Abstract
The use of wireless transmission networks in various environments has become widespread. One of the main challenges in wireless networks is that the wireless transmission is highly vulnerable to eavesdropping attacks. In this paper, an amplify-and-forward cooperative relaying wireless system with relay selection is considered to improve the physical layer (PHY) security of the wireless system in the presence of multiple eavesdroppers, under two cases, namely, perfect channel state information (CSI) and outdated CSI cases. To evaluate the PHY security of the system, we derive closed-form expressions for the PHY security performance metrics, including the probability of non-zero secrecy capacity, the average secrecy capacity, and the secrecy outage probability. Then using those expressions, we obtain several numerical results under system parameters. The results show that relay selection provides significant improvement in the PHY security of the system. Moreover, it is observed that, when the CSI used to select the best relay is outdated, the PHY secrecy performance is relatively inferior compared to that of the perfect CSI case. Finally, the obtained mathematical expressions are also validated using Monte-Carlo simulation.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Wireless networking has become an essential part of our daily life and is widely used in different applications. One of the major challenges of wireless networks is that the transmission between legitimate users can easily be overheard by eavesdroppers due to the broadcast nature of the wireless communication and is highly vulnerable to eavesdropping attacks. In order to increase the security of signal transmission, existing communication systems typically use encryption techniques to prevent eavesdropping attacks on transferring data between legitimate users. However, encryption protocols face several challenges due to the rapid growth of computing systems.
Recently, physical layer (PHY) security methods have been considered as an efficient way to overcome the problems caused by eavesdropping attacks. These methods are usually considered as the alternative and complement methods to create security in wireless communications using the physical properties of the wireless channel. The basis of the physical layer security scheme is the information theoretic approach, which is based on Shannon complete security concepts [1]. The concept of physical layer security was first proposed by Wyner with examining the memoryless wiretap channels [2]. In the considered system, two legitimate users communicate with each other via a main channel, in the presence of an eavesdropper that has access to the reduced version of the channel authorized for the legitimate receivers. Then, the memoryless wiretap channel model proposed by Wyner were extended to the Gaussian wiretap channel and the secrecy capacity concept was introduced [3]. The secrecy capacity is defined as the difference between main channel capacity and wiretap channel capacity. Accordingly, secure communication is not possible unless the signal-to-noise ratio (SNR) of the main channel is higher than that of the wiretap channel. To improve the secrecy capacity of the system, it is desirable to introduce a technique which causes an increase in the capacity of the main channel, and/or a decrease in the channel capacity of wiretap channel. To this end, several theoretical and practical research works have been reported for improving the physical layer security of digital communication systems, in which some effective approaches have been proposed such as modulation, channel coding and diversity methods, cooperative relaying, space-time coding, and multiple-input multiple-output (MIMO) methods [4,5,6,7,8,9,10,11,12,13,14,15,16]. In several research works, the PHY security performances of a direct communication system have been evaluated, in which a source transmits information to the destination while single or multiple eavesdroppers were able to receive the information [17, 18]. On the other hand, it has been shown that cooperative networks with AF relay selection have better system performances than direct communication networks (non-cooperative communications) and the average SNR gain is increased with the number of available relays [19, 20]. Therefore, the concept of relay selection in AF relaying systems can also improve the PHY secrecy performance of the system. It was shown that the security in multicasting through generalized fading channels can be improved with the best relay selection [21].
The performances of cooperative communications with opportunistic relaying have been examined with a perfect channel state information (CSI) in [22] and [23]. However, in time-variable environments, the CSI used for the relay selection, at the moment of selection may be different from the CSI at the moment of signal transmission. Therefore, relay selection based on the outdated CSI can yield a decrease in the performance of opportunistic relay selection [10, 24,25,26]. For example, in [26], authors have analyzed the Shannon capacity of the opportunistic relaying technique in amplify-and-forward cooperative systems over Rayleigh fading channels under outdated channel information. They have evaluated the effects of outdated channel information on the channel capacity and the outage performance. In [9], the secrecy performance has been evaluated for a cooperative transmission in a dual-hop MIMO relay system using a combined transmit antenna selection (TAS) and maximum ratio combining (MRC) scheme, denoted TAS/MRC scheme, over the Nakagami-m fading channels. The secrecy performance of the TAS/MRC scheme is then evaluated and the impacts of outdated CSI have been studied using the numerical results obtained from closed-form expressions of exact ergodic secrecy rate and exact secrecy outage probability. In [27], the impact of imperfect CSI on the PHY secrecy performance of a space time block coded MIMO system is evaluated over Rician fading wiretap channel, showing the advantages of using MIMO system, with respect to the PHY security.
In this paper, we analyze and evaluate the PHY secrecy performance of a cooperative network with multiple AF relays, in which to improve the physical layer security, an opportunistic relay selection is employed in the presence of multiple eavesdroppers. The main contributions of this paper are summarized as follows: (1) We obtain mathematical expressions for three important PHY security performance criteria: the probability of non-zero secrecy capacity, the secrecy outage probability, and the average secrecy capacity of the system. (2) Using the obtained expressions, we evaluate the secrecy performance of signal transmissions in the AF cooperative network. (3) We evaluate and analyze the physical layer security of AF cooperative relaying systems with relay selection under outdated CSI in the presence of multiple eavesdroppers. We also examine the effects of outdated channel information for relay selection using mathematical expressions, obtained for the probability of non-zero secrecy capacity, the secrecy outage probability, and the average secrecy capacity of the system. The validity of the obtained mathematical expressions are also verified using Monte-Carlo simulation.
The rest of this paper is organized as follows: Section 2 presents the system model and the assumptions. In Sect. 3, the PHY secrecy performance analyses of the system are presented and closed-form expressions are derived for the probability of non-zero secrecy capacity, the secrecy outage probability, and the average secrecy capacity of the system, where the analysis of the system under outdated CSI is given in Sect. 4. In Sect. 5, several numerical evaluation results which are verified by computer simulations are presented and discussed. Finally, concluding remarks are given in Sect. 6.
2 System model
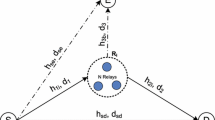
We consider a cooperative communication system over Rayleigh fading channel shown in Fig. 1. The source (S) communicates with the desired receiver (D) through N AF relays \(\mathrm {R}_{1},\mathrm {R}_{2},\cdots ,\mathrm {R}_{\mathrm {N}}\), in the presence of multiple eavesdroppers \(\mathrm {E}_{1},\mathrm {E}_{2},\cdots ,\mathrm {E}_{\mathrm {K}}\). The main channel consists of \(\mathrm {S} \rightarrow \mathrm {D}\) link and \(\mathrm {S}\rightarrow \mathrm {R}_{\mathrm {n}} \rightarrow \mathrm {D}\) links (\(n=1,\cdots ,N\)), and the wiretap channel consists of \(\mathrm {S} \rightarrow \mathrm {E}_{\mathrm {k}}\) links (\(k=1,\cdots ,K\)), and \(\mathrm {R}_{\mathrm {n}} \rightarrow \mathrm {E}_{\mathrm {k}}\) links. In the first time-slot, the received signals for \(\mathrm {S} \rightarrow \mathrm {D}\) link in terminal \(\mathrm {D}\), \(\mathrm {S} \rightarrow \mathrm {R}_{\mathrm {n}}\) link in \(\mathrm {R}_{\mathrm {n}}\) and \(\mathrm {S} \rightarrow \mathrm {E}_{\mathrm {k}}\) link in \(\mathrm {E}_{\mathrm {k}}\) can be respectively written as:
where \(P_s\) denotes the source transmit power, \(\alpha \) is the path loss exponent. \(d_{SD}\), \(d_{SR_n}\), and \(d_{SE_k}\) are the distances of \(\mathrm {S}\) from \(\mathrm {D}\), from n-th relay (\(\mathrm {R}_{\mathrm {n}}\)) and from k-th eavesdropper (\(\mathrm {E}_{\mathrm {k}}\)), respectively, \(h_{SD}\), \(h_{SR_n}\) and \(h_{SE_k}\) are the fading coefficients of \(\mathrm {S}\rightarrow \mathrm {D}\), \(\mathrm {S}\rightarrow \mathrm {R}_{\mathrm {n}}\) and \(\mathrm {S}\rightarrow \mathrm {E}_{\mathrm {k}}\) links, respectively, and s is the normalized information signal in \(\mathrm {S}\) terminal with \(\mathcal {E}[|s|^2]=1\), where \(\mathcal {E}(\cdot )\) is the expectation operation. The parameters \(n_{SD}\), \(n_{SR_n}\) and \(n_{SE_k}\) are zero mean additive white Gaussian noises (AWGN) in \(\mathrm {D}\) terminal with variance \(\sigma _{SD}^2\), in relay \(\mathrm {R}_{\mathrm {n}}\) with variance \(\sigma _{SR_n}^2\), and in \(\mathrm {E}_{\mathrm {k}}\) with variance \(\sigma _{SE_k}^2\), respectively. From (1), (2) and (3), the channels’ SNRs can respectively be written as
In the second time-slot, the received signal for \(\mathrm {R}_{\mathrm {n}}\rightarrow \mathrm {D}\) and \(\mathrm {R}_{\mathrm {n}}\rightarrow \mathrm {E}_{\mathrm {k}}\) links are given by
and
where \(G_n\) is n-th relay amplification coefficient that is equal to \(G_n=\sqrt{\frac{P_s}{\frac{P_s}{d_{SR_n}^{\alpha }}|h_{SR_n}|^2+\sigma _{SR_n}^2}}\) and \(d_{R_nD}\) and \(d_{R_nE_k}\) are the distances of \(\mathrm {R}_{\mathrm {n}}\) from \(\mathrm {D}\) and \(\mathrm {E}_{\mathrm {k}}\), respectively. The parameters \(h_{R_nD}\) and \(h_{R_nE_k}\) parameters are the fading coefficients of \(\mathrm {R}_{\mathrm {n}}\rightarrow \mathrm {D}\) and \(\mathrm {R}_{\mathrm {n}}\rightarrow \mathrm {E}_{{\mathrm {k}}}\), respectively, and the parameters \(n_{R_nD}\) and \(n_{R_nE_k}\) parameters are zero mean additive white Gaussian noise (AWGN) in \(\mathrm {D}\) terminal with variance \(\sigma _{R_nD}^2\), in \(\mathrm {R}_{\mathrm {n}}\) with variance \(\sigma _{SR_n}^2\) and in \(\mathrm {E}_{\mathrm {k}}\) with variance \(\sigma _{R_nE_k}^2\), respectively. The SNRs of the channels can be respectively expressed as:
The relay selection algorithm selects the best relay (b) such that
where \(\mathcal {R}=\{1,2, \cdots ,N\}\) and \(\gamma _{SR_nD}\) is the SNR of \(\mathrm {S}\rightarrow \mathrm {R}_{\mathrm {n}} \rightarrow \mathrm {D}\) channel. The SNR \(\gamma _{SR_nD}\) can be written as [19, 20]:
For the sake of simplicity, we consider an upper bound for the equivalent SNR as the approximate SNR that is given by [19]
This approximation has been widely used in the literature and has shown to be tight enough especially at medium to high SNR values [19, 28, 29]. Moreover, in Sect. 4, simulation results have been provided to show the validity of the use this approximation in this work.
Therefor, the SNR of the best relay link \(\mathrm {S}\rightarrow \mathrm {R}_{\mathrm {b}}\rightarrow \mathrm {D}\) can be expressed as:
Since the main channel consists of \(\mathrm {S \rightarrow D}\) and \(\mathrm {S} \rightarrow \mathrm {R}_{\mathrm {n}} \rightarrow \mathrm {D}\) links, then, due to the maximum ratio combining (MRC) used at terminal \(\mathrm {D}\), the main channel’s SNR can be written as:
Since eavesdroppers do not know the channel information of \(\mathrm {S} \rightarrow \mathrm {R}_{\mathrm {n}}\), then the wiretap channel consists of \(\mathrm {S} \rightarrow \mathrm {E}_{\mathrm {k}}\) and \(\mathrm {R}_{\mathrm {n}} \rightarrow \mathrm {E}_{\mathrm {k}}\) links. Therefor, using MRC at k-th eavesdropper receiver, the SNR of k-th wiretap channel can be written as
In addition, the SNR of the wiretap channel for multiple eavesdroppers can be obtained from [18]:
In the following, we express the probability density function (PDF) and cumulative distribution function (CDF) for the main channel’s SNR as well as for the wiretap channel’s SNR, which enable us to obtain and derive closed-form expressions for the probability of non-zero secrecy capacity, the outage probability and the average secrecy capacity of the considered system.
As shown in [19], the PDF and CDF of the main channel’s SNR are respectively given by:
and
where \(\overline{\gamma }_{SR_n}=\overline{\gamma }_{R_nD}=\overline{\gamma }\) and \(\overline{\gamma }_C=\frac{\overline{\gamma }_{SR_n}\overline{\gamma }_{R_nD}}{\overline{\gamma }_{SR_n}+\overline{\gamma }_{R_nD}}\).
On the other hand, similarly to the approach in [30], we can express the CDF and PDF for the k-th eavesdropper as:
and
where \(\overline{\gamma }_{SE_k}=\overline{\gamma }_{SE}\) and \(\overline{\gamma }_{R_nE_k}=\overline{\gamma }_{RE}\).
According to (17), the wiretap channel’s SNR is given by \(\gamma _W=\max \limits _{k \in \{1, \dots , K\}} \{\gamma _{W_k}\}\). Therefore, using the order statistic theory [31], the CDF of \(\gamma _W\) can be obtained from \(F_{\gamma _{W}}(y)=[F_{\gamma _{W_k}}(y)]^K\), and using (20), we obtain:
Employing the binomial expansions that are \((1+x)^K=\sum _{i=0}^{K}\displaystyle {K\atopwithdelims ()i} x^i\), and \((1-x)^K=\sum _{i=0}^{K}\displaystyle {K\atopwithdelims ()i} (-1)^i\, x^i\), the expression in (23) can be written as:
Using the fact that \(f_{\gamma _W}(y)=\frac{d}{dy}F_{\gamma _W}(y)\), by obtaining the derivative of (23), the probability density function of the wiretap channel’s SNR can be expressed as
3 Secrecy performance analysis
In the scenarios where the eavesdropper is passive, the CSI of the eavesdroppers and the intended receiver are not available at the source terminal, hence perfect secrecy is not guaranteed. In this Section, we analyze the PHY secrecy performance of the considered system. Considering the AF relaying system shown in Fig. 1, and using the definition of the capacity of additive white Gaussian noise (AWGN) channels, with SNRs \({\gamma }_\mathrm{_M}\) and \({\gamma }_\mathrm{_W}\), we can express the channel capacity of the main channel \(C_M\) and that of the wiretap channel \(C_W\) as \(C_M=\frac{1}{2}\log _2(1+\gamma _M)\) and \(C_W=\frac{1}{2}\log _2(1+\gamma _W)\), respectively. Hence, the instantaneous secrecy capacity can be written as
where the coefficient of 1/2 is due to the fact that transmission in AF relaying system is done in two time-slots.
3.1 Probability of non-zero secrecy capacity (PNZSC)
According to the definition of the instantaneous secrecy capacity in (25), when \(\gamma _M> \gamma _W\), the secrecy capacity is positive and when \(\gamma _M\le \gamma _W\), the secrecy capacity is zero. Thus, since \(\gamma _M\) and \(\gamma _W\) are statistically independent, the probability of non-zero secrecy capacity can be expressed as
By inserting (18) and (24) into (26) and solving the integrals, we obtain the following expression
3.2 Secrecy outage probability (SOP)
An important performance measure for evaluating the PHY secrecy is the secrecy outage probability denoted \(P_{out}(R_s)\). The secrecy outage probability is a probability that the secrecy capacity is lower than the threshold of \(R_s\), and can be written as [17]:
According to the expression in (25), for \(\gamma _M\le \gamma _W\), \(C_s=0\), and since \(R_s>0\), we can readily conclude that \(\Pr (C_s<R_s|\gamma _M\le \gamma _W)=1\). Also, we can write \(\Pr (\gamma _M\le \gamma _W)=1-\Pr (\gamma _M>\gamma _W)\). Therefore, using (25), the secrecy outage probability in (28) can be written as:
where assuming \(\mu \triangleq \left[ 2^{2R_s}(1+\gamma _W)-1\right] \), the expression in (29) can be written as
Assuming \(\lambda =2^{2R_s}\), we solve the inner integral in (30) as follows:
By inserting (19) and (24) into (31) and solving the integral, we obtain the closed-form expression of the secrecy outage probability as follows
3.3 Average secrecy capacity (ASC)
The average secrecy capacity can be obtained by averaging the instantaneous secrecy capacity over the joint PDF of \((\gamma _M, \gamma _W)\), where assuming \(\gamma _M\) and \(\gamma _W\) are statistically independent, it can be expressed as [18]:
By inserting (25) in above equation, we obtain
where
By inserting (18) and (23) in above equation, and solving the integral, we get
Using \(\int _{0}^{\infty }\ln (1+x)\exp (-\mu x)\,\mathrm {d}x=\frac{1}{\mu }\exp (\mu )E_1(\mu )\), we obtain the solution of integral, which yields:
Similarly, in (34), we have
By inserting (19) and (24) in above equation, and solving the integral, we get
By solving above integral, we obtain:
Substituting expressions of \(I_1\) given in (37) and \(I_2\) given in (40) into (34), we obtain the following closed-form expression for the average secrecy capacity:
4 Secrecy performance of the system under outdated CSI
In practice, in the AF system with relay selection, the CSI of \(\mathrm {S} \rightarrow \mathrm {R}_{\mathrm {n}} \rightarrow \mathrm {D}\) link, used for relay selection at the decision time t, may differ from its value at the signal transmission time \(t+\tau \). This difference can be due to several factors such as channel variations with time, feedback delay and the channel estimation errors. In other words, the best relay selected according to the outdated CSI at time t may not be the best relay at the time of the data transmission (time \(t+\tau \)). Therefore, it is of interest to evaluate the effects of outdated CSI on the secrecy performance of the system. In the outdated CSI scenario, in general, we have an estimate of the channel h denoted \(\widehat{ h }\), defined by the following model:
where \(\widehat{h}\) is the estimate of the channel h, and \(\epsilon \) is a complex Gaussian noise \(\mathcal {CN}(0, \sigma ^2_h)\). The correlation coefficient \(\rho \), \(0 \le \rho \le 1\) is a constant value which determines the average quality of the channel estimation. That model is a widely used model in the literature, which models the effects of outdated CSI and imperfect CSI [32].
In this Section, we evaluate and analyze the impacts of outdated CSI on the PHY secrecy of considered AF relaying system. To that end, we obtain closed-form expressions for the probability of non-zero secrecy capacity, the secrecy outage probability, and the average secrecy capacity average of the system under outdated CSI. Then using numerical evaluations, we study and evaluate the impacts of outdated CSI on the secrecy performance of the system. According to [20], for the AF cooperative system with relay selection under outdated CSI, the probability density function and the cumulative distribution function of the main channel’s SNR are given by:
and
where \(\rho \) is the correlation coefficient between the SNR of \(\mathrm {S}\rightarrow \mathrm {R}_{\mathrm {n}} \rightarrow \mathrm {D}\) link, at time t and the SNR of \(\mathrm {S}\rightarrow \mathrm {R}_{\mathrm {n}} \rightarrow \mathrm {D}\) link at time \(t+\tau \), where \(0\le \rho \le 1\) [20]. In fact, there is two extreme cases, where \(\rho =1\) corresponds to a perfect CSI case and \(\rho =0\) corresponds to a completely outdated CSI case. It is also worthy to notify that for the wiretap channel’s SNR, the PDF and CDF expressions are the same as those given in expressions (23) and (24).
4.1 Probability of non-zero secrecy capacity under outdated CSI
Similarly to the steps shown in Sect. 3, the expression for the probability of non-zero secrecy capacity under outdated CSI can be obtained from:
By substituting (43) and (23) into (45), we obtain:
We solve the integrals in (46), and we obtain a closed-form expression for probability of non-zero secrecy capacity, as follows:
4.2 Secrecy Outage Probability under Outdated CSI
Similarly to the steps followed in Section 3, the expression for the secrecy outage probability of the system under outdated CSI can be obtained from:
where \(\lambda =2^{2R_s}\). Substituting (44) and (24) into (48) yields:
Solving the integrals in (49), yields the closed-form expression for the secrecy outage probability of the system under outdated CSI, which can be written as
4.3 Average secrecy capacity under outdated CSI
The expression for the average secrecy of the system under outdated CSI can be obtained following similar steps given in Section 3 (using (34)), which can be written as
By inserting (43), (44), (23) and (24) into (51) and using \(\int _{0}^{\infty }\ln (1+x)\exp (-\mu x)\,\mathrm {d}x=\frac{1}{\mu }\exp (\mu )E_1(\mu )\), we solve the integrals and we obtain the following expression for the average secrecy capacity:
It is worthy to mention that, considering \(\rho =1\) (which corresponds to the perfect CSI), expressions (47), (50) and (52), reduce to the expressions (27), (32) and (41), which were obtained for the perfect CSI case in Sect. 3. In other extreme case, setting \(\rho =0\) (which corresponds to the completely outdated CSI), into expressions (47), (50) and (52) yield the corresponding expressions for the PHY secrecy of AF relaying system with one relay in the presence of multiple eavesdroppers. This implies that under completely outdated CSI, relay selection is equivalent to the random relay selection, where no diversity advantage can be achieved from using multiple relays.
5 Simulation and numerical results
In this section, we provide numerical and simulation results for three important PHY secrecy performance metrics for the considered AF relaying system, namely, the probability of non-zero secrecy capacity, the secrecy outage probability and the average secrecy capacity under different parameters. Numerical results are obtained from derived expressions (27), (32), (41), (47), (50) and (52), where to verify the validity of the numerical results and the analysis, we also provide Monte-Carlo simulation results. We considered the path loss for the channel to be \(\alpha =0\) in all Figures. We also assumed that the links corresponding to the main channel have the same average SNR values, i.e., \(\overline{\gamma }_{SD}=\overline{\gamma }_{SR_n}=\overline{\gamma }_{R_nD}\), for \(n=1,2,\cdots ,N\), but the SNRs associated to the eavesdroppers \(\overline{\gamma }_{SE}\) and \(\overline{\gamma }_{RE}\) may have different SNR values.
The simulation results are obtained as follows: First, using Monte Carlo simulations, we generate several realizations of the random Rayleigh distributed channel coefficients. For the outdated CSI case, we use the formula described in (42), in which we first generate several realizations of the random Rayleigh distributed channel coefficients h, and generate \(\epsilon \) that is a complex Gaussian noise \(\mathcal {CN}(0, \sigma ^2_h)\), then we obtain outdated channel coefficient \(\widehat{h}\). We then, calculate instant SNR values for each time-slot, i.e.. the values for \({\gamma }_{SD}\), \({\gamma }_{SR_n}\), \({\gamma }_{R_nD}\), the SNRs associated to the eavesdroppers \({\gamma }_{SE}\), and \({\gamma }_{RE}\). Then, we obtain the instant SNR values for \({\gamma }_{_M}\), and \({\gamma }_{_W}\) using (15) and (17). Then, using (25), we obtain several instantaneous values for the secrecy capacity \(\mathcal {C}_{s}\). Finally, for the given system parameters, defined for each figure, and using the obtained several realizations of the secrecy capacity, the average secrecy capacity (ASC), and the probability of non-zero secrecy capacity (PNZSC), the secrecy outage probability (SOP) are calculated for a total number larger than \(10^7\) channel realizations, where \(\mathrm{ASC}=\texttt {mean}(C_s)\), \({PNZSC}=\mathrm{Pr}\left( {C}_{s}>0\right) \), and \(\mathcal {P}_{out}(R_s)=\mathrm{Pr}\left( {C}_{s}\le R_s\right) \), have been used.
Fig. 2 shows the probability of non-zero secrecy capacity versus \(\overline{\gamma }_{SD}\), for the system assuming \(N=5\) relays and \(K=5\) eavesdroppers. We observe that increasing \(\overline{\gamma }_{SD}\), yields an increase in the probability non-zero secrecy capacity. Also, we can observe that increasing \(\overline{\gamma }_{SE}\) and/or \(\overline{\gamma }_{RE}\) cause a decrease in the probability of non-zero secrecy capacity, as expected.
Fig. 3 shows the secrecy outage probability versus \(\overline{\gamma }_{SD}\) for the system with \(N=5\) relays and \(K=5\) eavesdroppers and \(R_s=0.1\) bits/s/Hz. We observe that increasing \(\overline{\gamma }_{SD}\), decreases the secrecy outage probability. We also observe that increasing \(\overline{\gamma }_{SE}\) and \(\overline{\gamma }_{RE}\) increases the secrecy outage probability of the system.
Fig. 4 shows the secrecy outage probability versus \(\overline{\gamma }_{SD}\) with \(\overline{\gamma }_{SE}=5\) dB, \(\overline{\gamma }_{RE}=10\) dB, \(K=5\) eavesdroppers and \(R_s=0.1\) bits/s/Hz, for different number of relays N. It can be observed that, increasing the number of available relays, decreases the secrecy outage probability. To show the tightness of the upper bound approximation SNR, the SOP results are obtained for both cases of the upper bound approximate SNR \(\gamma _{SR_nD}=\min (\gamma _{SR_n},\gamma _{R_nD})\) and the exact SNR expression \(\gamma _{SR_nD}=\frac{\gamma _{SR_n}\gamma _{R_nD}}{1+\gamma _{SR_n}+\gamma _{R_nD}}\), which is obtained via simulations. We observe that the approximate results are tight enough to the exact results, especially at the medium to high SNRs.
Fig. 5 shows the secrecy outage probability versus \(R_s\) with \(N=K=5\), \(\overline{\gamma }_{SE}=0\) dB and \(\overline{\gamma }_{RE}=5\) dB. We observe that increasing \(R_s\), increases the secrecy outage probability. Also we can see that increasing \(\overline{\gamma }_{SE}\) and \(\overline{\gamma }_{RE}\) increases the secrecy outage probability.
The secrecy outage probability versus \(\overline{\gamma }_{SD}\) is shown in Fig. 6, where it is assumed that \(K=5\), \(R_s=0.1\) bits/s/Hz, \(\overline{\gamma }_{SE}=0\) dB and \(\overline{\gamma }_{RE}=5\) dB. It can be observed that increasing the number of available relays decreases the secrecy outage probability and therefore, the physical layer security is significantly improved.
The secrecy outage probability versus N and K, are shown in Fig. 7 and Fig. 8, respectively, where \(R_s=0.1\) bits/s/Hz and \(\overline{\gamma }_{SD}=20\) dB are assumed. We observe that increasing N the number of relays, decreases the secrecy outage probability. It is also observed that the secrecy outage probability increases with the number of eavesdroppers.
Fig. 9 and Fig. 10 show the average secrecy capacity. We observe that increasing \(\overline{\gamma }_{SD}\) and/or N, increases the average secrecy capacity. Also, it can be observed that increasing \(\overline{\gamma }_{SE}\) and \(\overline{\gamma }_{RE}\) decreases the average secrecy capacity.
In Fig. 2 to Fig. 10, the results are obtained assuming that the CSI used for relay selection is perfect. However, in the following, we provide the results of PHY secrecy performance under outdated CSI.
Fig. 11 shows the probability of non-zero secrecy capacity as a function of \(\overline{\gamma }_{SD}\), with \(N=5\) relays and \(K=3\) eavesdroppers. We observe that increasing \(\overline{\gamma }_{SD}\), increases the probability of non-zero secrecy capacity and also increasing \(\overline{\gamma }_{SE}\) and \(\overline{\gamma }_{RE}\), decreases the probability of non-zero secrecy capacity. Also, we can observe that decreasing \(\rho \) which corresponds to the case where CSI becomes more outdated, cause a decrease in the probability of non-zero secrecy capacity.
Fig. 12 and Fig. 13 show the secrecy outage probability versus \(\overline{\gamma }_{SD}\) for \(K=1\) and \(K=3\) eavesdroppers, respectively, and \(N=5\) relays, \(\overline{\gamma }_{SE}=0\) dB, \(\overline{\gamma }_{RE}=5\) dB and \(R_s=0.1\) bits/s/Hz for different value of \(\rho \). Increasing \(\overline{\gamma }_{SD}\), decreases the secrecy outage probability and increasing K, increases the secrecy outage probability. Also, it can be observed that increasing \(\rho \) decreases the secrecy outage probability. Moreover, it can be seen that for \(\rho =0\), the secrecy outage probability is equal to that of the considered AF relay system with one relay, indicating that with \(\rho =0\), no diversity advantage can be achieved from relay selection. In the other extreme case, with \(\rho =1\) (perfect CSI), the diversity order is equal to \(N+1\), as expected. For \(0\le \rho <1\) (outdated CSI), the outage probability curves have the same slope at high SNRs, implying that the diversity order in the outdated CSI is equal to 2 that is the diversity order of the AF relaying system with a single relay and \(\mathrm {S}\rightarrow \mathrm {D}\) direct channel.
In order to show the tightness of the upper bound approximation SNR \(\gamma _{SR_nD}\simeq \min (\gamma _{SR_n},\gamma _{R_nD})\) to the exact SNR expression \(\gamma _{SR_nD}=\frac{\gamma _{SR_n}\gamma _{R_nD}}{1+\gamma _{SR_n}+\gamma _{R_nD}}\), in Fig. 14, the simulation results for the secrecy outage probability versus \(\overline{\gamma }_{SD}\) are given assuming that \(\overline{\gamma }_{SE}=5\) dB, \(\overline{\gamma }_{RE}=10\) dB, \(K=5\) eavesdroppers and \(R_s=0.1\) bits/s/Hz, for different values of \(\rho \). We can see that the approximate results are tight enough to the exact results, especially at the medium to high SNR values.
Fig. 15 shows the secrecy outage probability versus N with \(\overline{\gamma }_{SD}=\overline{\gamma }_{SR_n}=\overline{\gamma }_{R_nD}=20\) dB, \(\overline{\gamma }_{SE}=0\) dB, \(\overline{\gamma }_{RE}=5\) dB and \(R_s=0.1\) bits/s/Hz. It can be seen that increasing K, causes an increase in the secrecy outage probability. Also, we can observe that increasing \(\rho \), decreases the secrecy outage probability. However, when \(\rho \) decreases to (\(\rho =0.5\)), the improvement in the secrecy outage probability due to the increasing of N, is small because of poor channel knowledge. Moreover, when \(\rho =0\), increasing N, the secrecy outage probability does not increase, since the system behaves similar to the AF relay system with one relay and \(\mathrm {S}\rightarrow \mathrm {D}\) direct link.
Fig. 16 shows the secrecy outage probability versus \(\rho \) with \(N=5\), \(K=3\), \(\overline{\gamma }_{SE}=0\) dB, \(\overline{\gamma }_{RE}=5\) dB and \(R_s=0.1\) bits/s/Hz. We observe that increasing \(\rho \), decreases the secrecy outage probability.
The average secrecy capacity versus \(\overline{\gamma }_{SD}\) is shown Fig. 17 with \(N=5\), \(K=3\), \(\overline{\gamma }_{SE}=0\) dB and \(\overline{\gamma }_{RE}=5\)dB . We observe that increasing \(\overline{\gamma }_{SD}\) and/or \(\rho \), increases the average secrecy capacity.
Fig. 18 shows the average secrecy capacity versus N with \(K=3\), \(\overline{\gamma }_{SE}=0\) dB and \(\overline{\gamma }_{RE}=5\) dB. We can observe that in the case of completely outdated CSI, \(\rho =0\), by increasing N, the average secrecy capacity does not change. This is the extreme case and implies that the relay selection based on the completely outdated CSI does not provide diversity to the system, as explained earlier.
In Fig. 2 to Fig. 18, it can be observed that the obtained numerical results obtained from theoretical mathematical formulas derived in this paper match closely with the simulation results, indicating the validity of the obtained mathematical expressions.
6 Conclusion
In this paper, we have analyzed and evaluated the PHY secrecy performance of an AF relaying system with relay selection under two cases, namely, perfect CSI and outdated CSI cases. We derived closed-form expressions for the probability of non-zero secrecy capacity, the average secrecy capacity and the secrecy outage probability. We provided numerical results to show the significant advantages of relay selection for improving the physical layer security. Moreover, we evaluated the effects of outdated CSI for relay selection on the physical layer security of the AF relaying cooperative communications systems with relay selection. It is observed that when the information used to select the relay is outdated, the PHY secrecy performance can be deteriorated. We also used Monte-Carlo simulation to verify the validity of the obtained mathematical expressions.
References
Shannon, C. E. (1949). Communication theory of secrecy systems. Bell system technical journal, 28(4), 656–715.
Wyner, A. D. (1975). The wire-tap channel. Bell system technical journal, 54(8), 1355–1387.
Leung-Yan-Cheong, S., & Hellman, M. (1978). The gaussian wire-tap channel. Information Theory, IEEE Transactions on, 24(451–456), 08.
Zou, Y., Zhu, J., Wang, X., & Leung, V. C. M. (2015). Improving physical-layer security in wireless communications using diversity techniques. IEEE Network, 29(1), 42–48.
Zou, Y., Zhu, J., Wang, X., & Hanzo, L. (2016). A survey on wireless security: Technical challenges, recent advances, and future trends. Proceedings of the IEEE, 104(9), 1727–1765.
Rawat, D. B., White, T., Parwez, M. S., Bajracharya, C., & Song, M. (2017). Evaluating secrecy outage of physical layer security in large-scale mimo wireless communications for cyber-physical systems. IEEE Internet of Things Journal, 4(6), 1987–1993.
He, B., Ni, Q., Chen, J., Yang, L., & Lv, L. (2018). User-pair selection in multiuser cooperative networks with an untrusted relay. IEEE Transactions on Vehicular Technology, 68(1), 869–882.
Harrison, W. K., Almeida, J., Bloch, M. R., McLaughlin, S. W., & Barros, J. (2013). Coding for secrecy: An overview of error-control coding techniques for physical-layer security. IEEE Signal Processing Magazine, 30(5), 41–50.
Zhao, R., Lin, H., He, Y.-C., Chen, D.-H., Huang, Y., & Yang, L. (2017). Secrecy performance of transmit antenna selection for mimo relay systems with outdated csi. IEEE Transactions on Communications, 66(2), 546–559.
Huang, Y., Al-Qahtani, F. S., Duong, T. Q., & Wang, J. (2015). Secure transmission in MIMO wiretap channels using general-order transmit antenna selection with outdated CSI. IEEE Transactions on Communications, 63(8), 2959–2971.
Melki, R., Noura, H. N., Mansour, M. M., & Chehab, A. (2020). Physical layer security schemes for MIMO systems: an overview. Wireless Networks, 26(3), 2089–2111.
BaghaeiPouri, A., & Torabi, M. (2019). Secrecy performance analysis of CIOD-OFDM systems over wireless fading channels. Wireless Networks, 1–14.
BaghaeiPouri, A., & Torabi, M. (2019). OFDM/OQAM transmission with improved physical layer security. Physical Communication, 36, 100787.
Mukherjee, A., Fakoorian, S. A. A., Huang, J., & Swindlehurst, A. L. (2014). Principles of physical layer security in multiuser wireless networks: A survey. IEEE Communications Surveys & Tutorials, 16(3), 1550–1573.
BaghaeiPouri, A., & Torabi, M. (2020). Physical layer security in space-time block codes from coordinate interleaved orthogonal design. IET Communications, 14(12), 2007–2017.
BaghaeiPouri, A., & Torabi, M. (2020). Analysis of secrecy outage performance of TAS-CIOD systems over wireless Rayleigh fading channels. Physical Communication, 101–129.
Barros, J., & Rodrigues, M. R. (2006). Secrecy capacity of wireless channels. In IEEE International Symposium on Information Theory, (pp. 356–360), IEEE.
Wang, P., Yu, G., & Zhang, Z. (2007). On the secrecy capacity of fading wireless channel with multiple eavesdroppers. In IEEE International Symposium on Information Theory, (pp. 1301–1305), IEEE.
Torabi, M., Ajib, W., & Haccoun, D. (2009). Performance analysis of amplify-and-forward cooperative networks with relay selection over rayleigh fading channels. In 69th IEEE Vehicular Technology Conference, VTC-Spring, (pp. 1–5), IEEE.
Torabi, M., & Haccoun, D. (2011). Capacity of amplify-and-forward selective relaying with adaptive transmission under outdated channel information. IEEE Transactions on Vehicular Technology, 60(5), 2416–2422.
Sarker, D. K., Sarkar, M. Z. I., & Anower, M. S. (2018). Secure wireless multicasting through AF-cooperative networks with best-relay selection over generalized fading channels. Wireless Networks, 1–14.
Bletsas, A., Khisti, A., Reed, D. P., & Lippman, A. (2006). A simple cooperative diversity method based on network path selection. IEEE journal on Selected Areas in Communications, 24(3), 659–672.
Zhao, Y., Adve, R., & Lim, T. J. (2006). Symbol error rate of selection amplify-and-forward relay systems. IEEE Communications Letters, 10(11), 757–759.
Ferdinand, N. S., da Costa, D. B., & Latva-aho, M. (2013). Effects of outdated csi on the secrecy performance of miso wiretap channels with transmit antenna selection. IEEE Communications Letters, 17(5), 864–867.
Fan, L., Lei, X., Yang, N., Duong, T. Q., & Karagiannidis, G. K. (2017). Secrecy cooperative networks with outdated relay selection over correlated fading channels. IEEE Transactions on Vehicular Technology, 66(8), 7599–7603.
Torabi, M., & Haccoun, D. (2010). Capacity analysis of opportunistic relaying in cooperative systems with outdated channel information. IEEE Communications Letters, 14(12), 1137–1139.
Kumar, R., & Chauhan, S. S. (2020). Physical layer security for space-time-block-coded MIMO system in Rician fading in the presence of imperfect feedback. Wireless Networks, 1–9.
Torabi, M., Frigon, J.-F., & Haccoun, D. (2016). Impact of spatial correlation on the BER performance of cooperative wireless relay networks with OSTBC. IET Commun., 10(8), 975–979.
Anghel, P., & Kaveh, M. (2004). Exact symbol error probability of a cooperative network in a Rayleigh-fading environment., 3, 1416–1421.
Yan, Z., Ouyang, B., Zhang, X., & Liu, H. -L. (2019). Secrecy Outage Performance of Opportunistic Relay Selection with Limited CSI Feedback. IEEE Wireless Communications Letters.
David, N. H. (2003). Order statistics (3rd ed.). New Jersey: Wiley.
Suraweera, H. A., Smith, P. J., & Shafi, M. (2010). Capacity limits and performance analysis of cognitive radio with imperfect channel knowledge. IEEE Transactions on Vehicular Technology, 59(4), 1811–1822.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Torabi, M., Parkouk, S. & Shokrollahi, S. Secrecy performance analysis of amplify-and-forward cooperative network with relay selection in the presence of multiple eavesdroppers. Wireless Netw 27, 2977–2990 (2021). https://doi.org/10.1007/s11276-021-02611-4
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-021-02611-4