Abstract
Watermarking has been suggested as a generic technique to solve various problems associated with topics in the areas of digital rights management and multimedia security. Most of the early methods were based on single watermark embedding, but there are great limitations when single watermark embedding algorithms are tried into practical applications. The multiple watermarks are intended to convey different information at the same time. Current approaches rely on adding many watermarks in different bands or channels by means of scaling factor and embedding locations that are mainly defined by experts. This brought many challenges in achieving equilibrium between security, robustness, and quality. The aim of this work is to introduce an intelligent dual watermarking model for colour images that ensure image security for copyright protection (dual watermarking for single purpose). To optimize the dual watermarking requirements, the proposed model that employs both successive (re-) and segmented watermarking techniques is to be implemented with a multi-purpose evolutionary algorithm. Genetic algorithm is adopted to determine the embedding locations and scaling factors for different watermarks according to the features of each host image to balance between imperceptibility and robustness. The wavelet transform is utilized for salient features extraction because of its excellent space-frequency localization of salient image features. In addition, the suggested model encrypts the watermarks with the aid of Walsh transform; so that it is difficult to handle the watermarks even after being extracted by the attackers. Experimental results show that the proposed model is more robust against common image manipulation attacks in terms of PSNR and NCC.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Extraordinary growth of Internet, peer-to-peer file sharing, and signal processing technologies have made the reproduction, manipulation, and distribution of multimedia data much easier than ever before. This unavoidably increases the demand for protection of copyrighted data. Digital watermarking is a promising technology for copyright protection [36]. Digital image watermarking techniques can be classified into [29, 48]: spatial and transform domain watermarking based on embedding domain of the host image. The watermark embedding techniques in spatial domain insert watermark directly by modifying the pixel value of the cover image. This technique has less computation time; however, it is less secure and not as robust as the frequency domain. The frequency domain embedded technique transforms data from the spatial domain into the frequency domain (reveals the most features of the image), and then embedded the hidden data in the image. This transform domain can strengthen resistance under attacks, and increase security.
To understand the concept of watermarking, a clear understanding of the difference between watermarking and other techniques like steganography, cryptography, and digital signature for data /image protection is required [6, 7, 9, 10, 21,22,23]. In steganography, data which is concealed has no association with the cover medium, and the necessity from such a system is that no suspicion should arise that a medium is carrying any concealed data. Watermarking is the subclass of steganography, but in this case, the data which is hidden has an association with the cover medium data. Cryptography scrambles a message so that it cannot be understood by unauthorized user. This does not happen in watermarking. Neither the cover medium nor the copyright data change its meaning [4, 8, 11, 12, 20]. Rather, copyright data is hidden to give the ownership information of the medium in which it is hidden. A digital signature validates the authenticity and integrity of a message, whereas a digital watermark is inside a multimedia message. Both digital signature and watermarking protect the integrity and authenticity of a document. A digital signature system is vulnerable to distortion, but a watermark system has to tolerate a limited distortion level [1, 13, 14, 17,18,19, 24, 25, 27, 28, 41, 54].
In order to identify and maintain proof of ownership, we need to extract watermark after embedding a watermark image in the host image. The extraction techniques of a watermark from the watermarked images are: blind, semi-blind, and non-blind. Blind watermarking does not need the original image to extract the embedded watermark from a watermarked image. The semi-blind watermarking technique needs some information about the original cover image to extract the embedded watermark. The Non-blind watermarking technique requires the complete cover image to extract the embedded watermark. Each watermark should follow its properties like robustness, imperceptibility, capacity, and security [2, 3, 16].
More recently, different watermarking strategies have been suggested in order to solve several problems, ranging from the detection of content manipulations to information hiding, to document usage tracing [35, 46]. Most of the early methods were based on single watermark embedding, but there are great limitations when single watermark embedding algorithms are tried into practical applications in few rare situations, like when multiple users share the copyright, it needs to support multiple users to embed their watermarks synchronously. This highlights the needs for multiple watermark embedding. Multiple watermarks are normally suggested as a method to provide extra security to an image by embedding two or more secret messages into the cover image. To advocate several goals, the multiple watermarks are embedded into the image; to achieve the robustness of image processing operations, which is the desired goal [37].
Unfortunately, there are still some problems that facing dual watermarking approaches and mainly depend on several different factors [31, 37, 43]: (1) adding multiple watermarks (noises) affect the perceptibility (quality) of the cover image. (2) The watermarks must be independent of each other during embedding and extraction phases. (3) The embedding of each watermark should be at a different location that must be known exactly at the extraction phase; i.e., the system requires extra data to save these locations and therefore needs extra payload. In general, building a robust dual image watermarking scheme that tackles the above challenges is required for many applications such as copyright protection, data integrity, tamper detection, fingerprinting, and broadcast monitoring. The attention here is to deal with the tradeoff between watermark capacity, extra payload, computational cost, and imperceptibility.
Recently several approaches have been presented that attempt to tackle the above problems. The existing multiple watermarking algorithms can be divided into three classes, namely: re-watermarking, composite watermarking, and segmented watermarking [31, 34, 38]. In re-watermarking, the watermarks are simply embedded one after the other. The problem which arises is that the watermarks interfere with each other. As a consequence, earlier embedded watermarks possibly get erased by later embedded ones. The advantage is that the embedders do not need to know each other and also the number of watermarks to embed do not need to be known in advance. Composite watermarking builds a single composite watermark from a collection of watermarks and then embeds the composite watermark into the cover image in a usual way. Suitable signal merging methods are required for increased performance. This approach has the need for a trusted party which does the composition and embedding of the single watermarks, and all watermarks have to be present at once.
Regarding segmented watermarking, it divides the cover image into several partitions and allocates each partition for a different watermark. Here, the number of divisions limits the number of watermark signals to be embedded. Besides, when the number of watermarks increases the size of each block decreases. Furthermore, the location of the embedding partitions has to be opened to the embedding algorithm, and each embedding algorithm has to know which partitions are already occupied. This type is one of the most commonly used algorithms. In all cases, it must be confirmed that the embedded watermark is not easily lost, and imperceptibility is also preserved [34, 51]. Recently, integrating the genetic algorithm (GA) into a watermarking scheme to improve its performance and effectiveness has received a great deal of attention among researchers working in this field [35, 36].
1.1 Problem statement
Current multiple watermarking approaches were introduced lately only to be found that they relied only on adding many watermarks in different bands or channels by means of a scaling factor and embedding locations that are mainly defined by experts. This brought many challenges in achieving a balance between security, robustness, and quality since each one can be achieved at the expense of the other and combining them does not give the ideal result. Attempting to attain the suitable trade-off between the previously mentioned requirements, this work is constructed to dispense the opinion of experts by replacing it with intelligent multiple watermarking schemes. However; this needed to bring certain facts about the image that response to various attacks after doing minor changes in the image that does not lead to any distortion or noise in the image which it’s a problem itself.
1.2 Motivation of the work
Motivated by the challenges that are facing dual watermarking approaches and in order to cope with them, in this paper, the aim is to introduce an intelligent dual watermarking scheme for colour images that ensure the image can be used in a secure manner for copyright protection. To accomplish such goal, a multi-purpose evolutionary algorithm is presented to optimize additive embedding’s scaling factor with the purpose of enhancing embedding strength that affects imperceptibility. Furthermore, it employs the same genetic algorithm with different fitness function to find the optimal embedding locations to achieve robustness against different types of attacks.
1.3 Novelty, contribution, and methodology
The novelty of the suggested model lies on the fusion of dual watermarks from re- and segmented watermarking classes in which both of them is positioned in different locations for easy extraction without affecting the perceptibility of the cover image and quality of the extracted watermarks. The configuration parameters of the fusion process (scaling factor and embedding locations) are semantically determined based on the features of both cover and watermarks images. Aiming to fill the gap of the stationary scaling factor and embedding locations inside existing dual image watermarking approaches, the proposed model adopts GA to find the optimality of these issues that will enhance both of watermarking capacity and imperceptibility in colour images.
To enhance the overall performance, the suggested system relies on (1) YCbCr colour space that is employed in order to take advantage of the lower resolution capability of the human visual system for colour with respect to luminosity. (2) Walsh Hadamard Transform (WHT) that is used to secure dual watermarks. (3) Discrete Wavelet Transform (DWT) that is exploited to enhance imperceptibility by highlighting the most important features appropriate for embedding. (4) Singular Value Decomposition (SVD) that is engaged for matrix factorization to obtain a smaller set of values which has maximum signal content (i.e., dimension reduction to cope with embedding computational cost). Herein, the embedding is within the different colour channels to increase the capacity and achieve multi-purpose watermarking such as copyright protection and content integrity.
The rest of this paper is organized as follows: Section 2 describes some of the recent related works. The detailed description of the proposed model has been made in Section 3. In Section 4, the results and discussions on the dataset are given. Finally, the conclusion is annotated in Section 5.
2 Literature review
Conventional single watermark systems are mainly aimed at accomplishing a single goal, either for forgery detection or image copyright protection [36]. This limitation has resulted in the introduction of multipurpose (multifunction watermarking) and multiple watermarking algorithms. However, most of the recent studies have not indicated a clear distinction between multipurpose and multiple watermark (or cocktail watermarking) algorithms [15, 33, 39, 52, 53]. In order to solve the dual watermarking problems described above, the authors in [46] have suggested applying a de-interlacing process on the transformation sub-bands of host image according to its even and odd row pixel value. It focuses on the robustness, imperceptibility, and capacity of the watermark in frequency domain against the unintentional and the intentional signals/distortion at the expense of the original image which can be modified due to piracy actions before embedding.
In recent years, swarm-based evolutionary algorithms have been received much attention from researchers [44, 45]. For instance, the authors in [45] presented a novel multiple objective optimized dual watermarking scheme for medical colour images. This approach integrated both of LWT domain and dual optimization technique that combines firefly and bat algorithms. The multiple objectives are perceptual quality, security, and robustness. Yet this method lacks immunity to geometric attack and has very complex computational processes.
In a recent study [43], the authors explored the multipurpose watermarking to hide both copyright and authentication information in the content of multiple watermarking. For this purpose, a wavelet transformation based on texture properties and secret sharing using visual cryptography is used. This scheme is highly robust, does not degrade the original signal, and very efficient in terms of quality. This method lacks the ability to be implemented on colour textures. Concurrently, in 2012, Liao [29] had examined other aspects of visual cryptography, wavelet transformation domain, and YCbCr colour model required to assure the re-watermarking concept in which all owners will have dual watermark authentication embedded in a protected colour image, and the number of ownership can be increased without re-computing.
Research reveals that all of the benefits of RGB color space are not attained as expected as there are many challenges and risk in this color space that work as barriers in the success of the RGB color space and make it more difficult to achieve expected benefits. To solve this problem, the author in [32] produced a novel hybrid digital watermarking technique based on the exploitation of both RGB and YCbCr colour spaces using spatial domain techniques. This method possessed invisibility, robustness, security, capacity, and complexity characteristics as opposed to the majority of methods which tend to focus only on invisibility and robustness. Yet the image will not survive under compression attack and will lose its commercial value in commercial images databases.
In another work, in 2013, Ouazzane et al. [38] highlighted the main concepts behind multiple levels transformation-based multiple watermarking along with two complementary directions: a “high-level”, and “low-level”. The authors analyzed the robustness and imperceptibility of watermarks in high and low-frequency sub-band at first and second level and find that second level is better than the first level in terms of robustness and imperceptibility at the expense of embedding capacity, watermarked image quality, and computational complexity. At present, wavelet and other frequency domain transformations have become a cutting edge and promising approach in the field of multiple images watermarking. For instance, the authors in [51] presented a proficient implementation of an authorized dual image watermarking system based on discrete wavelet Transform for medical data protection. It appears that by embedding both watermarks into one image, one could achieve extremely high robustness properties in a secure manner concerning a large spectrum of image processing operations.
The work in [15] suggested a new multiple watermarking approach in vector data rather than raster data. Based on the characteristics of vector data, the multiple watermarks were embedded additively in the cover data following additively rule. In the detection progress, the additive watermarks were extracted, and then the contents of watermarks were detected on the basis of correlation detection together with discriminant analysis. Since the embedding rule is additively in the paper, the suggested scheme requires the original data coordinates that require extra space. In [53], a novel intelligent multiple watermarking techniques for integrity and copyright protection for information present in the source document image is presented. The sensitivity of the information content of a block is based on the homogeneity and relative energy contribution parameters. The appropriate watermarking scheme is applied based on sensitivity classification of the block. Although identifying each block sensitivity requires more accurate classification approaches.
Some works have been done recently for multi-purpose watermarking of medical images. For instance, the concept of signature watermark embedding using error-correcting code is investigated in [5]. In this case, the medical image is divided into two parts, namely Region of Interest (ROI) and Region of Non-Interest (RONI). The reference watermark which is used to detect the authenticity of medical images (integrity control) is embedded in the ROI image. Meanwhile, the signature watermark, which is used for the authority of ownership (proprietary rights) is embedded in the RONI image on the wavelet domain. This method reduced computational time at the expense of image quality, even though it is good still not significant.
Although image dual watermarking has been studied for a few decades, there is still room to make it more efficient and practical in real applications. According to the aforementioned review, it can be found that past studies were primarily devoted to: (1) devising different type of watermarking either multi-objective or multi-purpose watermarking that employs the image information (color spaces, regional statistics, salient image features, and image frequency domain), (2) Not addressing the issues associated with the choice of appropriate scaling factor for embedding (manually adjusted), and (3) Embedding locations are usually identified randomly or according to criteria that do not consider image characteristics into account. However, to the best of our knowledge, little attention has been paid to advising new optimal selection algorithm to determine both of scaling factor and embedding locations and improving its efficiency in the multi-watermarking algorithm as well.
3 The proposed dual watermarking model
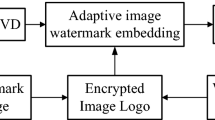
This paper proposes a new method that combines both of the first and third watermarking categories (Re-watermarking and segmented) that does not rely on supervised training for determining pixel embedding locations. Furthermore, the original image is segmented into several parts, and each watermark is embedded into the specific share. In this case, the embedding process is based on two overlapped segmented areas, including color channels and wavelet sub-bands. This interleaving makes it hard to know the embedding locations and increases the efficiency of the watermark in facing various types of attacks. Besides, it takes the human visual system into consideration by embedding in specific color channels. The main diagram of the suggested hybrid dual watermarking is depicted in Fig. 1. The following subsections describe in details the steps of the system.
3.1 Problem formulation
A basic dual watermarking scheme for digital image can be defined as a 4-tuple (I, W, E, D) such that [29] [31, 34, 35, 37, 38, 43, 46]:
I, the image data space (original un-watermarked image data), which is a set of pixels with value in the positive integers Z+ = {| a| ≥0 : a ∈ Z}. Each pixel is a set of coordinates, (x, y) for 2D space. An element of image data space is called an image of a × b size for 2D space, a, b ∈ Z+ and x = {1, 2, 3...a}, andy = {1, 2, 3...b}. \( W=\left\{{w}_1,{w}_2\right\},\hat{I},\overline{I}, \) and \( \tilde{I} \) are the subsets of I, where:
w1 ∈ W is the set of image data used for first watermark generation and w1 ∩ I = φ;
w2 ∈ W is the set of image data used for second watermark generation and w2 ∩ I = φ;
\( \overline{I} \) is the set of watermarked image data;
\( \tilde{I} \) is the set of estimated original image data;
\( {\tilde{w}}_1 \) is the set of estimated of first image watermark.
\( {\tilde{w}}_2 \)is the set of estimated of second image watermark.
E is a function \( E:I\times W\to \overline{I} \) that is used for watermarks embedding.
D is a function\( D:\overline{I}\times W\times \perp \to \tilde{I}\times {\tilde{w}}_1\times \tilde{w} \)that is used for watermark extraction, where ⊥ = {⊥1, ⊥2}indicates the embedding locations.
The dual watermarks w1 and w2 are valid if and only if they are obtained from valid inputs \( \left(\overline{I},\perp \right) \)using the valid first and second watermarks generation function W. Similarly, a watermarked image, \( \overline{I} \) is valid if and only if \( E\left(I,{w}_1,{w}_2\right)=\overline{I} \)for valid inputs, (I × W). More formally, we can define a digital image watermarking scheme to be complete, if the following is true: for I, w1, w2 there exists \( \tilde{I},{\tilde{w}}_1,{\tilde{w}}_2 \) where \( I\approx \tilde{I},{w}_1\approx {\tilde{w}}_1,{w}_2\approx {\tilde{w}}_2 \) such that\( D\left(E\left(I,W\right),\left(I,W\right)\right)=\left(\tilde{I},{\tilde{w}}_1,{\tilde{w}}_2\right) \). Here, the symbol ‘≈’ denotes the perceptual similarity between two images.
3.2 Watermarking embedding stage
Watermark embedding function considers where and how to embed the watermarks satisfying various requirements of the cover images. An embedding function takes the dual watermarks, w1, w2 and the original image data, I as input to output the watermarked image data, \( \overline{I} \). The following steps are performed to embed two grayscale images as watermarks inside a color RGB cover image.
- Step 1:
Converting into YCbCrColour Space
The cover image is converted to YCbCr colour space as it is better to model the human colour perception. This type of colour space allows more precise colour detectors to be created since colour intensity is removed when viewing the Cr or Cb vectors [31] [32] . Herein, the embedding is performed in Y, and Cb channels as the luminance channel represents the intensity of the image; it is the ideal space for data hiding whenever tolerance against JPEG compression and noise addition are the most important concerns; whereas the chrominance channel, Cb channel has more ability to defeat various types of attacks compared to chrominance space Cr [36].
- Step 2:
Securing Watermarks using WHT
The suggested model encrypts the watermarks to increase the security; so that it is difficult to handle the watermarks even after being extracted by the attackers. Herein, the WHT is employed because it contains only ±1, and no multiplications are required in the computation. The advantages of Hadamard transform include that its elements are real, and its rows and columns are orthogonal to each other [40]. The Hadamard matrix of m order is the (±1) matrix with a size of m × m, Hm satisfying the orthogonal condition:
where H is the Hadamard matrix, T is a transposition sign, Am is an identity matrix of m order that represents the number of rows and columns in the watermark image (square image in our case). One of the well-known Hadamard matrices is the Silvester matrix, which is a matrix of order 2k and can be recursively generated as follows:
\( {H}_{2^k} \) is the watermark encrypted matrix, and \( {H}_m^{-1} \) is the watermark decrypted matrix [40].
-
Step 3:
Salient Features Extraction using DWT
DWT is more frequently used in digital image watermarking due to its excellent spatial localization and multi-resolution techniques [38, 48]. The excellent spatial localization property is very convenient to recognize the area in the cover image in which the watermarks are embedded efficiently. DWT decomposes the image into four sub-bands (level 1); the LL sub-band represents the coarse-scale of DWT coefficients while the other sub-bands LH, HL, and HH represent the fine-scale of DWT coefficients. In general, most of the image energy is found at the LL sub-band and therefore, the embedding of the watermarks in other sub-bands may degrade the quality of image [39]. Informal, the wavelet decomposition can be described as [5] [30]:
where φ is the wavelet function and j, k, and p are integers represent scale (wavelet’s width) and dilate (vertical and horizontal positions) the wavelet function. The function Φ(x) is the scaling function. h0, h1, , ..., hN − 1 are the low pass wavelet coefficients, and g0, g1, ..., gN − 1are the high pass wavelet coefficients, and N is the number of vanishing moments. DWT is applied on both the cover image in addition to the dual encrypted watermarks for the selected channels only.
- Step 4:
Step 4: Dimension Reduction using SVD
SVD is a matrix decomposition to obtain a smaller set of values which has maximum signal content from the derived wavelet coefficients [30]. These singular values represent the most energy of the signal. Because of translation, scaling properties of SVD it can be used as a tool to develop watermarking schemes [49]. The system applies SVD to the LL band for image watermarks in which for a given two matrices \( W{T}_{LL,{w}_1},W{T}_{LL,{w}_2} \)of size n × n, SVD operation decomposes it to three different matrices U, S, and V such that [30, 49]:
where ui ∈ U and vi ∈ V are the left and right singular vectors respectively, S = diag (λi) is a diagonal matrix of singular values λi, i = 1, ..., n. For applying SVD to the cover image, the model divides each LL band of the selected channels into blocks of equal size to the LL band of the watermarks. After that, the SVD is applied for each block resulting \( {\lambda}_{I,{B}_i} \) for each color channel. The number of vectors λI depends on the number of blocks B calculated by dividing the size of LL band of the cover image on the size of the watermark. The rationale of using SVD is that when a small perturbation is added to an image, the large variety of its singular values of S matrix does not occur, furthermore, it represents intrinsic algebraic image properties [49].
- Step 5:
Determining Optimal Embedding Positions and Scaling Factor
In general, determining the scaling factor for additive watermarking to control the strength of watermarks embedding is an important parameter to satisfy the perceptibility even when dual watermarks are embedded. Furthermore, finding the paramount locations for the watermarks embedding to achieve optimal robustness against various types of attacks represents an essential requirement for watermarking schemes [35, 36, 48]. The strength of embedding watermark and embedding locations are determined by utilizing the GA method to balance the robustness and perceptual transparency requirements [48] [49].
Given the singular values for every block of the selected cover image’s color channels SI, Cb, Bi, SI, Y, Bi and singular values of gray-scale watermark images \( {S}_{w_1},{S}_{w_2} \); the algorithm first normalizes the singular values of the watermarks besides a random block, then the initial scaling factor Ω for that random block is calculated by aggregating the watermarks vector values \( {S}_{w_1},{S}_{w_2} \) and dividing them by the aggregated vector values in the block SI, Cb, Bi, SI, Y, Bi [35, 36, 48]:
r is length of S = diag (λi); this initial value for the block is used to embed \( {S}_{w_1} \) in the corresponding block of SI, Cb, Bi and \( {S}_{w_2} \) in SI, Cb, Bi using additive embedding. The rational of using this type of embedding is that it gives better quality and less distortion as compared to other embedding techniques in frequency domain [48] [49].
\( {\overline{S}}_{I, Cb, Bi},{\overline{S}}_{I,Y, Bi} \) are the result of the embedding both watermarks respectively in the randomly selected channel block. Then these modified singular values are combined with their left and right singular vectors of that random block by employing inverse SVD to get the watermarked LL band for each colour channel [49].
After that, each watermarked LL band is combined with the other unaltered bands to form the watermarked colour channels \( {Y}_W^{\prime },\mathrm{and}\ C{b}_W^{\prime } \). The three colour channels are then merged to get the watermarked image in YCbCr colour space; that are converted to RGB colour space to get watermarked image \( \overline{I} \) [34, 36, 48].
Given the initial watermarked image, the next step is to optimize the embedding locations by utilizing GA besides the optimal scaling factor given a specific objective function. In this case, an instance of a GA-based dual watermarking optimization problem can be described in a formal way as a four- tuple (P, Q, ζ, f) defined as [47, 49]:
P is the solution space (initial population – a combination of 2n indexed blocks) where n represent the number of bits needed to represent the block index. Each bit is signified as a gene and every block is represented as a chromosome.
Q is the feasibility predicate (different operators- selection, crossover, and mutation). The crossover is the process of exchanging the parent’s genes to produce one or two offspring that carry inherent genes from both parents to increase the diversity of the mutated individuals. Herein, a single point crossover is employed because of its simplicity. The purpose of mutation is to prevent falling into a locally optimal solution of the solved problem; a uniform mutation is employed for its simple implementation. The selection operator retains the best fitting chromosome of one generation and selects the fixed numbers of parent chromosomes. Tournament selection is probably the most popular selection method in the genetic algorithm due to its efficiency and simple implementation.
ζis the set of feasible solutions (new generation populations). With these new generations, the fittest chromosome will represent the best block of the cover’s LL band that gives the optimal embedding location according to its index. This individual (block) will specify the optimal scaling factor explicitly according to the block’s singular values.
f is the objective function (fitness function). The individual that has higher fitness will win to be added to the predicate operators mate. Herein, the fitness function is computed based on PSNR value that shows the extent of distortion introduced to the original cover image due to dual watermark insertion (transparency indicator) and NCC that specifies the degree of similarity between original watermarks and extracted watermarks of each block in the population for each generation (robustness indicator) [48].
Bi is the block with index i, and μ is a weight used to make a balance between transparency and robustness impact (μ = 1). The fitness parameters PSNR and NCC are calculated under different type of attacks such as Gaussian noise, cropping, and geometric attacks. Algorithm 1 illustrates the pseudo code of the GA.
Algorithm 1: Genetic Algorithm Pseudo Code.

During the embedding process, cover image ID, size, and some values will be stored in the database to be used later in the extraction process where the suggested system falls under the semi-blindness category. These values include SI, Cb, Bi and SI, Y, Bi of the original cover image, the embedding locations of both watermarks ⊥1, and ⊥2, the scaling factors used in the embedding process for both watermarks ΩI, Y, Bi, and ΩI, Cb, Bi, U, V matrices, LH, HL, HH sub-bands as additional data that are needed to fully extract the watermarks. As these matrices are sparse (most of items are zeroes) in natural, they do not need a large storage space.
3.3 Dual Watermarks Extraction
Extraction process is done in a reverse way to the embedding process, which includes the following steps [15, 29, 31, 33,34,35, 37,38,39, 43, 44, 46, 51,52,53]:
- 1-
Given the watermarked image \( \overline{I} \), match its’ ID and size from the database to retrieve the right GA parameters that are needed in the extraction process. Then the watermarked image \( \overline{I} \) is transformed from RGB colour space to YCbCr colour space.
- 2-
Separate YCbCr colour space into its basic channels and select both of Y and Cb channels for extraction process.
- 3-
Apply DWT for both channels to obtain LL bands WTLL, Y, and WTLL, Cb.
- 4-
Divide the WTLL, Y, and WTLL, Cb of the selected channels into blocks (the number of blocks was stored in the database) of equal size to the LL band of the watermarks’ WTLL, W.
- 5-
Determine the watermarks’ locations ⊥1, and ⊥2 according to the values stored in the database (block number).
- 6-
SVD is applied to the located blocks that contain the watermarks’ coefficients to obtain \( {\overline{S}}_{I, Cb, Bi},{\overline{S}}_{I,Y, Bi} \) that contain the singular values of the watermarks.
- 7-
Retrieve the singular values of the dual watermarks’\( {S}_{w_1},\mathrm{and}\ {S}_{w_2} \), then combining them with U and V vectors given from the database to get the LL band of each watermark \( W{T}_{LL,{w}_1}, \) and\( W{T}_{LL,{w}_2} \). These matrices are extracted given both of SI, Cb, Bi and SI, Y, Bi that are previously stored in the database.
-
8-
Given \( W{T}_{LL,{w}_1}, \) and\( W{T}_{LL,{w}_2} \)from the previous step, these bands are combined with their other three unaltered bands of the watermarks given from the database using inverse DWT to get the encoded watermarks (dual watermarks):
where HW represent the encoded watermarks.
- 9-
To acquire the dual watermarks, an inverse WHT is applied to acquire the watermarks \( {\tilde{w}}_1 \) and \( {\tilde{w}}_2 \).
4 Experimental results
Experiments were conducted on a benchmark colour image dataset [42] as illustrated in Fig. 2. It is important to test an image watermarking software on many different images and for fair comparison the same set of sample images should always be used. Pictures can be interesting from the signal processing point of view: textured/smooth areas, size, synthetic, straight edges, sharp, blur, brightness/contrast, etc. They should also cover a broad range of contents and types. The database is divided into volumes based on the basic character of the pictures. Images in each volume are of various sizes such as 512 × 512 pixels, or 1024 × 1024 pixels. All images are 8 bits/pixel for black and white images, 24 bits/pixel for colour images. The following volumes are currently utilized that includes textures, aerials, miscellaneous, sequences. All images in the database are currently stored in PNG format. In this case, the images that are used as watermarks are converted to grey-scale version. In this paper, the suggested intelligent dual watermarking scheme that relies on genetic algorithms has been tested with several test images were each cover image has been tested at different sizes with different GA parameters to perceive the influence of these parameters on the model performance.
The suggested model has been implemented in MATLAB (R2015a) based on image processing and optimization toolboxes; running on a laptop computer (DELL 3000 Series) with the following specifications: Processor: Intel (R), Core (TM) i5 CPU, 5200 U @ 2.20 GHz (4CPUs) 2.20 GHz, RAM: 8 GB with Microsoft windows 10 Single language as running 64-bit operating system. PSNR (Peak Signal to Noise Ratio), and NCC (Normal Correlation Coefficient) were employed as criteria for performance evaluation. PSNR value shows the degree of alteration introduced to the original host image due to watermark insertion and NCC specifies the degree of resemblance between original watermark and extracted watermark [29, 46].
where I(x, y) represent the original cover image, and \( {\overline{I}}_{\left(x,y\right)} \) represent the watermarked image.
where W(m, n) represent the original watermark, and \( {\overline{W}}_{\left(x,y\right)} \) represent the extracted watermark. Table 1 shows GA parameters that were taken for optimizing the suggested multiple watermarking scheme. It is clearly observed from Table 2 that the suggested system is imperceptible (subjective criteria).
4.1 Imperceptibility (quality) analysis- the effect of GA parameters
The first set of experiments was performed to show how the quality of the suggested model in terms of imperceptibility depends on GA parameters that includes Generation Number (GN), and Population Size (PS). The experiment was applied on Lena cover image with different sizes. Table 3 shows that the smaller the cover image’s size, the better PSNR result is acquired. On average, an increasing of 0.3% PSNR was obtained by reducing the cover image to half size. One possible explanation for this result is that smaller size is associated with smaller search space; so that GA can acquire optimal solution [21]. It is also clear from the Table that the increase in population size has a limited effect on number of optimal solution in terms of PSNR when the number of generations is constant. There is an increase with approximately 0.02 with each increase of 5 for the size of the population. Regarding the effect of the number of generations on the convergence to the optimal solution; in spite of the fact that the more the number of generations, the more diversity of the population and therefore the chances of obtaining a better solution are high. There is no significant increase in the PSNR values when generation number increases. One possible explanation of this result is that, populations diversity often is stabilized after a certain generation, in the sense that solution with high fitness are obtained from the previous generations.
4.2 Imperceptibility analysis- the effect of colour channels
The second set of experiments was conducted to show how the PSNR values of the suggested model depend on the embedding in different colour channels in order to determine the most suitable colour channels for the embedding process. It can be inferred from Table 4 that higher PSNR values are achieved in both of Y and Cb colour channels. For all test images, PSNR values are good and greater than the accepted ratio 30 and the differences between these values are small and negligible. One explanation of this result is that most of the visible information is in the Y channel (carry the intensity value of the pixel) and human eyes tolerate both lower spatial resolution and more aggressive quantization in the Cb and Cr channels that contains colour information of the pixel. Of course, the difference in the nature of the images in terms of degrees of colour leads to the preference of a colour channel over the other in the embedding. The proposed model depends on the color channels that achieve the highest PSNR in the embedding of dual watermarks. As stated in [5], the non-uniform colour spaces such as YCbCr colour space indeed provide a large amount of perceptual redundancy for embedding high-strength watermarking signals which can survive various attacks.
4.3 Imperceptibility analysis- the role of GA
The third set of experiments was implemented to illustrate the difference between embedding the watermarks at random locations with constant scaling factor that is identified by experts and the use of GA in the suggested model to find the optimality of these issues. As shown in Tables 5 and 6, the use of GA to find the optimal values of both scaling factor and embedding locations gives superiority results in terms of PSNR as compared with random values. Herein, the objective function comprises both of PSNR and NCC as a criteria to select the search space. The use of both PSNR and NCC achieve optimal quality in terms of imperceptibility by reducing the difference in pixels values between the cover image and the watermarked image. The use of GA improved the model performance in terms of PSNR and 30% for Lena image, 25% for Mandrill image. The average improvement in terms of image quality through employing GA for embedding is around 39%. This difference in PSNR values is due to the different contents of the image according to their colour characteristics. For watermarks quality in terms of NCC, utilizing GA improves the performance by average 60% in case of selecting embedding factors randomly. All GAs demand some compose of recombination, as this permit the ingenuity of new solutions that have, by virtue of their parent’s success, a higher probability of showing a good performance. In GA, diversification tries to explore the search space more efficiently by generating solutions with higher diversity. This diversity is achieved by discovering the search space (solutions) that have highest objective function.
4.4 Imperceptibility analysis- comparative study
The fourth set of experiments was performed to compare the imperceptibility performance (with attacks) of the suggested dual hybrid watermarking system (successive and segmented) that employs GA to find the optimal embedding locations and scaling factors with related dual watermarking approaches that includes (1) N. Mohananthini approach [34] in which dual watermarking technique for both successive and segmented watermarking is applied separately based on image salient features extracted from DWT – SVD. This approach employed GA to find optimal scaling factor only. (2) S. Vaidya approach [50] in which dual watermarking technique for successive watermarking only is applied based on DWT-SVD for determining embedding locations. Finally (3) C. Kumar et al. approach [26] in which dual watermarking technique for segmented watermarking only is applied based on Non-Subsampled Contourlet Transform for determining embedding locations. As shown in Table 7, the proposed dual watermark approach achieves 37.1% improvement in terms of PSNR (cover image quality) compared to the other approaches that outperform in many cases with a very small ratio in terms of NCC (watermark quality) as compared with suggested model.
One possible explanation for this improvement is that the merge of the two watermarking techniques yields a solution to the issue of watermarks interference with each other. Furthermore, the suggested model is based on embedding the watermarks in the most suitable locations with optimal scaling factors, which is not presented in the other models that determines the optimal scaling factor only. However, the overlap between different embedding techniques as in the proposed model may cause some problems in locations’ determination for watermarks extraction process; this may happen in simple cases which consequently decreases the NCC percentage. The other approaches relies on utilizing one watermarking technique to apply the dual watermarking, that embed watermarks in spaced locations without considering the quality of the host image.
4.5 Attacks Analysis
The fifth set of experiments was implemented to validate the robustness of the suggested model against different types of attacks. Different types of attacks as shown in Fig. 3 were implemented on the watermarked image. Tables 8 and 9 summarize the results in terms of PSNR for the watermarked image and NCC for the watermarks for both the suggested model and the comparative approaches. The results confirm that the robustness of proposed model is superior to the existing methods for different cases with improvement of about 0.8% in terms of PSNR. The results also clarified that the rotation attack has achieved the least PSNR value as it changes the pixels’ locations and consequently loss the synchronization between the original watermarks’ locations and the stored locations in the database. Whereas, the JPEG compression attack has achieved the highest PSNR value as this type of attack is usually applied to the high-frequency components, on the contrary the proposed model embeds the dual watermarks in the low-frequency components; so that this attack has no significant impact on the quality of the watermarked image and the watermarks. In common, simple attacks like noises attempt to damage the embedded watermark by manipulations of the whole watermarked data (host data plus watermark) without an attempt to identify and isolate the watermark. From Table 9, as expected, the comparative approaches outperform with a very small ratio (0.8%) in terms of NCC (watermark quality) for different type of attacks as compared with suggested model. This is due to problems in locations’ determination for watermarks extraction process; interference between embedding processes. The difference in the NCC values for the extracted watermarks form the same cover image is due to the nature of the characteristics of the image. Note that the correlation ratio between the extracted watermarks and the original ones is high in the presence of attacks because the suggested model determines the embedding parameters based on a fitness function that relies on NCC, which compare between the quality of the image before and after attacks in order to select the best parameters able to stand against attacks.
4.6 Statistical analysis
The following set of experiments was performed to determine the statistical inferences that are carried out for the multiple watermarking techniques with and without genetic algorithm. Table 10 gives the statistical inferences for the NCC values from the results given in Table 6 and Table 9 for different attacks, while Table 11 gives the statistical inferences for the PSNR values from the results given in Table 5 and Table 8 for different attacks. In this case, H0 represents the hypothesis that the multiple watermarking techniques with genetic algorithm is better and H1 represents the hypothesis that the multiple watermarking techniques without genetic algorithm is better. From Table 10 and Table 11, it is observed that the calculated value is less than the t table value at 5% level of significance; so the proposed model accept the H0 and it is concluded that the multiple watermarking techniques with genetic algorithm is found to be better. The improvement resulting from the use of GA is due to the GA ability to balance between the exploitation and the exploration to optima the best values of scaling factor and embedding locations [33] [52]. Exploitation means that given a reasonable solution, the algorithm will keep refining that solution until it reaches a local optimum. While the exploration means that the algorithm will attempt to achieve a good coverage of the search space, so that it will not eventually find just any local optimum, but a good local optimum, ideally one that is close to the global optimum. However, it cannot be equated these two notions with the crossover and mutation functions. Both have effects that work towards both exploitation and exploration. The choice of which genes die and which get to reproduce also has a large influence on this balance.
4.7 Time complexity analysis
The last set of experiments was conducted to evaluate the complexity of the suggested model. Time complexity analysis is a part of computational complexity theory that is used to describe an algorithm’s use of computational resources; in most cases, the worst case running time expressed as a function of its input using big-O notation [15]. As the proposed system was built using Matlab, which in turn depends on calling many built-in functions, therefore, it is difficult to extract the big-O, herein; time was used as a measurement to evaluate the complexity of the system. As shown in Table 12, more processing time is needed for the suggested model as compared to the successive watermarking by 19.38%. More specifically, the suggested model takes about 2.654468 s for the embedding process and takes about 0.678911 s for the extraction process; thus, the time of extraction process is roughly equivalent to one fifth of the time of embedding process. In general, this relatively large time in the embedding process represents the offline phase of the proposed model. Consequently, the proposed model is applicable in real-time applications. A possible explanation is that the suggested model relies on a hybrid watermarking technique, unlike the other approaches that relies on embedding multiple watermarking based on single technique. This extra time has been used to improve the efficiency of the proposed model in terms of robustness against the attacks and imperceptibility.
4.8 Limitation of the suggested model
In general, the application of the proposed dual watermarking model faces some constraints that includes (1) the segmentation operation is built using square sized images, (2) the watermarks are grey scale images for simple embedding, finally (3) extra memory space are needed to store some information that are used in the extraction process as the suggested model is semi-blind.
5 Conclusion
The design of suitable dual watermark embedding involves multiple criteria and specifications. Finding suitable embedding locations and optimal embedding strength are, therefore, not a simple task. In recent times, the merging of optimization techniques with the image watermarking scheme to improve its performance and effectiveness in different areas has received considerable attention among researchers working in this field. Inspired by the challenges that faced the dual image watermarking and in order to deal with it, in this paper, a novel model has been established to produce an intelligent dual watermarking scheme for colour images that guarantee the possibility of protecting the rights of ownership and publication and to be used effectively in different applications, that take into account the image quality. Herein, multi-purpose genetic algorithm is utilized to optimize watermarking embedding parameters to achieve robustness and imperceptibility.
The suggested model achieves high capacity (Payload). Studying the capacity of the image can show us the limit of watermark information that would be embedded and at the same time satisfying the imperceptibility and robustness. The main two issues of complexity are the speed of embedding and detection, and the number of embedders and detectors; the suggested model has low complexity. The proposed model has been evaluated using benchmark images. The results confirmed the capability of the proposed model in terms of robustness and imperceptibility. Utilizing genetic algorithm achieves 23% improvement in terms of peak signal to noise ratio compared to the traditional non-optimized dual watermarking methods. To set a plan for future works, the suggested model can be upgraded to exploit other color spaces that could improve the performance such as YUV, and CMYK. More features can be investigated in order to enhance the performance of the dual watermarking schemes by combining the DWT with other transforms. Furthermore, GA can be replaced with another appropriate optimization method to fine tuning watermarking embedding parameters. Finally, link the proposed model to the modern applications of e-business such as Blockchain.
References
Aakanksha T, Gupta B (2017) A Lightweight Mutual Authentication Protocol based on Elliptic Curve Cryptography for IOT Devices. International Journal of Advanced Intelligence Paradigms 9(2-3):111–121
Abdallah E, Hamza A, Bhattacharya P (2007) MPEG Video Watermarking using Tensor Singular Value Decomposition. International Conference Image Analysis and Recognition:772–783
Abdallah E, Hamza A, Bhattacharya P (2010) Video Watermarking using Wavelet Transform and Tensor Algebra. SIViP 4(2):233–245
Abu-Marie W, Gutub A, Abu-Mansour H (2010) Image based Steganography Using Truth Table Based and Determinate Array on RGB Indicator. International Journal of Signal and Image Processing 1(3):196–204
J. Advith, K. R. Varun, and K. Manikantan, "Novel Digital Image Watermarking using DWT-DFT-SVD in YCbCr Color Space", Proceedings of the IEEE International Conference on Emerging Trends in Engineering, Technology and Science, pp. 1-6, India, Feb. 2016.
Alanizy N, Alanizy A, Baghoza N, Al Ghamdi M, Gutub A (2018) 3-Layer PC Text Security via Combining Compression, AES Cryptography 2LSB Image Steganography. Journal of Research in Engineering and Applied Sciences 3(4):118–124
Alaseri K, Gutub A (2018) Merging Secret Sharing Within Arabic Text Steganography for Practical Retrieval. Journal of Computer Science Engineering 4(9):1–7
Al-Ghamdi M, Al-Ghamdi M, Gutub A (2019) Security Enhancement of Shares Generation Process for Multimedia Counting-vased Secret-Sharing Technique. Multimed Tools Appl 78(12):16283–16310
Al-Juaid A, Gutub A, Khan A (2018) Enhancing PC Data Security Via Combining RSA Cryptography and Video based Steganography. Journal of Information Security and Cybercrimes Research (JISCR) 1(1):8–18
Almazrooie M, Samsudin A, Gutub A, Salleh M, Omar M, Hassan S (2018) Integrity verification for digital Holy Quran verses using cryptographic hash function and compression, Journal of King Saud University - Computer and Information Sciences, Published by Elsevier, Published online: 8
Al-Otaibi N, Gutub A (2014) 2-Leyer Security System for Hiding Sensitive Text Data on Personal Computers. Lecture Notes on Information Theory 2(2):151–157
Al-Otaibi N, Gutub A (2014) Flexible Stego-System for Hiding Text in Images of Personal Computers Based on User Security Priority, Proceedings of International Conference on Advanced Engineering Technologies (AET-2014), pp. 250-256, UAE, 25-26 December
Alsaidi A, Al-lehaibi K, Alzahrani H, AlGhamdi M, Gutub A (2018) Compression Multi-Level Crypto Stego Security of Texts Utilizing Colored Email Forwarding. Journal of Computer Science & Computational Mathematics 8(3):33–42
Btihal M, Hassan N (2017) Homomorphic Encryption as a Service for Outsourced Images in Mobile Cloud Computing Environment. International Journal of Cloud Applications and Computing 7(2):27–40
Chetan KR, Nirmala S (2016) A Novel Intelligent Multiple Watermarking Schemes for the Protection of the Information Content of a Document Image. Proceedings of the International Conference on Computer Vision, Graphics, and Image processing, pp. 3-14, India.
Espinoza KR, Navarro EF, Ramos CC, Reyes RR, Miyatake MN, Meana HP (2018) Adaptive Removable Visible Watermarking Technique using Dual Watermarking for Digital Colour Images. Multimed Tools Appl 77(11):13047–13074
Gen WY, Xie D, Gupta BB (2018) A Study on the Collusion Security of LUT-based Client-Side Watermark Embedding. IEEE Access 6:15816–15822
Gupta BB (2018) Computer and Cyber Security: Principles, Algorithm, Applications, and Perspectives, CRC Press, Taylor & Francis, 666
Gupta B, Agrawal D, Yamaguchi S (2016) Handbook of Research on Modern Cryptographic Solutions for Computer and Cyber Security. IGI Global
Gutub A (2010) Pixel Indicator Technique for RGB Image Steganography. Journal of Emerging Technologies in Web Intelligence 2(1):56–64
Gutub A, Al-Ghamdi M (2019) Image based Steganography to Facilitate Improving Counting-based Secret Sharing. 3D Res 10(6):1–36
Gutub A, Al-Juaid N (2018) Multi-Bits Stego-System for Hiding Text in Multimedia Images based on User Security Priority. Journal of Computer Hardware Engineering 1(2):1–9
Gutub A, Al-Juaid N, Khan E (2019) Counting-based Secret Sharing Technique for Multimedia Applications. Multimed Tools Appl 78(5):5591–5619
Gutub A, Al-Qahtani A, Tabakh A (2009) Triple-A: Secure RGB Image Steganography based on Randomization, Proceedings of 7th ACS/IEEE International Conference on Computer Systems and Applications, pp. 400-403, Morocco, 10-13 May
Gutub M, Ankeer M, Abu-Ghalioun A, Alvi A (2008) Pixel Indicator high capacity Technique for RGB image based Steganography, IEEE International Workshop on Signal Processing and its Applications, pp. 1-4, U.A.E. 18-20 March
Kumar C, Singh AK, Kumar P, Singh R (2018) A Low Complexity Secure Force Encryption based Multiple Image Watermarking in NSCT Domain. Proceedings of the 2nd IEEE International Conference on Advances in Computing, Control and Communication Technology, pp. 92-96
Li D, Deng L, Gupta B, Wang H, Choi C (2019) A Novel CNN Based Security Guaranteed Image Watermarking Generation Scenario For Smart City Applications. Inf Sci 479:432–447
Li J, Yu C, Gupta B, Ren X (2018) Colour Image Watermarking Scheme based on Quaternion Hadamard Transform and Schur Decomposition. Multimed Tools Appl 77(4):4545–4561
Liao HW (2012) A Multiple Watermarking Scheme for Colour Images, Proceedings of the 3rd IEEE International Conference on Mobile, Ubiquitous, and Intelligent Computing, pp. 132-137, Canada
Liu J, Huang J, Luo Y, Cao L, Yang S, Wei D, Zhou R (2019) An Optimized Image Watermarking Method based on HD and SVD in DWT Domain. IEEE Access 7:80849–80860
Liu XL, Lin CC, Yuan SM (2016) Blind Dual Watermarking for Colour Images’ Authentication and Copyright Protection. International Journal of IEEE Transactions on Circuits and Systems for Video technology 26(3):1–9
Lusson F, Bailey K, Leeney M, Curran K (2013) A Novel Approach to Digital Watermarking Exploiting Colour Spaces. International Journal of Signal Processing 93(5):1268–1294
Mathivadhani D (2012) Multiple Watermarking Approaches using Enhanced Image Processing Techniques and Visual Cryptography. Master Thesis, Department of Computer Science, Avinashilingam Institute for Home science and Higher Education, India
Mohananthini N (2015) Analysis of Multiple Watermarking using Images. Master Thesis, Department of Electrical Engineering, faculty of Engineering and Technology, Annamalai University, India
Mohananthini N, Yamuna G (2016) Comparison of Multiple Watermarking Techniques using Genetic Algorithm. Journal of Electrical Systems and Information Technology 3(1):68–80
Moosazadeh M, Andalib A (2016) A New Robust Colour Digital Image watermarking Algorithm in DCT Domain using Genetic Algorithm and Coefficients Exchange Approach, Proceedings of the 2nd International Conference of Web Research (ICWR), pp. 19-24, Iran
Natarajan M, Govindarajan Y (2014) Performance Comparison of Single and Multiple Watermarking Techniques. International Journal of Computer Network and Information Security 6(7):28–34
Ouazzane H, Mahersia H, Hamrouni K (2013) A Robust Multiple Watermarking Scheme based on the DWT. Proceedings of the 10th IEEE International Multi-Conference on Systems, Signals & Devices, pp. 1-6, Tunisia
Ouazzane H, Mahersia H, Hamrouni K (2013) A Robust Multiple Watermarking Scheme based on the DWT. Proceedings of the 10th IEEE International Multi-Conference on Systems, Signals & Devices, pp. 1-6
Parvathavarthini S, Shanthakumari R (2014) An Adaptive Watermarking Process in Hadamard Transform. International Journal of Advanced Information Technology 4(2):1–7
Parvez M, Gutub A (2011) Vibrant Colour Image Steganography using Channel Differences and Secret Data Distribution. Kuwait Journal of Science and Engineering 38(1B):127–142
Public-Domain Test Images for Home works and Projects. Available at: https://homepages.cae.wisc.edu/~ece533/images/
Radharani S, Valarmathi ML (2011) Multiple Watermarking Scheme for Image Authentication and Copyright Protection using Wavelet based Texture Properties and Visual Cryptography. Int J Comput Appl 23(3):29–36
Sejpal S, Shah N (2016) A Novel Multiple Objective Optimized Dual Watermarking Scheme based on DWT-SVD using Firefly Algorithm", Proceedings of the IEEE International Conference on Computing, Analytics and Security Trends, pp. 46-51, India
Sejpal S, Shah N (2016) A Novel Multiple Objective Optimized Colour Watermarking Scheme based on LWT-SVD Domain using Nature based Bat Algorithm and Firefly algorithm. Proceedings of the 2016 IEEE International Conference on Advances in Electronics, Communication and Computer Technology, pp. 38-44, India
Singh S, Arya RK, Sharma H (2016) A Robust De-interlacing Multiple Image Watermarking Technique in DWT. Proceedings of the IEEE International Conference on Computational Techniques in Information and Communication Technologies, pp. 8-13
Soni N, Kumar T (2014) Study of Various Crossover Operators in Genetic Algorithms. International Journal of Computer Science and Information Technologies 5(6):7235–7238
Takore T, Kumar P, Devi G (2016) Efficient Gray Image Watermarking Algorithm based on DWT-SVD using Genetic Algorithm, Proceedings of the IEEE International Conference on Information Communication and Embedded System, pp. 1-6, India
Takore T, Kumar P, Devi G (2018) A Robust and Oblivious Grayscale Image Watermarking Scheme based on Edge Detection, SVD, and GA. Lecture Notes in Electrical Engineering 434:51–61
S. Vaidya, "Multipurpose Color Image Watermarking in Wavelet Domain using Multiple Decomposition Techniques", Proceedings of the 2nd IEEE International Conference on Inventive Communication and Computational Technologies, pp. 251-255, India, 2018.
Vinothini K, Mydhili S, Periyanayagi S, Sukanya G (2019) Dual Watermarking in Tele-radiology using DWT for Data Authentication and Security. Proceedings of the 8th IEEE International Conference on Communication and Signal Processing, pp. 887- 891
Wang Y, Yang C, Zhu C, Ren N, Chen P (2016) A Novel Multiple Watermarking Algorithm based on Correlation Detection for Vector Geographic Data. Proceedings of the International Conference on Geo-Informatics in Resource Management and Sustainable Ecosystems. pp. 429-436. Springer. Singapore
Wirayuda T, Winanjuar SD, Muslimah U (2012) The Multiple Watermarking on Digital Medical Image for Mobility and Authenticity. Proceedings of Operations Research:457–462
Zhang J, Gao H (2019) A Compact Construction for Non-Monotonic Key-Policy Attribute-based Encryption. International Journal of High Performance Computing and Networking 13(3):321–330
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Darwish, S.M., Al-Khafaji, L.D.S. Dual Watermarking for Color Images: A New Image Copyright Protection Model based on the Fusion of Successive and Segmented Watermarking. Multimed Tools Appl 79, 6503–6530 (2020). https://doi.org/10.1007/s11042-019-08290-w
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08290-w