Abstract
In this paper, we study a physical layer security improvement method for a multi-user cooperative non-orthogonal multiple access (NOMA) system in the presence of an adaptive eavesdropper. In the system, the eavesdropper adaptively switches the eavesdropping mode and interference mode. In order to resist the eavesdropping attack of the eavesdropper, a number of device-to-device (D2D) relay users are available for cooperating to forward legitimate signals, and one of them can be selected for assistance through a user selection strategy based on the channel side information (CSI) of the eavesdropping channel. The selected relay uses the NOMA technology to superimpose ordinary signals that only require data services with the received sensitive signals, and then forwards the superimposed signals. The ergodic secrecy sum capacity lower bound of the system is derived. Theoretical analysis and Monte Carlo simulation show that the performance of the proposed multi-user cooperative NOMA system is better than that of the single-relay user cooperative system.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Since the available frequency band of mobile communication is mainly below 3 GHz, 5G networks need to meet the requirements of low latency and massive connections under limited spectrum resources. Non-orthogonal multiple access (NOAM) is a important technology to solve the shortage of spectrum resources. Its basic principle is that the transmitter adopts power domain superposition coding, actively introducing interference information, and the receiver adopts successive interference cancellation (SIC) to realize correct demodulation [1].
Due to shadow fading and path loss, the communication reliability of users far from the transmitter is poor. Relay cooperative NOMA network can improve the communication quality of far users. According to the NOMA superposition coding principle, strong user know the signal information of weak users and act as a Decode-and-Forward (DF) relay to assist in forwarding the signal information of weak users [2]. Under the statistical channel state information (CSI), the authors analyzed a communication system in which a single relay forwards the signals of multiple edge users over Nakagami-m fading channels, and the differences between DF relay and amplify-and-forward (AF) relay in improving communication performance was compared in [3]. In addition, device-to-device (D2D) technology allows two adjacent user equipment to communicate directly by reusing the spectrum resources of the cellular network, thereby reducing communication delay and improve spectrum utilization. So D2D relay cooperative communication based on NOMA has attracted extensive research scholars’ attention. For D2D cooperative NOMA network, a power allocation strategy based on signal-to-noise ratio (SNR) was proposed in [4] to achieve the maximum capacity. Moreover, two different SIC decoding schemes were proposed in [5], namely the single signal decoding scheme and the maximum ratio combining (MRC) decoding scheme, respectively, and the authors compared and analyzed the influence of different decoding schemes on communication performance. In order to avoid the loss of communication performance caused by SIC error decoding, according to the decoding of D2D relay, three different relay forwarding strategies were studied in [6].
Due to the openness of RF signals, sensitive information with high security requirements is easily attacked by eavesdroppers during transmission. Therefore, the security of NOMA network must be considered. Relay cooperation can not only improve the communication reliability of cell-edge users, but also help legitimate nodes improve the physical layer security of the system. Physical layer security technology is based on Shannon theory. Its main idea is to protect the physical layer by using the inherent random characteristics of wireless channel [7]. At present, many researches on physical layer security are relay selection, cooperative beamforming, cooperative interference and so on. According to the different understanding of the eavesdropping channel, the corresponding relay selection strategy was proposed to combat the malicious eavesdropping of adaptive eavesdroppers in [8]. Considering the problem of energy limitation in communication, a AF relay collected energy from part of artificial interference signals, and forwarded the remaining artificial interference signals to eavesdroppers, so as to protect the legitimate signals [9]. In [10], the multi-antenna relay beamforming technology was used to design artificial interference signals to interfere with eavesdroppers without affecting the communication of legitimate users.
At present, there is little research on D2D cooperative NOMA scheme in the intelligent eavesdropping scenario. Furthermore, each user has different requirements for information security service experience. For example, sensitive information such as bank information and personal privacy information has high security requirements, but ordinary data information has low security requirements. So this paper proposes a multi-user cooperative NOMA scheme by using the differences of users’ security service requirements, in order to further improve physical layer security, a user selection strategy was studied. We derive the expression on the ergodic secrecy sum capacity lower bound of the proposed scheme, and compare the performance differences between the scheme and single user cooperative NOMA scheme.
2 System Model
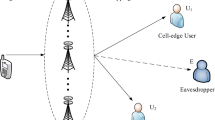
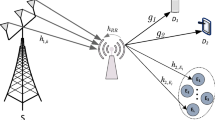
Figure 1 shows the system model of the proposed scheme, where a source node denoted S, a number N of DF relay user nodes denoted \({\text{R}}_k \left( {k = 1,2, \ldots ,N} \right)\), two destination nodes denoted \({\text{D}}_{1}\) and \({\text{D}}_2\), and a eavesdropping node denoted E are considered. All nodes work in half-duplex mode, equipped with a single antenna. Moreover, E is equipped with a directional antenna. We assume that all channels are independent quasi-static Rayleigh fading channels. Denote \(h_{{\text{S1}}}\), \(h_{{\text{SR}}_k }\), \(h_{{\text{R}}_k {\text{E}}}\), \(h_{{\text{R}}_k {2}}\), \(h_{{\text{E1}}}\), \(h_{{\text{ER}}_k }\) as the channel coefficients of links \({\text{S - D}}_1\), \({\text{S - R}}_k\), \({\text{R}}_k {\text{ - E}}\), \({\text{R}}_k {\text{ - D}}_2\), \({\text{E - D}}_1\), \({\text{E - R}}_k\) respectively. According to [11], \(h_{{\text{R}}_k {\text{E}}} = h_{{\text{ER}}_k }\). Due to path loss and shadow fading, the links \({\text{S - D}}_2\) and \({\text{S - E}}\) are not available. \(h_{{\text{S1}}}\), \(h_{{\text{SR}}_k }\), \(h_{{\text{R}}_k {\text{E}}}\), \(h_{{\text{R}}_k {2}}\), \(h_{{\text{E1}}}\), \(h_{{\text{ER}}_k }\) are independent complex Gaussian random variables with mean denoted as \(\lambda_{{\text{S1}}}\), \(\lambda_{{\text{SR}}_k }\), \(\lambda_{{\text{R}}_k {\text{E}}}\), \(\lambda_{{\text{R}}_k 2}\), \(\lambda_{{\text{E1}}}\), \(\lambda_{{\text{R}}_k {\text{E}}}\). Each node knows the CSI between itself and other nodes, and the CSI of the eavesdropping channel can be obtained by the method mentioned in [12]. Here E is an intelligent eavesdropper, which means that if E detects the signal transmitted by \({\text{R}}_k\), E will work in eavesdropping mode and directed eavesdropping \({\text{R}}_k\), otherwise it will switch to interference mode.
2.1 Design of Transmission Scheme
The entire transmission process comprises two phases. In the first phase, the source node S broadcasts the superimposed signal \(\sqrt {a_1 P_{\text{S}} } x_1 + \sqrt {a_2 P_{\text{S}} } x_2\), where \(P_{\text{S}}\) is the transmit power of S, \(x_i\) represents the intended message for \({\text{D}}_i\), \(i \in \left\{ {1,2} \right\}\). According to NOMA principles, the power allocation coefficient \(a_1 < a_2\) and \(a_1 + a_2 = 1\). At the same time, the eavesdropper E executes interference mode and transmits interference signals \(\sqrt {P_{\text{J}} } x_{\text{J}}\) to legitimate nodes. The signal received at \({\text{D}}_1\) and R are given by
where \(n_1 \sim CN\left( {0,\sigma_1 } \right)\) and \(n_{{\text{R}}_k } \sim CN\left( {0,\sigma_{{\text{R}}_k } } \right)\) represent the additive white Gaussian noise AWGN at \({\text{D}}_1\) and \({\text{R}}_k\) respectively. To abide with the principle of SIC, \({\text{D}}_1\) first decodes and removes the symbol \(x_2\) by treating the symbol \(x_1\) as noise, and then will decode symbol \(x_1\). The received signal-to-interference-plus-noise ratio (SINR) for \(x_1\) and \(x_2\) at \({\text{D}}_1\) are given by
Similarly, the received SINR for \(x_2\) at \({\text{R}}_k\) is expressed as
In the second phase, in order to alleviate the communication congestion and reduce the SINR of the eavesdropper, \({\text{R}}_k\) forwards the new superimposed signal \(\sqrt {a_1 P_{\text{R}} } x_{\text{R}} + \sqrt {a_2 P_{\text{R}} } x_2\) with the transmit power \(P_{\text{R}}\). \(x_{\text{R}}\) is the normal data signal intended for \({\text{D}}_2\). Assuming that in the entire time slot, E can detect the signal forwarded by R, so it works in eavesdropping mode. The signal received at \({\text{D}}_2\) and E are given by
where \(n_2 \sim CN\left( {0,\sigma_2 } \right)\) and \(n_{\text{E}} \sim CN\left( {0,\sigma_{\text{E}} } \right)\) represent the AWGN at \({\text{D}}_2\) and E respectively. The received SINR for \(x_2\) and \(x_{\text{R}}\) can be obtained as
Since E only decodes sensitive signals \(x_2\) that have eavesdropping value, the received SINR at E is given by
In order to reduce the eavesdropping quality of E, we propose a relay selection strategy that minimizes the channel gain of eavesdropping, and the mathematical expression is as follows
3 Analysis of Ergodic Secrecy Sum Capacity
Here we use ergodic secrecy sum capacity (ESSC) as the performance indicator to evaluate the effectiveness of the proposed scheme. For the convenience of writing, let \(\sigma_i^2 = \sigma^2\), for \(i \in \left\{ {1,2,{\text{R}}_b ,{\text{E}}} \right\}\), \(\gamma_{\text{S}} = \frac{{P_{\text{S}} }}{\sigma^2 }\), \(\gamma_{\text{J}} = \frac{{P_{\text{J}} }}{\sigma^2 }\), \(\gamma_{\text{R}} = \frac{{P_{\text{R}} }}{\sigma^2 }\), \(\beta_\varphi \triangleq \left| {h_\varphi } \right|^2\), for \(\varphi \in \left\{ {{\text{S1,SR}}_b ,{\text{R}}_b {\text{E}},{\text{R}}_b {\text{2,E1,ER}}_b } \right\}\).
3.1 Ergodic Secrecy Capacity of \({\varvec{x}}_{\bf{1}}\)
Ergodic secrecy capacity (ESC) of \(x_1\) is defined as \(\overline{C}_{{\text{ESC}}}^{x_1 } \triangleq {\mathbb{E}}\left[ {\left\{ {C_1^{x_1 } - C_{\text{E}}^{x_1 } } \right\}^+ } \right]\), where \(C_1^{x_1 }\) and \(C_{\text{E}}^{x_1 }\) is the achievable maximum instantaneous rate of \(x_1\) at \({\text{D}}_1\) and E respectively. According to Jensen’s inequality, the definition of the ESC lower bound of \(x_1\) can be expressed as
Let \(Q_1 = \gamma_{1 \to x_1 }\), the complementary cumulative distribution function (CCDF) of \(Q_1\) is written as
Using the equation in [5]
and [13, Eq. (25.4)], we can finally obtain
where \(\alpha_i = \cos \frac{{\left( {2i - 1} \right)\pi }}{2L_1 }\), \(\theta_i = \frac{\pi }{4}\alpha_i + \frac{\pi }{4}\), \(L_1\) denotes the number of the Gauss–Chebyshev quadrature approximation. Due to path loss and shadows, the eavesdropper E cannot eavesdrop on the superimposed signal broadcasted by S, thus \(\overline{C}_{\text{E}}^{x_1 } = 0\)。Substituting \(\overline{C}_{\text{E}}^{x_1 } = 0\) and (15) into (12), the expression of the ESC lower bound of \(x_1\) can be obtained as
3.2 Ergodic Secrecy Capacity of \({\varvec{x}}_{\bf{2}}\)
Similar to \(x_1\), using Jensen’s inequality, the definition of the ESC lower bound of \(x_2\) can be expressed as
where \(C_2^{x_2 }\) and \(C_{\text{E}}^{x_2 }\) is the achievable maximum instantaneous rate of \(x_2\) at \({\text{D}}_1\) and E. Let \(T_1 = \min \left\{ {\gamma_{1 \to x_2 } ,\gamma_{{\text{R}}_k \to x_2 } ,\gamma_{2 \to x_2 } } \right\}\), \(T_2 = \gamma_{{\text{E}} \to x_2 }\), \(V_1 = \beta_{{\text{R}}_b {\text{E}}}\), where \(T_1\) is the effective received SNR for \(x_2\). Due to \(\left| {h_{{\text{R}}_{1} {\text{E}}} } \right|^2 ,\left| {h_{{\text{R}}_2 {\text{E}}} } \right|^2 , \ldots ,\left| {h_{{\text{R}}_N {\text{E}}} } \right|^2\) are an independent and identically distributed random variable, the probability density function (PDF) of \(V_1\) is \(f_{V_1 } \left( {v_1 } \right) = \frac{N}{{\lambda_{{\text{RE}}} }}{\text{e}}^{ - \frac{N}{{\lambda_{{\text{RE}}} }}v_1 }\). The achievable ESC of \(x_2\) at \({\text{D}}_2\) and E can be written as
In order to obtain the expression of \(C_2^{x_2 }\) and \(C_{\text{E}}^{x_2 }\), we derive the CCDF of \(T_1\) and \(T_2\) as follows:
Substituting (20) into (18), the achievable ESC of \(x_2\) at \({\text{D}}_2\) is given by
where \(L_2\) denotes the number of the Gauss–Chebyshev quadrature approximation, \(y_i = \cos \frac{{\left( {2i - 1} \right)\pi }}{2L_2 }\), \(x_i = y_i\), and
Using (19), (21) and [14, Eq. (3.352.2)], the achievable ESC of \(x_2\) at E is given by
where \({\text{Ei}}\left( \cdot \right)\) is exponential integral function. Therefore, the expression of the ESC lower bound of \(x_2\) can be finally obtained as
3.3 Ergodic Secrecy Capacity of \({\varvec{x}}_{\bf{R}}\) and ESSC of System
Since \(x_{\text{R}}\) is a ordinary data signal, and E only intercepts valuable and sensitive signals, the ergodic secrecy capacity of \(x_{\text{R}}\) is its ergodic capacity. Let \(V_2 = \gamma_{2 \to x_{\text{R}} }\), CCDF of \(V_2\) is as follows
According to [14, Eq. (3.352.4)], the ergodic secrecy capacity of \(x_{\text{R}}\) can be written as
So the ESSC of system is approximated as
4 Numerical Analysis
In this section, we will evaluate the performance of our proposed D2D-NOMA system in terms of ESSC under the user selection scheme through simulation. The relevant parameter settings in the simulation are as follows: \(L_1 = L_2 = 100\), legal channel parameters \(\lambda_{{\text{S1}}} = \lambda_{{\text{SR}}} = 1\), \(\lambda_{{\text{R2}}} = 2\), in order to avoid being discovered, the eavesdropper is far away from the legal nodes, so \(\lambda_{{\text{RE}}} = \lambda_{{\text{E1}}} = 0.1\). If there is no special instructions, we set \(\gamma_{\text{S}} = \gamma_{\text{R}} = 30\,{\text{dB}}\), \(a_1 = 0.2\), \(a_2 = 0.8\) and \(N = 10\). Similarly, due to the need for concealment, \(\gamma_{\text{J}} = 5\,{\text{dB}}\). The number of Monte Carlo simulations is 1,000,000.
For comparison, we consider the following benchmark schemes in the simulation.
-
(1)
Benchmark scheme 1 is a multi-relay user cooperative NOMA scheme, in which the number of relay users is \(N = 10\). In the first time slot, S broadcast superimposed signal \(\sqrt {a_1 P_{\text{S}} } x_1 + \sqrt {a_2 P_{\text{S}} } x_2\), at the same time the eavesdropper transmits interference signals \(\sqrt {P_{\text{J}} } x_{\text{J}}\). In the second time slot, the selected relay forward the signal \(x_2\) with the transmit power \(P_{\text{R}}\), and E switches to eavesdropping mode.
-
(2)
Benchmark scheme 2 is a single-relay user cooperative NOMA scheme, in which the number of relay users is \(N = 1\). In first time slot, S broadcast superimposed signal \(\sqrt {a_1 P_{\text{S}} } x_1 + \sqrt {a_2 P_{\text{S}} } x_2\), and the eavesdropper transmits interference signals \(\sqrt {P_{\text{J}} } x_{\text{J}}\). In the second time slot, relay user forwards signal \(\sqrt {a_1 P_{\text{R}} } x_{\text{R}} + \sqrt {a_2 P_{\text{J}} } x_2\), and E switches to eavesdropping mode.
Figure 2 shows the relationship between the number of relay users and the system ESSC under different power allocation factors. As shown in Fig. 1, as the number of relay users increases, the ESSC of the system increases monotonically, and compared to \(a_1 = 0.4\), the number of relay users has a greater impact on the system ESSC when \(a_1 = 0.2\). It can also be observed from the figure, secrecy performance of the system when \(a_1 = 0.4\) is better than that of the system when \(a_1 = 0.2\). This is because there is more power allocated to \(x_1\) and \(x_{\text{R}}\) when \(a_1 = 0.4\), which is beneficial for \({\text{D}}_1\) to resist the interference attack of E, furthermore the eavesdropper does not eavesdrop on the ordinary data signals \(x_{\text{R}}\).
Figure 3 simulates the influence of the eavesdropper’s transmitted SINR on the system ESSC. The simulation shows that the security performance of the proposed scheme is better than that of Benchmark scheme 1 and Benchmark scheme 2, and the performance gap between the proposed scheme and Benchmark scheme 1 is more obvious. It implies that it is of great significance to design a secure communication scheme based on the differences in user experience requirements for information security services. In addition, it can also be observed that the ESSC of the proposed scheme and Benchmark scheme 2 tend to a positive definite value in the high SIR, this is because the transmission of \(x_{\text{R}}\) occurs in the second time slot, so it will not be affected by the interference of E. By comparing the curves of Monte Carlo simulation and theoretical analysis, it can be found that the two basically overlap, reflecting the accuracy of the numerical calculation.
5 Conclusions
This paper combines user selection technology with D2D technology to design a NOMA communication scheme against intelligent eavesdropping, and derives the expression of the ESSC lower bound of the proposed scheme. Theoretical derivation and simulation show that the proposed scheme is better than the two Benchmark schemes. The communication system can take advantage of the differences in information security service experience requirements of each user to alleviate communication congestion and improve the overall security performance. In addition, by increasing the number of relay users, the security of information transmission can be further ensured.
References
Wang, G., Xu, X., Zhou, R., Zhang, R.: Power domain non-orthogonal multiple access technology for wireless communication. Radio Commun. Technol. 45(4), 329–336 (2019)
Ding, Z., Peng, M., Poor, H.: Cooperative non-orthogonal multiple access in 5G systems. IEEE Commun. Lett. 19(8), 1462–1465 (2015)
Wan, D., Wen, M., Ji, F., Liu, Y., Huang, Y.: Cooperative NOMA systems with partial channel state information over Nakagami-m fading channels. IEEE Trans. Commun. 66(3), 947–958 (2018)
Kim, J., Lee, I., Lee, J.: Capacity scaling for D2D aided cooperative relaying systems using NOMA. IEEE Commun. Lett. 7(1), 42–45 (2018)
Ji, Y., Wen, M., Padidar, P., Duan, W., Li, J., Cheng, N., Ho, P.: Spectral efficiency enhanced cooperative device-to-device systems with NOMA. IEEE Trans. Intell. Transp. Syst. 22(7), 4040–4050 (2021)
Duan, W., Ji, Y., Hou, J., Zhuo, B., Wen, M., Zhang, G.: Partial-DF full-duplex D2D-NOMA systems for IoT with/without an eavesdropper. IEEE Internet Things J. 8(8), 6154–6166 (2021)
Zou, Y., Zhu, J., Wang, X., Hanzo, L.: A survey on wireless security: technical challenges, recent advances, and future trends. Proc. IEEE 104(9), 1727–1756 (2016)
Yang, L., Chen, J., Jiang, H., Vorobyov, S., Zhang, H.: Optimal relay selection for secure cooperative communications with an adaptive eavesdropper. IEEE Trans. Wireless Commun. 16(1), 26–42 (2017)
Lee, K., Hong, J., Choi, H., Levorato, M.: Adaptive wireless-powered relaying schemes with cooperative jamming for two-hop secure communication. IEEE Internet Things J. 5(4), 2793–2803 (2018)
Cao, Y., Zhao, N., Pan, G., Chen, Y., Fan, L., Jin, M., Alouini, M.: Secrecy analysis for cooperative NOMA networks with multi-antenna full-duplex relay. IEEE Trans. Commun. 67(8), 5574–5587 (2019)
Bletsas, A., Shin, H., Win, M.: Cooperative communications with outage-optimal opportunistic relaying. IEEE Trans. Wireless Commun. 6(9), 3450–3460 (2007)
Shim, K., Do, T., Nguyen, T., Costa, D., An, B.: Enhancing PHY-security of FD-enabled NOMA systems using Jamming and user selection: performance analysis and DNN evaluation. IEEE Internet Things J. https://doi.org/10.1109/JIOT.2021.3080425
Abramowitz, M., Stegun, I.: Handbook Mathematical Functions with Formulas, Graphs, Mathematical Tables. New York, NY , USA, Dover (1972)
Gradshteyn, I., Ryzhik, I.: Table of Integrals, Series and Products, 7th edn. NY, USA, Academic, New York (2007)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Ma, M., He, Y., Zhang, Y., Zhang, Y., Zhou, L. (2023). Enhancing Physical Layer Security of Cooperative NOMA Systems Using User Selection. In: Jain, L.C., Kountchev, R., Zhang, K., Kountcheva, R. (eds) Advances in Wireless Communications and Applications. ICWCA 2021. Smart Innovation, Systems and Technologies, vol 299. Springer, Singapore. https://doi.org/10.1007/978-981-19-2255-8_3
Download citation
DOI: https://doi.org/10.1007/978-981-19-2255-8_3
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-2254-1
Online ISBN: 978-981-19-2255-8
eBook Packages: EngineeringEngineering (R0)