Abstract
Device-to-Device (D2D) communications have emerged as a promising technology for the next generation mobile communication networks and wireless systems (5G). As an underlay network of conventional cellular networks (LTE or LTE-Advanced), D2D communications have shown great potential in improving communication capability, erasing communication delay, reducing power dissipation, and fostering multifarious new applications and services. However, security in D2D communications, which is essential for the success of D2D services, has not yet been seriously studied in the literature. In this paper, we explore a security architecture for D2D communications under the framework of 3GPP LTE. We further investigate potential security threats and specify security requirements accordingly. Existing security solutions in D2D communications are seriously surveyed and evaluated based on the specified security architecture and requirements in order to figure out open research issues and motivate future research efforts.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Recent demands on wireless and mobile communications motivate exploring new technologies to improve network performance in terms of overall throughput, spectrum utilization, and energy consumption as a whole. Meanwhile, the appearance of new commercial services such as location-based social networking and content distribution services encourage us to explore new paradigms to meet user demands. Device-to-Device (D2D) communications have been proposed as one of the promising technologies for the next generation mobile communication networks and wireless systems (i.e., 5G) in order to motivate new mobile applications and services.
At the beginning, Device-to-Device (D2D) communications referred to a type of technology that enables devices to communicate directly with each other without the involvement of fixed networking infrastructures such as Access Points (APs), Base Stations (BSs) and so on. They were designed occurring on unlicensed Industrial, Scientific and Medical (ISM) spectrums and work in a pure autonomous means. Typical applications of original D2D communications rely on Bluetooth [1], WiFi-Direct [2] and Near Field Communications (NFC) [3]. In the past, mobile operators and vendors excluded D2D communications out of universal cellular network systems, e.g., Global System for Mobile Communications (GSM) [4], Universal Mobile Telecommunications System (UMTS) [5] and Long Term Evolution (LTE) [6] since D2D communications were only envisioned as a technology to reduce the cost of local service provision. The main reason that hinders the adoption of D2D communications by mobile operators and vendors lies in they cannot foresee appropriate use cases and business models to make profits from this type of communications. However, the viewpoint on D2D communications is changing recently. One typical argument is that the D2D communications can play as a controlled or constrained underlay network of LTE-Advanced Networks (LTE-A) working on the same spectrum as cellular networks [7, 8]. Meanwhile, in order to meet market demands on new services, such as context-aware applications, proximity services and Machine Type Communications (MTC), mobile operators are exploiting new usage scenarios and new business models based on D2D communications, e.g., pervasive social networking, urgent rescue and location-based services.
As a promising technology, D2D communications have drawn considerable attentions in academia, industry and also in standard organizations in recent years. In academia, D2D communications were regarded as an underlay of LTE-A from the beginning [7]. Many researchers have paid their attentions to D2D application scenarios, communication mode selection [8, 9], resource allocation [10], power control and interference control [11]. In industry, development on D2D communications is active. For example, Qualcomm developed a D2D communication sub-system in cellular networks, known as FlashLinQ [12, 13] to make communications among proximity devices possible. D2D communications are expected to complement traditional cellular based networking services and serve as a scalable platform for new types of applications, such as advertisement, content sharing, and secure mobile payments. At the same time, the standardization work on D2D communications in the Third Generation Partnership Project (3GPP) [14] is on-going. Different from the general term of D2D communications, 3GPP defined it as Proximity-Based Services (ProSe). Its technical reports [15, 16] studied the feasibility of ProSe in LTE-A and defined its system architecture and the functions of network entities with a number of use cases.
In spite of the significant benefits of D2D communications, new application scenarios expose D2D services into unique security threats. Comparing with conventional connections between devices and BSs, direct connections between proximity devices are vulnerable to security threats due to (1) direct wireless connection between devices; (2) a new relay transmission structure; (3) mobility, BS handover and roaming; and (4) privacy issues in social applications. If the security issues are not handled well, they may severely hinder successful deployment of D2D communications in practice.
However, the research on D2D communication security is still in its infancy. Neither the academia nor industrial standardization communities have studied the security of D2D communications seriously. In this paper, we conduct an extensive survey on security in D2D communications. Based on application scenarios and use cases, we explore D2D security architecture, analyze security threats, and then specify security requirements in D2D communications. By reviewing exiting work, we discuss open research issues and propose future research directions in order to highlight the significance of security studies in D2D communications. As we know, this is one of the first surveys about D2D communication security. Specifically, the contributions of this paper are summarized as below.
-
We introduce D2D communication application scenarios and use cases in a holistic way and discuss its system architecture. Moreover, we explore a security architecture of D2D communication system, investigate its security threats and specify security requirements accordingly.
-
We review the current literature about D2D security countermeasures by analyzing and comparing their advantages and disadvantages according to the security architecture and requirements.
-
We further figure out a number of open issues and propose future research directions to motivate D2D security research.
The rest of this paper is organized as follows. Section 2 briefly introduces application scenarios, use cases and system architecture of D2D communications. Particularly, we compare D2D communications with traditional Mobile Ad-Hoc Networks (MANETs) to highlight their specific characteristics. Section 3 explores D2D security architecture, investigates security threats and specifies security requirements accordingly. In Section 4, we comprehensively review the state-of-arts of security countermeasures in D2D communications by applying the security architecture and requirements as a measure to analyze their effectiveness and comprehensiveness. Furthermore, we discuss open research issues and propose future research directions in Section 5. Finally, a conclusion is presented in the last section.
2 Overview of D2D communications
2.1 Application scenarios and use cases
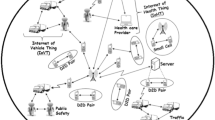
Various application scenarios and use cases have been proposed based on D2D communications. They are explored to play as an underlay of the cellular networks to improve network performance, offer a novel model to enrich network services, and support a national security and public safety network. We categorize them into three representative types according to the involvement of network facilities (e.g., cellular base stations or core networks) as illustrated in Fig. 1.
In-coverage
In this scenario, all user devices (e.g., UE1 and UE2) are located in the coverage of cellular networks. D2D communications between two user devices are fully controlled by the network infrastructure of operators, such as BS or core networks. The operator is in charge of user identity authentication, access control, connection establishment, resource allocation and security management in D2D communications. In this scenario, D2D links share the cellular licensed spectrum with normal cellular connections (UE-to-BS connections) under the coordination of the operator. Typical use cases of this scenario include but not limited to local traffic offloading from the core networks and operator controlled local data services, such as local content sharing, gaming and Machine-to-Machine (M2 M) communications.
Relay-coverage
When user devices (e.g., UE3 and UE4) are at the edge or out of BS coverage, they can communicate with the core network (BS) through relaying their communication data via other covered devices (e.g. UE3). In this “Relay-Coverage” scenario, D2D communications can greatly extend the coverage of cellular networks and improve network service quality at the edge of network coverage. In this case, just like the “In-Coverage” scenario, the operator is fully in charge of connection establishment, resource allocation and security management for both UE-to-BS connections and D2D (UE-to-UE) connections. The band used in the D2D link in this scenario is also the cellular licensed spectrum shared with conventional communications.
Out-of-coverage
Another representative application scenario of D2D communications occurs when the network coverage is absent. A typical use case of “Out-of-Coverage” is Emergence Communication Networks. For example, in an emergent situation where the cellular infrastructure has been partially or completely damaged due to natural disaster (e.g., earthquake or flood), D2D user devices (e.g. UE5, UE6 and UE7) can autonomously set up connections and start D2D communications with each other in proximity without the assistance of any operators. Studies in [17, 18] showed that the “Out-of-Coverage” D2D communication scenario can serve as a technical component for emergency communication services, e.g., public protection, disaster relief, national security and public safety communications. This D2D communication scenario looks similar to MANETs. However, there are still distinct differences between D2D communications and MANETs, as discussed in details in sub-section C.
2.2 System architecture
D2D communications are expected to be an underlay network of LTE-A. In order to introduce the D2D communications into existing LTE Networks and make them compatible with LTE-A, 3GPP proposed ProSe (i.e., D2D communications) system architecture under the framework of LTE Networks [16]. Figure 2 shows the integral system architecture of ProSe taking the roaming and inter-operator D2D communications into account.
In this system architecture, 3GPP defined two new functional entities: ProSe Function and ProSe App Server, and seven reference points (PC1 - PC7). The ProSe Function is a network entity that is suggested being deployed in LTE Evolved Packet Core (EPC). It is responsible for handling ProSe related operations, e.g., ProSe service registration and authorization, user discovery and communication management, security related function and so on. It relates to three reference points: PC4 towards Home Subscriber Server (HSS) in EPC, PC3 towards UE and PC2 towards another new functional entity: ProSe App Server. The ProSe App server is a third party application server that works based on the ProSe Function. It can connect and communicate with ProSe applications in the UEs (via reference point PC1). For supporting typical communications among devices, reference point PC5 is defined as the direct connection between two D2D UEs.
3GPP also defines a number of reference points related to roaming and inter-operator D2D communications. Refer to Fig. 2, when UE 3 roams to Operator A’s network, the ProSe Function of Operator A’s network should communicate with the ProSe Function of UE 3’s home network (Operator C) for user authentication, service authorization and other services via reference point PC7. Regarding inter-operator D2D communications, devices, e.g., UE 2 and UE 3, which subscribes to different operators can directly communicate with each other through the coordination of the ProSe Functions of their subscribed operators. Reference point PC 6 is defined for communications between different ProSe Functions belonging to different local operators.
2.3 D2D vs. MANET
D2D communications are similar to extensively researched MANETs [19] on many aspects, but with distinct differences as described below.
First, working spectrums are different. MANETs work autonomously on unlicensed spectrums. This makes spectrum control difficult, thus interference becomes a big issue in MANETs. However, D2D communications can work on licensed or unlicensed spectrums in different scenarios. In the In-Coverage scenario, D2D communications share licensed spectrums with traditional cellular links under the control of core networks. The spectrum resources can be efficiently consumed and the interference between links can be reduced at a very low level. But in the Out-of-Coverage scenario, the D2D communications can occur either on unlicensed spectrums like MANETs, or licensed spectrums in such a case as Public Safety Network in USA [20].
Second, control mode is obviously different. In MANETs, each node performs system operations autonomously in a distributed way, such as node discovery, route search, resource allocation, security management, and so on. But in D2D communications, these operations can be handled by core networks, or performed through the cooperation between core networks and D2D nodes. Comparing with MANETs, D2D devices can release many overhead-consuming operations to get longer power-on time. But in the Out-of-Coverage scenario, D2D nodes work autonomously without the support of network infrastructure, which works similar to MANETs.
Third, the routing patterns of these two kinds of communications are distinct. D2D communications mainly apply single hop communications, thus no need to consider the issue of multi-hop routing, which, however is a key but troublesome issue in MANETs. Notably, the Out-of-Coverage scenario in D2D communications holds a similarity to MANETs and faces the same challenges in multi-hop routing.
2.4 D2D vs. M2M and IoT
Machine-to-Machine (M2M) communications refer to the ways enabling automated applications that provide connectivity among machines or devices without any human intervention [21]. It is regarded as an underlay technology and an integral part of Internet of Things (IoT). IoT is defined as the next generation intelligent network that connects all things together.
But existing design and construction of M2M communications are based on traditional cellular networks (e.g., LTE or LTE-A). The communications between machines should be routed through core networks, such as Base Stations, M2M server and so on, even if a source and a destination are very close to each other. However, explosion of connected devices will greatly increase the burden of the core networks. D2D communications, as a new communication pattern, can be applied for M2M communications or IoT applications to improve communication performance, lower power consumption and reduce transmission delay. By adopting D2D communications for M2M communications in IoT, intelligent machines communicate directly with each other under the control of network infrastructures, which offloads the core network local traffic and leads to distinct improvement of networking performance.
3 Security requirements
Based on the system architecture described in Section 2. B and LTE system security levels, we explore a security architecture for D2D communications, and investigates security threats and requirements accordingly.
3.1 Security architecture
We propose a high-level security architecture for D2D communications based on the LTE networks. As shown in Fig. 3, there exist three different security domains in a D2D communication system.
Security Domain I: It refers to the security regarding 3GPP core networks EPC and the ProSe Functional entities, i.e., ProSe Function and ProSe App Server. This security domain can be divided into four security sub-domains: the sub-domain between the 3GPP EPC and the ProSe Function server that handles PC4 security; the sub-domain between the ProSe Function and the ProSe App Server that handles PC2 security; the sub-domain between two ProSe Functions of different operators that handles PC6 security; and the sub-domain between the ProSe Functions of a visiting network and a home network that handles PC7 security.
Security Domain II: It refers to the security with regard to D2D UEs and the ProSe Function. This security domain can be divided into two sub-domains: the sub-domain between D2D UEs and the ProSe Function server that handles PC3 security; the sub-domain between D2D UEs and the ProSe App Server that handles the security issues related to PC1.
Security Domain III: It refers to the security in terms of D2D UEs, which handles the security of PC5.
3.2 Security threats in D2D communications
New functional entities and reference points for implementing D2D communications introduce new security threats comparing with traditional cellular communication systems (e.g., LTE networks). Except for the traditional security issues in LTE networking, there are a number of D2D specific security threats that stem from the particularities of the D2D architecture and its security model. In what follows, we go through main security threats specifically relevant to D2D communications.
Impersonation attack
In traditional LTE networks, malicious users impersonating other identities to access the network services can be detected and addressed by core networks using EPS Authentication and Key Agreement (EPS AKA) [22], where the core network takes charge of the authentication of user identities and services authorization. However, direct communications between UEs make the process of user identity authentication complicated and vulnerable to user impersonation attacks. The conventional AKA schemes cannot handle the authentication among UEs in D2D communications, especially in the scenarios of Relay-Coverage and Out-of-Coverage. For example, in the Out-of-Coverage scenario, a malicious user can easily create multiple fake identities and impersonate legitimate users to communicate with other users due to the absence of the core network infrastructure.
Threats related to data transmission security
The communication data, which includes user data and control signaling, are subjected to eavesdropping, fabrication and manipulation during transmission among all system entities. In a LTE system, the data transmission among network entities that locate in security domain I can be protected by network domain security methods proposed by 3GPP in [23, 24], but the data transmitted between D2D UEs (in security domain III and between D2D UE and D2D functional entities (in security domain II) are under serious security threats, no matter on data confidentiality and integrity, or transmission non-repudiation.
Threats due to UE mobility
Mobile UEs are moving in nature. In a traditional cellular network system, a mobile UE can move from the coverage of one BS to another. UE mobility makes security management complicated. In D2D communications, this situation is more serious because UEs involved into D2D communications are moving across BS coverage and network coverage. Mobility brings additional challenges on the continuity of D2D communication security. On the other hand, the D2D connections may be interrupted due to UE mobility, thus authentication and secure channel establishment in D2D communications should be performed very efficiently.
Threats against privacy
User personal information could be disclosed in D2D communications. For instance, proximity discovery is an essential process in D2D communications before connection establishment. A UE discovers nearby UEs with BS assistance or autonomously. User private information, such as user ID, user location and user profile are normally needed for successfully fulfilling a D2D communication service. However, the above information may contain sensitive user data that may be utilized by malicious parties. Therefore, it becomes crucial to preserve user privacy in D2D communications.
3.3 Requirements of D2D communication security
In order to resist the potential threats mentioned above, we summarize the security requirements that a D2D communication system should satisfy.
Confidentiality and integrity (C\I)
Confidentiality and Integrity are two basic security properties a secure system should fulfill. In a D2D communication system, all data, no matter control signaling or user data, transmitted in any security domains should be prevented from malicious eavesdropping, modifying and leaking. Data confidentiality and integrity should be ensured. For example, in the Relay-Coverage scenario, a receiver can detect any accidental and malicious alteration to the data transmitted by a relay. All the security domains in D2D communications should support the confidentiality and integrity of data transmission, especially for control signaling. This is crucial to overcome the threats related to data transmission security.
Authentication (Au)
Authentication is the key to resist the impersonate attack. The system must be able to verify the eligibility of a UE to use D2D networking and related services (e.g., the ProSe Function and the ProSe App Server) through PC3 and PC1. Meanwhile, the authentication between the ProSe Function and the ProSe App Server should also be performed through PC2. On the other hand, D2D communications introduce a new direct communication link between UEs, therefore UEs must mutually authenticate with each other, which takes place in security domain III. Since the D2D communications contain relay and fully distributed communication scenarios, user authentication is different from common authentication in traditional cellular networks. New authentication schemes for D2D communications are expected, especially a uniform scheme that is applicable in all D2D communication scenarios and supports roaming and inter-operator authentication.
Fine-grained access control (FAC)
Fine-grained refers to the small granularity of an access policy, which could take into account a user’s personal profile and other factors. For example, the ProSe App Servers need control access of D2D devices to their services based on fine-grained policies in many cases. Moreover, FAC is often expected in group communications, which is a significant application scenario of D2D communications. Fine-grained data access control needs to be enforced for data delivery in D2D communications so that unauthorized users cannot obtain private information. It is an effective solution to overcome the threats against privacy and the threats related to data transmission security.
Privacy (Pr)
Many D2D use cases are related to social activities, e.g., social networking, gaming and medial content sharing. In these scenarios, users do not want to disclose personal and private information to unauthorized parties. Comparing with data confidentiality, user data privacy concerns more on D2D service functionalities in order to control data leakage to any other parties except a data owner. This requirement aims to overcome the threats against privacy in security domains involving mobile users, i.e., the security domain II and III.
Revocability (Re)
User privilege of a D2D service should be deprived in time if a user is detected as malicious, ineligible, harmful or invalid. This requirement helps overcoming the impersonate attack. Revocability should be paid special attention in group based D2D communications.
Availability and dependability (A\D)
Availability and dependability ensures survivability of D2D services to authorized users. The D2D services should be available even under Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attacks. Intermittent availability of D2D services may irritate user experiences thus hinder the adoption of D2D communications.
Non-repudiation (NR)
To be able to find and separate compromised devices, e.g., unwanted traffic sources in D2D communications, a message sender should not deny the authorship of a message. Non-repudiation can benefit to resist the impersonate attack and the threats related to data transmission security. Notably, this requirement is normally expected in some specific scenarios of D2D communications, e.g., mobile payment and compensation for resource provision in a communication relay.
4 Solutions of D2D security
In this section, we survey security schemes that have been developed for D2D communications since year 2000. We organize the section by reviewing existing related work, discussing whether they can satisfy the aforementioned requirements and analyzing whether they address related security issues based on the D2D security architecture. Table 1 compares comprehensiveness of existing work based on the security requirements. Table 2 compares existing work in terms of addressing related practical issues based on the D2D security architecture. We classify our review based on security design purposes: authentication and key management, secure routing, access control, physical layer security and other security issues.
4.1 Authentication and key management
Zhang et al. proposed a secure data sharing protocol for D2D communications in LTE-A [25]. They leveraged Diffle-Hellman Key Exchange (DHKE) to realize session key agreement between two D2D devices under the control of BS. The data transmission is protected by a symmetric encryption technique using a session key. Meanwhile, they took advantage of a Hash-based Message Authentication Code (HMAC) digital signature algorithm to guarantee identity authentication, data authority and integrity, as well as transmission non-repudiation. In order to encourage users to share their contents through D2D communications, BS keeps a status table to record the sharing times and malicious behaviors of users. This method helps regulating user behaviors and detecting malicious nodes. However, the applications of this protocol are specific and limited. For the purpose of D2D data sharing, a content providing server, which plays as the ProSe App Server in D2D communications, could be exposed to attacks and easily compromised. By evaluating this work with the security requirements, we find that this protocol did not consider or support FAC, and Re. Dependability and availability (A\D) were not well enhanced. It was not effective in the security domain I with regard to PC4 although it concerned other security domains. Roaming and inter-operator authentication was not discussed.
Sheng et al. established a shared secret key between two D2D devices for D2D communications based on DHKE [26]. In order to overcome Man-in-the-Middle Attacks (MITMA), the authors used a commitment scheme to realize mutual authentication between two devices. Nevertheless, the authentication process should be accomplished with a visual or verbal comparison in the end. This makes the scheme impractical in many cases. Furthermore, the scheme only dealt with two-device communications in the scenario of Out-of-Coverage. Thus, it cannot be applied into all three D2D application scenarios. Obviously, I, FAC, Pr, NR, Re and A\D were not supported by this scheme. It only supported C\I and Au in the D2D security domain III.
Goratti et al. proposed a security communication protocol to establish direct links among D2D devices [27]. The author first presented a D2D establishment protocol that broadcasts beacon to nearby devices to set up D2D communications. Then, they borrowed a random encryption key pre-distribution scheme from sensor networks [47] to help D2D devices selecting encryption keys from a common large pool of keys. The information of key exchange protocol was embedded into a sub-field of the beacon, thus this protocol addressed the compatibility issue with LTE specifications. C, Au and Re were supported by this protocol in the security domain III, while other security requirements were not considered.
Kwon et al. [28] proposed two protocols for D2D secure key establishment and authentication based on Bluetooth Pairing by using Ciphertext-Policy Attribute-Based Encryption (CP-ABE). Both the confidentiality of an initial secret key between D2D users and the fine-grain user access control are guaranteed. The authors proposed two schemes that can be applied into different application scenarios. In the first scheme, a D2D user can generate a session key using a shared initial key with arbitrary D2D users in a specific group. In the second scheme, a D2D user can set up an authenticated and secure link with a specific user in a group excluding other users. Message Integrity Code (MIC) is adopted to enhance message integrity. Benefiting from CP-ABE, the protocols achieve fine-grained user access control, mutual authentication, and also resist MITMA and replay attacks. However, the use of CP-ABE introduces a high computation cost and key management overhead. Meanwhile, Pr, Re and A/D are not well considered in the schemes. Referring to the security architecture, these two schemes only deal with the security in the security domain III and can be applied into the Out-of-Coverage scenario.
In [29], a secure D2D communication framework to perform authentication and secure communications between two D2D users was proposed. A security association is set up between two D2D users firstly using DHKE. Then, each user requests a certificate from their home core networks and uses the certificate to perform mutual authentication. Only C\I and Au were considered roughly in this work.
In [30], a key agreement protocol for D2D communications in LTE-A was proposed. It inherits a shared secret key between a UE and core networks to generate the session key for D2D communications, which makes it compatible with the existing LTE-A system. However, the session key of D2D communications is transmitted from the core networks to one UE, instead of deriving in the UE locally, which makes the session key under a leakage risk during transmission and thus could seriously impact the security of the D2D communications. This scheme did not take Au, FAC, NR, Re and A\D into account. Security protection means for the security domain I and PC1 was not discussed.
Alam et al. [31] proposed a key distribution scheme for D2D communications in LTE-A. It reuses the existing LTE-A security architecture as much as possible to reduce deployment costs. In the scheme, the core network is regarded as a fully trusted third party that controls the generation and distribution of the session key between two D2D communication UEs. In order to overcome the leakage risk of session key transmission between the core network and UEs, CN firstly XORs the keys of two D2D UEs and sends the XOR-ed key to each UE. Once receiving the XOR-ed key, each UE derives another key using its own key. After that, each UE gets a pair of session keys to protect the D2D communications. However, this XOR operation still cannot eliminate the risk of session key leakage. If one part of session key is disclosed, the other part can be computed easily through XOR operation. The safest way is no session key transmitted between CN and UEs or between UEs. In [32], a similar idea was proposed to establish a D2D communication key management framework, in which each D2D UE keeps a personal key and the core network combines their keys into a common key. Upon receiving the combined key, each D2D UE can derive the keys of other UEs. Then, they can securely and directly communicate with each other. However, the above schemes did not take other security issues (e.g, Au, FAC, Pr, Re, A\D and NR) into account except C\I.
An authentication protocol for D2D communications under LTE was proposed in [33]. It dealt with UE registration, key distribution, mutual authentication, and key update between UEs for D2D communications. This protocol depends on the core network to send a shared master key to UEs in order to derive a session key based on the shared master key. It is vulnerable if the master key leaks on the way of transmission. This scheme handles C\I, Au and also Re issues in the security domain III and PC3.
Massive solutions have been proposed to address authentication and key management issues in MANETs [48–51]. These solutions are heuristic for the research in D2D communication authentication and key management. The distribution and self-organization features of MANETs are similar to the Out-of-Coverage scenario of D2D communications. However, in most of use cases, such as Public Safety Networks, D2D UEs can be preloaded with secrets in device components or Subscriber Identity Module (SIM) cards, which makes D2D communication overhead lower and the process of authentication and key agreement more efficient compared with MANETs.
4.2 Secure routing
In the Out-of-Coverage scenario, routing from a source device to a destination device should be chosen securely. In order to protect relayed messages, a Secure Message Delivery (SMD) protocol was proposed to determine the lowest risk route to delivery messages in the D2D communications [34]. The decision made for the most secure route is not only based on the ability of collaborative detection of malicious messages for each route, but also takes energy costs and Quality-of-Service (QoS) into account. A device confusion matrix and a route confusion matrix were applied respectively to support Au and NR only in the security domain III. Route availability and dependability were supported through risk management and by considering QoS and energy costs.
In [35], the authors proposed a D2D group communication protocol by integrating routing control and group key agreement together. The proposed scheme controls routing through link and node state detection aiming to reduce dependency on network layer functions. Meanwhile, a Group Key Agreement (GKA) procedure is triggered to produce keys periodically or when networks are merged or separated, which can deal with revocation (Re). Moreover, key renewal latency is analyzed and evaluated to show the availability of this scheme. Certainly, C\I, Au, Re and A\D were supported in the security domain III.
MANET secure routing can be applied into the D2D scenario of Out-of-Coverage. There are a huge number of existing schemes in this research field [52–54]. Herein, we will not perform duplicated review on this. We would like to remark that D2D communications normally rely on one-hop or two-hop routing. The core networks can be applied to support device authentication and secure channel establishment, as well as other security functions. This fact makes security solutions of D2D communications distinct from those of MANETs.
4.3 Access control
In [36, 37], Huang et al. addressed the issue of access priority control for D2D communications in cellular networks. To mitigate the interference caused by D2D communications to cellular communications, the proposed access control model assigned multiple levels of priority for cellular and D2D communication access requests. Cellular communication requests are endowed with the strictly highest priority while D2D communication requests are assigned with distinct priorities according to their types. The authors innovatively applied Network Calculus Theory to evaluate the performance bounds of service rate, delay and backlog in the proposed solution. But this work did not pay attention to other security requirements except Au, FAC and A\D. Protection between D2D users is missed.
Yue et al. considered an access control issue under the framework of secrecy capacity in cellular communications [38]. Creatively, the authors introduced the D2D communications as an intentional interference into the cellular communications to prevent against eavesdroppers. With the prerequisite that the secrecy capacity of cellular communications is satisfactory, an optimal D2D pair can be selected to access a D2D network.
The above studies [36–38] are heuristic. They considered improving security from the perspective of cellular communications, rather than from D2D communications. In above studies, FAC was supported with regard to PC4 and PC1 in the security domain I and II, but not in the security domain III. Meanwhile, both studies considered Au and A\D.
Data access control schemes [55–58] explored in MANETs can provide valuable references for D2D communications. Group access control schemes proposed in [56, 58] may inspire secure data access in D2D group communications, no matter in “In-Coverage” or “Out-of-Coverage” scenarios. Furthermore, cache based data access schemes in MANETs [55, 57] provided new methods to improve data access efficiency in the D2D communications.
4.4 Physical layer security
Physical layer security generally refers to techniques that exploit wireless channel characteristics, modulation and coding, and multiple antennas in order to reduce the ability of eavesdroppers that detect and intercept sensitive communications [59–61]. A number of researches explore D2D security from the perspective of physical layer. Different from conventional security methods, physical layer security tries to establish security fundament by analyzing and applying physical characteristics of wireless channels between D2D devices.
Zhang et al. discussed the benefits of D2D communications for securing cellular communications as a whole [39]. They built a weighted bipartite graph model to analyze the security impact of D2D communications by utilizing Kuhn-Munkres (KM) algorithm. Experiment results show that the introduction of D2D communications can greatly improve the secrecy capacity of the whole cellular communication system.
Zhu et al. explored the security advantage of D2D communications in the physical layer [40]. They compared the Secrecy Outage Probability (SOP) of traditional cellular networks with D2D communications given a target secrecy rate when an eavesdropper exists. The experimental results show that, comparing with a traditional cellular model, a D2D model can gain lower SOP in almost all link Signal Noise Ratios (SNR). But the SOP of D2D is clearly inferior to that of the cellular model when sufficient antennas are equipped at an access point, which is an inherent weakness of mobile equipment. The work presented in [39, 40] attempted to improve the security of the whole cellular communication system by introducing D2D communications rather than the security of D2D communications.
Xi et al. proposed a novel Channel State Information (CSI) based on a key extraction protocol for D2D communications [41]. In this scheme, an adaptive quantizer generates a key bit stream from CSI measurements. In order to prevent key information from leakage, a universal hash function is applied to elaborately validate the consistence of key generation between two users. Furthermore, a fast key recombination method was proposed to dispose the inconsistent problem of a secret key.
Sun et al. introduced a cooperative key generation scheme [62] into D2D communications in order to setup shared secret keys between devices in physical layer [42]. To overcome the drawback of selfishness in an original cooperative key generation scheme, the authors innovatively modeled the cooperative key generation process as a coalitional game. In this game, all the devices involved in D2D and relay communications are strongly motivated to help other devices to establish secret keys, and thus gain benefits consequently.
The above two schemes in [41, 42] focused on supporting C\I in the security domain III. But how to merge or integrate them into other security domains requests additional investigation.
4.5 Other security issues
Recently, some studies explored user social relationships to improve the security of D2D communications. Zhang et al. proposed a traffic offloading mechanism based on D2D communications [43]. It takes social network characteristics extracted from an online social network model (OnSN) into decision of packet transmissions in an offline social network (OffSN) to enhance the performance, availability and dependability of the whole cellular communication system. Chen et al. developed a social-tie-based cooperation strategy for D2D communications by leveraging social trust and social reciprocity among human beings [44]. They built a two-layer system model that constitutes a physical graph and a social graph and designed three relay node selection algorithms based on social trust, social reciprocity or both according to the underlying system model. They also implemented the relay selection algorithms by proposing a network-assisted relay selection mechanism. This scheme can achieve significant performance improvement comparing with a traditional mobile system. However, above two studies only utilized user social properties to improve system performance and dependability, neither of them considered improving security using these social properties. Based on our previous work, trust relationship and reciprocity activities among human beings can be exploited to deal with security issues [63].
Another important security issue in D2D communications is how to overcome DoS and DDoS attacks. For example, in the Relay-Coverage scenario, malicious UEs can collude to attack a relay UE, disable its relay ability thus collapse the D2D communications. Hadiks et al. discussed impacts of the DoS and DDoS attacks in a D2D underlaying network at the first time [45]. They conducted experiments to launch DoS and DDoS attacks to a D2D server or a relay UE. The experiment results show that the relay UE is vulnerable to attacks and easily crashes due to limited computation capability. The D2D server can perform stably under the attacks. However, the upper link bandwidth of relay to server is exhausted by the attacks. In [46], Ma and Yan presented the design and implementation of an unwanted content control system in pervasive social networking with the support of D2D communications based on trust management in order to resist DoS and DDoS attacks. The above work investigated A/D issues of D2D communications.
5 Open research issues and future research directions
5.1 Open research issues
According to the above analysis and comparison from two aspects of view in Section 4, we find a number of open security issues in D2D communications.
First, a universal and comprehensive D2D security framework is missed in the literature. The existing work scattered into different security aspects of D2D and only dealt with some specific security issues in these aspects. As shown in Tables 1 and 2, none of existing work fulfilled all security requirements and resisted all security threats. No work was comprehensive, thus can solve all security issues in all D2D security domains. It lacks a holistic solution, e.g., a generic D2D security framework to resist all security threats and take all security requirements into account for supporting all D2D communication scenarios.
Second, secure D2D communications among inter-operator users and roaming users have not been studied. This application scenario is very valuable for mobile users with regard to communication costs, but more complicated than traditional cellular networking. New and effective security methods are expected. In traditional cellular communications, inter-operator communications can be divided into an inner-operator part and an inter-operator part. In the inner part, the communications can be protected locally without involving other operators. In the inter part, communications between operators can be secured by network entity protection schemes without considering UEs [23, 24]. However, in D2D communications, if two D2D UEs belong to different operators, a secure direct link between them can only be established collaboratively by involving both operators and both UEs. Moreover, user roaming could make security schemes more complicated. However, no research has been conducted to solve this issue, e.g., security channel establishment for inter-operator and roaming users to perform D2D communications.
Third, privacy preservation is still an open issue in D2D communications. Prior arts paid little attention to D2D privacy. So far, there exist few schemes about privacy preservation in D2D communications. However, many types of user personal information, such as user identities, locations, and behaviors are indispensably needed in the fulfillment of a D2D communication service. Given the sensitivity of these types of user information, it is critical to provide a D2D scheme that not only preserves user privacy, but also ensures the quality of D2D services. On the other hand, privacy preservation could introduce extra computation or communication overhead and cause data communication or processing delay. Thus, making a trade-off between user privacy and system performance becomes necessary in many practical situations.
Forth, the literature still lacks an effective solution to support group D2D communications in a secure way with the concern of group member privacy, revocation and non-repudiation.
Fifth, the possibility or applicability to merge a security solution into a generic D2D security framework has not yet been investigated in the literature. But this study is essential for evaluating a solution’s applicability and effectiveness. Furthermore, an integration method is needed to compose the advance of D2D security studies, especially for integrating security solutions that cross multiple security domains and reference points.
The security research in D2D communications is still in its infancy. A number of open security issues have not been studied. Many existing solutions need further exploration in order to evaluate their applicability and practicality. Therefore, comprehensive evaluation criteria are requested with regard to the investigation of a security scheme. In this paper, we propose a D2D security architecture and security requirements in order to use them as a measure to evaluate existing and future work.
5.2 Future research trends
All above open issues motivate future research. We further suggest a number of promising research directions about D2D communication security based on the literature review as follows.
-
(1)
Uniform and LTE-compatible key management and authentication schemes for D2D communications are required. New application scenarios and use cases call for novel authentication and key management schemes. Although the literature has investigated the key management and authentication issues, most of existing schemes can only deal with some specific application scenarios. For instance, the schemes in [25, 31] only worked with the assistance of CN; the schemes in [26, 28] only dealt with the D2D communication establishment in the Out-of-Coverage scenario. A uniform key management and authentication scheme that can support all scenarios is crucially important for providing continuous and seamless D2D services in a heterogeneous network environment. It is preferred that the new scheme should be compatible with the current LTE network security framework as much as possible, thus it is possible to greatly reduce the cost of D2D system deployment. Moreover, revocability of authentication and key management should also be seriously considered due to the mobility nature of D2D communications and group communications.
-
(2)
A secure scheme for inter-operator and roaming D2D communications should be designed to meet commercial and user demands. D2D communications under roaming and across operators could greatly reduce the cost of mobile users in proximity services, thus should be paid special attention due to business potential. However, how to provide secure D2D communications in this situation has not been explored in the literature, which is a promising research topic.
-
(3)
Fine-grained access control mechanisms are expected to address data protection in all scenarios of D2D communications. The access control solutions proposed in [36, 38] focused on the D2D communications with LTE network support. The access control directly among devices without CN support was seldom discussed and supported. Heterogeneous and fine-grained access control mechanisms that can cooperate with key management and authentication have not yet been seriously investigated in order to support all application scenarios of D2D communications.
-
(4)
User privacy should be well preserved in D2D communications. Nowadays, users pay much attention to their personal privacy when they use networking services, especially social networking services. Many application scenarios of D2D communications are related to social activities. Therefore, designing effective, personalized and low-cost privacy protection schemes becomes essential. User privacy preservation will impact the final adoption and success of a D2D communication service.
-
(5)
Security solutions based on social and trust relationships will open a new research field to enhance the security of D2D communications. Since D2D communications are expected to be used in many social application scenarios, the social and trust relationships among D2D users can be extracted from social layer and then applied to improve the security and performance of the network layer in D2D communications. For example, users with historical trust relationships can set up a D2D communication channel in a quick and conventional way with the assistance of a trust-based access control mechanism.
6 Conclusions
D2D communications have been treated as a promising technical component in 5G. In spite of impressive benefits, D2D communications still encounter many security problems. However, D2D security has not yet been seriously investigated in academia, industry and standardization communities. In this paper, we performed a serious survey on the security of D2D communications. We introduced three types of typical D2D application scenarios and use cases in order to illustrate its differences from MANETs. We further proposed a D2D security architecture compatible with the LTE system, analyzed security threats and suggested D2D security requirements accordingly. Based on the security architecture and requirements, we extensively reviewed the existing work of security in D2D communications. Our survey has explored that there are still a number of open security issues that have not yet been seriously investigated. We promoted future research by directing a number of research trends. We found that significant efforts are needed in order to overcome D2D security problems.
References
Bluetooth, S.I.G, Specification of the Bluetooth system, Bluetooth Core Specification, Version 4.2, 2014
Asadi A, Wang Q, Mancuso V (2014) A survey on Device-to-Device communication in cellular networks. IEEE Commun Surv Tutorials 16(4):1801–1819
NFC Protocol Technical Specification, http://nfc-forum.org/our-work/specifications-and-application-documents/
Mouly M, Pautet M, Haug T (1992) “The GSM system for mobile communications,” Telecom publishing
Dahlman E, Gudmundson B, Nilsson M, Skold A (1998) UMTS/IMT-2000 based on wideband CDMA. IEEE Commun Mag 36(9):70–80
Sesia S, Toufik I, Baker M (2009) LTE: the UMTS long term evolution: from theory to practice. Wiley, Chichester
Doppler K, Rinne M, Wijting C, Ribeiro C, Hugl K (2009) Device-to-Device communication as an underlay to LTE-advanced networks. IEEE Commun Mag 47(12):42–49
Lei L, Zhong Z, Lin C, Shen X (2012) Operator controlled Device-to-Device communications in LTE-advanced networks. IEEE Wirel Commun 19(3):96–104
Doppler K, Yu C, Ribeiro C, Janis P (2010) “Mode selection for Device-To-Device communication underlaying an LTE-Advanced network,” 2010 I.E. wireless communications and networking conference (WCNC), pp 1–6
Gamage A, Liang H, Zhang R, Shen X (2014) Device-to-device communication underlaying converged heterogeneous networks. IEEE Wirel Commun 21(6):98–107
Janis P, Yu C, Doppler K, Ribeiro C, Wijting C, Hugl K, Tirkkonen O, Koivunen V (2009) Device-to-Device communication underlaying cellular communications systems. Int J Commun Netw Syst Sci 2(3):169–178
Corson M, Laroia R, Li J, Park V, Richardson T, Tsirtsis G (2010) Toward proximity-aware internetworking. IEEE Wirel Commun 17(6):26–33
Wu X, Tavildar S, Shakkottai S, Richardson T, Li J, Laroia R, Jovicic A (2013) Flashlinq: a synchronous distributed scheduler for peer-to-peer ad hoc networks. IEEE/ACM Trans Networking 21(4):1215–1228
3rd Generation Partnership Project; Technical Specification Group Service and System Aspects; 3GPP System Architecture Evolution (SAE); Security architecture (Rel 12), 3GPP TS 33.401V12.5.0, (2012–09)
3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Feasibility study for Proximity Services (ProSe) (Rel 12), 3GPP TR 22.803V1 2.2.0 (2013–06)
3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Study on architecture enhancements to support Proximity-based Services (ProSe) (Rel 12), 3GPP TS 23.703V12.0.0 (2014–02)
3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Proximity-based services (ProSe); Stage 2 (Rel 12), 3GPP TS 23.303V12.0.0 (2014–02)
Fodor G, Parkvall S, Sorrentino S, Wallentin P, Lu Q, Brahmi N (2014) Device-to-Device communications for national security and public safety. IEEE Access 2:1510–1520
Toh C (2001) Ad hoc mobile wireless networks: protocols and systems. Prentice Hall, Saddle River
FCC, Public Safety & Homeland Security Bureau, http://publicsafety.fcc.gov/pshs/public-safety-spectrum/index.htm
Ghavimi F, Chen H (2015) M2M communications in 3GPP LTE/LTE-A networks: architectures, service requirements, challenges, and applications. IEEE Commun Surv Tutorials 17(2):525–549 Second Quarter
3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; 33GPP System Architecture Evolution (SAE) (Rel 12), 3GPP TS 33.401, V12.12.0 (2014–09)
3rd Generation Partnership Project; Technical Specification Group Service and System Aspects; 3G security; Network Domain Security (NDS); IP network layer security (Rel 12), 3GPP TS 33.210V12.2.0, (2012–12)
3rd Generation Partnership Project; Technical Specification Group Service and System Aspects; Network Domain Security (NDS); Authentication Framework (AF) (Rel 12), 3GPP TS 33.310V12.2.0, (2014–09)
Zhang A, Chen J, Hu R, Qian Y (2015) SeDS: Secure data sharing strategy for D2D communication in LTE-Advanced networks. IEEE Trans Veh Technol PP(99):1
Shen W, Hong W, Cao X, Yin B, Shila D, Cheng Y (2014) “Secure key establishment for Device-to-Device communications,” 2014 I.E. Global Communications Conference (GLOBECOM), pp. 336–340
Goratti L, Steri G, Gomez K, Baldini G (2014) “Connectivity and security in a D2D communication protocol for public safety applications,” 2014 International Symposium on Wireless Communications Systems (ISWCS), pp. 548–552
Kwon H, Hahn C, Kim D, Kang K, Hur J (2014) “Secure Device-to-Device Authentication in Mobile Multi-hop Networks,” the 9th International Conference on Wireless Algorithms, Systems, and Applications, pp. 267–278
Ekberg J, Uusitalo M, Li Z, “Device to device communication security,” WO2014207506A1, 2013–06–25
Y. Liu and D. Zhang, “Methods and apparatus for generating keys in device to device communication,” WO2014205697A1, 2013–06–26
Alam M, Yang D, Rodriguez J, Abd-Alhameed R (2014) Secure device-to-device communication in LTE-A. IEEE Commun Mag 52(4):66–73
Hakola S, Koskela T, Koskinen H “Method and apparatus for device to device key management,” WO2011117677A1, 2011–09–29
Wang J, Lin T “Authentication system for device-to-device communication and authentication method therefore,” EP2663051A1, 2013–05-06
Panaousis E, Alpcan T, Fereidooni H, Conti M (2014) Secure message delivery games for Device-to-Device communications. Decision and Game Theory for Security, Lect Notes Comput Sci 8840:195–215
Jung Y, Festijo E, Peradilla M (2014) “Joint operation of routing control and group key management for 5G ad hoc D2D networks,” 2014 International Conference on Privacy and Security in Mobile Systems (PRISMS), pp. 1–8
Huang J, Sun Y, Xiong Z, Duan Q, Zhao Y, Cao X, Wang W (2015) Modeling and analysis on access control for Device-to-Device communications in cellular network: a network calculus based approach. IEEE Trans Veh Technol PP(99):1
Huang J, Xiong Z, Li J, Chen Q, Duan Q, Zhao Y (2014) A priority-based access control model for Device-to-Device communications underlaying cellular network using network calculus. Wirel Algoritm Syst Appl 8491:613–623
Yue J, Ma C, Yu H, Zhou W (2013) Secrecy-based access control for Device-to-Device communication underlaying cellular networks. IEEE Commun Lett 17(11):2068–2071
Zhang H, Wang T, Song L, Han Z (2014) “Radio resource allocation for physical-layer security in D2D underlay communications,” 2014 I.E. International Conference on Communications (ICC 2014), pp. 2319–2324
Zhu D, Swindlehurst A, Fakoorian S, Xu W, Zhao C (2014) “Device-to-device communications: The physical layer security advantage,” 2014 I.E. International Conference on Acoustics, Speech and Signal Processing (ICASSP), pp.1606–1610
Xi W, Li X, Qian C, Han J, Tang S, Zhao J, Zhao K (2014) “KEEP: Fast secret key extraction protocol for D2D communication,” 2014 I.E. 22nd International Symposium of Quality of Service (IWQoS), pp. 350–359
Sun J, Chen X, Zhang J, Zhang Y, Zhang J (2014) “SYNERGY: A game-theoretical approach for cooperative key generation in wireless networks,” 2014 I.E. Conference on Computer Communications (INFOCOM), pp 997–1005
Zhang Y, Pan E, Song L, Saad W, Dawy Z, Han Z (2015) Social network aware Device-to-Device communication in wireless networks. IEEE Trans Wirel Commun 14(1):177–190
Chen X, Proulx B, Gong X, Zhang J (2015) Exploiting social ties for cooperative D2D communications: a mobile social networking case. IEEE/ACM Trans Networking 23(5):1471–1484
Hadiks A, Chen Y, Li F, Liu B (2014) “A study of stealthy denial-of-service attacks in Wi-Fi direct device-to-device networks,” 2014 I.E. 11th consumer communications and networking conference (CCNC 2014), pp507–508
Ma S, Yan Z (2015) An unwanted content Control system in pervasive social networking based on trust management. ACM Trans Multimed Comput Commun Appl 12(1s)
Eschenauer L, Gligor VL (2002) “A Key Management Scheme for Distributed Sensor Networks,” 2002 9th ACM Internation conference. on Computers and Commun Security (CCS), pp 41–47
Zhao S, Robert K, Akshai A (2013) A key management and secure routing integrated framework for mobile ad-hoc networks. Ad Hoc Netw 11(3):1046–1061
Lakshmi P, Kumar A (2015) Parallel key management scheme for mobile ad hoc network based on traffic mining. IET Inf Secur 9(1):14–23
Papadimitratos P, Haas Z (2006) Secure data communication in mobile ad hoc networks. IEEE J Sel Areas Commun 24(2):343–356
Ramkumar M, Memon N (2005) An efficient key predistribution scheme for ad hoc network security. IEEE J Sel Areas Commun 23(3):611–621
Deng H, Li W, Agrawal D (2002) Routing security in wireless ad hoc networks. IEEE Commun Mag 40(10):70–75
Djamel D, Khelladi L, Badache N (2007) A survey of security issues in mobile ad hoc networks. IEEE Wirel Commun 14(5):85–91 Fourth Quarter
Loay A, Khokhar A, Guizani M (2008) A survey of secure mobile ad hoc routing protocols. IEEE Commun Surv Tutorials 10(4):78–93 Fourth Quarter
Yu D, Gupta S, Varsamopoulos G (2009) Improving on-demand data access efficiency in MANETs with cooperative caching. Ad Hoc Netw 7(3):579–598
Saxena N, Gene T, Jeong H (2004) “Identity-based access control for ad hoc groups,” 2004 Information security and cryptology (ICISC) pp. 362–379
Murali M, Srinivasan R (2015) “Cached data access in MANET employing AODV protocol,” 2015 International Conference on Computer, Communication and Control (IC4), pp. 1–4
Bakar A, Ghapar A, Ismail R (2014) “Access control and privacy in MANET emergency environment,” 2014 International Conference on Computer and Information Sciences (ICCOINS), pp. 1–6
Bloch M, Barros J (2011) Physical-layer security: from information theory to security engineering. Cambridge University Press, Cambridge
Zhou X, Song L, Zhang Y (2013) Wireless networks and mobile communications series - physical layer security in wireless communications. CRC Press, Boca Raton
Hong Y, Lan P, Kuo C (2013) Enhancing physical-layer secrecy in multi-antenna wireless systems: an overview of signal processing approaches. IEEE Signal Process Mag 30(5):29–40
Lai L, Liang Y, Du W (2012) Cooperative key generation in wireless networks. IEEE J Sel Areas Commun 30(8):1578–1588
Yan Z, Wang M (2014) Protect pervasive social networking based on two-dimensional trust levels. IEEE Syst J PP(99):1–12
Acknowledgments
This work is sponsored by the NSFC (grant U1536202), the 111 project (grant B08038), the PhD grant of the Chinese Educational Ministry (grant JY0300130104), the initial grant of the Chinese Educational Ministry for researchers from abroad (grant JY0600132901), and the grant of the Shaanxi Province for excellent researchers from abroad (grant 680F1303), as well as Aalto University.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, M., Yan, Z. A Survey on Security in D2D Communications. Mobile Netw Appl 22, 195–208 (2017). https://doi.org/10.1007/s11036-016-0741-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-016-0741-5