Abstract
In recent years, the increased availability of lower-cost telecommunications systems and customized patients monitoring devices made it possible to bring the advantages of telemedicine directly into the patient’s home. These telecare medicine information systems enable health-care delivery services. These systems are moving towards an environment where automated patient medical records and electronically interconnected telecare facilities are prevalent. Authentication, security, patient’s privacy protection and data confidentiality are important for patient or doctor accessing to Electronic Medical Records (EMR). A secure authentication scheme will be required to achieve these goals. Many schemes based on cryptography have been proposed to achieve the goals. However, many schemes are vulnerable to various attacks, and are neither efficient, nor user friendly. Specially, in terms of efficiency, some schemes are resulting in high time cost. In this paper we propose a new authentication scheme that is using the precomputing to avoid the time-consuming exponential computations. Finally, it is shown to be more secure and practical for telecare medicine environments.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Telecare medicine information systems are essential part of this cloud computing age. There are various low-cost hand-held telecommunication systems and customized patient monitoring devices. By using these devices advantage of telehealth are reaching directly to the patient home. In such systems, users is connected with various types of networks - wired or wireless. These systems therefore are vulnerable to attackers. To access these services, authentication between both parties becomes an essential need. The host server need authentication to safe its records from unauthorized person. It should ensure the privacy of the patient. On the other hand, patient needs the authentication from server, so that intruder should not be able to impersonate the server.
In 1981, Lamport [9] proposed a solution to the problem of remote authentication using cryptographic hash functions. However, high hash overhead and the necessity for password resetting decreases its suitability for practical use. Since then, many improved password authentication schemes e.g. [10, 12, 14] have been proposed. One of the common feature of these schemes is that the server has to securely store a verification table. If the the verification table is stolen by the adversary, the system may be broken. To resist such a stolen-verifier attack, in 1990, Hwang et al. [7] proposed a non-interactive password authentication scheme and its enhanced version, which additionally uses smart cards. In Hwang et al.’s schemes, the server does not require any verification table. In 2000, Hwang and Li [11] proposed a verification-free password authentication scheme using smart cards based on ElGamal’s public-key technique [13]. However, Hwang-Li’s scheme doesn’t allow users freely choosing and changing their passwords. Furthermore, Hwang-Li’s scheme was found to be vulnerable to various impersonation attacks [2, 3, 6].
A remote user authentication scheme mainly employs the possession of a smart cards or such other device and/or the knowledge of a secret (password, etc.) in order to establish the identity of an individual. However, a smartcard can be lost, stolen [15], misplaced, or willingly given to an unauthorized user; and a secret can be forgotten, guessed, and willingly or unwillingly be disclosed to an unauthorized user. Therefore, biometric techniques have emerged as a powerful tool for remote user authentication to resolve these problems. Since it is based on the physiological and behavioral characteristics of an individual, biometrics does not suffer from disadvantages found in traditional authentication methods. Also, biometrics and smartcard have the potential to be a very useful combination. First, the security and convenience of biometrics allow for the implementation of high-security applications regarding smartcards. Second, smartcards represent a secure and portable way of storing biometric templates, which would otherwise need to be stored in a central database
Chaotic cryptography with its random behavior constitutes a potential protection a set in modern cryptography. Few schemes in literature, based on new family of one-way collision free chaotic hash function [1] showed its supremacy over modular exponentiation-based authentication schemes e.g. Diffie-Helman [1] El Gamal [13] and RSA based encryption algorithms [5].
Related works
Chaotic hash function
This section briefly reviews chaotic hash function. The proposed scheme is based on the following one-dimensional and chaotic piecewise linear map:
where \(x_{i} \in [0,1]\), \(\beta \in (0,0.5)\) is the control parameter. The map is piecewise linear, and the parameter \(\beta \) ensures that the map runs in a chaotic state when \(0 < \beta <0.5\) It transforms an interval [0, 1] onto itself and contains only one parameter \(\beta \). Let \(x_{i}\) be the chaining variable and has initial value \(x_{0}\). That is specified as part of the hash algorithm. \(H_{0}\) is encryption key for the remaining message M. Given a remaining message M, \(H_{0}\) is a constant which is chosen from \((0,1)\). Now the three step iteration, 1st to nth, \((n+1)\)th to 2nth, and \((2n+1)\)th to 3nth, ensure that each bit of the final hash valuewill be related to all bits of messages. (Refer [4])
Chaotic map based nonce
The following spatially generated 2D logistic systems can be used in the proposed scheme to generate a nonce (a pseudo random binary sequence). (Refer [8])
Here \(x_{m,n}\) is the spatial state of the system, w is a real constant and \(\mu \) is a positive parameter. Research shows that when \(2>\mu \geq 1.55\) and \(w \in (-1,1)\), the system is in chaotic state.
Generating a nonce from the orbit of a chaotic map essentially requires mapping the state of the system to \(\{0,1\}\). A simple way to generate a bit sequence from a chaotic real valued signal is as follows:
where c is chosen threshold such that likelihood of \(x_{m,n} > c\) is equal to that of \(x_{m,n} < c\). We choose 128 bit block in proposed scheme as this is cryptographically secure.
Proposed biometric authentication nonce based scheme
The proposed scheme consists of four phases: registration, login, authentication, password change. Information held by Remote System: \(x, h_{c}(.)\)
Registration phase
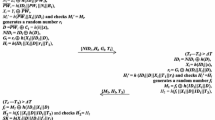
Figure 1 shows the registration phase of proposed scheme. In the registration phase user \(U_{i}\) chooses his/her identity \(ID_{i}\) and password \(pw_{i}\), a random nonce n and interactively submits \(ID_{i}, E_{pu}(pw_{i}\oplus n)\) encrypted with public key pu to the registration center. \(U_{i}\) also imprints his/her fingerprint impression \(\gamma =(S_{i}\oplus n)\) at the sensor, and then registration system performs the following operations:
-
1.
Decrypt the encrypted message by the server private key pr and get \(\alpha =(pw_{i}\oplus n)\).
-
2.
Compute \((pw_{i}\oplus S_{i})\) from \(\alpha =(pw_{i}\oplus n)\) and \(\gamma =(S_{i}\oplus n)\).
-
3.
Computes \(A_{i}=h_{c}(ID_{i}\oplus x)\) and \(X_{i}=h_{c}(A_{i})\) where x is the private key of the remote system, \(\oplus \) is a bit-wise exclusive-OR operation, \(h_{c}(.)\) is a collision free one-way chaotic hash function.
-
4.
Computes \(V_{i} = A_{i}\oplus h_{c}(pw_{i}\oplus S_{i})\) where \(S_{i}\) is the extracted fingerprint template of the user.
-
5.
The remote system personalizes the secure information \(ID_{i}, X_{i}, V_{i}, S_{i}, h_{c}(.)\) and saves it into the mobile device system of the \(U_{i}\).
Login phase
Figure 2 shows the login phase of the proposed scheme. If \(U_{i}\) wants to login the remote system, he or she opens the login application software, enters identity \(ID_{i}\) and password \(pw_{i}*\) and imprints a fingerprint biometric at the sensor. If \(U_{i}\) is successfully verified by his/her fingerprint biometric, a mobile device will perform the following operations:
-
1.
Computes \(B_{i} = V_{i}\oplus h_{c}(pw_{i}*\oplus S_{i})\), and verifies whether \(h_{c}(B_{i}) = X_{i}\) or not. If equal the user’s device performs further operation; otherwise it terminates the operation.
-
2.
Computes \(D_{1} = h_{c}(B_{i}\oplus T_{u})\), where \(T_{u}\) is the current time stamps of the device.
-
3.
At the end of the login phase, \(U_{i}\) sends the login message \(m=(ID_{i},D_{1}, T_{u})\) to the remote system over an insecure network.
Authentication phase
In the authentication phase, when the remote system receives the message \(m=(ID_{i},D_{1}, T_{u})\) from the user, the remote system and user perform following operations.
-
1.
The remote system checks if the format of \(ID_{i}\) is invalid or if \(T_{s}=T_{u}\) where \(T_{s}\) is the current time stamp of the remote system, then rejects the login request.
-
2.
If \((T_{s}-T_{u})\succ \Delta T\), Where \(\Delta T\) denotes the expected valid time interval for transmission delay, then the remote system rejects the login request.
-
3.
The remote system computes \(D_{1}* = h_{c}(h_{c}(ID_{i}\oplus x)\oplus T_{u})\). If \(D_{1}*\) is equal to the received \(D_{1}\). It means the user is authentic and the remote system accepts the login request and performs the next step, otherwise the login request is rejected.
-
4.
For mutual authentication, the remote system computes \(D_{2}=h_{c}(h_{c}(ID_{i}\oplus x)\oplus T_{s})\) and then sends a mutual authentication message \(D_{2}, T_{s}\) to the \(U_{i}\).
-
5.
Upon receiving the message \(D_{2}, T_{s}\), the user verifies that either \(T_{s}\), is invalid or \(T_{s}=T_{u}\), then the user \(U_{i}\) terminates this session; otherwise performs the next step.
-
6.
\(U_{i}\) computes \(D_{2} = h_{c}(B_{i}\oplus T_{s})\) and compares \(D_{2}*=D_{2}\). If equal, the user believes that the remote party is an authentic, and it holds mutual authentication between.
Password change phase
When user wants to update his password, he can use following clint side protocol:
-
1.
User inputs his credential \(S_{i}\) and request smartcard reader to update password. After valid authentication system asks old password and new password.
-
2.
User submits old password \(pw_{i}\) and new password \(pw_{i}^{new}\).
-
3.
system computes
$$V_{i}^{new} = V_{i} \oplus h_{c}(pw_{i}\oplus S_{i})\oplus h_{c}(pw_{i}^{new} \oplus S_{i})$$and it updates the smartcard information \(V_{i}\) to \(V_{i}^{new}\).
Now information on smartcard is \(\left \{ID_{i}, X_{i}, V_{i}^{new},S_{i},\right .\) \(\left . h_{c}(.)\}\right .\). Thus Password now changed.
Security analysis
Next, this section shows that the improved scheme is secure against the impersonation attack, privileged insider attack, the stolen verifier attack, and this section analysis the enhanced security features of our improved scheme.
Resistance to guessing attack
A guessing attack involves an adversary tries to get long-term private keys (user’s password or server secret and private key), but using non invertible chaotic hash function for any attacker it becomes difficult to extract \(A_{i}\) by knowing \(X_{i}=h_{c}(A_{i})\) . Although the adversary can obtain the secret information stored in the stolen smart card by analyzing the leaked information [15] however adversary could not be able to extract \(A_{i}\).
Resistance to parallel session, reflection attack
In parallel session attack, without knowing the correct password of the user, an attacker can masquerade as the legal user by creating a valid login message out of some eavesdropped communication between the user and the server. but our proposed scheme is free from parallel session attack.
Resistance to insider attack
If an insider of S has obtained \(U_{i}'s\) password \(pw_{i}\). He can try to impersonate \(U_{i}\) to access other server. In the registration phase of the improved scheme, \(U_{i}\) sends encrypted password with appropriate nonce, i.e., \(E_{pu}(pw_{i}\oplus n)\) thus \(pw_{i}\) will not be revealed to S without knowing remote system’s private key.Since the insider can not obtain \(pw_{i}\), the improved scheme can withstand the insider attack.
Resistance to server spoofing attack
The spoofing attack completely solved by providing mutual authentication between user and server.Since remote system S sends mutual authentication message \([D_{2}]\) to the user in login phase. If an attacker intercepts it and re-send the forged message i.e. \([D_{2}']\) to user U, it will not be verified by authentication phase since \({D_{2}}^{*} = h_{c}(B_{i}\oplus T_{s})\neq D_{2}'\). Therefore proposed scheme can withstand the spoofing attack.
Conclusion
This paper proposes a secure Biometric Authentication Scheme for Telecare Medicine Information Systems with nonce with better resistance to the to the impersonation attack, the stolen smart card attack, the privileged insider attack.
References
Menezes, A. J., Oorschot, P. C., and Vanstone, S. A., Handbook of applied cryptography. CRC Press, 1997.
Chang, C. C., and Hwang, K. F., Some forgery attack on a remote user authentication scheme using smart card. Informatica 14(3):289–294, 2003.
Chan C. K., and Cheng, L. M., Cryptanalysis of a remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 46(4):992–993, 2000.
Deng, S., Xiao, D., Liao, X., One-way hash function construction based on chaotic map with changeable parameter. Chaos, Solitons Fractals 24:65–71, 2005.
Sun, H. M., An efficient remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 46(4):958–961, 2000.
Yeh, H. T., Sun, H. M., and Hsieh, B. T., Security of a remote user authentication scheme using smart cards. IEICE Trans. Commun. B(1)(E87):192–194, 2004.
Hwang, T., Chen, Y., and Laih, C.-S., Non-interactive password authentications without password tables. In: Computer and Communication Systems, 1990. IEEE TENCON’90., 1990 IEEE Region 10 Conference on, Vol. 1, pages 429–431, 1990.
Liu S., and Sun, L., Cryptographic pseudo random sequence from spatial chaotic map. Chaos, Solitions Fractals 41:2216–2229, 2009.
Lamport, L., Password authentication with insecure communication. Commun. ACM 24:770–772, 1981.
Sandirigama, M., Shimizu, A., and Noda, M. T., Simple and secure password authentication protocol(sas). IEICE Trans. Commun. B(6)(E83):1363–1365, 2000.
Hwang, M. S., and Li, L. H., A new remote user authentication scheme using smart card. IEEE Trans. Consum. Electron. 46(1):28–30, 2000.
Haller, N. H., The s/key(tm) one time password system. In: Proceedings Internet Society Symposium on Network and Distributed System Seurity, pages 151-158, 1994.
Elgamal, T., A public key cryptosystem and a signature scheme based on discrete logarithm. IEEE Trans. Inf. Theory 31(4):469–472, 1985.
Chen T. H., and Lee, W. B., A new method for using hash function to solve remote user authentication. Comput. Electr. Eng. 34(1):53–62, 2008.
Messerges, T. S., Dabbish, E. A., and Sloan, R. H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of interests
The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Awasthi, A.K., Srivastava, K. A Biometric Authentication Scheme for Telecare Medicine Information Systems with Nonce. J Med Syst 37, 9964 (2013). https://doi.org/10.1007/s10916-013-9964-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-013-9964-1