Abstract
The increasing role of Telecare Medicine Information Systems (TMIS) makes its accessibility for patients to explore medical treatment, accumulate and approach medical data through internet connectivity. Security and privacy preservation is necessary for medical data of the patient in TMIS because of the very perceptive purpose. Recently, Mohit et al.’s proposed a mutual authentication protocol for TMIS in the cloud computing environment. In this work, we reviewed their protocol and found that it is not secure against stolen verifier attack, many logged in patient attack, patient anonymity, impersonation attack, and fails to protect session key. For enhancement of security level, we proposed a new mutual authentication protocol for the similar environment. The presented framework is also more capable in terms of computation cost. In addition, the security evaluation of the protocol protects resilience of all possible security attributes, and we also explored formal security evaluation based on random oracle model. The performance of the proposed protocol is much better in comparison to the existing protocol.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
With the quick progress of information technology, the use of TMIS is increasing day by day. To offer conducive and rapid network services, a novel kind of cloud computing organization [8, 25] which contains of a large number of processors, memories, high-speed networks, and various appliances is expected by consumers through the internet. Cloud computing services are offered via a browser to access an online data applications. These computing methods can be achieved by the cloud platform. Further, the work [44] explained that the cloud services will develop in the future. Therefore, the security and privacy of the cloud computing have become important issues. Various articles have proposed different issues of their apprehensions, such as: cloud security [9, 54], personal privacy and cloud services [11, 52]. According to the article [12], several operations are associated to cloud services and their uses.
With the fast development of internet appliances, people can select an appropriate hospital for high excellence of healthcare [2, 40]. Furthermore, for the progress of medical center superiority and the medical trade struggles the healthcare center sustains hospitals in remote localities. The medical manufacturing offers more specialized medical apparatus and improves medical maintenance superiority. With the help of medical manufacturing the healthcare centers are trying to improve their services so that patients can get easy access of medical facilities [36]. For an example, if the electronic medical records shared very well, the healthcare centers can share their resources through the internet. Patients need not to depict their inspection reports. On the other side, as we know if the patient has come to healthcare center, the medical employees should try to get the patient’s medical reports as early as possible for the preparation of medical treatment and to decrease errors. Moreover, the sensor planted in the patient’s body is another option for the healthcare center to get his/her medical report.
In medical organization, the cloud users store medical data in the cloud database to recapture the data securely. As it is common that cloud is not completely secured, so a protected and authenticated framework required to prevent simple security attacks [33]. In newly years, there are several authentication schemes [3,4,5, 13, 18, 45] proposed for TMIS, where the patients find their treatment online. As indicated in [14] TMIS proficiency medical doctor and patients to begin a conversation via public channels to support healthcare assistances precisely in the patient’s residence. As attribute of TMIS, both doctors and patients can perform together through the cloud server, i.e. a patient transfer his/her manifestations to the TMIS server and the doctor collect them and uploads diagnosis data report of the patient to the cloud server as if they are collaborating precisely, and it is happening via TMIS. Furthermore, the transmission is done via public channel, so it is important to know how to get extra benefits from medical resources with secure communication. Additionally, the security obligations, data confidentiality, patient anonymity, and patient authentication are the significant appearances to retain throughout the communication. In order to keep up patient anonymity [19, 28, 41], the identification of the patient need to differentiate from the others including eavesdropper. In TMIS, the patient’s medical reports are extremely significant, and they have not to revealed widely. As the message shared between patients/doctors and cloud are very serious information and so, data are gathered strongly. As medical information comes under imperative data and collapse of it may reason deterioration of ones life [50], thus it is essential to prove a protected scheme so that no attacker can attempt to find patient’s data and mistreatment it. Newly, there have been several protocols proposed to recognize anonymity concern. Mainly of these existing schemes are not relevant to offer patient anonymity in the healthcare system.
Related works
Smart card based authentication technique is the ordinary which adopted to avert unapproved access over the confident networks. There are various authentication scheme [35, 36, 42] obtainable using card [30], where the clients accept a password and imports a smart card with it. The authentication scheme is very favorable in different use, such as wireless sensor network, medical system and adhoc networks[6, 7, 20,21,22,23,24,25,26,27,28, 34, 40, 52,53,54]. Wu et al. first suggested a password-based user authentication protocol [47] and a reliable client authentication and key agreement protocol for network based hospital-acquired epidemic surveillance information system [49] then, Wu-Lee et al. [48] presented a secure authentication scheme for TMIS. Then, He et al. [18] accumulated that Wu et al.’s protocol[48] has different technical issues, like as an insider and impersonation attack, they also advised an improved scheme. In 2012, Wei et al. [46] observed that earlier schemes [18, 48] which are not secured across security flaws and recommended an appreciated protocol to prevent the occurring attacks. After that, Zhu [52] proved that Wei et al. [46] protocol is not protected against off-line password guessing attack and implemented a protected authentication protocol for TMIS, which based on the RSA cryptosystem. In 2013, Jiang et al.’ [29] proposed privacy enhanced authentication scheme for TMIS. Kumari et al. [31] proposed cryptanalysis and improvement of a privacy enhanced scheme TMIS which claimed that [29] fails to offer online password guessing attack, impersonation attack, and stolen-verifier attack. Nonetheless, Mishra et al. [38] presented a secure and capable chaotic map-based authenticated key agreement protocol for TMIS in which they examined that the scheme [29] does not resist denial-of-service attack. In current year , Liu et al.’s [55] proposed authentication based a practical privacy preserving data aggregation scheme which is efficient in communication security aspects.
In 2013, Tan [43] suggested a capable biometrics based authentication scheme for TMIS which is a smart card based password authentication and key agreement protocol by implementing a biometric system, and the protocol is more secure. Further, Yan et al. [50] proposed a secure biometric-based authentication protocol for TMIS which validated that the scheme [51] not passes to resist Denial-of-Service attack. In 2014, Mishra et al. [37] presented cryptanalysis and improvement of Yan et al. Biometric-based authentication method for TMIS which described that scheme [50] have a number of security outlet, like as the client privacy, ineffectual password, insufficient login phase, password guessing attack, biometric update phase and three-factor authentication difficulty. To decide the above recognized complication, they as well presented an enhanced protocol. Li et al. [33] presented a secure chaotic maps, and smart card based password authentication and key agreement scheme with user anonymity for TMIS and declared that the Lee et al.’s [32] chaotic –maps based client authentication protocol bear security weaknesses like absence of client identifier in authentication phase, service misuse attacks, and advised a more effective explanation for accessing TMIS. In 2014 Chen et al. [16] associates the cloud computing environment with mobile devices to give medical resources and uses cryptographic infrastructure to defend the patients secret information. Then, the scheme has several security flaws. Chen et al. [15] also proposed a new scheme for the same environment based on the cloud computing environment, although the scheme does not support message authentication and patient anonymity. To improvise the security flaws in [15], Chiou et al. [17] adapted the occurring protocol and believed that the framework prepares real TMIS, message authentication and patient anonymity. In 2016, Liu et al.’s [56] proposed a privacy-preserving health data aggregation scheme. In 2017, Liu et al. [57] presented a lightweight pseudonym authentication scheme for multi-medical server architecture for TMIS. Furthermore, Mohit et al. [39] proposed mutual authentication framework for cloud environment based healthcare system, we found that it is vulnerable to stolen verifier attack, many logged-in patient attack, patient anonymity, impersonation attack and fails to protect session key.
Motivation and contribution
Recently, Mohit et al. [39] suggested a mutual authentication protocol for TMIS that can work in the cloud computing environment.
-
It is analyzed and shown as follows:
-
Their scheme does not secure against stolen-verifier attack.
-
Their protocol does not support many logged in patient attack.
-
Their protocol does not ensure the anonymity of the patient.
-
Their protocol does not secure against impersonation attack.
-
Their protocol fails to protect session key.
-
-
In this regard, to attain security against the aforementioned attacks and to ensure the security of an entire package, a mutual authentication framework for TMIS is presented which is suitable for the cloud computing. The proposed framework has many significant characteristics, such as:
-
Mutual authentication is accomplished between healthcare center and cloud server, patients and cloud server, doctor and cloud server, and patient and healthcare centers to strengthen the safety of a structure and transforming information.
-
Furthermore, the proposed protocol is strong against many security attributes, i.e., implements security against, patient anonymity, man-in-the-middle attack, strong replay attack, known key security property, data confidentiality, data non-repudiation, message authentication, impersonation attack, session key security, stolen mobile device attack, off-line password/identity guessing attack and many logged-in patient’s attack.
-
We provided formal security analysis of our proposed protocol based on random oracle model.
-
We evaluate the proposed scheme with other existing works and found that our scheme gets minimum computational and communication expenditure, but ensures security of the system.
-
Road map of the paper
The rest of this paper is formulated as follows. In “??”, we describe the Preliminaries. Section “??”, We reviewed Mohit et al.’s scheme. Section “Cryptanalysis of Mohit et al.’s scheme”, The cryptanalysis of Mohit et al.’s Scheme. Section “??”, Security model, Section “The proposed protocol”, We proposed an improved mutual authentication protocol for healthcare system in cloud computing. Section “??”, formal security analysis of the proposed protocol. Section “Performance analysis”, performance analysis of the proposed and earlier existing schemes. Finally, Section “Conclusion”, discusses about the conclusion. Moreover, we make use of the notation/symbol throughout the paper as given in Table 1.
Preliminaries
Elliptic curve cryptography
Let q be the large prime and \(\mathcal {E}\) denote an elliptic curve over the prime finite field Fq, an equation of elliptic curve over prime finite field is given by y2 = x3 + ax + bmodq with a,b ∈ Fq and 4a3 + 27b2modq≠ 0. So, this is a non singular elliptic curve. Then, the additive elliptic curve group defined as G = {(x,y) : x,y ∈ Fq; \((x, y) \in \mathcal {E}\} \bigcup \{ {\Theta }\}\), where the point Θ is known as point at infinity which works as the identity element of G. The scalar multiplication on the group G is defined as tP = P + P... + P(t − times) and the point addition in G as: If P = (x1,y1), Q = (x2,y2) ∈ G , then P + Q = (x3,y3), where x3 = λ2 − x1 − x2modq, y3 = (λ(x1 − x2) − y1)modq where
The more details of elliptic curve group are given in [20].
-
Elliptic Curve Discrete Logarithms Problem (ECDLP): For given P,Q ∈ G, find \(k\in Z^{\ast }_{q}\) such that P = kQ, which is hard.
-
Elliptic Curve Computational Diffie-Hellman Problem (ECCDHP): For \(a, b \in Z^{\ast }_{q}\) and g is the generator of G, for given (g, ag, bg), then to compute abg is hard for the group G.
Hash function
Definition
A one-way hash function Hi : {0,1}∗→{0,1}l, inputs an arbitrary string length take x ∈{0,1}∗, and outputs a finite length string l bit message assimilate or hash value h(x) ∈{0,1}∗. A best hash function should contain the following properties:
-
For any given input x, it is accessible to calculate the digest h(x).
-
One-way: For a given hash value y = h(x), it is computationally not feasible to obtain x.
-
Weak-collision resistance: For any given input x, obtaining any other input y, with x≠y, such that h(x) = h(y) is computationally infeasible.
-
Strong-collision resistance: Finding a pair of inputs (x,y) with x≠y, such that h(x) = h(y) is also computationally not feasible.
Assumptions for the mutual authentication protocol
We take some assumptions to evaluation the invoked mutual authentication protocol.
Assumption 1
The hash results, the random number and secret numbers stored in cloud server. They reach the secure length l.
Assumption 2
The Ey (m), Dy (m) and h(.) are capable. That is to tell, in polynomial time, anybody can not decrypt the encrypted string Ey (m) without knowing y and no one find the collision of h(m), where m is the string [58,59,60,61].
Assumption 3
According to [2, 3, 60], both the identity and the one time password (OTP) of the entity have low entropy. There are two dictionaries in which one for identities and second for OTP. Advisory E can guess them in polynomial time.
Assumption 4
Adversary E can get the previous session keys, which is from the known-key attacks [60, 61].
Review of Mohit et al.’s scheme
Mohit et al. proposed a standard mutual authentication scheme for cloud based healthcare environment. There are five bodies : Patient, Cloud server, Doctor, Body sensor and Healthcare center. This scheme involves of four phases: (1) Healthcare center upload phase, (2) Patient data upload phase, (3) Treatment phase and (4) Checkup phase. Those are followed as:
Healthcare center upload phase (HUP)
The patient P registers herself/himself in the HC, and the HC provides OTP. The HC operates authentication with CS and uploads the P’s inspection medical report to CS as described bellow as:
- Step 1. :
-
The healthcare center generates inspection record mH = (IDP,DataP), and uses unique identity IDH of healthcare center with a elected random number R. The HC sends message {IDH,mH} to the CS via secure channel.
- Step 2. :
-
On receiving messages, CS takes secure key x and executes A = h(IDH∥R∥x),S1 = h(A) and B = IDH ⊕ x. Sends {S1,B} to HC via public channel.
- Step 3. :
-
On collecting message, HC computes x′ = B ⊕ IDH,A′ = h(IDH∥x′∥R) and checks whether \(S^{\prime }_{1}=?h(A^{\prime })\) holds or not. If it does not hold, HC exits the session. Otherwise HC computes session key SKHC = h(IDH∥A′∥B),key1 = h(IDP∥OTP) and encrypts the record as \(C_{H}= E_{key_{1}}(m_{H})\). Further, the HC computes MDH = h(mH), digital signature \(Sig_{H}= S_{PR_{H}}(MD_{H})\), encrypts \(C_{1}= E_{SK_{HC}}(ID_{P}, C_{H}, Sig_{H}, SID)\) and computes S2 = h(SKHC∥C1). Finally sends message {S2,C1} to the CS via public channel.
- Step 4. :
-
Upon gathering message, the CS computes session key \(SK^{\prime }_{HC}= h(ID_{H} \|A \|B)\) and checks whether \(S^{\prime }_{2}\overset {?}{=} h(SK^{\prime }_{HC}\|C_{1})\) hold or not. If, it does, CS authenticates HC and decrypts the message using session key \(SK^{\prime }_{HC}\) to get \((ID_{P},C_{H}, Sig_{H},SID)= D_{SK_{HC}}(C_{1})\), and store IDP,CH,SigH,SID. Otherwise, it fails and goes to Step.
Patient data upload phase (PUP)
The BS is fixed in the P’s body. The P requests BS, to assemble the reorganized health information, and presented it to the P through secure mobile device. The patient inputs identity IDP and OTP of his/her mobile device. The cloud server provides a slot sequence number sni, inspection record card mH to the patient which discussed below as:
- Step 1. :
-
P obtains health information message mB = (IDP,DataB) from BS through mobile device. Then, P inputs his/her IDP,SID and forwards message {IDP,SID} to the CS through a secure channel.
- Step 2. :
-
On collecting messages, CS computes I = sni ⊕ SID,S3 = h(SID∥I∥CH∥SigH) and sends {I,S3,CH,SigH} to P via open channel.
- Step 3. :
-
On getting information, P computes \(sn^{\prime }_{i}=I \oplus SID\) and checks whether \(S^{\prime }_{3}=?h(SID\|I\|C_{H}\|Sig_{H})\) grips or not. If is does, P authenticates CS and calculates session key SKPC = h(IDP∥SID), key1 = h(IDP∥OTP). Then, P decrypts the ciphertext to find \(m_{H}=D_{key_{1}}(C_{H})\) and computes \(MD_{H}=V_{PU_{H}}(Sig_{H})\). After that, checks mH =?h(MDH) holds or not. If is does, computes keyPD = h(IDP∥IDD∥sni), encrypts \(E_{key_{PD}}(m_{H}, m_{B})\), computes MDP = h(mB), generates signature \(Sig_{P}= S_{MD_{P}}(MD_{P})\) and computes S4 = h(SKPC∥CP∥SigP). Sends message {S4,CP,SigP} to CS over public channel.
- Step 4. :
-
On accepting messages, CS executes \(SK^{\prime }_{PC}=h(ID_{P}\|SID)\) and checks whether \(S^{\prime }_{4}=?h(SK^{\prime }_{PC}\|C_{P}\|Sig_{P})\) holds or not. If is does, cloud store CP,SigP. Otherwise, terminates the session.
Treatment phase (TP)
In this phase, doctor provides treatment of authenticated patient by acting authentication between the doctor and the cloud server. Cloud contains all the medical report of patients and sends to doctor. Doctor and cloud server perform as bellow:
- Step 1. :
-
Doctor D sends his/her identity IDD and random number RD to CS through secure public channel.
- Step 2. :
-
On receiving message, CS sends identity IDD of the P and sequence number sni to D via secure public channel. Then, CS computes S5 = h(RD∥SigP∥sni) and sends message {S5,SigP,CP} to D through public channel.
- Step 3. :
-
Upon receiving message, doctor verifies whether \(S^{\prime }_{5}=?h(RD\|Sig_{P}\|P_{P})\) holds or not. If it does, D authenticates the CS and computes session key SKDC = h(IDP∥RD∥sni), else rejects the message. Moreover, D computes keyPD = h(IDP∥IDD∥sni), and decrypts the received message as \((m_{H}, m_{B})= D_{key_{PD}}(C_{P})\), and verifies the patient’s signature using public key of P, which is \(MD_{P}=V_{PU_{P}}(Sig_{P})\) and checks whether MDP =?h(mB) hold or not. If it does, D generates medical report mD = (IDP,DataD), encrypts ciphertext \(C_{D}=E_{key_{PD}}(m_{H}, m_{B}, m_{D})\) and computes MDD = h(mD), D signature \(Sig_{D}=S_{PR_{D}}(MD_{D})\), and S6 = h(SKDC∥CD∥SigD) and sends message {S6,CD,SigD} to CS through public channel.
- Step 4. :
-
On getting messages, CS computes \(SK^{\prime }_{DC}=h(ID_{P}\|RD\|sn_{i})\) and check whether \(S^{\prime }_{6}=?h(SK^{\prime }_{DC}\|C_{D}\|Sig_{D})\) holds or not. If it does, CS store CD,SigD. Otherwise, terminates the session and goes to Step 1.
Check up phase (CP)
In this phase, the P authenticates CS to encrypted medical report of the patient. The detail of the narration of this section is as follows:
- Step 1. :
-
The patient inputs identity IDP, request and sends message {IDP,Request} to CS via secure public channel.
- Step 2. :
-
On collecting message, CS executes S8 = h(IDP∥IDD∥SigD) and sends message {S8,C8,SigD} to P via open channel.
- Step 3. :
-
Upon getting information, P checks whether \(S^{\prime }_{8}=? h(ID_{P}\|ID_{D}\|Sig_{D})\) holds or not. If it does not hold, exits the session. Otherwise, the P decrypts the ciphertext with using keyPD to get \((m_{H}, m_{B}, m_{D})= D_{key_{PD}}(C_{D})\) and verifies the signature \(Sig_{D}= V_{PU_{D}}(Sig_{D})\) and checks whether MDD =?h(mD) hold or not. If it does, P encrypts message \(C_{2}=E_{key_{P}}(m_{H}, m_{B}, m_{D})\), computes S9 = h(SID∥C2) and sends message {S9,C2} to the CS through public channel.
- Step 4. :
-
On receiving message, CS checks whether \(S^{\prime }_{9}=?h(SID\|C_{2})\) holds or not. If it does, CS store C2, otherwise terminates the session and goes to Step 1.
Cryptanalysis of Mohit et al.’s scheme
After reviewed the Mohit et al.’s scheme, we found five security weaknesses in the protocol. We have discussed below as:
Stolen-verifier attack
The stolen-verifier attack, means that an adversary stoles the password or identity-verifier from the CS database and applies an off-line guessing attack on it to get patient’s correct OTP or identity IDP. In Mohit et al.’s scheme, E stolen patient’s mobile phone, and intercepts in PUP. There are two following cases possible:
Stolen-verifier password attack
If an adversary E retrieves the store parameter key1 = h(IDP∥OTP), then he/she can successfully perform password guessing attack:
- Step 1.:
-
An adversary E intercept in PUP, and retrieves IDP.
- Step 2.:
-
E guesses one time password OTP∗ in one time password dictionary |OTP| and computes key1 = h(IDP∥OTP∗), verifies h(IDP∥OTP) =?h(IDP∥OTP∗).
- Step 3.:
-
If the verification succeed, E consider OTP∗ as a patients’s one time password. Otherwise step 2 is repeated.
The illustration of the attack is shown in Fig. 1.
Stolen-verifier identity attack
If E retrieves the store parameter key1 = h(IDP∥OTP), then he/she can successfully perform identity guessing attack:
- Step 1.:
-
E intercept in PUP, and retrieves patient’s OTP.
- Step 2.:
-
E guesses an identity IDE in identity dictionary |ID| and executes key1 = h(IDE∥OTP) and verifies h(IDE∥OTP) =?h(IDP∥OTP).
- Step 3.:
-
If the verification succeed, consider IDE as the patient identity, Otherwise Step 2 is repeated.
The illustration of the attack is shown in Fig. 2.
Many logged-in patient attack
The many logged-in patient attack is defined as the simultaneous access of a legitimate patient’s account of a CS by multiple adversaries using the same identity of the P. In Mohit et al.’s scheme, CS store the identity and OTP of the P in the database. But in this attack, we discuss only patient identities in PUP. Assume that legitimate identity IDP is accountably exposed to many adversaries E1,E2,E3,.....Ej......Em, all knows IDP and SID, then performed to CS at the same time by executing following steps:
- Step 1.:
-
Each Ej sends the message {IDP,SID} to CS.
- Step 2.:
-
The CS computes I1 = sni1 ⊕ SID,I2 = sni2 ⊕ SID,I3 = sni3 ⊕ SID,........Ij = snij ⊕ SID,.....Im = snim ⊕ SID and \({s^{1}_{3}}= h(SID\|I_{1}\| C_{H}\|Sig_{H}), {s^{2}_{3}}=h(SID \|I_{2}\| C_{H}\|Sig_{H}), {s^{3}_{3}}= h(SID\|I_{3}\|C_{H}\|Sig_{H}) .... {s^{j}_{3}}= h(SID\|I_{j}\|C_{H}\|Sig_{H}).....{s^{m}_{3}}= h(SID\|I_{m}\|C_{H}\|Sig_{H})\). Thus, CS allows all E1,E2,E3,.....Ej......Em to communicates in concurrently (Fig. 3).
Patient anonymity
In Mohit et al.’s protocol, patient has the same identity in PUP, TP and CP. There was no anonymous identity use in these phases. These offer a chance for the attacker to track patient’s activity over public network.
Impersonation attack
In HUP of Mohit et al.’s protocol, CS store parameters IDP,CH,SigH,SID in database and sni is public. If E intercepts in PUP and perform as:
- Step 1.:
-
E computes IE = sni ⊕ SID,S3E = h(SID∥IE∥CH∥SigH) and sends {IE,S3E,CH,SigH} to P.
- Step 2.:
-
On receiving message, P computes \(sn^{\prime }_{i}= I_{E}\oplus SID, S^{\prime }_{3}= h(SID\|I_{E}\|C_{H}\| Sig_{H})\) and verifies that \(S_{3E}= S^{\prime }_{3}\). Further, the P computes session key \(SK_{PC}= h(ID_{P}\|SID), key_{1}=h(ID_{P}\|OTP), m_{H}= D_{key_{1}}(C_{H}), MD_{H}= V_{PU_{H}}(Sig_{H})\), where mH = h(MDH) and computes keyPD = h(IDP∥IDD∥sni), encrypts \(C_{P}= E_{key_{PD}}(m_{H}, m_{B})\), computes MDP = h(mB), signature \(Sig_{P}= S_{PR_{P}}(MD_{P}), S_{4}= h(SK_{PC}\|C_{P}\|Sig_{P})\) and sends {S4,CP,SigP} to E.
- Step 3.:
-
On receiving message, E computes \(SK^{E}_{PC}=h(ID_{P}\|SID)\) and \({S^{E}_{4}}= h(SK^{E}_{PC}\|C_{P}\|Sig_{P})\).
Here, \(SK^{E}_{PC}\)= SKPC and \({S^{E}_{4}}\) = S4. Thus, Mohit et al.’s scheme fails to protect the impersonation attack.
Fails to protect the session key
In PUP of Mohit et al.’s protocol. Then, P computes session key SKPC = h(IDP∥SID). From impersonation attack session 4.4, adversary E computes session key \(SK^{E}_{PC}= h(ID_{P}\|SID)\). Thus E successfully computes the session key of the patient. Similarly, E got session key in HUP and TP. Hence, Mohit et al.’s scheme fails to support of session key.
Security model
In this section, we discuss the security model on the proposed scheme which is based on [1, 10, 53, 61]. There are two entities U and V, or every partner I with no difference in the proposed protocol \(\mathcal {P}\). U has an identity IDU and a password PWU. V has an identity IDV and a password PWV. All passwords are in a dictionary with size \(\mathcal {N}\), and elliptic curve group G has a generator g of order q.
Every party has several occurrence. Let US be the Sth occurrence of U. Similarly, V S and IS can be prescribed. E case is an oracle. We apply a simulator to provides the replay to input information. In this way, there are three cases for an oracle: accept, reject and ⊥. If an oracle finds a ordinary information, the obtain state is achieved. If an incorrect information is collected, the reject case is arrived. Otherwise, if no response is generated, ⊥ occurs. Once upon a time the oracle Ui or V j is established and determines a session key, each of them has the subsequent elements: a session identity \((sid_{U^{i}})\) or \((sid_{V^{j}})\), a partner identity \((pid_{U^{i}})\) or \((pid_{V^{j}})\), and a session key \((SK_{U^{i}})\) or \((SK_{V^{j}})\). E can totally run the simulator and query oracles to destroy the security of authentication or the session keys. We list all the oracles as followings:
- Execute (Ui,V j)::
-
This query simulates the passive attack, and permits the attacker E to learn all the transmitted communication between the instances of entities Ui and V j.
- Send[[spiespace:
-
]\((I, {I^{j}_{r}}, M)\):] This query simulates the active attack and It makes that the body I forwards a message M to the occurance \({I^{j}_{r}}\). If M is exact message and \({I^{j}_{r}}\) is prepared to accept the information, the simulator will return the message which \({I^{j}_{r}}\) should develop. Otherwise, if M is wrong, the query is aborted.
- Reveal (Ik)::
-
It expresses known-key attacks and for U and V. If Ik grasps the status of partnering, the adversary E can obtain the session key through asking this query.
- Corrupt (Ik)::
-
This query is use to check the perfect forward security property of the session key on the oracle Ik. All the messages of Ik is obtained by adversary E after this query, since E has known some message in the system, we list the specific as follow:
-
Corrupt (Ui): It allows the adversary E to concession the long-term private key of the session key of Ui.
-
Corrupt (V j): It allows the adversary E to concession the long-term private key of the session key of V j.
-
- Test (Ik)::
-
At last adversary E chooses a session to challenge. At this time I may be U or V. If Ik has not been approved or it is not able for the view sfs − fresh which will disclosed below, the simulator will go back ⊥. Otherwise a coin s is toss. The simulator will output the actual session key if s = 1 appear. If s = 0 appears, a random string say session key is returned to adversary E.
We use few definitions for the verification of proof as follows:
- Partnering : :
-
As the session key is created between Ui and V j, we call Ui and V j are partners if and only if they are established and \(sid_{U^{i}}= sid_{V^{j}}\), \(pid_{U^{i}} = V^{j}, Pid_{V^{j}}= U^{j}\) and \(SK_{U^{i}}= SK_{V^{j}}\).
- pfs-fresh (fresh with perfect forward security)::
-
We use this opinion for only Ui and V j, we say that Ik is the pfs − fresh if no one the followings queries appears:
-
E Reveal(Ik) occurs;
-
E Reveal\((pid_{I^{k}})\) appears;
-
Before Test arises, Corrupt(Ik) or \(\textit {Corrupt}(pid_{I^{k}} )\) has been asked.
-
- pfs- ake security : :
-
we define E’s advantage against the protocol \(\mathcal {P}\) is the probability that E properly guesses the coin s after Test(Ik) query. Of course, Ik is established and pfs − fresh.
The advantage of E is \(Adv^{pfs - ake}_{\mathcal {P}}(E)= 2Pro[s= s^{\prime }]-1\).
Where E outputs s′. If Qs is the number of Send queries and \(Adv^{pfs - ake}_{\mathcal {P}}(E)\) is negligibly longer than \(\frac {O(Q_{s})}{N}\) with l, the protocol is pfs − ake secure.
To show the protocol, we take two new assumptions for ECC. Those are based on the “Elliptic curve cryptography”.
-
Elliptic Curve Decisional Diffie-Hellman problem (ECDDHP): Let ag,bg,cg ∈ G, The probability for E to determine whether cg = abg polynomial time t is \(Adv^{ECDDHP}_{E}(t)\) and 𝜖 is an ignorably small positive real number and in fact \(Adv^{ECDDHP}_{E}(t) \leq \epsilon \).
-
Elliptic Curve Gap Diffie-Hellman problem (ECGDHP): Let ag,bg ∈ G, The probability for E to execute abg with an ECDDHP oracle in polynomial time t is \(Adv^{ECDDHP}_{E}(t) \leq \epsilon \).
The proposed protocol
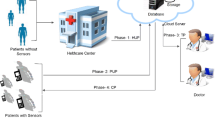
Architecture
There are five components associated in the proposed protocol for conversation are as follows:
- (1) Patient: :
-
A person, who is applying for medical treatment.
- (2) Doctor: :
-
A person, who has been skilled in medical science and offer treatment to patients.
- (3) Healthcare center: :
-
A physical residence where the patient takes treatment.
- (4) Cloud server: :
-
A server to collect patient’s medical data or records.
- (5) Body sensor: :
-
A device associated with a physical impression of the patient and sends information to the patient’s mobile device.
The architecture of this proposed protocol is shown in the Fig. 4, and the details are as follows:
-
Firstly P goes to HC for the routine-checkup/ inspection and takes registration, where HC support the report of the P.
-
HC uploads the medical report/data of P to the CS. B installed in the P’s body collects the fitness information of the patient and forward to a P’s mobile device securely.
-
P upload current medical record by updating the earlier data of the HC with the developed record by BS to the CS.
-
CS forwards the medical information of P to the appreciated D in order of sequence number.
-
D executes medical treatment by looking into the medical data and uploads latest information with the digital signature to the CS.
-
CS sends the final medical report to P.
Protocol description
This scheme contains of five phases: (1) Healthcare center upload phase, (2) Patient data upload phase, (3) Treatment phase, (4) Checkup phase, and (5) Emergency phase. The details are as follows:
Healthcare center upload phase (HUP)
The patient registers herself/himself in HC, and HC assigns OTP and a dynamic pseudo random identity SID to P through secure mobile device. In this phase, HC performs mutual authentication with CS and uploads the P’s medical report to CS as displayed in the Fig. 5 and expressed as below:
- Step 1. :
-
The healthcare center generates inspection report MH = (IDP,DataP), random number \(r \in Z^{\star }_{q}\), and inputs unique identity IDH and r. Furthermore, HC sends M1 = {IDH,r,TH1} to CS via a secure channel.
- Step 2. :
-
On collecting message, CS verifies TC1 − TH1 ≤△T. If it does not hold, the CS terminates the session. Otherwise, generates random number \(x \in Z^{\star }_{q}\) and computes H1 = h(IDH∥r∥x), A = IDH ⊕ x,H2 = h(H1∥A∥r). Further, generates another random number \(b \in Z^{\star }_{q}\) and sends message M2 = {H2,A,b,TC2} to HC via public channel.
- Step 3. :
-
On getting messages, HC checks TH2 − TC2 ≤△T. If it does not hold, HC terminates the session. Otherwise, computes \(y= A\oplus ID_{H}, H_{3}= h(ID_{H}\| r \| y), \\H^{*}_{2}=h(H_{3}\|A\|r)\) and verifies whether \(H^{*}_{2}=? H_{2}\) hold or not. If it does not hold, HC exits the session. Otherwise, HC authenticates CS and generates random number \(a \in Z^{\star }_{q}\). Further, HC computes SKHC = h(IDH∥H3∥A∥brg), K1 = h(IDP∥OTP∥IDH), encrypts \(C_{H}= E_{K_{1}}(M_{H})\), computes \(MD_{H}= h(M_{H}), Sig_{H}= S_{PR_{H}}(MD_{H})\), H4 = h(SKHC∥CH∥SigH∥abg∥TH3) and again encrypts \(C_{1}= E_{SK_{HC}}(ID_{P}, a, C_{H}, H_{4}, Sig_{H}\), SID,TH3). Finally, the HC sends ,message M3 = {C1,TH3} to the CS via public channel.
- Step 4. :
-
Upon receiving message, the CS verifies TC3 − TH3 ≤△T. If it does not hold, CS terminate the session. Otherwise, computes SKCH = h(IDH∥H1∥A∥brg), decrypts (IDP,a,CH,H4, \(Sig_{H}, SID, T_{H3})= D_{SK_{CH}}(C_{1})\), computes H5 = h(SKCH∥CH∥SigH∥abg∥TH3) and verifies whether H5 =?H4 hold or not. If it does, CS authenticates HC and CS stores IDP,CH,SigH and SID. Otherwise, CS terminates the session.
Patient data upload phase (PUP)
The patient requests to BS, to gather the updated fitness information, and arranges it to the P through the mobile device securely. The P makes the request using his/her identity IDP and OTP of the mobile device. CS contributes an engagement sequence number sni, inspection data report MH to P as displayed in the Fig. 6 and discussed as below:
- Step 1. :
-
The patient gets report MB = (IDP,DataB) from body sensor via secure mobile device. Then, P takes his/her identity IDP and dynamic pseudo random SID and sends message M4 = {IDP,SID,TP1} to CS via secure channel.
- Step 2. :
-
Upon collecting message, CS verifies TC4 − TP1 ≤△T. If it does not hold, CS terminate the session. Otherwise, computes N = sni ⊕ h(SID∥IDP), generates random number \(c \in Z^{\star }_{q}\), computes H6 = h(SID∥sni∥CH∥SigH∥TC5), encrypts \(L_{1}=E_{sn_{i}}(Sig_{H}, C_{H},H_{6}, ID_{H}, c, T_{C5})\) and sends message M5 = {L1,N,TC5} to P.
- Step 3. :
-
On receiving message, P checks TP2 − TC5 ≤△T. If it does not hold, P stops the session. Otherwise, computes N1 = N ⊕ h(SID∥IDP), decrypts \((Sig_{H}, C_{H},H_{6}, ID_{H}, c, T_{C5}) = D_{N_{1}}(L_{1})\), computes H7 = h(SID∥N1∥CH∥SigH∥TC5) and verifies whether H7 =?H6 hold or not. If it does not hold, P exits the session. Otherwise he/she authenticates CS, and generates random number \(d \in Z^{\star }_{q}\). Further, computes SKPC = h(IDP∥IDH∥N1∥H7∥cdg) and K2 = h(IDP∥OTP∥IDH). Moreover, P decrypts the report \(M^{*}_{H}= D_{K_{2}}(C_{H})\) and checks whether \(M^{*}_{H}=? M_{H}\) hold or not. If it does not hold, P exits the session. Otherwise, computes \(MD^{*}_{H}= V_{PU_{H}}(Sig_{H}\)) and verifies \(MD^{*}_{H}=? MD_{H}\). if it hold, computes KPC = h(IDP∥IDH∥N1), encrypts \(C_{P}=E_{K_{PC}}(M_{H},M_{B})\), computes MDP = h(MB), makes digital signature \(Sig_{P}= S_{PR_{P}}(MD_{P})\), computes H8 = h(SKPC∥CP∥SigP∥cdg∥TP3), again encrypts \(L_{2}=E_{N_{1}}(d, H_{8}, Sig_{P}, C_{P}, ID_{P}, T_{P3})\) and sends message M6 = {L2,TP3} to CS via public channel.
- Step 4. :
-
Upon receiving message, the CS verifies TC6 − TP3 ≤△T. If it does not hold, CS terminate the session. Otherwise, decrypts \((d, H_{8},Sig_{P},C_{P}, ID_{P}, T_{P3}) = D_{sn_{i}}(L_{2})\), computes session key SKCP = h(IDP∥IDH∥sni∥H6∥cdg), H9 = h(SKCP∥CP∥SigP∥cdg∥TP3) and checks whether H9 =?H8 hold or not. If it does, CS authenticates P and stores CP,SigP. Otherwise, terminates the session.
Treatment phase (TP)
In this phase, the doctor and cloud server authenticates to each other and the doctor performs treatment of the patients. If they are valid entities, the cloud server uses the identity of doctor IDD to find all of the D’s requests by P, who have prepared medical appointments, and forwards the P’s treatment description to doctor as displayed in the Fig. 7 and described as below:
- Step 1. :
-
The Doctor generates random number e \(\in Z^{\star }_{q}\) and sends message M7 = {IDD,e,TD1} to the CS via a secure channel.
- Step 2. :
-
On receiving message, CS verifies TC7 − TD1 ≤ΔT. If it does not hold, CS exits the session. Otherwise, computes N2 = sni ⊕ h(SID∥IDD∥IDP), generates random number \(f \in Z^{\star }_{q}\), computes H10 = h(e∥sni∥SigP∥CP∥TC8), \(L_{3}=E_{sn_{i}}(Sig_{P}, C_{P}, ID_{P}, ID_{H}, H_{10}, f, T_{C8})\). Further, sends the message M8 = {L3,N2,TC8} to D via public channel.
- Step 3. :
-
On receiving message, D checks TD2 − TC8 ≤△T. If it does not hold, D terminates the session. Otherwise, computes N3 = N2 ⊕ h(SID∥IDD∥IDP) and decrypts (SigP,CP,IDP,IDH, \(H_{10}, f, T_{C8})= D_{N_{3}} (L_{3})\). Further, D computes H11 = h(e∥N3∥SigP∥CP∥TC8), verifies whether H11 =?H10 hold or not. If it does not hold, D exits the session. Otherwise, he/she authenticates to the CS and computes SKDC = h(IDP∥IDD∥N3∥H11∥efg), KDC = h(IDP∥IDH∥N3). Moreover, D decrypts the report as \((M_{H}, M_{B})=D_{K_{DC}}(C_{P})\), computes \(MD^{*}_{P}= V_{PU_{P}}(Sig_{P})\) and checks whether \(MD^{*}_{P}= ? MD_{P}\) hold or not. If it does not hold, then D stops the session. Otherwise, D makes a medical diagnosis report based on MD = (IDP,DataD) and encrypts \(C_{D}= E_{K_{DC}}(M_{H}, M_{B}, M_{D})\). Furthermore, D computes MDD = h(MD) and makes digital signature message \(Sig_{D}= S_{PR_{D}}(MD_{D})\). In additionally, D computes H12 = h(SKDC∥CD∥SigD∥SigP∥efg∥TD3), encrypts L4=\(E_{N_{3}}(Sig_{D}\), CD, H12, TD3) and sends message M9 = {L4,TD3} to CS via public network.
- Step 4. :
-
On accepting message, CS verifies TC9 − TD3 ≤△T. If it does not hold, CS terminates the session. Otherwise, CS decrypts (SigD,CD, \(H_{12}, T_{D3})=E_{sn_{i}}(L_{4})\), computes SKCD = h(IDP∥IDD∥sni∥H10∥efg),H13 = h(SKCD∥CD∥SigD∥SigP∥efg∥TD3) and checks whether H13 =?H12 hold or not. If it does, CS authenticates D and stores CD,SigD. Otherwise, D terminates the session.
Checkup phase (CP)
In this phase, P and CS authenticate to each other. Then, CS sends the encrypted the report to P. The detail description of this phase as displayed in the Fig. 8 and explained as below:
- Step 1. :
-
The patient takes his/her identity IDP, as request and sends message M10 = {IDP,request,TP4} to CS via a secure channel.
- Step 2. :
-
Upon collecting message, CS verifies TC10 − TP4 ≤△T. If it does not hold, CS exits the session. Otherwise, computes N4 = h(IDP∥sni). Further, generates random number \(f_{1} \in Z^{\star }_{q}\), computes H14 = h(IDP∥CD∥SigD∥SigP∥TC11), \(L_{5}=E_{N_{4}}(H_{14},Sig_{D}, C_{D}, f_{1}, T_{C11})\) and sends message M11 = {L5,TC11} to P via public channel.
- Step 3. :
-
On receiving message, P checks TP4 − TC11 ≤△T. If it does not hold, P stop the session. Otherwise, computes N5 = h(IDP∥N1), decrypts \((H_{14}, Sig_{D}, C_{D}, f_{1}, T_{C11})= D_{N_{5}} (L_{5})\), and computes \(H^{*}_{14}= h(ID_{P}\|C_{D}\|Sig_{D}\|Sig_{P}\| T_{C11})\), and verifies whether \(H^{*}_{14}=? H_{14}\) hold or not. If it does not hold, D stops the session. Otherwise he/she authenticates CS. Then, P decrypts the report as \((M_{H}, M_{B}, M_{D})= D_{K_{PC}}(C_{D})\), and computes \(MD^{*}_{D}= V_{PU_{D}}(Sig_{D})\) to checks whether \(MD^{*}_{D}=? h(M_{D})\) hold or not. If it does not hold, then stops the session. Otherwise, generates random number \(f_{2} \in Z^{\star }_{q}\), encrypts \(C_{2}= E_{K_{PC}}(M_{H}, M_{B}, M_{D}, f_{2})\), computes H15 = h(N5∥C2∥SigP∥SigD∥f1f2g∥TP6), again encrypts \(L_{6}=E_{N_{5}}(C_{2}, H_{15}, f_{2}, T_{P6})\) and sends message M12 = {L6,TP6} to CS via public channel.
- Step 4. :
-
Upon receiving message, CS verifies TC12 − TP5 ≤△T. If it does not hold, CS terminates the session. Otherwise, CS decrypts computes \((C_{2},H_{15}, f_{2}, T_{P6})= D_{N_{4}} (L_{6})\), computes \(H^{*}_{15}= h(N_{4}\|C_{2}\|Sig_{P}\|Sig_{D}\|f_{1}f_{2}g\|T_{P6})\) and also verifies whether \(H^{*}_{15}=? H_{15}\) hold or not. If it does, CS authenticates P and stores C2. Otherwise, terminates the session.
Emergency phase (EP)
The patients use the body sensors network, and relocate the regular medical information to the cloud server. If the patient has an emergency, then the patient inputs his/her identity, sequence number and request sends to CS. Then, CS sends the information to HC. After verification the doctor provides treatment to the patients. The detail description of this phase as shown in the Fig. 9 and discussed as below:
- Step 1. :
-
P inputs his/her identity IDP,N5,request, computes H16 = h(IDP∥N5∥TEP1), encrypts \(L_{7}=E_{N_{5}}(H_{16}, T_{EP1})\) and sends message ME1= {L7,TEP1} to CS via public channel.
- Step 2. :
-
On receiving message, CS verifies TEC1 − TEP1 ≤△T. If it does not hold, CS terminates the session. Otherwise, decrypts \((H_{16}, T_{EP1})= D_{N_{4}} (L_{7})\), computes \(H^{*}_{16}= h(ID_{P}\|N_{4}\|T_{EP1})\) and checks whether \(H^{*}_{16}=? H_{16}\) hold or not. If it does not hold, CS terminates the session. Otherwise, generates random number \(p \in Z^{\star }_{q}\), computes H17 = h(IDP∥IDH∥SigH∥SigP∥TEC2), \(L_{8}=E_{SK_{CH}}(H_{17}, p, Sig_{P}, ID_{P}, T_{EC2})\) and sends message ME2 = {L8,TEC2} to HC via public network.
- Step 3. :
-
On receiving messages, HC verifies TEH1 − TEC2 ≤△T. If it does not hold, HC terminates the session. Otherwise, decrypts (H17,p,SigP, \(ID_{P}, T_{EC2})= D_{SK_{HC}} (L_{8})\), computes \(H^{*}_{17}= h(ID_{P}\|ID_{H}\|Sig_{H}\|Sig_{P}\|T_{EC2})\) and verifies \(H^{*}_{17}=? H_{17}\) hold or not. If it does not hold, HC terminates the session. Otherwise, generates random number \(s \in Z^{\star }_{q}\), computes SKHP = h(IDP∥IDH∥SigH∥SigP∥psg), H18 = h(IDP∥IDH∥p∥s∥TEH2), \(L_{9}=E_{SK_{HC}}(s, H_{18}, T_{EH2})\) and sends message ME3 = {L9,TEH2} to CS via public channel.
- Step 4. :
-
On receiving message, CS verifies TEC3 − TEH2 ≤△T. If it does not hold, CS stops the session. Otherwise, CS decrypts \((s, H_{18}, T_{EH2})= D_{SK_{CH}} (L_{9})\), computes \(H^{*}_{18}= h(ID_{P}\|ID_{H}\| p\|s\|T_{EH2})\) and verifies \(H^{*}_{18}=? H_{18}\) hold or not. If it does not hold, CS terminates the session. Otherwise, authenticates HC by computing H19 = h(SigP∥SigH∥pg∥sg∥TEC4), encrypts \(L_{10}=E_{N_{4}}(ID_{H}, p, s, H_{19}, T_{EC4})\) and sends message ME4 = {L10, TEC4} to P via public network.
- Step 5. :
-
Upon receiving message, P verifies TEP2 − TEC4 ≤△T. If it does not hold, P terminates the session. Otherwise, decrypts \((ID_{H}, p, s, H_{19}, T_{EC4})=D_{N_{5}} (L_{10})\), computes \(H^{*}_{19}= h(Sig_{P}\| Sig_{H}\|pg\|sg\|T_{EC4})\), and verifies whether \(H^{*}_{19}=? H_{19}\) hold or not. If it does not hold, P terminates the session. Otherwise, P authenticates CS and computes session key SKHP = h(IDP∥IDH∥SigH∥SigP∥psg).
Security proof
Formal proof of the proposed protocol
Theorem: Patient data upload phase (PUP) of our protocol \(\mathcal {P}\) employees a additive cyclic group G on an elliptic curve with a large prime order q. \(\mathcal {N}\) is the size of one time password dictionary \(\mathcal {D}\). If adversary E makes no more than Qs send queries, Qh hash queries, and Qe execute queries, then
Where t′ = t + (O(Qe) + O(Qs))TM and TM is the time of one multiplication in G.
Proof: We prove this theorem with the help of a sequence of games. There are total eight games from G0 to G7. Succj is the action for adversary E accurately guessing the coin s through the investigation session in Game Gj. Since, there is one patient P in these games, E want to computes or guesses P’s identity IDP. We have to discuss the games following as:
-
Game G0: This game is the actual game against the proposed authentication scheme of PUP with the random oracle model, from the definition, we have
$$ Adv^{pfs - ake}_{\mathcal{P}}(E)= 2Pro[Succ_{0}]-1 $$(1)Furthermore, If various atypical circumstances occur, a random s∗ is called as a report. The list of the atypical circumstances as follows:
-
The game exit or cancels or since E does not present the predicted s∗.
-
More queries than the prearranged upper bound are used by E.
-
More time than the deliberated upper bound is used by E.
-
-
Game G1: In this game, we take addition of all counterfeited queries. Moreover, there are only three lists to accumulate the answers to the queries.
-
LH: For the answer to all hash queries.
-
LP: For the transcription of the communication.
-
LE: It is for the respond of the two random oracles queried precisely by adversary E.
The queries are established in Fig. 10. According to the situations mentioned above, Game G1 and Game G0 are indistinguishable and we can notice that
$$ Pro[Succ_{1}]=Pro[Succ_{0}] $$(2) -
-
Game G2: In this game, we avoid the collisions in the transcriptions. There are three types of collisions. As stated in the birthday paradox, we display the probabilities of them:
-
\( c, d \in Z^{\star }_{q}\) may collide particular session and upper bound for the case is
$$\frac{O(Q_{s}+ Q_{e})^{2}}{2(q-1)} $$ -
Dynamic pseudo random identity \(SID \in Z^{\star }_{q}\) may collide in different session and upper bound for the case is
$$\frac{O(Q_{s}+ Q_{e})^{2}}{2^{l + 1}} $$ -
The hash function results may collide and upper bound for the case is
$$\frac{O(Q_{h})^{2}}{2^{l + 1}}. $$
From Game G2 and Game G1 are indistinguishable except the collisions occur. We observe that
$$\begin{array}{@{}rcl@{}} |Pro[Succ_{2}]&-&Pro[Succ_{1}]|\leq \frac{O(Q_{s}+ Q_{e})^{2}}{2(q-1)}\\ &+&\frac{{O(Q_{h})^{2}}+ O(Q_{s}+ Q_{e})^{2}}{2^{l + 1}} \end{array} $$(3) -
-
Game G3: In this game, we consider the probability of the attack that adversary E fakes message M4. Since the simulator permits the answer as CS, we attach some steps on Send(Pi,CSj,M4) the simulator wants to verify if M4 ∈ LP. If it is failing the query will stop. Here Game G3 and Game G2 are indistinguishable if the verifiers are under deliberation. We can obtain
$$ | Pro[Succ_{3}]-Pro[Succ_{2}]| \leq \frac{O(Q_{s})}{2^{l}} $$(4) -
Game G4: In this game, we deal with the probability of the attack that adversary E fakes message M5. Since the simulator permits the answer as P, we attach some steps on Send(CSj,Pi,M5) the simulator wants to verify if M5 ∈ LP and, (⋆∥IDP,⋆),(⋆∥sni∥CH∥SigH∥TC5,H6) ∈ LE. If it is failing the query will stop. Here Game G4 and Game G3 are indistinguishable if the verifiers are under deliberation. We can obtain
$$ | Pro[Succ_{4}]-Pro[Succ_{3}]| \leq \frac{O(Q_{s}+Q_{e})}{2^{l}} $$(5) -
Game G5: In this game, we consider the probability of fake message M6. Since the simulator gives the response as the CS. We append some steps on Send(Pi,CSj,M6). The simulator wants to validate if M6 ∈ LP and (⋆∥IDP,⋆),(⋆∥⋆∥CH∥SigH∥TC5,H7),(1,IDP∥IDH∥⋆∥⋆∥⋆,⋆),(IDP∥IDH∥⋆,KPC),(⋆∥CP∥SigP∥⋆∥TP3,H8) ∈ LE. If it is failing the query will stop. Here Game G5 and Game G4 are indistinguishable if the verifiers are under deliberation. We can obtain (⋆∥IDP,⋆),(⋆∥⋆∥CH∥SigH∥TC5,H7),(1,IDP∥IDH∥⋆∥⋆∥⋆,⋆),(IDP∥IDH∥⋆,KPC),(⋆∥CP∥SigP∥⋆∥TP3,H8) ∈ LE. So we found that
$$ |Pro[Succ_{5}]-Pro[Succ_{4}]|\leq \frac{O(Q_{h}+ Q_{s})}{2^{l}} $$(6) -
Game G6: In this game, we take on ECGDHP. If adversary E can obtain the actual session key via hash oracle and be the success, we judge that E crack the problem. We adjust the hash oracle as follows: On one occasion E queries (1,IDP∥IDH∥sni∥X∥X,X),(X∥CP∥SigP∥X∥X∥TP3), the simulator first verifies if (1,IDP∥IDH∥sni∥H6∥⋆,SKPC),(SKPC∥CP∥SigP∥ ⋆ ∥TP3) ∈ LE. If it is in, SKPC is returned. Otherwise, the simulator utilizes the ECGDHP oracle to evaluator X =?ECGDHP(cg,dg). If it is unsuccessful, the query is dropped. Otherwise, the simulator selects a random string SKPC ∈{0,1}l outputs it and adds (1,IDP∥IDH∥sni∥X∥X,SKPC) to LE.
We analyze this game with two characteristics: the active attack and the passive attack. First E asks a Corrupt query and obtains all information:
-
It is for online OTP guessing attacks. E could embrace judge a OTP from the dictionary. Since E can utilize Send query Qs and the size of OTP dictionary is \(\mathcal {N}\), the probability for E to guess the exact OTP by loading a session is bounded by \(\frac {Q_{s}}{\mathcal {N}}\).
-
For the passive attacks. There are two methods in this case:
-
◇ The first is E finds information, he/she asks Execute queries. At the end E asks the hash query to succeed and cracks ECGDHP. We can find cdg. From LE with the probability 1/Qh. So the probability for this case is bounded by \(Q_{h}Adv^{ECGDHP}_{E}(t+O(Q_{e})T_{M}\)).
-
◇ The other is E asks Send queries successively. Like the first kind of a passive attack, we can find that the upper bound probability of this case is \(Q_{h}Adv^{ECGDHP}_{E}(t+ O(Q_{s})T_{M})\)
-
-
The probability for the two types of the passive attack is
Let t′ = (2t + [O(Qs) + O(Qe)]TM), then we got
-
Game G7: This game is for perfect forward security. E can determine all planned Corrupt queries. But according to the approach of sfs − fresh, Corrupt queries should be asked after the Test query. So adversary E can only exploit the historical queries and transcripts. In this last game, we can obtain (1,IDP∥IDH∥sni∥X∥X,SKPC) in LE. The probability of getting cg and dg in the same session is 1/(Qs + Qe)2 and we have
$$ |Pro[Succ_{7}]-Pro[Succ_{6}]|\!\!\leq\!\! Q_{h}(Q_{s}+Q_{e})^{2}Adv^{ECGDHP}_{E}(t^{\prime}) $$(8)
Combining the above games, there is no benefit for E to guess the session key and \(Pro [Succ_{6}] =\frac {1}{2}\). Taking the sum of all results of these games, Theorem can be proved.Remark : Similarly the formal security proof of Healthcare center upload phase (HUP), Treatment phase (TP) and Emergency phase (EP) can also be analyzed.
Informal security analysis
In this phase, we evaluated that the prospective scheme has the capability to resist different cryptographic attacks.
Proposition 1
The proposed framework could assure the man-in-the-middle attack.
Proof
In our protocol, every step of every phase has time-stamp condition Ti − Tj ≤△T and hash condition Hi =?Hj. If possible, an attacker inter in these phases after verifying the times-tamp condition then, check the hash condition Hi=?Hj which not possible by the definition one way hash function is secure. Thus adversary will not get success in any phase. Therefore, our protocol protects the man-in middle attack. □
Proposition 2
The proposed protocol could assure the patient anonymity.
Proof
We describe the patient anonymity in each authentication phase:
-
During HUP, the patient identity IDP is encrypted by screening original identity. Here, patient identity IDP in encrypted with session key SKHC = h(IDH∥H1∥A∥brg), as get \(C_{1}= E_{SK_{HC}}(ID_{P}, a, C_{H}, H_{4}, Sig_{H}, SID, T_{H3})\) and only be decrypt by cloud server \((ID_{P}, a, C_{H}, H_{4}, Sig_{H}, SID, T_{H3})= D_{SK_{CH}}(C_{1})\) with containing session key SKCH = h(IDH∥H1∥A∥brg) and verifies the condition H5 =?H4 then, stores IDP,CH,SigH,SID.
-
During PUP, the patient identity IDP is encrypted by screening original identity. Here, patient identity IDP in encrypted with session key N1 = N ⊕ h(ID(SID∥IDP), as get \(L_{2}= E_{N_{1}}(d, H_{8}, Sig_{P}, C_{P} a, C_{H}, ID_{P}, T_{P3})\) and only be decrypt by cloud server \((d, H_{8}, Sig_{P}, C_{P}, a, C_{H}, ID_{P}, T_{P3})= D_{sn_{i}}(L_{2})\), where, sni is the sequence number of patient and verified hash condition H9 =?H8 then, stores CP,IDP,SigP.
Similarly, the patient anonymity is hold in TP, CP and EP. Therefore, our protocol provides patient anonymity. □
Proposition 3
The proposed protocol could protect the strong replay attack.
Proof
Replay attack is a common attack in authentication procedure. However, the common countermeasures are time-stamps and random number. In our protocol, we adopt the time-stamp and random number as a counter-measure in every steps of every phases, receiver will check it. the times-tamps is legal or not by checking the valid time interval with equation Ti − Tj ≤△T , where △T is the valid time interval. Further, random number used random number to computing session key, hash values and different keys. Therefore, replay attack could not work in the proposed protocol. □
Proposition 4
The proposed protocol could provide the known-key security property.
Proof
The proposed scheme describes the different session keys in different phases:
-
During HUP, the HC computes session key SKHC = h(IDH∥H3∥A∥brg) and CS computes session key SKCH = h(IDH∥H1∥A∥brg).
-
During PUP, P computes session key SKPC = h(IDP∥IDH∥N1∥H7∥cdg) and CS computes SKCP = h(IDP∥IDH∥sni∥H6∥cdg).
-
During TP, D computes session key SKDC = h(IDP∥IDD∥N3∥H11∥efg) and CS computes SKCD = h(IDP∥IDD∥sni∥H10∥efg).
-
During EP, P computes session key SKPH = h(IDP∥IDH∥SigP∥SigH∥psg) and HC computes SKHP = h(IDP∥IDH∥SigP∥SigH∥psg).
The proposed protocol, presents different session key in a different phase. Even if the adversary abducts the earlier session key, she/he cannot computes the session key for the new phase. Thus, the proposed scheme has the quality of known-key security. □
Proposition 5
The proposed framework could protect the data Confidentiality.
Proof
Confidentiality is the method to security on transferring of data from the attacker. The encryption and description of data are given below:
-
During HUP, HC encrypts the report as \(C_{H}= E_{K_{1}}(M_{H})\) with using key K1 = h(IDP∥OTP∥IDP) and upload to cloud server.
-
During PUP, the patient encrypts \(C_{P}= E_{K_{PC}}(M_{H}, M_{B})\) with using key KPC = h(IDP∥IDD∥N1) and upload to CS.
-
During TP, D encrypts ciphertext \(C_{D}= E_{K_{DC}}(M_{H}, M_{B}, M_{D})\) with using key KDC = h(IDP∥IDD∥N3) and upload to CS.
-
During CP, P decrypts \(C_{2}= E_{K_{PC}}(M_{H}, M_{B}, M_{D}, f_{2})\) using key KPC = h(IDP∥IDD∥N1) and upload to CS.
Thus, if an attacker tries to find data information during the transmission, she/he encrypts message which cannot be decrypted without the key and the hash value of inputs, as the definition of hash function is secure and one way. Therefore, the proposed protocol protect the confidentiality. □
Proposition 6
The proposed scheme could protect the data Non-repudiation.
Proof
The proposed protocol describes data Non- repudiation in different phases:
-
During HUP, HC signs a message SigH= \(S_{PR_{H}} (MD_{H})\).
-
During PUP, P verified HC’s signature by computing \(MD^{*}_{H}= V_{PU_{H}}(Sig_{H})\) and Verifies if \(MD^{*}_{H}\overset {?}{=}MD_{H}\) hold or not. After that, P computes signature \(Sig_{P}= S_{PR_{P}}(MD_{P})\).
-
During TP, D verified P’s signature by computing \(MD^{*}_{P}= V_{PU_{P}}(Sig_{P})\), checks whether \(MD^{*}_{P}=? M_{P}\) hold or not and makes signature \(Sig_{D}= S_{PR_{D}}(MD_{D})\).
-
During CP, P verified D’s signature by computing \(MD^{*}_{D}= V_{PU_{D}}(Sig_{D})\), checks whether \(MD^{*}_{D}=?h(MD_{D})\) hold or not.
Thus, the patient verifies the health records. If the medical data have similar complications, the responsible person cannot be refused. The non-repudiation facts are stored in the cloud. Therefore, our proposed protocol protested data non-repudiation (Table 2). □
Proposition 7
The proposed protocol could provide Message authentication.
Proof
Message authentication is a method used to authenticate the integrity of the information. We describe message authentication in different phases below as:
-
In HUP, HC receives message M2 = {H2,A,b,TC2} and verifies the validity by checking time-stamps condition TH2 − TP2 ≤△T and hash function \(H^{*}_{}=? H_{2}\). Similarly, CS receives message M3 = {C1,TH3} and verifies the validity by checking timestamps condition TC3 − TH3 ≤△T, and hash function H5 =?H4. If any attacker endeavors alter any change of the message CS will recognize it.
-
In PUP, P receives message M5 = {L1,N,TC5}, verifies the validity by checking time-stamps condition TP2 − TC5 ≤△T, hash condition H7 =?H6 and \(M^{*}_{H}=? M_{H}, MD^{*}_{H}=? MD_{H}\). Similarly, CS receives message M6 = {L2,TP3} and verifies the validity by checking time-stamps condition TC6 − TP3 ≤△T and hash condition H9 =?H8. If any of the validation fails message will not be established.
-
In TP, D receives message M8 = {L3,N2,TC8} and verifies the validity by checking the time-stamp condition TD2 − TC8 ≤△T and hash function H11 =?H10 and \(MD^{*}_{P}=? MD_{P}\). Further, CS receives message M9 = {L4,TD3} and verifies the validity by checking the time-stamp condition TC9 − TD3 ≤△T and hash function H13 =?H12. Message authentication verified between the D and the CS.
-
In CP, P receives message M11 = {L5,TC11} and verifies the validity by checking the time-stamp condition TP4 − TC11 ≤△T hash function \(H^{*}_{14}=? H_{14}\) and \(MD^{*}_{D}=?h(M_{D})\). Again CS receives message M12 = {L6,TP6} and verifies the validity by checking time-stamps condition TC12 − TP6 ≤△T and hash condition \(H^{*}_{15} =? H_{15}\). If any of the verification fails message will not be accepted.
-
In EP, HC receives message ME2 = {L7,TEC2} and verifies the validity by checking time-stamps condition TEH1 − TEC2 ≤△T and hash condition \(H^{*}_{17}=? H_{17}\). CS receives message ME1 = {L8,TEP1} and verifies the validity by checking time-stamps condition TEC1 − TEP1 ≤△T and hash condition \(H^{*}_{16}=? H_{16}\), and CS also receives message ME3 = {L9,TEH2} and verifies the validity by checking time-stamps condition TEC3 − TEH2 ≤△T and hash condition \(H^{*}_{18}=? H_{18}\). Further, P receives message ME4 = {L10,TEC4} and verifies the validity by checking time-stamps condition TEP2 − TEC4 ≤△T, hash function \(H^{*}_{19}=? H_{19}\). If any of the verification fails message will not be accepted.
Therefore, this protocol protects the message authentication in every phase. □
Proposition 8
The proposed protocol could protect the impersonation attack.
Proof
We discussed the details of impersonation attacks in HUP as below:
-
Any E tries to masquerade as a valid CS, and eavesdrop the transferred information message M2 = {H2,A,b,TC2} and tries to computes H2, where H1 = h(IDH∥r∥x),A = IDH ⊕ x,H2 = h(H1∥A∥r). E cannot compute H1, which the hash attribute of parameters IDH,r,x where IDH is the unique identity of the HC, r is a random number which generated by the HC and x is the secret value of CS. Note that, guessing of all three value at the same time is impossible. Further, E cannot compute H2 which the hash value of H1,A,r. Thus the adversary cannot impersonate as valid CS.
-
E tries to impersonate as a valid a HC. If E breaks the time-stamp condition TH2 − TC2 ≤△T, guesses the identity of HC as IDE = IDH and random number r. Then, computes yE = A ⊕ IDE,HE3 = h(IDE∥r∥yE) and HE2 = h(H3∥A∥r). Verifies the condition \(H^{*}_{E2}=? H_{2}\) which not hold, as \(H^{*}_{2}\) is the hash value of parameters H3,A, and r. By the definition of hash function, \(H^{*}_{2}\) is the secure value. Thus, E cannot impersonate as the valid HC.
Similarly, impersonation attacks not possible in PUP, TP, CP and EP phases. Hence, the protocol is secured against the impersonation attack. □
Proposition 9
The proposed scheme could protect the session key security.
Proof
The proposed protocol having four session keys those are compute between 1) HC and CS, 2) P and CS, 3) D and CS, and 4) P and HC. Here, we have discuss the session key security of HUP. However, the approach is the similar other remaining phases.
-
In HUP, the session key between the HC and CS is SKHC = SKHC, where SKHC = h(IDH∥H3∥A∥brg) and SKCH = h(IDH∥H1∥A∥brg). E cannot computes the session key SKHC or SKHC, where \(H_{1}= h(ID_{H}\|r\| x), H_{3}= h(ID_{H}\| r\|y), A= ID_{H}\oplus x, H^{*}_{2}= h(ID_{H}\|A\|r)\). With the help of Proposition 8, H1 and \(H^{*}_{2}\) cannot be computed by E. Further, For \(b, r \in Z^{\star }_{q}\) and g is the generator of G, given (g,bg,rg), then compute brg is hard to the group G by ECCDHP in the elliptic curve cryptography. Thus, the session key can only be generated by the authenticated party.
Similarly, session key generated in PUP, TP and EP. Hence the proposed scheme could protect the session key □
Proposition 10
The proposed framework could protect the stolen mobile device attack.
Proof
Suppose that E stolen the mobile phone of the authorized P, E cannot find any secret communication of the P. As the mobile phone accepts the message, which is reachable only by inputs valid identity of P and OTP of mobile phone. In PUP, P computes key K2 = h(IDP∥OTP∥IDH). Where OTP is the unique one time password of P’s mobile device and h(.) is the one way hash function which is secure by define it. Therefore, E cannot break the system even if she/he gets the mobile device of the valid patient.
Similarly, in HUP adversary does not break the system even if she/he grabs the mobile phone of the registered P. Thus, the proposed framework assures the stolen mobile device attack. □
Proposition 11
The proposed protocol could protect the off-line password/ identity guessing attack.
Proof
We discussed this attack in PUP. If possible, any E interprets in PUP and guesses the identity IDE of valid P, then compute NE = N ⊕ h(SID∥IDE) and key KE1 = h(IDE∥OTP∥IDH), Where OTP is the unique OTP of P. Thus, NE≠N1 and KE≠K2 because SID is unique for each patient, N1 = N ⊕ h(SID∥IDP) and IDH is identity of HC which is also unique. On the other hand, if possible he/she guesses one time password OTPE of legal patient, then computes KE2 = h(IDE∥OTPE∥IDH). As a result, KE2≠K2. Hence, off-line password/identity guessing attack cannot work in PUP of the proposed protocol.
Similarly, off-line password/identity guessing attack not possible in HUP, TP, CP and EP. Thus, off-line password/ identity guessing attack not possible in the proposed framework. □
Proposition 12
The proposed framework could resist many logged-in patient attack.
Proof
We discussed this attack in PUP. Suppose that many adversaries E1,E2,E3,....Ej....Em having same identity IDP and sends messages \(\{ID_{P}, SID, T_{E_{1}}\}, \{ID_{P}, SID, T_{E_{2}}\},\! \{ID_{P},\! SID,\! T_{E_{3}}\},......\{ID_{P}\!,\! SID\!,\! T_{E_{j}}\},\!.....\{ID_{P}\!,\!SID,T_{E_{m}}\}\) to CS, where \(T_{E_{j}}\) is current message sending time of jth adversary. Here, we discuss about only adversary Ej. On receiving message from adversary Ej, then CS verifies \(T_{C4}- T_{E_{j}} \leq \triangle T\), If possibly hold, the CS computes N = sni ⊕ h(SID∥IDP), generates random number \(c \in Z^{\star }_{q}\), computes H6 = h(SID∥sni∥CH∥SigH∥TC5), encrypts \(L_{1}=E_{sn_{i}}(Sig_{H}, C_{H},H_{6}, ID_{H}, c, T_{C5})\) and sends message M5 = {L1,N,TC5} to Ej via public channel. On receiving message Ej verifies \(T_{E_{j}} - T_{C5} \leq \triangle T\) and computes \({N^{E}_{1}}= N\oplus h(SID\|ID_{P})\), decrypts \((Sig_{H}, C_{H},H_{6}, ID_{H}, c, T_{C5}) = D_{N^E_{1}}(L_{1})\), computes \({H^{E}_{7}}= h(SID\|N^E_{j}\|C_{H}\|Sig_{H}\|T_{C5})\). Here, \(H^{E_{j}}_{7}\neq H_{6}\) as sni,SID,TC5 are different and unique for each patients. Thus many logged-in patient’s attack is not work in PUP.
Similarly, many logged-in patient attack does not work in in CP and EP. Therefore, our protocol protected against many logged-in patient’s attack. □
Performance analysis
In this section, we estimate performance of the proposed framework with the relevant schemes worked in cloud environment for secure medical data communication, such as Chen et al. [15], Chiou et al. [17], Chen-Yang et al. [16] and Mohit et al. [39] protocols. The comparison performed in all the phases of framework like HUP, PUP, TP, CP and EP bellow as:
We have adopted different cryptographic operations in this paper based on the information applicable in Chiou et al. [17] to test the computation cost of the proposed protocol still existing relevant research. Chiou et al. [17], Windows 7 OS and Android phone used and the system structure of mobile phone is Android 4.4.4KTU84P along with a 2GB RAM and 1.8 GHz processor. The configurations of computer system is Windows 7, Professional with an Intel (R) core (TM) 2 Quad CPU Q8300, 2GB RAM and @2.50Hz. The execution time in second for the different time complexity symbols are as follows:
-
TSign :The time for calculating execute/verify a signature (TSign ≈ 0.3317sec).
-
TA : the time for calculating asymmetric encryption/ decryption operation (TA ≈ 0.3057sec).
-
TM : the time for calculating multiplication operation (TM ≈ 0.0503sec).
-
TP : the time for calculating a bilinear pairing operation (TP ≈ 0.0621sec).
-
TS : the time for calculating symmetric encryption/ decryption operation (TS ≈ 0.0087sec).
-
TH : the time for calculating one-way hash function (TH ≈ 0.0005sec).
Table 3 recaps the computation cost of the proposed scheme with relevant schemes. It is famous that the computational cost of XOR (⊕) and concatenation (∥) operations treated as imperceptible analyzed to other operations like as symmetric encryption/decryption, multiplication, pairing free, bilinear pairing, etc. There are following observation about computation cost and security information:
-
In Fig. 11 shows that the computation cost of the HUP of the protocol is ≈ 0.3538sec which is greater than Mohit et al.’s scheme[39]. The proposed scheme is secured but Mohit et al. and other schemes have security weaknesses.
Table 3 Computation cost of our protocol with related protocols -
In Fig. 12 shows that the computation cost of the PUP of the protocol is ≈ 0.7031sec which is greater than Mohit et al.’s scheme[39], Chiou et al.’s [17] and less than Chen et al.’s [15] and Yang et al.’s [16]. The proposed protocol is secured but other relative schemes have security weaknesses.
-
In Fig. 13 shows that the computation cost of the TP of the protocol is ≈ 0.7026sec which is greater than Mohit et al.’s scheme[39]. The proposed framework is secured but Mohit et al. and other schemes have security weaknesses.
-
In Fig. 14 shows that the computation cost of the CP of the protocol is ≈ 0.3689sec which is greater than Mohit et al.’s scheme[39] and less than Chiou et al.’s [17]. Therefore, the proposed protocol is secured but Mohit et al.’s and Chiou et al.’s scheme are not secure.
-
In Fig. 15 shows that the computation cost of the EP of the protocol is ≈ 0.0506sec which is more less than Yang et al.’s scheme[16]. But in this phase, presented protocol is secured and efficient but Yang et al.’s scheme is not secure and efficient.
Liu et al.’s [57] is lightweight pseudonym authentication scheme for multi-server architecture in TMIS. This work efficient for authentication and key agreement process in TMIS. In the proposed protocol, we used single cloud server and patient, doctor and healthcare center. So, Liu et al.’s scheme is not applicable in this domain. It is clear from Fig. 16 that the the proposed protocol has less computation cost than the earlier protocols worked in a cloud environment for medical communication of data exchange. The computation cost of the proposed protocol is greater than Mohil et al.’s protocol, but Mohit et al.’s scheme has no emergency phase and have some security weaknesses.
Conclusion
The evolution of information technology offers conveniences to humanize medical services, maintaining patients with effectual treatment with enlarged convenience and security. In this paper, we have reviewed Mohit et al.’s mutual authentication scheme described for a TMIS using cloud computing environment. On cryptanalysis, we found that the protocol is susceptible to stolen-verifier attack, many logged-in patient attack, patient anonymity, impersonation attack and fails to protect session key. Then, we proposed an improved, secure and efficient mutual authentication scheme in the same environment. Further, we proved that the proposed protocol provides better security than other previous protocols by the security analysis. The proposed protocol is also profitable in terms of performance like as computation overheads.
References
Abdalla, M., Izabachene, M., and Pointcheval, D.: Anonymous and transparent gateway-based password-authenticated key exchange. In: International conference on cryptology and network security, pp. 133–148. Springer, Berlin, 2008.
Abor, P.A., and Agrizzi, D.: Healthcare governance and patients’ perception of service quality. In: Annual conference on innovations in business & Management, London, pp. 21–23, 2012
Amin, R., Cryptanalysis and efficient dynamic ID based remote user authentication scheme in multi-server environment using smart card. IJ Netw. Secur. 18(1):172–181, 2016.
Amin, R., and Biswas, G. P., Cryptanalysis and design of a three-party authenticated key exchange protocol using smart card. Arab. J. Sci. Eng. 40(11):3135–3149, 2015.
Amin, R., and Biswas, G. P., A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. J. Med. Syst. 39(8):1–19, 2015.
Amin, R., Hafizul Islam, S.K., Biswas, G. P., Khan, M.K., and Kumar, N., A robust and anonymous patient monitoring system using wireless medical sensor networks. Futur. Gener. Comput. Syst. 80:483–495, 2018.
Amin, R., Sk, H.I., Biswas, G. P., Khan, M.K., and Li, X., Cryptanalysis and enhancement of anonymity preserving remote user mutual authentication and session key agreement scheme for e-health care systems. J. Med. Syst. 39(11):1–21, 2015.
Bajpai, D., Vardhan, M., Gupta, S., Kumar, R., and Kushwaha, D.S.: Security service level agreements based authentication and authorization model for accessing cloud services. In: Advances in computing and information technology, pp. 719–728. Springer, Berlin, 2012.
Balduzzi, M., Zaddach, J., Balzarotti, D., Kirda, E., and Loureiro, S.: A security analysis of amazon’s elastic compute cloud service. In: Proceedings of the 27th annual ACM symposium on applied computing, pp. 1427–1434 ACM, 2012
Bresson, E., Chevassut, O., and Pointcheval, D.: Security proofs for an efficient password-based key exchange. In: Proceedings of the 10th ACM conference on Computer and communications security, pp. 241–250 ACM, 2003
Cao, B.-Q., Li, B., and Xia, Q.-M.: A service-oriented qos-assured and multi-agent cloud computing architecture. In: IEEE international conference on cloud computing, pp. 644–649. Springer, Berlin, 2009.
Casalicchio, E., and Silvestri, L., Mechanisms for SLA provisioning in cloud-based service providers. Comput. Netw. 57(3):795–810, 2013.
Chaudhry, S.A., Khan, M.T., Khan, M.K., and Shon, T., A multiserver biometric authentication scheme for tmis using elliptic curve cryptography. J. Med. Syst. 40(11):230, 2016.
Chaudhry, S.A., Naqvi, H., Shon, T., Sher, M., and Farash, M.S., Cryptanalysis and improvement of an improved two factor authentication protocol for telecare medical information systems. J. Med. Syst. 39(6):65–75, 2015.
Chen, C.-L., Yang, T.-T., Chiang, M.-L., and Shih, T.-F., A privacy authentication scheme based on cloud for medical environment. J. Med. Syst. 38(11):1–16, 2014.
Chen, C.-L., Yang, T.-T., and Shih, T.-F., A secure medical data exchange protocol based on cloud environment. J. Med. Syst. 38(9):1–12, 2014.
Chiou, S.-Y., Ying, Z., and Liu, J., Improvement of a privacy authentication scheme based on cloud for medical environment. J. Med. Syst. 40(4):1–15, 2016.
Debiao, H.E., Jianhua, C., and Rui, Z., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012.
Gope, P., and Amin, R., A novel reference security model with the situation based access policy for accessing ephr data. J. Med. Syst. 40(11):41–53, 2016.
Hankerson, D., Menezes, A.J., and Vanstone, S.: Guide to elliptic curve cryptography. Springer Science & Business Media, 2006
He, D., Kumar, N., Chen, J., Lee, C.-C., Chilamkurti, N., and Yeo, S.-S., Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst. 21(1): 49–60, 2015.
He, D., Kumar, N., Shen, H., and Lee, J.-H., One-to-many authentication for access control in mobile pay-TV systems. Sci. China Inf. Sci. 59(5):1–14, 2016.
He, D., Kumar, N., Wang, H., Wang, L., Choo, K.-K.R., and Vinel, A.: A provably-secure cross-domain handshake scheme with symptoms-matching for mobile healthcare social network. IEEE Transactions on Dependable and Secure Computing , 2016
He, D., and Wang, D., Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst. J. 9(3):816–823, 2015.
He, D., Zeadally, S., Kumar, N., and Lee, J.-H., Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 11(4):2590–2601, 2017.
Hwang, J.-J., Chuang, H.-K., Hsu, Yi-C., and Wu, C.-H.: A business model for cloud computing based on a separate encryption and decryption service. In: International conference on information science and applications (ICISA), pp. 1–7. IEEE, 2011
Islam, S. K., Obaidat, M.S., and Amin, R., An anonymous and provably secure authentication scheme for mobile user. Int. J. Commun. Syst. 29(9):1529–1544, 2016.
Islam, S.K.H., Amin, R., Biswas, G. P., Farash, M.S., Li, X., and Kumari, S., An improved three party authenticated key exchange protocol using hash function and elliptic curve cryptography for mobile-commerce environments. J. King Saud Univ. Comput. Inf. Sci. 29(3):311–324, 2017.
Jiang, Q., Ma, J., and Ma, Z., A privacy enhanced authentication scheme for telecare medical information systems. J. Med. Syst. 37(1):1–8, 2013.
Karati, A., Amin, R., and Biswas, G. P., Provably secure threshold-based abe scheme without bilinear map. Arab. J. Sci. Eng. 41(8):3201–3213, 2016.
Kumari, S., Khan, M.K., and Kumar, R., Cryptanalysis and improvement of ’a privacy enhanced scheme for telecare medical information systems’. J. Med. Syst. 37(4):1–11, 2013.
Lee, C.-C., Hsu, C.-W., Lai, Y.-M., and Vasilakos, A., An enhanced mobile-healthcare emergency system based on extended chaotic maps. J. Med. Syst.. 37(5):1–12, 2013.
Li, C.-T., Lee, C.-C., and Weng, C.-Y., A secure chaotic maps and smart cards based password authentication and key agreement scheme with user anonymity for telecare medicine information systems. J. Med. Syst. 38(9):1–11, 2014.
Li, X., Niu, J., Karuppiah, M., Kumari, S., and Fan, W.U., Secure and efficient two-factor user authentication scheme with user anonymity for network based e-health care applications. J. Med. Syst. 40(12):267–277, 2016.
Li, X., Niu, J., Khan, M.K., and Liao, J., An enhanced smart card based remote user password authentication scheme. J. Netw. Comput. Appl. 36(5):1365–1371, 2013.
Maitra, T., Obaidat, M.S., Amin, R., Islam, S.K., Chaudhry, S.A., and Giri, D.: A robust ElGamal based password authentication protocol using smart card for client server communication. International Journal of Communication Systems 30(11), 2017
Mishra, D., Mukhopadhyay, S., Chaturvedi, A., Kumari, S., and Khan, M.K., Cryptanalysis and improvement of Yan others.’s biometric-based authentication scheme for telecare medicine information systems. J. Med. Syst. 38(6):1–12, 2014.
Mishra, D., Srinivas, J., and Mukhopadhyay, S., A secure and efficient chaotic map-based authenticated key agreement scheme for telecare medicine information systems. J. Med. Syst. 38(10):1–10, 2014.
Mohit, P., Amin, R., Karati, A., Biswas, G.P., and Khan, M.K., A standard mutual authentication protocol for cloud computing based health care system. J. Med. Syst. 41(4):1–13, 2017.
Ramez, W.S., Patients’ perception of health care quality, satisfaction and behavioral intention: an empirical study in Bahrain. Int. J. Bus. Soc. Sci. 3(18):131–141, 2012.
Sureshkumar, V., Anitha, R., Rajamanickam, N., and Amin, R., A lightweight two-gateway based payment protocol ensuring accountability and unlinkable anonymity with dynamic identity. Comput. Electr. Eng. 57:223–240, 2017.
Sutrala, A.K., Das, A.K., Odelu, V., Wazid, M., and Kumari, S., Secure anonymity-preserving password-based user authentication and session key agreement scheme for telecare medicine information systems. Comput. Methods Prog. Biomed. 135:167–185, 2016.
Tan, Z., An efficient biometrics-based authentication scheme for telecare medicine information systems. Network 2(3):200–204, 2013.
Tsai, Y. L., Cloud computing security. Commun. CCISA 18(2):62–68, 2012.
Wazid, M., Das, A.K., Kumari, S., Li, X., and Fan, W.U., Design of an efficient and provably secure anonymity preserving three-factor user authentication and key agreement scheme for TMIS. Secur. Commun. Netw. 9(13):1983–2001, 2016.
Wei, J., Xuexian, H.U., and Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3597–3604, 2012.
Wu, Z.-Y., Chung, Y., Lai, F., and Chen, T.-S., A password-based user authentication scheme for the integrated EPR information system. J. Med. Syst. 36(2):631–638, 2012.
Wu, Z.-Y., Lee, Y.-C., Lai, F., Lee, H.-C., and Chung, Y., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012.
Wu, Z.-Y., Tseng, Y.-J., Chung, Y., Chen, Y.-C., and Lai, F., A reliable user authentication and key agreement scheme for web-based hospital-acquired infection surveillance information system. J. Med. Syst. 36 (4):2547–2555, 2012.
Yan, X., Li, W., Li, P., Wang, J., Hao, X., and Gong, P., “A secure biometrics-based authentication scheme for telecare medicine information systems. J. Med. Syst. 37(5):1–6, 2013.
Yang, H., Kim, H., and Mtonga, K., An efficient privacy-preserving authentication scheme with adaptive key evolution in remote health monitoring system. Peer-to-Peer Netw. Appl. 8(6):1059–1069, 2015.
Srinivas, J., Das, A.K., Kumar, N., and Rodrigues, J.: Cloud centric authentication for wearable healthcare monitoring system. IEEE Transactions on Dependable and Secure Computing, 2018
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6): 3833–3838, 2012.
Srinivas, J., Mishra, D., and Mukhopadhyay, S., A Mutual Authentication Framework for Wireless Medical Sensor Networks. J. Med. Syst. 41(5):80, 2017.
Mishra, D., Kumar, V., and Mukhopadhyay, S.: A pairing-free identity based authentication framework for cloud computing. In: International conference on network and system security, pp. 721–727. Springer, Berlin, 2013.
Liu, Y., Guo, W., Fan, C.-I., Chang, L., and Cheng, C.: A practical privacy-preserving data aggregation (3PDA) scheme for smart grid. IEEE Transactions on Industrial Informatics, 2018
Liu, Y., Liu, G., Cheng, C., Xia, Z., and Shen, J., A Privacy-Preserving Health Data Aggregation Scheme. TIIS 10(8):3852–3864, 2016.
Liu, X., Li, Y., Juan, Q.U., and Ding, Y., A lightweight pseudonym authentication and key agreement protocol for multi-medical server architecture in TMIS. KSII Trans. Internet & Inf. Syst. 11(2):924–943, 2017.
Xu, L., and Fan, W.U., An improved and provable remote user authentication scheme based on elliptic curve cryptosystem with user anonymity. Secur. Commun. Netw. 8(2):245–260, 2015.
Menezes, A J, Van Oorschot, P C, and Vanstone, S. A.: Handbook of applied cryptography. CRC Press, 1996
Wu, F., Lili, X.U, Kumari, S., and Li, X., A new and secure authentication scheme for wireless sensor networks with formal proof. Peer-to-Peer Netw. Appl. 10(1):16–30, 2017.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Kumar, V., Jangirala, S. & Ahmad, M. An Efficient Mutual Authentication Framework for Healthcare System in Cloud Computing. J Med Syst 42, 142 (2018). https://doi.org/10.1007/s10916-018-0987-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-018-0987-5