Abstract
The rapidly evolving communication technology has now made it easy for people to enjoy kinds of online services over the insecure public internet. However, with convenience, ensuring data security as well as user privacy and authentication is particularly important and urgent. In view of this, this work presents a new biometrics-based three-factor authentication with key agreement scheme for multi-server environment using ECC. The formal authentication proof using BAN logic confirms that the new scheme can achieve mutual authentication and agree on a common session key; and the heuristic cryptanalysis shows that the new scheme provides perfect forward secrecy, preserves user anonymity and secures against various known security vulnerabilities. Furthermore, the performance evaluation demonstrates that our scheme is efficient.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The advancement of network and communication technologies has brought more and more offline services online, and people are now enjoying high-efficiency online services such as e-health, e-commerce and e-government, etc. However, these online services are provided over the insecure public internet, where adversaries can easily perform some attacks, like privacy violating, impersonation attack, replay attack, man-in-the-middle attack, etc. To deal with these security challenges, authentication with session key agreement protocol is deployed to ensure that only certified users can enjoy services, only the legitimate service providers can be accessed, and the exchanged critical information is secured by encryption with the negotiated session key.
1.1 Related works
In recent years, numerous authentication schemes have been designed to maintain secure communications between the remote users and the servers over the internet. Many smart-card based two-factor authentication schemes [4, 8, 9, 12, 17, 20, 21, 23, 24] were proposed in which the elliptic curve cryptography (ECC) was applied to establish security since ECC can provide the same level of security with far less key size and faster computing speed. However, all these schemes are only applicable to single-server environment and many of them have been found vulnerable to various attacks. Compared with single-server environment, multi-server environment has the obvious advantage that it enables users to access various application servers with one account. To adapt to the security requirements of multi-server environment, several kinds of authentication schemes [1, 3, 5, 6, 10, 11, 13, 15, 16, 18, 19, 22, 25] with respect to multi-server environment have therefore been presented.
In 2013, Yoon and Yoo [25] presented a biometrics-based multi-server authentication scheme using ECC, while Kim et al. [15] proved that this scheme is prone to the offline password guessing attack, and an improvement for this scheme was presented. Later, Chuang et al. [6] came up with an anonymous biometrics-based authentication scheme with respect to multi-server environment, while Mishra et al. [18] soon proved that this scheme was prone to the server spoofing, smart-card stolen and impersonation attacks, and they put forward a new scheme. However, Lu et al. [16] soon proved that Mishra et al.’s new scheme was not to secure against the forgery and server masquerading attacks, and they redesigned an authentication scheme for multi-server environment using asymmetric cryptography. Nevertheless, Lu et al.’s new scheme was soon identified by Chaudhry et al. [5] to be vulnerable to the impersonation attack.
Afterwards, Odelu et al. [19] put forward a new biometrics-based multi-server authentication scheme on the basis of He and Wang’s scheme [10] with the aim to eliminate its security weaknesses. Later, Shen et al. [22] came up with a multi-server authentication scheme not preserving user anonymity. Later, Amin et al. [1] proposed an anonymity preserving authentication scheme for multi-server telemedicine information system using ECC, but very recently, their scheme was found by Irshad et al. [11] to be vulnerable to the offline password guessing and impersonation attacks. Recently, Chandrakar and Om [3] presented an anonymous three-factor authentication scheme for multi-server environment using ECC; and Jangirala et al. [13] presented a dynamic identity based multi-server authentication scheme. However, like the schemes [6, 18], Jangirala et al.’s scheme doesn’t employ asymmetric cryptographic primitives to ensure security either. Thus, it fails to provide the forward secrecy.
1.2 Motivation and contributions
By investigating the related existing schemes, it can be found that various weaknesses are still within many of them. To ensure that remote users can enjoy online services and exchange critical data securely, this work designs a new robust biometrics-based authentication scheme based on previous researches for multi-server environment. The proposed scheme preserves user’s biometrics template privacy by employing the fuzzy extractor [7], and the formal authentication proof by Burrows-Abadi-Needham (BAN) logic [2] shows that the new scheme can effectively realize mutual authentication and agree on a common session key. Besides, the heuristic security discussion in this paper demonstrates that our scheme can preserve user anonymity, provide perfect forward secrecy and protect users from various known security loopholes such as impersonation attack, replay attack, denial of service attack, and offline password guessing attack, etc. In addition, since our scheme has the advantage in network architecture design, i.e. the registration center in our scheme will no longer participate in the subsequent user-server session key negotiation processes after completing the user authentication, thus greatly reducing computation and communication costs in the authentication with key agreement phase. Hence, besides the security attributes, our new scheme has advantages over other relevant schemes in terms of computation and communication costs.
1.3 Organizations
The rest of this article is arranged as follows. Section 2 describes the necessary preliminaries. Section 3 introduces our new biometrics-based authentication with key agreement scheme for multi-server environment. The authentication proof by BAN logic is presented in Section 4; the security analysis of the proposed scheme is presented in Section 5; and the performance evaluation is presented in Section 6. Finally, conclusions are given in Section 7.
2 Preliminaries
This section briefly lists the notations used throughout this work, and introduces the essential notion and definitions of ECC and the fuzzy extractor.
2.1 Notation guide
The meaning of the frequently used notations in this paper is shown in Table 1.
2.2 Elliptic curve over a prime field F p
Let the symbol Ep(a, b) denote an elliptic curve E over a prime finite field Fp, defined by the non-singular elliptic curve equation: y2 = x3 + ax + b mod p, a, b ∈ Fp with the discriminant: ∆ = 4a3 + 27b2mod p ≠ 0. That is,  .
.
The scalar multiplication over Ep(a, b) defined as tP = P + P + ⋯ + P (t times).
A point P has order n if \( nP=\mathcal{O} \) for the smallest integer n > 0, where \( \mathcal{O} \) is the extra point called infinity point.
Definition 1
Elliptic curve discrete logarithm problem (ECDLP) is defined as follows: Given P ∈ Ep(a, b) with order n and Q = kP ∈ Ep(a, b), it is infeasible to derive the integer k ∈ [1, n − 1].
Definition 2
Computational Diffie-Hellman problem (CDHP) is defined as follows: Given P, aP, bP ∈ Ep(a, b), it is intractable to compute abP ∈ Ep(a, b).
2.3 Fuzzy extractor
Fuzzy extractor [7] is used to extract a uniform random string σi from the inputted biometrics template Bi in an error-tolerant way, which means σi can be derived each time with a noisy biometrics template \( {B}_i^{\ast } \) and an auxiliary string θi if \( {B}_i^{\ast } \) is reasonably similar to the original Bi. A fuzzy extractor comprises two procedures, namely, the probabilistic generation procedure Gen and the deterministic reproduction procedure Rep. More concrete descriptions are as follows:
-
(1)
(σi, θi) = Gen(Bi) means when receiving the inputted biometrics Bi, Gen outputs a uniform random string σi and an auxiliary string θi.
-
(2)
\( {\sigma}_i= Rep\left({B}_i^{\ast },{\theta}_i\right) \) means Rep can recover σi with the noisy biometrics \( {B}_i^{\ast } \) and the corresponding random auxiliary string θi when \( dis\left({B}_i^{\ast },{B}_i\right)<\Delta t \), where dis represents the distance function and ∆t is the error threshold.
3 Our proposed scheme
This section presents our new biometrics-based authentication with key agreement protocol for multi-server environment, which comprises the following four phases.
3.1 System initialization phase
The registration center RC first takes the following steps to initialize the system parameters.
-
(1)
RC selects an non-singular elliptic curve Ep(a, b) with a large prime order n, and a base point G with the order n over Ep(a, b).
-
(2)
RC selects two cryptographic hash functions: \( H:{\left\{0,1\right\}}^{\ast}\to {Z}_p^{\ast } \), \( h:{\left\{0,1\right\}}^{\ast}\to {Z}_p^{\ast } \).
-
(3)
RC generates its private key \( x\in {Z}_n^{\ast } \) which should be kept secret strictly, and then computes its public key Ppub = x ∙ G.
-
(4)
RC publishes the system parameters {Ep(a, b), G, n, Ppub, H(∙), h(∙)}.
3.2 Registration phase
The registration phase of our scheme comprises the following two phases.
3.2.1 Server registration phase
To deploy a new server Sj to be a legal server, the following steps also shown in Fig. 1 need to be executed.
-
(1)
Sj selects its identity SIDj and transmits it to RC via a secure channel.
-
(2)
RC generates a random number rj and computes the secret key kj = h(SIDj‖x‖rj), then stores {SIDj, rj} into its security database and transmits kj back to Sj via a secure channel, where x is the system private key.
-
(3)
Upon receiving kj, Sj keeps it secretly.
3.2.2 User registration phase
To be a legal user, Ui needs to take the following steps also shown in Fig. 2, to register in RC.
-
(1)
Ui inputs his/her identity IDi, pwi and imprints Bi on a sensor.
-
(2)
Ui computes (σi, θi) = Gen(Bi), MPi = h(pwi‖σi) and transmits IDi, MPi to RC by a secure channel.
-
(3)
Upon receiving IDi and MPi, RC checks the validity of IDi and whether h(IDi) exists in RC’s user database. If not, RC stores h(IDi) in its user database and computes ri = h(IDi‖x) ki = ri ⊕ MPi, vi = H(IDi‖ri‖MPi), where x is the system private key, and then RC stores {ki,vi, H(∙),h(∙)} into a smart-card SCi and returns it back to Ui; otherwise RC aborts the procedure.
-
(4)
After receiving SCi, Ui stores θi into SCi.
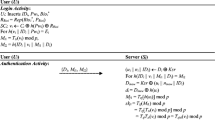
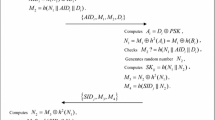
3.3 Login and mutual authentication with key agreement phase
Assume that a remote user Ui wants to enjoy online services from Sj, then, he/she needs to perform the following steps to accomplish the mutual authentication processes and agree on a session key for encrypting the subsequent communications over the insecure public channel as shown in Fig. 3.
-
(1)
Ui inserts his/her smart-card SCi into a card reader, then inputs IDi, pwi, and imprints Bi at a sensor.
-
(2)
SCi computes σi = Rep(Bi, θi), \( {MP}_i^{\prime }=h\left({pw}_i\Big\Vert {\sigma}_i\right) \), \( {r}_i={k}_i\oplus {MP}_i^{\prime } \), and checks whether \( {v}_i=H\left({ID}_i\left\Vert {r}_i\right\Vert {MP}_i^{\prime}\right) \) holds. If not, SCi rejects Ui, otherwise, SCi generates a random number α to compute X = α ∙ G, K = α ∙ Ppub, k = h(K), c1 = Ek(SIDj‖IDi‖H(ri‖X‖t1)), where t1 is the current timestamp of Ui, and sends {c1,X,t1} to RC.
-
(3)
Upon receiving the message {c1,X,t1}, RC gets its current timestamp \( {t}_1^{\prime } \) and checks whether \( {t}_1^{\prime }-{t}_1<\Delta t \) holds. If not, RC aborts the procedure, otherwise, RC computes K′ = x ∙ X, k′ = h(K′), \( {SID}_j^{\prime}\left\Vert {ID}_i^{\prime}\right\Vert {H}^{\prime}\left({r}_i\left\Vert X\right\Vert {t}_1\right)={D}_{k^{\prime }}\left({c}_1\right) \), \( {r}_i^{\prime }=H\left({ID}_i^{\prime}\Big\Vert x\right) \) and checks whether \( {H}^{\prime}\left({r}_i\left\Vert X\right\Vert {t}_1\right)=H\left({r}_i^{\prime}\left\Vert X\right\Vert {t}_1\right) \) holds. If not, RC aborts the procedure; otherwise, RC retrieves the random number rj by \( {SID}_j^{\prime } \) and computes \( {k}_j=h\left({SID}_j^{\prime}\left\Vert x\right\Vert {r}_j\right) \), \( che=H\left({ID}_i^{\prime}\left\Vert H\left({r}_i^{\prime}\right)\right\Vert X\right) \), \( {c}_2={E}_{k_j}\left({SID}_j^{\prime}\left\Vert {ID}_i^{\prime}\right\Vert H\left({r}_i^{\prime}\right)\left\Vert X\right\Vert che\Big\Vert {t}_2\right) \) and sends {c2,t2} to Sj.
-
(4)
Upon receiving the message {c2,t2}, Sj gets its current timestamp \( {t}_2^{\prime } \) and checks whether \( {t}_2^{\prime }-{t}_2<\Delta t \) holds. If not, Sj aborts the procedure, otherwise, computes \( {SID}_j^{\prime}\left\Vert {ID}_i^{\prime}\right\Vert H\left({r}_i^{\prime}\right)\left\Vert X\right\Vert {che}^{\prime}\Big\Vert {t}_2^{\prime }={D}_{k_j}\left({c}_2\right) \) and checks whether \( {t}_2^{\prime }={t}_2 \) and \( {che}^{\prime }=H\left({ID}_i^{\prime}\left\Vert H\left({r}_i^{\prime}\right)\right\Vert X\right) \) hold. If not, Sj aborts the procedure, otherwise, generates a random number β to compute Y = β ∙ G, Z = β ∙ X, \( {SK}_s=h\left({ID}_i^{\prime}\left\Vert {SID}_j\right\Vert H\left({r}_i^{\prime}\right)\left\Vert X\right\Vert Y\Big\Vert Z\right) \), \( {V}_j=H\left({SK}_s\left\Vert H\left({r}_i^{\prime}\right)\right\Vert X\left\Vert Y\right\Vert {t}_3\right) \) where t3 is the current timestamp of Sj, and sends {Vj,Y,t3} to Ui.
-
(5)
Upon receiving the message {Vj,Y,t3}, Ui gets its current time stamp \( {t}_3^{\prime } \) and checks whether \( {t}_3^{\prime }-{t}_3<\Delta t \) holds. If not, Ui aborts the procedure, otherwise, computes Z = α ∙ Y, SKi = h(IDi‖SIDj‖H(ri)‖X‖Y‖Z) and checks Vj ? = H(SKi‖H(ri)‖X‖Y‖t3); if not, Ui aborts the procedure, otherwise, accepts SK = h(IDi‖SIDj‖H(ri)‖X‖Y‖Z) as the session key, then, computes Vi = H(SKi‖H(ri)‖Y) and sends {Vi} to Sj.
-
(6)
Upon receiving the message {Vi}, Sj checks \( {V}_i?=H\left({SK}_s\left\Vert H\left({r}_i^{\prime}\right)\right\Vert Y\right) \). If not, Sj aborts the procedure, otherwise, Sj accepts SK = h(IDi‖SIDj‖H(ri)‖X‖Y‖Z) as the session key for subsequent communications.
3.4 Password change phase
A legal user Ui may for security reasons need to change the old password pwi, and then, he/she just needs take the following steps without connecting to RC or Sj.
-
(1)
Ui inserts his/her smart card SCi into a card reader, then inputs IDi, pwi and imprints Bi at a sensor.
-
(2)
SCi computes σi = Rep(Bi, θi), \( {MP}_i^{\prime }=h\left({pw}_i\Big\Vert {\sigma}_i\right) \), \( {r}_i={k}_i\oplus {MP}_i^{\prime } \), and checks whether \( {v}_i=H\left({ID}_i\left\Vert {r}_i\right\Vert {MP}_i^{\prime}\right) \) holds. If not, SCi rejects Ui; otherwise, SCi asks Ui to input new password \( {pw}_i^{\ast } \).
-
(3)
Upon receiving \( {pw}_i^{\ast } \), SCi computes \( {MP}_i^{\ast }=h\left({pw}_i^{\ast}\Big\Vert {\sigma}_i\right) \), \( {k}_i^{\ast }={k}_i\oplus {MP}_i\oplus {MP}_i^{\ast } \), \( {v}_i^{\ast }=H\left({ID}_i\left\Vert {r}_i\right\Vert {MP}_i^{\ast}\right) \) and replaces ki, vi with \( {k}_i^{\ast } \), \( {v}_i^{\ast } \), respectively.
4 Authentication proof by BAN logic
This section formally proves that our new scheme can achieve mutual authentication with session key agreement by BAN logic [2]. Detailed proof is as follows.
-
BAN logic notations:
-
P ∣ ≡ X: The principal P believes X.
-
#(X): The formula X is fresh.
-
P ⇒ X: P has jurisdiction over X.
-
P ∣ ~X: P once said the statement X.
-
P ∣ ⊲ X: P sees the statement X.
-
(X, Y): X or Y is one part of the (X, Y).
-
{X}K: X is encrypted with the key K.
-
(X)K: X is hashed with the key K.
-
⟨X⟩K: X is combined with the key K.
-
\( P\overset{K\kern0.5em }{\leftrightarrow }Q: \)P and Q use the shared session key K to communicate, and K will never be discovered by any principal except P and Q.
-
BAN logic rules:
-
Rule(1) : Message-meaning rule: \( \frac{P\mid \equiv P\overset{K\kern0.5em }{\leftrightarrow }Q,\kern0.75em P\mid \vartriangleleft {\left\{X\right\}}_K\ }{P\left|\equiv Q\right|\sim X} \)
-
Rule(2) : Nonce-verification rule: \( \frac{P\mid \equiv \#(X),\kern0.75em P\mid \equiv Q\mid \sim X\ }{P\mid \equiv Q\mid \equiv X} \)
-
Rule(3) : Jurisdication rule: \( \frac{P\mid \equiv Q\Rightarrow X,\kern0.75em P\mid \equiv Q\mid \equiv X\ }{P\mid \equiv X} \)
-
Rule(4) : Freshness-conjuncatenation rule: \( \frac{P\mid \equiv \#(X)\ }{P\mid \equiv \#\left(X,\kern0.75em Y\right)} \)
-
Establishment of security goals:
-
Goal 1: \( {S}_j\mid \equiv {U}_i\overset{H\left({r}_i\right)\ }{\leftrightarrow }{S}_j \).
-
Goal 2: \( {U}_i\left|\equiv {S}_j\right|\equiv {U}_i\overset{SK_s\ }{\leftrightarrow }{S}_j \).
-
Goal 3: \( {U}_i\mid \equiv {U}_i\overset{SK_s\ }{\leftrightarrow }{S}_j \).
-
Goal 4: \( {S}_j\left|\equiv {U}_i\right|\equiv {U}_i\overset{SK_i\ }{\leftrightarrow }{S}_j \).
-
Goal 5: \( {S}_j\mid \equiv {U}_i\overset{SK_i\ }{\leftrightarrow }{S}_j \).
-
Idealized the proposed scheme
-
Hypotheses of the proposed scheme
-
The proof of our proposed scheme
-
According to M2, we have
-
According to S1, H5 and Rule(1), we have
-
According to S2, H3, Rule(4) and Rule(2), we have
-
According to S3, we have
-
According to S4, H6 and Rule(3), we have
-
According to M3, we have
-
According to S6, H4 and Rule(1), we have
-
According to H1, Rule(4), S7 and Rule(2), we have
-
According to S8, we have
-
According to H7, S9 and Rule(3), we have
-
According to M4, we have
-
According to S5, S11 and Rule(1), we have
-
According to H2, Rule(4), S12 and Rule(2), we have
-
According to S13, we have
-
According to H8, S14 and Rule(3), we have
5 Security analysis
This section demonstrates how our scheme accomplishes perfect security requirements and resists all well known attacks in the heuristic way. Detailed analysis is as follows.
5.1 Perfect forward secrecy
The negotiated session key is SK = h(IDi‖SIDj‖H(ri)‖X‖Y‖Z) in our scheme, where X = α ∙ G, Y = β ∙ G, Z = αβ ∙ G, α and β are randomly generated in every session by Ui and Sj respectively. If an adversary A tries to derive α and β by X = α ∙ G and Y = β ∙ G, then A has to resolve the ECDLP, which is well-known impossible. Meanwhile, the session key SK is obviously independent of the system private key x, so even if x is leaked to A, he/she cannot get any information about the former established session keys. Thus, our scheme provides perfect forward secrecy.
5.2 User anonymity
In our scheme, Ui’s original identity IDi together with other parameters are first encrypted by k and transmitted to RC, where k = h(K) and K = α ∙ Ppub are dynamic for that α is randomly generated in every session. Then, the IDi is encrypted by RC with the shared secret key kj = h(SIDj‖x‖rj) between RC and Sj, and the cipher text is transmitted to Sj. For an adversary A, if he/she wants to derive IDi, then he/she has to get K or kj, which further requires him/her to get the system private key x or solve the ECDLP (X = α ∙ G) to obtain α. Obviously, that is impossible. So, our scheme preserves user anonymity.
5.3 Impersonation attack
In our scheme, a patient Ui must be first authenticated by RC before accessing to Sj, so if an adversary A wants to impersonate Ui, he/she has to pass the verification test performed by RC. Thus, A must try to compute ri = h(IDi‖x), which requires A to obtain Ui’s IDi and the system private key x at the same time. Obviously, that is impossible. Another way to deceive RC is to obtain Ui’s IDi, pwi, biometrics Bi, and smart-card SCi simultaneously, which is also obviously impossible. Analogously, for an illegal Sj, without the secret kj, it cannot get the parameter \( H\left({r}_i^{\prime}\right) \), and thus it cannot forge the valid message \( {V}_j=H\left({SK}_s\left\Vert H\left({r}_i^{\prime}\right)\right\Vert X\left\Vert Y\right\Vert {t}_3\right) \) to deceive Ui. So, the impersonation attack is infeasible in our scheme.
5.4 Replay attack
A legal user Ui’s previous login message {c1,X,t1} may be intercepted by an adversary A, then A may try to replay the old message to RC, but RC will reject A for \( {\mathrm{t}}_1^{\prime }-{t}_1>\Delta t \) will hold. Further, A may modify the timestamp t1 to satisfy the condition \( {t}_1^{\prime }-{t}_1<\Delta t \), but RC will also reject A for the validation equation \( {H}^{\prime}\left({r}_i\left\Vert X\right\Vert {t}_1\right)?=H\left({r}_i^{\prime}\left\Vert X\right\Vert {t}_1\right) \) embedded with the original timestamp t1. If t1 is modified, \( {H}^{\prime}\left({r}_i\left\Vert X\right\Vert {t}_1\right)\ne H\left({r}_i^{\prime}\left\Vert X\right\Vert {t}_1\right) \) will hold, then RC will reject A. Analogously, A cannot replay the old messages exchanged between RC/Ui and Sj to deceive the participants. So, the replay attack is infeasible in our scheme.
5.5 Man-in-the-middle attack
For an adversary A to perform the man-in-the-middle attack, he/she needs to establish independent connections with the legal participants and replay messages between them, making them mistaken that they are talking directly to each other. Thus, A needs to successfully deceive Ui and Sj at the same time, which further requires A to obtain H(ri) = H(h(IDi‖x)) or kj = h(SIDj‖x‖rj), and then A has to get the system private key x, which is obviously impossible. So, the man-in-the-middle attack is infeasible in our scheme.
5.6 Stolen-verifier attack
In our scheme, RC just stores h(IDi) which is useless to an adversary A, moreover, RC and Sj don’t store Ui’s pwi and biometrics Bi at all. Thus, even if A breaks into RC or Sj, there are no useful authentication credentials for him/her to steal. So, the stolen-verifier attack is infeasible in our scheme.
5.7 Privileged insider attack
In our scheme, Ui’s password pwi and biometrics Bi never leave the user side, and only in the registration phase does Ui send MPi = h(pwi‖σi) to RC, which is embedded with his/her password pwi. It is obvious that the password pwi is protected by one-way hash function with the random string σi derived by (σi, θi) = Gen(Bi). Thus, it is impossible for an insider to get Ui’s password pwi and biometrics Bi throughout our scheme. So, the privileged insider attack is infeasible in our scheme.
5.8 Denial of service attack
In our scheme, before launching the login message, the legality of a user Ui is first verified by the smart-card SCi by checking whether \( {v}_i=H\left({ID}_i\left\Vert {r}_i\right\Vert {MP}_i^{\prime}\right) \) holds, where \( {r}_i={k}_i\oplus {MP}_i^{\prime } \), \( {MP}_i^{\prime }=h\left({pw}_i\Big\Vert {\sigma}_i\right) \), σi = Rep(Bi, θi). If not, SCi will directly reject Ui. In other words, only when Ui is first authenticated by SCi locally, the login message is sent to RC. Besides, there is no information needed to be synchronized for SCi, Sj and RC in each session. So, the denial of service attack is infeasible in our scheme.
5.9 Offline password guessing attack
Suppose that an adversary A has got Ui’s smart-card SCi by some means, and extracted the stored parameters ki, vi and θi from SCi by side-channel attacks, then, to guess Ui’s password pwi by the equation vi = H(IDi‖ri‖MPi), where MPi = h(pwi‖σi), A has to obtain Ui’s biometrics Bi to compute σi by σi = Rep(Bi, θi), which is almost impossible. So, the offline password guessing attack is infeasible in our scheme.
6 Performance evaluation
We’ve chosen the recent biometrics based authentication schemes [1, 10] for comparison since they have the same technology backgrounds with our scheme, i.e. all are biometrics based using ECC as the cryptographic foundation. Moreover both the schemes were designed for generic multi-server environments rather than a specific application environment, which are consistent with ours from the design goal. So, this section compares our proposed scheme with them in security, computation and communication costs aspects. Table 2 shows these schemes’ abilities to resist the identified attacks, which signifies the robustness of our proposed scheme over the others. To conveniently evaluate our scheme with other relevant schemes in the aspects of computation and communication costs, we assume that the length of identity, timestamp, hash digest and an elliptic curve point are 64, 64, 160 and 320 bits respectively, and use the following notations to depict time complexities of different operations:
-
Tm: the time for executing elliptic curve scalar point multiplication
-
Ts: the time for executing symmetric encryption/decryption operation
-
Th: the time for executing hash function
-
TG: the time for executing the fuzzy extractor operation Gen
According to the experimental results of Kilinc and Yanik [14], Tm, Ts and Th approximately take 2.226, 0.0046 and 0.0023 ms respectively. And we here assume that the time complexity of Gen(∙) is the same with the elliptic curve scalar point multiplication. Then, the detailed comparison of the computation and communication costs of registration phase and authentication with key agreement (AKA) phase between our scheme and the others are demonstrated in Tables 3 and 4. According to Table 3, we can see that the computation and communication costs of registration phase are almost the same in all schemes. According to Table 4, our proposed scheme consumes the lowest computation cost of 13.411 ms and communication cost of 1408 bits in the AKA phase, while the scheme [10] bears the average computation cost of 17.856 ms and communication cost of 3520 bits, and the scheme [1] bears the average computation cost of 24.546 ms and communication cost of 1792 bits. So, in the light of the fact demonstrated in Tables 2, 3 and 4, it can be concluded that our new scheme has advantages over the others, whether in terms of security and functionalities or computation and communication costs.
7 Conclusions
This work presents our biometrics-based mutual authentication with session key agreement scheme for multi-server environment. The security analysis demonstrates that our scheme has perfect security features and can resist various known attacks. The performance evaluation shows that our new scheme is more efficient in the aspects of computation cost and communication cost, for the RC no longer participates in the subsequent user-server session key negotiation processes after it authenticates the user, and thus reducing the computation and communication costs. Hence, it can be said that our new scheme is a more suitable authentication key exchange protocol for multi-server environment.
References
Amin R, Islam SH, Biswas GP, Khan MK, Kumar N (2015) An efficient and practical smart card based anonymity preserving user authentication scheme for TMIS using elliptic curve cryptography. J Med Syst 39(11):1–18
Burrows M, Abadi M, Needham R (1990) A logic of authentication. ACM Trans Comput Syst 8(1):18–36
Chandrakar P, Om H (2017) A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC. Comput Commun 110:26–34
Chaudhry SA, Naqvi H, Sher M, Farash MS, Hassan MU (2015) An improved and provably secure privacy preserving authentication protocol for SIP. Peer-to-Peer Networking and Applications 10:1–15
Chaudhry SA, Naqvi H, Farash MS et al (2015) An improved and robust biometrics-based three factor authentication scheme for multiserver environments. J Supercomput:1–17
Chuang MC, Chen MC (2014) An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst Appl 41(4):1411–1418
Dodis Y, Reyzin L (2008) Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. SIAM J Comput 38(1):97–139
Farash MS (2016) Security analysis and enhancements of an improved authentication for session initiation protocol with provable security. Peer-to-Peer Networking and Applications 9(1):82–91
Farash MS, Attari MA (2014) A secure and efficient identity-based authenticated key exchange protocol for mobile client–server networks. J Supercomput 69(1):395–411
He D, Wang D (2015) Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst J 9(3):816–823
Irshad A, Sher M, Nawaz O, Chaudhry SA, Khan I, Kumari S (2017) A secure and provable multi-server authenticated key agreement for tmis based on amin et al. scheme. Multimed Tools Appl 76(15):1–27
Islam SH, Biswas GP (2011) A more efficient and secure ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. J Syst Softw 84(11):1892–1898
Jangirala S, Mukhopadhyay S, Das AK (2017) A multi-server environment with secure and efficient remote user authentication scheme based on dynamic id using smart cards. Wirel Pers Commun:1–33
Kilinc HH, Yanik T (2014) A survey of SIP authentication and key agreement schemes. IEEE Communications Surveys & Tutorials 16(2):1005–1023
Kim H, Jeon W, Lee K, Lee Y, Won D (2012) Cryptanalysis and improvement of a biometrics-based multi-server authentication with key agreement scheme. In: International Conference on Computational Science and ITS Applications. Springer-Verlag, pp 391–406
Lu Y, Li L, Peng H et al (2015) A biometrics and smart cards-based authentication scheme for multi-server environments. Security & Communication Networks 8(17):3219–3228
Maitra T, Obaidat MS, Islam SH, Giri D, Amin R (2016) Security analysis and design of an efficient ECC-based two-factor password authentication scheme. Security & Communication Networks 9(17):4166–4181
Mishra D, Das AK, Mukhopadhyay S (2014) A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst Appl 41(18):8129–8143
Odelu V, Das AK, Goswami A (2015) A secure biometrics-based multi-server authentication protocol using smart cards. IEEE Transactions on Information Forensics & Security 10(9):1953–1966
Qi M, Chen J (2017) An efficient two-party authentication key exchange protocol for mobile environment. Int J Commun Syst. https://doi.org/10.1002/dac.3341
Qi M, Chen J (2017) An enhanced authentication with key agreement scheme for satellite communication systems. Int J Satell Commun Netw. https://doi.org/10.1002/sat.1218
Shen H, Gao C, He D, Wu L (2015) New biometrics-based authentication scheme for multi-server environment in critical systems. J Ambient Intell Humaniz Comput 6(6):825–834
Wang RC, Juang WS, Lei CL (2011) Robust authentication and key agreement scheme preserving the privacy of secret key. Comput Commun 34(3):274–280
Wu F, Xu L, Kumari S et al (2015) A new authenticated key agreement scheme based on smart cards providing user anonymity with formal proof. Security & Communication Networks 8(18):3847–3863
Yoon EJ, Yoo KY (2013) Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. J Supercomput 63(1):235–255
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Qi, M., Chen, J. Anonymous biometrics-based authentication with key agreement scheme for multi-server environment using ECC. Multimed Tools Appl 78, 27553–27568 (2019). https://doi.org/10.1007/s11042-019-07812-w
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-07812-w