Abstract
Device-to-device (D2D) communication in cellular networks is one of the emerging technologies for 5G communications. Initiating D2D communication device discovery is a vital research problem due to energy consumption, the need for fast discovery in dense areas and discovery in poor coverage areas. Many approaches are suggested for device discovery like Bio-inspired and Firefly proximity base discovery. Ellipsoid device discovery model is proposed for multi users and orthogonal frequency division multiple access (OFDMA) network, in which radio resources are divided into time slots and frequency divisions. In large device density areas, devices establish a local area network that can be a centralised or a distributed local area network. In this proposed model, devices which are located in poor coverage area can be discovered easily. An iterative algorithm with linear pre-processing is applied to find the position of devices that gives the ellipsoid solution of the device position. The probability of false alarm and probability of misdetection verify the proposed solution. Results show an enhancement in the system capacity, rate of detection and maximum distance discovery in comparison with the firefly proximity algorithm.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
For the establishment of device-to-device (D2D) communication in a 5G network, it is necessary for the network and the devices to discover the existence of neighbour devices which are qualified for D2D communication. There are two techniques for device discovery, Ad hoc network base, and network controlled base. In ad-hoc network base discovery, devices use the industrial scientific and medical (ISM) band, where interference between devices is uncontrollable. In network controlled base discovery, discovered devices operate in a licensed spectrum, and they are fully or partially controlled by the base transceiver system (BTS). In order to achieve an efficient device discovery, the neighbour devices, in time and space, should have a minimum energy and time consumption. If the two devices are adept and have too much information about each other, they just perform a random search which will result in low efficiency and low throughput. Normally neighbour discovery methods are affected due to the mobility decoration, where the devices have heterogeneous mobility. Therefore, accurate neighbour discovery is a big challenge.
There are many issues for establishing a D2D communication in cellular networks as 1. Modes of communication 2. Device discovery 3. Resources allocation, and 4. Interference management as depicted in Fig. 1. In terms of the modes of communication, there are cellular, dedicated and shared modes, where each of them has its own advantages and disadvantages [1]. But due to user capacity, shared mode is considered in this research. Moreover, three possible scenarios for D2D device discovery are available that are network assisted, direct device discovery and autonomous discovery. To avoidance of interference, network assisted discovery is considered.
For wireless synchronous network comprised of N devices that are homogeneously located on a predetermined plane, there is a problem of centralized network neighbour discovery where each device wants to discover maximum number of devices in its vicinity. Suppose there are K available radio resources and L allocated for device discovery purpose in the network. Each device can take one of the resources from L to send its device identity and can receive the identities of the remaining \(L - 1\) resources from other neighbour devices. All the devices broadcast their identity through coded transmission on a radio resource. In this scheme, a link level approach is adopted as \(N = c \times L\) to increase the average quantity of discovered devices where c is the degree of network density. In conventional, one device per resource would lead \(L - 1\) devices being discovered.
In this paper, a device discovery model is proposed for network assisted underlay D2D communication, where iterative decoding is proposed. Our proposed discovery method relies on multiple access scenarios, where numerous devices are jointly discovered resulting in overall device discovery performance. The suggested iterative decoding has many techniques such as successive interference cancellation (SIC), minimum mean square error (MMSE) and maximum likelihood (ML) with linear pre-processing. Pre-processor is an approach in which sub-optimal local optimisation algorithm is applied to the detection process in order to avoid the signalling overhead.
The rest of the paper is organised as follows: Sect. 2 presents, the device discovery modelling and related work. Section 3 offers, details of device discovery procedure for OFDMA system. Discovery model analysis and suppositions are presented in Sect. 4. Section 5 expresses the detail of iterative algorithms SIC and iterative detection and estimation. Section 6 offers the linear pre-processing for discovery and Sect. 7 presents the performance evaluation using the probability of misdetection and false alarm, while the paper is concluded in Sect. 8.
2 Device Discovery Modelling and Related Work
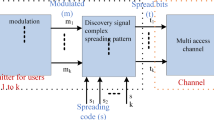
In general, communication model for device discovery is fully characterised and distinguished by two levels: 1. Device level discovery 2. Network level discovery. Joint device discovery can be implemented at a device and network level. Two main device discovery models of D2D communication in wireless networks are 1. Devices announce their presence simultaneously, 2. Devices searched by the BTS. In this research, the focus is on network level device discovery in which the BTS is involved, and the discovery model is illustrated in Fig. 2. The device discovery model is divided into two parts, D2D part, and BTS part. Discovery request is initiated by the device, if the required neighbour device is found directly by the device then a request is sent to the BTS for the direct D2D communication link. If a device is not directly discovered by the device, then it will report to the BTS for device discovery.
In general, discovery models are classified into two groups; probabilistic and deterministic [2,3,4,5]. The probabilistic approach as Birthday [3], improves the average discovery latency. The probabilistic approach can be applied on numerous application for its wonderful flexibility. While deterministic approach as Search Light [5] and Disco [4], do not perform well in term of discovery latency. This approach performs inadequately in average discovery latency and configuration flexibility is much poorer than a probabilistic algorithm. As for wireless sensor network in out-band communication worst cases, bound-ness is not necessary since nodes are substantially adjacent to each other, so they are not affected by discovery latency [6]. Furthermore, collision avoidance base multi-channel ALOHA with energy sensing (MCALOHA-ES) is proposed in [7]. This scheme is energy and time saving and resolve the contention. Some more device discovery procedures which are proposed by the researchers are compared in Table 1. A comparison is made in the table for different network and services types. In a cellular system, device discovery must have minimum discovery latency. Therefore, there is a need to focus on designing neighbour discovery with smaller discovery period, a higher discovery ratio and tractability in configuration as depicted in Fig. 3.
3 Device Discovery Procedure for OFDMA System
In this work, a scenario of an orthogonal frequency division multiple access (OFDMA) base LTE networks is assumed. The basic disparity between an OFDM and an OFDMA systems is that in the OFDM, the EU is apportioned on the time domain while in an OFDMA system the EU would be apportioned by both frequency and time [24]. This is valuable for LTE since it makes conceivable to exploit frequency reliance scheduling. In the OFDMA network based D2D communications, spatial radio resources are centrally assigned to an individual device by the BTS. In the radio resource sharing, the frequency is separated into sub-channels and time is separated into slots. The unit of resource allocation is radio resources, which involve one sub-channel per slot. That is why OFDMA makes grids of time and frequency for radio resources as shown in Fig. 4. In each discovery time, one round of discovery procedure is completed. \(T_{dis}\) is the regular discovery time and each time is indexed by numbers. At the beginning of every discovery time, there is a code swap period, and the complete length of the code swap is T. The code swap time is very small as compared to discovery time.
During the code swap time, entire radio resources are shared by the devices. Every discovery code message contains shortcode which describes the coded application name of the device. Time slots (T S ) and frequency sub-channel (F S ) are used during the code swap period. So, total radio resources during the code swap time is \(T_{s} \times F_{s}\). During every code swap time, a device chooses a radio resource of a random from \(T_{s} \times F_{s}\), the available radio resources and transmit a discovery message. During the period in which a particular radio resource is comprised, the device is in a broadcasting mode. Therefore, this device cannot accept any discovery message from any other device in this particular period. On the other hand, devices can accept discovery messages from other neighbouring devices when they are in receiving mode. It is noted that if two or more devices transmit discovery messages using the same radio resource, the discoverer device will not be able to organize the messages and collision will occur [25].
After the code swap period, the device can make an announcement through an application knowledge message about the comprehensive knowledge of application in the device. Each application knowledge message has the information of one application which consists of the application name “social network” and additional useful knowledge “ID of the social network”. There are no common or shared radio resources for transmitting the application information signal. Instead, application message signal is multiplexed with usual data transmission. Therefore, every device needs to request a dedicated radio resource from the BTS.
4 Discovery Model Analysis and Suppositions
Consider discrete time wireless synchronous OFDMA system with single subcarrier, flat fading and memoryless channel characteristics. The choice of sub carries is very important as it is constraint between BTS power and user supported as shown in MATLABFootnote 1 simulation result Fig. 5. Results show that more subcarriers lead to more power constraint and capacity. In the case of multiple-input-multiple-output (MIMO) system, the output is
where H is channel matrix of a flat fading MIMO system patterned by \(M_{R} \times M_{T}\).
Received vector is \({\text{y}}_{\text{i}} = \sum\nolimits_{{{\text{j}} = 1}}^{{{\text{M}}_{\text{T}} }} {{\text{h}}_{\text{ij}} *{\text{s}}_{\text{j}} + {\text{n}}_{\text{i}} , {\text{where }}\;{\text{i}} = 1,2 \ldots {\text{M}}_{\text{R}} }\) and \({\text{s}}_{\text{j}}\) transmitted vector \({\text{s}}_{\text{j}} = \left[ {{\text{s}}_{1} , {\text{s}}_{2} , \ldots ,{\text{s}}_{\text{j}} } \right]\). Channel state information (CSI) is available but, H is a random variable. The mutual information between input and output is \({\mathbf{I}}\left( {{\text{s}}:{\text{y}}} \right) = {\text{B log}}_{2} \left[ {{\mathbf{HR}}_{\text{s}} {\mathbf{H}}^{H} + {\mathbf{I}}_{{M_{R} }} } \right]\), where channel capacity depends upon the mutual information so, \(C = \mathop {max}\limits_{P\left( s \right)} \varvec{I}\left( {{\text{s}};{\text{y}}} \right) = \mathop {max}\limits_{P\left( s \right)} h\left( {\text{y}} \right) - h({\text{y}}|{\text{s}})\) and
5 Iterative Algorithms
5.1 Successive Interference Cancellation (SIC)
The device discovery performance can be enhanced by cancelling out the interference as
This subtraction procedure is repeated until all vectors have been discovered, and it is called Layer Peeling. Minimum mean square error with successive interference cancellation (MMSE-SIC) is used for iterative detection, but it has high computational complexity
where \({\mathbf{P}} = \left( {{\mathbf{HH}}^{\text{T}} + \sigma_{n}^{2} {\mathbf{I}}} \right)^{ - 1}\).
5.2 Iterative Detection and Estimation
The most joint methodology to dealing with channel uncertainty is iterative detection and channel estimation. Channel uncertainty is overlooked altogether in the starting and the data is perceived with a receiver designed using the uncertain channel. Then, the channel is re-estimated using detected data in the first step. Then the estimated channel is reused to design a receiver to perceive the data. This method is called local optimisation algorithm. After a couple of iterations, this algorithm converges to a local solution. Mathematically, the received signal is represented as \(\underbrace {{\left[ {{\text{x}}\left[ 1 \right]\; \ldots \;{\text{x}}\left[ {\text{N}} \right]} \right]}}_{\text{x}} = {\mathbf{H}}\underbrace {{\left[ {{\text{s}}\left[ 1 \right]\; \ldots \;{\text{s}}\left[ {\text{N}} \right]} \right]}}_{\text{s}} + \underbrace {{\left[ {{\text{n}}\left[ 1 \right]\; \ldots \;{\text{n}}\left[ {\text{N}} \right]} \right]}}_{\text{N}}\). Estimation of the channel is a linear least squares problem and an estimate of H can be found using linear least squares method. The estimate uses the detected data \({\hat{\text{S}}}\).
An equaliser designed per this channel estimate may then be used to form an estimate of the transmit signal for use in channel estimation in the next iteration. The received signal may be expressed as
where P is a matrix that defines an ellipsoid that models the channel uncertainty. The ellipsoid is the iterative solution to find out the position of devices.
6 Linear Pre-processing
It is well-defined by (11) that the second term \(\left( {\underbrace {{{\mathbf{PU}}{\text{s}}}}_{\text{interference}} + {\text{n}}} \right)\) establishes interference to the device discovery process and thus poor discovery results, if the second term is not blocked. Therefore, linear pre-processing is used to overwhelm the second term. This methodology is a sub-optimal local optimisation algorithm since it evaluates to overwhelm a term that is data dependent and could support the data detection process. Consider the condition where \({\text{M}}_{\text{R}} \ge {\text{M}}_{\text{T}} + {\text{M}}_{\text{P}}\). Under this postulation, it is potential to take a matrix W, with rank equal to \(M_{T}\) and null space of P. Where \({\mathbf{WP}} = 0\), when this pre-processing is applied at the received signal, interference term completely disappears as
From (11), linear pre-processor is to eradicate the terms generated by the channel uncertainty. Then SD or ML is applied to calculate effective channel G in order to distinguish the transmitted data and make sure that interference term does not reduce the recognition of the transmitted signal. W s are weights of linear pre-processor and when they are applied at the received signal x, the cost function J is
After minimising the cost function, weights will be represented as
where \({\mathbf{R}}_{\text{ys}} = E\left\{ {{\text{ys}}^{H} } \right\}\) and \({\mathbf{R}}_{\text{yy}} = E\left\{ {{\text{yy}}^{H} } \right\}\).
For wK, the cost function becomes
Iterative detection and channel estimation require a good initialization to perform well but it incorporates the uncertainty term into the detection process. Applying a linear pre-processor will suppress the interference term due to the channel uncertainty and provide a better estimate but does not incorporate the interference term into the detection process. As shown in Fig. 6, the smallest ellipse shows the maximum neighbour device which is qualified for D2D communication.
Perfect channel information is obligatory to accomplish efficient power allocation, interference management, and resource allocation. Cellular systems need information about the downlink channel from user terminals, while uplink channel information is readily calculated at the BTS. D2D communication involves channel gain information for D2D pairing, channel gain among D2D transmitter and cellular users, and the channel gain among cellular transmitter and D2D users. The simulated relation between power constraint and distance from BTS is shown in Fig. 7.
The conversation of such additional channel information can develop an insupportable overhead to the arrangement if the system desires instantaneous CSI feedback. Network based device discovery is prioritised by using the air interface instead of service level prioritising. Service level prioritising will be deliberated in future work for D2D communication. In the networks assisted D2D communication, one of the improvements for discovery is potential against the collisions and also discovery time can be efficiently controlled by the network. Furthermore, BTS has the information of all the devices centrally and resources allocation in an optimised way to save the resources for multi-hope and single hope D2D communication. Therefore, the discovery process can be fast-tracked through numerous methods.
Important parameters of device discovery signal must have the characteristics of power efficiency, interference tolerance, free from near and far effects, and minimal signalling overhead. How to implement this technique in multi-hope network device discovery is a vital study problem. Discovered devices must be efficiently coordinate frequency, time, power, space and device cooperate jointly with each other.
7 Performance Evaluation
Using probability of false alarm (P fa ) and misdetection (P md ), the performance of our proposed scheme is evaluated. Power consumption, number of users supported, and distance of the devices are also calculated in addition to calculating the SNR of each discovered device. Determination of coefficients k 1 and k 2 which are used to accomplish the target discovery along with d n can be achieved by detection theorem [26]. Discovery accuracy of neighbour terminal discovery in our proposed model using P fa and P md is shown in Fig. 8. Results show an improvement in comparison with the work achieved by
Advantages of proposed model’s results are shown Figs. 9, 10, and 11. In our proposed model, an improvement can be seen in the number of accommodated users and system capacity. Figure 9 presents the number of supported users relative to BTS transmitted power and terminal distances from the BTS. With respect to base station power, the maximum distance between the devices and a maximum number of the devices which can be accommodated for D2D users and cellular users. Figure 10 shows the SNR of each discovered devices. Each discovered device SNR is calculated and based on calculated SNR, it is decided that which devices are qualified for D2D communication. One of the advantages of D2D communication is increasing the system capacity dramatically. Figure 11, shows the enhancement in a capacity that has been improved based on the utilisation of our proposed scheme.
8 Conclusion
Neighbour device discovery in cellular networks is studied in this work, and results are found based on iterative detection with linear pre-processing that converge to an ellipsoid solution in OFDM single carrier sub-system, where linear pre-processing removes the interference term. The proposed solution has been verified in different scenarios such as system capacity, user supported at different subcarriers, maximum device distance, and SNR of each discovered device. Proposed solution correctness has been also verified by the probability of misdetection and false alarm. The cooperative iterative method helps to minimise the interference from the unwanted sources and channel uncertainty. Results show an improvement in system capacity and a large number of discovered devices in minimum time. It also shows the minimum misdetection ratio.
Notes
References
Mach, P., Becvar, Z., & Vanek, T. (2015). In-band device-to-device communication in OFDMA cellular networks: A survey and challenges. IEEE Communications Surveys & Tutorials, 17(4), 1885–1922.
Lien, S.-Y., Chien, C.-C., Tseng, F.-M., & Ho, T.-C. (2016). 3GPP device-to-device communications for BeyonD 4G cellular networks. IEEE Communications Magazine, 54(3), 29–35.
McGlynn, M. J., & Borbash, S. A. (2001) Birthday protocols for low energy deployment and flexible neighbor discovery in ad hoc wireless networks. In Proceedings of the 2nd ACM international symposium on Mobile ad hoc networking & computing (pp. 137–145). ACM.
Dutta, P., & Culler, D. (2008). Practical asynchronous neighbor discovery and rendezvous for mobile sensing applications. In Proceedings of the 6th ACM conference on embedded network sensor systems (pp. 71–84). ACM.
Bakht, M., & Kravets, R. (2011). SearchLight: Asynchronous neighbor discovery using systematic probing. ACM SIGMOBILE Mobile Computing and Communications Review, 14(4), 31–33.
Chen, L., Wang, Z., Cheng, H., Zhang, J., Cheng, Y., You, H., et al. (2015). Asynchronous probabilistic neighbour discovery algorithm in mobile low-duty-cycle WSNs. Electronics Letters, 51(13), 1031–1033.
Kaleem, Z., Li, Y., & Chang, K. (2016). Public safety users’ priority-based energy and time-efficient device discovery scheme with contention resolution for ProSe in third generation partnership project long-term evolution-advanced systems. IET Communications, 10(15), 1873–1883.
Baccelli, F., Khude, N., Laroia, R., Li, J., Richardson, T., Shakkottai, S., et al. (2012). On the design of device-to-device autonomous discovery. In 2012 Fourth international conference on communication systems and networks (COMSNETS 2012) (pp. 1–9). IEEE.
Vigato, A., Vangelista, L., Measson, C., & Wu, X. (2011). Joint discovery in synchronous wireless networks. IEEE Transactions on Communications, 59(8), 2296–2305.
Doppler, K., Ribeiro, C. B., & Kneckt, J. (2011). Advances in D2D communications: Energy efficient service and device discovery radio. In 2011 2nd international conference on wireless communication, vehicular technology, information theory and aerospace & electronic systems technology (Wireless VITAE) (pp. 1–6). IEEE.
Flathagen, J., & Øvsthus, K. (2008). Service discovery using OLSR and bloom filters. In 4th OLSR interop & workshop, Ottawa, Canada.
Huang, J., Wang, S., Cheng, X., & Bi, J. (2016). Big data routing in D2D communications with cognitive radio capability. IEEE Wireless Communications, 23(4), 45–51.
Zhang, B., Li, Y., Jin, D., & Han, Z. Network science approach for device discovery in mobile device-to-device communications.
Widhalm, P., Yang, Y., Ulm, M., Athavale, S., & González, M. C. (2015). Discovering urban activity patterns in cell phone data. Transportation, 42(4), 597–623.
Mustafa, H. A. U., Imran, M. A., Shakir, M. Z., Imran, A., & Tafazolli, R. (2015). Separation framework: An enabler for cooperative and D2D communication for future 5G networks. IEEE Communications Surveys & Tutorials, 18(1), 419–445.
Ashraf, Q. M., Habaebi, M. H., Islam, M. R., & Khan, S. (2016). Device discovery and configuration scheme for Internet of Things. In 2016 International conference on intelligent systems engineering (ICISE) (pp. 38–43). IEEE.
Le Sommer, N., & Sassi, S. B. (2010). Location-based service discovery and delivery in opportunistic networks. In 2010 Ninth international conference on networks (ICN) (pp. 179–184). IEEE.
Helgason, Ó. R., Yavuz, E. A., Kouyoumdjieva, S. T., Pajevic, L., & Karlsson, G. (2010). A mobile peer-to-peer system for opportunistic content-centric networking. In Proceedings of the second ACM SIGCOMM workshop on Networking, systems, and applications on mobile handhelds (pp. 21–26). ACM.
Bianchi, G., Loreti, P., & Trkulja, A. (2012). Let me grab your App: Preliminary proof-of-concept design of opportunistic content augmentation. In 2012 IEEE international conference on communications (ICC) (pp. 7034–7039). IEEE.
Cheung, K. W., So, H.-C., Ma, W.-K., & Chan, Y.-T. (2004). Least squares algorithms for time-of-arrival-based mobile location. IEEE Transactions on Signal Processing, 52(4), 1121–1130.
Cheng, S., Chang, C. K., & Zhang, L.-J. (2009). An efficient service discovery algorithm for counting bloom filter-based service registry. In IEEE international conference on web services, 2009. ICWS 2009 (pp. 157–164). IEEE.
Song, L., Cheng, X., Chen, M., Zhang, S., & Zhang, Y. (2016). Coordinated device-to-device local area networks: The approach of the China 973 project D2D-LAN. IEEE Network, 30(1), 92–99.
Bluetooth, S. (2007). Bluetooth core specification version 2.1+edr. Specification of the Bluetooth system.
Astely, D., Dahlman, E., Fodor, G., Parkvall, S., & Sachs, J. (2013). LTE release 12 and beyond [accepted from open call]. IEEE Communications Magazine, 51(7), 154–160.
Hong, J., Park, S., & Choi, S. (2014). Neighbor device-assisted beacon collision detection scheme for D2D discovery. In 2014 International conference on information and communication technology convergence (ICTC) (pp. 369–370). IEEE.
Lee, W., Kim, J., & Choi, S.-W. (2016). New D2D Peer discovery scheme based on spatial correlation of wireless channel.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hayat, O., Ngah, R. & Zahedi, Y. Cooperative Device-to-Device Discovery Model for Multiuser and OFDMA Network Base Neighbour Discovery in In-Band 5G Cellular Networks. Wireless Pers Commun 97, 4681–4695 (2017). https://doi.org/10.1007/s11277-017-4745-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4745-7