Abstract
Internet of Thing (IoT) collects huge amount of data from the surrounding by monitoring and sensing. Further, transferring these data from IoT devices to cloud environment seems is very challenging. Such that, this paper concentrates on energy consumption, in which the energy efficient routing and priority dependent techniques are proposed. This technique depends upon the RPL network (Routing Protocol for Low power and Lossy), which efficiently predicts routing over contents. Every network slot utilizes timing pattern while forwarding image data, audio data. The proposed method enhances the strength of routing protocol and also avoids congestion. The outcomes of the study illustrates that proposed Energy efficient priority based routing (EEPR) technique minimize overheads on mesh, energy consumption and end-end delay. Also, the proposed method outperforms the existing QRPL methods in IoT platform.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
IoT plays an important role in network by managing continuous data collection [1]. The IoT is system of interrelated smart computing devices, mechanical devices, digital objects and machines with potential of transferring data over a network which is linked with intermediate nodes to cloud data center. Mobile and stationary IoT devices helps in providing complex and simple services for big data application and cloud environment [2]. However, increase in size of IoT applications, there are various limitation of IoT devices. Certain challenges were addressed by the large scale IoT applications in transferring data such as: load balancing, energy consumption, security and fault tolerance. Energy consumption is one among the challenges which has attracted the researchers [3, 4].
Energy-aware IoT application with respect to computing, gathering, consumption and energy optimization has become critical industrial problems [5, 6]. For lower power devices, IoT have concrete path to become portion of internet and donates to exchange and collection of information to satisfy needs of the installed system [7, 8].
Installment of such system have revolutionized exchange of services and information in various fields likes environmental and health monitoring. Hence, energy-aware routing are most significant for IoT based applications [9, 10].
Most of the IoT application concentrates on monitoring discrete events which produce huge quantity of data [11]. Extracting meaningful data from big data which is collected by IoT components and sensors is big challenge for IoT based system. The IoT applications uses WSN (Wireless sensor network) for data transmission and communication, where security problem becomes more serious. Therefore, various security mechanism had been introduced [12]. It’s observed that ESN has several challenges because of their connected capabilities hardware, limited coverage area [13]. Apparently, inherent risk of such kind of networks is routing, communication and data aggregation from source to final end point [14]. For instance, gathering huge quantity of data results in increased traffic congestion in the network. Network traffic yields unpredictable and unreliable performance of network. Hence, nodes in the platform was gathered for their energy while directing data [15].
Sensors and smart devices forward data constantly to cloud and cloud has responsibility to analyze the data and take right decision mainly for dynamic environment [16]. Hence, energy effective routing protocol is needed to eliminate overheads and data congestion.
In this paper, energy effective and priority dependent routing method is introduced depending on RPL to maintain IoT systems, where content type is used to predict routing. In proposed RPL, suppose if the error arises in the parent member node, then its members would stay active till configuration and convergence of parentless comments and their packet terminate because of time lapse. Additionally, the researcher makes an attempt to choose parent node to avoid delay. Here technology of content-dependent routing is used with RPL to determine routing. Whereas by integrating roaming data with respect to conventional relay nodes for aggregation, data processing was attained at higher rate. Therefore, congestion in network get reduced efficiently. Hence, delay is reduced besides satisfying QoS (Quality of Service) for requirements.
1.1 Objective of the Paper
-
Proposed energy-effective and priority dependent RPL model for IoT system to minimize energy consumption, delay and traffic.
-
In RPL approximate parent node is chosen to avoid development of unsuitable branches and minimize energy consumption and delay.
-
Increasing efficiency of network with respect to optimal speed for transmission packets in IoT platform.
1.2 Paper Organization
Rest of this research is organized as: In Sect. 2, various research works were reviewed with respect to proposed method’s advantage and limitation. In Sect. 3, proposed work is elaborated briefly with flow diagram. In Sect. 4, implementation of proposed work is done to evaluate its performance. In Sect. 5, research work is concluded with future work.
2 Review of Exisitng Works
This section introduce discussion routing protocol for energy efficient and priority dependent technique in IoT platform.
2.1 Priority-Dependent Routing
Data aggregation technique and routing models in WSN is of great interest [5, 6]. 2 methods were introduced such as distributed and centralized. Before network begins with work, optimal routing structure is developed and pre-computation is done. For instance, [17] for maximum network lifetime presented merge tree solution. Energy aware data aggregation technique were taken in [18] which reduce count of packets in WSN platform. Above said technique acquire packet overheads, therefore distributed clustering technique were utilized to minimize overheads [19, 20]. Such techniques route to hierarchical topologies over local message distribution. However, shortest path is simple topology which was utilized in [21]. Dynamic clustering was proposed in [22]. Clustering is need to be done on any applications. This enforce large transfer cost to create cluster. Moreover, to run directed acyclic graph [5] and tree dependent techniques [5, 23] requires routing topology and capacity to control dynamic network situation was restricted. This is due to, whenever alteration happens in network dynamic like discharge of few critical IoT nodes, failure of primary energy link, there is need to update by network topology to reproduces conditions of ruling. It would also presents extra traffic control cost and creates extra delays.
2.2 Energy Effective Routing
Baker et al. [24] introduced energy aware routing design to control Power consumption for transferring data to the cloud data centers. Experiments was conducted with liner programming technique. Vaiyapuri et al. [13] proposed routing technique for IoT platform. This technique depends on ant colony inspired algorithm for resolving tedious issues. /solution develop decentralized ant-dependent algorithm with potential to navigate to find shortest route from source to destination. RPL was provided to optimize target function which facilitates to use more number of nodes as routing nodes to develop (DODAG) destination oriented DAG structure. Here, once IPV6 routing protocol was received by RPL from neighbor then score for every unnamed node was computed.
Yan and Chung [25] presented power aware routing protocol depending on protocol (AODV) Ad-hoc On-demand Distance Vector for vehicular network. Jin et al. [26] proposed (CCR) content centric routing technique to provide data integration and content-dependent data flow inside network with intension to minimize energy sources, avoiding duplicate network congestion, network delay and improving network’s life span.
Dhumane and Prasad [27] proposed energy aware deduction routing technique depending on several objective algorithm for IoT networks. 3 significant factors such as distance, energy and life time of node was considered for examining routing protocol. The researcher used c-means technique for selecting cluster head to reduce count of IoT nodes. Result illustrates that proposed routing technique have possible and optimal feedback when compared with heuristic algorithms.
Preeth et al. [28] introduced fuzzy clustering technique to improve routing protocol’s energy efficiency in IoT platform. In this research used immune based routing algorithm along with reduced energy consumption and high reliability for IoT nodes. According to this research, reducing energy consumption is main contribution for cluster communication. Simulation result illustrates that jitter ratio and packet loss ratio for proposed algorithm were less than existing algorithm which was utilized for same scenario.
Wang and Wang [29] introduced particle energy aware routing technique to balance WSN node’s energy consumption in AODV protocol. Here researcher concentrates on every node’s partial energy level to recognize neighbor node’s optimal link. Simulation was performed with NS2 and result illustrates proposed method’s efficiency.
Yuan et al. [30] proposed energy effective routing protocol and Markov chain for UAV (Unmanned Aerial Vehicles) in platform of IoT. Additionally proposed probabilistic communication graph approach to assist semi-deterministic interactions among UAV node with intention to minimize energy consumption and delay ratio with use of proposed protocol.
3 Proposed Technique
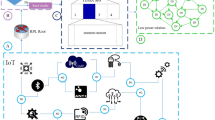
IoT system were developed for several applications like smart city infrastructure, urban services and heath care [4, 11]. However, gathering huge quantity of data from such network for multimedia content frequently outputs in traffic congestion in the network. For the purpose to resolve these problems, here the researcher proposed EEPR technique depending on RPL protocol. Proposed method utilized timing pattern like distance and time data is forwarded in network slot to destination, along with type of data and kind of network traffic.
Figure 1 illustrates framework of proposed EEPR. In IoT platform, numerous types of sensors are utilized to gather data from all electronic devices. In IoT big challenge is to discover best route to transfer data between the nodes.so in order to find appropriate route, RPL protocol is installed. In IoT platform, objects might have serious resource restriction, and therefore there is need for resource management to attain communication and optimal node connection between other devices through internet. However, gathering huge quantity of data like video and image from network yields traffic congestion in network.
Therefore, the researcher has created routing method to predict correct route related to object’s content. In lower-traffic case, video packets were put into TDMA (Time Division Multiple Access) slot. In contrast, for higher traffic case, audio packets were put into TDMA slots. In RPL, node implements DIS (DODAG Information Solicitation) message to predict its following node for neighboring DODAG. Every node makes DODAG maintenance, creation and detection. Following section gives brief explanation for the framework.
3.1 RPL
RPL is standardized and developed by Internet Engineering Task Force (IETF) for low and lossy power networks to allow connectivity in the Internet mesh networks [5]. RPL implement alive process to develop and manage routing for non-circular, directed, destination-oriented graph. In graph, data focus on DODAG’s root. Edges create path from every node to DAG’s root. If network remains constant, low rate DIO beacon process were utilized by RPL to reserve DODAG’s topology. DIO beacons’ were controlled by trickle timer.
Producing RPL message depends on trickle timer, which facilitates nodes to minimize transfer of their control message by maintaining network stability. Till node obtains message which were compatible with its own data, forwarding control packet is expanded by the nodes till it reaches the maximum value [31].
Proposed DODAG is distinct as input of routing with DODAG = (U, M), where U denotes group of nodes and M denotes group of bits used to transfer in packets by Eq. (1).
where \(U_{0}\) denotes DODAG root, \(M_{r}\) denotes primary bit, \(M_{j}^{0}\) and \(M_{j}^{1}\) illustrates 0 and 1 value of jth bit in binary coding voice or video packets.
3.2 Proposed EEPR
In EEPR routing method, every node of the network have 2 properties such as: transmission rate and priority. Node priority takes random bit of 1 or 0 (1 denotes low priority and 0 denotes high priority). Every node in the packets at source side takes the value of 1 or o and forwarded to destination node.
Mostly video or audio are used in input packets. As expressed in EEPR algorithm, video data transferring nodes has (0) as high priority and audio data transferring node has (1) as low priority. Once there occurs congestion in network, nodes with smaller data like text and audio will have priority for forwarding packets. When there is no congestion in network, nodes with numerous packets like video has priority to transfer their packets.
TDMA were utilized to synchronize among receiver and sender and also minimize consumption of energy. Primarily traffic must be checked before positioning data on TDMA slot. If traffic are high then audio packets were forwarded else video packets were forwarded. Committing the time slot to forward the packets depends on transmission rate and priority of node.
Coordinators are responsible committing time slots. Suppose if numerous nodes has same priorities then choosing TDMA depends on transmission rate. Frame value can be altered Utilizing information processing unit to put frame into inactive mode. Preamble bits were utilized in frame’s initial part to synchronize among receiver and sender. For instance, receiver identify that valid data is positioned on channel by obtaining sample of 01,010,101 when there is no data existing on channel. When receiver obtains 10,101,011 this consist of 2 sequential bits of 1, this denotes that valid data begins after 2 sequential 1 r and is ready for obtaining. Module modify its preamble bits in a way to obtain remaining bits.
Iteration’s count is based on primary setting done by data processing unit for the modules in the preamble bits. Once examination of data performed on channel which means once obtaining sequential bits 11 of the sample 10,101,011 in the preamble bits, successive bits were forwarded as the address.
Source address denotes address of the sender frame. In address field of the receiver, destination address of the device is stored to which frame needs to be forwarded this represent destination frame where sensor node needs to forward. In packet’s control part, payload’s length is determined. If there is necessary to forward confirmation, then in control section of packet, ACK bit is activated. Data processing unit utilize space which is referred as payload to obtain data from sensor with use of serial communication among module and data processing unit. In module setting part, payload’s length could be organized from 0 to 32 bytes.
CRC (Cyclic Redundancy Check) towards end of frame is accountable for correctness of frame. Validity of frame is verified only when there is enable of error prediction code, otherwise CRC won’t match the frame and it becomes invalid.

4 Performance Evaluation
Evaluation of EEPR is introduced in this section. Primarily, the researcher highlights used parameters, experimental setup, end-end delay, routing overheads and energy consumption. Then result acquired using proposed is discussed as follows.
4.1 Simulation Setup
NS2 were utilized for simulation test. In experiments used parameters were tabulated in Table 1.
To examine consumption of energy, factor consist of retrieve data, store data and 2 equations was formulated as illustrated below. Energy need to transfer is illustrated in Eq. (7) and energy needed to receive data by node is acquired according to Eq. (8).
Moreover, total consumption of energy for entire node at receiving and sending in RPL is computed in accordance with Eq. (9), where n is count of nodes in RPL path:
Table 2 illustrates used parameters in consumption of energy by Eqs. (1) and (7). Ratio of control packet’s total size to data packet’s total size which is given to destination is discovered as routing overheads. Control packet consist of packets forwarded to request route and the packets which are sent back due to route error is represented as \(S_{{{\text{request}}}}\) and \(S_{{{\text{error}}}}\), to total size of delivered data packets to the destination which is illustrated in Table 3.
Overhead of routing bandwidth is one of the most significant parameter. But in simulation routing overhead is not measurable. Therefore in our experiments the researcher avoids routing overheads. For clarity, the researcher illustrated how routing overhead was computed:
EED (End–End Delay) consist of 3 parameters such as \(c_{{{\text{tranf}}}}\), \(c_{{{\text{priority}}}}\), \(c_{{{\text{trans}}}}\) which is illustrated in Table 4. EED is computed as said in Eq. (11)
Examined EEPR algorithm in varied scenario with different criteria. EEPR is compared with existing QRPL [32] with respect to node’s pause time, EED against node’s maximum speed, routing overheads and energy consumption. This comparison illustrates functionalities and efficiency between existing QRPL and proposed EEPR model.
4.2 Energy Consumption
Comparison among existing QRPL and proposed EEPR algorithm is discussed with respect to consumption of energy. Every node consumes energy for retrieving and storing data. In network, node’s energy is most important and it’s based on battery, which have restricted energy source. For energy consumption, in our algorithm 3 criteria is used: node’s maximum speed, count of nodes and node’s pause time.
4.2.1 Energy Consumption vs Node’s Pause Time
As illustrated in Fig. 2, for every node, there is an increase in pause time with decrease in energy consumption. It’s illustrated that packets were controlled and uploaded for various kinds of traffic, requirements to rebuild connection is minimized which results in increase in lifetime of algorithm. EEPR reduce more consumption of energy than QRPL.
4.2.2 Energy Consumption vs Count of Nodes
In Fig. 3, the researcher compare EEPR with QRPL for energy consumption against count of nodes. By enhancing count of nodes, network’s consumption of energy for EEPR and QRPL gets decreased. When count of node gets increased in the network, then node’s frequency in sample space will be higher. Similarly, while density of network gets increased then nodes consume minimum energy for routing. This minimum consumption of energy by EEPR is mainly due to usage of supplementary nodes. This verifies the scalability of EEPR. Minimum consumption of energy by EPR is higher than QRPL.
4.2.3 Energy Consumption vs Node’s Maximum Speed
As depicted in Fig. 4, both EEPR and QRPL increase energy consumption with increase in node’s maximum speed. This is because of dynamics network topology. When nodes move rapidly, there is rapid changes in network topology. Hence, more number of routing is required, which would improve overall consumption of energy.
4.3 Routing Overheads
For routing overheads, simulation results is depicted in Fig. 5 which express comparison of EEPR and QRPL. Routing overheads represents control packet’s total count in network layer which was forwarded during simulation process, also includes packets which request for path, packets which responds for packet request and packets which announces path failure. Node’s maximum speed is fix to 25 m/s, count of node is fit to 100 and every node’s energy is fit 2 J.
As illustrated in Fig. 5, node’s pause time increases with decrease in mobility of node and routing overheads. In EEPR algorithm information related to coordinate’s prioritization, forwarding packets related to kind of traffic, node’s pause time, least requirement for redesigning EEPR algorithm. Hence, few request for path is forwarded to network which ultimately results in reduction in routing overheads.
4.4 Average EED
This section describes about comparison of EEPR and QRPL with respect to EED. EED is average time required by the packets to attain their destination. In simulation, node’s maximum speed is fix to 25 m/s and count of node fix to 100.
4.4.1 Average EED vs Node’s Maximum Speed
For simulation, pause time is fix to 1 s. As illustrated in Fig. 6, node’s maximum speed gets increased with increase in EED for both algorithms. This is dynamic effect of network topology and rate of breakdown of path. Hence, average EED of EEPR is lower than existing QRPL.
4.4.2 Average EED vs Node’s Pause Time
As illustrated in Fig. 7, Node’s pause time increase with decrease in dynamic network which makes network more stable. Hence, there is no necessity for rerouting. Due to scheduling and prioritization of forwarding packets in EEPR, delay reduction are more visible.
4.4.3 Average EED vs Count of Nodes
In Fig. 8, comparison is done between average EED and count of nodes. With increase in count of nodes won’t has prominent effect on EED when compared with other parameters? Therefore increase in network density and count of nodes decreases EED for both EEPR and QRPL. This is because of increase in count of path among destination and source, and choosing auxiliary node.
5 Conclusion
In general, the IoT applications utilizes more bandwidth and results in traffic congestion in the network core. In IoT system, packet routing from source to destination is a challenging task, particularly in dense crowded platform. With increasing IoT devices, consumption of energy had become critical problem. To overcome this problem, here in this research a new RPL dependent technique was proposed to reduce energy consumption by IoT device. In our method, QoS of IoT application is considered, where time slot TDMA us utilized to synchronize between receiver and sender to minimize consumption of energy. Then trickle timer is sued to control DODAG routing topology. Evaluation was performed with NS2 to make comparison between EEPR and QRPL with respect to EED, routing overheads and energy consumption. Experimental result depicts that EEPR using TDMA minimize energy consumption and EED for choosing communication nodes in IoT network. In future, proposed EEPR is planned to apply on vehicular network. Moreover, planned to use meta-heuristic algorithm to control transferring frames to route nodes in IoT system.
References
Witkowski, K. (2017). Internet of things, big data, industry 4.0–innovative solutions in logistics and supply chains management. Procedia Engineering, 182, 763–769.
Kotb, Y., Al Ridhawi, I., Aloqaily, M., Baker, T., Jararweh, Y., & Tawfik, H. (2019). Cloud-based multi-agent cooperation for IoT devices using workflow-nets. Journal of Grid Computing, 17, 625–650.
Al Ridhawi, I., Kotb, Y., Aloqaily, M., Jararweh, Y., & Baker, T. (2019). A profitable and energy-efficient cooperative fog solution for IoT services. IEEE Transactions on Industrial Informatics, 16, 3578–3586.
Souri, A., Hussien, A., Hoseyninezhad, M., & Norouzi, M. (2019). A systematic review of IoT communication strategies for an efficient smart environment. Transactions on Emerging Telecommunications Technologies, p. e3736
Kharrufa, H., Al-Kashoash, H. A., & Kemp, A. H. (2019). RPL-based routing protocols in IoT applications: A Review. IEEE Sensors Journal, 19, 5952–5967.
Zikria, Y. B., Afzal, M. K., Ishmanov, F., Kim, S. W., & Yu, H. (2018). A survey on routing protocols supported by the Contiki Internet of things operating system. Future Generation Computer Systems, 82, 200–219.
Salameh, H. B., Otoum, S., Aloqaily, M., Derbas, R., Al Ridhawi, I., & Jararweh, Y. (2020). Intelligent jamming-aware routing in multi-hop IoT-based opportunistic cognitive radio networks. Ad Hoc Networks, 98, 102035.
Aloqaily, M., Al Ridhawi, I., Salameh, H. B., & Jararweh, Y. (2019). Data and service management in densely crowded environments: Challenges, opportunities, and recent developments. IEEE Communications Magazine, 57, 81–87
Al Ridhawi, I., Aloqaily, M., & Boukerche, A.(2019). Comparing fog solutions for energy efficiency in wireless networks: Challenges and opportunities. IEEE Wireless Communications, 26, 80–86
Balasubramanian, V., Otoum, S., Aloqaily, M., Al Ridhawi, I., & Jararweh, Y. (2020). Low-latency vehicular edge: A vehicular infrastructure model for 5G. Simulation Modelling Practice and Theory, 98, 101968.
Souri, A., & Norouzi, M. (2019). A state-of-the-art survey on formal verification of the internet of things applications. Journal of Service Science Research, 11, 47–67.
Tomić, I., & McCann, J. A. (2017). A survey of potential security issues in existing wireless sensor network protocols. IEEE Internet of Things Journal, 4, 1910–1923.
Vaiyapuri, T., Parvathy, V. S., Manikandan, V., Krishnaraj, N., Gupta, D., & Shankar, K. (2021). A novel hybrid optimization for cluster‐based routing protocol in information-centric wireless sensor networks for IoT based mobile edge computing. Wireless Personal Communications, pp. 1–24
Yahiaoui, S., Omar, M., Bouabdallah, A., Natalizio, E., & Challal, Y. (2018). An energy efficient and QoS aware routing protocol for wireless sensor and actuator networks. AEU-International Journal of Electronics and Communications, 83, 193–203.
Raoof, A., Matrawy, A., & Lung, C.-H. (2018). Routing attacks and mitigation methods for RPL-based Internet of Things. IEEE Communications Surveys and Tutorials, 21, 1582–1606.
Souri, A., Navimipour, N. J., & Rahmani, A. M. (2018). Formal verification approaches and standards in the cloud computing: A comprehensive and systematic review. Computer Standards and Interfaces, 58, 1–22.
Kumar, M., Azad, M., & Agrawal, N. (2019). Comparative analysis of tree-based data aggregation protocols to maximize lifetime of wireless sensor networks. Pervasive computing: A networking perspective and future directions (pp. 153–163). Springer.
Ambigavathi, M., & Sridharan, D. (2018). Energy-aware data aggregation techniques in wireless sensor network. Advances in power systems and energy management (pp. 165–173). Springer.
Gilbert, E. P. K., Kaliaperumal, B., Rajsingh, E. B., & Lydia, M. (2018). Trust based data prediction, aggregation and reconstruction using compressed sensing for clustered wireless sensor networks. Computers and Electrical Engineering, 72, 894–909.
Petrovic, D., Shah, R. C., Ramchandran, K., & Rabaey, J. (2003). Data funneling: Routing with aggregation and compression for wireless sensor networks. Proceedings of the First IEEE International Workshop on Sensor Network Protocols and Applications, 2003, 156–162.
Mazumdar, N., Nag, A., & Nandi, S. (2021). HDDS: Hierarchical Data Dissemination Strategy for energy optimization in dynamic wireless sensor network under harsh environments. Ad Hoc Networks, 111, 102348.
Wang, S., Yu, J., Atiquzzaman, M., Chen, H., & Ni, L. (2018). CRPD: A novel clustering routing protocol for dynamic wireless sensor networks. Personal and Ubiquitous Computing, 22, 545–559.
Han, Z., Li, Y., & Li, J. (2018). A novel routing algorithm for IoT cloud based on hash offset tree. Future Generation Computer Systems, 86, 456–463.
Baker, T., Al-Dawsari, B., Tawfik, H., Reid, D., & Ngoko, Y. (2015). GreeDi: An energy efficient routing algorithm for big data on cloud. Ad Hoc Networks, 35, 83–96.
Yan, S., & Chung, Y. (2020). Improved ad hoc on-demand distance vector routing (AODV) protocol based on blockchain node detection in ad hoc networks. International Journal of Internet, Broadcasting and Communication, 12, 46–55.
Jin, Y., Raza, U., Aijaz, A., Sooriyabandara, M., & Gormus, S. (2017). Content centric cross-layer scheduling for industrial IoT applications using 6TiSCH. IEEE Access, 6, 234–244.
Dhumane, A. V., & Prasad, R. S. (2019). Multi-objective fractional gravitational search algorithm for energy efficient routing in IoT. Wireless networks, 25, 399–413.
Preeth, S. S. L., Dhanalakshmi, R., Kumar, R., & Shakeel, P. M. (2018). An adaptive fuzzy rule based energy efficient clustering and immune-inspired routing protocol for WSN-assisted IoT system. Journal of Ambient Intelligence and Humanized Computing, 624, 1–13.
Wang, Y., & Wang, Z. (2019). Routing algorithm of energy efficient wireless sensor network based on partial energy level. Cluster computing, 22, 8629–8638.
Yuan, P., Wang, Y., Su, M., Yang, Z., & Zhang, Q. (2019). Markov decision process-based routing algorithm in hybrid Satellites/UAVs disruption-tolerant sensing networks. IET Communications, 13, 1415–1424.
Gara, F., Saad, L. B., Ayed, R. B., & Tourancheau, B. (2019). A new scheme for RPL to handle mobility in wireless sensor networks. International Journal of Ad Hoc and Ubiquitous Computing, 30, 173–186.
Mohamed, B., & Mohamed, F. (2015). QoS routing RPL for low power and lossy networks. International Journal of Distributed Sensor Networks, 11, 971545.
Funding
This research work was not funded by any organization/institute/agency.
Author information
Authors and Affiliations
Contributions
I Am Saumya Raj Hereby State That The Manuscript Title Entitled “Routing Protocol for Low Power and Lossy Network using Energy Efficient Priority Based Routing” Submitted To Wireless Personal Communications, I and my Co-author R. Rajesh Confirm That This Work Is Original And Has Not Been Published Elsewhere, Nor Is It Currently Under Consideration For Publication Elsewhere. And I Am Research Scholar in Bharathiar University, Coimbatore, India.
Corresponding author
Ethics declarations
Conflict of interest
I confirm that this work is original and has either not been published elsewhere, or is currently under consideration for publication elsewhere.
Competing Interests
None of the authors have any competing interests in the manuscript.
Availability of Data and Material
Not applicable.
Code Availability
Not applicable.
Consent to Participate
I confirm that any participants (or their guardians if unable to give informed consent, or next of kin, if deceased) who may be identifiable through the manuscript (such as a case report), have been given an opportunity to review the final manuscript and have provided written consent to publish.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Raj, S., Rajesh, R. Routing Protocol for Low Power and Lossy Network Using Energy Efficient Priority Based Routing. Wireless Pers Commun 123, 1379–1394 (2022). https://doi.org/10.1007/s11277-021-09185-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-09185-6