Abstract
The robust truss topology optimization against the uncertain static external load can be formulated as mixed-integer semidefinite programming. Although a global optimal solution can be computed with a branch-and-bound method, it is very time-consuming. This paper presents an alternative formulation, semidefinite programming with complementarity constraints, and proposes an efficient heuristic. The proposed method is based upon the concave–convex procedure for difference-of-convex programming. It is shown that the method can often find a practically reasonable truss design within the computational cost of solving some dozen of convex optimization subproblems.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Many studies have been done on robust optimization of structures against uncertainty in external loads. A possibilistic (or bounded-but-unknown) model of uncertainty, assuming only the set of values that the input data can possibly take, might be useful when reliable statistical property of uncertainty, which is required for a probabilistic model of uncertainty, is unavailable or imprecise. With a possibilistic model of uncertainty, design optimization considering structural robustness against the uncertainty is treated within the framework of robust optimization [5].
Attention of this paper is focused on robust topology optimization of truss structures against uncertainty in the static nodal external load.Footnote 1 Namely, we attempt to find a truss design that minimizes the worst-case compliance, i.e., the maximal value of the compliance among the specified set of external loads.Footnote 2 The seminal work of Ben-Tal and Nemirovski [7] shows that, based on the conventional ground structure method, this optimization problem can be formulated as semidefinite programming (SDP).Footnote 3 SDP is a class of convex optimization, and can be solved efficiently with a primal-dual interior-point method [3, 60]. Closely related formulations of continuum-based robust structural optimization can be found in Cherkaev and Cherkaev [12, 13], Calafiore and Dabbene [11], de Gournay et al. [16], Takezawa et al. [57], Brittain et al. [10], Hashimoto and Kanno [25] and Thore [58]. Furthermore, nonlinear SDP approaches to robust structural optimization have been proposed in Guo et al. [22, 24], Kanno and Takewaki [33], and Holmberg et al. [26]. This paper discusses and deals with intrinsic difficulty in robust truss topology optimization.
Suppose that uncertain external forces can possibly be applied at any nodes, and that no external force is applied at an intermediate point of a truss member. If the set of exiting nodes is specified, then the robust truss optimization problem can be recast as SDP [7]. In this approach, all the nodes in the specified set remain in the obtained solution. Also, the obtained solution can possibly have some nodes other than the specified ones, but at such extra nodes no uncertain external force is considered. Thus, it is difficult to predict in advance the set of existing nodes in the robust optimal truss. In other words, the uncertainty model of external forces should be treated as a design-dependent model [32]. This design dependency can be addressed by introducing 0–1 variables to represent the set of existing members in a truss design [61]. The robust truss topology optimization problem is then formulated as mixed-integer semidefinite programming problem (MISDP), which can be solved globally with a branch-and-bound method [61]. Unfortunately, due to large computational cost, this MISDP approach can be applied only to small-scale problem instances [61].
Another issue that has not been considered in literature on robust truss topology optimization [7, 32, 61] is the treatment of parallel consecutive members in the ground structure method. Specifically, in robust truss topology optimization with uncertain external load, overlapping members in the ground structure are not redundant.Footnote 4 Such non-redundancy of overlapping members has also been recognized in truss topology optimization considering the self-weight load [8, 34] and the member buckling constraints [23, 41]. Consider the conventional truss topology optimization. It is often that the optimal solution has parallel consecutive members that are connected by nodes supported only in the direction of those members. A sequence of such members is sometimes called a chain [1]. If only the compliance is considered as the structural performance, one can remove the intermediate nodes and replace the chain with a single longer member. This procedure is called the hinge cancellation [1, 49]. Since the hinge cancellation does not change the compliance, overlapping of members in a ground structure can be removed in advance by deleting the longer member when two members overlap. In contrast, in robust truss optimization under load uncertainties, a solution having a chain is infeasible,Footnote 5 while the one stabilized by hinge cancellation can be feasible. This means that, in general, a global optimal truss topology cannot be captured without incorporating overlapping members in a ground structure. However, on the other hand, presence of overlapping members in a final truss design is not allowed from a practical point of view. Therefore, a special treatment is required in a robust optimization method to prohibit the presence of overlapping members.
This paper addresses the two difficulties in robust truss optimization explained above: the design dependency of the uncertainty model of the external load and the necessity of incorporating overlapping members in a ground structure. Both can be dealt with by introducing, for each member, a 0–1 design variable indicating whether the member vanishes or exists. Therefore, the robust truss topology optimization can be formulated as MISDP; see Sect. 4.2. However, as mentioned before, this approach is applicable only to problems of small size. In contrast, in this paper we attempt to propose a heuristic that can often find a feasible solution with a reasonable objective value. Through the numerical experiments with problem instances having up to about 700 members, it is shown that the proposed method usually converges after solving only a few dozen of convex optimization subproblems, and that it finds a practically reasonable solution.
This paper is partially inspired by papers of Jara-Moroni et al. [30] and Lipp and Boyd [39]. Jara-Moroni et al. [30] present a DC (difference-of-convex) programming approach to finding a stationary point of linear programming with complementarity constraints; see also Le Thi and Pham Dinh [38] and Muu et al. [43] for DC programming approaches to complementarity constraints. A function is said to be a DC (difference-of-convex) function if it can be represented as a difference of two convex functions. A DC programming problem is a minimization problem of a DC function under some inequality constraints, where all the constraint functions are DC functions. One of well-known heuristics for finding a local optimal solution of DC programming is the concave–convex procedureFootnote 6 [14, 18, 44, 50, 64]. Lipp and Boyd [39] show that an extension of the concave–convex procedure can serve as an efficient heuristic for diverse nonconvex optimization problems. For more account on the DC programming and the concave–convex procedure, see Sect. 3.1 and the references therein. In this paper, we first formulate the robust truss topology optimization as semidefinite programming with complementarity constraints (SDPCC). Following an idea found in Jara-Moroni et al. [30], we recast this problem as a DC programming problem. A variant of the concave–convex procedure, which is similar to the one in Lipp and Boyd [39], is then applied to this DC programming formulation. Each iteration of the proposed method consists of solving an SDP problem.
The paper is organized as follows. In Sect. 2 we explain intrinsic difficulties in robust truss topology optimization by using some illustrative examples. Section 3 provides an overview of the necessary background of the DC programming and the concave–convex procedure, and presents the general framework of the algorithm used in this paper. Section 4 briefly reviews the existing MISDP formulation for robust truss topology optimization, and extends it to the problem setting with a ground structure incorporating overlapping members. Section 5 presents a new formulation, as well as a solution method, of robust truss topology optimization. Section 6 reports the results of numerical experiments. Conclusions are drawn in Sect. 7.
In our notation, we use \(\varvec{x}^{\top }\) and \(X^{\top }\) to denote the transposes of vector \(\varvec{x} \in \mathbb {R}^{n}\) and matrix \(X \in \mathbb {R}^{m \times n}\), respectively. For vectors \(\varvec{x} = (x_{i}) \in \mathbb {R}^{n}\) and \(\varvec{y} = (y_{i}) \in \mathbb {R}^{n}\), we write \(\varvec{x} \ge \varvec{y}\) if \(x_{i} \ge y_{i}\) \((i=1,\dots ,n)\). Particularly, \(\varvec{x} \ge \varvec{0}\) means \(x_{i} \ge 0\) \((i=1,\dots ,n)\). The Euclidean norm of \(\varvec{x}\) is denoted by \(\Vert \varvec{x} \Vert = \sqrt{\varvec{x}^{\top } \varvec{x}}\). We use \(\varvec{1} = (1,1,\dots ,1)^{\top }\) to denote the all-ones vector. Let \(\mathcal {S}^{n}\) denote the set of \(n \times n\) real symmetric matrices. We write \(X \succeq 0\) if \(X \in \mathcal {S}^{n}\) is positive semidefinite. We use \(\mathop {\mathrm {diag}}\nolimits (\varvec{x})\) to denote a diagonal matrix, the vector of diagonal entries of which is \(\varvec{x}\). For a finite set T, we use |T| to denote the cardinality of T, i.e., the number of elements in T.
2 Motivation
In this section, we explain intrinsic difficulties in robust truss topology optimization, which motivate us to develop the method proposed in this paper. Details of the examples in this section appear in Sect. 6.1.
Suppose that uncertain static external forces are possibly applied at all the nodes. The robust truss topology optimization is to find a truss design that minimizes the worst-case compliance, i.e., the maximum value of the compliance among possible realizations of the external load, under the upper bound constraint on the structural volume.
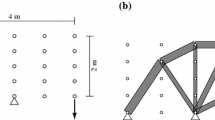
With reference to the examples in Figs. 1 and 2, we explain that incorporating overlapping members into a ground structure is necessary for the robust truss topology optimization. We begin with the conventional compliance minimization, without considering uncertainties. Figure 1a shows a ground structure, which consists of 12 members and has no overlapping members. The ground structure is an initial setting for truss topology optimization. The members consisting of a ground structure are called the candidate members, and their cross-sectional areas are design variables to be optimized. It is worth noting that the locations of the nodes are not treated as design variables. If the cross-sectional area of a member becomes equal to zero as a result of optimization, then the member is removed from the truss. Thus, the connectivity of members, called the topology in this research area, usually changes from the ground structure. Suppose that a vertical external load is applied at the rightmost bottom node, as shown in Fig. 1a. The optimal solution is shown in Fig. 1b, where the width of each member is proportional to its cross-sectional area. This solution has a chain consisting of two members. The hinge cancellation yields the final truss design shown in Fig. 1c. It should be clear that the objective value, i.e., the compliance, of the solution in Fig. 1c is same as the one in Fig. 1b. We next consider the robust optimization. Since uncertain external force is supposed to be applied also at the intermediate node of the chain, the solution in Fig. 1b becomes infeasible. As a result, the optimal solution has one additional member to stabilize that node, as shown in Fig. 2a. Alternatively, consider a ground structure in Fig. 2b, which consists of 14 members. The newly added two members, depicted as slightly curved lines, are in fact straight bars. Therefore, each of them overlaps with two shorter members, and is called an overlapping members. Moreover, the middle node is exactly located on a line forming an overlapping member. Therefore, we say that the overlapping member lies on the middle node. The robust optimal solution obtained from this ground structure is shown in Fig. 2c.Footnote 7 Namely, at the global optimal solution, the longer member is selected instead of the chain and the intermediate node of the chain is removed. Thus, overlapping members do not mean redundancy, because connection of two members via an intermediate node introduces an extra uncertain load applied to that node. Similar non-redundancy of overlapping members in a ground structure can be observed also in, e.g., the compliance minimization of trusses under the self-weight loads [8, 34].
Difficulties in the robust truss topology optimization. a The ground structure and the nominal external load; b the optimal solution for the nominal load; c a solution obtained for a design-independent uncertainty model of the external load; d the robust optimal solution for the design-dependent uncertainty model and the ground structure without overlapping members (the objective value is \(3259.115\,\mathrm {J}\)); and e the robust optimal solution for the design-dependent uncertainty model and the ground structure with overlapping members (the objective value is \(2442.708\,\mathrm {J}\))
A key in this robust optimization is selecting the set of nodes which the optimal solution has. This is because the uncertainty in external loads depends on the set of existing nodes, in a manner that uncertain external forces are supposed to be applied to all the existing nodes. Moreover, a node lying on an existing member should be removed. The next example illustrates that exploring an optimal set of nodes in a heuristic manner is indeed difficult.
Consider the problem setting shown in Fig. 3a. Figure 3b shows the optimal solution of the nominal (i.e., not robust) optimization problem. A simple heuristic to predict a set of existing nodes in a robust optimal solution is to adopt the set of nodes that the nominal optimal solution has. Suppose that uncertain external forces are applied only to the five free nodes that the solution in Fig. 3b has. The optimal solution of this robust optimization problem is shown in Fig. 3c. This solution has two extra nodes that the solution in Fig. 3b does not have. Therefore, the solution in Fig. 3c assumes that external forces are not applied to these two nodes (in this sense, this solution is not truly robust). On the other hand, Fig. 3d shows the optimal solution of the robust topology optimization with a ground structure which does not include overlapping members. It is observed that one of the nodes in Fig. 3c is missing in the solution in Fig. 3d. Furthermore, Fig. 3e shows the optimal solution of the robust topology optimization with a ground structure including overlapping members. It is observed that the three intermediate nodes in Fig. 3b are removed and the two chains are replaced by longer members. As a result, the objective value of the solution in Fig. 3d is more than 1.33 times larger than that of the solution in Fig. 3e. Thus, it is crucial to design an optimization process so as to allow vanishment of intermediate nodes on chains.
It is also possible that a node which is not lying on a chain vanishes as a result of robust optimization. Consider the problem setting in Fig. 4a. The optimal solution of the nominal optimization problem is shown in Fig. 4b. If we suppose that uncertain external forces are applied to the eight free nodes in Fig. 4b, then the solution in Fig. 4c becomes optimal. Unlike the example in Fig. 3c, uncertain external forces are supposed to be applied to all the nodes that the solution in Fig. 4c has. In this sense, the solution in Fig. 4c is a local optimal solution of the robust topology optimization. In contrast, the global optimal solution of the robust topology optimization is shown in Fig. 4d.Footnote 8 It is observed that three nodes in Fig. 4c are missing in Fig. 4d. The objective value of the solution in Fig. 4c is more than 1.25 times larger than that of the solution in Fig. 4d. Thus, it is crucial to design an optimization algorithm that can deal with the design-dependent uncertainty model of the external load.
A node which is not on a chain can also vanish as a result of the robust topology optimization. a The ground structure and the nominal external load; b the optimal solution for the nominal load; c the robust solution obtained for a design-independent uncertainty model of the external load (the objective value is \(13934.896\,\mathrm {J}\)); d the robust optimal solution for the design-dependent uncertainty model (the objective value is \(11093.750\,\mathrm {J}\))
In Sects. 4 and 5, we propose a formulation and an algorithm for overcoming the difficulties discussed in this section.
3 Algorithmic framework
As preliminaries, Sect. 3.1 briefly introduces the notion of DC programming and the concave–convex procedure for solving it. In Sect. 3.2, we introduce the optimization problem that we consider in this paper, and present an extension of the concave–convex procedure.
3.1 Fundamentals: DC programming and concave–convex procedure
Let \(f_{i}\), \(g_{i} : \mathbb {R}^{n} \rightarrow \mathbb {R}\) \((i=0,1,\dots ,m)\) be convex. The optimization problem having the following form is called a DC programming problem:
For simplicity, we assume that \(g_{0}\), \(g_{1},\dots ,g_{m}\) are differentiable.
The concave–convex procedure is known as a heuristic for finding a local optimal solution of problem (1). Let \(\varvec{x}^{(k)} \in \mathbb {R}^{n}\) denote the incumbent value of \(\varvec{x}\) at the kth iteration. Define \(\hat{g}_{i}(\,\cdot \, ; \varvec{x}^{(k)}) : \mathbb {R}^{n} \rightarrow \mathbb {R}\) \((i=0,1,\dots ,m)\) by
The concave–convex procedure updates the solution by letting \(\varvec{x}^{(k+1)}\) be the optimal solution of the following optimization problem:
It is worth noting that this subproblem is convex.
For the sequence, \(\{ \varvec{x}^{(k)} \}\), generated by the concave–convex procedure, it is known that the objective value of (1), i.e., \(\{ f_{0}(\varvec{x}^{(k)}) - g_{0}(\varvec{x}^{(k)}) \}\), converges. However, \(\{ \varvec{x}^{(k)} \}\) does not necessarily converges to a local optimal solution; see, e.g., Lipp and Boyd [39, Sect. 1.3]. Applications of the concave–convex procedure include transductive support vector machines (transductive SVMs) [14, 18], feature selection in SVMs [44], sparse learning [19], etc.
The concave–convex procedure can be considered as a version of DCA (difference of convex algorithm) [45, 47]; see Lipp and Boyd [39] and Sriperumbudur and Lanckriet [50] for accounts of this fact. For DCA and its applications we direct the reader to Le Thi and Pham Dinh [37] and Pham Dinh and Le Thi [46]; an application of DCA in structural engineering can be found in Stavroulakis and Polyakova [52]. As shown in Sriperumbudur and Lanckriet [50], the concave–convex procedure can also be viewed as a variant of MM algorithms (majorization-minimization algorithms) [28, 36].Footnote 9 The MM algorithm is a generalization of the well-known EM algorithm (expectation-maximization algorithm) [15]. The MM algorithms have been frequently employed in machine learning and image processing as seen in, e.g, Hunter and Li [29], Hunter and Lange [27], Figueiredo et al. [17], Sriperumbudur et al. [51], and Sun et al. [54].
MMA (the method of moving asymptotes) [55, 56, 65], which is frequently used for continuum-based topology optimization [9], also solves a sequence of convex optimization approximations of the original problem. MMA approximates the objective function and the constraint functions by convex linear fractional functions by using the function values and gradients as well as some parameters controlling the vertical asymptotes of the generated functions. Also, sequential parametric convex approximation methods with application to truss optimization can be found in Beck et al. [4] and Ben-Tal et al. [6].
3.2 Heuristic for convex optimization with complementarity constraints
In this paper we attempt to solve problems having the following form:
Here, \(f : \mathbb {R}^{l} \times \mathbb {R}^{n} \times \mathbb {R}^{n} \rightarrow \mathbb {R}\) is convex, \(\varOmega \subseteq \mathbb {R}^{l} \times \mathbb {R}^{n} \times \mathbb {R}^{n}\) is closed and convex, and the optimization variables are \(\varvec{\xi } \in \mathbb {R}^{l}\), \(\varvec{y} \in \mathbb {R}^{n}\), and \(\varvec{z} \in \mathbb {R}^{n}\). Problem (4) is convex optimization with complementarity constraints.
Following the idea in Jara-Moroni et al. [30], we can reduce problem (4) to a DC programming problem as follows. Consider a differentiable function \(\phi : \mathbb {R}^{n} \times \mathbb {R}^{n} \rightarrow \mathbb {R}\) satisfying
The complementarity constraints, (4e), can be replaced by a penalization term as follows:
Here, \(\rho > 0\) is a penalty parameter. For sufficiently large \(\rho \), problem (5) is equivalent to problem (4). We next assume that \(\phi \) can be decomposed as
where \(\phi _{+}\) and \(\phi _{-}\) are convex. Then problem (5) is reduced to the following form:
This is a DC programming problem, because \(f(\varvec{\xi },\varvec{y},\varvec{z}) + \rho \phi _{+}(\varvec{y},\varvec{z})\) and \(\rho \phi _{-}(\varvec{y},\varvec{z})\) are convex. There exist several different choices for \(\phi \), \(\phi _{+}\), and \(\phi _{-}\) [30, 38]. In this paper we adopt
To solve problem (5), we apply the concave–convex procedure to problem (6) with gradually increasing the penalty parameter, \(\rho \). For point \((\varvec{y}^{(k)},\varvec{z}^{(k)}) \in \mathbb {R}^{n} \times \mathbb {R}^{n}\), define \(\hat{\phi }_{-}(\,\cdot \,; \varvec{y}^{(k)},\varvec{z}^{(k)}) : \mathbb {R}^{n} \times \mathbb {R}^{n} \rightarrow \mathbb {R}\) by
The proposed algorithm updates the solution by letting \((\varvec{\xi }^{(k+1)},\varvec{y}^{(k+1)},\varvec{z}^{(k+1)})\) be an optimal solution of the following convex optimization problem:
A reasonable stopping criterion is that the residual of the complementarity constraints is small enough, i.e.,
and the update of the incumbent solution is small enough, i.e.,
where \(\epsilon _{1}\), \(\epsilon _{2} > 0\) are thresholds. The algorithm is formally stated in Algorithm 1.Footnote 10.

Remark 1
Algorithm 1 is designed essentially based on the algorithm proposed by Lipp and Boyd [39] for solving problem (1). In their algorithm, the following subproblem is solved to update \(\varvec{x}^{(k)}\):
Thus, penalization terms for all the constraints are added to the objective function by using the \(\ell _{1}\)-exact penalty function. In contrast, in Algorithm 1 only the complementarity constraints are penalized, and the other constraints of the original optimization problem are satisfied at a solution of the subproblem. \(\square \)
4 Mixed-integer semidefinite programming formulation for robust truss topology optimization
In Sect. 4.1, we recall the existing MISDP formulation for robust truss topology optimization, without considering overlapping members in a ground structure. Section 4.2 presents treatment of overlapping members within the framework of MISDP.
4.1 Review of existing formulation
In this section we briefly review an MISDP formulation of the robust truss topology optimization under the load uncertainty [61]; see also Ben-Tal and Nemirovski [7].
Following the ground structure method, consider a truss consisting of candidate members connected by nodes. Let m and d denote the number of the members and the number of degrees of freedom of the nodal displacements,Footnote 11 respectively. We use \(x_{i}\) \((i=1,\dots ,m)\) to denote the member cross-sectional areas, which are design variables to be optimized. Throughout the paper, we assume small deformation and linear elasticity.
Let \(t_{i} \in \{ 0,1 \}\) be a variable that serves as an indicator of existence of member i such that \(t_{i}=1\) means that member i exists and \(t_{i}=0\) means that it vanishes. We use \(\overline{x} > 0\) and \(\underline{x} \in [0, \overline{x}]\) to denote the specified upper and lower bounds for the cross-sectional area of an existing member, i.e., \(x_{i}\) should satisfy \(x_{i} \in \{ 0 \} \cup [\underline{x}, \overline{x}]\). This constraint can be written by using \(t_{i}\) as
We next introduce \(s_{j} \in \{ 0,1 \}\) \((j=1,\dots ,d)\) to represent the existence of the jth degree of freedom of the nodal displacements. A node in a ground structure is removed if and only if all the members connected to the nodes vanish. Let \(s_{j}=1\) mean that the node having the jth degree of freedom exists, and \(s_{j}=0\) mean that it vanishes. We use \(I(j) \subseteq \{ 1,\dots ,m \}\) to denote the set of indices of the members connected to the node having the jth degree of freedom. Then \(s_{j}\) is related to \(t_{1},\dots ,t_{m}\) as follows:
Let \(K(\varvec{x}) \in \mathbb {R}^{d \times d}\) denote the stiffness matrix of a truss, which is a (matrix-valued) linear function of \(\varvec{x}\). For a given external load, denoted \(\varvec{p} \in \mathbb {R}^{d}\), the compliance of the truss is defined by
The conventional compliance minimization problem is formulated in variable \(\varvec{x}\) as follows:
Here, \(c_{i}\) is the undeformed length of member i, \(\varvec{c} = (c_{1},\dots ,c_{m})^{\top }\), and \(\overline{c} > 0\) is the specified upper bound for the structural volume.
The uncertainty model of the external load is defined as follows: Let \(\tilde{\varvec{p}} \in \mathbb {R}^{d}\) denote the nominal value (or the best estimate) of the external load. Define a constant matrix \(Q \in \mathbb {R}^{d \times d}\) by
where \(\varvec{q}_{1},\dots ,\varvec{q}_{d-1} \in \mathbb {R}^{d}\) are the orthonormal basis vectors of the orthogonal complement of \(\tilde{\varvec{p}}\), and \(\alpha > 0\) is a constant representing the level (or the magnitude) of uncertainty. Then the uncertainty set of the external load, i.e., the set of all possible realizations of the external load, is defined by
For example, suppose that \(\tilde{\varvec{p}}\) has only one nonzero entry. Then, without loss of generality we can assume \(\tilde{p}_{1} \not = 0\), and we have
Let \(J_{\mathrm {f}} \subseteq \{ 1,\dots ,d \}\) denote the set of indices of nonzero entries of \(\tilde{\varvec{p}}\), i.e.,
The nodes to which the nominal external load, \(\tilde{\varvec{p}}\), is applied should not be removed in the course of optimization. Therefore, we impose the following constraint:
In robust optimization, we attempt to find a truss design that minimizes the maximal compliance (i.e., the worst-case compliance) when the external load can take any value in \(P(\varvec{s})\). With reference to (14), (15), (17), (18), and (20), we can see that this optimization problem can be formulated as follows:
For \(\varvec{x} \in \mathbb {R}^{m}\) \((\varvec{x} \ge \varvec{0})\), \(\varvec{s} \in \{ 0,1 \}^{d}\), and \(w \in \mathbb {R}\), define \(W(\varvec{x},\varvec{s},w) \in \mathcal {S}^{d+1}\) by
It is shown in Ben-Tal and Nemirovski [7, Lemma 2.2] that \(w \in \mathbb {R}\) satisfies
if and only if
holds. Consequently, problem (21) is equivalently rewritten as follows:
Problem (23) is an MISDP problem. By relaxing the 0–1 constraints into linear inequality constraints, we obtain an SDP relaxation. Since SDP can be solved efficiently with a primal-dual interior-point method, we can find a global optimal solution of problem (23) with a branch-and-bound method [61].
4.2 Treatment of members lying on a line
As explained in Sect. 2, for the robust truss topology optimization it is necessary to incorporate overlapping members to a ground structure. Since the existence of overlapping members in a final truss design is not accepted, it is required to incorporate the constraints prohibiting the presence of overlapping members in a truss design. To the best of the author’s knowledge, such a consideration cannot be found in literature on robust truss topology optimization.
Recall that, for each \(j=1,\dots ,d\), \(s_{j}=1\) means that the node having the jth degree of freedom exists, and \(s_{j}=0\) means that it vanishes. Also, \(t_{i}=1\) means that member i exists and \(t_{i}=0\) means that it vanishes. Let \(L(j) \subseteq \{ 1,\dots ,m \}\) denote the set of indices of the members lying on the node having the jth degree of freedom. Figure 5 shows an example of ground structure with overlapping members. It has \(m=18\) members and \(d=12\) degrees of freedom of the nodal displacements. In this example, we have \(L(j)=\{ 16,18 \}\) and \(I(j)=\{ 1,4,13,14,17 \}\). If \(s_{j}=1\), then all the members in L(j) cannot exist, i.e., \(t_{i}=0\) \((\forall i \in L(J))\). Also, if there exists an \(i \in L(j)\) such that \(t_{i}=1\), then the corresponding node cannot exist, i.e., \(s_{j}=0\). These two conditions can be formulated as
In the following, we add (24) to problem (23).
It is worth noting that a truss design involving a chain is infeasible for the presented robust optimization problem, because it is unstable and cannot be in equilibrium with uncertain forces applied at an intermediate node of the chain. Therefore, a solution obtained by the proposed method does not involve a member that is longer than the maximum member length of the ground structure. This might be considered an advantage of the robust topology optimization, because in a conventional truss topology optimization an optimal solution may possibly have a long chain and special treatment, such as the local buckling constraints [23, 41], is necessary for avoiding presence of a too long member.
5 Simple heuristic for robust truss topology optimization
The MISDP approach presented in Sect. 4 is only applicable to small-scale problem instances. Alternatively, in this section we present a heuristic having small computational cost. In Sect. 5.1, we reformulate our robust truss topology optimization as SDPCC. A concave–convex procedure is then applied to this formulation in Sect. 5.2.
5.1 Formulation as semidefinite programming with complementarity constraints
In this section, we reformulate problem (23) with constraint (24) as SDPCC, which is well suited for applying the concave–convex procedure.
We begin with constraints (23d) and (23e), which describe the relation between \(s_{j}\) and \(\varvec{x}\). Let \(r_{j}\) \((j=1,\dots ,d)\) denote the sum of the cross-sectional areas of the members that are connected to the node having the jth degree of freedom, i.e.,
Observe that \(r_{j}>0\) implies \(s_{j}=1\), because at least one member connected to the corresponding node exists and, hence, the node should exist. Also, \(s_{j}=0\) implies that the corresponding node vanishes, and hence \(r_{j}=0\), i.e., all the members connected to the node should vanish. These two assertions can be written as
Namely, constraint (23d) can be replaced with (26). For notational simplicity, in the following we write (25) as
with a constant matrix \(R \in \mathbb {R}^{d \times m}\).
We next consider constraints (23e) and (24), which describe the relation between \(s_{j}\) and \(\varvec{x}\). Let \(v_{j}\) \((j=1,\dots ,d)\) denote the sum of the cross-sectional areas of the members that lying across the node with the jth degree of freedom, i.e.,
Observe that \(v_{j}>0\) implies \(s_{j}=0\), because at least one member lying across the corresponding node exists and, thence, the node should vanish. Also, \(s_{j}=1\) implies that the corresponding node exists, and hence all the members lying across the node should vanish, i.e., \(v_{j}=0\). These two assertions can be written as
Namely, constraint (24) can be replaced with (28), For notational simplicity, we write (27) as
by using a constant matrix \(V \in \mathbb {R}^{d \times m}\).
Finally, consider constraint (23e). For each \(i=1,\dots ,m\), we introduce a new variable \(z_{i} \in \mathbb {R}\) so that \(\underline{x}-z_{i}\) corresponds to the lower bound for the cross-sectional area of member i. If \(x_{i}>0\), then member i exists and the lower bound should be \(\underline{x}\), which means \(z_{i}=0\). Also, when the lower bound becomes smaller than \(\underline{x}\) (i.e., \(z_{i}>0\)), then member i should vanish (i.e., \(x_{i}=0\)), and hence we set \(z_{i}=\underline{x}\). These relations can be written as follows:
Consequently, constraints (23e) and (23h) can be replaced with (29), (30), and (31).
The upshot is that problem (23) incorporating constraint (24) is equivalently rewritten as follows:
Here, \(\varvec{x}\), \(\varvec{z}\), \(\varvec{s}\), \(\varvec{r}\), \(\varvec{v}\), and w are variables to be optimized. Observe that any feasible solution of problem (32) satisfies \(1-s_{j} \ge 0\), \(r_{j} \ge 0\), \(s_{j} \ge 0\), \(v_{j} \ge 0\), \(x_{i} \ge 0\), and \(z_{i} \ge 0\). Therefore, constraints (32j), (32k), and (32l) are complementarity constraints. Constraint (32b) is a linear matrix inequality constraint in terms of \(\varvec{x}\), \(\varvec{s}\), and w. Thus, problem (32) has the form of SDPCC.
Remark 2
Since the algorithm presented in this paper consists of sequential approximation, adding some linear inequalities may possibly limit the search space and enhance the convergence. In the following, we consider linear valid inequalities, which naturally stem from the complementarity constraints and can be handled effectively in the numerical solution. Suppose that two variables, \(\alpha \), \(\beta \in \mathbb {R}\), are subjected to the complementarity constraint and their upper bounds are given, i.e.,
where \(\bar{\alpha }\) and \(\bar{\beta }\) are positive constants. It is known that the inequality
serves as a valid constraint for (33), (34), and (35) [42, 63]. In the same manner, we can construct valid constraints for problem (32). Concerning (32j), observe that we obtain
from (32f) and (25), respectively. Therefore, the constraints
are valid for (32j). Similarly, inequalities
are valid constraints for (32k) and (32l), respectively. In the following, we add constraints (36), (37), and (38) to problem (32). \(\square \)
5.2 Penalty concave–convex procedure for robust truss topology optimization
Problem (32) has the form of problem (4) studied in Sect. 3.2. To see this, it is convenient to rewrite problem (32) as follows:
Here, F is defined by
which is a convex set. The complementarity constraints in (39c), (39d), and (39e) can be replaced with penalization terms added to the objective function as follows:
Here, \(\rho > 0\) is a sufficiently large penality parameter, and \(\phi \) has been defined by (7). Problem (40) has the same form as problem (5).
We are now in position to apply Algorithm 1 to problem (40). Algorithm 1 solves the subproblem in (11), which is explicitly written as follows:
Here, \(\phi _{+}\) and \(\hat{\phi }_{-}\) are defined by (8) and (10), respectively. Since the constant terms in the objective function can be neglected, problem (41) can be reduced to the following problem:
Problem (42) is a minimization problem of a convex quadratic function under a linear matrix inequality constraint. Hence, this problem can be recast as SDP. Thus, at each iteration of Algorithm 1 we solve an SDP problem.
As mentioned in Sect. 3.2, a reasonable stopping criterion is that (12) and (13) are satisfied. In practice, however, we might use a relaxed criterion, which may save some iterations before convergence. Specifically, we terminate the algorithm when either (12) or
is satisfied. Then, by using the obtained solution we can fix the set of existing members and the set of existing nodes. Fixing these sets means that one variable in all the complementarity constraints in problem (32) is fixed. Therefore, the problem now becomes SDP, which is to be solved as the post process. The solutions presented in Sect. 6 are obtained in this manner.
6 Numerical experiments
This section reports three numerical experiments.
The proposed algorithm was implemented in MATLAB ver. 9.0. At each iteration we solved an SDP problem in (42) by using CVX, a MATLAB package for specifying and solving convex optimization problems [20, 21]. SDPT3 ver. 4.0 [59] was used as a solver. Computation was carried out on a \(2.2\,\mathrm {GHz}\) Intel Core i5 processor with \(8\,\mathrm {GB}\) RAM. The Young modulus of the trusses in the following numerical examples is \(20\,\mathrm {GPa}\).
The initial point for Algorithm 1 is chosen as follows. We first solve problem (17) for the nominal external load \(\tilde{\varvec{p}}\), i.e., the compliance minimization without considering uncertainties,Footnote 12 and let \(\varvec{x}^{(0)}\) be the obtained optimal solution. The initial values for the other variables are given by \(\varvec{z}^{(0)}=\varvec{0}\), \(\varvec{s}^{(0)}=\varvec{1}/2\), \(\varvec{r}^{(0)}=R \varvec{x}^{(0)}\), and \(\varvec{v}^{(0)}=V \varvec{x}^{(0)}\). The parameters of Algorithm 1 are \(\rho _{0}=10^{-2}\), \(\rho _{\mathrm {max}}=10^{6}\), and \(\mu =1.5\). We terminate Algorithm 1 if either (12) or (43) is satisfied, where \(\epsilon _{1}=2m\times 10^{-2} \,\mathrm {mm}^{2}\) and \(\epsilon _{2}=10^{-2}\,\mathrm {mm}^{2}\). Then, as explained in Sect. 5.2, we fix one variable in all the complementarity constraints in problem (32), and solve the resulting SDP problem to obtain the final solution. The settings of the initial point and the parameters explained above were determined by preliminary numerical experiments. In Sect. 6.1, we consider three problem instances that could be solved with a global optimization method. Cantilever truss examples with two different loading conditions, which are frequently solved in structural optimization, are considered in Sects. 6.2 and 6.3.
6.1 Example (I): Comparison with global optimization
In this section, we consider the small-scale instances presented in Sect. 2. For comparison, the MISDP formulation, i.e., problem (23) with constraint (24), is solved with YALMIP [40]. YALMIP finds a global optimal solution of an MISDP problem with a branch-and-bound method, at each iteration of which an SDP problem is solved. We used YALMIP with the default setting, where SDP subproblems are solved with SeDuMi ver. 1.3 [48, 53].
Consider the problem settings in Figs. 2, 3, and 4. Table 1 lists the number of members (m), the number of degrees of freedom of displacements (d), and the upper bound for the structural volume (\(\overline{c}\)). In Figs. 2b and 3a, the nodes are aligned on a \(1\,\mathrm {m} \times 1\,\mathrm {m}\) grid. In Fig. 4a, we use a \(1\,\mathrm {m} \times 0.5\,\mathrm {m}\) grid. In Fig. 3a, the ground structure has all possible members connecting two nodes but are no longer than \(3\,\mathrm {m}\). The nominal external load, \(\tilde{\varvec{p}}\), is applied as shown in Figs. 2b, 3a and 4a. The uncertainty model of the external load is defined by using (19) with \(\tilde{p}_{1}=100\,\mathrm {kN}\), \(\alpha = 0.75 \tilde{p}_{1}\) for Figs. 2 and 3, and \(\alpha = 0.5\tilde{p}_{1}\) for Fig. 4. The lower and upper bounds for the member cross-sectional areas are \(\underline{x}=1\,\mathrm {mm^{2}}\) and \(\overline{x}=700\,\mathrm {mm^{2}}\), respectively. In Table 1, “rob. opt.” reports the optimal value, obtained by YALMIP, of the robust optimization problem. The obtained solutions are shown in Figs. 2c, 3e and 4d. For reference, the optimal solutions of the (not robust) compliance minimization with the nominal external load, \(\tilde{\varvec{p}}\), are shown in Figs. 1b, 3b and 4b.Footnote 13 The optimal values are listed in “nom. opt.” of Table 1.
It is remarkable that, for every problem instance, the solution obtained by the proposed algorithm coincides with the global optimal solution (obtained by YALMIP). Table 2 reports the computational costs of the two methods, where “#iter.” is the number of iterations, and “time” is the required computational time. Note that the computational cost of the proposed method does not include the ones for generation of an initial point and for the post-processing. It is also worth noting that the problem size of SDP solved at each iteration of the proposed method is larger than that of YALMIP, and hence the computational time per an iteration required by the proposed method is larger than that of YALMIP. For every instance, the number of SDP problems solved by the proposed method is smaller than that of YALMIP.
In the experiments in this section, it has been observed that the proposed method converges to a global optimal solution for a small-scale problem instance. In Sects. 6.2 and 6.3, we examine large-scale instances that cannot be solved with a global optimization method within realistic computational time.
6.2 Example (II)
Consider the ground structures shown in Fig. 6. The nodes are aligned on a \(1\,\mathrm {m} \times 1\,\mathrm {m}\) grid, and the number of the nodes is \((N_{X}+1)(N_{Y}+1)\). The leftmost nodes are pin-supported. The candidate members are defined as follows. We first generate all possible members such that any two nodes are connected by a member. Then we remove members that are longer than \(3\,\mathrm {m}\). It should be clear that the ground structure retains overlapping members.
As for the nominal external load, \(\tilde{\varvec{p}}\), a vertical force is applied to the bottom rightmost node as shown in Fig. 6. The uncertainty model of the external load is given as explained in (19), where \(\tilde{p}_{1}=100\,\mathrm {kN}\) and \(\alpha = 0.5 \tilde{p}_{1}\). The lower and upper bounds for the member cross-sectional areas are \(\underline{x}=50\,\mathrm {mm^{2}}\) and \(\overline{x}=700\,\mathrm {mm^{2}}\). The upper bound for the structural volume is \(\overline{c}=2N_{X}N_{Y} \times 10^{5}\,\mathrm {mm}^{3}\).
As for problem sizes, we consider six cases, \((N_{X},N_{Y})=(3,7)\), (4, 6), (5, 5), (6, 4), (7, 3), and (8, 2). Table 3 lists the number of members, the number of degrees of freedom of the nodal displacements, and the upper bound for the structural volume. Figure 7 collects the optimal solutions of the conventional (i.e., not robust) compliance minimization in (17) for the nominal external load, \(\tilde{\varvec{p}}\). For the robust optimization, the solutions obtained by the proposed method are shown in Fig. 8. It is observed in Fig. 8a that the three chains in Fig. 7a are replaced with longer single members and four intermediate nodes are removed. The length of the bottom horizontal chain in Fig. 7c is \(5\,\mathrm {m}\). This chain is replaced with two members in Fig. 8c, because the maximum member length in the ground structure is \(3\,\mathrm {m}\). Similar observation can be made also in Fig. 8d, e. The nominal optimal solution in Fig. 7f has many thin members as well as many nodes. In contrast, the robust solution in Fig. 8f has simple topology, which may be considered practically preferable. In all the solutions in Fig. 8, the longest member is not longer than the maximum member length in the ground structure, as explained in Sect. 4.1.
The computational results are listed in Table 4. Here, “obj.” reports the objective value of the solution obtained by the proposed method, and \(\tilde{w}\) is the compliance of this solution for the nominal external load, \(\tilde{\varvec{p}}\). The optimal value of problem (17) for \(\tilde{\varvec{p}}\) is listed as “nom. opt.” Therefore, \(\tilde{w}\) is no smaller than the value of “nom. opt.” It is observed in Table 4 that these two values are very close. Namely, in these examples, robustness can be achieved with compensation of only very small increase of the nominal compliance.
As explained in Sect. 2, one of difficulties of the robust truss topology optimization is that the uncertainty model of the external load depends on the existing nodes, i.e., on \(\varvec{s}\). For comparison, we fix \(\varvec{s}\) to obtain a robust solution. As a simple heuristic, we construct an estimate of \(\varvec{s}\), denoted \(\bar{\varvec{s}}\), from the existing nodes of a solution in Fig. 7. Then we solve the following robust optimization problem:
This problem can be recast as SDP. For simplicity, the lower bound constraints on the cross-sectional areas of the existing members are omitted. The obtained solutions are shown in Fig. 9. The optimal value is reported in “fixed \(\varvec{s}\)” of Table 4. It should be clear that, at each solution in Fig. 9, uncertain external forces are applied only to the nodes that the corresponding solution in Fig. 7 has. Nevertheless, the objective value of a solution in Fig. 9 is much larger than that of the corresponding solution in Fig. 8. In other words, the solution obtained by the proposed method has quite high quality.
6.3 Example (III)
Consider the problem setting shown in Fig. 10. Ground structures are generated in the manner explained in Sect. 6.2. The maximum length of the members in a ground structure is \(3\,\mathrm {m}\). The uncertainty model of the external load is defined by using (19) with \(\tilde{p}_{1}=100\,\mathrm {kN}\) and \(\alpha =0.75\tilde{p}_{1}\). The lower and upper bounds for the member cross-sectional areas are \(\underline{x}=50\,\mathrm {mm^{2}}\) and \(\overline{x}=500\,\mathrm {mm^{2}}\), respectively. The upper bound for the structural volume is \(\overline{c}=4N_{X}N_{Y} \times 10^{5}\,\mathrm {mm}^{3}\).
For problem instances with \((N_{X},N_{Y})=(5,2)\), \((6,2),\dots ,(9,2)\), Fig. 11 shows the optimal solutions of the compliance minimization for the nominal external load. For the robust optimization, the solutions obtained by the proposed method are collected in Fig. 12. The problem sizes are listed in Table 5. The computational results are listed in Table 6. It is observed in Fig. 12a, d that the intermediate nodes on chains in Fig. 11a, d are removed as a result of robust optimization. Although the nominal optimal solutions in Fig. 11b, c, e have very complicated forms, the robust solutions in Fig. 12b, c, e are simple and practically preferable. Thus, it is often that robustness against uncertain loads and the minimal cross-sectional area constraints for the existing members yield simple truss topology.
The solutions obtained for the instances with \((N_{X},N_{Y})=(5,4)\), \((6,4),\dots ,(9,4)\) are collected in Figs. 13 and 14. The robust optimal solution obtained by the proposed method has a form similar to the corresponding nominal optimal solution, but many chains in the nominal optimal solution are replaced with single members.
The solutions obtained for the instances with \((N_{X},N_{Y})=(5,6)\), \((6,6),\dots ,(9,6)\) are collected in Figs. 15 and 16. It is observed that the nominal optimal solutions in Fig. 15c, e have so many thin members. In contrast, the robust solutions in Fig. 16c, e have fewer members. The layout of thick members in Fig. 16b is different from that in Fig. 15b. Also, the layout of thick members in Fig. 16d is different from that in Fig. 15d.
It is observed in Table 6 that the proposed method converged mostly within 40 iterations. The computational time for the instance with about 600 members is about 10 min. Thus, the proposed method finds a reasonable feasible solution with relatively small computational cost.
7 Conclusions
In this paper, we have presented a new formulation and algorithm for robust truss topology optimization considering uncertainty in the external load. Specifically, combinatorial aspects of the problem have been dealt with in the framework of the complementarity constraints. As for the uncertainty model of the external load, we have supposed that uncertain external forces can be applied to all the nodes of a truss. This model depends on the set of existing nodes, and hence on the set of existing members, while the member cross-sectional areas are the design variables to be optimized. Thus, the robust optimization problem involves design-dependent constraints. Also, it has been explained that overlapping members should be incorporated to a ground structure. In the final truss design, however, presence of overlapping members is not allowed from a practical point of view. In this paper, the set of existing nodes, the selection among overlapping members, and the lower bound constraints for the cross-sectional areas of the existing members are treated by using the complementarity constraints.
In the conventional truss topology optimization, it is often that an optimal solution has a sequence of parallel consecutive members, called a chain. To stabilize a truss, a chain is replaced with a longer single member. Special consideration, such as the local buckling constraints, is needed to avoid presence of a too long member converted from a chain. In contrast, the solution obtained with the proposed method does not have a member which is longer than the maximum member length of the ground structure, because a truss design including a chain is infeasible for the presented robust optimization problem.
This paper has presented an SDPCC (semidefinite programming with complementarity constraints) formulation of a structural optimization problem. Then, its DC programming reformulation has been solved with a convex-concave procedure. This algorithm is a version of MM algorithms and EM algorithms, which are widely used in machine learning, image processing, etc. It has been shown through the numerical experiments that the proposed heuristic can converge to a high-quality solution within relatively small computational cost. The method can certainly handle complementarity constraints other than the ones presented in this paper. An example is a set of constraints that prohibits the presence of mutually crossing members in a truss design.
Notes
A truss is an assemblage of straight bars (called members) connected by pin-joints (called nodes) that do not transfer moment. See Sect. 2 for some concrete examples.
The compliance of a truss, formally defined by (16), is equivalent to the twice strain energy of the truss at the equilibrium state under the prescribed boundary conditions (as far as the prescribed displacements are zeros [35]). It can be regarded as a global measure of the displacements, and hence by minimizing the compliance the global stiffness of the truss is maximized.
The ground structure method is commonly used in truss topology optimization. It prepares an initial setting, called the ground structure, consisting of many members connected by nodes. The cross-sectional areas of the members are treated as design variables, while the locations of the nodes are specified. See Sect. 2 for more account.
With reference to concrete examples, we will thoroughly discuss this issue in Sect. 2.
A solution having a chain cannot be in equilibrium with uncertain loads applied at intermediate nodes of the chain. Therefore, the worst-case compliance of the solution is infinitely large.
In this example, overlapping longer members are not incorporated into the ground structure, because with overlapping members the global optimization method (YALMIP [40]) did not converge within realistic computational time.
In fact, \(-\hat{g}_{i}(\cdot \,; \varvec{x}^{(k)})\) is a majorization function of \(-g_{i}\).
Choice of an initial point in the numerical experiments is explained in Sect. 6
The degrees of freedom of a truss are the possible components of the nodal displacements that define the configuration of the truss.
Problem (17) is convex. Various reformulations are known in literature; see, e.g., Achtziger et al. [2] and Jarre et al. [31]. For example, replacing \(\mathop {\mathrm {diag}}\nolimits (\varvec{s})Q\) in (22) with \(\tilde{\varvec{p}}\), one can readily obtain SDP that minimizes w under constraint \( \begin{bmatrix} w&\tilde{\varvec{p}}^{\top } \\ \tilde{\varvec{p}}&K(\varvec{x}) \\ \end{bmatrix} \succeq 0 \), (17b), and (17c). This formulation was used in the numerical experiments. It should be clear that a ground structure with overlapping members is used for generating the initial point, \(\varvec{x}^{(0)}\).
References
Achtziger, W.: Local stability of trusses in the context of topology optimization. Part I: exact modelling. Struct. Optim. 17, 235–246 (1999)
Achtziger, W., Bendsøe, M.P., Ben-Tal, A., Zowe, J.: Equivalent displacement based formulations for maximum strength truss topology design. Impact Comput. Sci. Eng. 4, 315–345 (1992)
Anjos, M.F., Lasserre, J.B. (eds.): Handbook on Semidefinite. Conic and Polynomial Optimization. Springer, New York (2012)
Beck, A., Ben-Tal, A., Tetruashvili, L.: A sequential parametric convex approximation method with applications to nonconvex truss topology design problems. J. Global Optim. 47, 29–51 (2010)
Ben-Tal, A., El Ghaoui, L., Nemirovski, A.: Robust Optimization. Princeton University Press, Princeton (2009)
Ben-Tal, A., Jarre, F., Kočvara, M., Nemirovski, A., Zowe, J.: Optimal design of trusses under a nonconvex global buckling constraint. Optim. Eng. 1, 189–213 (2000)
Ben-Tal, A., Nemirovski, A.: Robust truss topology optimization via semidefinite programming. SIAM J. Optim. 7, 991–1016 (1997)
Bendsøe, M.P., Ben-Tal, A., Zowe, J.: Optimization methods for truss geometry and topology design. Struct. Optim. 7, 141–159 (1994)
Bendsøe, M.P., Sigmund, O.: Topology Optimization. Springer-Verlag, Berlin (2003)
Brittain, K., Silva, M., Tortorelli, D.A.: Minmax topology optimization. Struct. Multidiscip. Optim. 45, 657–668 (2012)
Calafiore, G.C., Dabbene, F.: Optimization under uncertainty with applications to design of truss structures. Struct. Multidiscip. Optim. 35, 189–200 (2008)
Cherkaev, E., Cherkaev, A.: Principal compliance and robust optimal design. J. Elast. 72, 71–98 (2003)
Cherkaev, E., Cherkaev, A.: Minimax optimization problem of structural design. Comput. Struct. 86, 1426–1435 (2008)
Collobert, R., Sinz, F., Weston, J., Bottou, L.: Large scale transductive SVMs. J. Mach. Learn. Res. 7, 1687–1712 (2006)
Dempster, A.P., Laird, N.M., Rubin, D.B.: Maximum likelihood from incomplete data via the EM algorithm. J. R. Stat. Soc. Ser. B (Methodological) 39, 1–38 (1977)
de Gournay, F., Allaire, G., Jouve, F.: Shape and topology optimization of the robust compliance via the level set method. ESAIM Control Optim. Calc. Var. 14, 43–70 (2008)
Figueiredo, M.A.T., Bioucas-Dias, J.M., Nowak, R.D.: Majorization-minimization algorithms for wavelet-based image restoration. IEEE Trans. Image Process. 16, 2980–2991 (2007)
Fung, G., Mangasarian, O.L.: Semi-superyised support vector machines for unlabeled data classification. Optim. Methods Softw. 15, 29–44 (2001)
Gotoh, J., Takeda, A., Tono, K.: DC formulations and algorithms for sparse optimization problems. Math. Program. 169, 141–176 (2018)
Grant, M., Boyd, S.: Graph implementations for nonsmooth convex programs. In: Blondel, V., Boyd, S., Kimura, H. (eds.) Recent Advances in Learning and Control (A Tribute to M. Vidyasager), pp. 95–110. Springer, Vidyasagar (2008)
Grant, M., Boyd, S.: CVX: Matlab Software for Disciplined Convex Programming, Version 2.1 (2016 October). http://cvxr.com/cvx
Guo, X., Bai, W., Zhang, W., Gao, X.: Confidence structural robust design and optimization under stiffness and load uncertainties. Comput. Methods Appl. Mech. Eng. 198, 3378–3399 (2009)
Guo, X., Cheng, G.D., Olhoff, N.: Optimum design of truss topology under buckling constraints. Struct. Multidisc. Optim. 30, 169–180 (2005)
Guo, X., Du, J., Gao, X.: Confidence structural robust optimization by non-linear semidefinite programming-based single-level formulation. Int. J. Numer. Methods Eng. 86, 953–974 (2011)
Hashimoto, D., Kanno, Y.: A semidefinite programming approach to robust truss topology optimization under uncertainty in locations of nodes. Struct. Multidisc. Optim. 51, 439–461 (2015)
Holmberg, E., Thore, C.-J., Klarbring, A.: Worst-case topology optimization of self-weight loaded structures using semi-definite programming. Struct. Multidisc. Optim. 52, 915–928 (2015)
Hunter, D.R., Lange, K.: Quantile regression via an MM algorithm. J. Comput. Graphical Stat. 9, 60–77 (2000)
Hunter, D.R., Lange, K.: A tutorial on MM algorithms. Am. Stat. 58, 30–37 (2004)
Hunter, D.R., Li, R.: Variable selection using MM algorithms. Ann. Stat. 33, 1617–1642 (2005)
Jara-Moroni, F., Pang, J.-S., Wächter, A.: A study of the difference-of-convex approach for solving linear programs with complementarity constraints. Math. Program. 169, 221–254 (2018)
Jarre, F., Kočvara, M., Zowe, J.: Optimal truss design by interior-point methods. SIAM J. Optim. 8, 1084–1107 (1998)
Kanno, Y., Guo, X.: A mixed integer programming for robust truss topology optimization with stress constraints. Int. J. Numer. Methods Eng. 83, 1675–1699 (2010)
Kanno, Y., Takewaki, I.: Sequential semidefinite program for maximum robustness design of structures under load uncertainties. J. Optim. Theory Appl. 130, 265–287 (2006)
Kanno, Y., Yamada, H.: A note on truss topology optimization under self-weight load: mixed-integer second-order cone programming approach. Struct. Multidisc. Optim. 56, 221–226 (2017)
Klarbring, A., Strömberg, N.: A note on the min–max formulation of stiffness optimization including non-zero prescribed displacements. Struct. Multidisc. Optim. 12, 147–149 (2012)
Lange, K., Chi, E.C., Zhou, H.: A brief survey of modern optimization for statisticians. Int. Stat. Rev. 82, 46–70 (2014)
Le Thi, H.A., Pham Dinh, T.: The DC (difference of convex functions) programming and DCA revisited with DC models of real world nonconvex optimization problems. Ann. Oper. Res. 133, 23–46 (2005)
Le Thi, H.A., Pham Dinh, T.: On solving linear complementarity problems by DC programming and DCA. Comput. Optim. Appl. 50, 507–524 (2011)
Lipp, T., Boyd, S.: Variations and extension of the convex–concave procedure. Optim. Eng. 17, 263–287 (2016)
Löfberg, J.: YALMIP: A toolbox for modeling and optimization in MATLAB. In: 2004 IEEE International Conference on Computer Aided Control System Design, Taipei, pp. 284–289 (2004)
Mela, K.: Resolving issues with member buckling in truss topology optimization using a mixed variable approach. Struct. Multidisc. Optim. 50, 1037–1049 (2014)
Mitchell, J.E., Pang, J.-S., Yu, B.: Obtaining tighter relaxations of mathematical programs with complementarity constraints. In: Terlaky, T., Curtis, F.E. (eds.) Modeling and Optimization: Theory and Applications, pp. 1–23. Springer, Berlin (2012)
Muu, L.D., Dinh, Q.T., Le Thi, H.A., Tao, P.D.: A new decomposition algorithm for globally solving mathematical programs with affine equilibrium constraints. Acta Math. Vietnam. 37, 201–217 (2012)
Neumann, J., Schnörr, C., Steidl, G.: Combined SVM-based feature selection and classification. Mach. Learn. 61, 129–150 (2005)
Pham Dinh, T., Le Thi, H.A.: Convex analysis approach to D. C. programming: theory, algorithms and applications. Acta Math. Vietnam. 22, 289–355 (1997)
Pham Dinh, T., Le Thi, H.A.: Recent advances in DC programming and DCA. In: Nguyen, N.T., Le Thi, H.A. (eds.) Transactions on computational intelligence XIII. Springer-Verlag, Berlin (2014)
Pham Dinh, T., Le Thi, H.A.: A D.C. optimization algorithm for solving the trust-region subproblem. SIAM J. Optim. 8, 476–505 (1998)
Pólik, I.: Addendum to the SeDuMi User Guide: Version 1.1. Technical Report. Advanced Optimization Laboratory, McMaster University, Hamilton (2005). http://sedumi.ie.lehigh.edu/
Rozvany, G.I.N.: Difficulties in truss topology optimization with stress, local buckling and system stability constraints. Struct. Optim. 11, 213–217 (1996)
Sriperumbudur, B.K., Lanckriet, G.R.G.: On the convergence of the concave–convex procedure. Adv. Neural Inf. Process. Syst. 22, 1759–1767 (2009)
Sriperumbudur, B.K., Torres, D.A., Lanckriet, G.R.G.: A majorization-minimization approach to the sparse generalized eigenvalue problem. Mach. Learn. 85, 3–39 (2011)
Stavroulakis, G.E., Polyakova, L.N.: Nonsmooth and nonconvex structural analysis algorithms based on difference convex optimization techniques. Struct. Optim. 12, 167–176 (1996)
Sturm, J.F.: Using SeDuMi 1.02, a MATLAB toolbox for optimization over symmetric cones. Optim. Methods Softw. 11(12), 625–653 (1999)
Sun, Y., Babu, P., Palomar, D.P.: Majorization-minimization algorithms in signal processing, communications, and machine learning. IEEE Trans. Signal Process. 65, 794–816 (2017)
Svanberg, K.: The method of moving asymptotes—a new method for structural optimization. Int. J. Numer. Methods Eng. 24, 359–373 (1987)
Svanberg, K.: A class of globally convergent optimization method based on conservative convex separable approximations. SIAM J. Optim. 12, 555–573 (2002)
Takezawa, A., Nii, S., Kitamura, M., Kogiso, N.: Topology optimization for worst load conditions based on the eigenvalue analysis of an aggregated linear system. Comput. Methods Appl. Mech. Eng. 200, 2268–2281 (2011)
Thore, C.-J.: Multiplicity of the maximum eigenvalue in structural optimization problems. Struct. Multidisc. Optim. 53, 961–965 (2016)
Tütüncü, R.H., Toh, K.C., Todd, M.J.: Solving semidefinite-quadratic-linear programs using SDPT3. Math. Program. B95, 189–217 (2003)
Wolkowicz, H., Saigal, R., Vandenberghe, L. (eds.): Handbook on Semidefinite Programming: Theory. Algorithms and Applications. Kluwer Academic Publishers, Boston (2000)
Yonekura, K., Kanno, Y.: Global optimization of robust truss topology via mixed integer semidefinite programming. Optim. Eng. 11, 355–379 (2010)
You, S., Cheny, L., Liu, Y.: Convex–concave procedure for weighted sum-rate maximization in a MIMO interference network. In: 2014 IEEE Global Communications Conference, Austin, pp. 4060–4065 (2014)
Yu, B., Mitchell, J.E., Pang, J.-S.: Solving linear programs with complementarity constraints using branch-and-cut. Technical Report, Department of Mathematical Sciences, Rensselaer Polytechnic Institute, Troy, NY (2016 October)
Yuille, A., Rangarajan, A.: The concave–convex procedure. Neural Comput 15, 915–936 (2003)
Zillober, C.: Global convergence of a nonlinear programming method using convex approximations. Numer. Algorithms 27, 265–289 (2001)
Acknowledgements
This work is partially supported by JSPS KAKENHI 26420545 and 17K06633.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kanno, Y. Robust truss topology optimization via semidefinite programming with complementarity constraints: a difference-of-convex programming approach. Comput Optim Appl 71, 403–433 (2018). https://doi.org/10.1007/s10589-018-0013-3
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10589-018-0013-3