Abstract
The rapid advancement in communication technologies enables remote users to acquire a number of online services. All such online services are provided remotely facilitating the users to freely move any where with out disruption of the services. In order to ensure seamless and secure services to the remote user such services espouse authentication protocols. A number of authentication protocols are readily available to achieve security and privacy in remote client server architecture. Most of these schemes are tailored for single server architecture. In such scenario, if a user wants to attain the services provided by more than one servers he has to register with each server. In recent times, multiserver authentication has got much attention, where a user can register once and then can acquire services provided by multiple servers. Very recently, Lu et al. proposed a biometric, smart card and password-based three factor authentication scheme usable for multiserver environments. Furthermore, Lu et al. identified their scheme to resist known attacks. However, the analysis in this paper ascertains that Lu et al.’s scheme is vulnerable to impersonation attack. An adversary registered to the system just after knowing the public identity of a user can impersonate himself as the latter. Then we propose an improvement over Lu et al.’s scheme. Our improvement is more robust than the existing schemes. The security of proposed scheme is substantiated formally along with informal security discussion, while same is also validated using a popular automated tool ProVerif. The analysis confirms that proposed scheme achieves mutual authentication and is robust against known attacks. In addition, the proposed scheme does not incur any extra computation as compared with Lu et al.’s scheme.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
During the recent times, wireless and mobile technologies have endured growth. Now a huge number of people are using mobile/wireless devices (e.g. smart phones, notebooks and PDAs) to access varying online services from anywhere and at anytime. These services include: remote medical treatment, video conferencing, VoIP, net-browsing and government services. However, the real constraint to such online services is the underlying public Internet infrastructure, which allows the attacker to intercept, eavesdrop and temper the messages transmitted between two honest entities. Therefore, it is most important to ensure the security of transmitted messages as well as the privacy of the participants. Password-based authentication scheme if employed properly can resolve such security issues. The first authentication scheme was proposed by Lamport [1]. However, their scheme was vulnerable to different attacks but it provided a basis for future research. The failure of Lamport’s scheme was the usage of only a single factor (i.e. password) for authentication. Afterwards a number of two factor authentication using password as well as smart card were proposed [2–21]. Similarly to enhance the security, a number of three factor authentication schemes using password, smart card, and biometrics were also proposed [22–29]. All the mentioned biometric-based authentication schemes are usable in single server environments. In such cases, the user has to register to various servers, which in turn limits the scalability, because he has to remember a number of identities and password also he needs a separate smart card for each server. In 2010, Yoon and Yoo [30] proposed a biometric-based authentication scheme for multiserver environments. However in 2014, He and Wang [31] found a number of weaknesses including vulnerability to impersonation and smart card theft attack in Yoon et al.’s scheme. Then He et al. proposed an improved scheme. In 2014, Chaung and Chen [32] presented an authentication scheme based on biometrics for multiserver environments and claimed that their scheme is resistant to all known attacks, but soon Mishra et al. [33] realized that scheme proposed by Chaung and Chen is vulnerable to: (1) smart card theft attack; (2) server spoofing attack; and (3) denial of services attack. Mishra et al. then presented an authentication scheme to enhance the security. Very recently Lu et al. [34] identified that Mishra et al.’s scheme cannot resist user impersonation and server spoofing attacks. They also demonstrated that Mishra et al.’s scheme does not provide perfect forward secrecy. Lu et al. then proposed a new biometric-based three factor authentication scheme for multiserver environments. Lu et al. further claimed that their scheme is robust against numerous attacks. However, the analysis in this paper proves that Lu et al.’s scheme is defenseless against user impersonation attack. We show that a dishonest user of the system can impersonate as another user of the system by just knowing the public identity of the latter.
Rest of the paper is prescribed as follows: Sect. 2 accommodates notations used throughout the paper and basic concepts relating to one way hash functions, bio-hashing and the common adversarial model. Section 3 elaborates review of Lu et al.’s biometric-based authentication scheme for multiserver environments, followed by its cryptanalysis performed in Sect. 4. The proposed enhanced scheme is presented in Sect. 5. The formal and informal security analysis is performed in Sect. 6. The automated security validation of proposed scheme using ProVerif is performed in Sect. 7. The performance evaluation is done in Sect. 8. Finally, the conclusion is made in Sect. 9.
2 Preliminaries
This section elaborates some basics related to hash functions, bio-hashing, and adversarial model along with the notations used throughout the paper outlined in Table 1.
2.1 One way hash functions
A one way hash function \(H : \{0, 1\}^{*}\rightarrow Z_{q}^{*}\) takes arbitrary length string S as input and outputs a fixed length code \(C\ =H(S)\), the fixed length out put C is termed as hash value/hash code. A slight change in S results a significant change in C. Following are the properties to qualify a secure hash function:
-
It is computationally easy to find \(C=H(S)\), if S is given.
-
It is computationally infeasible to compute S, if \(C=H(S)\) is given.
-
It is difficult to find two inputs S and T such that \(H(S)=H(T)\). This property is known as collision-resistance property.
Definition 1
(Collision-resistant hash functions) Let H(.) be a collision resistant hash function. The probability for an attacker \({\mathcal {A}}\) to find a twain \((S\ne T)\) such that \(H(S)=H(T)\) is defined as \(\textit{Adv}^{\textit{HASH}}_{{\mathcal {A}}}(t_{e1})=\textit{Prb}[(S,T) \Leftarrow _r {\mathcal {A}} : (S\ne T)\ and\ H(S)=H(T) ]\). Where \({\mathcal {A}}\) can randomly select a twain (S, T). The carried advantage of \({\mathcal {A}}\) over the randomly made selections within polynomial time \(t_{e1}\) is illustrated as \(\textit{Adv}^{\textit{HASH}}_{{\mathcal {A}}}(t_{e1})\). The collision-resistant property for secure has functions implies that \(\textit{Adv}^{\textit{HASH}}_{{\mathcal {A}}}(t_{e1})\le \epsilon \) for any sufficiently small \(\epsilon > 0\).
2.2 Bio-hashing
The biometric refers to the measurable and distinct features used to mark and describe human. Biometric is often used for enabling the authentication to work provided the physical appearance of person. The biometric features (e.g. finger prints, facial expressions and retina etc.) may slightly vary at each imprint, which may cause a number of false rejection of legal users. Consequently impacting the usability of the system. To cope with false rejection, Jin et al. [35] presented a two factor authenticator using iterated inner product of human biometric features and tokenized random number. To accommodate this, user specific codes are generated. The user specific codes are termed as Bio-hash codes. During recent times, many bio-hashing schemes are proposed [36, 37]. Bio-hashing is proved to be a convenient technique usable in small devices, such as smart card, smart phone.
2.3 Adversarial model
In this paper, we consider the common adversarial model as mentioned in [38–40]. Where according to capabilities of the adversary \({\mathcal {A}}\), following assumptions are made:
-
1.
\({\mathcal {A}}\) completely controls the public communication link. \({\mathcal {A}}\) is able to intercept, replay, modify, remove or can send a new fabricated message.
-
2.
\({\mathcal {A}}\) can extract information contained in smart card by examining power analysis or leaked information [41, 42].
-
3.
\({\mathcal {A}}\) can be an outsider or can be a dishonest user of the system.
-
4.
Identities of the registered users and servers are public and known to insiders.
-
5.
The servers are assumed to be secure and \({\mathcal {A}}\) can not compromise any server of the system. (i.e. \(\textit{PSK}_{rs}\) cannot be accessible to any adversary).
3 Review of Lu et al.’s scheme
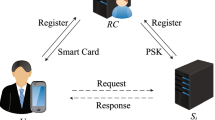
In this section, we briefly review Lu et al.’s biometric-based authentication scheme. Lu et al. employed public key technique to achieve user anonymity and forward secrecy. Their scheme involves three participants: a user \({\mathcal {U}}_i\), a server \({\mathcal {S}}_j\) and the registration center \(\textit{RC}\). The scheme is illustrated in Fig. 1. We also elaborate Lu et al.’s scheme by the following three phases.
3.1 Registration phase
Registration involves following three steps:
-
Step Reg 1:
\({\mathcal {U}}_i\) selects his identity \(\textit{ID}_{ui}\), password \(\textit{PW}_{ui}\), a random number \(N_{ui}\) along with his master private key \(x_{ui}\). Then \({\mathcal {U}}_i\) scans his biometrics \(\textit{BIO}_{ui}\). Further, \({\mathcal {U}}_i\) sends \(\{\textit{ID}_{ui},h(\textit{PW}_{ui},N_{ui})\}\) to \(\textit{RC}\) on a private channel.
-
Step Reg 2:
\(\textit{RC}\) computes \(R_{ui}=h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\) and personalizes the smart card \(\textit{SC}_{ui}\) by \(\{R_{ui},h(\textit{PSK}_{rs})\}\), where \(\textit{PSK}_{rs}\) is the shared secret key between \(\textit{RC}\) and \({\mathcal {S}}_j\). \(\textit{RC}\) using private channel sends \(\textit{SC}_{ui}\) to \({\mathcal {U}}_i\).
-
Step Reg 3:
Upon receiving smart card, \({\mathcal {U}}_i\) computes \(X_{ui}=h(\textit{PSK}_{rs})\oplus x_{ui}\), \(B_{ui}=N_{ui}\oplus H(\textit{BIO}_{ui})\). Then \({\mathcal {U}}_i\) deletes \(h(\textit{PSK}_{rs})\) from smart card (\(\textit{SC}_{ui}\)) and stores \(X_{ui}\) and \(B_{ui}\) in the smart card (\(\textit{SC}_{ui}\)). Finally, the smart card (\(\textit{SC}_{ui}\)) contains \(\{R_{ui},X_{ui},B_{ui},h()\}\).
3.2 Login and authentication phase
During login and authentication phase, \({\mathcal {U}}_i\) inserts his \(\textit{SC}_{ui}\) into card reader, imprints his biometrics (\(\textit{BIO}_{ui}\)) and submits \(\textit{ID}_{ui}\) and \(\textit{PW}_{ui}\). The steps performed by \(\textit{SC}_{ui}\) and \({\mathcal {S}}_j\) are as follows:
-
Step LA1:
\(\textit{SC}_{ui}\) computes \(N_{ui}=B_{ui}\oplus H(\textit{BIO}_{ui})\) and \(R_{ui}'=h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\).
-
Step LA2:
\(\textit{SC}_{ui}\) verifies \(R_{ui}\mathop {=}\limits ^{?}h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), if not true, \(\textit{SC}_{ui}\) aborts the session.
-
Step LA3:
\(\textit{SC}_{ui}\) generates a random number \(n_{ui}\) and computes \(M_1=E_{\textit{Pub}_{sj}}(\textit{ID}_{ui},n_{ui},h(\textit{PW}_{ui}\Vert N_{ui}))\) and \(M_2=h((X_{ui}\Vert x_{ui})\Vert n_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\).
-
Step LA4:
Further, \(\textit{SC}_{ui}\) sends login message \(\{ M_1,M_2\}\) to \({\mathcal {S}}_j\).
-
Step LA5:
For the received login message, \({\mathcal {S}}_j\) using his private key decrypts \(M_1\) to get \((\textit{ID}_{ui},n_{ui},h(\textit{PW}_{ui}\Vert N_{ui}))\).
-
Step LA6:
\({\mathcal {S}}_j\) checks whether \(M_2\mathop {=}\limits ^{?}h(h(\textit{PSK}_{rs})\Vert n_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), if not true \({\mathcal {S}}_j\) aborts the session. Otherwise, \({\mathcal {S}}_j\) selects a random number \(n_{sj}\) and computes \(M_3=n_{sj} \oplus h(n_{ui}\Vert \textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), the session key \(\textit{SK}_{ji}=h(n_{ui}\Vert n_{sj}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\) and \(M_4=h(\textit{ID}_{ui}\Vert n_{ui}\Vert \textit{SK}_{ji}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\). Further, \({\mathcal {S}}_j\) sends \(\{M_3,M_4\}\) to \({\mathcal {U}}_i\).
-
Step LA7:
For the received login message, \({\mathcal {U}}_i\) computes \(n_{sj}=M_3\oplus h(n_{ui}\Vert \textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui})) \) and session key \(\textit{SK}_{ij}=h(n_{ui}\Vert n_{sj}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\). \({\mathcal {U}}_i\) then checks \(M_4 \mathop {=}\limits ^{?}h(\textit{ID}_{ui}\Vert n_{ui}\Vert \textit{SK}_{ij}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\). If it holds, \({\mathcal {U}}_i\) ponders \({\mathcal {S}}_j\) as authenticated.
-
Step LA8:
Finally, \({\mathcal {U}}_i\) computes and sends \(M_5=h(\textit{SK}_{ij}\Vert \textit{ID}_{ui}\Vert n_{sj}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\) to \({\mathcal {S}}_j\).
-
Step LA9:
\({\mathcal {S}}_j\) checks \(M_5 \mathop {=}\limits ^{?} h(h(\textit{SK}_{ji}\Vert \textit{ID}_{ui}\Vert n_{sj}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\) if it holds, \(\mathcal {S}_j\) ponders \({\mathcal {U}}_i\) as authenticated.
The computed shared key between \({\mathcal {U}}_i\) and \({\mathcal {S}}_j\) is:
3.3 Password change phase
\({\mathcal {U}}_i\) inserts his smart card (\(\textit{SC}_{ui}\)) in specialized reader. \({\mathcal {U}}_i\) then inputs \(\textit{ID}_{ui}\), \(\textit{PW}_{ui}\) and \(\textit{BIO}_{ui}\). \(\textit{SC}_{ui}\) computes \(N_{ui}=B_{ui}\oplus H(\textit{BIO}_{ui})\) and checks \(R_{ui}=h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), if it holds \(\textit{SC}_{ui}\) asks for new password. \({\mathcal {U}}_i\) inputs new password \(\textit{PW}_{ui}^{\textit{new}}\). \(\textit{SC}_{ui}\) computes \(R_{ui}^{\textit{new}}=h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}^{\textit{new}}\Vert N_{ui}))\). Finally \(\textit{SC}_{ui}\) replaces \(R_{ui}\) by \(R_{ui}^{\textit{new}}\).
4 Cryptanalysis of Lu et al.’s scheme
This section elaborates the weakness of Lu et al.’s scheme against user impersonation attack. We show that a dishonest legal user \({\mathcal {A}}\) can easily masquerade himself as an other honest user \({\mathcal {U}}_i\) considering the common adversarial model as mentioned in Sect. 2.3. Let \({\mathcal {A}}\) be a legal user having smart card \(\textit{SC}_{a}\) and wants to impersonate himself as another user \({\mathcal {U}}_i\). The attack is illustrated in Fig. 2. The description of the same is also detailed in following steps performed during interaction of \({\mathcal {A}}\) and \({\mathcal {S}}_j\):
-
Step IA 1:
\({\mathcal {A}}\) extracts the information stored in \(\textit{SC}_{a}\) and computes:
$$\begin{aligned} h(\textit{PSK}_{rs})= X_{a}\oplus x_{a} \end{aligned}$$(2) -
Step IA 2:
\({\mathcal {A}}\) generates two random number \(n_{a}\) and \(P_{a}\) and computes:
$$\begin{aligned} M_{\bar{1}}&=E_{\textit{Pub}_{sj}}(\textit{ID}_{ui},n_{a},P_{a}) \end{aligned}$$(3)$$\begin{aligned} M_{\bar{2}}&=h((X_{a}\oplus x_{a})\Vert n_{a}\Vert P_{a}) \end{aligned}$$(4) -
Step IA 3:
\({\mathcal {A}}\) sends \(M_{\bar{1}}\) and \(M_{\bar{2}}\) as login message to \({\mathcal {S}}_j\).
-
Step IA 4:
For the received login message, \({\mathcal {S}}_j\) decrypts \(M_{\bar{1}}\) to obtain:
$$\begin{aligned} (\textit{ID}_{ui},n_{a},P_{a})=D_{Pri_{sj}}(M_{\bar{1}}) \end{aligned}$$(5) -
Step IA 5:
\({\mathcal {S}}_j\) further verifies \(M_{\bar{2}}\mathop {=}\limits ^{?} h(h(\textit{PSK}_{rs})\Vert n_{a}\Vert P_{a})\) and finds it to be true.
-
Step IA 6:
\({\mathcal {S}}_j\) further selects \(n_{sj}\) and computes:
$$\begin{aligned} M_3&=n_{sj} \oplus h(n_{ui}\Vert \textit{ID}_{ui}\Vert P_{a}) \end{aligned}$$(6)$$\begin{aligned} \textit{SK}_{ji}&=h(n_{ui}\Vert n_{sj}\Vert P_{a}) \end{aligned}$$(7)$$\begin{aligned} M_4&=h(\textit{ID}_{ui}\Vert n_{ui}\Vert \textit{SK}_{ji}\Vert P_{a}) \end{aligned}$$(8) -
Step IA 7:
\({\mathcal {S}}_j\) sends \(M_3\) and \(M_4\) to \({\mathcal {U}}_i\) as response message.
-
Step IA 8:
\({\mathcal {A}}\) intercepts the message and computes:
$$\begin{aligned} n_{sj}&=M_3\oplus h(n_{ui}\Vert \textit{ID}_{ui}\Vert P_{a}) \end{aligned}$$(9)$$\begin{aligned} \textit{SK}_{ij}&=h(n_{ui}\Vert n_{sj}\Vert P_{a}) \end{aligned}$$(10)$$\begin{aligned} M_{\bar{5}}&=h(\textit{SK}_{ij}\Vert \textit{ID}_{ui}\Vert n_{sj}\Vert P_{a}) \end{aligned}$$(11) -
Step IA 9:
\({\mathcal {A}}\) sends \(M_{\bar{5}}\) to \({\mathcal {S}}_j\).
-
Step IA 10:
\({\mathcal {S}}_j\) checks \(M_{\bar{5}} \mathop {=}\limits ^{?} h(h(\textit{SK}_{ji}\Vert \textit{ID}_{ui}\Vert n_{sj}\Vert P_a)\) and finds it to be true.
Hence, \({\mathcal {A}}\) successfully deceived \({\mathcal {S}}_j\) by impersonating himself as \({\mathcal {U}}_i\). The shared key between \({\mathcal {A}}\) and \({\mathcal {S}}_j\) is:
5 Proposed scheme
This section elaborates the proposed improvement of Lu et al.’s scheme. The main problem of Lu et al.’s scheme is usage of secret parameter \(h(\textit{PSK}_{rs})\). This parameter is stored on smart card of each user. Therefore, an adversary after registering to the system can extract \(h(\textit{PSK}_{rs})\) from his own smart card. After obtaining \(h(\textit{PSK}_{rs})\), the adversary can easily impersonate himself any user of the system. In proposed scheme, we have alternated the generic secret \(h(\textit{PSK}_{rs})\) by a unique secret \(h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\). The proposed scheme as illustrated in Fig. 3 is described in following subsections.
5.1 Registration phase
Registration involves following three steps:
-
Step PR 1:
\({\mathcal {U}}_i\) selects his identity \(\textit{ID}_{ui}\), password \(\textit{PW}_{ui}\) and a random number \(N_{ui}\). Then \({\mathcal {U}}_i\) scans his biometrics \(\textit{BIO}_{ui}\). Further \({\mathcal {U}}_i\) sends \(\{\textit{ID}_{ui},h(\textit{PW}_{ui},N_{ui})\}\) to \(\textit{RC}\) on a private channel.
-
Step PR 2:
\(\textit{RC}\) computes \(R_{ui}=h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\) and personalizes the smart card \(\textit{SC}_{ui}\) by \(\{R_{ui},h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\}\), where \(\textit{PSK}_{rs}\) is the shared secret key between \(\textit{RC}\) and \({\mathcal {S}}_j\). \(\textit{RC}\) using private channel sends \(\textit{SC}_{ui}\) to \({\mathcal {U}}_i\).
-
Step PR 3:
Upon receiving smart card, \({\mathcal {U}}_i\) computes \(X_{ui}=h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\oplus h(\textit{PW}_{ui}\Vert \textit{ID}_{ui}\Vert N_{ui})\), \(B_{ui}=N_{ui}\oplus H(\textit{BIO}_{ui})\). Then \({\mathcal {U}}_i\) deletes \(h(\textit{PSK}_{rs}\Vert {} \textit{ID}_{ui})\) from smart card (\(\textit{SC}_{ui}\)) and stores \(X_{ui}\) and \(B_{ui}\) in the smart card (\(\textit{SC}_{ui}\)). Finally, the smart card (\(\textit{SC}_{ui}\)) contains \(\{R_{ui},X_{ui},B_{ui},h()\}\).
5.2 Login and authentication phase
During login and authentication phase, \({\mathcal {U}}_i\) inserts his \(\textit{SC}_{ui}\) into card reader, imprints his biometrics (\(\textit{BIO}_{ui}\)) and submits \(\textit{ID}_{ui}\) and \(\textit{PW}_{ui}\). The steps performed by \(\textit{SC}_{ui}\) and \({\mathcal {S}}_j\) are as follows:
-
Step LA1:
\(\textit{SC}_{ui}\) computes \(N_{ui}=B_{ui}\oplus H(\textit{BIO}_{ui})\) and \(R_{ui}'=h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\).
-
Step LA2:
\(\textit{SC}_{ui}\) verifies \(R_{ui}\mathop {=}\limits ^{?}h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), if not true, \(\textit{SC}_{ui}\) aborts the session.
-
Step LA3:
\(\textit{SC}_{ui}\) generates a random number \(n_{ui}\) and computes \(M_1=E_{\textit{Pub}_{sj}}(\textit{ID}_{ui},n_{ui},h(\textit{PW}_{ui}\Vert N_{ui}))\) and \(M_2=h((X_{ui}\oplus h(\textit{PW}_{ui}\Vert \textit{ID}_{ui}\Vert N_{ui})\Vert n_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\).
-
Step LA4:
Further, \(\textit{SC}_{ui}\) sends login message \(\{ M_2,M_3\}\) to \({\mathcal {S}}_j\).
-
Step LA5:
For the received login message, \({\mathcal {S}}_j\) using his private key decrypts \(M_1\) to get \((\textit{ID}_{ui},n_{ui},h(\textit{PW}_{ui}\Vert N_{ui}))\).
-
Step LA6:
\({\mathcal {S}}_j\) checks whether \(M_2\mathop {=}\limits ^{?}h(h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\Vert n_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), if not true \({\mathcal {S}}_j\) aborts the session. Otherwise, \({\mathcal {S}}_j\) selects a random number \(n_{sj}\) and computes \(M_3=n_{sj} \oplus h(n_{ui}\Vert \textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), the session key \(\textit{SK}_{ji}=h(n_{ui}\Vert n_{sj}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\) and \(M_4=h(\textit{ID}_{ui}\Vert n_{ui}\Vert \textit{SK}_{ji}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\). Further \({\mathcal {S}}_j\) sends \(\{M_3,M_4\}\) to \({\mathcal {U}}_i\).
-
Step LA7:
For the received login message, \({\mathcal {U}}_i\) computes \(n_{sj}=M_3\oplus h(n_{ui}\Vert \textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui})) \) and session key \(\textit{SK}_{ij}=h(n_{ui}\Vert n_{sj}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\). \({\mathcal {U}}_i\) then checks \(M_4 \mathop {=}\limits ^{?}h(\textit{ID}_{ui}\Vert n_{ui}\Vert \textit{SK}_{ij}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\). If it holds, \({\mathcal {U}}_i\) ponders \({\mathcal {S}}_j\) as authenticated.
-
Step LA8:
Finally, \({\mathcal {U}}_i\) computes and sends \(M_5=h(\textit{SK}_{ij}\Vert \textit{ID}_{ui}\Vert n_{sj}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\) to \({\mathcal {S}}_j\).
-
Step LA9:
\({\mathcal {S}}_j\) checks \(M_5 \mathop {=}\limits ^{?} h(h(\textit{SK}_{ji}\Vert \textit{ID}_{ui}\Vert n_{sj}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\) if it holds, \({\mathcal {S}}_j\) ponders \({\mathcal {U}}_i\) as authenticated.
The computed shared key between \({\mathcal {U}}_i\) and \({\mathcal {S}}_j\) is:
5.3 Password change phase
\({\mathcal {U}}_i\) inserts his smart card (\(\textit{SC}_{ui}\)) in specialized reader. \({\mathcal {U}}_i\) then inputs \(\textit{ID}_{ui}\), \(\textit{PW}_{ui}\) and \(\textit{BIO}_{ui}\). \(\textit{SC}_{ui}\) computes \(N_{ui}=B_{ui}\oplus H(\textit{BIO}_{ui})\) and checks \(R_{ui}=h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), if it hold \(\textit{SC}_{ui}\) asks for new password. \({\mathcal {U}}_i\) inputs new password \(\textit{PW}_{ui}^{\textit{new}}\). \(\textit{SC}_{ui}\) computes \(R_{ui}^{\textit{new}} = h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}^{\textit{new}}\Vert N_{ui}))\) and \(X_{ui}^{\textit{new}} = X_{ui}\oplus h(\textit{PW}_{ui}\Vert \textit{ID}_{ui}\Vert N_{ui})\oplus h(\textit{PW}_{ui}^{\textit{new}}\Vert \textit{ID}_{ui}\Vert N_{ui}^{\textit{new}})\). Finally, \(\textit{SC}_{ui}\) replaces \(R_{ui}\) and \(X_{ui}\) by \(R_{ui}^{\textit{new}}\) and \(X_{ui}^{\textit{new}}\).
6 Security analysis
This section elaborates the security analysis of proposed scheme. Here, we prove that proposed scheme is robust and can with stand several attacks under the common adversarial model as mentioned in Sect. 2.3. The evidence is solicited in following subsections.
6.1 Formal security
To demonstrate that proposed scheme is provably secure, we adopted the same analysis as mentioned in [33, 34]. For analysis, we define Reveal oracle as follows:
-
Reveal: This oracle results an input string S from the hash code \(T=h(S)\).
Theorem 1
The proposed scheme is provably secure against an adversary \({\mathcal {A}}\) for stemming \({\mathcal {U}}_i\)’s identity \(\textit{ID}_{ui}\), password \(\textit{PW}_{ui}\), the session key \(\textit{SK}_{ij}\) and the shared key \(\textit{PSK}_{rs}\) between Registration center \(\textit{RC}\) and the server \({\mathcal {S}}_j\) considering one way hash function as a random oracle.
Proof 1
For the proof purpose, we construct an attacker \({\mathcal {A}}\) with capabilities to derive a legal user \({\mathcal {U}}_i\)’s \(\textit{ID}_{ui}\), \(\textit{PW}_{ui}\), the session key \(\textit{SK}_{ij}\) between \({\mathcal {U}}_i\) and \({\mathcal {S}}_j\) and the shared key \(\textit{PSK}_{rs}\) between \({\mathcal {S}}_j\) and \(\textit{RC}\). \({\mathcal {A}}\) simulates Reveal oracle to executes algorithmic experiment \(\textit{EXPE}1^{\textit{HASH}}_{{\mathcal {A}},\textit{MSBTFAS}}\) against our proposed multiserver biometric-based three factor authentication scheme (\(\textit{MSBTFAS}\)). The success probability for \(\textit{EXPE}1^{\textit{HASH}}_{{\mathcal {A}},\textit{MSBTFAS}}\) is defined as \(\textit{Succe}_1=|\textit{Pr}[\textit{EXPE}1^{\textit{HASH}}_{{\mathcal {A}},\textit{MSBTFAS}}=1]-1|\). The adversary advantage is defined as \(\textit{Advt}_{{\mathcal {A}}, \textit{MSBTFAS}}^{\textit{HASH}}(t_{e1},q_{rv}) = max_{{\mathcal {A}}}(\textit{Succe}_1)\), where \(t_{e1}\) is the maximum execution time for polynomial bound adversary \({\mathcal {A}}\) and \(q_{rv}\) are the maximum number of Reveal queries. Referring to the experiment, \({\mathcal {A}}\) can derive \(\textit{ID}_{ui}\), \(\textit{PW}_{ui}\), \(\textit{SK}_{ij}\) and \(\textit{PSK}_{rs}\) if he can invert hash value (i.e. find S out of h(S)), which is infeasible as per Definition 1. Therefore, \(\textit{Advt}_A^{\textit{HASH}}(t_{e1})\le \epsilon \) for sufficiently small value \(\epsilon > 0\). The advantage \(\textit{Advt}_{{\mathcal {A}},,\textit{MSBTFAS}}^{\textit{HASH}}(t_{e1},q_{rv})\) relies on \(\textit{Advt}_A^{\textit{HASH}}(t_{e1})\). Hence, \(\textit{Advt}_{{\mathcal {A}}, \textit{MSBTFAS}}^{\textit{HASH}} (t_{e1},q_{rv})\le \epsilon \). Therefore, the proposed scheme is secure against \({\mathcal {A}}\) for deriving \(\textit{ID}_{ui}\), \(\textit{PW}_{ui}\), \(\textit{SK}_{ij}\) and \(\textit{PSK}_{rs}\). \(\square \)

6.2 Further security discussion
In this subsection, we informally describes the security functionalities provided by proposed scheme.
6.2.1 Anonymity and privacy
In proposed scheme, \({\mathcal {U}}_i\)’s identity \((\textit{ID}_{ui})\) is not transmitted in plain text, rather it is encrypted by intended server \({\mathcal {S}}_j\)’s public key. Hence, only \({\mathcal {S}}_j\) can know the real identity of the sender. Furthermore, the message \(M_1\) contains session specific \(n_{ui}\). Hence, no adversary can predict whether two sessions are initiated by same user.
6.2.2 Mutual authentication
\({\mathcal {S}}_j\) authenticates \({\mathcal {U}}_i\) by verifying \(M_2\mathop {=}\limits ^{?}h(h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\Vert n_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\). To compute valid \(M_2\) the adversary needs \(h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\) which can only be computed by involving both \({\mathcal {U}}_i\)’s password and smart card. Similarly \({\mathcal {S}}_j\) is authenticated by verifying \(M_4 \mathop {=}\limits ^{?}h(\textit{ID}_{ui}\Vert n_{ui}\Vert \textit{SK}_{ij}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\). \({\mathcal {U}}_i\) sends \(M_1\) and \(M_2\) to server as authentication request. The session specific information \(n_{ui}\) and \({\mathcal {U}}_i\)’s password, identity and secret number \(N_{ui}\) can be extracted by decrypting \(M_1\). As \(M_1\) is decrypted by using public key of \({\mathcal {S}}_j\). Hence to decrypt one needs private key of \({\mathcal {S}}_j\). Hence, only legal user can generate valid \((M_1,M_2)\) pair. Similarly, only legal server can respond by \(M_4\). Therefore, proposed scheme posses mutual authentication between \({\mathcal {U}}_i\) and \({\mathcal {S}}_j\).
6.2.3 User and server impersonation attacks
As described earlier in Sect. 6.2.2, only legal user can generate valid request \((M_1,M_2)\) pair and only valid intended server can generate valid response \(M_4\) and no adversary can generate either of the mentioned messages. Hence, proposed scheme resists user as well as server impersonation attacks.
6.2.4 Smart card theft/stolen attack
In proposed scheme, even if an adversary becomes able to acquire \({\mathcal {U}}_i\)’s smart card. The adversary can further extracts \(R_{ui}=h(\textit{ID}_{ui}\Vert h(\textit{PW}_{ui}\Vert N_{ui}))\), \(X_{ui}=h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\oplus h(\textit{PW}_{ui}\Vert \textit{ID}_{ui}\Vert N_{ui})\) and \(B_{ui}=N_{ui}\oplus H(\textit{BIO}_{ui})\). Then to obtain \(h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\) and \(N_{ui}\) he needs \({\mathcal {U}}_i\)’s password as well as biometrics. Hence, no forgery attack is possible with theft smart card.
6.2.5 Replay attack
An adversary after intercepting a previous message request \((M_1,M_2)\) can replay it later on. But he will not be able to compute session specific \((n_{ui},n_{sj})\) and password-related \(h(\textit{PW}_{ui}\Vert N_{ui})\). Furthermore, adversary will not be able to generate valid response message \(M_5\). Hence no replay attack is feasible on proposed scheme.
6.2.6 Perfect forward secrecy
In proposed scheme, the session key contains session specific \(n_{ui}\) contributed by \({\mathcal {U}}_i\) and \(n_{sj}\) putted by \({\mathcal {S}}_j\). If some session key or long term private key of the server or user’s password is exposed to the adversary it will have no effect on established session keys.
6.2.7 Insider and stolen verifier attacks
In proposed scheme, the user’s password is not sent in plain text to the server. Furthermore, the server does not store any verifier table for user authentication. Hence, no insider or stolen verifier attack is possible on proposed scheme.
6.2.8 Password guessing attack
In proposed scheme, the information relating to \({\mathcal {U}}_i\)’s password is protected by \(N_{ui}\) and one way hash function. Furthermore, there is no parameter to verify correctness of user’s password. Hence password guessing attack is not feasible on proposed scheme.
6.2.9 No clock synchronization
The proposed scheme made use of session specific random number \(n_{ui}\) and \(n_{sj}\) for authentication. There is no time stamp involved in any message. Hence in proposed scheme, there is no need to perform clock synchronization.
7 Verification through ProVerif
Cryptographic verification aims to examine the robustness of protocols against strong active attackers such as insiders who know some of the cryptographic parameters. ProVerif as designed is an automated verification tool to analyze security protocols against strong adversaries. Based on applied \(\pi \) calculus, ProVerif can verify numerous security aspects like: secrecy, reachability, and authentication [43–48]. To analyze the security of proposed scheme, we model the mentioned steps of Sect. 5, which are also illustrated in Fig. 3. The formal model of ProVerif can be described by following three parts: (1) declaration; (2) process; and (3) main. Declaration part is reserved for defining variables, constants and cryptographic primitives. As shown in Fig. 4a, we define two channels, the variables and constants. We also model the primitives used in proposed scheme as constructors, destructors and equations in declaration part. We define three processes for each registration center, server and user in processes part as shown in Fig. 4b. In main part, we simulate parallel execution of the three processes. To verify reachability property, we define start and end events of server and user. Finally, we applied three queries as shown in Fig. 4c. Following are the results:
-
1.
RESULT inj-event(end_ServerSj(id)) ==> inj-event(begin_ServerSj(id)) is true.
-
2.
RESULT inj-event(end_UserUi(id_3409)) ==> inj-event(begin_UserUi(id_3409)) is true.
-
3.
RESULT not attacker(SKij[]) is true.
Results (1) and (2) confirms both the user and server processes initiated and terminated successfully which verifies that proposed scheme is correct and posses the reachability property. Result (3) confirms that the attacker is not able to compute the session key \((\textit{SK}ij[])\). Hence, proposed scheme is correct and fulfills reachability as well as secrecy and authentication properties.
8 Performance and security comparisons
This section elaborates the performance and security comparisons of proposed and related recent schemes [32–34]. We illustrate the security comparison of proposed scheme with related schemes in Table under the mentioned adversarial model in Sect. 2.3. The vulnerability to impersonation attack of Lu et al.’s scheme was due to the fact, they used a generic value \(h(\textit{PSK}_{rs})\) to authenticate any user. Hence a registered user can extract this value from his smart card and then can impersonate himself as any user of the system provided he obtains the public identity of the user. We alternated the use of generic value \(h(\textit{PSK}_{rs})\) by user specific value \(h(\textit{PSK}_{rs}\Vert \textit{ID}_{ui})\), which prevents impersonation and other attacks. Refer to Table 2, Proposed scheme is robust against all attacks, while all other schemes are vulnerable to impersonation attacks. In addition, Mishra et al. scheme does not provide forward secrecy, while Chaung et al.’s scheme can not resist smart card lost/theft attack. Following are the notations used for performance comparison:
-
\(t_{h}\): time to compute hash code
-
\(t_{pml}\): time to perform point multiplication
-
\(t_{aen}\): time to perform asymmetric operations
Table 3 illustrates the computational cost comparisons. It can be seen that only Mishra et al. and Chaung et al.’s schemes are having least cost because both schemes are based on hash function. Proposed scheme is having same computation cost as of Lu et al.’s scheme. Hence proposed scheme not only improved the security but is also having same computation cost as of Lu et al.’s scheme.
9 Conclusion
In this paper, we analyzed Lu et al.’s biometric-based authentication scheme for multiserver environments. We proved that Lu et al.’s scheme cannot withstand user impersonation attack. Then we proposed an improved and robust biometric-based authentication scheme to enhance security. We also proved the security of proposed scheme using popular automated tool ProVerif. The improved scheme did not change the computation and communication costs of original scheme while ensuring security and privacy of the remote user.
References
Lamport L (1981) Password authentication with insecure communication. Commun ACM 24(11):770–772
He D (2012) An efficient remote user authentication and key agreement protocol for mobile client–server environment from pairings. Ad Hoc Netw 10(6):1009–1016
Farash MS, Attari MA (2014) A secure and efficient identity-based authenticated key exchange protocol for mobile client-server networks. J Supercomput 69(1):395–411
Farash MS, Attari MA (2014) An anonymous and untraceable password-based authentication scheme for session initiation protocol using smart cards. Int J Commun Syst. doi:10.1002/dac.2848
Farash MS, Attari MA (2014) Cryptanalysis and improvement of a chaotic map-based key agreement protocol using Chebyshev sequence membership testing. Nonlinear Dyn 76(2):1203–1213
Irshad A, Sher M, Faisal MS, Ghani A, Ul Hassan M, Ch SA (2013) A secure authentication scheme for session initiation protocol by using ECC on the basis of the Tang and Liu scheme. Secur Commun Netw 7(8):1210–1218. doi:10.1002/sec.834
Irshad A, Sher M, Rehman E, Ch SA, Hassan MU, Ghani A (2013) A single round-trip sip authentication scheme for voice over internet protocol using smart card. Multimed Tools Appl 74(11):3967–3984. doi:10.1007/s11042-013-1807-z
Islam S, Khan M (2014) Cryptanalysis and improvement of authentication and key agreement protocols for telecare medicine information systems. J Med Syst. doi:10.1007/s10916-014-0135-9
Chaudhry S, Naqvi H, Shon T, Sher M, Farash M (2015) Cryptanalysis and improvement of an improved two factor authentication protocol for telecare medical information systems. J Med Syst. doi:10.1007/s10916-015-0244-0
Jiang Q, Ma J, Tian Y (2014) Cryptanalysis of smart-card-based password authenticated key agreement protocol for session initiationprotocol of zhang et al. Int J Commun Syst. doi:10.1002/dac.2767
Zhang L, Tang S, Cai Z (2014) Robust and efficient password authenticated key agreement with user anonymity for session initiation protocol-based communications. IET Commun 8(1):83–91
He D, Kumar N, Chen J, Lee C-C, Chilamkurti N, Yeo S-S (2015) Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Syst 21(1):49–60. doi:10.1007/s00530-013-0346-9
He D, Kumar N, Chilamkurti N (2015) A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf Sci 321:263–274. doi:10.1016/j.ins.2015.02.010
He D, Zeadally S (2015) Authentication protocol for an ambient assisted living system. Commun Mag IEEE 53(1):71–77
Farash MS, Chaudhry SA, Heydari M, Sajad Sadough SM, Kumari S, Khan MK (2015) A lightweight anonymous authentication scheme for consumer roaming in ubiquitous networks with provable security. Int J Commun Syst. doi:10.1002/dac.3019
Mehmood Z, Uddin N, Ch SA, Nasar W, Ghani A (2012) An efficient key agreement with rekeying for secured body sensor networks. In: 2012 second international conference on digital information processing and communications (ICDIPC). IEEE, pp 164–167
Chaudhry SA, Farash MS, Naqvi H, Islam SH, Shon T, Sher M (2015) A robust and efficient privacy aware handover authentication scheme for wireless networks. Wirel Pers Commun. doi:10.1007/s11277-015-3139-y
Heydari M, Sadough S, Farash M, Chaudhry S, Mahmood K (2015) An efficient password-based authenticated key exchange protocol with provable security for mobile client–client networks. Wirel Pers Commun. doi:10.1007/s11277-015-3123-6
Guo P, Wang J, Geng XH, Kim CS, Kim J-U (2014) A variable threshold-value authentication architecture for wireless mesh networks. J Internet Technol 15(6):929–935. doi:10.6138/JIT.2014.15.6.05
Amin R, Biswas G (2015) A novel user authentication and key agreement protocol for accessing multi-medical server usable in TMIS. J Med Syst 39(3):1–17
Amin R, Islam SH, Biswas G, Khan MK, Kumar N (2015) An efficient and practical smart card based anonymity preserving user authentication scheme for TMIS using elliptic curve cryptography. J Med Syst 39(11):1–18
Lu Y, Li L, Peng H, Yang Y (2015) An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J Med Syst 39(3):1–8
Awasthi AK, Srivastava K (2013) A biometric authentication scheme for telecare medicine information systems with nonce. J Med Syst 37(5):1–4
Li X, Niu J, Khan MK, Liao J, Zhao X (2014) Robust three-factor remote user authentication scheme with key agreement for multimedia systems. Secur Commun Netw. doi:10.1002/sec.961
Zhang M, Zhang J, Zhang Y (2015) Remote three-factor authentication scheme based on fuzzy extractors. Secur Commun Netw 8(4):682–693. doi:10.1002/sec.1016
Mishra D, Kumari S, Khan MK, Mukhopadhyay S (2015) An anonymous biometric-based remote user-authenticated key agreement scheme for multimedia systems. Int J Commun Syst. doi:10.1002/dac.2946
Das AK (2015) A secure and effective biometric-based user authentication scheme for wireless sensor networks using smart card and fuzzy extractor. Int J Commun Syst. doi:10.1002/dac.2933
Li X, Khan M, Kumari S, Liao J, Liang W (2014) Cryptanalysis of a robust smart card authentication scheme for multi-server architecture. In: 2014 international symposium on biometrics and security technologies (ISBAST), pp 120–123. doi:10.1109/ISBAST.2014.7013106
He D, Kumar N, Lee J-H, Sherratt R (2014) Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans Consum Electron 60(1):30–37. doi:10.1109/TCE.2014.6780922
Yoon E-J, Yoo K-Y (2013) Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. J Supercomput 63(1):235–255
He D, Wang D (2014) Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst J 99:1–9. doi:10.1109/JSYST.2014.2301517
Chuang M-C, Chen MC (2014) An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst Appl 41(4):1411–1418
Mishra D, Das AK, Mukhopadhyay S (2014) A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst Appl 41(18):8129–8143
Lu Y, Li L, Peng H, Yang Y (2015) A biometrics and smart cards-based authentication scheme for multi-server environments. Secur Commun Netw. doi:10.1002/sec.1246
Jin ATB, Ling DNC, Goh A (2004) Biohashing: two factor authentication featuring fingerprint data and tokenised random number. Pattern Recognit 37(11):2245–2255
Lumini A, Nanni L (2007) An improved biohashing for human authentication. Pattern Recognit 40(3):1057–1065
Belguechi R, Rosenberger C, Ait-Aoudia S (2010) Biohashing for securing minutiae template. In: 2010 20th international conference on pattern recognition (ICPR). IEEE, pp 1168–1171
Eisenbarth T, Kasper T, Moradi A, Paar C, Salmasizadeh M, Shalmani M (2008) On the power of power analysis in the real world: a complete break of the KeeLoq code hopping scheme. In: Wagner D (ed) Advances in cryptology, CRYPTO 2008, vol 5157 of lecture notes in computer science. Springer, Berlin, pp 203–220. doi:10.1007/978-3-540-85174-5_12
Dolev D, Yao AC (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208. doi:10.1109/TIT.1983.1056650
Cao X, Zhong S (2006) Breaking a remote user authentication scheme for multi-server architecture. IEEE Commun Lett 10(8):580–581. doi:10.1109/LCOMM.2006.1665116
Kocher P, Jaffe J, Jun B (1999) Differential power analysis. In: Advances in cryptology CRYPTO 99. Springer, pp 388–397
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. IEEE Trans Comput 51(5):541–552
Xie Q, Dong N, Wong DS, Hu B (2014) Cryptanalysis and security enhancement of a robust two-factor authentication and key agreement protocol. Int J Commun Syst. doi:10.1002/dac.2858
Chaudhry SA, Mahmood K, Naqvi H, Khan MK (2015) An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography. J Med Syst. doi:10.1007/s10916-015-0335-y
Kumari S, Chaudhry SA, Wu F, Li X, Farash MS, Khan MK (2015) An improved smart card based authentication scheme for session initiation protocol. Peer-to-Peer Netw Appl. doi:10.1007/s12083-015-0409-0
Chaudhry SA, Naqvi H, Sher M, Farash MS, Hassan Mu (2015) An improved and provably secure privacy preserving authentication protocol for sip. Peer-to-Peer Netw Appl. doi:10.1002/ppna.1299
Chaudhry SA, Farash MS, Naqvi H, Kumari S, Khan MK (2015) An enhanced privacy preserving remote user authentication scheme with provable security. Netw Secur Commun. doi:10.1002/sec.1299
Chaudhry SA, Farash M, Naqvi H, Sher M (2015) A secure and efficient authenticated encryption for electronic payment systems using elliptic curve cryptography. Electron Commer Res. doi:10.1007/s10660-015-9192-5
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chaudhry, S.A., Naqvi, H., Farash, M.S. et al. An improved and robust biometrics-based three factor authentication scheme for multiserver environments. J Supercomput 74, 3504–3520 (2018). https://doi.org/10.1007/s11227-015-1601-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-015-1601-y