries to get the identity of a patient from the communicating messages, his/her attempts would fail. This is because the patient’s identity, IDp, was never transmitted over the unreliable channels and the adversary cannot acquire it from EIDp = Encs(IDp ‖ rs). Furthermore, because EIDp is updated in each key agreement or even password change, the adversary is not able to relate or link two messages to a specific patient. Therefore, the proposed protocol can provide the strong anonymity.
Session key verification
In the proposed protocol, the server computes the session key as SK = h2(Tp ‖ K) and a verifier as Vs = h0(Ap ‖ Xs ‖ EIDpnew ‖ SK). Accordingly, in step 3 of the login and authentication phase, the patient verifies the SK by checking whether its computed Vs matches the received Vs. Hence, the proposed protocol has the session key verification property.
Key compromise impersonation attack
Preventing this attack is one of the critical security requirements of the authentication and key agreement protocols. In the suggested protocol, if the long-term secrets of server are leaked, the adversary cannot still impersonate as an authentic patient and similarly, knowing the long-term secrets of a valid patient does not help the adversary to impersonate as the server. Therefore, the proposed protocol can properly resist the key compromise impersonation attack.
Denial of service attack
In the proposed protocol, using some hash-based verifiers, each entity can validate the integrity of the received message very soon. Thus, if an adversary, by frequent changing of his/her IP address and submitting some fake messages, attempts to occupy some time or resources of the server, his/her attempts will fail. For that reason, the registered patients can receive services smoothly and the suggested protocol can correctly withstand this attack.
Performance evaluation
In this section, the performance of the proposed protocol is compared with Chaudhry et al.’s [15], Arshad and Rasoolzadegan’s [16], Giri et al.’s [17], Amin and Biswas’s [18], Arshad and Nikooghadam’s [23], Tan’s [24], Islam and Khan’s [30], Arshad et al.’s [31], Bin Muhaya’s [32], Amin and Biswas’s [33], Tseng et al.’s [35], Jiang et al.’s [38], Lu et al.’s [39], Qiu et al. ‘s [40], and Xu et al.’s [47] protocols. The comparison of the proposed protocol with the mentioned related authentication and key agreement protocols, in terms of security features, execution time, communication cost, and storage cost are indicated in Tables 3 and 4. The description of the used notations is as follows.
-
TF: the time for computing a fuzzy extraction
-
TM: the time for computing an elliptic curve (EC) point multiplication
-
TA: The time for computing an EC point addition
-
TE: The time for computing a modular exponentiation
-
TH: The time for computing a hash operation
-
TS: The time for computing a symmetric encryption/decryption
According to the experimental results obtained in [48], the TF, TM, TA, TE, TH, and TS is 0.063075 s, 0.063075 s, 0.000262 s, 0.522 s, 0.0005 s, 0.0087 s, respectively. In addition, we have considered the size of an identifier or timestamp to be 32 bits, a nonce to be 64 bits, an EC point to be 320 bits, and a hash output to be 256 bits.
In the login and authentication phase of the proposed protocol, two EC point multiplication operations, eleven hash operations, and two EC point addition operations are executed by the patient mobile device. Hence, the computational cost for the mobile device is 2TM + 2TA + 11TH, which is 0.1321s. Moreover, two EC point multiplication operations, one symmetric encryption operation, one symmetric decryption operation, eight hash operations, and two EC point addition operations are done by the server. As a result, the computational cost for the server is TM + 2TA + 2TS + 8TH, which is 0.148 s. Hence, the total execution time of the proposed protocol is 0.2801 s. For the communication cost, in the login and authentication phase of the proposed protocol, the mobile device submits {Tokenppw, EIDp, Xp, Vp, Vppw, Tp} and recieves {OEIDpnew, Xs, Vs}. Therefore, the total communication cost is 1632 bits.
As observed in Table 3, most of the authentication and key agreement protocols for TMISs do not meet the appropriate security features, while the suggested protocol covers the drawbacks of the existing protocols. It is clear that the proposed protocol has less computation overhead than [15, 17, 18, 24, 30,31,32,33, 35, 38], and [47]. Likewise, it has less communication cost compared to [15, 17, 18], and [31]. More importantly, unlike the protocols [15, 16, 18, 23, 31,32,33, 38, 39], and [40], where three messages are required for the key agreement between the patient and server, the key agreement process of the proposed protocol is done using just two messages.
According to the cryptanalysis, Arshad and Rasoolzadegan’s protocol [16] is vulnerable to the key compromise impersonation attack. In a similar sense, none of the related protocols are secure against the key compromise impersonation attack whereas the suggested protocol can resist against this attack. Thus, considering the security metrics, the proposed protocol is more suitable than the related ones. In other words, the proposed protocol not only can cover the security problems of Arshad and Rasoolzadegan’s protocol [16], Giri et al.’s protocol [17], and Amin and Biswas’s protocol [18] but also, as Table 3 shows, it keeps their merits. Furthermore, according to the obtained result of Table 4, the proposed protocol also has an acceptable level of performance in comparison to the all related protocols. The proposed protocol has achieved the resistance against the key compromise impersonation attack with only two elliptic curve multiplications at each side, which we believe is the minimal possible value.
Conclusion
Numerous user authentication and session key agreement protocols have been proposed for accessing the medical server; however, most of them fail to fulfil the complete security requirements. In order to cover the existing security challenges, this article, using the elliptic curve cryptography, has presented a new patient authentication and session key agreement protocol for accessing the medical server in the TMISs. We have then evaluated the robustness of the proposed scheme using formal and informal security analyses. It is found that the proposed protocol meets the all required security features. More specifically, the simulation results of the formal security verification using the widely-accepted AVISPA tool have been presented, which expresses that the proposed protocol is secure against active and passive attacks including the man-in-the-middle and replay attacks. The performance of the proposed protocol in terms of computation and communication overheads proves that it has a comparable efficiency. In conclusion, considering both security and efficiency, we have indicated that the proposed protocol is quite appropriate to be used for providing secure communications in the context of the telecare medical information systems.
References
Chaudhry, S. A., Mahmood, K., Naqvi, H., and Khan, M. K., An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography. J. Med. Syst. 39(11):175, 2015.
Jindal, A., Dua, A., Kumar, N., Das, A. K., Vasilakos, A. V., and Rodrigues, J. J., Providing Healthcare-as-a-Service Using Fuzzy Rule Based Big Data Analytics in Cloud Computing. IEEE Journal of Biomedical and Health Informatics 22(5):1605–1618, 2018.
Lee, T. F., Verifier-based three-party authentication schemes using extended chaotic maps for data exchange in telecare medicine information systems. Comput. Methods Prog. Biomed. 117(3):464–472, 2014.
Chaudhry, S. A., Naqvi, H., and Khan, M. K., An enhanced lightweight anonymous biometric based authentication scheme for TMIS. Multimedia Tools and Applications 77(5):5503–5524, 2018.
Amin, R., and Biswas, G. P., A novel user authentication and key agreement for accessing multi-medical server usable in TMIS. J. Med. Syst. 39(3):33, 2015.
Zhang, K., Yang, K., Liang, X., Su, Z., Shen, X., and Luo, H. H., Security and privacy for mobile healthcare networks. IEEE Wirel. Commun. 22(4):104–112, 2015.
Li, C. T., Shih, D. H., and Wang, C. C., Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems. Comput. Methods Prog. Biomed. 157:191–203, 2018.
Irshad, A., Sher, M., Nawaz, O., Chaudhry, S. A., Khan, I., and Kumari, S., A secure and provable multi-server authenticated key agreement for TMIS based on Amin et al. scheme. Multimedia Tools and Applications 76(15):16463–16489, 2017.
Sutrala, A. K., Das, A. K., Odelu, V., Wazid, M., and Kumari, S., Secure anonymity-preserving password-based user authentication and session key agreement scheme for telecare medicine information systems. Comput. Methods Prog. Biomed. 135:167–185, 2016.
Wazid, M., Zeadally, S., Das, A. K., and Odelu, V., Analysis of security protocols for mobile healthcare. J. Med. Syst. 40(11):229, 2016.
Wu, F., Xu, L., Kumari, S., Li, X., Das, A. K., and Shen, J., A lightweight and anonymous RFID tag authentication protocol with cloud assistance for e-healthcare applications. J. Ambient. Intell. Humaniz. Comput. 9(4):919–930, 2018.
Chaudhary, R., Jindal, A., Aujla, G. S., Kumar, N., Das, A. K., and Saxena, N., LSCSH: Lattice-Based Secure Cryptosystem for Smart Healthcare in Smart Cities Environment. IEEE Commun. Mag. 56(4):24–32, 2018.
J. Srinivas, A. K. Das, N. Kumar and J. Rodrigues, Cloud centric authentication for wearable healthcare monitoring system. IEEE Transactions on Dependable and Secure Computing, 2018.
S. Roy, A. K. Das, S. Chatterjee, N. Kumar, S. Chattopadhyay and J. J. Rodrigues, Provably secure fine-grained data access control over multiple cloud servers in mobile cloud computing based healthcare applications. IEEE Transactions on Industrial Informatics, 2018.
Chaudhry, S. A., Khan, M. T., Khan, M. K., and Shon, T., A multiserver biometric authentication scheme for TMIS using elliptic curve cryptography. J. Med. Syst. 40(11):230, 2016.
Arshad, H., and Rasoolzadegan, A., Design of a secure authentication and key agreement scheme preserving user privacy usable in telecare midicine information systems. J. Med. Syst. 40(11):237, 2016.
Giri, D., Maitra, T., Amin, R., and Srivastava, P. D., An efficient and robust RSA-based remote user authentication for telecare medical information systems. J. Med. Syst. 39(1):145, 2015.
Amin, R., and Biswas, G. P., An improved RSA based user authentication and session key agreement protocol usable in TMIS. J. Med. Syst. 39(8):79, 2015.
R. Canetti and H. Krawczyk, Analysis of key-exchange protocols and their use for building secure channels. Advances in Cryptology, pp. 453–474, 2001.
Hwang, M. S., and Li, L. H., A new remote user authentication scheme user smart cards. IEEE Transactions on Consumers Electronics 46(1):28–30, 2000.
Sun, H. M., An efficient user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 46(4):958–961, 2000.
Tan, Z., An efficient biometrics-based authentication scheme for telecare medicine information systems. Network 2(3):200–204, 2013.
Arshad, H., and Nikooghadam, M., Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst. 38(12):136, 2014.
Tan, Z., A user anonymity preserving three-factor authentication scheme for telecare medicine information systems. J. Med. Syst. 38(3):16, 2014.
Das, A. K., and Goswami, A., An enhanced biometric authentication scheme for telecare medicine information systems with nonce using chaotic hash function. J. Med. Syst. 38(6):27, 2014.
Awasthi, A. K., and Sirvastava, K., A biometric authentication scheme for telecare medicine information systems with nonce. J. Med. Syst. 37(5):9964, 2013.
Mishra, D., Mukhopadhyay, S., Chaturvedi, A., Kumari, S., and Khan, M. K., Cryptoanalysis and improvment of Yen et al.;s biometric-based authentication scheme for telecare medicine information systems. J. Med. Syst. 38(6):24, 2014.
Khan, M. K., and Kumari, S., An authentication scheme for secure access to healthcare services. J. Med. Syst. 37(4):9954, 2013.
Chaudhry, S. A., Naqvi, H., Shon, T., Sher, M., and Farash, M. S., Cryptoanalysis and improvment of an improved two factor authentication protocol for telecare medical information systems. J. Med. Syst. 39(6):66, 2015.
Islam, S. H., and Khan, M. K., Cryptoanalysis and improvment of authentication and key agreement protocols for telecare medicine information systems. J. Med. Syst. 38(10):135, 2014.
Arshad, H., Teymoori, V., Nikooghadam, M., and Abbassi, H., On the security of a two-factor authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst. 39(8):76, 2015.
Bin Muhaya, F. T., Cryptoanalysis and security enhancement of Zhau's authentication scheme for telecare midicine information systems. Security and Communication Networks 8(2):149–158, 2015.
Amin, R., and Biswas, G. P., A secure three-factor user authentication and key agreement protocol for TMIS with user anonymity. J. Med. Syst. 39(8):78, 2015.
Xu, X., Jin, Z. P., Zhang, H., and Zhu, P., A dynamic ID-based authentication scheme based on ECC for telecare medicine information systems. Appl. Mech. Mater. 457:861–866, 2014.
Tseng, C. H., Wang, S. H., and Tsaur, W. J., Hierarchical and dynamic elliptic curve cryptosystem based self-certified public key scheme for medical data protection. IEEE Trans. Reliab. 64(3):1078–1085, 2015.
Amin, R., Islam, S. H., Biswas, G., Khan, M. K., and Kumar, N., An efficient and practical smart card based anonymity preserving user authentication scheme for tmis using elliptic curve. J. Med. Syst. 39(11):1–18, 2015.
Zhang, L., Zhu, S., and Tang, S., Privacy protection for telecare medicine information systems using a chaotic map-based three-factor authenticated key agreement scheme. IEEE Journal of Biomedical and health informatics 21(2):465–475, 2017.
Jiang, Q., Chen, Z., Li, B., Shen, J., Yang, L., and Ma, J., Security analysis and improvment of bio-hashing based three-factor authentication scheme for telecare medical information systems. J. Ambient. Intell. Humaniz. Comput.:1–13, 2017.
Lu, Y., Li, L., Peng, H., and Yang, Y., An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J. Med. Syst. 39(3):32, 2015.
Qiu, S., Xu, G., Ahmad, H., and Wang, L., A robust mutual authentication scheme based on elliptic curve cryptography for telecare medical information systems. IEEE Access 6:7452–7463, 2018.
Li, C. T., Shih, D. H., and Wang, C. C., Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems. Comput. Methods Prog. Biomed. 157:191–203, 2018.
Mohit, P., Amin, R., Karati, A., Biswas, G. P., and Khan, M. K., A standard mutual authentication protocol for cloud computing based health care system. J. Med. Syst. 41(4):50, 2017.
Yau, W. C., and Phan, R. C. W., Security analysis of a chaotic map-based authentication scheme for telecare medicine information systems. J. Med. Syst. 37(6):9993, 2013.
Das, A. K., A secure and effective user authentication and privacy preserving protocol with smart. Netw. Sci., 2012.
S. H. Islam and G. P. Biswas, A provably secure identity-based strong designated verifier proxy. Journal of King Saud University-Computer and Information Sciences, 2013.
AVISPA, Automated validation of internet security protocols and applications. 2014. [Online]. Available: http://www.avispa-project.org/.
X. Xu, P. Zhu, Q. Wen, Z. Jin, H. Zhang and L. He, A secure and efficient authentication and key agreement scheme based on ECC for telecare medicine information systems. Journal of Medical systems, 38, 2014.
He, D., Kumar, N., Khan, M., and Lee, J. H., Anonymous two-factor authentication for consumer roaming service in global mobility networks. IEEE Trans. Consum. Electron. 59(4):811–817, 2013.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
A. Ostad-Sharif, D. Abbasinezhad-Mood, and M. Nikooghadam declare that they have no conflict of interest.
Human and animal rights
This article does not contain any studies with human or animal participants performed by any of the authors. Further, this research has been done without any grant.
Additional information
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Ostad-Sharif, A., Abbasinezhad-Mood, D. & Nikooghadam, M. A Robust and Efficient ECC-based Mutual Authentication and Session Key Generation Scheme for Healthcare Applications. J Med Syst 43, 10 (2019). https://doi.org/10.1007/s10916-018-1120-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-018-1120-5