Abstract
A new image encryption scheme is presented based on the chaotic system and the swapping operations of the pixels both at the decimal and DNA levels. By randomly choosing two arrays of the given input image for a number of times, randomly chosen pixels of these two arrays are swapped with each other. Same operation is performed on the two randomly chosen columns to get the scrambled image. Next, an XOR operation is performed between the scrambled image and the key stream of random data given by the chaotic system. Further, both the image data and the streams of random numbers are DNA-encoded. Again, the DNA-encoded pixels data are scrambled the way, scrambling was performed on the decimal data but with the different key streams of random numbers. To realize the effects of diffusion at the DNA level, the DNA-encoded scrambled pixels data and the DNA-encoded key stream are XORed with each other. Finally, the DNA-encoded data is translated back into its decimal equivalent. SHA-256 hash codes for the given input image have been used in the proposed cipher in order to achieve the plaintext sensitivity. The simulation and the performance analysis portray the good security effects, defiance to the varied threats and the bright prospects for the real world application of the proposed cipher.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
As the digital technologies are getting developed, the concern for security of data is increasing day by day. Digital images account for a large proportion for this data. These images are stored on the different storage devices. Besides, they are exchanged on constant basis between the different stakeholders using the public network like the Internet. Be it commerce, medicine, traffic, government and diplomacy, these images are dealt with in virtually all walks of life. Sometimes, these images are very sensitive and they require extreme care during their storage and transmission, the picture of a newly developed automobile by some company, for instance. So, measures must be taken for their safety. Classically, the ciphers like AES, DES, RSA etc. have been performing the job of the security of data by converting it into some blurry form. Unfortunately, these ciphers can’t be applied over the images data [35, 49]. They were designed to encrypt the text data only. In contrast to the text data, images have diametrically distinct characteristics like strong inter-pixel correlation, high redundancy and bulky volume etc. Many image encryption algorithms have been developed by using the chaotic maps as the literature review indicates. These maps render the chaotic numbers which are used for the diffusion and confusion operations on the pixels of the given image.
The literature on image security is replete with image cryptosystems developed using the chaotic maps and some other instruments like DNA [1, 5, 8, 11, 36], cellular automaton [12], 15-puzzle [18], knight [40], Rubik’s cube [29], Magic square [57], Nine palace [48], king chess piece [19], hybrid chaotic map [15] etc. In [1], an algorithm for medical image encryption was suggested based on multi chaotic map and DNA. The multi chaotic map was used for the spawning of random data for permutation and DNA was used in final diffusion process to get the cipher image. The thrust of this study was on medical images; the results demonstrated that their scheme has low correlation, better peak-signal-to-noise-ratio and better key space, and can defy differential and statistical attacks. Article in [11] presents an algorithm for images encryption through the usage of Lorenz chaotic map and DNA modeling. The chaotic map was used for substitution operation while the DNA encoding scheme was used for the confusion process. In first stage, they diffused the image using the chaotic map and then they split the diffused image into eight subparts to use the DNA rules over them. At the end they combined all parts to a single cipher image. Results showed that the suggested scheme was more potent against differential attack, chosen plaintext attack and provided better plaintext sensitivity. Using DNA modeling, chaotic map and SHA-256 hash codes, a novel image cryptosystem was proposed in [8]. Variables of Logistic-adjusted-Sine map (2D-LASM) and one-dimensional chaotic system were tempered through usage of SHA-256 hash function. The 2D-LASM was exploited for the production of DNA encoding rules, in order to perform the permutation process, and ID chaotic map was employed to generate matrix to XOR with the obtained permuted image. Thus a complete encrypted image was generated. The simulation results demonstrated that the suggested scheme had not only better security effects but also was secured against the different known attacks. Besides, a five step image encryption algorithm for RGB images using the chaotic map and 3D space was proposed in [5]. In first step, they separated the RGB channels of color image. In the second step, the 3D substitution operation was performed; in the third step, the permutation operation was carried out; in the fourth step, the 3D permutation operation was done and in the final step, again the substitution operation was conducted. The concept of 3D improved the performance and helped in increasing the key space. In [36], DNA and Piecewise Linear Chaotic Map based image encryption technique was given. This was a double layer scheme in which the DNA encoding rules were used in both permutation and diffusion processes and good results of different validation metrics like numbers of pixels change rate, correlation coefficient, information entropy, unified average changing intensity, key space etc. were produced. Besides, a novel hybrid chaotic map and a new optimization technique has been given in [13] in order to improve the encryption algorithms. This new hybrid chaotic map renders an excellent performance of randomness and the sensitivity. Moreover, its characteristics are better than the others due to the Lyapunov exponents and entropy measure. New image cipher has been written by exploiting the Shannon properties of confusion and diffusion. Apart from that, by using the quaternion Fresnel transforms, 2D Logistic-adjusted-Sine map and computer generated hologram, four-image scheme for encryption has been given in [51]. Simulation demonstrated that the new cryptosystem is furnished with the desirable security effects.
Recently, a novel image encryption algorithm has been written by exploiting the random numbers given by the time delay chaotic system [45]. The salient feature of this system is that it has varied behavior as the time passes. Based on the random numbers given by this system, a new encryption scheme for the images has been developed. The simulation suggests that it has higher security. Apart from that, using the 3D scrambled image, a new image encryption scheme has been proposed in [20]. The pixels taken from the input color images are inserted randomly upon the different 3D addresses of the 3D scrambled image. Both the simulation and security analysis indicate that the proposed scheme has the high security against the potential threats. In a yet another image encryption algorithm [43], the concept of semi-tensor product was employed. The pixels of the given input image have been distributed in the four blocks. After that, by using the Arnold transformation, the pixels were subjected to the varied rounds. Then, these blocks were joined to get the confused image. Through the updation of the Boolean network, real secret key was generated. This key was employed to the chaotic map for spawning the random numbers. Lastly, semi-tensor product was implemented both on the random numbers and the scrambled image to get the final cipher image.
As described earlier, confusion and diffusion are the two principal operations to ensure safety from the diverse attacks of the hackers. In the literature, one may find the ciphers based only on the permutation operations [23, 24, 33]. Such kinds of image cryptosystems are vulnerable to various chosen and known plaintext threats since they only change the locations of image pixels and not the intensity values [23]. Some image ciphers did not introduce the plaintext sensitivity in the design principles of their encryption algorithms due to which they were broken by the community of cryptanalysts. For instance, these encryption algorithms [56, 58, 59] were cracked by [9, 17, 46] through the chosen ciphertext attack, differential attack and chosen plaintext attack in a respective manner. Underlying causing for the cracking of these cryptosystems was that the random numbers produced were unrelated to the input image being used in the algorithms. So corrective steps need to be adopted to make the future ciphers more robust against the differential attacks.
Some other loopholes and lacunas plague many ciphers as well. For example, Zhang et al. [28] wrote a novel cipher by exploiting DNA modeling and chaotic system in one setting. This cipher was demonstrated insecure by [34] when a potential chosen plaintext attack was launched over it. Moreover, the confidential key of this cipher could be revealed through the usage of four plain images. Apart from that, in these studies [2, 16, 53, 54], static and fixed rules for the encoding/decoding were employed, both for the input plain images and the key/mask images. Specifically, in the algorithm [54], for encoding purpose, third rule was used; for decoding purpose, fourth rule was used. This fixation of encoding and decoding rules assist a lot to the hackers in their cryptanalytic efforts. Not only these rules should be made fixed, rather, they must adapt as the input images changes. Hence, measures need to be taken to inject more security stuff in the ciphers.
In the proposed work, the afore-mentioned loopholes have been avoided in the design principle of the potential cipher. Confusion and diffusion operations have been carried out at the decimal and DNA levels. Plaintext sensitivity has been achieved through embedding SHA-256 hashing for given input image. The same key streams have been used again and again to fulfill the different requirements of the encryption algorithm by introducing some twist in them. The following bullet points characterize the features of the suggested image cipher.
-
Both scrambling/confusion and diffusion/substitution have been performed at the decimal level and DNA strands level. This act boosted the security effects of the cipher and the potential attacks would be averted.
-
The peculiar algorithm for our cipher requires more key streams than the ones provided by the chaotic system. The same key streams have been recycled again and again after twisting them. In this way, an optimal usage of the system resources has been assured.
-
Dynamic DNA encoding rules have been employed in the proposed cipher since they depend upon chaotic data. This chaotic data, in turn, depend on the used input image.
-
To introduce the plaintext sensitivity, SHA-256 hash codes have been embedded which tempered the initial values of the chaotic map being used. For each input plain image, unique random data would be generated due to which the potential differential attacks would be averted.
The current study is formated like this. Section 2 covers the preliminaries of chaotic maps and DNA modeling. Section 3 explains the way chaotic data has been generated and the newly suggested algorithm for image encryption in detail. Simulation and security analyses have been covered in the Sections 4 and 5. Lastly, Section 6 draws the necessary conclusion of the paper.
2 Preliminaries
This section will cover two preliminaries of the proposed research work, i.e., chaotic systems and DNA computing.
2.1 Chaotic systems/maps
Theory of chaos investigates the behavior and conduct of those systems which are highly sensitive to the system parameters and the initial conditions. These systems are also called dynamic systems. Complying with this notion, mathematicians have developed a lot of chaotic systems/maps. These systems are the part and parcel of the hundreds of image ciphers found in the literature upon the images security. The underlying reason for the usage of these systems is that these systems bear the extra-ordinary properties of unpredictability, aperiodicity, pseudo-randomness, ergodicity, mixing etc.
The current research has chosen a 5D hyper-chaotic system which can be defined as [25].
x,y,z,w,v are the state variables and a,b,c,d,e,f,g,h are the system parameters in the above set of equations. yz,xy and x2y are the nonlinear terms in the dynamical system written above in the form of mathematical equations. Periodic orbit, chaotic and hyper-chaotic and other dynamic behaviors of these systems can be seen here [25].
2.1.1 Attractors and Lyapunov exponents of 5D multi-wing hyperchaotic system
We have chosen chaotic system’s values as shown in the Table 1. Further, the time step for the solution of the system is 0.001. The chaotic behavior of the system (1) has been depicted in the Fig. 1. Moreover, the Lyapunov exponents came out to be L1 = 9.979, L2 = 1.96. L3 = 0.005362. L4 = − 19.13. L5 = − 27.82 as depicted in the Fig. 2.
Different attractors of the system (1):(a) 3D view in the xyz space; (b) projection on xy plane; (c) projection on xz plane; (d) projection on yz plane; (e) projection on xv plane; (f) projection on zw plane
Lyapunov exponents of the system (1)
2.1.2 Randomness analysis of 5D multi-wing hyperchaotic system
Just to spawn the arbitrary numbers through some chaotic map is not sufficient, rather, there must be a set of objective criteria to check the randomness of the generated data. Luckily, NIST Test Suite [52] exists for this purpose. The significance level p for the different tests should be above 0.01 for accepting the randomness of given bit sequences [50]. The test results for the five bit streams of system (1) are shown in the Table 2.
2.2 DNA Modeling
Four strands/bases, which are normally described through the four English capital letters are A(Adenine), T(Thymine), C(Cytosine), G(Guanine). In a pairwise fashion, these DNA strands complement each other. For instance, if ‘10’ corresponds to A then ‘01’ will correspond to T. Similarly, if ‘00’ corresponds to C then ‘11’ will correspond to G. Out of the total 4! or 24 types of encoding, just 8 of 24 satisfy the Watson-Crick complementary rules (Table 3). In DNA modeling, studies [21] inform us the XOR, addition and subtraction binary operations over the DNA strands. Since the proposed research work only uses the XOR operation so it has been shown in the Table 4. We have defined two conversion functions whose names are DNA_Encoding and DNA_Decoding. DNA_Encoding translates a given pixel value (8-bit) to its corresponding DNA sequence of length four by taking some translation/conversion rule(1-8) and DNA_Decoding converts the DNA sequence of length four to some decimal number, again by taking some rule (1-8). For example DNA_Encoding(212,2) = TCCA, DNA_Encoding(212,4) = ACCT and DNA_Encoding(212,8) = CAAG. Further, DNA_Decoding(TCCA,2) = 212, DNA_Decoding(ACCT,4) = 212 and DNA_Decoding(CAAG,8) = 212. Moreover, for DNA XOR operation, ⊕ (CATG,TCGA) = GCCG.
3 Proposed image encryption scheme
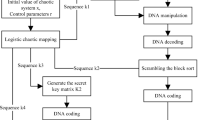
Potential new scheme gives the solution for the problem of image encryption. These images are assumed to be gray scale with dimension m × n. The diagram depicting the flow of the potential scheme is shown in the Fig. 3.
The encryption algorithm comprises of some phases. In the first phase, hash codes for the function SHA-256 have been obtained with the gray scale image as input. These codes change the variables of the chaotic map/system being used in the scheme. This tempering serves the purpose of plaintext sensitivity. Due to the incorporation of this sensitivity, the potential threats of differential attacks are curbed. In the second phase, the tempered initial values have been fed to the 5D multi-wing hyperchaotic system which rendered the five keystreams namely x, y, z, w and v. In order to make them compatible to our proposed algorithmic logic, we have customized them and obtained a set of another five keystreams ks1, ks2, ks3, ks4 and ks5. In the third phase, decimal level scrambling has been achieved for the given input gray scale image by using the key streams ks1, ks2, ks3, ks4. In this scrambling, two arrays of the given input image are chosen randomly for a number of times. In each choice, the randomly selected pixels from these arrays are swapped with each other. Same operations have been carried out upon the columns. In this way, the operation of confusion is abundantly done at the decimal level. In the fourth phase, an XOR operation has been conducted between the scrambled image obtained in the third phase and the key stream ks5 which is being treated as the key image. In the fifth phase, both the encrypted image and the key image flip(ks5) have been DNA-encoded by using the key streams ks1,ks2 and ks3,ks4 respectively. It is to be noted that key stream ks5 was treated as the key image in the fourth phase. The same key stream has been reused in the fifth phase by recycling it through the flip(.) operation over it, where flip(.) reverses the input. This act would expedite the security effects. In the sixth phase, the DNA encoded image has been scrambled in the same way as was done at the decimal level (third phase) but by using the key streams flip(ks1), flip(ks2), flip(ks3), flip(ks4). In the seventh phase, the purpose of DNA level diffusion has been realized by taking DNA XOR operation between the DNA level scrambled image and the DNA encoded key image by using the Table 4. In the eighth and last phase, the DNA level diffused image obtained in the seventh phase has been translated to its original form, i.e, decimal by using the key streams ks2,ks3 to obtain the final encrypted gray scale image.
3.1 Key stream generation procedure
Here we will shed light on the way, SHA-256 hash codes have been used in order to change the system parameters and initial conditions of chaotic map being employed. The 256-bit secret key K given by the hash function is broken down into slices of 8-bit size each as
With the help of the below steps, we have obtained the key streams of random data. These random data will, of course, be used in order to perform the operations of confusion and diffusion.
-
Step 1: Through the following set of equations, the slices of the secret key K are causing to update the initial values of the chaotic map as follows:
$$ x_{0} = x^{\prime}_{0} + \frac{((k_{1} \oplus k_{2}) + (k_{3} \oplus k_{4}) + (k_{5} \oplus k_{6})) }{4096} $$(3)$$ y_{0} = y^{\prime}_{0} + \frac{((k_{7} \oplus k_{8}) + (k_{9} \oplus k_{10}) + (k_{11} \oplus k_{12})) }{4096} $$(4)$$ z_{0} = z^{\prime}_{0} + \frac{((k_{13} \oplus k_{14}) + (k_{15} \oplus k_{16}) + (k_{17} \oplus k_{18})) }{4096} $$(5)$$ w_{0} = w^{\prime}_{0} + \frac{((k_{19} \oplus k_{20}) + (k_{21} \oplus k_{22}) + (k_{23} \oplus k_{24})) }{4096} $$(6)$$ v_{0} = v^{\prime}_{0} + \frac{((k_{25} \oplus k_{26}) + (k_{27} \oplus k_{28}) + (k_{29} \oplus k_{30}) + (k_{31} \oplus k_{32})) }{4096} $$(7)where the set of variables \(x^{\prime }_{0}, y^{\prime }_{0}, z^{\prime }_{0}, w^{\prime }_{0}, v^{\prime }_{0}\) form the initial values of the map before the addition of the plaintext sensitivity. Further, the set x0,y0,z0,w0,v0 denotes the initial values after the addition of plaintext sensitivity. The symbol ⊕ refers to the operation of XOR.
-
Step 2: Tempered initial values are fed to the chaotic map defined in (1). As the iteration of this map ended, we got these sequences \(x = [x_{1}, x_{2},...x_{m + n_{0}}]\), \(y = [y_{1}, y_{2},...y_{n + n_{0}}]\), \(z = [z_{1}, z_{2},...z_{m + n_{0}}]\), \(w = [w_{1}, w_{2},...w_{n + n_{0}}]\) and \(v = [v_{1}, v_{2},...v_{mn + n_{0}}]\), (m,n) being the size of the input image. In the above equations, n0 ≥ 500. To avoid the transient influences/effects of the chaotic system/map, normally the first n0 values are ignored and the values after that are utilized for diffusion and confusion operations.
-
Step 3: To make the above set of equations useful, the following (8) translate them and provide the sequences ks1, ks2, ks3, ks4 and ks5.
$$ \left\{ \begin{array}{llll} ks1(i) = floor(mod(abs(x(i))-floor(abs(x(i))) \times 10^{14}, m)) + 1, & \\ ks2(j) = floor(mod(abs(y(j))-floor(abs(y(j))) \times 10^{14}, n)) + 1, & \\ ks3(i) = floor(mod(abs(z(i))-floor(abs(z(i))) \times 10^{14}, m)) + 1, & \\ ks4(j) = floor(mod(abs(w(j))-floor(abs(w(j))) \times 10^{14}, n)) + 1, & \\ ks5(k) = floor(mod(abs(v(k))-floor(abs(v(k))) \times 10^{14}, 256)) & \end{array} \right. $$(8)In the above equations, mod(.,.) gives the remainder when first parameter is divided by the second parameter. Apart from that, this division is being treated as an integer division. 1 ≤ i ≤ m, 1 ≤ j ≤ n and 1 ≤ k ≤ mn.
3.2 Image encryption procedure

The steps below explicate the suggested image encryption procedure (Fig. 3).
-
Step 1: (Decimal level confusion) Let the dimensions of gray scale plain image img are m × n. Call Algorithm 1 with parameters img, ks1, ks2, ks3, ks4, m, n. The task of this algorithm is to scramble the pixels of the image img through swapping them with the help of the chaotic sequences ks1,ks2,ks3 and ks4 and to return the scrambled image img1. Line 3 of Algorithm 1 swaps the pixels img(ks1(row),ks2(col)) and img(ks3(row),ks4(col)). In each iteration of the line 2, the value of row row remains fixed whereas the value of column col changes in the line 3. This means that for a single iteration of the loop of line 1, two randomly selected rows at line 3 remain fixed and columns change (due to the nested loop at line 2), and the two pixels of these rows are swapped with each other. The same purpose is being served in the lines (4-6) by fixing the two columns. The last line 7 assigns the scrambled image img to the variable img1 and returns it.
-
Step 2: (Decimal level diffusion)
Reshape the confused image img1 to 1 × mn which was obtained in Step 1. The image img1 and the key image ks5 are XORed with each other to throw the diffusion effects in the image img1 as follows:
$$ img2(i) = img1(i) \oplus ks5(i) $$(9)i = 1,2,3,...,mn. img2 is the encrypted image of size 1 × mn.
-
Step 3: (DNA encoding of image and key stream)
Reshape both img2 and ks5 from one-dimensional format into two-dimensional m × n. Further, by using the translation/conversion rules, these two 2-dimensional arrays img2, ks5 are converted into their DNA strands equivalents for getting the arrays img3 and key_image.
$$ \left\{ \begin{array}{ll} img3(i,j)=DNA\_Encoding(img2(i,j),mod(ks1(i) \times ks2(i),8) + 1), & \\ key\_image(i,j)=DNA\_Encoding(flip(ks5)(i,j), mod(ks3(i) \times ks4(i), 8) + 1), & \end{array} \right. $$(10)for 1 ≤ i ≤ m and 1 ≤ j ≤ n. Arrays img3 and key_image consist of mn DNA sequences of length 4. In the above equations, mod(.,8) + 1 serves as the rule for decimal to DNA conversion. Further, we have taken two streams of random numbers for the sake of security.
-
Step 4: (DNA level confusion)
Invoke Algorithm 1 again with the parameters img3, flip(ks1), flip(ks2), flip(ks3), flip(ks4), m and n to confuse the image by swapping the DNA strands and to get the image img4. It is to be noted that the random data has been given in the reverse order this time through the operation flip(.) to inject more sophistication and hence more security in the proposed cipher.
-
Step 5: (DNA level diffusion)
By taking a DNA XOR operation between img4 and mask DNA image key_image (Table 4), the purpose of DNA level diffusion is getting served.
$$ img5(i,j)=img4(i,j) \oplus key\_image(i,j), $$(11)for 1 ≤ i ≤ m and 1 ≤ j ≤ n. Array img5 is final cipher image after substitution/diffusion operation comprising of DNA sequences of length 4. Symbol ⊕ refers to the operation of XOR.
-
Step 6: (Decimal conversion) Lastly DNA array img5 is translated back into its decimal equivalent to get img6 by using the conversion rules as follows.
$$ img6(i,j)=DNA\_Decoding(img5(i,j), mod(ks2(i) \times ks3(i),8) + 1)) $$(12)for i = 1,2,...,m and j = 1,2,....,n. img6 is the m × n sized final output cipher image.
The decryption algorithm is trivial. We have followed the approach of private key/symmetric key in the proposed cipher. So, the decryption algorithm consists of the steps in reverse order of the encryption algorithm.
3.2.1 Preconditions and postconditions of the proposed algorithm
In order to enhance the software reliability, preconditions and postconditions, a sort of acceptance tests, are widely employed over the developed algorithms [4]. Precondition of an algorithm is a logical condition which must be true before the calling of that algorithm. For instance, if an algorithm has to be invoked working in the domain of real numbers for calculating the square root of a number, a very obvious condition that emanates from the given scenario is that the number being passed to the algorithm must be nonnegative.
A postcondition about a method invocation is a condition that must be true as we return from a method. For the sake of an example, if an algorithm for calculating the arcsin with input x is called, and the algorithm returns y, then we must have the postcondition x = sin(y).
Following list characterizes the preconditions of Algorithm 1.
Postcondition is very trivial, i.e., plain and cipher images involved in the process should be distinct img≠img1.
4 Simulation and experiments
Here, a practical demonstration of the framework we have developed for the images encryption and decryption would be presented. For this purpose, eight gray scale images from the diverse areas of human society have been taken. Baboon, Brain, Butterfly, Couple, Girl, House, Lena and Truck are the names of these images. 256 × 256 is the size of these images. One can download these images from the USC-SIPI Image Database. Apart from that, MATLAB 2016 version has been used for the sake of experimentation. Besides, this tool is 64-bit double-precision according to the IEEE [14] standard 754.
In order to kick-start the chaotic system being employed in suggested cipher for the generation of random data, Table 5 shows the initial values given to variables of the system. Figures 4, 5, 6 and 7 depict the selected plain gray scale images, scrambled/confused images, cipher/encrypted images and decrypted/restored images respectively. One can verify success and do-ability of the proposed encryption and decryption algorithms. The given input images are looking noise-like. Further, they leak no clue or hint to the input images. Besides, the decryption algorithm also successfully decrypted the encrypted images.
5 Performance analyses
In these analyses, cryptographers find an opportunity to validate their proposed ciphers through the different objective yardsticks whom the scientists and researchers have developed over the years. Apart from that, we have selected these researches [3, 6, 7, 20, 30, 31, 37, 41, 44, 47] from the literature to compare the proposed image cipher with them.
5.1 Key space
Large key space of any cipher acts as a good immunity to brute-force attacks which may be made by the community of hackers, adversaries and other antagonists. The set of variables of the chaotic system x0, y0, z0, w0, v0, a, b, c, d, e, f, g, h form the secret key of the proposed image cipher. Upon taking the computer precision to be 10− 15, the key space is calculated to be 10195 ≈ 2647. Hence, it has requisite ability to endure brute-force threat since 2647 >> 2100. Besides, we have compared the key space of suggested cipher (Table 6) with other ciphers in the literature. The Table 6 depicts that our scheme beats the schemes given in [6, 7, 30, 44, 47] as far as key space is concerned.
5.2 Key sensitivity
A secured cipher entails an extreme sensitivity to the secret key. Put in other words, if some cipher is claimed to be secure, then it must have an extreme key sensitivity. The idea of this security parameter is that a very small change is done in the secret key for the encryption/decryption machineries of the proposed image cipher. The outputs should be radically different from the ones which were obtained with no change in the secret keys. These phenomena refer to the key sensitivity, also called avalanche effect.
This key sensitivity in the encryption algorithm has been demonstrated like this. Two slightly different keys have been used to encrypt the same input image say Lena. Let {x0,y0,z0,w0,v0,a,b,c,d,e,f,g,h} is the initial key set and call this as Key0. By using this key, the encryption algorithm has been applied over the Lena image drawn in the Fig. 8a to get its cipher version which has been later drawn in the Fig. 8b. Next, a very minute change of 10− 14 has been done to x0, i.e., \(x_{0}{{~}^{\prime }} = x_{0} + 10^{-14}\). In this process, the other keys have been made intact. This act of ours rendered an other key set say Key1. Now the same Lena image of Fig. 8a has been encrypted by Key1 and the cipher image so obtained has been drawn in the Fig. 8c. Besides, Fig. 8d shows the pixel-to-pixel differential image between these two cipher images. The encrypted image of the Fig. 8b has 99.6501% different pixel intensity values from the one in Fig. 8c. To further explore the key sensitivity in the proposed cipher, the difference rates have been calculated between the two encrypted images generated by Key0 and Keyt(t = 1,2,...10). Both the keys Key0 and Keyt have very minute difference, the results so obtained have been written in the Table 7. Further, 99.6141% has come out to be the average key sensitivity which is better than [22, 26, 27]. Therefore, we are justified in saying that suggested cryptosystem has advantage over the other published works.
Key sensitivity test on the Lena image:(a) Original plain image; (b) Encrypted image with key set Key0; (c) Encrypted image with key set Key1; (d) Differential image got through (b) and (c); (e) Decrypted image from (b) with the valid/correct key set Key0; (f) Decrypted image from (b) with the invalid/incorrect key set Key1; (g) Decrypted image from (c) with the valid/correct key set Key1; (h) Decrypted image from (c) with the invalid/incorrect key set Key0
Two sets of secret keys Key0 and Key1 have been used to decrypt the cipher images in Fig. 8b and c respectively in order to evaluate the key sensitivity for the decryption algorithm. The restored/decrypted images so obtained are drawn in the Fig. 8a-h. These figures cogently say that plain images are restored only after the application of correct keys. A very small tempering in the variables of keys causes to get an entirely different output which is, of course, not intended. Hence, we can assert that the proposed encryption and decryption machineries are equipped with extreme sensitivity of key.
5.3 Statistical analysis
In this heading, normally two analyses are carried out, i.e., correlation analysis and histogram analysis.
5.3.1 Histogram
How the pixels’ intensity values are scattered in an image, is normally depicted through the instrument called histogram. The histograms of any normal/natural image have a very curved and slantingly running bars over them, which is full of information about the image. As the encryption technique is implemented over an image, histogram of cipher image should have a very uniform and smooth bar over it. This uniformity and smoothness of the bar proves a great resistant to any potential histogram attack. Lena’s histograms for the cipher and plain images have been shown in the Fig. 9. One can see that in case of plain image, bar of the histogram is slanting whereas, it is uniform for encrypted image. Uniform bar of the encrypted image implies good security effects.
The uniformity of the histogram bar through a naked eye aside, there exists an objective way to measure it, i.e., variance. Relatively smaller values of variance correspond to the greater uniformity of the bar of the histogram and, of course, the greater values of variance correspond to the smaller uniformity of the bar of the histogram [55, 61]. The values of the variance for the different histograms of the ciphered Baboon, Brain, Butterfly, Couple, Girl, House, Lena and Truck images can be seen in the Table 8. Through the usage of the initial key set Key0, the values in the first row of the table have been calculated. Whereas, the values in the left over rows have been obtained by changing the secret key Keyt (t = 1,2,...,10) (defined in the Section 5.2). The average variance value for all the cipher-images is 253.4553 according to the Table 8. While, around 87,000 comes out to be the variance value for the plain-images. Therefore, we assert that the suggested method is efficient.
5.3.2 Correlation coefficient analysis
The adjacent/consecutive pixels in the natural/normal images are highly correlated with each other. Adjacent pixels are those which are next to each other. These neighboring pixels may be attached with each other in horizontal, vertical or diagonal directions. The principal job of any image cryptosystem is to dismantle this nexus between the adjacent pixels. Once this nexus is broken through the application of cipher upon the plain image, the correlation between the adjacent pixels drops phenomenally. This is the reason that the cipher image has a noisy and cloudy looking. In an ideally encrypted image, a nil correlation is there between the adjacent pixels. Normally, an image has tens of thousands of pixels. It will be too much time consuming to take every two neighboring pixels to calculate the correlation coefficient. So, to avoid this hassle, we randomly chose 5,000 pairs of consecutive pixels, both from the cipher image and plain image. For the sake of calculation of this important security metric, the following mathematical formula was used [10]:
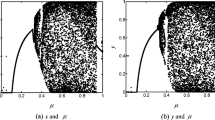
In the above equation, z and w denote the intensity values of the given pixels. Further, these pixels are assumed to be consecutive. Here P denotes the total number of pixels. Figure 10 shows the distribution of these pixels of the Lena’s plain and cipher images in the three orientations. These orientations span horizontal, vertical and diagonal.
Correlation coefficients between two consecutive pixels for original and cipher image of Lena have been given in Table 9.
One can deduce the fact from Table 9 that the correlation coefficients for the pixels of the input image is almost nearly equal to 1. Further, this security parameter is nearly equal to 0 when the image is encrypted. Table 9 and Fig. 10 aggregately indicate that after the application of encryption algorithm over the input images, the relationship between the input image and output image came down steeply. Further, Table 10 compared this security metric of the proposed algorithm with different related schemes. One can see that the results of the proposed scheme are comparable to our chosen researches [3, 6, 7, 30, 41, 44, 47].
5.4 Information entropy analysis
As the normal image is confused and diffused, the highly correlated pixels get scattered and dispersed. Naturally some metric is required to measure this dispersion of the pixels. Information entropy performs this job. It measures the scale of uncertainty, unpredictability and randomness of some information source. Shannon in 1949 [39] developed a formula for the appreciation of this concept
Z(r) refers to the information entropy for the given signal r. Moreover, in the above equation, p(rc) is the probability of rc. As the pixels of plain image are disturbed, this value boosts. Its value reaches to 8 for ideal cases with 256 gray values. Good image ciphers are expected to give the value of this metric very close to the ideal value of 8. Table 11 shows the entropies of our chosen images. 7.9973 is the average value for the entropies for our chosen images. Therefore, we can assert that the suggested cipher is defiant to the attack of entropy over it. Besides, Table 11 draws a comparison of this metric between the suggested work and the works published in the literature. The proposed cipher performs better than [7, 44, 47] for the Lena image.
5.5 Differential attack
Differential attack is yet an other frequently used attack on the image ciphers. In this attack, as the name implies, two samples of plain images are taken; one is the straightforward image and the other one with a very minute tempering in just one pixel. Then both of these images are encrypted. With a smart handling, a potential relationing is spotted between these two encrypted images which has the power to the revelation of secret key of cipher. To tackle this issue, two measures have been developed by the scientists, i.e., NPCR and UACI. The former is an abbreviation of number of pixels change rate and the latter is of unified average changing intensity. The mathematical formulae of these concepts are
where F × G denote the dimensions of the image. D(l,m) is defined as
In the above equation, C is encrypted image without changing the pixel value and \(C^{\prime }\) is the encrypted image after changing the pixel value.
The values for the security parameters of the differential attack, i.e., NPCR and UACI have been drawn in the Table 12 against the chosen eight images. The average value for NPCR is 99.6193% and that of UACI is 33.4269%. These results prove the workability of suggested cryptosystem regarding the security parameter differential attack. Further Table 13 compares our values of NPCR and UACI for the Lena image with our selected researches. Our technique has the better values of NPCR than the ones in [3, 44], while the UACI results are not so competitive.
5.6 Irregular deviation and maximum deviation security analyses
These two parameters Irregular deviation (ID) and maximum deviation (MD) are another yardsticks through which the defiance and immunity of the image ciphers against the potential threats is guaged. In these analyses, the discrepancy/deviation of the pixel intensity values between the cipher image and the given plain image is determined. The mathematical formulae used for this purpose are [20]
and
In the above equations, Deviationi refers to the amplitude of difference between the ciphertext image and plaintext image histograms at i. Besides, average sum of the values of the histogram is represented by Amplitude. Apart from that, N represents the total number of pixels in the given image. Lower value of IrregularDeviation and bigger value of MaximumDeviation are expected from the image ciphers for the desirable security effects. The lower values of IrregularDeviation in Table 14 depict the better uniformity of pixels’ intensity values for the suggested encryption scheme. Additionally, average value of 40,633 for chosen images is better than 43,506 [20]. Apart from that, average value 65,407 is better than 58,691 [20] as far as the metric of MaximumDeviation is concerned.
5.7 Contrast and energy analyses
When some plain image is encrypted, the variations in the pixel intensity values are increased. By contrast analysis, this variation is measured. The cipher images with high variation values are desirable for the better effects of security. Mathematically, this contrast is defined as [20]
q(c,d) denotes the number of gray-level co-occurrence matrices (GLCM). Table 15 shows the results of this metric calculated for the chosen images. Average value of contrast for cipher images comes out to be 10.4963 which is better than 8.6448 [20] and slightly lower than 10.5325 [37]. These results depict that suggested encryption algorithm renders the comparable results.
Moreover, the sum of elements in gray level co-occurrence matrix after taking their square represents the energy of an image [20]
whereas q(c,d) is the number of gray-level co-occurrence matrices as narrated earlier. If this metric calculates to be lower, then this indicates the better security. Table 16 gives results of energy analyses for both cipher and plain images. The values of this security parameter for the plain images are higher. Besides, they are lower if the image under consideration is cipher. Apart from that, 0.0156 is the average value of energy using the chosen images which is better than 0.1650 [20] and equal to 0.0156 [37].
5.8 Peak signal-to-noise ratio analysis
Producing a maximum difference between the plain and cipher images is recurrent idea of images cryptography. (PSNR), a contraction of Peak-Signal-to-Noise Ratio, is normally used to measure this difference. Its mathematical equation is
where F and G refer to the size of the test image. R0(l,p) and R1(l,p) are the intensity values of the pixels for the input and output images. Besides, MSE refers to the mean squared error which exists between the two images. Greater value of MSE corresponds to the better security. Besides, this greater value of MSE leads to the smaller value of PSNR. Hence relatively low value for the metric PSNR is always desirable.
Table 17 shows the PSNR values got by different techniques in the literature. According to the table, the value of this security parameter (O-D) is infinity Inf for all the chosen images. This phenomenon denotes to the fact that both the original image and the decrypted image are ‘verbatim.’ In other words, they are exactly the same. It further means that the proposed cipher is lossless. Besides, the suggested algorithm gave its smallest value for Lena image which is better than those in [32, 42, 60].
5.9 Noise and data loss/crop attacks
Every day world is very precarious and uncertain. Things do not operate always as they are expected. As the cipher images are stored on some gadget or are transmitted from one point to the other, they are occasionally subjected to the noise attack due to which they become polluted. Sometimes, a portion of the cipher image is also lost often called data loss/data crop attack. Enduring the noise and data crop attacks on the ciphered images is a built-in feature of the image cryptosystems. In order to show that the suggested cryptosystem is defiant to these attacks, we have mixed Pepper & Salt noise with densities 0.1, 0.2, 0.3 and 0.4 in the encrypted images of Lena, Baboon, Brain and Truck respectively. Figure 11a – d show them. As the decryption algorithm gets applied over them, we get the restored images in the Fig. 11e – h. One can easily appreciate the images which points out the fact that suggested cipher is immune to the noise attack.
Pepper & Salt noise attack on the encrypted images with the noise density:(a) Lena image, 0.1; (b) Baboon image, 0.2; (c) Brain image, 0.3; (d) Truck image, 0.4; (e) Restored image Lena from (a); (f) Restored image Baboon from (b); (g) Restored image Brain from (c); (h) Restored image Truck from (d)
Apart from that, cipher images of Lena, Baboon and Butterfly are plotted in the Fig. 12a to c with diverse attacks of data losss. Later on, in order to recover the original plain images, these cropped cipher images have been decrypted by applying the decryption algorithm over them. Figure 12d to f plot the restored images. These plotted images assert that potential cryptosystem has the power to endure data crop threats as well.
5.10 Speed performance and complexity analysis
The proposed cipher has been written under Intel(R) Core(TM) i7-3740QM CPU @ 2.70GHz, RAM = 8.00 GB, System Type: 64-bit Operating System, x64-based processor.
Security is such a feature in the realm of cryptography that no compromise can be made over it. At the same time, cryptographic products taking relatively less time find more opportunities for their real world applications. There exist two methods to analyze the performance of some algorithm in academia and industry. The first one through a straightforward observation of the time, the cipher takes in giving its results. In this method, some timing device like stopwatch can be used. Although this method is very simple but it has some drawbacks. The observed results do not correspond the inherent, intrinsic and innate property of the algorithm vis-à-vis time. Many factors contaminate its performance like particular input, particular software, particular hardware etc. To avoid these particularities, we require a setting which may lead us to the exact performance of the designed algorithm. Luckily such a setting exists called theoretical analysis. In this analysis, theory of mathematics called Asymptotics [38] is normally employed. In this study, we have carried out both of these analyses. The Table 18 gives us the time taken by the proposed algorithm upon the different chosen images. Besides, a comparison is drawn. The suggested scheme performs better only than [3]. Its reason is that we have incorporated the DNA operations in the cipher which take more time for their execution.
Encryption throughput (ET) is an other way for measuring the efficiency of some image cipher. Through this metric, we may know the quantity of image being encrypted in the given time. Its mathematics is
The last and the third column of Table 18 shows the values of ET for the proposed cipher. Again the proposed cipher only beats [3] as far as ET is concerned.
In theoretical analysis of time complexity, normally two factors are reckoned with, i.e., generation of key streams (Subsection 3.1) and the encryption scheme (Subsection 3.2). Step 3 of Subsection 3.1 contributes Θ(mn + 2m + 2n) to the complexity since 1 ≤ i ≤ m, 1 ≤ j ≤ n and 1 ≤ k ≤ mn.
Table 19 shows the time complexity of each step of the proposed encryption algorithm. In the decimal level confusion, two nested for loops on the lines (1-2) of Algorithm 1 iterate mn times. Same is being happened at the lines (4-5). So Algorithm 1 is contributing Θ(2mn) to the complexity. It is to be noted that this algorithm has been called by the operation of decimal level confusion. Through the (9), the purpose of decimal level diffusion is being served which contributes Θ(mn) to the complexity. Step 3 is for DNA encoding and its contribution to the complexity is Θ(2mn), Θ(mn) for image img3 and Θ(mn) for the key − image as given in the (10). The complexity of DNA level confusion in Step 4 is Θ(2mn) which is the same as the complexity of the decimal level confusion operation. Its reason is that the same algorithm has been invoked for both the operations. The complexity of the DNA level diffusion operation at Step 5 is Θ(mn) (11). Lastly the cost for Step 6 about the decimal conversion of DNA is Θ(mn) (12). By adding all these costs, we get Θ(9mn). The total time complexity comes out to be Θ(10mn) after adding Θ(mn + 2m + 2n) and Θ(9mn) and ignoring the lower order terms. The time complexity Θ(10mn) of the proposed algorithm is better than Θ(24mn) [47] and Θ(24mn) [7].
6 Conclusion
Leveraging upon the chaotic system and DNA cryptography, a novel image encryption scheme for the gray scale images has been proposed in this study. Confusion and diffusion are the principal operations for any cryptography product. Both of these operations have been carried out at the decimal and DNA levels. The five key streams rendered by the chaotic system have been recycled again and again in the proposed cipher. It served the two-fold purpose. On the one hand, it helped to use the minimum system resources and on the other hand, it intensified security. A novel idea of scrambling has been employed in this study. As the gray scale image is input, its two rows are chosen randomly for a number of times. By fixing these two chosen rows, its randomly selected pixels are swapped with each other for arbitrary times. Same operation of swapping has been performed by fixing two columns. At the DNA level, swapping of the DNA strands has been done in the same way as was done at the decimal level but with different chaotic data. To realize the confusion effects, XOR operation has been conducted both at the decimal and DNA levels. The simulation and the comprehensive security analysis of the cipher depict the good security effects, resistance to the varied threats from the community of cryptanalysts and potential for the real world application in the industry.
References
Abdelfattah RI, Mohamed H, Nasr ME (2020) Secure image encryption scheme based on DNA and new multi chaotic map. Journal of Physics: Conference Series 1447(1):012053
Babaei M (2013) A novel text and image encryption method based on chaos theory and DNA computing. Nat Comput 12(1):101–107
Bashir Z, Iqbal N, Hanif M (2021) A novel gray scale image encryption scheme based on pixels’ swapping operations. Multimedia Tools and Applications 80(1):1029–1054
Boreale M (2020) Complete algorithms for algebraic strongest postconditions and weakest preconditions in polynomial odes. Sci Comput Program 193:102441
Broumandnia A (2019) The 3D modular chaotic map to digital color image encryption. Futur Gener Comput Syst 99:489–499
Chai X, Chen Y, Broyde L (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng 88:197–213
Chai X, Fu X, Gan Z, Lu Y, Chen Y (2019) A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process 155:44–62
Chai Xiuli, et al. (2019) A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput Applic 31(1):219–237
Chen L, Ma B, Zhao X, Wang S (2017) Differential cryptanalysis of a novel image encryption algorithm based on chaos and Line map. Nonlinear Dynamics 87(3):1797–1807
Chen G, Mao Y, Chui CK (2004) A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Solitons & Fractals 21(3):749–761
ElKamchouchi DH, Mohamed HG, Moussa KH (2020) A bijective image encryption system based on hybrid chaotic map diffusion and DNA confusion. Entropy 22(2):180
Enayatifar R, Sadaei HJ, Abdullah AH, Lee M, Isnin IF (2015) A novel chaotic based image encryption using a hybrid model of deoxyribonucleic acid and cellular automata. Opt Lasers Eng 71:33–41
Farah MB, Farah A, Farah T (2019) An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dynamics, pp 1–24
Floating-Point Working Group (1985) IEEE Computer society: IEEE standard for binary floating-point arithmetic, Standard, pp 754–1985
Guesmi R, Farah MB (2021) A new efficient medical image cipher based on hybrid chaotic map and DNA code. Multimedia Tools and Applications 80(2):1925–1944
Guesmi R, Farah MAB, Kachouri A, Samet M (2016) A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dynamics 83(3):1123–1136
Hoang TM, Thanh HX (2018) Cryptanalysis and security improvement for a symmetric color image encryption algorithm. Optik 155:366–383
Iqbal N, Abbas S, Khan MA, Alyas T, Fatima A, Ahmad A (2019) An RGB image cipher using chaotic systems, 15-Puzzle problem and DNA computing. IEEE Access 7:174051–174071
Iqbal N, Abbas S, Khan MA, Fatima A, Ahmed A, Anwer N (2020) Efficient image cipher based on the movement of king on the chessboard and chaotic system. Journal of Electronic Imaging 29(2):023025
Iqbal N, Hanif M, Abbas S, Khan MA, Rehman ZU (2021) Dynamic 3D scrambled image based RGB image encryption scheme using hyperchaotic system and DNA encoding. J Inform Secur Appl 58:102809
King OD, Gaborit P (2007) Binary templates for comma-free DNA codes. Discret Appl Math 155(6-7):831–839
Kulsoom A, Xiao D, Abbas SA (2016) An efficient and noise resistive selective image encryption scheme for gray images based on chaotic maps and DNA complementary rules. Multimedia Tools and Applications 75(1):1–23
Li S, Li C, Chen G, Zhang D, Bourbakis NG (2004) A general cryptanalysis of permutation-only multimedia encryption algorithms. IACR’s Cryptology ePrint Archive: Report 374
Li C, Lo KT (2011) Optimal quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process 91(4):949–954
Li Y, Wang C, Chen H (2017) A hyper-chaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Opt Lasers Eng 90:238–246
Liao X, Hahsmi MA, Haider R (2018) An efficient mixed inter-intra pixels substitution at 2bits-level for image encryption technique using DNA and chaos. Optik-International Journal for Light and Electron Optics 153:117–134
Liao X, Kulsoom A, Ullah S (2016) A modified (Dual) fusion technique for image encryption using SHA-256 hash and multiple chaotic maps. Multimedia Tools and Applications 75(18):11241–11266
Liu L, Zhang Q, Wei X (2012) A RGB image encryption algorithm based on DNA encoding and chaos map. Computers & Electrical Engineering 38 (5):1240–1248
Loukhaoukha K, Chouinard JY, Berdai A (2012) A secure image encryption algorithm based on Rubik’s cube principle. Journal of Electrical and Computer Engineering, 2012
Nestor T, De Dieu NJ, Jacques K, Yves EJ, Iliyasu AM, El-Latif A, Ahmed A (2020) A multidimensional hyperjerk oscillator: Dynamics analysis, analogue and embedded systems implementation, and its application as a cryptosystem. Sensors 20(1):83
Njitacke ZT, Isaac SD, Nestor T, Kengne J (2020) Window of multistability and its control in a simple 3D Hopfield neural network: application to biomedical image encryption. Neural Comput Applic, pp 1–20
Norouzi B, Mirzakuchaki S (2014) A fast color image encryption algorithm based on hyper-chaotic systems. Nonlinear Dynamics 78(2):995–1015
Özkaynak F, Özer AB (2016) Cryptanalysis of a new image encryption algorithm based on chaos. Optik 127(13):5190–5192
Özkaynak F, Özer AB, Yavuz S (2013) Security analysis of an image encryption algorithm based on chaos and DNA encoding. In: 2013 21st signal processing and communications applications conference (SIU), IEEE, pp 1–4
Parvin Z, Seyedarabi H, Shamsi M (2016) A new secure and sensitive image encryption scheme based on new substitution with chaotic function. Multimedia Tools and Applications 75(17):10631–10648
Patro KAK, Babu MPJ, Kumar KP, Acharya B (2020) Dual-layer DNA-encoding–decoding operation based image encryption using one-dimensional chaotic map. Advances in Data and Information Sciences 94:67–80
Qayyum A, Ahmad J, Boulila W, Rubaiee S, Masood F, Khan F, Buchanan WJ (2020) Chaos-based confusion and diffusion of image pixels using dynamic substitution. IEEE Access 8:140876–140895
Ramesh VP, Gowtham R (2017) Asymptotic notations and its applications. Ramanujan Math Soc Math Newsl 28(4):10–16
Shannon CE (1949) Communication theory of secrecy systems. The Bell System Technical Journal 28(4):656–715
Sivakumar T, Venkatesan R (2016) A new image encryption method based on knight’s travel path and true random number. J Inform Sci Eng 32 (1):133–152
Tamang J, Nkapkop JDD, Ijaz MF, Prasad PK, Tsafack N, Saha A, Son Y (2021) Dynamical properties of ion-acoustic waves in space plasma and its application to image encryption. IEEE Access 9:18762–18782
Taneja N, Raman B, Gupta I (2012) Combinational domain encryption for still visual data. Multimedia Tools and Applications 59(3):775–793
Wang X, Gao S (2020) Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a Boolean network. Inform Sci 539:195–214
Wang X, Wang Y, Zhu X, Luo C (2020) A novel chaotic algorithm for image encryption utilizing one-time pad based on pixel level and DNA level. Opt Lasers Eng 125:105851
Wang B, Zhang BF, Liu XW (2021) An image encryption approach on the basis of a time delay chaotic system. Optik 225:165737
Wu J, Liao X, Yang B (2018) Cryptanalysis and enhancements of image encryption based on three-dimensional bit matrix permutation. Signal Process 142:292–300
Wu X, Wang K, Wang X, Kan H, Kurths J (2018) Color image DNA encryption using NCA map-based CML and one-time keys. Signal Process 148:272–287
Xiong Z, Wu Y, Ye C, Zhang X, Xu F (2019) Color image chaos encryption algorithm combining CRC and nine palace map. Multimedia Tools and Applications 78(22):31035–31055
Xu L, Li Z, Li J, Hua W (2016) A novel bit-level image encryption algorithm based on chaotic maps. Opt Lasers Eng 78:17–25
Yavuz E, Yazıcı R, Kasapbaşı MC, Yamaç E (2016) A chaos-based image encryption algorithm with simple logical functions. Computers & Electrical Engineering 54:471–483
Yu C, Li J, Li X, Ren X, Gupta BB (2018) Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimedia Tools and Applications 77(4):4585–4608
Zaman JKMS, Ghosh R (2012) Review on fifteen Statistical Tests proposed by NIST. Journal of Theoretical Physics and Cryptography 1:18–31
Zhang Q, Guo L, Wei X (2010) Image encryption using DNA addition combining with chaotic maps. Math Comput Model 52(11-12):2028–2035
Zhang Q, Guo L, Wei X (2013) A novel image fusion encryption algorithm based on DNA sequence operation and hyper-chaotic system. Optik-International Journal for Light and Electron Optics 124(18):3596–3600
Zhang YQ, Wang XY (2015) A new image encryption algorithm based on non-adjacent coupled map lattices. Appl Soft Comput 26:10–20
Zhang W, Wong KW, Yu H, Zhu ZL (2013) A symmetric color image encryption algorithm using the intrinsic features of bit distributions. Commun Nonlinear Sci Numer Simul 18(3):584–600
Zhang Y, Xu P, Xiang L (2012) Research of image encryption algorithm based on chaotic magic square. In Advances in Electronic Commerce. Web Application and Communication 149:103–109
Zhang W, Yu H, Zhao YL, Zhu ZL (2016) Image encryption based on three-dimensional bit matrix permutation. Signal Process 118:36–50
Zhou G, Zhang D, Liu Y, Yuan Y, Liu Q (2015) A novel image encryption algorithm based on chaos and Line map. Neurocomputing 169:150–157
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. Opt Commun 285(1):29–37
Zhu ZL, Zhang W, Wong KW, Yu H (2011) A chaos-based symmetric image encryption scheme using a bit-level permutation. Inf Sci 181(6):1171–1186
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Iqbal, N., Hanif, M., Rehman, Z.U. et al. On the novel image encryption based on chaotic system and DNA computing. Multimed Tools Appl 81, 8107–8137 (2022). https://doi.org/10.1007/s11042-022-11912-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-11912-5