Abstract
Non-orthogonal multiple access (NOMA) technique can potentially increase spectral efficiency and improve the network capacity of wireless networks. Ergodic secrecy capacity (ESC) is an important parameter for evaluating the security of wireless systems. In this paper, we investigate the secrecy performance of a cooperative NOMA system with an untrusted user using a half-duplex amplify-and-forward relay in terms of ESC over Rayleigh fading environments. A satellite source uses the NOMA technique to communicate with the near and far users, which is assisted by a relay for downlink communication, and an untrusted user, i.e., an eavesdropper, also interacts with this relay. We derive the lower bound ESC of the proposed system and analyze its performance in terms of power allocation coefficient, variance between relay and user, variance between relay of the eavesdropper, and average signal-to-noise ratio of the eavesdropper link. Simulation results demonstrate that the cooperative NOMA system outperforms the cooperative orthogonal multiple access system in terms of ESC. Finally, Monte Carlo simulations are used to validate the analytical results.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Non-orthogonal multiple access (NOMA) is urgently required to be used in order to remove the orthogonality requirement in frequency, time, and code resources by overlapping signals partially with an acceptable degree of interference [1]. This is due to the constantly growing demands for massive connectivity, low latency, and high spectral efficiency. From the perspective of enhancing the multiplexing advantage by leveraging various domains, NOMA has recently been subdivided into power-domain NOMA and code-domain NOMA. The fundamental idea behind power-domain NOMA is to allow signals from several users to share the same resource block (frequency, time, or code) while occupying it at various power levels. NOMA, in particular, employs superposition coding (SC) at the transmitting end to transmit the superimposed massage in the exact same resource, as well as successive interference cancellation (SIC) at the receiving end to separate the superimposed massage of the user with poor channel conditions before decoding its own massage with relatively better channel conditions [2]. NOMA can enable enormous connections, achieve improved spectral efficiency [3, 4], and enhance user fairness [5,6,7,8]. The ergodic secrecy rate in cooperative NOMA systems is a measure of the average secure communication rate attained by users in the network over an extended period of time. In such systems, several users share the same frequency and time resources. The transmission of cooperative NOMA focuses on collaboration between users to strengthen the security and dependability of the connection [9,10,11,12]. Cooperative NOMA may be categorized into two types, specifically based on the network components: relay-aided and user-aided cooperative NOMA. In user-aided cooperative NOMA, users who benefit from better channel conditions serve as a relay to improve the performance of weaker user. In [13, 14], the performance of cooperative NOMA in terms of outage probability and throughput is analyzed and showed the outage performance of user-aided cooperative NOMA is superior to the non-cooperative NOMA cell-centre users can act as relays in both full-duplex (FD) and half-duplex (HD) modes to produce diversity gain, which improves cell-edge user performance in a cellular NOMA network [15,16,17,18]. The NOMA approach has received a lot of attention in an effort to boost spectral efficiency [19,20,21]. The traditional orthogonal multiple access (OMA) approaches assign orthogonal resources only to one user. As a result, OMA does not provide the requisite spectral efficiency to meet 5G specifications. Because NOMA serves numerous customers with the same resource block, it effectively utilizes the spectrum and offers greater connection than traditional OMA systems. The NOMA shares a single frequency channel with several users rather than dividing the available bandwidth across users like the OMA does [3, 22]. As a consequence, the throughput of system increases since each user may transmit data using the whole spectrum [23]. There are two basic approaches used in NOMA: superposition coding and SIC. The key factor of NOMA is its ability to simultaneously send information to many users from the same signal by using superposition coding. At the transmitter, a power allocation coefficient is assigned to each user on the basis of channel quality, and after that, the transmitter superimposes the information signals [24,25,26]. At the receiver, each message is arranged in accordance with the channel strength, and the weaker message is first decoded and subtracted from the incoming superimposed message. In order to extract the desired message, the user must repeat this step repeatedly until it gets its own message by performing SIC [27].
1.1 Related Work
In [28], strictly positive secrecy capacity (SPSC) and secrecy outage probability (SOP) of cooperative NOMA system with two users and multiple DF relays in the presence of an eavesdropper are analyzed over Rayleigh fading channel and results show that SPSC can be maximized or SOP can be minimized by optimizing the power allocation of NOMA users. In [29], SOP of cooperative NOMA system with two NOMA users and multiple DF relays in presence of multiple eavesdroppers is analyzed over Nakagami-m fading. In [30], the SOP of a cooperative NOMA system with two users and one untrusted user is analyzed over Rician fading, in which the near user acts as a relay and performs the SIC. In [31], the SOP of a cooperative NOMA system with two users, multiple DF relays and multiple base stations is studied in the presence of an untrusted user using relay selection technique over Nakagami-m fading. In [32], the SPSC and SOP of a cooperative NOMA system with two users, one DF relay, one eavesdropper, and all the end users have direct link, are studied over Rayleigh fading. Ergodic secrecy analysis is impotent factor for designing and optimizing the wireless network. It assists in evaluating resource allocation schemes to maximize collective secrecy rate by taking the dynamic nature of wireless channels and possible eavesdroppers into consideration. In [33], ergodic secrecy sum rate (ESSR) of cooperative NOMA system with two users, one passive eavesdropper, and one DF is analyzed over Rayleigh fading for downlink communication. Simulation results show that ESSR degrades as the eavesdropper comes closer to either of the users. In [34], the ESSR of a cooperative NOMA system with two users and one untrusted amplify-and-forward (AF) relay is analyzed over Rayleigh fading channels for both uplink and downlink communication. In [35], the ergodic secrecy rate (ESR) of a cooperative NOMA system with one user, one DF relay and one eavesdropper is analyzed over Rayleigh fading channel for downlink communication. In [36], the ESR of cooperative NOMA system with three users and one of the three user acting as DF relay is analyzed over the Rayleigh fading channel for downlink communication.
1.2 Motivation
The following observations have been made on the basis of the above literature survey:
-
The cooperative NOMA increases spectral efficiency by allowing several users to utilize the same time and frequency resources concurrently. As a result, it addresses to the growing demand for data and multimedia services while using the limited spectrum resources more effectively.
-
Cooperative NOMA also increases system capacity, which is necessary to handle the expanding number of connected devices and applications in modern wireless networks. This is accomplished by allowing several users to access the network at once.
-
The main aim of ergodic secrecy analysis is to improve the security and privacy of wireless communications by creating methods that can shield confidential information from eavesdropping, which is crucial in today's digital age. Also, it measures the fastest rate at which information may be sent securely while being intercepted.
It can also be observed from the above literature survey that the secrecy performance analysis of a cooperative NOMA network in terms of ESC has not been addressed with two NOMA users and an AF relay in the presence of an eavesdropper. Motivated by the above observations, in this paper, we propose and analyze the secrecy performance of a downlink cooperative NOMA system with an untrusted user.
1.3 Contribution
To the best of our knowledge, no analysis of ESC for proposed NOMA-based systems with untrusted user has been performed yet. The main contributions of this paper are given below:
-
We propose a cooperative NOMA system for downlink communication that consists of an untrusted user, a DF relay, and two mobile users with different channel conditions.
-
We derive the closed-form expressions of lower bound ESC for the proposed cooperative system model and analyze the performance in terms of power allocation coefficient, variance between relay and eavesdropper, variance between relay and mobile user, and the average signal-to-noise ratio (SNR) of the eavesdropper link. The proposed method, in particular, defines a positive lower limit of ESC, showing that complete secrecy may be assured.
-
To validate the theoretical analysis, Monte Carlo simulations are used, and the advantage of the proposed cooperative NOMA technique with an untrusted user over the OMA scheme is also shown.
The remaining sections of the paper are structured as follows: Sect. 2 presents the system model and the secure transmission scheme assisted by AF. The ESC of proposed system model is analyzed in Sect. 3. Section 4 evaluates the numerical results. Lastly, Sect. 5 concludes the paper.
2 System Model
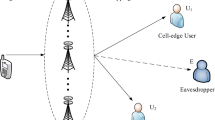
We consider a cooperative NOMA based wireless network that consists of a satellite (X) as the source, an amplify and forward relay (AFR) that works in half-duplex mode, two mobile users (MU2 as a strong mobile user and MU1 as a weak mobile user), and an eavesdropper (E), as shown in Fig. 1. It is assumed that there are no direct links between X and both users and also between X and E. The E, X, and both users consist of a single antenna, whereas the relay consists of both transmitting and receiving antennas. The only link between the AFR and the E is considered as an illegal link which is an unauthorized pathway that may be utilized for a variety of illegal activities and threaten legitimate communication systems. We also assume that all the channels suffer from independent Rayleigh fading distribution. The channel coefficients for X-to-AFR, AFR-to-MU1, AFR-to-MU2 and AFR-to-E link are denoted as \(h_{X,AFR}\), \(h_{{AFR,MU_{1} }}\), and \(h_{{AFR,MU_{2} }}\) and \(h_{AFR,E}\) respectively.
The X transmits the superposition of two different information, \(x_{{s_{1} }}\) and \(x_{{s_{2} }}\), to the AFR in the first time slot (FTSL) which is defined as follows:
where \(x_{{s_{i} }}\) denotes the data symbol of ith mobile user with normalized power \(E\left[ {\left| {x_{{s_{i} }} } \right|^{2} } \right] = 1\), \(W_{st}\) is the total transmit power of X, and \(a_{{s_{i} }}\) is the power allocation coefficient of ith mobile user. To fulfill the quality of service requirement of weak user, we consider the power allocation coefficient of weak user is greater than power allocation coefficient of strong user \((a_{{s_{1} }} > a_{{s_{2} }} )\) that satisfy the condition \(a_{{s_{1} }}^{2} + a_{{s_{2} }}^{2} = 1\).
The received signals at the AFR in the FTSL from X (\(y_{X}^{AFR} )\) can be expressed as
where \(n_{X}^{AFR}\) represents the additive white Gaussian noise (AWGN) with \(N_{MU}\) variance and zero mean.
Using (2), the received SINR at AFR to get the information \(x_{{s_{1} }}\) (\(\gamma_{X,AFR}^{{s_{1} }} )\) can be defined as
where \(\rho_{s} = \frac{{W_{st} }}{{N_{MU} }}\)
Similarly, the received SINR at AFR to get the information \(x_{{s_{2} }}\) (\(\gamma_{X,AFR}^{{s_{2} }} )\) can be defined as
In the second time slot (STSL), AFR amplifies the received signal and forward it to the mobile users. Now, the received message signal at mobile users can be expressed as
where \(MU_{i}\) represents the ith mobile user, \(h_{{AFR,MU_{i} }}\) is the channel gain between the AFR and ith mobile user,\(n_{{MU_{i} }}^{AFR}\) represents the AWGN with \(N_{MU}\) variance and zero mean between the AFR and ith mobile user and, \(\beta\) shows the gain of AFR and it can be defined as
Substituting \(y_{X}^{AFR}\) from (2) in to (5), we obtain
So, the signals received (\(y_{{MU_{1} }}^{AFR} and y_{{\begin{array}{*{20}c} {MU_{2} } \\ \\ \end{array} }}^{AFR} )\) at both mobile users can be represented as
In the STSL, E also gets the same message signal as both mobile user (MU) gets. The signal received at the E can be defined as
where \(n_{E}^{AFR}\) show the AWGN with \(N_{E}\) variance and zero mean. Now (10) can be modified using (2) as
Furthermore, SINR of weak mobile user (\(\gamma_{{AFR,MU_{1} }}^{ } )\) using (8) can be defined as
Further (12) can be modified as
The strong mobile first decodes the information of the weak user and then subtracts this information to get its own information by performing perfect SIC. So, the SINR of a strong mobile user (\(\gamma_{{AFR,MU_{2} }}^{ }\)) using (9) and similar to [37] can be defined as
Similarly, the SINR at eavesdropper using (11) can be defined as
where \(\rho_{E}\) shows average SINR of eavesdropper link and it is defined as \(\rho_{E} = \frac{{W_{st} }}{{N_{E} }}\). \(\gamma_{{AFR,E_{i} }}^{ }\) shows the SINR of ith mobile user at the eavesdropper.
Now considering the case of high SINR similar to [37], (13), (14) and (15) can be modified as
3 Secrecy Analysis
In this section, we derive the analytical expression of ergodic secrecy capacity (ESC) for proposed cooperative NOMA system with an untrusted user. The maximum achievable data rate for sending secret data over a wireless communication channel while ensuring its secrecy from eavesdroppers is known as ESC. ESC is calculated as the average rate of secure communication accomplished over time, taking into consideration the worst-case scenario with regard to the eavesdropper's channel circumstances. It's simply the average rate at which confidential data may be transferred securely.
The achievable rate of strong mobile user using AFR [38] can be defined by
Now considering the case of high SINR and using (4) and (17), (19) can be modified as
Similarly, the achievable rate of weak mobile user can be defined by
Further, considering the case of high SINR and using (3) and (16), (21) can be modified as
Similarly, the achievable rate of \(x_{{s_{1} }}\) and \(x_{{s_{2} }}\) at eavesdropper can be defined as
Since eavesdropper only wiretaps the massage from the AFR, the ESC of the cooperative NOMA system can be represented as
where \(\left\{ {\text{X}} \right\}^{ + } = \max { }\left\{ {0,{\text{X}}} \right\}^{ + }\)
Now, the lower bound of ESC of proposed system can be defined by using Jensen’s inequality [39], which is written as
Now, using (25) and (26) the lower bound of ESC can be defined as
Now, \({\mathbb{E}}[C_{{x_{{s_{1} }} }} ]{ }\) can be obtained using (23) as
Now \({\text{F}}_{{\gamma_{X,AFR}^{{s_{1} }} }} \left( {z_{1} } \right)\) can be simplified as
After substituting the value of \(\gamma_{X,AFR}^{{s_{1} }}\) from (3) and using the CDF of the Rayleigh fading distribution, Eq. (31) can be modified as
where \({\mathcal{P}} = \frac{1}{{\rho_{s} \left( {a_{{s_{1} }}^{2} - z_{1} a_{{s_{2} }}^{2} } \right)}}\)
Now substituting (32) in to (30), we obtain
Using Gauss–Chebyshev integral [40], (33) can be modified as
where \(N\) represents the Gauss–Chebyshev quadrature approximation and \(z_{n} = \cos \left[ {\frac{2n\pi - \pi }{{2N}}} \right]\)
Using (18), \({\mathbb{E}}[C_{{x_{{s_{2} }} }} ]\) of strong mobile user (MU2) can be defined as
where \(u_{2} = \rho_{s} \left| {h_{{AFR,MU_{2} }} } \right|^{2}\) and \(u_{1} = \rho_{s} \left| {h_{X,AFR} } \right|^{2}\)
As \(\mathop \int \limits_{0}^{\infty } e^{ - \delta x} \ln \left( {1 + \varphi x} \right)dx = - \frac{1}{\delta }e^{{\frac{\delta }{\varphi }}} E_{i} \left( { - \frac{\delta }{\varphi }} \right)\) [37], (38) can be modified as
After applying Gauss–chebyshev integral [40], (40) can be modified as
where \(\theta_{n} = \frac{\pi }{4}\left( {z_{n} + 1} \right)\).
Similarly the ESC of \(x_{{s_{1} }}\) at eavesdropper can be defined as,
where \(u_{3} = \rho_{E} \left| {h_{{AFR,E_{1} }} } \right|^{2}\) and \(u_{1} =\) \(\rho_{s} \left| {h_{X,AFR} } \right|^{2}\)
Now (45) can be modified using approximation provided in [41] as,
After further calculation, (47) can be modified as
Similarly, the ESC of \(x_{{s_{2} }}\) at eavesdropper can be defined as
Now after substituting the value of \({\mathbb{E}}\left[ {C_{{x_{{s_{1} }} }} } \right],{\mathbb{E}}\left[ {C_{{x_{{s_{2} }} }} } \right],{\mathbb{E}}\left[ {C_{{Ex_{{s_{1} }} }} } \right]{ }\) and \({\mathbb{E}}\left[ {C_{{Ex_{{s_{2} }} }} } \right]\) from (34), (41), (48) and (49) respectively in to (27), we obtain
4 Results and Discussion
In this section, we analyze the performance of proposed system from the derived expression of ESC. We use the Monte carlo simulation (MC) to verify the results obtained from the Analytical simulation (AS). The values of parameters taken in simulation are shown in Table 1.
Figure 2 shows the plots of ESC vs. average SNR of legal link with parameters \({\text{N}}_{{{\text{MU}}}} = 1\), \({\text{N}}_{{\text{E}}} = 1\), \({\uprho }_{{\text{E}}}\) = 1, \({\text{a}}_{{{\text{s}}_{1} }}\) = 0.4, 0.5 and 0.6. The plots show that ESC increases significantly with the average SNR of legal link at lower values of average SNR, i.e., up to 10 dB, and after that, it becomes almost constant with respect to the average SNR of legal link. Further, ESC increases with increasing the value of \({\text{a}}_{{{\text{s}}_{1} }} { }\) at fixed values of \({\text{N}}_{{{\text{MU}}}}\), \({\text{N}}_{{\text{E}}}\), and \({\uprho }_{{\text{E}}}\). This result shows that there is a boost to ESC when more power allocation factor is given to weak mobile user.
Figure 3 shows the plots of ESC versus average SNR of the legal link with parameters \({\text{N}}_{{\text{E}}} = 1\), \({\uprho }_{{\text{E}}}\) = 1, \({\text{a}}_{{{\text{s}}_{1} }}\) = 0.4, and \({\text{N}}_{{{\text{MU}}}} = 1\), 2 and 4. The plots show that as the value of \({\text{N}}_{{{\text{MU}}}}\) increases at fixed values of \({\text{a}}_{{{\text{s}}_{1} }}\), \({\text{N}}_{{\text{E}}}\) and \({\uprho }_{{\text{E}}}\), ESC increases. So, a higher value of variance between the relay and user increases the system performance in terms of ESC.
Figure 4 shows the plots of ESC vs. average SNR of legal link with parameters \({\text{N}}_{{{\text{MU}}}} = 1\), \({\uprho }_{{\text{E}}} = 1\), \({\text{a}}_{{{\text{s}}_{1} }} = 0.4\), and \({\text{N}}_{{\text{E}}} = 1\), 2 and 4. The plots show that as the value of \({\text{N}}_{{\text{E}}}\) increases at fixed values of \({\text{a}}_{{{\text{s}}_{1} }}\), \({\text{N}}_{{\text{E}}}\) and \({\uprho }_{{\text{E}}}\), ESC decreases. So, higher value of variance of eavesdropper link decreases the system performance in term of ESC.
Figure 5 shows the plots of ESC vs. average SNR of legal link with parameters \({\text{N}}_{{{\text{MU}}}} = 1\), \({\text{a}}_{{{\text{s}}_{1} }}\) = 0.4, and \({\uprho }_{{\text{E}}}\) = 1, 4 and 8. The plots show that as the value of \({\uprho }_{{\text{E}}}\) increases at fixed values of \({\text{a}}_{{{\text{s}}_{1} }}\), \({\text{N}}_{{\text{E}}}\) and \({\text{N}}_{{{\text{MU}}}}\) ESC decreases. So, as the value of average SNR of the eavesdropper link increase the performance of system decreases in term of ESC.
To provide a comparative analysis of the proposed cooperative NOMA system, a cooperative OMA system is considered in the simulation. Figure 6 shows the plots of ESC versus average SNR of legal link and results that cooperative NOMA system outperforms the cooperative OMA system in terms of ESC.
5 Conclusion
In this paper, we propose a cooperative NOMA model with an untrusted user. We derive the lower bound of ergodic secrecy capacity of the proposed cooperative NOMA system. Simulation results demonstrate that proposed NOMA system outperforms the conventional cooperative OMA system in terms of secrecy performance. The analysis of proposed system model may be help in current wireless networks to avoid the leakage of confidential data by untrusted users with strong eavesdropping capabilities, which receives a lot of interest from both academics and industry. In the future, multi-relay scenarios may be used for proposed system model in which the best relay need to be chosen to transfer the message signal and the other relays may be used to provide interference to the untrusted user.
Availability of Data and Material
Not applicable.
Code Availability
Not applicable.
References
Dai, L., Wang, B., Yuan, Y., Han, S., Chih-Lin, I., & Wang, Z. (2015). Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Communications Magazine, 53(9), 74–81.
Islam, S. R., Avazov, N., Dobre, O. A., & Kwak, K. S. (2016). Power-domain non-orthogonal multiple access (NOMA) in 5G systems: Potentials and challenges. IEEE Communications Surveys and Tutorials, 19(2), 721–742.
Ding, Z., Liu, Y., Choi, J., Sun, Q., Elkashlan, M., Chih-Lin, I., & Poor, H. V. (2017). Application of non-orthogonal multiple access in LTE and 5G networks. IEEE Communications Magazine, 55(2), 185–191.
Zhang, Z., Ma, Z., Xiao, M., Liu, G., & Fan, P. (2017). Modeling and analysis of non-orthogonal MBMS transmission in heterogeneous networks. IEEE Journal on Selected Areas in Communications, 35(10), 2221–2237.
Yue, X., Liu, Y., Kang, S., Nallanathan, A., & Ding, Z. (2017). Exploiting full/half-duplex user relaying in NOMA systems. IEEE Transactions on Communications, 66(2), 560–575.
Lv, L., Chen, J., Ni, Q., & Ding, Z. (2017). Design of cooperative non-orthogonal multicast cognitive multiple access for 5G systems: User scheduling and performance analysis. IEEE Transactions on Communications, 65(6), 2641–2656.
Yang, Q., Wang, H. M., Ng, D. W. K., & Lee, M. H. (2017). NOMA in downlink SDMA with limited feedback: Performance analysis and optimization. IEEE Journal on Selected Areas in Communications, 35(10), 2281–2294.
Lv, L., Zhou, F., Chen, J., & Al-Dhahir, N. (2019). Secure cooperative communications with an untrusted relay: A NOMA-inspired jamming and relaying approach. IEEE Transactions on Information Forensics and Security, 14(12), 3191–3205.
Timotheou, S., & Krikidis, I. (2015). Fairness for non-orthogonal multiple access in 5G systems. IEEE Signal Processing Letters, 22(10), 1647–1651.
Xu, P., & Cumanan, K. (2017). Optimal power allocation scheme for non-orthogonal multiple access with α-fairness. IEEE Journal on Selected Areas in Communications, 35(10), 2357–2369.
Liu, Y., Elkashlan, M., Ding, Z., & Karagiannidis, G. K. (2016). Fairness of user clustering in MIMO non-orthogonal multiple access systems. IEEE Communications Letters, 20(7), 1465–1468.
Ding, Z., Peng, M., & Poor, H. V. (2015). Cooperative non-orthogonal multiple access in 5G systems. IEEE Communications Letters, 19(8), 1462–1465.
Do, T. N., da Costa, D. B., Duong, T. Q., & An, B. (2018). Improving the performance of cell-edge users in NOMA systems using cooperative relaying. IEEE Transactions on Communications, 66(5), 1883–1901.
Zhou, Y., Wong, V. W., & Schober, R. (2018). Stable throughput regions of opportunistic NOMA and cooperative NOMA with full-duplex relaying. IEEE Transactions on Wireless Communications, 17(8), 5059–5075.
Khan, M. J., Chauhan, R. C. S., & Singh, I. (2022). Performance analysis of heterogeneous network using relay diversity in high-speed vehicular communication. Wireless Personal Communications, 125(2), 1163–1184.
Khan, M. J., Chauhan, R. C. S., & Singh, I. (2022). Outage probability and throughput of cooperative non-orthogonal multiple access with moving relay in heterogeneous network. Transactions on Emerging Telecommunications Technologies, 33(12), e4616.
Khan, M. J., Chauhan, R. C. S., & Singh, I. (2023). Energy-efficient multiple cooperative moving relay selection for heterogeneous nonorthogonal-multiple access systems. International Journal of Communication Systems, 36(4), e5408.
Khan, M. J., Chauhan, R. C. S., & Singh, I. (2022). Comparative analysis of full duplex and half duplex relay for high-speed vehicular scenario. Wireless Personal Communications, 127(4), 3435–3448.
Saito, Y., Benjebbour, A., Kishiyama, Y., & Nakamura, T. (2013). System-level performance evaluation of downlink non-orthogonal multiple access (NOMA). In 2013 IEEE 24th annual international symposium on personal, indoor, and mobile radio communications (PIMRC) (pp. 611–615). IEEE.
Ding, Z., Yang, Z., Fan, P., & Poor, H. V. (2014). On the performance of non-orthogonal multiple access in 5G systems with randomly deployed users. IEEE Signal Processing Letters, 21(12), 1501–1505.
Liaqat, M., Noordin, K. A., Abdul Latef, T., & Dimyati, K. (2020). Power-domain non orthogonal multiple access (PD-NOMA) in cooperative networks: An overview. Wireless Networks, 26, 181–203.
Zeng, M., Yadav, A., Dobre, O. A., & Poor, H. V. (2017). A fair individual rate comparison between MIMO-NOMA and MIMO-OMA. In 2017 IEEE globecom workshops (GC Wkshps) (pp. 1–5). IEEE.
Abuajwa, O., Roslee, M. B., Yusoff, Z. B., Lee, L. C., & Pang, W. L. (2022). Throughput fairness trade-offs for downlink non-orthogonal multiple access systems in 5G networks. Heliyon, 8(11), e11265.
Laneman, J. N., Tse, D. N., & Wornell, G. W. (2004). Cooperative diversity in wireless networks: Efficient protocols and outage behavior. IEEE Transactions on Information Theory, 50(12), 3062–3080.
Saito, Y., Kishiyama, Y., Benjebbour, A., Nakamura, T., Li, A., & Higuchi, K. (2013). Non-orthogonal multiple access (NOMA) for cellular future radio access. In 2013 IEEE 77th vehicular technology conference (VTC Spring) (pp. 1–5). IEEE.
Ding, Z., Lei, X., Karagiannidis, G. K., Schober, R., Yuan, J., & Bhargava, V. K. (2017). A survey on non-orthogonal multiple access for 5G networks: Research challenges and future trends. IEEE Journal on Selected Areas in Communications, 35(10), 2181–2195.
Zhao, J., Liu, Y., Chai, K. K., Chen, Y., Elkashlan, M., & Alonso-Zarate, J. (2016). NOMA-based D2D communications: Towards 5G. In 2016 IEEE global communications conference (GLOBECOM) (pp. 1–6). IEEE.
Zaghdoud, N., Mnaouer, A. B., Boujemaa, H., & Touati, F. (2020). Secrecy performance analysis of cooperative NOMA system with multiple DF relays. In 2020 International wireless communications and mobile computing (pp. 2160–2163). Limassol, Cyprus.
Yu, C., Ko, H. L., Peng, X., & Xie, W. (2019). Secrecy outage performance analysis for cooperative NOMA over Nakagami-m channel. IEEE Access, 7, 79866–79876.
Li, B., Xu, D., Chen, B., & Ahmad, I. (2022). On the secrecy outage performance of cooperative NOMA-assisted hybrid satellite-terrestrial networks. Wireless Communications and Mobile Computing. https://doi.org/10.1155/2022/9425490
Kieu, T. N., Tran, D. D., Ha, D. B., & Voznak, M. (2019). Secrecy performance analysis of cooperative MISO NOMA networks over Nakagami-m fading. IETE Journal of Research, 68(2), 1183–1194.
Van Nguyen, M. S., & Do, D. T. (2020). Evaluating secrecy performance of cooperative NOMA networks under existence of relay link and direct link. International Journal of Communication Systems, 33(6), e4284.
Shukla, M. K., & Nguyen, H. H. (2020). Ergodic secrecy sum rate analysis of a two-way relay NOMA system. IEEE Systems Journal, 15(2), 2222–2225.
Awad, M., Ibraheem, S. M., Napoleon, S. A., Saad, W., Shokair, M., & Nasr, M. E. (2020). Secrecy enhancement of cooperative NOMA networks with two-way untrusted relaying. IEEE Access, 8, 216349–216364.
Yuan, C., Tao, X., Li, N., Ni, W., Liu, R. P., & Zhang, P. (2019). Analysis on secrecy capacity of cooperative non-orthogonal multiple access with proactive jamming. IEEE Transactions on Vehicular Technology, 68(3), 2682–2696.
Ruby, R., Riihonen, T., Wu, K., Liu, Y., & ElHalawany, B. M. (2021). Performance analysis of multi-phase cooperative NOMA systems under passive eavesdropping. Signal Processing, 182, 107934.
Chen, J., Yang, L., & Alouini, M. S. (2018). Physical layer security for cooperative NOMA systems. IEEE Transactions on Vehicular Technology, 67(5), 4645–4649.
Kim, J. B., & Lee, I. H. (2015). Capacity analysis of cooperative relaying systems using non-orthogonal multiple access. IEEE Communications Letters, 19(11), 1949–1952.
Wang, M., Duan, W., Zhang, G., Wen, M., Choi, J., & Ho, P. H. (2022). On the achievable capacity of cooperative NOMA networks: RIS or relay? IEEE Wireless Communications Letters, 11(8), 1624–1628.
Barton, D. E. (1965). Handbook of mathematical functions with formulas, graphs and mathematical tables. Wiley.
Gradshteyn, I. S., & Ryzhik, I. M. (2014). Table of integrals, series, and products. Academic Press.
Acknowledgements
The authors would like to express their gratitude to Integral University, Lucknow, Uttar Pradesh, India, for its support. The manuscript communication number for this publication is IU/R&D/2023-MNC0002246.
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
The First Author has conceptualized the manuscript. The second author has handled the simulations and drafting.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical Approval and Consent to Participate
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ahmad, S., Khan, M.J. Ergodic Secrecy Capacity of Cooperative NOMA System with Untrusted User. Wireless Pers Commun 133, 181–198 (2023). https://doi.org/10.1007/s11277-023-10761-1
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10761-1