Abstract
In this paper, a fractional order dynamical system is constructed that exhibits chaotic and reverse chaotic attractors by changing the sign of the one parameter which involves in the existence of the phase reversal function. A new method of fast projective synchronization of fractional order dynamical systems is introduced. An affine cipher is proposed for secure communication based on the solutions of the synchronized fractional order chaotic systems with the support of the sender’s and receiver’s date of birth. The efficiency and security of an affine cipher are analyzed. Numerical simulations are demonstrated to show the feasibility of the presented theory.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Fractional calculus is a mathematical issue with more than 300-year-old history, and it has been known since the work of Leibniz and L’Hopital in 1695. Recently, the study of fractional order differential systems has greatly attracted the interest of many researchers due to the applications in science and engineering. It has been proven that many systems in different disciplines could be described by fractional differential equations such as viscoelastic [1], diffusion [2], dynamo theory [3], dengue fever [4], and chemical processing [5]. Chaotic phenomena in fractional order dynamical systems become an important theme of study in nonlinear dynamics. Chaotic behaviors have been found in certain long familiar fractional order dynamical systems such as Lorenz system [6], Rössler system [7] and Lü system [8].
In the fractional field, to find a minimum effective dimension for retaining chaos in a fractional order dynamical system is an important problem. Another challenge that to analyze stability theory, the method of constructing chaos control and synchronization are also equally important. Synchronization of chaotic systems means two or more chaotic systems share a mutual dynamical behavior. A method of synchronization between two identical chaotic systems with different initial conditions has been introduced by Pecora and Carroll [9]. Recently, fractional order chaotic and synchronization of fractional order chaotic systems have been started to attract increasing attention among researchers due to its potential applications in secure communication, circuit theory, and control processing see [3, 10–13]. Some investigations have been dedicated in [14, 15] for achieving stability and stabilization of fractional order systems.
Lately, several techniques have been applied for synchronizing fractional order chaotic systems such as adaptive method [16], phase synchronization [17], nonlinear control technique [18], impulsive [19], sliding mode approach [20], and projective synchronization [21–24]. Among the various types of chaos synchronization, projective synchronization (PS) has received much attention due to its faster communication with proportional feature. PS is qualified that the master system and the slave system could be synchronized up to a scaling factor. The unpredictability of the scaling function in PS can additionally strengthen the security of communication, so this feature could be utilized to get more secure communication in practical application, see [24, 25].
Inspired by the above discussions, in this paper, a fractional order dynamical system is modified. The dynamical behaviors of the modified fractional order system are investigated analytically and numerically. It has phase reversed by changing the sign of the one parameter, and the system exhibits reverse chaotic attractor. A new fast projective synchronization (FPS) method is described for synchronizing fractional order dynamical systems and applied for fractional order chaotic and reverse chaotic systems. It is shown that there is no synchronization error that exists between the fractional order dynamical systems by using the proposed FPS. That is, the synchronization error is zero for every time \(t\ge 0\). These synchronized systems are utilized into a novel secured affine cipher for sharing text and image secretly. At the first time, the affine cipher key can be consider as a combination of date of birth (DOB) and the solutions of the derived synchronized fractional order chaotic systems in the proposed affine cipher. Also, the level of security and efficiency of the proposed affine cipher are discussed. Finally, the higher-level security is obtained for the proposed affine cipher due to the hardness of fractional order system and DOB keys.
The outline of this paper is organized as follows: Some basic preliminaries of fractional calculus are presented in Sect. 2. In Sect. 3, a fractional order dynamical system is constructed and their particular cases are discussed. Basic dynamical properties of the modified fractional order system are analyzed in Sect. 4. The FPS of fractional order dynamical systems is investigated by analytically and numerically in Sect. 5. Section 6 is devoted to the application of the synchronized fractional order chaotic systems. The conclusions are finally drawn in Sect. 7.
2 Preliminaries
In this section, a mathematical definition of fractional derivative, some important theorems, and definitions will be presented.
Even though several definitions for fractional derivatives exist such as Riemann–Liouville definition, Caputo definition, and Grunwald–Letnikov definition, we use the following Caputo’s derivative since it has the traditional initial conditions.
Definition 1
([28]) The Caputo fractional derivative is defined as
where \(n=[q]+1,\,[q]\) is the integer part of \(q,\,\varGamma (\cdot )\) is the gamma function and \(D^q\) is called the \(q\)-order Caputo differential operator.
Theorem 1
([29]) For a given fractional order autonomous system
where \(0<q<1,\,x\in \mathbb {R}^n\) and \(A\in \mathbb {R}^{n\times n}\). Then the fractional order system (2) is asymptotically stable if and only if
In this case, the component of the state decay toward 0 like \(t^{-q}\).
Definition 2
([30]) An equilibrium point \(E\) of the system (2) is called a saddle point of index 1 (index 2) if the Jacobian matrix \(J\) at \(E\) has one (two) unstable eigenvalue(s).
Theorem 2
([30]) A necessary condition for the system (2) to remain chaotic is keeping at least one eigenvalue \(\lambda \) in the unstable region. This means that
3 Description of a 3D modified fractional order chaotic system
Recently, a new chaotic attractor has been introduced and their dynamical behaviors have been studied in [26] for the following
where \((x,y,z)\in \mathbb {R}^3, a,b,c,d,e,f \) are the parameters of the system (5). It has found that, the system (5) exhibits chaos when \(a=16,b=5,c=10,d=6,e=18\) and \(f=0.5\).
The following fractional order form of the system (5) has been introduced in [27], and its dynamical behaviors have been investigated for the above parameter values
Further, the authors in [27] found that the fractional order system (6) exhibits chaos when a fractional order \(q\ge 0.95\) and has been synchronized via adaptive sliding mode control.
Remark 1
For the system (6), replacing the nonlinear term \(y^2\) by \(xy\) and fixing the parameters \(f=-1,d=-1,e=1,\) we found the following simulations hold for \(q=1\).
-
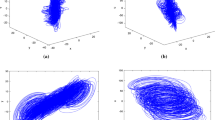
1.
If \(a=-5,b=3.83\)and \(c=-10\), then the attractor is similar to the Lorenz attractor [32], which is depicted in Fig. 1.
-
2.
If \(a=-5,b=3.4\) and \(c=-10\), then the attractor is similar to the Chen’s attractor [33], which is depicted in Fig. 2.
Remark 2
The Euler equations for motion of a 3D rigid body with principle axes at the center of mass is described by [34]
where \(w_x,w_y,w_z\) are the angular velocities of the spindle, \(I_{xx},I_{yy},I_{zz}\) are the main moments of inertia, and \(M_x,M_y,M_z\) are applied moments. We take the applied moments are the linear feedback of the angular velocities, let it be \(M_x=l_{11}w_x,M_y=l_{22}w_y\) and \(M_z=l_{33}w_z\).
Define \(w_x=x,w_y=y\) and \(w_z=z\), then the system (7) can be written as
If \(I_{zz}=3I,I_{yy}=I,I_{xx}=2I,\frac{l_{11}}{I_{xx}}=5,\frac{l_{22}}{I_{yy}}=-10\) and \(\frac{l_{33}}{I_{zz}}=-3.8\), then the system (8) behave chaos, which is represented in Fig. 3.
Substitute \(\frac{I_{yy}-I_{zz}}{I_{xx}}=f, \frac{I_{zz}-I_{xx}}{I_{yy}}=-d,\frac{I_{xx}-I_{yy}}{I_{zz}}=e,\frac{l_{11}}{I_{xx}}=-a, \frac{l_{22}}{I_{yy}}=c, \frac{l_{33}}{I_{zz}}=b\) and replace \(xy\) by \(y^2\) in (8), then the Euler equation of motion (8) is equivalent to the system (6) with fractional order \(q\). Hence, the fractional order system (6) is more generalization of the integer order Lorenz, Chen’s and the Euler equations for motion.
In order to reduce the minimum effective dimension and the synchronization error, a parameter \(f\) should be replaced by a parameter \(a\) of an existing fractional order system (6). Now, the modified fractional order system (6) is described by
where \(D^{q}\) denotes the Caputo fractional operator defined in [28], \(0<q<1, (x,y,z)\in \mathbb {R}^3\) are state variables and \(a,b,c,d,e\) are the parameters of the modified system (9).
Now, we have fixed the parameters \(a=18,b=5,c=10,d=6\) and \(e=18\). For these fixed parameter values, the integer order (\(q=1\)) of the modified system (9) exhibits chaos with the Lyapunov exponents \(L_1=1.3424 >0, L_2=0\) and \(L_3=-14.3447<0\). The chaotic attractor corresponding to the integer order system (9) is depicted in Fig. 4. The basic dynamical properties of the proposed system (9) will be analyzed in the following section.
Different phase portraits of the modified system (9) with \(q=1\)
4 Analysis of dynamical properties
In this section, some basic dynamical properties of the system (9) are analyzed. Throughout this manuscript, we consider the value of the parameters of the system (9) are \(a=18,b=5,c=10,d=6\) and \(e=\pm 18\). We will start with equilibria of the system (9).
The equilibrium points of the system (9) can be obtained by solving the equations
The system of equations (10) has three equilibrium points for the above parameter values. If \(e=18\), then the three equilibrium points are \(O=(0,0,0)\), \( E_+=(0.7731,0.5988,1.2910)\) and \(E_-=(-0.7731,-0.5988,1.2910)\). If \(e=-18\), then the three equilibrium points are \(O=(0,0,0), F_+=(0.7731,0.5988,-1.2910)\) and \(F_-=(-0.7731, -0.5988,-1.2910)\).
4.1 Symmetry, invariance, and phase reversal
The system (9) has a natural symmetry under the transformation \((x,y,z)\rightarrow (-x,-y,z)\) based on equilibria. But the invariance of the system (9) under the coordinate transformation is \((x,y,z,a,b,c,d,e)\rightarrow (-x,y,-z,a,b,c,d,-e)\). Hence, the phase reversal function exists for parameter \(e\). That is, the polarity of signals \(x,z\) changes only with parameter e. It is displayed in Fig. 5.
4.2 Dissipation
The dynamical system is called dissipative if
In that case of system (9), \(\nabla \cdot V = -a+c-b=-13<0\). Therefore, the dissipative condition holds for the system (9). Further, the exponential contraction rate of the system (9) is
4.3 Stability and chaos
The stability of the system based on the eigenvalues, which are determined through the evaluation of the Jacobian matrix of the system (9).
For equilibrium \(O(0,0,0)\), the system (9) are linearized. The Jacobian matrix at \(O\) is defined as
The eigenvalues of (13) are \(\lambda _1=-a=-18,\lambda _2=c=10\) and \(\lambda _3=-b=-5\). Here \(\lambda _2\) is a positive real number, \(\lambda _1\) and \(\lambda _3\) are negative real numbers.
According to Theorem 1 and Definition 2, the equilibrium point \(O\) is unstable and it is a saddle point with index 1.
For equilibria \(E_{\pm }\) or \(F_{\pm }\), the system (9) are linearized. The Jacobian matrix at \(E_{\pm }\) or \(F_{\pm }\) is defined by
The eigenvalues of (14) are \(\lambda _1=-17.1124,\lambda _2=2.0562+14.3578i\) and \(\lambda _3=2.0562-14.3578i\).
Here \(\lambda _2\) and \(\lambda _3\) become a pair of complex conjugate eigenvalue with positive real part, \(\lambda _1\) is a negative real number. Therefore, the equilibrium points \(E_{\pm }\) or \(F_{\pm }\) are unstable and they are saddle points with index 2 according to Theorem 1 and Definition 2.
According to Theorem 2, the necessary condition for the system (9) to remain chaos is
Therefore, the system (9) exhibits chaos when the fractional order \(q>0.9094\). Consequently, the system (9) is stable and doesn’t exhibit chaos when \(q\le 0.9094\). The corresponding iconography is visualized in Fig. 6 when \(q=0.90\). Further, the chaotic attractor corresponding to the system (9) are depicted in Figs. 7 and 8 when \(q=0.91\) and \(q=0.99\) respectively.
System (9) at \(q=0.90\): A 3D view, B time series of \(x(t),y(t),z(t)\) for \(e=18\) and \(e=-18\)
Different phase portraits of system (9) when \(q=0.91\)
Different phase portraits of the system (9) when \(q=0.99\)
Result 1
The proposed system (9) exhibits chaos when \(q>0.9094\). But an existing fractional order system (6) exhibits chaos when \(q\ge 0.95\). Hence, the minimum effective dimension is obtained for the modified system (9).
5 Novel method of FPS of fractional order dynamical systems
In this section, we describe the FPS between two fractional order dynamical systems.
Consider the \(n\)-dimensional fractional order drive system
where \(X=(x_1,x_2,\ldots ,x_n)^T\in \mathbb {R}^n\) and \(G(X)\) is a nonlinear function of \(X\).
Construct the \(n\)-dimensional fractional order response system
where \(Y=(y_1,y_2,\ldots ,y_n)^T\in \mathbb {R}^n\) and \(G(Y)\) is a nonlinear function of \(Y\) and \(U(Y,X)\) is the controller to be designed.
Define the error function \(e=Y-\beta X\) where \(\beta \) is the scaling factor and \(e=(e_1,e_2,\ldots ,e_n)^T\). The ultimate aim is to design the controller \(U(Y,X)\) such that
where \(\Vert \cdot \Vert \) is the Euclidean norm.
The error dynamical system can be written as
Since \(e=Y-\beta X\),
Define
Using (20) in (19), the error dynamical system becomes
Construct
where \(A=\left( \begin{array} {c@{\quad }c@{\quad }c@{\quad }c} a_1 &{} 0 &{} \ldots &{} 0 \\ 0 &{} a_2 &{} \ldots &{} 0 \\ \vdots \\ 0 &{} 0 &{} \ldots &{} a_n \end{array} \right) , \ \forall \ a_i\in \mathbb {R}, \ i=1,2,\ldots ,n\)
and
Then the error dynamical system (21) can be written as
Theorem 3
In general, if
where \(B=\left( \begin{array}{c@{\quad }c@{\quad }c@{\quad }c} b_1 &{} 0 &{} \ldots &{} 0 \\ 0 &{} b_2 &{} \ldots &{} 0 \\ \vdots \\ 0 &{} 0 &{} \ldots &{} b_n \end{array} \right) ,\ \forall \ b_i\in \mathbb {R},\ i=1,2,\ldots ,n\) then \((i)\) if \((A+B)<0\), then the PS between the drive system (16) and the response system (17) can be achieved. \((ii)\) if \((A+B)=0\), then the fractional order error dynamical system (22) makes the fastest potential PS between the drive system (16) and the response system (17). That is, the necessary condition for the existence of FPS between the drive system (16) and the response system (17) is \((A+B)=0\) in the corresponding error dynamical system.
Proof
Substituting given hypothesis in (22), we get
The Jacobian matrix of (23) is
The eigenvalues of (24) are \(\lambda _i=a_i+b_i\), where \(i=1,2,\ldots ,n\) and \((a_i+b_i)\in \mathbb {R}\).
-
(i)
If \((A+B)<0\), then \((a_i+b_i)<0\). Hence the stability condition \(|\arg (\lambda _i)|>\frac{q\pi }{2}\) is satisfied for all \(0<q<1\) and the error states \(e_i(t),\ i=1,2,\ldots ,n\) are tend to zero as \(t\rightarrow \infty \). Therefore the fractional order error dynamical system (23) is asymptotically stable and hence the PS is achieved between the systems (16) and (17).
-
(ii)
If \((A+B)=0\), then the zero error fractional order dynamical system is obtained for the system described by
$$\begin{aligned} D^qe(t)=0. \end{aligned}$$(25)
Thus the error states are \(e_i(t)=0\) for every \(t\ge 0, i=1,2,\ldots ,n\). Therefore, the FPS is achieved between the systems (16) and (17) because the convergence rate of error states in case \((ii)\) is faster than the convergence rate of error states in case \((i)\) for the system (23). Therefore, this PS with the condition \((A+B)=0\) is called as FPS.
Remark 3
In the proposed method of FPS, if \(\beta =-1\) then anti-synchronization between the fractional order dynamical systems (16) and (17) could be achieved. Therefore, the proposed FPS is fully suitable for synchronization and anti-synchronization of fractional order dynamical systems.
Remark 4
From the case \((ii)\) of Theorem 3, the convergence rate of synchronization error of the proposed PS method is very faster than the convergence rate of all exiting PS methods with a small or large quantity of synchronization errors, for example see [21–24] because the states of fractional order error dynamical system (25) are tend to zero for every \(t\ge 0\). That is, there is no synchronization error exists between the fractional order dynamical systems (16) and (17).
5.1 Numerical example
Let \(e=18\) be \(\hat{e_1}\) and let \(e=-18\) be \(\hat{e_2}\) for the system (9). Consider the fractional order chaotic system (9) with \(\hat{e_1}\) as a drive system and the system (9) with \(\hat{e_2}\) as a response system. Here, the drive system is a fractional order chaotic system and the response is a fractional order reverse chaotic system.
The drive system is described by
and the response system is described by
Here \(X=(x_1,y_1,z_1)^T, Y=(x_2,y_2,z_2)^T\) and \(U=(u_1,u_2,u_3)^T\). The fractional order \(q\) is set arbitrarily as \(q=0.93\) since the fractional order drive system (26) and the fractional response system (27) are chaotic for every \(q>0.9094\). The scaling factor \(\beta \) is chosen as \(\beta =3\).
The fractional order error dynamical system is
Then \(\phi (X,e)\)
Here
and \(A=\left( \begin{array} {c@{\quad }c@{\quad }c} -a &{} 0 &{} 0 \\ 0 &{} c &{} 0 \\ 0 &{} 0 &{} -b \end{array} \right) .\)
Construct
According to Theorem 3,
Case (i): Assume that \((A+B)<0.\)
Choose \(B=\left( \begin{array} {c@{\quad }c@{\quad }c} 0 &{} 0 &{} 0 \\ 0 &{} -2c &{} 0 \\ 0 &{} 0 &{} 0 \end{array} \right) \). Then the error dynamical system (28) can be written as
The Jacobian matrix of (30) is
The eigenvalues of (31) are \(\lambda _1=-a, \lambda _2=-c\) and \(\lambda _3=-b\). Then, the fractional order error dynamical system (30) is asymptotically stable according to Theorem 1.
Since by Theorem 3, the systems (26) and (27) are achievable PS.
The time response of the states of the PS of fractional order chaotic (drive) system and reverse chaotic (response) system is exposed in Fig. 9 and the projections of the synchronized chaotic attractors of the drive system (26) and the response system (27) are shown in Fig. 10. Further, the PS errors between the systems (26) and (27) are depicted in Fig. 11.
Case (ii): Assume that \((A+B)=0.\)
Choose \(B=\left( \begin{array} {c@{\quad }c@{\quad }c} a &{} 0 &{} 0 \\ 0 &{} -c &{} 0 \\ 0 &{} 0 &{} b \end{array} \right) \). Then the error system (28) can be written as
Therefore, the state trajectories of the fractional order error dynamical system (28) attains zero for every time \(t\ge 0\).
Since by Theorem 3, the systems (26) and (27) are achievable FPS. The FPS errors between the systems (26) and (27) are depicted in Fig. 12. It is evident that from Figs. 11 and 12 that the convergence rate of the error states \(e_i,\ i=1,2,\ldots ,n\) in (28) with the condition \((A+B)=0\) is very faster than the error states \(e_i,\ i=1,2,\ldots ,n\) in (28) with the condition \((A+B)<0\).
6 Application of synchronized systems
In this section, we propose an affine cipher based on the synchronized fractional order chaotic and reverse chaotic systems with the support of the DOB keys. DOB key means, a key consist of birth day, month, and year of the sender (receiver).
Cryptography is split into two ways of changing the message systematically to confuse anyone who intercepts it: these are codes and ciphers. A code is a way of changing the message by replacing each word with another word that has a different meaning. Ciphers convert the message by a rule, known only to the sender and the recipient, which change each individual letter.
An affine cipher is a combination of the shift cipher and the multiplication cipher. The key for an affine cipher consists of two integers \(k=(l,m)\). The encryption \(E(\cdot )\) and decryption \(D(\cdot )\) processes of affine cipher for given message \(\mathbf {M}\) are defined by [31] as
where \(l'\) is the inverse of \(l\) modulo \(p\) and \(p\) is a positive integer.
Note that, if \(l=1\) then \(E(\cdot )\) and \(D(\cdot )\) process is called shift cipher. If \(m=0\) then the \(E(\cdot )\) and \(D(\cdot )\) process is called multiplicative cipher. In the proposed affine cipher, we generate the affine cipher key pair as a combination of the solutions of fractional order chaotic system and date of birth of sender (receiver). At the first time, an affine will be utilized for image encryption and decryption technique based on synchronized fractional order chaotic systems.
6.1 Proposed affine cipher
Before going to propose an affine cipher, some basic assumptions are needed. Consider \(\mathcal {S}\) as a sender and \(\mathcal {R}\) as a receiver in the cryptosystem. Also consider the drive system (26) as a sender’s system and the response system (27) as a receiver’s system. \(\mathcal {S}\) and \(\mathcal {R}\) are agree on a time \(t\ge t_0\) ( synchronization errors between the systems (26) and (27) are tend to zero from time \(t_0\) onwards), a scaling factor \(\beta \), fractional order \(q\ge 0.91\) and a positive integer \(p\). Let \(D=(D_1,D_2)\) be a pair of date of birth of \(\mathcal {S}\) and \(\mathcal {R}\). Here, \(D_1\) is DOB of \(\mathcal {S}\) and \(D_2\) is the DOB of \(\mathcal {R}\) and they can be represented as \(D_1=DD\text {-}MM\text {-}YYYY\), \(D_2=dd\text {-}mm\text {-}yyyy\) in the day, month, and year format. Then \(D\) is only shared by \(\mathcal {S}\) and \(\mathcal {R}\). The details of key generation, encryption, and decryption processes between \(\mathcal {S}\) and \(\mathcal {R}\) are described as follows.
Key generation:
In the key generation phase, both \(\mathcal {S}\) and \(\mathcal {R}\) generate their own secret key pair.
-
1.
\(\mathcal {S}\) solves a fractional order chaotic system (26) at time \(t\) when fractional order \(q\ge 0.91\) and generates \(K_1=DD*x_1(t)+MM*y_1(t)+YYYY*z_1(t)\) (mod \(p\)) and \(K_2=dd*x_1(t)+mm*y_1(t)+yyyy*z_1(t)\) (mod \(p\)).
-
2.
\(\mathcal {S}\) kept secret on his/him key pair \((K_1,K_2)\).
-
3.
\(\mathcal {R}\) solves a fractional order reverse chaotic system (27) at time \(t\) when fractional order \(q\ge 0.91\) and generates \(L_1=DD*x_2(t)+MM*y_2(t)+YYYY*z_2(t)\) (mod \(p\)) and \(L_2=dd*x_2(t)+mm*y_2(t)+yyyy*z_2(t)\) (mod \(p\)).
-
4.
\(\mathcal {R}\) kept secret on his/him key pair \((L_1,L_2)\).
Encryption:
In the encryption phase, \(\mathcal {S}\) wants to share a message \(\mathbf {M}\) with \(\mathcal {R}\) secretly. So, \(\mathcal {S}\) encrypted a message \(\mathbf {M}\) by using the function \(E(\cdot )\).
-
1.
\(\mathcal {S}\) computes, \(E(\mathbf {M})=(\mathbf {M}*K_1)+K_2\) (mod \(p\)).
-
2.
\(\mathcal {S}\) sends \(E(\mathbf {M})\) to the receiver \(\mathcal {R}\).
Decryption:
In the decryption phase, \(\mathcal {R}\) receives \(E(\mathbf {M})\) from \(\mathcal {S}\) and recovers an original message \(\mathbf {M}\) by the following computation.
-
1.
\(\mathcal {R}\) computes \(D(\mathbf {M})=(E(\mathbf {M})-L_2)*L_1^{-1}\) (mod \(p\)).
-
2.
Finally, \(\mathcal {R}\) recovers an original message \(D(\mathbf {M})=\mathbf {M}\) (mod \(p\)).
For, \(D(\mathbf {M})\)
Note that, a message \(\mathbf {M}\) has two types. One is text and another one is an image. The proposed affine cipher is fully suitable for both text and image encryption–decryption. The detailed procedure is given in the following remarks.
Remark 5
Suppose \(\mathcal {S}\) and \(\mathcal {R}\) want to share a text message \(\mathbf {M}\). In that case, \(\mathcal {S}\) and \(\mathcal {R}\) are assigning the numerical value 0–25 for alphabets \(A-Z\) and 26 for blank space (gap between two words). Then, find the number of characters including the blank space of \(M\), let it be \({{\varvec{c}}}\). Finally, assign a suitable \(M_{m\times n}\) matrix ( that is, \({{\varvec{c}}}\) is equal to \(m\times n\)) for numerical message \(M\). If \({{\varvec{c}}}\) is not equal to \(m\times n\), then add the necessary blank spaces at the end of the message to complete the \(\mathbf {M}_{m\times n}\).
Remark 6
Any image of size \(m\times n\) can be easily encrypted with high security through the proposed affine cipher because an image can be easily represented by matrices of size \(m\times n\). Each element of the matrix determines the intensity of the corresponding pixel value. Every digital image has intensity between 0 and 255. Therefore, we assume that the value of \(p\) as 256 in the proposed affine cipher only for image encryption and decryption. Hence the proposed affine cipher is well supported to encrypt and decrypt a text message and an image.
In the following subsection, the proposed affine cipher will be demonstrated numerically.
6.2 Demonstration of the proposed affine cipher
Assume that, \(\mathcal {S}\) and \(\mathcal {R}\) agree on the fractional order \(q=0.93\). For \(q=0.93\), the PS (FPS) errors between the systems (26) and (27) are tend to zero after a time \(t\ge t_0=0.8\) (\(t\ge t_0=0\)) with a scaling factor \(\beta =3\) since by Figs. 11 and 12 respectively. For every \(\beta \ne 0, q\ge 0.91\), the FPS errors between the systems (26) and (27) are tend to zero after a time \(t\ge t_0=0\). Therefore, both \(\mathcal {S}\) and \(\mathcal {R}\) agree on a time \(t=5.001\) with a scaling factor \(\beta =1\) and set \(p=29\). Further, \(\mathcal {S}\) and \(\mathcal {R}\) shared their DOBs, \(D_1=\,DD\text {-}MM\text {-}YYYY=27\text {-}06\text {-}1986\) and \(D_2=\,dd\text {-}mm\text {-}yyyy=11\text {-}06\text {-}1986\).
\(\mathcal {S}\) wants to send a message \(\mathbf {M}=\mathbf{PASSWORD}\). Here, \(\mathbf {M}\) has eight elements then \(\mathcal {S}\) choose a \(3\times 3\) matrix. Note that, \(3\times 3\) matrix has nine elements. So, \(\mathcal {S}\) insert a blank space at the end of the message \(\mathbf {M}\) and assign the numerical value of each character of the message \(\mathbf {M}\). According to Remark 5, the numerical assignment of \(\mathbf {M}\) as 15 0 18 18 22 14 17 3 26. Then, the matrix form of the message \(\mathbf {M}\) as \(\mathbf {M}=\left( \begin{array} {ccc} 15 &{} 0 &{} 18 \\ 18 &{} 22 &{} 14 \\ 17 &{} 3 &{} 26 \end{array} \right) \).
For encryption, \(\mathcal {S}\) solves a system (26) at \(t\) when \(q=0.93\) and finds \(x_1(t)=0.5615,y_1(t)=1.017,z_1(t)=1.098\).
Thus, \(\mathcal {S}\) generates a secret key pair \((K_1,K_2)\) as
Then, \(\mathcal {S}\) computes
\(\mathcal {S}\) assigns an alphabet for each numerical value of \(E(\mathbf {M})\), \(E(\mathbf {M})=\mathbf{CGHHEKPLA}\) and sends to \(\mathcal {R}\). \(\mathcal {R}\) receives \(E(\mathbf {M})\) from \(\mathcal {S}\).
For decryption, \(\mathcal {R}\) solves a system (27) at \(t\) when \(q=0.93\) and finds \(x_2(t)=0.5615,y_2(t)=1.017,z_2(t)=1.098\).
Then, \(\mathcal {R}\) generates a secret pair \((L_1,L_2)\) as
Further, \(\mathcal {R}\) computes \(D(\mathbf {M})\)
Finally, \(\mathcal {R}\) assigns an alphabet for each numerical value of \(D(\mathbf {M}),\,D(\mathbf {M})=\mathbf{PASSWORD }\). Hence, the original message \(\mathbf {M}\) has been recovered.
Suppose \(\mathcal {S}\) wants to send an image \(I\) with size \(596\times 411\ (I_{596\times 411})\), which is visualized in Fig. 13. Assume that, \(t,q,\beta \) values and the solutions of (26) and (27) are given above. Further, set \(p=256, \mathbf {M}=I_{596\times 411}\), \(D_1=DD\text {-}MM\text {-}YYYY\,=\,02\text {-}02\text {-}1986\) and \(D_2=\,dd\text {-}mm\text {-}yyyy=11\text {-}06\text {-}1986\). Then, \(\mathcal {S}\) generates a secret key pair \((K_1,K_2)\) as
For encryption, \(\mathcal {S}\) computes
The encrypted image is depicted in Fig. 14. \(\mathcal {S}\) sends \(E(\mathbf {M})\) to \(\mathcal {R}\).
\(\mathcal {R}\) receives an encrypted message \(E(\mathbf {M})\) and generates a secret pair \((L_1,L_2)\) as
For decryption, \(\mathcal {R}\) computes
The decrypted image is depicted in Fig. 15.
Finally, \(\mathcal {R}\) recovers an original image \(D(\mathbf {M})=\mathbf {M}=I_{596\times 411}\).
6.3 Security analysis of proposed affine cipher
The proposed affine cipher consists of two pairs of keys \((K_1,K_2)\) and \((L_1,L_2)\), which are computed by the sender and receiver separately. Which is entirely different from the existing affine ciphers. The receiver cannot recover an original text or image without the knowledge of the receivers private key \((K_1,K_2)\). Further, the proposed scheme only allows a designated receiver to recover the original text or image from the encrypted message because the private key \((K_1,K_2)\) is used for message encryption and it is generated by the public key \((D_1,D_2)\). Hence, the proposed cipher is fully authenticated.
Only the sender’s private key is used for encryption and that cannot be used anywhere in the proposed ciphers. Therefore, it has non-repudiation. Moreover, only the receiver recovers the message \(\mathbf {M}\) by computing \(D(\mathbf {M})=(E(\mathbf {M)}-L_2)L_1^{-1}\) (mod \(p\)) using the private key \((L_1,L_2)\) with the knowledge of \((L_1,L_2)\) and the solutions of the response system (27). Hence, the communication must be observable only by the sender and the receiver, but not anyone else. Hence, it has confidentiality. Therefore, the proposed affine cipher is more efficient than the ordinary affine cipher method due to the existence of message authentication, non-repudiation, and confidentiality.
Suppose an adversary (ADV) trying to recover an original message, she/he should be computed the \((E(\mathbf {M})-L_2)L_1^{-1}\) (mod \(p\)). It is impossible because \(L_1\) and \(L_2\) are the private keys of the receiver. On the other hand, ADV would try to obtain \(L_1\) and \(L_2\) with the knowledge of \(D_1\) and \(D_2\). It is also impossible because \(L_1\) and \(L_2\) are a combination of the solutions of the response system (27) and the public key \((D_1,D_2)\). Moreover, finding the solutions of the fractional order chaotic system at time \(t\) is impossible. So, ADV would fail to recover the private keys of the receiver. Hence, ADV would fail to recover an original message.
Suppose ADV only has \((L_1,L_2)\) and try to recover an original message from \((E(\mathbf {M})-L_2)L_1^{-1}\) (mod \(p\)), which is also impossible because the computational part of the \(L_1^{-1}\) (mod \(p\)) is not possible without the knowledge of modulo \(p\) and the computation of integer factorization problem is very hard. Note that, \(p\) is only shared by the receiver and sender not by else. This attempt is also failed for ADV. Hence, the proposed affine cipher is more secure and efficient than the ordinary affine cipher.
7 Conclusions
In this paper, the stability and chaotic behaviors of an altered fractional order dynamical system have been investigated. We found that, the modified fractional order dynamical system has phase reversal and exhibits reverse chaotic attractor. Further, the minimum effective dimension of the modified fractional order system is 2.73. The FPS of fractional order dynamical systems has been presented analytically and numerically. The different phase projections have been displayed. An efficient and secured affine cipher has been proposed based on these synchronized fractional chaotic systems with the support of the sender’s and receiver’s DOB. The efficiency and security of the proposed affine cipher have been assured. Numerical simulations have been confronted to validate the efficacy of the proposed fractional order chaotic system and an affine cipher.
References
El-Shahed, M.: MHD of a fractional viscoelastic fluid in a circular tube. Mech. Res. Commun. 33, 261–268 (2006)
Jesus, I.S., Machado, J.T.: Fractional control of heat diffusion systems. Nonlinear Dyn. 54, 263–282 (2008)
Muthukumar, P., Balasubramaniam, P., Ratnavelu, K.: Synchronization of a novel fractional order stretch-twist-fold (STF) flow chaotic system and its application to a new authenticated encryption scheme (AES). Nonlinear Dyn. (2014). doi:10.1007/s11071-014-1398-x
Diethelm, K.: A fractional calculus based model for the simulation of an outbreak of dengue fever. Nonlinear Dyn. 71, 613–619 (2013)
Flores-Tlacuahuac, A., Biegler, L.T.: Optimization of fractional order dynamic chemical processing systems. Ind. Eng. Chem. Res. 53, 5110–5127 (2014)
Grigorenko, I., Grigorenko, E.: Chaotic dynamics of the fractional Lorenz system. Phys. Rev. Lett. 91, 034101 (2003)
Li, C., Chen, G.: Chaos and hyperchaos in the fractional-order R\(\ddot{o}\)ssler equations. Phys. A 341, 55–61 (2004)
Lu, J.G.: Chaotic dynamics of the fractional-order L\(\ddot{u}\) system and its synchronization. Phys. Lett. A 354, 305–311 (2006)
Pecora, L.M., Carroll, T.L.: Synchronization in chaotic systems. Phys. Rev. Lett. 64, 821–824 (1990)
Abdullah, A.: Synchronization and secure communication of uncertain chaotic systems based on full-order and reduced-order output-affine observers. Appl. Math. Comput. 219, 10000–10011 (2013)
Muthukumar, P., Balasubramaniam, P.: Feedback synchronization of the fractional order reverse butterfly-shaped chaotic system and its application to digital cryptography. Nonlinear Dyn. 74, 1169–1181 (2013)
Teng, L., Iu, H.H., Wang, X., Wang, X.: Chaotic behavior in fractional-order memristor-based simplest chaotic circuit using fourth degree polynomial. Nonlinear Dyn. 77, 231–241 (2014)
Li, R., Chen, W.: Lyapunov-based fractional-order controller design to synchronize a class of fractional-order chaotic systems. Nonlinear Dyn. 76, 785–795 (2014)
Chen, L., He, Y., Chai, Y., Wu, R.: New results on stability and stabilization of a class of nonlinear fractional-order systems. Nonlinear Dyn. 75, 633–641 (2014)
Wang, Z., Yang, D., Ma, T., Sun, N.: Stability analysis for nonlinear fractional-order systems based on comparison principle. Nonlinear Dyn. 75, 387–402 (2014)
Agrawal, S.K., Das, S.: A modified adaptive control method for synchronization of some fractional chaotic systems with unknown parameters. Nonlinear Dyn. 73, 907–919 (2013)
Odibat, Z.: A note on phase synchronization in coupled chaotic fractional order systems. Nonlinear Anal. Real World Appl. 13, 779–789 (2012)
Matouk, A.E., Elsadany, A.A.: Achieving synchronization between the fractional-order hyperchaotic Novel and Chen systems via a new nonlinear control technique. Appl. Math. Lett. 29, 30–35 (2014)
Jin-Gui, L.: A novel study on the impulsive synchronization of fractional-order chaotic systems. Chin. Phys. B 22, 060510 (2013)
Zhang, R., Yang, S.: Robust synchronization of two different fractional-order chaotic systems with unknown parameters using adaptive sliding mode approach. Nonlinear Dyn. 71, 269–278 (2013)
Sha, W., Yong-Guang, Y., Hu, W., Rahmani, A.: Function projective lag synchronization of fractional-order chaotic systems. Chin. Phys. B 23, 040502 (2014)
Liu, L., Liang, D., Liu, C.: Nonlinear state-observer control for projective synchronization of a fractional-order hyperchaotic system. Nonlinear Dyn. 69, 1929–1939 (2012)
Wu, X., Wang, H.: A new chaotic system with fractional order and its projective synchronization. Nonlinear Dyn. 61, 407–417 (2010)
Wu, X., Wang, H., Lu, H.: Modified generalized projective synchronization of a new fractional-order hyperchaotic system and its application to secure communication. Nonlinear Anal. Real World Appl. 13, 1441–1450 (2012)
Chee, C.Y., Xu, D.: Secure digital communication using controlled projective synchronisation of chaos. Chaos Solitons Fractals 23, 1063–1070 (2005)
Li, C., Li, H., Tong, Y.: Analysis of a novel three-dimensional chaotic system. Optik 124, 1516–1522 (2013)
Li, C., Su, K., Wu, L.: Adaptive sliding mode control for synchronization of a fractional-order chaotic system. J. Comput. Nonlinear Dyn. 8, 031005 (2013)
Caputo, M.: Linear models of dissipation whose Q is almost frequency independent-II. Geophys. J. Int. 13, 529–539 (1967)
Matignon, D.: Stability results for fractional differential equations with applications to control processing. Proceedings of Computational engineering in systems applications 2, 963–968 (1996)
Tavazoei, M.S., Haeri, M.: A necessary condition for double scroll attractor existence in fractional-order systems. Phys. Lett. A 367, 102–113 (2007)
Hoffstein, J., Pipher, J., Silverman, J.H.: An Introduction to Mathematical Cryptography. Springer, New York (2008)
Sparrow, C.: The Lorenz equations: bifurcations, chaos, and strange attractors. Springer, New York (1982)
Chen, G., Ueta, T.: Yet another chaotic attractor. Int. J. Bifur. Chaos 9, 1465–1466 (1999)
Chen, H.K., Lee, C.I.: Anti-control of chaos in rigid body motion. Chaos Solitons Fractals 21, 957–965 (2004)
Acknowledgments
This work is supported by the University Grants Commission-Basic Science Research (UGC-BSR), Grant No: F.7-73/2007 (BSR), Government of India, New Delhi. It is also supported by the Project No: UM.C/625/1/HIR/MOHE/13, University of Malaya, Malaysia. The authors are very much thankful to the editors and anonymous reviewers for their careful reading, constructive comments and fruitful suggestions to improve this manuscript.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Muthukumar, P., Balasubramaniam, P. & Ratnavelu, K. Fast projective synchronization of fractional order chaotic and reverse chaotic systems with its application to an affine cipher using date of birth (DOB). Nonlinear Dyn 80, 1883–1897 (2015). https://doi.org/10.1007/s11071-014-1583-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-014-1583-y