Abstract
In this paper, a novel robust color image watermarking method based on Discrete Cosine Transform (DCT) and Discrete Wavelet Transform (DWT) is proposed. In this method, RGB cover image is divided into red, green and blue components. DCT and DWT are applied to each color components. Grayscale watermark image is scrambled by using Arnold transform. DCT is performed to the scrambled watermark image. Transformed watermark image is then divided into equal smaller parts. DCT coefficients of each watermark parts are embedded into four DWT bands of the color components of the cover image. The robustness of the proposed color image watermarking has been demonstrated by applying various image processing operations such as rotating, resizing, filtering, jpeg compression, and noise adding to the watermarked images. Experimental results show that the proposed method is robust to the linear and nonlinear attacks and the transparency of the watermarked images has been protected.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Distribution of multimedia data has become widespread with the development of internet and mobile technologies. These multimedia data, consisting of digital images, video, audio and texts, can easily be copied and modified. Therefore, the protection of the copyright of these data has become important. Digital watermarking has emerged to provide copyright protection and has become one of the most widely used methods. The process of embedding or hiding a digital data as a watermark into another digital data, and then extracting the hidden information can be defined as digital watermarking [72]. Digital watermarking is also used in application areas such as content authentication, digital forensic, content identification and management, fingerprinting, tamper detection, broadcast monitoring and media file archiving [36].
Digital image watermarking, which is categorized into two classes such as visible and invisible, is the most commonly used watermarking technique. Visible watermarks are visual patterns like logos or labels that can easily be perceived. These watermarks are inserted into an image to specify the content ownership [44]. Invisible watermarks are embedded into unknown parts of an image and cannot be perceived by the human vision system [6]. Depending on the requirements of the application, invisible image watermarking techniques should have major characteristics such as imperceptibility, robustness, security and computational complexity. The digital watermark should be invisible in a watermarked image [33]. The watermark should still be detectable even if intentional or unintentional attacks are applied on the watermarked image [27]. Secret keys should be used in the watermarking technique in order to ensure security against attacks [76]. In copyright protection, the watermarking method should have high computational complexity.
Image watermarking techniques can be generally classified namely spatial domain and transform domain. Watermark embedding is performed by modifying the gray-level pixel values of the original image in spatial domain watermarking techniques [43, 52, 68]. In the transform domain, watermarks can be embedded by modifying the frequency coefficients of discrete Fourier transform [25, 55, 66], discrete cosine transform (DCT) [28, 40, 64], discrete wavelet transform (DWT) [8, 19, 35], Karhunen-Loeve transform [9, 10], Hadamard transform [16, 38] and Contourlet transform [13, 70]. Apart from these transform domain techniques, vector quantization and singular value decomposition (SVD) based image watermarking techniques have also been proposed. In vector quantization based techniques, the watermark is compressed by the quantization methods and then embedded into the original image in the vector quantization domain [29, 51]. In SVD based techniques, the watermark embedding is performed by using the diagonal matrix of the original image [4, 71].
With respect to the application area, image watermarking techniques can be categorized as fragile, semi-fragile, and robust [29]. Fragile and semi-fragile watermarking techniques are used for integrity identification, content authentication and tamper detection [5, 49, 67]. Robust watermarking techniques are mainly used for the purpose of copyright protection, ownership identification, and fingerprinting. Therefore, robust watermarking techniques should be able to resist against intentional and unintentional image modifications or attacks such as rotation, scaling, filtering, compression, noise addition etc. [3, 82]. DCT and DWT are most widely used transform domain methods for robust watermarking. DCT has excellent energy compaction property; thus, it can achieve more robustness against lossy compression attacks [31, 33, 81]. DCT based watermarking can be performed by applying DCT either on the whole image [14, 63] or on non-overlapping blocks [42, 47]. On the other hand, DWT provides excellent spatio-frequency localization properties [65, 81]. It decomposes the image hierarchically into set of low-low (LL), high-low (HL), low-high (LH) and high-high (HH) bands. DWT can identify the regions in the cover image in order to embed the watermark imperceptibly. Furthermore, in robust watermarking techniques, in order to increase the security, scrambling transformations have been used to shuffle watermark information before embedding [39, 74, 83]. Arnold transformation is one of the simplest and most popular method for watermark image scrambling [77].
Most of the robust watermarking techniques have been developed for grayscale images. Block based DCT watermarking schemes have been commonly used in robust watermarking area [48, 64]. In these schemes, cover image has been divided into non-overlapping blocks and DCT has been performed on each block separately to obtain low frequency, middle frequency and high frequency sub-bands [32]. Watermark embedding has been generally performed in the middle frequency sub-bands [26, 73]. DWT based watermarking schemes have also been improved for robust watermarking. In these schemes, cover image has been decomposed into one-level [24, 41] or multi-level decomposition [1, 80] by Haar wavelet transform. Then, watermark has been commonly embedded into LL band of the decomposed image. Moreover, in the past decades, many watermarking techniques have been proposed for color images. In most of these techniques, RGB color space of the cover image has been converted to YCbCr color space [7, 39, 59,60,61, 76]. Then, YCbCr color space of the cover image has been separated into luminance (Y) and chrominance (Cb and Cr) components. The watermark has been usually embedded into the luminance component in these techniques. Furthermore, in recent years, DWT and DCT based hybrid methods have been improved for robust watermarking [18, 34, 54, 79, 84]. In these methods, firstly DWT has been applied to the cover image to obtain the LL band. Then, DCT has been implemented to the obtained LL band. Watermark embedding has been performed by modifying the DCT coefficients of the LL band.
By considering the advantages of DCT and DWT algorithms in robust watermarking applications, as mentioned above, a novel DCT-DWT based hybrid color image watermarking method is proposed in this paper. Unlike the aforementioned methods, firstly global DCT has been applied to RGB cover image’s color components in the proposed method. Then, one-level DWT has been performed to the DCT coefficients of each color components. Grayscale image is used as a watermark in this method. The watermark image has been scrambled by using Arnold transform. DCT has been applied to the scrambled watermark image. Then, transformed watermark image has been divided into equal smaller parts. DCT coefficients of each watermark parts have been embedded into LL, HL, LH and HH bands of each color components of the cover image. The proposed method provides high robustness and imperceptibility due to embedding watermark parts separately into all the DWT bands of the each color components of the cover image. The robustness of the proposed color image watermarking has been evaluated by applying linear and nonlinear attacks to the watermarked images. Normalized Correlation (NC) values between the extracted watermark and the original watermark have been used to determine the robustness of the proposed algorithm. The Peak Signal to Noise Ratio (PSNR) value between the original image and the watermarked image has also been used to determine the imperceptibility and transparency.
The main contributions of this paper are as followings: 1) we introduce a new robust DCT-DWT based hybrid color image watermarking method, in which firstly global DCT is applied to RGB cover image’s color components and then one-level DWT has been performed to the DCT coefficients of the each color components; 2) we divide grayscale watermark image into 12 equal smaller parts, and then we have embedded the DCT transformed watermark parts separately into all the DWT bands of the each color components of the RGB cover image; 3) we apply various attacks (such as rotation, noise addition, image filtering, resizing and etc.) to the watermarked images, and we achieve high robustness.
The organization of the paper is as follows: Section 2 provides a literature review. Section 3 describes the proposed watermark embedding and extracting methods. Experimental results are demonstrated in Section 4. The conclusion and future work are given in Section 5.
2 Related work
In recent years, researchers have studied to improve DCT and DWT based color image watermarking methods. Lin et al. [39] proposed a DCT-based image watermarking method against JPEG compression. In this method, binary watermark image was permuted based on Torus automorphism and then it was embedded into the low-frequency bands of DCT transformed luminance component of the cover image. Su et al. [69] presented a robust color image watermarking method based on two-level DCT. Color watermark image was embedded into the direct current (DC) and the alternating current (AC) coefficients of the color cover image using one-level and two-level DCT transformations in this method. Parah et al. [47] proposed a blind and robust DCT based color image watermarking method, where the watermark embedding was performed by using inter-block coefficient differencing. Roy and Pal [57] presented a DCT based color watermarking method, in which two binary watermarks were embedded into color image. In this method, binary watermarks were scrambled using Arnold transform and then they were embedded into the middle-frequency bands of the DCT transformed green and blue components of the cover image. Chang et al. [12] proposed a DCT based color image watermarking method using two-dimensional Linear Discriminant Analysis scheme in YIQ color space. In this method, two binary watermarks were embedded into the AC coefficients of DCT transformed quadrature chrominance component of the cover image. Moosazadeh and Ekbatanifard [42] presented a DCT based robust image watermarking method in YCoCg color space. Arnold transformed binary watermark was embedded into the luminance component of the cover image by using block-based DCT coefficients relationship. Gao et al. [17] proposed a 2-level DWT based color image watermarking method. Arnold transformed grayscale watermark image was embedded into the LL bands of DWT transformed blue and green components of the cover image in this method. Giri et al. [20] presented a DWT based color image watermarking method, where watermark was embedded into the HL band of one-level DWT transformed cover image. Gupta et al. [21] improved the DWT based color image watermarking method using artificial bee colony algorithm and uncorrelated color space. In this method 3-level DWT decomposition was applied on each color components of the cover image and LL, HL, LH, and HH bands were chosen for embedding process. Huynh et al. [30] presented a selective bit watermark embedding method in the one-level wavelet domain. In this method, grayscale watermark was embedded into the middle-frequency bands of the two optimal color channels of cover image by using difference quantization algorithm. Rosales-Roldan et al. [56] proposed DWT, DCT, and SVD based color image watermarking methods using quantization index modulation technique. In these methods, QR code generated with the personal information was used as a binary watermark sequence and watermark embedding was performed in the luminance component of the cover image. In the DWT based method, two-level decomposition was performed, and the LL band was used for watermark embedding.
Hybrid methods have also been developed by the researchers using transform domain techniques. Sari et al. [61] presented a SVD-DCT based color image watermarking method. In this method, singular values of the binary watermark image were embedded into the SVD performed DC coefficients of the luminance component of the cover image. Li et al. [38] proposed a quaternion DCT (QDCT) and SVD based color image watermarking method, in which encrypted binary hologram watermark was generated by using computer-generated hologram technique and particle swarm optimization algorithm. The encrypted hologram watermark was embedded into the QDCT-SVD transformed cover image in this method. Bajracharya and Koju [7] presented a SVD-DWT based image watermarking method in YCbCr color space. Singular values of the 3-level DWT transformed red color component of the watermark image were embedded into the singular values of the 4-level DWT transformed luminance component of the cover image. HH band was chosen for embedding process in this method. Vaidya and Mouli [76] proposed a color image watermarking method based on multiple decompositions such as DWT, contourlet transform, Schur decomposition and SVD. In this method, singular values of the Arnold transformed grayscale watermark image were embedded into the multiple decomposition performed LL band of the DWT transformed luminance component of the cover image. Rasti et al. [53] presented a color image watermarking method based on DWT, SVD, orthogonal-triangular decomposition, and chirp z-transform. Singular values of the grayscale watermark image were embedded into the multiple decomposition performed LL band of the 2-level DWT transformed cover image based on entropy of each color components in this method. Roy et al. [60] proposed a DWT-SVD based color image watermarking method in YCbCr color space. 4-level DWT was applied to Cb component of the cover image. In this method, singular values of the watermark were embedded into singular values of the Cb component of the cover image in the HL band. Lakrissi et al. [37] presented a DWT-SVD based dynamic color image watermarking method. 3-level DWT was applied to luminance component of the cover image and a dynamic block was selected randomly using a pseudo random generator from the LL band. In this method, encrypted binary watermark was embedded into the singular values of the selected dynamic block. Roy and Pal [58] proposed a DWT-SVD based image watermarking method for copyright protection and authentication of color images. Block based 3-level DWT was applied to the luminance component of the cover image. In this method, decomposed watermark image blocks were embedded into the singular values of the DWT transformed blocks. Also, Roy and Pal [59] improved a similar study by using block based redundant DWT and SVD algorithms, in which Arnold scrambled grayscale watermark was used. Pandey et al. [45, 46] presented a stationary wavelet transform (SWT) and SVD based image watermarking methods in YCbCr color space. SWT and SVD were applied to the luminance components of the color watermark and the cover image. In these methods, singular values of the color watermark were embedded into corresponding singular values of the cover image in the LL band. Gill and Soni [18] proposed a color image watermarking method based on DCT and DWT. DCT coefficients of the red color component of the watermark image were embedded into the DCT transformed red color component of the cover image. Also, in this method, DWT decomposition was applied on green and blue color components of the watermark and the cover images, and the watermark embedding was performed by using the LL band. Kalra et al. [33] presented a color image watermarking method using DWT and DCT. In this method, DWT was performed on luminance color component of the cover image, and the binary watermark image was encrypted using Hamming codes, Chaos and Arnold transform. Encrypted watermark image was embedded into the DCT transformed HL band of the cover image. Chaitanya et al. [11] proposed a DWT-DCT-SVD based color image watermarking method. 2-level DWT decomposition was applied on blue color component of the cover image, and by using median energy a sub-band was chosen for embedding process in this method. Singular values of the grayscale watermark image were embedded into the singular values of the DCT transformed sub-band of the cover image. Divecha and Jani [15] presented a DWT-DCT-SVD based color image watermarking method, where 2-level DWT decomposition was applied on color components of the cover image. Singular values of the color watermark image were embedded into the singular values of the DCT transformed LL-HH sub-bands of the cover image. Similar study was proposed by Hallur et al. [22], in which red color component was used for watermark embedding process. Zear et al. [81] improved the DWT-DCT-SVD based watermarking method using Back Propagation Neural Network for healthcare applications, where three watermarks were used such as medical image, the signature code and diagnostic information. He and Hu [23] presented a DWT-DCT-SVD based color image watermarking method in YUV color space. One-level DWT decomposition was applied to the luminance component of the cover image. Arnold scrambled watermark image was embedded into the singular values of DCT transformed HH band of the cover image. Similar study was proposed by Xu et al. [79], in which LL band of the cover image was used for watermark embedding. Al-Afandy et al. [2] presented DWT-SVD based and Stationary Wavelet Transform (DSWT)-DCT based color image watermarking methods. In DWT-SVD based method, one-level DWT decomposition was applied to each color components of the cover image. The watermark was embedded into the singular values of the LL bands of each color components. On the other hand, in DSWT-DCT based method, the DCT was applied on each color components of the cover image. Then, 3-level DSWT was performed to the DCT coefficients of the color components and watermark embedding was performed in the LL band. Thanki and Borra [75] proposed Finite Ridgelet Transform (FRT) and DWT based color image watermarking method. FRT was applied to each color components of the cover image. Then, one-level DWT was performed to the ridgelet coefficients of each color components. In this method, Arnold scrambled color watermark image was embedded into the wavelet coefficients in the LL band.
In the literature, most of the color image watermarking techniques have been developed based on DCT and DWT transform domains. Block based DCT watermarking techniques have been commonly used, in which DCT has been performed on non-overlapping blocks of the cover image, and watermark embedding has been generally performed in the middle frequency sub-bands. On the other hand, in DWT watermarking techniques, multi-level decomposition has been usually used which decomposes the cover image hierarchically into set of LL, HL, LH, and HH sub-bands. Watermark embedding has been commonly performed in the LL sub-band in these techniques. Moreover, DWT, DCT, and SVD based hybrid color image watermarking methods have been improved in recent years. In most of these methods, firstly multi-level DWT has been applied to the cover image. Then, only one sub-band (generally the LL sub-band) has been selected for watermark embedding. Block based DCT has been applied to the selected sub-band. Finally, watermark has been generally embedded into the singular values of the DCT transformed sub-band. Furthermore, in most of the color image watermarking techniques, RGB color space of the cover image has been converted to YCbCr color space, and the watermark has been usually embedded only into the luminance color component.
In this paper, an efficient DCT-DWT based hybrid color image watermarking method in RGB color space is proposed. Unlike the related methods, firstly global DCT has been performed to each color components of the RGB cover image in the proposed method. Then, one-level DWT has been applied to the DCT coefficients of each color components. In this method, grayscale image has been used as a watermark. Before embedding process, this watermark image has been scrambled by using Arnold transform. DCT has been implemented to the scrambled watermark image. Then, DCT transformed watermark image has been divided into 12 equal smaller parts. Finally, DCT coefficients of each watermark parts have been embedded into LL, HL, LH and HH bands of each color components of the RGB cover image. By embedding the watermark parts separately into all the DWT bands of each color components of the cover image, high robustness and imperceptibility have been obtained with the proposed method.
3 Proposed method
DCT and DWT based color image watermarking method is proposed to provide copyright protection. The proposed method consists of two main parts; watermark embedding and watermark extracting.
3.1 Watermark embedding method
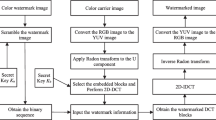
The block diagram of the proposed watermark embedding method is given in Fig. 1. Also, the pseudocode form of the watermark embedding process is presented in Algorithm 1. In this method grayscale watermark image of size 96x96 is embedded into the RGB cover image of size 1024x1024x3. The basic steps of the watermark embedding method are as follows:
-
1.
Separate the original RGB cover image, Io, into color components of red, green and blue, \( {I}_c^o\left(c=R,G,B\right) \).
-
2.
Apply DCT to each color components:
-
3.
Apply one-level DWT using Haar wavelet to each DCT coefficients of the color components to obtain 512x512 LLc, LHc, HLc, HHc bands:
-
4.
Scramble the grayscale watermark image, W, using Arnold transform.
-
5.
Convert the 96x96 scrambled watermark, Ws, to 9216x8 binary watermark, Wbin.
-
6.
Divide the binary watermark, Wbin, into three parts, and by using zero-padding obtain three 160x160 binary watermark blocks, Wc(c = R, G, B).
-
7.
Apply DCT to each watermark block:
-
8.
Divide DCT coefficients of each 160x160 watermark block into 80x80 non-overlapped sub-blocks:
-
9.
Insert each 80x80 sub-block into the upper left corner of 512x512 zero matrix to obtain four 512x512 watermark blocks, Wc, s(c = R, G, B and s = A, B, C, D), for each color component’s DWT bands.
-
10.
Embed the watermark blocks, Wc, s, into the coefficients of the LLc, LHc, HLc, and HHc bands by using scaling factor, k, for each color components:
$$ {\displaystyle \begin{array}{c}L{L}_{c,w}=L{L}_c+{W}_{c,A}\ast k\\ {}L{H}_{c,w}=L{H}_c+{W}_{c,B}\ast k\\ {}H{L}_{c,w}=H{L}_c+{W}_{c,C}\ast k\\ {}H{H}_{c,w}=H{H}_c+{W}_{c,D}\ast k\end{array}} $$ -
11.
Apply inverse DWT (IDWT) to LLc, w, LHc, w, HLc, w, and HHc, w bands for each color components:
-
12.
Apply inverse DCT (IDCT) to obtain watermarked color components:
-
13.
Reconstruct watermarked color components, IR, w, IG, w, and IB, w to obtain watermarked color image, Iw.
Algorithm 1: Watermark Embedding Process

3.2 Watermark extracting method
The block diagram of the proposed non-blind watermark extracting method is illustrated in Fig. 2. In addition, the pseudocode form of the watermark extracting process is given in Algorithm 2. Original RGB cover image is required to extract the watermark image in the proposed method. The basic steps of the watermark extracting method are as follows:
-
1.
Separate the original cover image, Io, and watermarked image, Iw, into red, green and blue color components, \( {I}_c^o \) and \( {I}_c^w, \) (c = R, G, B).
-
2.
Apply DCT to each color components of the watermarked image:
$$ {I}_{c,w}^{DCT}= DCT\left({I}_c^w\right) $$ -
3.
Apply one-level DWT to each DCT coefficients of the color components of the watermarked image to obtain LLc, w, LHc, w, HLc, w, HHc, w bands:
-
4.
Apply DCT to each color components of original cover image:
-
5.
Apply one-level DWT to each DCT coefficients of the color components of original cover image:
$$ {LL}_c,{LH}_c,{HL}_c,{HH}_c= DWT\left({I}_c^{DCT}\right) $$ -
6.
Extract four 512x512 watermark blocks, \( {W}_{c,s}^{ext} \), from the coefficients of the LLc, w, LHc, w, HLc, w, and HHc, w bands by using scaling factor, k, for each color components:
$$ {\displaystyle \begin{array}{c}{W}_{c,A}^{ext}=\left(L{L}_{c,w}-L{L}_c\right)./k\\ {}{W}_{c,B}^{ext}=\left(L{H}_{c,w}-L{H}_c\right)./k\\ {}{W}_{c,C}^{ext}=\left(H{L}_{c,w}-H{L}_c\right)./k\\ {}{W}_{c,D}^{ext}=\left(H{H}_{c,w}-H{H}_c\right)./k\end{array}} $$ -
7.
Get four 80x80 sub-blocks from the upper left corners of 512x512 extracted watermark blocks, \( {W}_{c,s}^{ext} \), for each color components.
-
8.
Merge the 80x80 sub-blocks to obtain 160x160 extracted watermark DCT coefficients, \( {W}_c^{\mathit{\operatorname{ext}}, DCT} \).
-
9.
Apply IDCT to each 160x160 extracted watermark DCT coefficients for each color components:
$$ {W}_c^{ext}= IDCT\left({W}_c^{\mathit{\operatorname{ext}}, DCT}\right) $$ -
10.
Merge three 160x160 color watermark blocks (\( {W}_R^{ext} \), \( {W}_G^{ext} \), and \( {W}_B^{ext} \)) and reconstruct 9216x8 extracted binary watermark, \( {W}_{bin}^{ext} \).
-
11.
Convert the 9216x8 extracted binary watermark, \( {W}_{bin}^{ext} \), to 96x96 grayscale scrambled watermark, \( {W}_s^{ext} \).
-
12.
Descramble the extracted watermark, \( {W}_s^{ext} \), using inverse Arnold transform to obtain extracted grayscale watermark image, Wext.
Algorithm 2: Watermark Extracting Process

4 Experimental results
In order to demonstrate the performance of the proposed method, 1024x1024x3 Baboon, Pears, Peppers, Jet Plane, and Barbara, cover images (as shown in Fig. 3) and 96x96 grayscale Lena, Cameraman and Saturn watermark images (as shown in Fig. 4) are used.
To determine the transparency of the watermarked images, PSNR are calculated using the equation as given below:
where, mxnxp is the size of the original cover image, \( {I}_{\left(i,j,k\right)}^o \) and \( {I}_{\left(i,j,k\right)}^w \) denote the pixel values at position (i, j, k) of the original covet image, Io, and the watermarked image, Iw, respectively.
NC values between the embedded watermarks and extracted watermarks are calculated as follows:
where, MxN is the size of the grayscale watermark image, W(i, j) and Wext(i, j) are the pixel values of the embedded original watermark and the extracted watermark, respectively. Wm and \( {W}_m^{ext} \) denote the mean values of the embedded and extracted watermarks, respectively.
The watermarked images embedded by Lena watermark for scaling factor, k, values of “40” and “70” are illustrated in Fig. 5. The period of the Arnold transform is chosen as 10 to scramble watermark images [62]. The PSNR values of the watermarked images are higher than 35 and 30 dB for scaling factor values of “40” and “70”, respectively. It can be seen from the figure that the quality and the transparency of the watermarked images have been protected.
The robustness of the proposed color image watermarking method is conducted by applying various image processing operations to the watermarked images. Median filter (MF), average filter (AF) and sharpen attacks have been applied with 3x3 kernel size to the watermarked images. For blurring, Gaussian low-pass filter with filter kernel size of 5x5 has been performed. Gaussian white noise (GWN) with mean 0 and variance of 0.001, Speckle noise (SN) with variance of 0.01, Salt-and-pepper noise (S&PN) with density of 0.01, and Poisson noise (PN) have been added to the watermarked images. JPEG compression with quality of 20%, clockwise 25° rotation, and bilinear resizing (1024 → 512 → 1024) have been also performed.
Extracted watermarks from attacked watermarked Baboon images for the scaling factor value of “40” are shown in Fig. 6. It can be seen from the figure that watermarked Baboon image is robust under blurring, AV, JPEG, MF, and GWN attacks. Also, extracted watermarks are recognizable under sharpen, resizing, PN, SN, S&PN, and rotation attacks. For the scaling factor value of “70”, extracted watermarks from attacked watermarked Baboon image are illustrated in Fig. 7. As can be seen from the figure that the watermarked Baboon image is more robust under all the attacks. Extracted watermarks from attacked watermarked Pears images are shown in Figs. 8 and 9, for scaling factor values of “40” and “70”, respectively. It is clear from the figures that the watermarked Peers image is robust under all the attacks except PN, SN, S&PN, and rotation attacks for the scaling factor value of “40”. However, extracted watermarks are recognizable under all these attacks. Also, watermarked Pears images are more robust under all the attacks for the scaling factor value of “70”. It can be also seen from the figures that the visual effects of the extracted watermarks from attacked Pears images are better than the extracted watermarks from attacked Baboon images.
Performance of the proposed color image watermarking method is evaluated for various scaling factors. NC values of the extracted watermarks from attacked Baboon images are given in Table 1. It can be seen from the table that, stronger robustness is obtained for larger scaling factor values. PSNR values of the watermarked Baboon images are also shown in Table 2. It is clear from the table that higher transparency can be obtained for smaller scaling factor values. NC values of the extracted watermarks from attacked Pears, Peppers, Jet Plane, and Barbara images and given in Tables 3, 4, 5, and 6 respectively. PSNR values of the watermarked images are also shown in Table 2. As can be seen from the tables, as the scaling factor value increases, the PSNR values decrease and NC values increase.
PSNR value higher than 30 dBs is considered to be acceptable transparency of the watermarked image [50, 78]. Experimental results illustrate that the proposed method has better transparency (PSNR > = 35 dBs) and is robust under various attacks for the scaling factor value of “40”.
5 Conclusions
In this paper, an efficient DCT-DWT based hybrid image watermarking method has been proposed for copyright protection of color images. RGB cover image has been divided into red, green and blue components in this method. Firstly global DCT has been performed to each color components, and then one-level DWT has been applied to the DCT coefficients of the color components. Grayscale image has been used as a watermark. Before embedding process, the watermark image has been scrambled, and then has been transformed with DCT. Transformed watermark image has been divided into equal smaller parts. Finally, DCT coefficients of each watermark parts have been embedded into all four frequency bands of each color components of the RGB cover image. The robustness of the method has been demonstrated by applying various attacks to the watermarked images. Experimental results illustrate that the proposed method is robust under various attacks and the imperceptibility and transparency of the watermarked images have been protected. The most important contribution of our paper is that, by embedding the DCT transformed watermark parts separately into all the DWT bands of each color components of the cover image, high robustness and imperceptibility have been obtained with the proposed method.
As a future work, in order to improve the proposed method, different scaling factors can be used for the DWT bands and the color components. In addition, multi-level DWT can be performed for the proposed method. Furthermore, the robustness of the proposed method can be developed for print/scan attacks.
References
Ahmad A, Sinha GR, Kashyap N (2014) 3-level DWT image watermarking against frequency and geometrical attacks. Int J Comput Netw Inf Secur 6(12):58–63
Al-Afandy KA, El-Shafai W, El-Rabaie ESM, Abd El-Samie FE, Faragallah OS, El-Mhalaway A, Shehata AM, El-Banby GM, El-Halawany MM (2018) Robust hybrid watermarking techniques for di_erent color imaging systems. Multimed Tools Appl 77(19):25709–25759
Ali M, Ahn CW, Pant M (2018) An efficient lossless robust watermarking scheme by integrating redistributed invariant wavelet and fractional fourier transforms. Multimed Tools Appl 77(10):11751–11773
Aslantas V (2009) An optimal robust digital image watermarking based on SVD using differential evolution algorithm. Opt Commun 282(5):769–777
Aslantas V, Ozer S, Ozturk S (2007) A novel clonal selection algorithm based fragile watermarking method. In: Artificial immune systems. Springer, Berlin, pp 358–369
Aslantas V, Ozer S, Ozturk S (2009) Improving the performance of DCT-based fragile watermarking using intelligent optimization algorithms. Opt Commun 282(14):2806–2817
Bajracharya S, Koju R (2017) An improved DWT-SVD based robust digital image watermarking for color image. Int J Eng Manuf 1(11):49–59
Barni M, Bartolini F, Piva A (2001) Improved wavelet-based watermarking through pixel-wise masking. IEEE Trans Image Process 10(5):783–791
Barni M, Bartolini F, Rosa AD, Piva A (2002) Color image watermarking in the Karhunen-Loeve transform domain. J Electron Imaging 11(1):87–95
Botta M, Cavagnino D, Pomponiu V (2015) Fragile watermarking using Karhunen-Loeve transform: the KLT-F approach. Soft Comput 19(7):1905–1919
Chaitanya K, Reddy ES, Rao KG (2014) Digital color image watermarking in RGB planes using DWT-DCT-SVD coefficients. Int J Comput Sci Inf Technol 5(2):2413–2417
Chang TJ, Pan IH, Huang PS, Hu CH (2018) A robust DCT-2DLDA watermark for color images. Multimed Tools Appl:1–23
Chen L, Zhao J (2018) Contourlet-based image and video watermarking robust to geometric attacks and compressions. Multimed Tools Appl 77(6):7187–7204
Cox IJ, Kilian J, Leighton FT, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. IEEE Trans Image Process 6(12):1673–1687
Divecha N, Jani NN (2013) Implementation and performance analysis of DCT-DWT-SVD based watermarking algorithms for color images. In: Intelligent systems and signal processing (ISSP), 2013 international conference on. IEEE, pp 204–208
Etemad E, Samavi S, Soroushmehr SMR, Karimi N, Etemad M, Shirani S, Najarian K (2018) Robust image watermarking scheme using bit-plane of hadamard coefficients. Multimed Tools Appl 77(2):2033–2055
Gao H, Jia L, Liu M (2013) A digital watermarking algorithm for color image based on DWT. Indonesian J Electr Eng Comput Sci 11(6):3271–3278
Gill R, Soni R (2017) An efficient image watermarking using 2-DCT and 2-DWT in color images. Int J Adv Res Comput Sci 8(5):1304–1308
Giri KJ, Bashir R (2018) A block based watermarking approach for color images using discrete wavelet transformation. Int J Inf Technol 10(2):139–146
Giri KJ, Peer MA, Nagabhushan P (2015) A robust color image watermarking scheme using discrete wavelet transformation. Int J Image Graph Signal Process 7(1):47–52
Gupta M, Parmar G, Gupta R, Saraswat M (2015) Discrete wavelet transform-based color image watermarking using uncorrelated color space and artificial bee colony. Int J Comput Int Sys 8(2):364–380
Hallur SR, Kuri S, Kulkarni GH (2015) Robust digital watermarking using DWT-DCT-SVD algorithms for color image. Int J Curr Eng Technol 5(4):2722–2727
He Y, Hu Y (2018) A proposed digital image watermarking based on DWT-DCT-SVD. In: 2018 2nd IEEE advanced information management, communicates, electronic and automation control conference (IMCEC). IEEE, pp 1214–1218
Hemamalini B, Nagarajan V (2018) Wavelet transform and pixel strength-based robust watermarking using dragonyoptimization. Multimed Tools Appl:1–20
Hernandez MC, Ugalde FG, Miyatake MN, Meana HP (2015) Robust watermarking method in DFT domain for effective management of medical imaging. SIViP 9(5):1163–1178
Hsu LY, Hu HT (2017) Robust blind image watermarking using crisscross inter-block prediction in the DCT domain. J Vis Commun Image Represent 46:33–47
Huang HC (2009) Information hiding and applications, vol 227. Springer
Huang J, Shi YQ, Shi Y (2000) Embedding image watermarks in DC components. IEEE Trans Circuits Syst Video Technol 10(6):974–979
Huang HC, Wang FH, Pan JS (2001) Efficient and robust watermarking algorithm with vector quantization. Electron Lett 37(13):826–828
Huynh-The T, Hua CH, Tu NA, Hur T, Bang J, Kim D, Amin MB, Kang BH, Seung H, Lee S (2018) Selective bit embedding scheme for robust blind color image watermarking. Inf Sci 426:1–18
Islam M, Roy A, Laskar RH (2018) Neural network based robust image watermarking technique in LWT domain. J Intell Fuzzy Syst 34(3):1691–1700
Jeswani J, Sarode T (2014) An improved blind color image watermarking using DCT in RGB color space. Int J Comput Appl 92(14):50–56
Kalra GS, Talwar R, Sadawari H (2015) Adaptive digital image watermarking for color images in frequency domain. Multimed Tools Appl 74(17):6849–6869
Kang XB, Zhao F, Lin GF, Chen YJ (2018) A novel hybrid of DCT and SVD in DWT domain for robust and invisible blind image watermarking with optimal embedding strength. Multimed Tools Appl 77(11):13197–13224
Kaur S, Jindal H (2017) Enhanced image watermarking technique using wavelets and interpolation. Int J Image Graph Signal Process 9(7):23–35
Kumar C, Singh AK, Kumar P (2018) A recent survey on image watermarking techniques and its application in e-governance. Multimed Tools Appl 77(3):3597–3622
Lakrissi Y, Saaidi A, Essahlaoui A (2018) Novel dynamic color image watermarking based on DWT-SVD and the human visual system. Multimed Tools Appl 77(11):13531–13555
Li J, Yu C, Gupta BB, Ren X (2018) Color image watermarking scheme based on quaternion Hadamard transform and Schur decomposition. Multimed Tools Appl 77(4):4545–4561
Lin SD, Shie SC, Guo JY (2010) Improving the robustness of DCT-based image watermarking against JPEG compression. Comput Stand Inter 32(1–2):54–60
Lutovac B, Dakovic M, Stankovic S, Orovic I (2017) An algorithm for robust image watermarking based on the DCT and zernike moments. Multimed Tools Appl 76(22):23333–23352
Moeinaddini E, Afsari F (2018) Robust watermarking in DWT domain using SVD and opposition and dimensional based modified firefly algorithm. Multimed Tools Appl 77(19):26083–26105
Moosazadeh M, Ekbatanifard G (2017) An improved robust image watermarking method using DCT and YCoCg-R color space. OPTIK 140:975–988
Nikolaidis N, Pitas I (1998) Robust image watermarking in the spatial domain. Signal Process 66(3):385–403
Pan JS, Huang HC, Jain LC (2004) Intelligent watermarking techniques, vol 7. World scientific
Pandey MK, Parmar G, Gupta R (2018) A robust non-blind hybrid color image watermarking with Arnold transform. ICTACT J Image Video Process 9(1):1814–1820
Pandey MK, Parmar G, Gupta R, Sikander A (2018) Non-blind Arnold scrambled hybrid image watermarking in YCbCr color space. Microsyst Technol:1–11
Parah SA, Sheikh JA, Loan NA, Bhat GM (2016) Robust and blind watermarking technique in DCT domain using inter-block coefficient differencing. Digit Signal Process 53:11–24
Parah SA, Loan NA, Shah AA, Sheikh JA, Bhat G (2018) A new secure and robust watermarking technique based on logistic map and modification of DC coefficient. Nonlinear Dynam 93(4):1933–1951
Patel HA, Divecha NH (2018) A feature-based semi-fragile watermarking algorithm for digital color image authentication using hybrid transform. In: Advances in computer and computational sciences. Springer, pp 455–465
Pradhan C, Rath S, Bisoi AK (2012) Non blind digital watermarking technique using DWT and cross chaos. Proc Technol 6:897–904
Qin C, Ji P, Wang J, Chang CC (2017) Fragile image watermarking scheme based on VQ index sharing and self-embedding. Multimed Tools Appl 76(2):2267–2287
Qin C, Ji P, Zhang X, Dong J, Wang J (2017) Fragile image watermarking with pixel-wise recovery based on overlapping embedding strategy. Signal Process 138:280–293
Rasti P, Anbarjafari G, Demirel H (2017) Colour image watermarking based on wavelet and QR decomposition. In: Signal processing and communications applications conference (SIU), 2017 25th. IEEE, pp 1–4
Raviya MKH, Kothari AM (2018) Comparative study of digital image watermarking based IJ Cox's algorithm versus proposed hybrid DWT-DCT approach. Eur J Acad Essays 5(5):98–104
Riad R, Ros F, Harba R, Douzi H, Elhajji M (2017) Enhancement of fourier image watermarking robustness. Control Eng Appl Inf 19(4):25–33
Rosales-Roldan L, Chao J, Nakano-Miyatake M, Perez-Meana H (2018) Color image ownership protection based on spectral domain watermarking using QR codes and QIM. Multimed Tools Appl 77(13):16031–16052
Roy S, Pal AK (2017) A blind DCT based color watermarking algorithm for embedding multiple watermarks. AEU-Int J Electron Commun 72:149–161
Roy S, Pal AK (2018) A hybrid domain color image watermarking based on DWT-SVD. IJST-T Electr Eng:1–17
Roy S, Pal AK (2018) An SVD based location specific robust color image watermarking scheme using RDWT and Arnold scrambling. Wirel Pers Commun 98(2):2223–2250
Roy A, Maiti AK, Ghosh K (2018) An HVS inspired robust non-blind watermarking scheme in YCbCr color space. Int J Image Graph 18(03):1850015
Sari CA, Rachmawanto EH et al (2017) Robust and imperceptible image watermarking by DC coefficients using singular value decomposition. Proceeding of EECSI 4:187–191
Shankar SS, Rengarajan A (2016) Data hiding in encrypted images using Arnold transform. ICTACT J Image Video Process 7(1):1339–1344
Sheth RK, Nath VV (2016) Secured digital image watermarking with discrete cosine transform and discrete wavelet transform method. In: Advances in computing, communication, & automation (ICACCA)(spring), international conference on. IEEE, pp 1–5
Singh SP, Bhatnagar G (2018) A new robust watermarking system in integer DCT domain. J Vis Commun Image Represent 53:86–101
Singh AK, Dave M, Mohan A (2014) Hybrid technique for robust and imperceptible image watermarking in DWT-DCT-SVD domain. Natl Acad Sci Lett 37(4):351–358
Solachidis V, Pitas L (2001) Circularly symmetric watermark embedding in 2-D DFT domain. IEEE Trans Image Process 10(11):1741–1753
Sreenivas K, Prasad VK (2018) Fragile watermarking schemes for image authentication: a survey. Int J Mach Learn Cybern 9(7):1193–1218
Su Q, Chen B (2018) Robust color image watermarking technique in the spatial domain. Soft Comput 22(1):91–106
Su Q, Wang G, Jia S, Zhang X, Liu Q, Liu X (2015) Embedding color image watermark in color image based on two-level DCT. SIViP 9(5):991–1007
Su Q, Wang G, Lv G, Zhang X, Deng G, Chen B (2017) A novel blind color image watermarking based on Contourlet transform and Hessenberg decomposition. Multimed Tools Appl 76(6):8781–8801
Su Q, Wang G, Zhang X, Lv G, Chen B (2017) An improved color image watermarking algorithm based on QR decomposition. Multimed Tools Appl 76(1):707–729
Tao H, Chongmin L, Zain JM, Abdalla AN (2014) Robust image watermarking theories and techniques: a review. J Appl Res Technol 12(1):122–138
Tewari TK, Saxena V (2010) An improved and robust DCT based digital image watermarking scheme. Int J Comput Appl 3(1):28–32
Thakur S, Singh AK, Ghrera SP, Mohan A (2018) Chaotic based secure watermarking approach for medical images. Multimed Tools Appl:1–14
Thanki R, Borra S (2018) A color image steganography in hybrid FRT-DWT domain. J Inf Sec Appl 40:92–102
Vaidya P, PVSSR CM (2017) A robust semi-blind watermarking for color images based on multiple decompositions. Multimed Tools Appl 76(24):25623–25656
Wang XL, Qiu LK (2010) Image watermarking algorithm based on Arnold scrambling and DCT transform [J]. Comm Technol 4:078
Wang Q, Ding Q, Zhang Z, Ding L (2008) Digital image encryption research based on DWT and chaos. In: Natural computation, 2008. ICNC'08. Fourth international conference on, vol 5. IEEE, pp 494–498
Xu H, Kang X, Wang Y, Wang Y (2018) Exploring robust and blind watermarking approach of colour images in DWT-DCT-SVD domain for copyright protection. Int J Electron Secur Digit Forensic 10(1):79–96
Yadav B, Kumar A, Kumar Y (2018) A robust digital image watermarking algorithm using DWT and SVD. In: Soft computing: theories and applications. Springer, pp 25–36
Zear A, Singh AK, Kumar P (2018) A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine. Multimed Tools Appl 77(4):4863–4882
Zebbiche K, Kheli_ F, Loukhaoukha K (2018) Robust additive watermarking in the DTCWT domain based on perceptual masking. Multimed Tools Appl 77(16):21281–21304
Zhou NR, Luo AW, Zou WP (2018) Secure and robust watermark scheme based on multiple transforms and particle swarm optimization algorithm. Multimed Tools Appl:1–17
Zhou X, Zhang H, Wang C (2018) A robust image watermarking technique based on DWT, APDCBT, and SVD. Symmetry 10(3):77
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Abdulrahman, A.K., Ozturk, S. A novel hybrid DCT and DWT based robust watermarking algorithm for color images. Multimed Tools Appl 78, 17027–17049 (2019). https://doi.org/10.1007/s11042-018-7085-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-7085-z