Abstract
Device to device (D2D) communication is one of the potentials to achieve the established standards for 5G. It represents a direct communication between two devices located in the vicinity of each other. In D2D communication, user’s data traffic can be offloaded without passing through the base transceiver system (BTS) and the core network. In order to initiate the D2D communication, device discovery is needed, and it is a major design issue for D2D communication. To achieve a potential discovery, there are some requirements such as energy efficient discovery capability, supporting a large number of devices and proximity discovery in the network assisted underlay D2D communication network. In this paper, device discovery processes and methods are presented and assessed using different approaches. In addition, a device discovery technique is proposed for single cell and a multi cell which capable to provide accurate and fast discovery with energy efficient and optimized routed path. D2D discovery techniques are evaluated, its main challenges are analyzed and potential solutions are also suggested.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
A Device-to-Device (D2D) communication permits two proximity devices to communicate directly to each other without passing through a Base Transceiver System (BTS). It’s plays a vital role in achieving the established standards of 5G communication due to its ability of resource sharing. D2D communication is promising to provide high data rate, assured quality of service, a huge user capacity and network congestion control [1]. An important point to be mention regarding D2D communication deployment is the spectrum re-utilization efficiently. Cellular spectrum and the unlicensed Industrial, Scientific, and Medical (ISM) spectrum are targeted choices for D2D communication. In terms of the ISM band, however, the spectrum is unlicensed which helps in deploying D2D communication without any alteration to present communication systems but several issues e.g., interference, quality of service and delay etc., are available and more are highlighted in [2].
The First concept of D2D communications was developed by Qualcomm’s Flash-LinQ [3]. This system consists of physical and medium access control layer network architecture for the implementation of underlay cellular network D2D communication. Flash-LinQ used the characteristics of distributed scheduling, orthogonal frequency division multiple access (OFDMA) and frequency division multiple access (FDMA) technologies. Based on these technologies, Flash-LinQ established an effectual method for synchronization, device discovery, and resource management for D2D communication in cellular networks. At the same time, 3rd Generation Partnership Project (3GPP) has been also working on D2D communication as a Proximity Services (Pro-Se) [4, 5]. Pro-Se has been discussed by many researchers and its feasibility has been made by long term evolution (LTE) [4, 6].
Currently, 3GPP released 12 promised that D2D need to accommodate to be suitable for public safety networks [7]. In addition, IEEE 802.X group has completed much work on proximate device discovery and D2D communication [8]. There are three modes of D2D communication that are in-band, out-band and D2D relay communication. For the case of in-band D2D communication, allocated cellular spectrum is shared between cellular and D2D users, while for out-band communication, an unlicensed spectrum, e.g., 2.4 GHz band, is utilised for communicating. For the case of D2D relay communication, in coverage device act as a relay to transfer the data to poor or out of coverage devices. The difference between D2D transmission and other transmission techniques are equated in Table 1 [5]. One of the primary issues for establishing a D2D communication is the device discovery. In device discovery, proximal devices search for their neighbour devices in order to establish the direct link. If they found proximal devices in certain distances, then a request for a communication link will be sent by the discovered devices [9]. Briefly overview and Flow diagram of D2D Communication with research flow is depicted in Fig. 1.
There is a need to explore device discovery for optimal resource allocation and mode selection under different scenarios and also need to explore maximum flow optimisation to achieve the maximum contents downloading without interference. Based on the previous presentation, there is a need to propose discovery methods that should be energy efficient and result in minimum interference to the multi cellular system. In addition, the proposed discovery techniques need to be efficient in dense area networks where a huge number of devices are available such as shopping malls, airports, stadiums etc. In this survey, an evaluation of the device discovery concept and techniques in the licensed spectrum is presented. The evaluation is based on efficient discovery, low latency rate and maximum system throughput in cellular networks. This work targets achieving less energy consumption, extensive communication range, up to 500 m, and the ability of discovery in high-density areas contain up to 1000 devices.
2 Classification of D2D communication
2.1 Out-Band D2D (OBD) Communication
D2D communication, which is used based on unlicensed spectrum is called Out-Band D2D (OBD) communication. The purpose of OBD communication is to meet the effective data rate in local transmissions such as personal area networks, public area networks, and industrial area networks. In public area networks, mostly ZigBee and Bluetooth are used, while in wireless local area network, Wi-Fi is used. The concept of using D2D communication for the case of unlicensed spectrum is illustrated in Fig. 2. The inspiration behind utilizing OBD communication is to dispose of the interference issue amongst D2D and cellular networks. The main challenge in OBD communication is to manage the interference between D2D users and cellular users. OBD may also experience the ill effects of the uncontrolled way of the unlicensed spectrum [10].
2.2 In-Band D2D (IBD) Communication
The need for regular communication between neighboring devices develops congestion, specifically, the capability of devices for game playing, public safety, and contents sharing and so on. Though, the traditional uplink and downlink transmission mode in a cellular system neglect to address this interest. Therefore, one of the technologies in 5G is IBD D2D communication, which can dramatically improve the data rate, manage the interference between cellular users (CU) and D2D users (DU) and so on, to meet the standards of 5G. The inspiration for picking IBD communication is typically the ability of control over licensed spectrum [11].
IBD communication is categorized into underlay and overlay D2D communication. In Underlay D2D communication, DU and CU share the similar wireless resources as shown in Fig. 3. On the contrary, in overlay D2D communication, dedicated resources are used for DU and CU [12]. IBD communication can enhance the spectrum efficiency of the cellular network by reusing the resources (based on underlay communication). That’s why to underlay D2D communication is the best solution to achieve the 5G requirements. Because of the physical nearness call proximity, and the potential reuse of resources, D2D communication can essentially expand system spectral efficiency and power efficiency.
A comparison is made between different short ranges communication technologies of Bluetooth, Zig-Bee, NFC, Wi-Fi Direct, and in-band D2D (LTE direct) in Table 1. Collectively, using of unlicensed spectrum for communication may bring low QoS. It is due to uncontrolled interferences. What’s more, the discovery process and making a connection in OBD as in Wi-Fi direct, Zig-Bee, NFC and Bluetooth is very complicated. It needs manually set up between the two devices. On the other hand, the previously mentioned issues are eliminated in IBD D2D communication in a more proficient manner.
2.3 Comparison Between IBD Underlay and Overlay
The majority of researchers have suggested the reuse of resources for D2D communication. Though IBD got a special attention for the researchers. There are several advantages of using IBD underlay communication. These are
-
1.
Increase the spectral efficiency using the spatial diversity in IBD underlay.
-
2.
BTS has a full control on the in-band spectrum. As a result, maintaining the QoS is much easier.
There may be some issues in IBD overlay communication:
-
1.
Due to dedicated cellular resources, it might be unexploited.
-
2.
Interference management is much difficult due to DU and CU.
-
3.
Power solution and interference solution is more complex than underlay
Therefore, from the above comparison underlay, IBD is more prevalent than overlay IBD.
3 D2D Implementation scenarios
Even though D2D communication is not developed yet [13], it is as of now being concentrated by the 3GPP standardization authority. 3GPP currently has decided that D2D communication in LTE focuses on public safety networks [4]. Besides that, Qualcomm has indicated interests in this innovation. They also assembled prototype model for D2D communication for IBD in a cellular system, which can be utilized as a scenario of various situations. For example, Qualcomm has been working on contents sharing, data offloading, and social networking. These applications support D2D communication as another exploration topic in the researcher community [3]. Possible D2D implementation scenarios for D2D communication are given below.
3.1 Device Relaying Operator Control
A device is positioned at the border of a cell or in a poor coverage zone, where maintaining QoS and battery life is difficult. In this case, in order to achieve a proper communication, devices in the coverage area can act as a relay [14]. Relaying is possible when D2D communication authentication will occur in BTS as shown in Fig. 4. BTS has partial full or partial control on relaying devices.
3.2 D2D Communication Operator Control
They devices require the communication between each other, and this is done based on communication through the BTS and then there is a need to communicate via BTS. In this case, they establish their link through BTS as shown in Fig. 5.
3.3 Device Relaying Device Control
The operator or BTS is not involved in a session setup between a sender and a receiver. Therefore, devices are self-responsible for communication between each other via a relay [15] as shown in Fig. 6.
3.4 D2D Communication Device Control
In this scheme, two devices directly communicate with each other without any BTS control as shown in Fig. 7. So, that, these devices communicate with each other in such a way to ensure, the minimum interference [16].
4 D2D Challenges
Current work can be categorized into two approaches, distributed D2D, and centralized D2D. In the centralized D2D approach a specific unit in the cellular system, for example, data network gateway and mobility management unit, distinguishes that it might be better for two DUs to setup a communication. This unit then updates the Evolved Node B (eNB) to demand measurement from the DUs to see if the D2D communication compromises higher throughput. Provided that this is true, the eNB chooses the two DUs that can connect in a D2D mode. In distributed D2D approach the DUs communicate their identities occasionally so that different DUs might know about its presence and chooses whether it should begin a D2D communication with it. This methodology does not require the contribution of the BTS. The distributed discovery approach is more adaptable and versatile than the centralized approach. Consequently, the operator cannot prohibit illegitimate users to broadcast or eaves-drop information to or from the D2D peers in the licensed band. A practical implementation D2D communication challenges in heterogeneous networks are mainly device discovery, inter cell interference, effective medium access control, and resource allocations [4]. Some more main parameters are depicted in Fig. 8.
4.1 D2D Discovery
D2D communication starts once devices in the vicinity of each other are discovered. Device discovery for in-band D2D communication is a major and first challenge that needs to be explored vitally [17, 18]. D2D discovery scenarios are restricted discovery, open discovery, information utilization from Public Land Mobile Network (PLMNs), discovery from roaming subscribers, and network base ProSe discovery [19].
4.2 Interference Management
Under IBD communication, DU and CU reuse the same uplink and downlink resources in the same cell. Based on that, it is critical to plan the D2D system in a way that DUs don’t interfere to CUs in the cellular system. Interference management is normally tended to improve the resource allocation and power allocation schemes.
4.3 Power Allocation
In the case of IBD, transmitted power ought to be appropriately regulated. In this way, the DU transmitter does not interfere with the CU in the cellular system. It is necessary to have less interference in order to get better signal to interference noise ratio (SINR).
4.4 Resource Allocation and Optimization
When proximate devices are discovered and they are intended to communicate, then the problem is, how they initiate communication and who provide the resources like channel allocation, control and power allocation in an optimized way [20].
4.5 Security and Privacy
Regardless of the remarkable advantages, new applications are exposing day by day for D2D communication. The security issues of these applications cannot be ignored in comparison to the conventional cellular network. These security threats are due to direct connected devices, relay structure, handover, roaming and privacy in social networks. In the event that the security issues are taken in regard, they may extremely frustrate fruitful deployment of D2D communication, practically speaking [21].
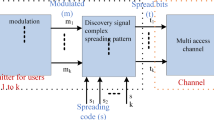
5 Device Discovery
A key part of the D2D communication is the device discovery of DUs, which is also known as peer discovery or proximity discovery [22]. The motivation behind the D2D discovery is that two devices could communicate with each other without using the operator resources [23]. The general device discovery can be divided into two phases. First is the initiation of the discovery process and second is the control of that process. D2D discovery can be started by the device or by the network. These two techniques are called, a priori and a posteriori discovery [24]. A priory discovery is used to share the explicit contents among the devices. Then, a posteriori D2D discovery could be utilized, for instance, by mobile phones that move to the region of each other during information exchange. General surveys on D2D communication and discovery can be seen in [6], [25] and [23], where an exposure for overall D2D communication and its technical details is also included.
Other classifications of device discovery are distributed and centralized as represented in Figs. 9 and 10 respectively. In distributed scheme devices searches their proximal by self and it causes interference. D2D discovery procedure can be controlled at different levels, where it can be fully or partially controlled by the network, and these use cases are called network assisted and autonomous D2D discovery, respectively. Network assisted D2D discovery has more advantages as described earlier in section II., where the approximate location of devices is approximately known, and DUs can communicate with each other within the same cell or between different cells. However, the main problem of network assisted D2D communication is the signaling overhead [23]. The benefit of autonomous D2D discovery is the small signaling overhead due to distributed networks. In any case, the discovery process itself could consume battery expressively as it is completely taken care by separate devices in the network.
In order to perform an autonomous D2D discovery, Gate Way (GW) node detects possible D2D candidates that want to be part of the communication process. Then a message contains information regarding mobility management, the eNB, and the interested DU is sent. After the D2D carrier is built up, D2D communication can be established. This proposed D2D discovery has substantial signaling overhead. Another D2D discovery method called search and listen is proposed in [26]. In this method at a particular discovery time, many DUs perform discovery procedure using a discovery message. To stay away from interference among them, the DUs go through three phases, (1) search or listen to phase, (2) discovery interval and (3) discovery channel. The outcomes show that the proposed system can enlarge the quantity of discovered devices within the discovery period. Using provisional identity, a signature-based D2D discovery method is proposed in [7]. The research presents how the discovery signal plans the utilization of physical resources and how to keep away from the collision in the network.
A completely distributed device discovery for Orthogonal Frequency Division Multiplexing (OFDM) based network utilizing time division multiplexing (TDM) system is projected in [27]. Discovery time slots are assigned to the radio resources, and the discovery signal can be sent or received during the specific discovery time. This discovery time allows devices to show their presence continuously and discover other devices in a distributed fashion. Another autonomous device discovery method is proposed which is based on routing protocol as stochastic, Bio inspired and hieratical [28]. The proposed pattern is modified based on packets flooding for device discovery. These packets incorporate channel number, power utilized for transmission and interference power which is calculated by the transmitter. Subsequently, using the packet information, the receiver can figure out the SINR and path loss of the transmitted data. These figured out values are transferred to the transmitter so that it can adjust the transmission power. Therefore, two nodes can make a D2D pair of bi-directional connection can be set up while the power requirement is set to minimize the interference between CUs and DUs. In [29], beacon signal based peer discovery is proposed, where a small portion of physical layer frames are used in order to avoid low discovery overhead. In this proposed method, neighboring devices discovery is based on the calculated SINR using received beacon signal.
A position discovery system based on high frequency is proposed in [30]. In this research, Cramer Rao Bound is used with centralized control to find the angle of arrival and time of arrival of statistics. However, this method is specific for narrow band channels, and the accuracy cannot be definite for proximity based D2D communication [31]. An overlapping communities based discovery procedure is proposed in [32]. In this method, the overlapped users in different communities are identified. After identification, the beacon signal discovery rates can be distinguished. Besides, the beacon discovery rates can be progressively adjusted by associating the status of other intra and inter community users, which can also improve energy efficiency and discovery rate.
An algorithm FST (Firefly Spanning Tree) for device discovery is proposed in [33]. The FST algorithm is proposed on the base of greedy and Firefly algorithms. In this method, signal strength is measured by the neighbor device and a tree with steady device signal strength is constructed. Regularly monitoring the uplink transmitted signal based discovery method is proposed in [34]. Nonetheless, the security of clients can be uncovered, and the social association between users was not considered in the mentioned discovery method. Energy efficient base discovery protocol e-discovery method is proposed in [35] and [36]. This scheme is the most popular for opportunistic communication in smart phones. In this scheme blue-tooth over Wi-Fi, is used as the underlying technology for device discovery. E-discovery is efficient but the operational distance between devices is low. Using an innovative functionality of Wi-Fi, direct base device discovery method is proposed in [37], and it presents an experimental assessment that depicts the performance in practical situations.
A self-governing ProSe server base device discovery scheme is proposed in [38]. The functionality of this server is to perform ProSe task and application server. ProSe assisted discovery need a high-level design for the direct discovery process. A social aware based peer discovery method is proposed in [39]. In this scheme, the author took the concept from ad-hoc peer discovery using social networking features. In this method, users are divided into community groups according to the social information. Then the beacon signal will be transmitted on regular basis to each group. However, energy consumption is the main issue in this scheme, and it is due to the frequency of transmitted beacon signals. 3GPP has presented the LTE centered proximity services in issuance 12 and 13 to accomplish D2D communication. The primary focus of LTE was data offloading. For this, 3GPP introduced proximity services. Though, it can be comprehensive to several cases including a large number of devices to connect in ProSe to one another with the benefit of utilizing the LTE resources.
An energy efficient discovery mechanism is proposed in [40], where the device discovery process takes the benefit of proximity services explicitly where in DU triggers their D2D abilities. In this method, DU performs discovery process when there are high chances to discover other DUs in the same service area. This method is an energy saving procedure in discovering the devices. But the question is if the DUs are not in same service area then how energy efficiency is possible.
Radio channel values based device discovery process is proposed in [41]. In this scheme beacon signal is designed on the basis of the value of channel measurement and it will be adapted if the wireless channel is correlated. As a result, DUs can precisely find the closest peer with minimum energy consumption. But the problem with this method is if the channel is uncorrelated then how beacon signal can be designed? Based on applying the CUs as presence announcers in cellular networks, discovery method is proposed in [42]. In this proposed scheme, the CUs announce for attention, to establish a D2D link. Usually, announcers send their invitation for D2D communication at the dedicated channel. In this proposed method, power control mechanism is applied at downlink channel, which guarantees reliable underlay proximity discovery. This may create interference, and this problem is not discussed.
A link base device discovery method is proposed in [43]. This scheme is simple and can be performed by the devices. Although this discovery scheme gives guaranteed security, interference between different links still a problem. Device beaconing method based discovery and enabled services based scheme are proposed in [44]. It is a novel approach for interchanging data packets and enabling connection at the appropriate radio channel link. The author tries to make an energy efficient scenario at different device densities. Frequency Hopping Sequences (FHS) based discovery method is defined in [45]. The discovery process can be possible in ad-hoc and cellular networks through sending a reference signal by a party. Regardless of the known facts, the important difficulty of the device discovery is that when two devices need to peer, they should have coherency in frequency, time and space. Sending the synchronization pulses every time is energy and time-consuming. This problem can be solved using underlay network assisted device communication.
A discovery method in unlicensed spectrum based on joint discovery is proposed in [46], but the interference is the major problem in this method. From the above analyses, it is clear that D2D communication in the cellular network depends upon many network parameters in order to achieve an efficient discovery. The neighbor discovery execution can be enhanced by expanding the discovery frequency of the users. From the above literature survey, the following parameters must be considered for efficient discovery, and these are energy efficiency, interference aware discovery, fast discovery, and efficient discovery from high-density devices, discovery from multi cells and multi operators and efficient discovery when the device is out of coverage.
6 Possible Way of Discovery in Cellular Networks
The performance of D2D communication largely depends upon the neighbor device discovery process in the cellular networks. From the literature survey presented earlier in Section V, it is concluded that any device is discoverable in a cellular spectrum based on using one of the methods shown in Fig. 11.
6.1 Request-Based Discovery
In request-base discovery, a device transmits a discovery request in its vicinity and waits for the response of detected devices. When the device founds the response from the replied device, an agreement is made to make the connection. Bluetooth, IR, and Wi-Fi schemes also work on this phenomenon. This scheme is suitable for a small number of devices, and it is not efficient for a large number of devices.
6.2 Direct Discovery
In Direct discovery strategy, a device transmits a discovery signal to promote its nearness or eavesdrops for other devices. In this method, there is no need to the response from the individual requester.
6.3 Network-Assisted Discovery
In the network assisted discovery, a source device starts a demand to the network for communication with an objective device. A network assisted discovery process is proposed in [47]. The network generates D2D discovery signal and illuminates both source and destination devices. Along with network, allocates the resources to establish the link for related data. Source device sends the discovery signal and destination device distinguishes the signal on the up to date resources. This scheme has great discovery effectiveness, however, may likewise build the dependence on the network system and additional signaling overhead. Network base device discovery concept is also presented in Fig. 5.
6.4 Packet-Based Discovery
Generally, the reason for device discovery is to accomplish two objectives: location of the nearness of neighbor devices and the identification of located devices. Packet based discovery utilizes an encoded packet, that incorporates full, unique identification of the device. For instance, mobile identification number, MAC address or IP address and other information related to the device. The benefit of the packet based method is that full information identified associated with device discovery. This information can be acquired from the discovery signal without extra signaling. Nonetheless, the disadvantage is that the packet is big in size, and subsequently must be robustly channel coding is needed due to turbo codes or convolutional codes for better spectral efficiency. Furthermore, due to the packet size, this discovery scheme is not efficient because a device has to pay high channel complexity estimation and algorithms for decoding. The benefit of packet based discovery is that all the information in the packet is self-contained and has a minimum network dependence
6.5 Signature-Based Discovery
In the signature base device discovery, utilizing a signature includes the transmission of the special waveform on the physical layer. This physical layer waveform is used as a discovery signal and temporary mark of identification of the device throughout the discovery process. The information that can be incorporated into the signature is commonly a much smaller complex than packet based device discovery. The lack of signature-based discovery is that only the signature cannot carry full device information. On the other hand, the benefit of signature-based D2D discovery is its high discovery performance and good spectral efficiency due to less coding.
6.6 Hybrid
Hybrid discovery scheme, can be also an arrangement of a sequence of signature pulses and packets. These signature pulses act as part of a reference signal and packet decoding information. Any device attempts to interpret the packet first it has read the sequences pulses. Therefore this can save lot of device power
6.7 Beacon Base Discovery
Base station transmits one short pulse periodically that is called a beacon signal. Beacon signals convey the following information such as network types, timestamp, area identity, and channel information [18]. To discover the devices, the beacon signal is sent in per unit time in the specific area. A beacon table (also called a beacon kernel table) is created in the data base of transmitter or base station. Devices eavesdrop for a new beacon, where they check the active devices in the beacon kernel table and find near devices. The found devices initiate the negotiation using the base station to establish the link. For these devices, the base station acts as a gateway. Figure 12 shows if the user is out of subscribed area, then how the cellular system support to beacon signal to locate the device.
Figure 12 shows the device communication when a device is out of the subscribed area. The beacon base device discovery process is sequenced as follows:
-
1.
Beacon is sent, if the device is active then it will be registered in the active kernel table. If the found device request to connect with a new base station, then beacon table start to hand off.
-
2.
The device is located through user level processing in the closest base station.
-
3.
When a device is registered in a visiting base station, through user level processing visiting base station take the information from home base station for billing and services information.
-
4.
The home base station sends an authentication signal.
-
5.
After all processing, the visiting base station will be able to accept or reject. When a device is in any cell area, a beacon signal is generated with roaming service. The device registered to the nearest base station and start communication as shown in Fig. 12.
6.8 Summary
All above summarize discussion about device discovery; there are many schemes which are suggested by the researchers and they are incomplete and tradeoff between different parameters of device discovery. Following parameters must not be in a trade off during discovery such as fast discovery, energy efficiency, accurate discovery from dense devices, discovery, efficient discovery from multi cells and multi operators and discovery when devices are out of coverage. The foremost weakness of the current research is a deficiency of D2D mobility and additional accurate circumstances for upcoming mobile networks such as heterogeneous mobile and landline networks with densely installed small cells. From literature survey, we propose two robust schemes for discovery. One of proposed method is femto cell GPS base device discovery which will help full for above parameters and also discover the device when out of coverage using relay devices information. Second beacon base discovery, in which a beacon signal is designed for discovery using the measured channel value. It will efficient and will have minimum misdetection rate. When beacon will have designed, based on channel information it also will have minimum signaling overhead, minimum resources utilization and will improve the user discovery rate.
7 Future Work
In this survey, we elaborate approximate potential research guidelines and undeveloped complications in device discovery for D2D communications in licensed spectrum. In the following, we grade open difficulties founded on diverse research methodologies. Theoretically, mathematical solutions and optimization methods are very partial. The existing literature absolutely deficient for, device discovery, modes of communication choices method, interference management, and power control tools. The beacon signal analysis for devices discovery by means of methods such as bio inspired proximity discovery, genetic algorithms and swarm optimization can be also a stimulating problem solution. This can be more enhanced to afford, more efficient device discovery, accurate throughput, power efficiency, minimum delay in D2D communications of the underlay cellular networks. There is actual slight work to illuminate the essential architecture in demand to the provision of device discovery in D2D communications in the underlay cellular networks. It is stimulating to auxiliary consideration on the ability of the present centralized cellular network to maintain D2D communication such as device discovery, connection setup, network registration, intervention control, resources allocation, security. Likewise, software defined based networks design can also help for device discovery in D2D communication. Certainly, device discovery in D2D communication needs to be considered in the further difficult background of heterogeneous networks due to increasing market attention for the availability of numerous radio technologies installed on the mobile devices.
7.1 Application
A decade before, D2D communication was primarily suggested for relaying in the underlay cellular networks. Up to now, scholars suggested novel usage of D2D communications in the underlay cellular networks such as multicasting, cellular offloading and peer to peer communication. We trust that D2Dcommunication can have supplementary applications in the present world of telecommunication, for example, social networking, smart grid, vehicular networks and location-aware services.
7.2 Result Verification
Majority of the existing works is based on home grew simulations and numerical. Though these kinds of assessment method are appropriate for learning the potential gains. They are quiet at distant from the legitimacy due to simplified conventions. We rely on a performance assessment by means of the current network simulators such as NS3, OPNET, OMNET or an experimental assessment can help in enlightening together an actual presentation and new challenges like device discovery of D2D communications in the underlay cellular networks.
8 Conclusion
In this paper, we are providing a wide study of the existing literature on device discovery in D2D communications in underlay cellular networks. We classified the existing literature founded on the licensed band of D2D broadcast into two key groups, named as in-band D2D communication (IBD) and out-band D2D communication (OBD). The works beneath in-band D2D communication were further distributed into underlay communication and overlay communication. The key issue in underlay D2D communication is device discovery, power control mechanism, interference controlling between D2D users and cellular users. In Overlay D2D communication, interference is not a major issue because D2D users and cellular users do not overlap. Though, this method allocates dedicated resources to D2D users and cellular users and has a poor spectral efficiency than the underlay. In out-band D2D communication the interference level is uncontrollable. We have also deliberated the shortcomings and strong points of the existing literature on device discovery. We pointed out the deficiencies of existing mechanisms and proposed possible future research directions. Our survey presented that D2D communication in in-band underlay cellular networks is under developing and device discovery is the first important phase for the initiation of D2D communication. Along with the discovery, there are still several exposed complications such as interference, power control, and time.
References
Song, L., Cheng, X., Chen, M., Zhang, S., & Zhang, Y. (2016). Coordinated device-to-device local area networks: The approach of the China 973 project D2D-LAN. IEEE Network, 30, 92–99.
Agiwal, M., Roy, A., & Saxena, N. (2016). Next Generation 5G Wireless Networks: A Comprehensive Survey (in English). Ieee Communications Surveys and Tutorials., 18(3), 1617–1655.
Wu, X., Tavildar, S., Shakkottai, S., Richardson, T., Li, J., Laroia, R., et al. (2013). FlashLinQ: A synchronous distributed scheduler for peer-to-peer ad hoc networks. IEEE/ACM Transactions on Networking (TON), 21, 1215–1228.
Lin, X., Andrews, J. G., Ghosh, A., & Ratasuk, R. (2014). An overview of 3GPP device-to-device proximity services. IEEE Communications Magazine, 52, 40–48.
Feng, D., Lu, L., Yuan-Wu, Y., Li, G. Y., Li, S., & Feng, G. (2014). Device-to-device communications in cellular networks. IEEE Communications Magazine, 52, 49–55.
Doppler, K., Rinne, M., Wijting, C., Ribeiro, C. B., & Hugl, K. (2009). Device-to-device communication as an underlay to LTE-advanced networks. IEEE Communications Magazine, 47, 42–49.
Zou, K. J., Wang, M., Yang, K. W., Zhang, J., Sheng, W., Chen, Q., et al. (2014). Proximity discovery for device-to-device communications over a cellular network. IEEE Communications Magazine, 52, 98–107.
Lien, S.-Y., Chien, C.-C., Tseng, F.-M., & Ho, T.-C. (2016). 3GPP device-to-device communications for beyond 4G cellular networks. IEEE Communications Magazine, 54, 29–35.
Li, Y., Wang, Z., Jin, D., & Chen, S. (2014). Optimal mobile content downloading in device-to-device communication underlaying cellular networks. IEEE Transactions on Wireless Communications, 13, 3596–3608.
Das, C. B. (2015). A Study on Device To Device Communication in Wireless Mobile Network. International Journal of Modern Communication Technologies & Research, 3(3), 1–5.
Shen, Y., Jiang, C., Quek, T. Q., & Ren, Y. (2016). Device-to-device-assisted communications in cellular networks: An energy efficient approach in downlink video sharing scenario. IEEE Transactions on Wireless Communications, 15, 1575–1587.
Araniti, G., Raschellà, A., Orsino, A., Militano, L., & Condoluci, M. (2017). Device-to-device communications over 5G systems: Standardization, challenges and open issues. In 5G mobile communications (pp. 337–360). Springer.
Orange, J. S.-B., Armada, A. G., Evans, B., Galis, A., & Karl, H. (2016). White Paper for Research Beyond 5G (Final Edit), Networld (NW) 2020, version 1.0, pp. 1–43, Oct 2016.
Tehrani, M. N., Uysal, M., & Yanikomeroglu, H. (2014). Device-to-device communication in 5G cellular networks: Challenges, solutions, and future directions. IEEE Communications Magazine, 52, 86–92.
Tonk, V., Dwivedi, V., & Yadav, P. (2017). Coded-Cooperation based Multi-Relay Algorithm for Device-to-Device Communication in 5G Cellular Networks. Indian Journal of Science and Technology, 10(4).
Lei, L., Zhong, Z., Lin, C., & Shen, X. (2012). Operator controlled device-to-device communications in LTE-advanced networks. IEEE Wireless Communications, 19, 96.
Hayat, O., Ngah, R., & Zahedi, Y. (2017). Cooperative Device-to-Device Discovery Model for Multiuser and OFDMA Network Base Neighbour Discovery in In-Band 5G Cellular Networks (in English). Wireless Personal Communications, 97(3), 4681–4695.
Hayat, O., Ngah, R., & Zahedi, Y. (2018). Device discovery for D2D communication in in-band cellular networks using sphere decoder like (SDL) algorithm, (in English). Eurasip Journal on Wireless Communications and Networking, 2018(1), 74.
Peng, Y., Gao, Q., Sun, S., & Yan-Xiu, Z. (2013). Discovery of device-device proximity: Physical layer design for D2D discovery. In 2013 IEEE/CIC international conference on communications in China-workshops (CIC/ICCC).
Zhou, Z., Gao, C., & Xu C. (2016). Joint peer discovery and resource allocation for social-aware D2D communications: A matching approach. In 2016 IEEE international conference on communication systems (ICCS) (pp. 1–6).
Wang, M., & Yan, Z. (2017). A survey on security in D2D communications. Mobile Networks and Applications, 22(2), 195–208.
Gandotra, P., & Jha, R. K. (2016). Device-to-device communication in cellular networks: A survey. Journal of Network and Computer Applications, 71, 99–117.
Mach, P., Becvar, Z., & Vanek, T. (2015). In-band device-to-device communication in OFDMA cellular networks: A survey and challenges. IEEE Communications Surveys and Tutorials, 17, 1885–1922.
Mumtaz, S., Lundqvist, H., Huq, K. M. S., Rodriguez, J., & Radwan, A. (2014). Smart Direct-LTE communication: An energy saving perspective. Ad Hoc Networks, 13, 296–311.
Asadi, A., Wang, Q., & Mancuso, V. (2014). A survey on device-to-device communication in cellular networks. IEEE Communications Surveys and Tutorials, 16, 1801–1819.
Nguyen, P., Wijesinghe, P., Palipana, R., Lin, K., & Vasic D. (2014). Network-assisted device discovery for LTE-based D2D communication systems. In 2014 IEEE international conference on communications (ICC) (pp. 3160–3165).
Jung, S., & Chang, S. (2014). A discovery scheme for device-to-device communications in synchronous distributed networks. In 16th international conference on advanced communication technology (pp. 815–819).
Kaufman, B., Aazhang, B., & Lilleberg, J. (2009). Interference aware link discovery for device to device communication. In Forty-third Asilomar conference on, signals, systems and computers (pp. 297–301).
Sarret, M. G., Berardinelli, G., Mahmood, N. H., Soret, B., & Mogensen, P. (2016). Providing fast discovery in D2D communication with full duplex technology. In International workshop on multiple access communications (pp. 98–108).
Mallat, A., Louveaux, J., & Vandendorpe L. (2007). UWB based positioning in multipath channels: CRBs for AOA and for hybrid TOA-AOA based methods. In 2007 IEEE international conference on communications (pp. 5775–5780).
Gezici, S. (2008). A survey on wireless position estimation. Wireless Personal Communications, 44, 263–282.
Wang, R., Yang, H., Wang, H., & Wu, D. (2016). Social overlapping community-aware neighbor discovery for D2D communications. IEEE Wireless Communications, 23(4), 28–34.
Chao, S.-L., Lee, H.-Y., Chou, C.-C., & Wei, H.-Y. (2013). Bio-inspired proximity discovery and synchronization for D2D communications. IEEE Communications Letters, 17, 2300–2303.
Tang, H., Ding, Z., & Levy, B. C. (2014). Enabling D2D communications through neighbor discovery in LTE cellular networks. IEEE Transactions on Signal Processing, 62, 5157–5170.
Han, B., Li, J., & Srinivasan, A. (2015). On the energy efficiency of device discovery in mobile opportunistic networks: A systematic approach. IEEE Transactions on Mobile Computing, 14, 786–799.
Han, B., & Srinivasan A. (2012). eDiscovery: Energy efficient device discovery for mobile opportunistic communications. In 2012 20th IEEE international conference on network protocols (ICNP) (pp. 1–10).
Camps-Mur, D., Garcia-Saavedra, A., & Serrano, P. (2013). Device-to-device communications with Wi-Fi Direct: Overview and experimentation. IEEE Wireless Communications, 20, 96–104.
Sharmila, K., Mohan, V., Ramesh, C., & Munda, S. P. (2016). Proximity services based device-to-device framework design for direct discovery. In 2016 2nd international conference on advances in electrical, electronics, information, communication and bio-informatics (AEEICB) (pp. 499–502).
Zhang, B., Li, Y., Jin, D., Hui, P., & Han, Z. (2015). Social-aware peer discovery for D2D communications underlaying cellular networks. IEEE Transactions on Wireless Communications, 14, 2426–2439.
Prasad, A., Kunz, A., Velev, G., Samdanis, K., & Song, J. (2014). Energy-efficient D2D discovery for proximity services in 3GPP LTE-advanced networks: ProSe discovery mechanisms. IEEE Vehicular Technology Magazine, 9, 40–50.
Lee, W., Kim, J., & Choi, S. W. (2016). New D2D Peer Discovery Scheme Based on Spatial Correlation of Wireless Channel. IEEE Trans. Vehicular Technology, 65(12), 10120–10125.
Pratas, N. K., & Popovski, P. (2015). Network-assisted device-to-device (D2D) direct proximity discovery with underlay communication. In 2015 IEEE global communications conference (GLOBECOM) (pp. 1–6).
Bello, O., & Zeadally, S. (2016). Intelligent device-to-device communication in the internet of things. IEEE Systems Journal, 10(3), 1172–1182.
Doppler, K., Ribeiro, C. B., & Kneckt, J. (2011). Advances in D2D communications: Energy efficient service and device discovery radio. In 2011 2nd international conference on wireless communication, vehicular technology, information theory and aerospace & electronic systems technology (wireless VITAE) (pp. 1–6).
Fodor, G., Dahlman, E., Mildh, G., Parkvall, S., Reider, N., Miklós, G., et al. (2012). Design aspects of network assisted device-to-device communications. IEEE Communications Magazine, 50, 170–177.
Vigato, A., Vangelista, L., Measson, C., & Wu, X. (2011). Joint discovery in synchronous wireless networks. IEEE Transactions on Communications, 59, 2296–2305.
Yang, M. J., Lim, S. Y., Park, H. J., & Park, N. H. (2013). Solving the data overload: Device-to-device bearer control architecture for cellular data offloading. IEEE Vehicular Technology Magazine, 8, 31–39.
Gerasenko, S., Joshi, A., Rayaprolu, S., Ponnavaikko, K., & Agrawal, D. P. (2001). Beacon signals: What, why, how, and where? Computer, 34, 108–110.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hayat, O., Ngah, R. & Zahedi, Y. In-Band Device to Device (D2D) Communication and Device Discovery: A Survey. Wireless Pers Commun 106, 451–472 (2019). https://doi.org/10.1007/s11277-019-06173-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06173-9