Abstract
A novel color image encryption algorithm based on a cross 2D hyperchaotic map is proposed in this paper. The cross 2D hyperchaotic map is constructed using one nonlinear function and two chaotic maps with a cross structure. Chaotic behaviors are illustrated using bifurcation diagrams, Lyapunov exponent spectra, phase portraits, etc. In the color image encryption algorithm, the keys are generated using hash function SHA-512 and the information of the plain color image. First, the color plain image is converted to a combined bit-level matrix and permuted by the chaos-based row and column combined cycle shift scrambling method. Then, the scrambled integer matrix is diffused according to the selecting sequence which depends on the chaotic sequence. Last, decompose the diffusion matrix to get the encrypted color image. Simulation experiments and security evaluations show that the algorithm can encrypt the color image effectively and has good security to resist various kinds of attacks.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
In modern society, along as the fast growth of the Internet, big data, artificial intelligence, and 5G communications, a large amount of information has been digitized and transmitted over the network. As an important information carrier, the security of digital images attracts more and more attention. Because color images contain richer information than gray-level images, the related research in encryption of color images has been a hot research topic [1,2,3,4,5,6,7,8,9,10,11].
The method to encrypt image is different from the way to encrypt text because the image has characteristics of massive data volume and highly relevant contents between pixels. Thus, traditional encryption technologies include DES, IDES, and RSA are not any more appropriate for encrypting image. The chaotic system has the features of sensitiveness of control parameters and initial conditions, ergodicity, random-like behavior, and unpredictable orbit. It corresponds to the concepts of key design, confusion, diffusion, and round-robin in cryptography, which makes chaos theory have great potential in the field of cryptography.
In the last decades, many methods of image cryptography are introduced based on chaos theory [12,13,14,15,16,17,18,19,20]. Because of the limitation of computer precision, the dynamical behavior of most low-dimensional chaotic systems degenerates, which leads to the defects of small keyspace and weak security performance. The image encryption algorithms design of using a high-dimensional continuous chaotic system still have the defect that the encrypted image interruptible by known-plaintext attack or selected plaintext attack [21,22,23,24]. Besides, the computational complexity and time consumption of the encryption algorithm are increased.
Compared with chaotic systems, hyperchaotic maps having more than one positive Lyapunov exponent have more complicated and abundant behaviors of dynamics, which enhance the stochasticity and unpredictability of the relevant systems [25]. Therefore, when applied to encryption, the hyperchaotic system can generate larger keyspace and more complex random sequences. Using the hyperchaotic system to design algorithms for encrypting color image will greatly improve the security of the algorithm [26,27,28,29,30,31,32].
How to design an encryption algorithm according to the characteristics of the color image and chaotic system still has a large research value. In the last several years, some new chaotic maps have been applied to image encryption algorithms [33,34,35,36,37]. Some of the new chaotic maps still have defects that trajectory is not distributed in the whole phase space or has no complex dynamic behavior.
Because of the above shortcomings, we design a nonlinear discrete cross 2D hyperchaotic map and propose a color image cryptography technique based on this hyperchaotic map. The 2D hyperchaotic map is constructed using one nonlinear function and two chaotic maps with cross structure. Chaotic behaviors are illustrated using bifurcation diagrams, Lyapunov exponent spectra, phase portraits, etc. The simulation results prove that the cross 2D hyperchaotic map has good chaotic performance. In the color image encryption algorithm, the keys are associated with the plain color image, that is, distinct plain color images produce different keys, thus enhancing security against selected plaintext/ciphertext attacks. The color plain image is converted to a combined bit-level matrix and permuted by the chaos-based row and column combined cycle shift scrambling method. Then, the scrambled integer matrix is diffused according to the selecting sequence which depends on the chaotic sequence. The cipher color image is obtained by decomposed the diffused matrix. The proposed encryption algorithm makes the three color components of the color image influence each other to eliminate the correlations between them. Simulation results show that the algorithm can encrypt the color image effectively and has good security.
The remainder of this paper has been structured in the following ways. Section 2 introduces the model of the nonlinear cross 2D hyperchaotic map. In Sect. 3, we analyze the dynamic behaviors of the proposed cross 2D hyperchaotic map. Section 4 introduces algorithm for encryption and decryption of color images. Section 5 evaluates the results of the experiments and the security of the method. Section 6 provides the conclusion.
2 Cross 2D hyperchaotic map
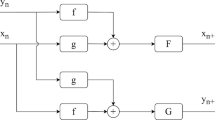
In this paper, a cross 2D hyperchaotic map is proposed, and the structure is shown in Fig. 1. The proposed model has two inputs variables and two cross outputs, which is when input is xn the output is yn+1, and when input is yn the output is xn+1. Function f is a nonlinear function, functions F and G are two chaotic maps. The + sign indicates the addition of two inputs. The mathematical expression of the model is shown in Eq. (1).
where F and G can be selected as any one-dimensional chaotic map.
The chaotic map F is chosen as the infinite collapse map [38] defined as
where its control parameter \(\alpha \ne 0\). And the chaotic map G is chosen as the Sine map in this paper. The Sine map is given as
where \(\beta\) is a control parameter and it has an interval of (0,1]. The nonlinear function f is set to sin function, that is \(f(x) = sin(x)\). So the mathematical expression of the modified 2D coupled chaotic map model is set to
where its control parameter \(\alpha \ne 0\), \(\beta \in (0,1]\), the initial value \(y_{0} \ne 0\).
3 Dynamics analysis of the cross 2D hyperchaotic map
3.1 Bifurcation diagram
The dynamical behaviors of a chaotic system can be evaluated by its bifurcation diagram. A bifurcation diagram shows the changes in the system’s motion state along with the control parameters. The evolution process of the system can be directly observed by the bifurcation diagram. Set the initial conditions \(x_{0} = 0.3\)and \(y_{0} = 0.6\). Fixing \(\beta = 1\), when the control parameter \(\alpha\) in the range [0.25, 2], the bifurcation diagram is illustrated in Fig. 2a. From Fig. 2a, we can see that the system goes through a periodic state to chaotic orbit. When \(0.55 < \alpha \le 2\), the system exhibits chaotic behavior. Fixing \(\alpha = 1\) illustrates the bifurcation diagram when control parameter \(\beta\) in the range [0.1, 1] in Fig. 2b. The results show that the system exhibits the periodic behavior between (0.34, 0.353), and produces chaotic attractors throughout the remaining range.
3.2 Lyapunov exponent spectrum
The Lyapunov exponent is one of the characteristics used to identify the chaotic characteristics of dynamic systems. For a high-order dynamic system, due to the different directions of the initial separation vector, the exponential divergence rate will be different, so there are multiple Lyapunov exponents. The system has the same number of Lyapunov exponents and order. Consequently, the two-dimensional system with two Lyapunov exponents.
The Lyapunov exponents of the system are two negative numbers, indicating that the system is at a fixed point. The system has a negative and a zero Lyapunov exponent when it is in a periodic orbit. The Lyapunov exponent of the system is one positive and one negative when it is in a chaotic orbit. The Lyapunov exponent of the system is two positive numbers when the system is in hyperchaotic state. Hyperchaotic systems normally possess more sophisticated and abundant dynamic behaviors compared to chaotic systems, which enhances the stochastic and unpredictable nature of the systems.
In the proposed map, the Lyapunov exponents spectrum is shown in Fig. 3a when fixing \(\beta = 1\) and varying \(\alpha\). It can be seen that when \(\alpha \in (1.55,{\text{ }}1.47)\), the largest Lyapunov exponent is positive, so the system is in the chaotic state. When \(\alpha \in [1.47,{\text{ }}2]\), the two Lyapunov exponents are both positive, so the system can generate hyperchaotic attractors.
Figure 3b shows the Lyapunov exponents spectrum varying \(\beta\) when \(\alpha = 1\). We can see that the system exhibits the periodic behavior when \(\beta \in (0.34,{\text{ }}0.353)\). There are two positive Lyapunov exponents when \(\beta \in [0.25,{\text{ }}0.34] \cup [0.354,{\text{ 0}}{\text{.56}}]\), and the map exhibits the hyperchaotic state. The system is in chaotic attractors in the range of \(\beta \in (0.56,{\text{ }}1]\).
It can be seen that there is a one-to-one correspondence between the Lyapunov exponent spectrum and the bifurcation diagrams.
3.3 Attractor phase diagram
A chaotic system with good chaotic performance usually has complex attractors which occupy a large area in the phase diagram. Set the initial conditions \(x_{0} = 0.3\) and \(y_{0} = 0.6\); the attractor phase diagrams are generated in Fig. 4. The system generates the hyperchaotic attractors as shown in phase diagrams (Fig. 4a and b) when parameters \(\alpha = 2\), \(\beta = 1\) and \(\alpha = 1\), \(\beta = 0.5\). When parameters \(\alpha = 1\) and \(\beta = 1\), the attractor phase diagram is shown in Fig. 4c; the system generates the chaotic attractor. When parameters \(\alpha = 1\) and \(\beta = 0.35\), the system demonstrates the periodic behavior displayed in Fig. 4d.
3.4 Sensitivity analysis of initial value
A well-performing chaotic system can be extremely sensible to its initial values. A slight difference of initial value can produce a completely diverse chaotic trajectory. In order to analyze the initial sensitivity of the proposed hyperchaotic map, the initial value is varied 10–16, and the experimental outcomes are shown in Fig. 5. It is observed that the proposed hyperchaotic system has great sensitivity to the initial value.
The simulation results indicate that, compared with other two-dimensional chaotic maps, the proposed 2D hyperchaotic map has better chaotic property as shown in Table 1.
4 Cross 2D hyperchaotic map-based color image encryption and decryption algorithm
Since the proposed cross 2D hyperchaotic map has good chaotic performance, this section proposes a color image cryptographic method based on this hyperchaotic map. Figure 6 displays the flowchart for the proposed encryption scheme, which includes the substitution process and the diffusion process.
4.1 Key generation
Due to the irreversibility and strong security of the hash algorithm, we use it to generate the key of the color image encryption scheme. A 512-bit secret key K is produced by the SHA-512 hash function \(K = SHA_{{512}} ({\text{ }})\), in which the input value of this hash function is related to the plain color image to increase the security and able to resist select plaintext/ ciphertext attack. Divide the 512-bit key K into 8-bit blocks, which can be expressed as \(K{\text{ = }}k_{1} ,k_{2} ,...,k_{{64}}\). K is processed and grouped in sub-keys as follows:
4.2 Chaos-based row and column combined cycle shift scrambling
In the scrambling process, average the statistical information of the image by varying the position of the image pixels to make the image energy uniform. A chaos-based row and column combined cycle shift scrambling method is proposed:
Step 1. The image matrix is assumed to be of size M × N, that is M rows and N columns. Set the row vectors PR and column vectors PC. Process rows and columns together, there are M + N vectors.
Step 2. A chaotic sequence X1 of length M + N, a chaotic sequence X2 of length M and a chaotic sequence X3 of length N are selected. The chaotic sequences are further processed by
where ceil(x) gives back the smallest integer greater than or equal to x, and mod() represents the modular action.
Step 3. Sort the sequence \(X_{1} ^{\prime }\), record the transform position TP of each element in the chaotic series, thus the length of vector TP is M + N and the elements of TP are all non-repeating integers between 1 and M + N.
Step 4. Exchange the locations of image elements using row and column combined cycle shift by
where \(circshift(A,SHIFTSIZE)\) circularly move the data in array A using the SHIFTSIZE elements. When \(TP(i) \le M\), circularly shift the \(TP(i)\) th row by \(X_{2} ^{\prime } (j)\) elements to the right. When \(TP(i) > M\), circularly shift the \(TP(i) - M\) th column by \(X_{3} ^{\prime } (k)\) elements down.
Take an image matrix with the size of 4 × 4 as an example shown in Fig. 7, where TP = {8, 1, 4, 7, 3, 2, 5, 6}, \(X_{2} ^{\prime }\) = {3, 2, 3, 1}, \(X_{3} ^{\prime }\) = {2, 0, 1, 3}. It can be seen that the position of every pixel varies only after a single permutation.
4.3 Permutation process
Step 1. In general, the size of the color plain image P is assumed to be M × N. And there are three components in the color image: the red (R) part, the green (G) part, and the blue (B) part. Each part pixel’s value in the range of 0 to 255. Hence, one pixel can be converted into 8-bit binary value. Therefore, an M × N size color image P can be expended to three binary image matrixes Rb, Gb, and Bb with size M × 8 N. Combine the Rb, Gb, and Bb matrixes vertically and get a combined image matrix Pb with 3 × M rows, 8 × N columns. Thus, the three color image components can influence each other.
Step 2. Set the permute key \(K_{{permute}} = SHA_{{512}} (R,G,B)\), which R, G, and B are all the pixels in each color component of plain image so that different plain images will get a distinct key. Obtain the sub-keys K1, K2, K3, K4 according to Eq. (5), and the chaotic system (4) parameters and initial conditions are given:
Step 3. Iterate the chaotic system (4) 3 M + 8 N + k times, the length of the sequence discarded is k for better chaos, where \(k = \bmod (sum(R + G + B),100) + 500\), \(sum(R + G + B)\) means the sum of all these elements in three components. Get the chaotic sequences \(x(i) = \left\{ {x_{1} ,x_{2} ,...,x_{{3M + 8N}} } \right\}\) and \(y(i) = \left\{ {y_{1} ,y_{2} ,...,y_{{3M + 8N}} } \right\}\).
Step 4. Use the chaos-based row and column combined cycle shift scrambling method described in Sect. 4.2 to permute the bit-level image matrix Pb with the size of 3 M × 8 N, where the chaotic sequence X1 = \(x(i)\) (i = 1, 2,…, 3 M + 8 N), X2 = \(y(i)\) (i = 1, 2,…, 3 M), X3 = \(y(i)\) (i = 3 M + 1,…, 3 M + 8 N). A permutated bit-level image matrix \(P_{b} ^{\prime }\) is generated.
Step 5. Transform \(P_{b} ^{\prime }\) to an integer image matrix denoted as \(P^{\prime }\) with the size of 3 M × N. The position of pixels is changed as well as the value of the pixels in the permutated image \(P^{\prime }\).
4.4 Diffusion process
During the diffusion process, the pixel values of the image are altered so that small differences in a single pixel spread over a maximum number of pixels. The proposed diffusion equation is chosen according to the selecting sequence which depends on the chaotic sequence.
Step 1. Set the diffuse key \(K_{{diffuse}} = SHA_{{512}} (P^{\prime } ([i{\text{ }}j{\text{ }}k],:))\), where \(P^{\prime } ([i{\text{ }}j{\text{ }}k],:)\) is the ith row, jth row, and kth row of the permutated image matrix \(P^{\prime }\). Obtain the sub-keys K1’, K2’, K3’, K4’ according to Eq. (5), and set the initial conditions and parameters of the chaotic system (4) using Eq. (10).
Step 2. The hyperchaotic map (4) is iterated 3 M × N + k1 times, where \(k_{1} = \bmod (sum(sum(P^{\prime } (:,i:j))),100) + 500\), \(P^{\prime } (:,i:j)\) is the ith to jth columns of \(P^{\prime }\). Discard the former k values of the chaotic sequences. Get the chaotic series \(x^{\prime}(i) = \left\{ {x_{1} ^{\prime } ,x_{2} ^{\prime } ,...,x^{\prime}_{{3M \times N}} } \right\}\) and \(y^{\prime}(i) = \left\{ {y_{1} ^{\prime } ,y_{2} ^{\prime } ,...,y^{\prime}_{{3M \times N}} } \right\}\).
Step 3. The selecting sequence \(S(i) = \left\{ {s_{1} ,s_{2} ,...,s_{{3M \times N}} } \right\}\) and the diffusion sequence \(D(i) = \left\{ {d_{1} ,d_{2} ,...,d_{{3M \times N}} } \right\}\) can be obtained using Eqs. (11) and (12)
Step 4. According to the chaotic-based selecting diffusion equations below, the encrypted combined image pixel matrix \(C^{\prime}(i) = \left\{ {c^{\prime}_{1} ,c^{\prime}_{2} ,...,c^{\prime}_{{3M \times N}} } \right\}\) can be acquired out of the diffusion matrix D and the permutation image \(P^{\prime }\).
where \(\oplus\) denotes bit-level XOR operator.
Step 5. Vertical transformation \(C^{\prime}\) into the R, G, and B color matrix to get its cipher color image C in size of M × N.
4.5 Decryption algorithm
The decryption method is the reverse of the encryption method using the permute key \(K_{{permute}}\) and the diffuse key \(K_{{diffuse}}\) provided in the encryption algorithm, which means \(K_{{permute}}\) and \(K_{{diffuse}}\) should be provided and known in the decryption method.
Step 1. Obtain the cipher image C and convert it to the R, G, and B color components’ matrix. Combine the color matrixes vertically and get a combined encrypted image matrix \(C^{\prime }\) with 3 × M rows, N columns.
Step 2. Use the same diffuse key \(K_{{diffuse}}\) as the encryption algorithm to obtain the same selecting sequence \(S(i)\) and the diffusion sequence \(D(i)\).
Step 3. The matrix \(C_{D}\) can be attained using the inverse diffusion formula equation below from the diffusion matrix D and the encrypted image matrix \(C^{\prime }\).
Step 4. Extended the matrix \(C_{D}\) to its binary image matrixes \(C_{{Db}}\). Use the same permute key \(K_{{permute}}\) as the encryption algorithm to obtain the same chaotic sequences X1, X2, and X3 in the encryption permutation process.
Step 5. The matrix \(C_{P}\) can be acquired using the reverse row and column combined cycle shift scrambling Eq. (15) to reverse permute the bit-level image matrix \(C_{{Db}}\).
Step 6. Transform \(C_{P}\) to an integer image matrix denoted as \(C_{I}\) which its size is 3 M × N. Convert \(C_{I}\) into the R, G, and B color matrix vertically to obtain the decrypted image.
5 Experimental results and performance analysis
The experimental results and performance of the algorithm are analyzed. To verify the effectiveness of the cryptographic system, a number of images were simulated numerically.
The chosen sample images are the different sizes color images of 256 × 256 House, 500 × 480 Baboon, 512 × 512 Lena, 512 × 512 Peppers, 720 × 576 Barbara, and 768 × 512 Parrots. Figure 8 illustrates the experimental simulation performance of the House, Baboon, Lena, Barbara, and Parrots images. The encrypted images are comparable to the image of noise with no visual leakage of information.
5.1 Keyspace analysis
The encryption algorithm with larger keyspace are better able to resist brute-force assaults and have higher degree of security. In this method, the key contains the initial conditions \(x_{0}\), \(y_{0}\), \(x_{0} ^{\prime }\), \(y_{0} ^{\prime }\), parameters \(\alpha\), \(\beta\), \(\alpha ^{\prime}\), \(\beta ^{\prime}\) and the discard length k, k1 of the hyperchaotic system in the permutation and diffusion processes. Because the computational precision is 10–16, the size of the keyspace for one round encryption is \(10^{{16 \times 8}} > 2^{{425}}\) which is much bigger than \(2^{{100}}\) to guarantee the security according to [39]. So the keyspace is sufficiently large to defend against any violent attack.
5.2 Key sensitivity analysis
For the high-security image encryption algorithm, key sensitivity is an essential feature. A slightly different key used in encryption will generate a radically altered cryptographic image. And minor changes in the key used for decryption will cause decryption failure. The encryption and decryption keys are changed 10–16 to analyze the key sensitivity of the proposed scheme. Figure 9 displays the experimental performance of the key sensitivity. Any small modification in the encryption key will lead to a totally distinct encrypted image. A minor alteration in a key will produce an entirely different image, and the correct decrypted image will not be available.
5.3 Histogram
The image histogram reveals information about the distribution of pixel values. To prevent statistical analysis attacks from recovering any meaningful message from the histogram of a cryptographic image, the cryptographic image needs to be uniformly distributed. Figure 10 shows the histograms of the plain images and the relevant cryptographic images. As shown in Fig. 10, the histogram allocation of the cryptographic images is uniform, which makes it very hard for any attacker to analyze the cryptographic image through a statistically analysis attack.
5.4 Correlation of adjacent pixels
The correlation between the neighboring pixels is at a high degree in a plain image, which may reveal the attacker's statistical information. Therefore, encrypted images should minimize the correlation between the adjacent pixels. For each pair, the correction factor is computed using the equation below.
where \(E(x) = \frac{1}{N}\sum\limits_{{i = 1}}^{N} {x_{i} }\), \(D(x) = \frac{1}{N}\sum\limits_{{i = 1}}^{N} {(x_{i} - E(x))^{2} }\), \(\text{cov} (x,y) = \frac{1}{N}\sum\limits_{{i = 1}}^{N} {(x_{i} - E(x))(y_{i} - E(y))}\), x and y are gray-scale values of two neighboring pixels in the image.
The distribution of the correlation between the color components of the original Lena image and the encrypted image in horizontal, vertical, and diagonal adjacent pixels are shown in Fig. 11. The correlation results between the adjacent pixels of the test images are provided in Table 2. From the figure and table, it can be observed that the correlation between neighboring pixels of the encrypted image satisfies zero correlation by effectively encrypt the image, indicating that the encryption method provides promising security.
5.5 Information entropy analysis
Information entropy can be applied to quantitatively quantify and calculate the information source’s randomness. The entropy \(H(m)\) of a signal source m could be calculated using the following equation:
where \(p(m_{i} )\) denotes the symbol \(m_{i}\)’s probability represents the probability of symbol and the entropy is represented in bits. The information entropy is 8 for an ideal completely random image.
Table 3 calculates the information entropy of the encrypted images and compares them with those of other methods. The information entropy of the encrypted image is quite near to the theory value 8, which implies that the information disclosure during encryption is ignorable and that the cryptosystem is secure.
5.6 Differential attack
A safe image cryptography method is supposed to be extremely sensible to any small changes in the plain image, implying that a single pixel variation in the plain image will result in a totally distinct encrypted image.
The differential attack is tested using the uniform average change intensity (UACI) and the number of pixels change rate (NPCR). The following formulas are used to calculate NPCR and UACI:
where M and N denote the rows and columns of the image, C1 and C2 are the encrypted images before and after a pixel change of the plain image, respectively.
We randomly vary the one-bit value of the pixel among any color component, and then evaluate NPCR and UACI in the red, green, and blue components. Table 3 lists the NPCR and UACI performance of this algorithm and compares them with other methods. It can be observed from Table 4 that the NPCR and UACI results are quite near to the theoretical values, and the cryptosystem is effective against both plaintext and differential attacks.
5.7 Noise and data loss attacks
Image data are vulnerable to disturbance and data damage during the transmission process. A highly secure image cryptography algorithm is supposed to be resistant to disturbance and data loss attacks. Different densities of salt and pepper noise are added to the encrypted Lena images. From Fig. 12, it is visible that the decrypted image can be still restored with success and the noise cannot stop us to identify the decrypted image content visually.
The encrypted image of the lost data and the corresponding decrypted image are illustrated in Fig. 13. Results of the experiments show that the more the image is lost, the more unclear the image is decrypted. However, the image can still be decrypted and recognized although the image is half lost. The algorithm is highly robust to noise attacks and information loss attacks.
5.8 Running Performance
To satisfy the fast increase in image data capacity, image cryptography methods should be fast and efficient. In the proposed algorithm, all pixels in the three color components can be completely shuffled through one operation of row and column combined cycle shift scrambling. And it requires only a single turn of permutation and diffusion to realize high security. So our proposed algorithm can exhibit rapid encryption speed.
To analyze the calculation complexity of the proposed scheme, assume that the size of the color plain image is M × N. In the permutation process, the time complexity is O(3 M + 8 N). During the diffusion process, the complexity of time is O(M × N × 3). Therefore, the time complexity of the proposed method is O(M × N).
To calculate the properties of this method, MATLAB R2017a with Intel(R) Core (TM) i5-8300H CPU@2.30 GHz and 4.0G RAM on Windows 10 OS were utilized. Table 5 lists the running time of the proposed encrypting images. When encryption and decryption of different color images with different sizes, the program can achieve good running performance within a few seconds.
Table 6 indicates the running time of the proposed algorithm compares with other methods when encrypt and decrypt color images of size 512 × 512. Although the experimental environments are different, our proposed algorithm shows relatively good efficiency compared with the similar environment algorithms. It shows that our proposed algorithm is preferred for real-time applications due to its performance in encryption and decryption speed.
6 Conclusion
This paper designed a cross 2D hyperchaotic map, which is constructed using one nonlinear function and two chaotic maps with cross structure. Numerous experiments such as bifurcation diagrams, Lyapunov exponent spectra, and phase portraits are carried out to illustrate the complex chaotic behavior of the proposed hyperchaotic system. The simulation outcomes show that this nonlinear crossed two-dimensional hyperchaotic system provides good chaotic performance. In the color image encryption algorithm, the keys are generated using hash function SHA-512 and the information of the plain color image. First, the color plain image is converted to a combined bit-level matrix and permutated by the chaotic-based row and column combined cycle shift scrambling method. Then, the scrambled integer matrix is diffused according to the selecting sequence. The cipher color image is obtained by decomposed the diffused matrix. The proposed encryption algorithm makes the three color components of color image affect one another to eliminate the correlations between them. Through the comparison of encryption performance, this proposed algorithm has been proven to have enough keyspace, a sensitive key, resistance to statistical attacks and differential attacks, and is applicable for real-time implementations.
Data availability
Data sharing is not applicable to this article as no datasets were generated or analyzed during the current study.
References
Xiong, Z.G., Wu, Y., Ye, C.H., Zhang, X.M., Xu, F.: Color image chaos encryption algorithm combining CRC and nine palace map. Multimed. Tools Appl. 78(22), 31035–31055 (2019)
Sneha, P.S., Sankar, S., Kumar, A.S.: A chaotic colour image encryption scheme combining Walsh-Hadamard transform and Arnold-Tent maps. J. Ambient. Intell. Humaniz. Comput. 11(3), 1289–1308 (2020)
Kaur, G., Agarwal, R., Patidar, V.: Color image encryption scheme based on fractional Hartley transform and chaotic substitution-permutation. Vis. Comput., (3):1–24, (2021).
Chai, X., Bi, J., Gan, Z., et al.: Color image compression and encryption scheme based on compressive sensing and double random encryption strategy. Signal Process. 176, 107684 (2020)
Pak, C., An, K., Jang, P., et al.: A novel bit-level color image encryption using improved 1D chaotic map. Multimed. Tools Appl. 78, 12027–12042 (2019)
Zhou, J., Zhou, N.R., Gong, L.H.: Fast color image encryption scheme based on 3D orthogonal Latin squares and matching matrix. Opt. Laser Technol. 131, 106437 (2020)
Wang, L., Ran, Q., Ma, J.: Double quantum color images encryption scheme based on DQRCI. Multimed. Tools Appl. 79(9–10), 6661–6687 (2020)
Li, Z., Peng, C., Tan, W.: A novel chaos-based color image encryption scheme using bit-level permutation. Symmetry 12(9), 1497 (2020)
Zhang, Y.Q., He, Y., Li, P., et al.: A new color image encryption scheme based on 2DNLCML system and genetic operations. Opt. Lasers Eng. 128, 106040 (2020)
Wen, W., Wei, K., Zhang, Y., et al.: Colour light field image encryption based on DNA sequences and chaotic systems. Nonlinear Dyn. 99(2), 1587–1600 (2020)
Kang, X., Guo, Z.: A new color image encryption scheme based on DNA encoding and spatiotemporal chaotic system. Signal Process. Image Commun. 80, 115670 (2020)
Wang, S.C., Wang, C.H., Xu, C.: An image encryption algorithm based on a hidden attractor chaos system and the Knuth-Durstenfeld algorithm. Opt. Lasers Eng. 128, 105995 (2020)
Nestor, T., Kengne, J., Abd-El-Atty, B., et al.: Design and implementation of a simple dynamical 4-D chaotic circuit with applications in image encryption. Inf. Sci. 515, 191–217 (2020)
Wang, X.Y., Gao, S.: Image encryption algorithm for synchronously updating Boolean networks based on matrix semi-tensor product theory. Inf. Sci. 507, 16–36 (2020)
Farah, M.A.B., Guesmi, R., Kachouri, A., et al.: A Novel Chaos Based Optical Image Encryption Using fractional Fourier transform and DNA Sequence Operation. Opt. Laser Technol. 121, 105777 (2019)
Xian, Y.J., Wang, X.Y., Yan, X.P., Li, Q., Wang, X.Y.: Image encryption based on chaotic sub-block scrambling and chaotic digits selection diffusion. Opt. Lasers Eng. 134, 106202 (2020)
He, Y., Zhang, Y.Q., Wang, X.Y.: A new image encryption algorithm based on two-dimensional spatiotemporal chaotic system. Neural Comput. Appl. 32, 247–260 (2020)
Liu, H., Zhang, Y., Kadir, A., et al.: Image encryption using complex hyper chaotic system by injecting impulse into parameters. Appl. Math. Comput. 360, 83–93 (2019)
Wang, X.Y., Feng, L., Li, R., Zhang, F.C.: A fast image encryption algorithm based on non-adjacent dynamically coupled map lattice model. Nonlinear Dyn. 95(4), 2797–2824 (2019)
Wang, X.Y., Sun, H.H.: A chaotic image encryption algorithm based on improved Joseph traversal and cyclic shift function. Opt. Laser Technol. 122, 105854 (2020)
Zhu, C., Sun, K.: Cryptanalyzing and Improving a novel color image encryption algorithm using rt-enhanced chaotic tent maps. IEEE Access 6, 18759–18770 (2018)
Farajallah, M., Assad, S.E., Deforges, O.: Cryptanalyzing an image encryption scheme using reverse 2-dimensional chaotic map and dependent diffusion. Multimed. Tools Appl. 77(21), 28225–28248 (2018)
Ge, X., Lu, B., Liu, F., et al.: Cryptanalyzing an image encryption algorithm with compound chaotic stream cipher based on perturbation. Nonlinear Dyn. 90(2), 1141–1150 (2017)
Wen, H., Yu, S., Lü, J.H.: Breaking an image encryption algorithm based on DNA encoding and spatiotemporal chaos. Entropy 21(3), 246 (2019)
Rössler, O.E.: An equation for hyperchaos. Phys. Lett. A 71, 155–157 (1979)
Zhu, S.Q., Zhu, C.X.: Secure image encryption algorithm based on hyperchaos and dynamic DNA coding. Entropy 22(7), 772 (2020)
Xu, C., Sun, J., Wang, C.: An image encryption algorithm based on random walk and hyperchaotic systems. Int J Bifurcation Chaos 30(4), 2129–2151 (2020)
Bouslehi, H., Seddik, H.: Innovative image encryption scheme based on a new rapid hyperchaotic system and random iterative permutation. Multimed. Tools Appl. 77(23), 1–23 (2018)
Cheng, G., Wang, C., Chen, H.: A novel color image encryption algorithm based on hyperchaotic system and permutation-diffusion architecture. Int. J. Bifurcation Chaos 29(09), 1950115 (2019)
Kaur, M., Singh, D., Sun, K., et al.: Color image encryption using non-dominated sorting genetic algorithm with local chaotic search based 5D chaotic map. Futur. Gener. Comput. Syst. 107, 333–350 (2020)
Zhou, M., Wang, C.: A novel image encryption scheme based on conservative hyperchaotic system and closed-loop diffusion between blocks. Signal Process. 171, 107484 (2020)
Ouyang, X., Luo, Y., Liu, J., et al.: A color image encryption method based on memristive hyperchaotic system and DNA encryption. Int. J. Mod. Phys. B 34(4), 2050014 (2020)
Hua, Z.Y., Zhou, Y.C., Pun, C.M., Chen, C.L.P.: 2D sine logistic modulation map for image encryption. Inf. Sci. 297, 80–94 (2015)
Hua, Z.Y., Zhou, Y.C.: Image encryption using 2D Logistic-adjusted-Sine map. Inf. Sci. 339, 237–253 (2016)
Liu, W., Sun, K., et al.: A fast image encryption algorithm based on chaotic map. Opt. Lasers Eng. 84, 26–36 (2016)
Cao, W., Mao, Y., Zhou, Y.: Designing a 2D infinite collapse map for image encryption. Signal Process. 171, 107457 (2020)
Wang, M.X., Wang, X.Y., Zhao, T.T., Zhang, C., Xia, Z.Q., Yao, N.M.: Spatiotemporal chaos in improved Cross Coupled Map Lattice and its application in a bit-level image encryption scheme. Inf. Sci. 544, 1–24 (2021)
He, D., He, C., Jiang, L.G., et al.: Chaotic characteristics of a one-dimensional iterative map with infinite collapses. IEEE Trans. Circuits Syst. I Fundament. Theory Appl. 48(7), 900–906 (2001)
Alvarez, G., Li, S.: Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurcation Chaos 16(8), 2129–2151 (2006)
Funding
The work is funded by the Postdoctoral Research Foundation of China (No: 2020M680933), the National Natural Science Foundation of China (Nos: 61701070, 61672124), the Doctoral Start-up Foundation of Liaoning Province (No: 2018540090), Key R&D Projects of Liaoning Province (No: 2019020105-JH2/103), Liaoning Province Science and Technology Innovation Leading Talents Program Project (No: XLYC1802013), Research Fund of Guangxi Key Lab of Multi-source Information Mining & Security (No: MIMS20-M-02), Jinan City ‘20 universities’ Funding Projects Introducing Innovation Team Program (No: 2019GXRC031).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Teng, L., Wang, X., Yang, F. et al. Color image encryption based on cross 2D hyperchaotic map using combined cycle shift scrambling and selecting diffusion. Nonlinear Dyn 105, 1859–1876 (2021). https://doi.org/10.1007/s11071-021-06663-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-021-06663-1