Abstract
A novel removable visible watermarking (RVW) algorithm by combining Block Truncation Coding (BTC) and chaotic map (RVWBCM) is presented in this paper. It embeds a visible watermark in the BTC codes of images, namely both the host image and the watermarked image are BTC compressed images. First, the original image is divided into watermarked region and non-watermarked region, and a predicted version of original image can be obtained by predicting pixel values in watermarked region. Second, adaptive embedding factors are computed according to the image features. Third, the watermark is adaptively embedded into two quantization levels of the BTC compressed image in visible manner. Meanwhile, to further prevent illegal watermark removal, original bi-level watermark is encrypted and then losslessly embedded in invisible manner by adjusting the relationship of two quantization levels. At the receiver’s end, only authorized users can exactly extract original bi-level watermark according the relationship of two quantization levels of BTC codes and succeed in remove the embedded visible watermark to reconstruct the original image. The experimental results show that this scheme can achieve a good balance between perceptual transparence and the watermark strength (watermark visibility) and can resist common image processing attacks. The proposed algorithm has low complexity and simplicity of implementation due to the use of BTC. It can be applicable to copyright notification and secure access control in mobile communication.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Visible watermarking techniques are particular embodiments of digital watermarking [8, 10], which overlay perceptual copyright information on the media in such a way that the watermark is intentionally perceptible to human observers but must not significantly obscure the image details beneath it. In addition, the watermark must be hard to remove [13, 15]. A visible watermark can deter attempts of copyright violations, but generally it is designed to be irreversible so as to resist unintentional modifications or malicious attacks [7, 16]. Distortion is unavoidably introduced into the host content during the visible watermark embedding and causes degradation of media. Although the distortion is normally small, there are some applications such as medical imagery, remote sensing, military and law enforcement, where any permanent distortion introduced by watermarking is not allowable. This calls for new visible watermarking techniques called removable [1] or reversible watermarking [11, 17], which can revert to the high quality or exact copy of the original media by removing distortion caused by the watermark embedding.
Hu et al. [6] proposed a user-key-controlled RVW scheme in discrete wavelet transform domain by embedding a visually same but numerical different watermarked versions for different users. Yang et al. [19] proposed a RVW algorithm in discrete cosine transform (DCT) domain where the key dependent preprocessed watermark is adaptively superposed on host image by considering human visual system characteristic of DCT coefficients. Both the two visible watermarking schemes [6, 19] need original watermark during original image recovery. However, the original watermark is not available in some real-time or low-bandwidth environments. Moreover, unauthorized users can obtain an acceptable original image by watermark removal with a tiny different secret key.
Yip et al. [22] presented two lossless visible watermarking algorithms, Pixel Value Matching Algorithm (PVMA) and Pixel Position Shift Algorithm (PPSA). They use the bijective intensity mapping function and circular pixel shift to insert visible watermarks, respectively. Liu and Tsai [9] exploit one-to-one compound mappings for overlaying visible watermarks by mapping image pixel values to those of the desired visible watermarks. Lossless though they are, these algorithms [9, 22] resort to the visible watermark for original image recovery, and have low watermark visibility.
Some lossless visible watermark schemes [5, 18, 20, 23] remove visible watermark overlaying on the cover image and recover original image by embedding some additional information about the watermark and host image with reversible data hiding techniques. But due to the embedded additional information, the visible watermark on the watermarked image produced by these approaches is inevitably blurred in certain and is low visible especially in texture region.
The above-mentioned visible watermarking algorithms do not work in compressed domain and are not suitable for real-life applications via internet. Yeh et al. [21] claimed that a reversible visible watermarking method in JPEG compression domain was proposed, though it inserts the visible watermark in DCT domain rather than compressed domain in fact. Farrugia [2] tries to extend Yang et al.’s scheme [19] to compressed domain. His scheme completely uses the same embedding strategy as Yang et al.’s and inserts the visible watermark in spatial domain, although it adds JPEG compression after watermark embedding and decompression process before watermark removal. Generally, mobile terminals have only limited batteries life, limited memory, and limited computational power. Some complex computation is hard to implement on these portable devices. BTC is a simple and fast compression method with relatively good compression ratio [3]. In order to provide secure and real-time copyright protection for digital media via internet or mobile terminals, a novel RVW algorithm applicable for BTC compressed images is proposed in this paper. The visible watermark image is adaptively added to the BTC compressed image by exploiting the image smoothness and luminance features so that the watermark visibility is good. To prevent unauthorized users from recovering the original BTC compressed image, the watermark is encrypted and then losslessly hidden by modifying the relationship of two quantization levels of BTC codes.
The rest of this paper is organized as follows. The principle of BTC is introduced in Section 2. In Section 3, the proposed RVW scheme is presented. Experimental results are given in Section 4, and finally the conclusion is made in Section 5.
2 Block truncation coding
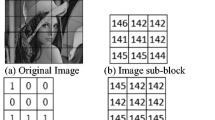
BTC is a simple compression method based on moment preserving quantization [12]. There are many different variants of BTC in the literature. We embed the visible watermark into absolute moment block truncation coding (AMBTC) compressed images. There are encoding phase and decoding phase in the AMBTC. During the encoding phase, the original image is first divided into non-overlapping blocks of s × s pixels. The pixels in each block are then classified into two groups according to the relationship between their values and the certain threshold, such as the mean value of each block. The pixel values greater than or equal to the threshold are marked as 1’s, otherwise denoted as 0’s. Meanwhile, a bitmap B is used to record whether a pixel value is less than a certain threshold or not. So the pixel values marked as 1’s are grouped into group 1, and others into group 2. The two quantization levels a and b for each block can be computed using means of the corresponding group, and higher mean a and lower mean b are computed as follow.
Where s × s is the total number of pixels in the block and q is the number of pixels greater than the mean l. x k is the intensity values of the pixels in the block of original image. Finally, each image block is compressed by using two quantization levels a and b, and one binary bitmap B.
In the decoding processing, one can reconstruct image blocks from the compressed code (a, b, B). The corresponding pixels marked as 1’s in the bitmap B are reconstructed by the higher mean a, Otherwise, reconstructed by the lower mean b. Figure 1 shows an example of AMBTC coding and decoding procedures. One can notice that the reconstructed AMBTC image blocks will remain the same when interchange two quantization levels a and b, and perform Logical NOT operation on the bitmap B. That is to say, the following equation always holds [4].
where \( \overline{B} \) is the result of the logical NOT operation on the bitmap B, and the operator OP() denotes the reconstruction function for AMBTC compressed image blocks.
3 Removable visible watermarking scheme for BTC compressed images
In order to achieve fast and secure visible watermarking schemes, this paper presented a new RVW algorithm based on AMBTC. It prevents illegal watermark removal by embedding the encrypted watermark signal into AMBTC codes according to the relationship between two quantization levels in invisible manner, and produces the watermarked image with visible watermark by superposing the visible watermark on two quantization levels. The details of watermark embedding and removing processes are described in the following subsections.
3.1 Visible watermark embedding
During watermark embedding, pixels in compressed image I are overlapped with the corresponding black logo pixels in the watermark W. The overlapped region in image I is the watermarked region called I c and the other is the non-watermarked region called I n . Given an AMBTC code C of host image I of m × n and a binary visible watermark W of m/s × n/s. The flowchart of the visible watermark embedding is illustrated in Fig. 2 and details of the watermark embedding procedure are described as follows.
-
Step 1:
For the sake of simplicity, the visible watermark can be viewed as p-dimensional vectors, where p = m/s × n/s is also the total number of blocks to be encoded. Read the AMBTC code C of host image I and obtain a sequence of AMBTC code (a i , b i , B i ), i = 1, 2, …, p.
-
Step 2:
Generate a mean array L from AMBTC codes, which have values \( {l}_i=\left[\frac{q_i{a}_i+\left(s\times s-{q}_i\right){b}_i}{s\times s}\right] \) in non-watermarked region I n , otherwise l i = −1, and then an estimated mean image \( \tilde{L} \) is produced from the mean array L by approximating the corresponding pixel values in I c with the estimated pixel values and the non-watermarked pixel values in their neighborhood. The intensity values \( {\tilde{l}}_i \) of the estimated mean image \( \tilde{L} \) can be calculated as follows.
$$ {\tilde{l}}_i=\left\{\begin{array}{ll}\left[\frac{q_i{a}_i+\left(s\times s-{q}_i\right){b}_i}{s\times s}\right],\hfill & bloc{k}_i\in {I}_n\hfill \\ {}\frac{1}{\left|{O}_1\right|+\left|{O}_2\right|}\left({\displaystyle \sum_{bloc{k}_j\in {O}_1}{l}_j}+{\displaystyle \sum_{bloc{k}_j\in {O}_2}{\tilde{l}}_j}\right),\hfill & bloc{k}_i\in {I}_c\hfill \end{array}.\right. $$(3)Where O 1 = {non-watermarked blocks in the neighborhood of block i}, O 1 = {watermarked blocks with estimated means in the neighborhood of block i}. The block j belongs to the neighborhood of block i. An R × R neighborhood centered as block i is illustrated in Fig. 3. [•] denotes the round function, |•| operator returns the cardinality of this set, and q i is the number of 1’s in the bitmap of block i. Note that we do not use the information of pixels in the watermarked regions for generating the estimated mean image \( \tilde{L} \). So the identical mean image \( \tilde{L} \) can be obtained from a watermarked image by the receiver for the purpose of watermark removal.
-
Step 3
Considering the nature of human vision that human eyes are more sensitive to changes in smooth areas of an image than in textured areas, we can compute the block smoothness according to the bitmaps of AMBTC codes as follows.
$$ {\alpha}_i=\frac{\left|s\times s-2{q}_i\right|+\tau }{s\times s+\tau }. $$(4)Where τ is a user-defined parameter for avoid zero smoothness factor and division by zero in Eq. (6). The block smoothness α i will be unchangeable before and after watermark embedding because that watermark insertion does not change the absolute difference of the number of pixels in group 1 and group 2.
The eye is most sensitive to distortion in middle intensity regions and less sensitive to distortion for brighter or darker background. So the luminance factor can be roughly measured by the following equation based on the estimated mean image \( \tilde{L} \).
$$ {\beta}_i=\frac{\left|{\tilde{l}}_i-255/2\right|}{255/2}. $$(5) -
Step 4:
Based on the above consideration of human visual perception, the visual factor for watermark embedding strength can be written as
$$ {\gamma}_i=\frac{\beta_i}{\alpha_i}. $$(6)To avoid obtrusive embedding, the visual factor γ is normalized to a narrow range [r 1 , r 2 ] by using Eq. (7).
$$ {\tilde{\gamma}}_i=\frac{r_2-{r}_1}{ \max \left(\gamma \right)- \min \left(\gamma \right)}\times \left({\gamma}_i- \min \left(\gamma \right)\right)+{r}_1. $$(7)Where max() and min() are maximum and minimum functions respectively, and r 1 , r 2 (0 < r 1 , r 2 < 1) are predetermined parameters. It can be seen that the greater the value of the visual factor \( \tilde{\gamma} \), the higher the watermark strength.
-
Step 5:
For each triple (a i , b i , B i ), Embed adaptively the visible watermark signal to produce the triple (a ′ i ,b ′ i ,B i ) by modifying the two quantization levels of AMBTC codes according to Eq. (8) as below.
$$ t\prime =\left\{\begin{array}{ll}t,\hfill & {w}_i=1\hfill \\ {}\left(1-{\tilde{\gamma}}_i\right){\rho}_1t+{\tilde{\gamma}}_i{W}_A,\hfill & {w}_i=0,{\tilde{l}}_i>={G}_1\hfill \\ {}\left(1-{\tilde{\gamma}}_i\right){\rho}_2t+{\tilde{\gamma}}_i\left(255-{W}_A\right),\hfill & {w}_i=0,{\tilde{l}}_i<{G}_1\hfill \end{array}\right. $$(8)Where t ∈ {a i , b i }, t ′ ∈ {a ′ i ,b ′ i }, ρ 1 and ρ 2 are user-defined constants, and ρ 1 ∈ [0.5, 1], ρ 2 ∈ [1, 5.1]. To achieve good balance between visual quality of stego image and watermark visibility, generally the watermark component W A ∈ [15, 40] and gray threshold G 1 is the mean of minimum grayscale and maximum grayscale value. Especially W A = 20 and G 1 is set to 128 in the experiments. This embedding strategy makes the intensity of the visible watermark high and low for dark and light gray background respectively, and ensures good watermark visibility.
-
Step 6:
Use a chaotic logistic map [14]
$$ {y}_{n+1}=\mu {y}_n\left(1-{y}_n\right). $$(9)with the secret key key 1 in the open interval (0, 1) as the initial value y 0 to generate a pseudo-random binary sequence D 1 = {D 1 (i)| D 1 (i) = 0, 1, i = 1, 2, …, p}. And then apply the chaotic map with another secret key key 2 to produce a pseudo-random integer sequence D 2 whose elements have different integer value in the closed interval [1, p]. The bifurcation parameter μ should be chosen from the half-open interval (3.599456, 4) so as to ensure that the logistic map falls in a chaotic state.
-
Step 7:
Perform element-wise XOR operation on two sequences D 1 and W to produce modulated watermark signal W′, and then the encrypted watermark W′′ can be obtained by scrambling the modulated signal W′ using the pseudo-random integer sequence D 2 .
-
Step 8:
To prevent illegal watermark removal, the encrypted watermark W′′ is losslessly embedded in BTC codes in invisible manner. For each block i with triple (a ′ i ,b ′ i ,B i ), we change the triple (a ′ i ,b ′ i ,B i ) to \( \left({b}_i^{\prime },{a}_i^{\prime },{\overline{B}}_i\right) \) if the corresponding encrypted watermark bit w ′ ′ i = 0. Otherwise, the triple (a ′ i ,b ′ i ,B i ) remains unchanged. So, the lossless embedding strategy can be written as
$$ \left({a}_i^{\prime },{b}_i^{\prime },{B}_i\right)=\left\{\begin{array}{ll}\left({b}_i^{\prime },{a}_i^{\prime },{\overline{B}}_i\right)\hfill & if\ {w}_i^{\prime \prime }=0\hfill \\ {}\left({a}_i^{\prime },{b}_i^{\prime },{B}_i\right)\hfill & else\hfill \end{array}\right.. $$(10)The entire watermarked AMBTC code stream C′ will be obtained when all the encrypted watermark bits are embedded, and finally the watermarked BTC compressed image I w is generated.
3.2 Visible watermark removal and image recovery
The procedure of removing the visible watermark is roughly the inverse operation of the embedding procedure. Given private keys key 1 and key 2 , and the watermarked image I w , the steps for watermark removal are as follows:
-
Step 1:
Read AMBTC code stream C′ from he watermarked image I w, and get the triple (a ′ i ,b ′ i ,B i ) for each block i.
-
Step 2:
For each triple (a ′ i ,b ′ i ,B i ), extract the encrypted watermark bits according to the relationship of two quantization levels by
$$ {w}_i^{\prime \prime }=\left\{\begin{array}{llll}1,\hfill & {a}_i^{\prime }>{b}_i^{\prime}\hfill & or\hfill & \left({a}_i^{\prime }={b}_i^{\prime }\ and\ {q}_i>0\right)\hfill \\ {}0,\hfill & {a}_i^{\prime }<{b}_i^{\prime}\hfill & or\hfill & \left({a}_i^{\prime }={b}_i^{\prime }\ and\ {q}_i=0\right)\hfill \end{array}.\right. $$(11) -
Step 3:
Use Eq. (9) with the same secret key key 1 and key 2 to generate a pseudo-random binary sequence D 1 and a pseudo-random binary sequence D 2 , and then the modulated watermark signal W′ can be got by descrambling the encrypted watermark W″ with D 2 . Furthermore, apply an element-wise XOR operation between the watermark signal W′ and the sequence D 1 to generate the original watermark W. Note that unauthorized users without correct secret keys can not extract the exact watermark signal, so illegal users can not remove the visible watermark from the watermarked image.
-
Step 4:
Produce the estimated mean image \( \tilde{L} \) based on the BTC codes of non-watermarked regions in the watermarked image using Eq. (3), and go further to deduce the visual factor \( \tilde{\gamma} \) using the same methods as step 3 and step 4 in watermark embedding process.
-
Step 5:
Remove the visible watermark component for each image block with the triple (a ′ i ,b ′ i ,B i ) using
$$ t=\left\{\begin{array}{l}{t}^{\prime },\kern6.75em {w}_i=1\\ {}\frac{t^{\prime }-{\tilde{\gamma}}_i{W}_A}{\rho_1\left(1-{\tilde{\gamma}}_i\right)},\kern3.25em {w}_i=0,{\tilde{l}}_i>={G}_1\\ {}\frac{t^{\prime }-{\tilde{\gamma}}_i\left(255-{W}_A\right)}{\rho_2\left(1-{\tilde{\gamma}}_i\right)},\kern0.5em {w}_i=0,{\tilde{l}}_i<{G}_1\end{array}\right.. $$(12)Where t ∈ {a i , b i }, t ′ ∈ {a ′ i ,b ′ i }.
Finally, the unmarked image can be reconstructed according to the BTC codes (a i , b i , B i ) for each block when the visible watermark is removed.
4 Experimental results and analysis
The proposed removable visible watermarking algorithm (RVWBCM) has been implemented and intensively tested on many different types of grayscale images of 512 × 512 from the USC-SIPI image database and some binary watermark patterns of 128 × 128 for evaluating its performance. Figure 4 shows some AMBTC compressed image and two visible binary watermark images for evaluation. The block size for AMBTC compression is 4 × 4 (i.e. s = 4). In the experiments, we set parameter τ = 0.01 to avoid division by zero in Eq. (6), and r 1 = 0.1, r 2 = 0.3, W A = 20, G 1 = 128, ρ 1 = 0.9, ρ 2 = 1.3 are empirical values determined by statistical experiments (see Eq. (7) and Eq. (8)). The bifurcation parameter μ = 3.618742 in Eq. (9) is arbitrarily chosen from the range (3.599456, 4).
4.1 Watermarked image quality
Figure 5 shows the visible watermarked images generated by the proposed RVWBCM scheme using AMBTC compressed images with different texture characteristics and various watermark logos from Fig. 4. From these resultant images, we find that visibly embedded watermark logos do not obscure obviously the image details, and that the watermarked images have good visual quality for different types of images although the overlaid visible watermark patterns are visible enough. The corresponding PSNR values of these watermarked images are list in Table 1. From the data in the Table, we can see that the RVWBCM scheme obtains about 24.50 dB PSNR for different host images and watermark patterns on average, and that it can achieve pleasant visual quality of watermarked images under various types of images range from highly textured images to smooth images.
4.2 Watermark visibility
Visibility is a term associated with the human visual perception, and means that the embedded watermarks should have high intensity contrast under satisfactory visual quality of watermark images. At first, we can evaluate subjectively the visibility by carefully observing the watermarked image as shown in Fig. 5. Figure 5 demonstrates that the watermarked images produced by the RVWBCM scheme have satisfactory watermark translucence for various types of test images range from fairly smooth images like Lena to highly textured images like Baboon. Furthermore, the watermark visibility can be measured by the visible watermark content in the difference image between host image and watermarked image as shown in Fig. 6. From Fig. 6, it can be seen that the watermark strength is adaptive to host images and the watermarks are apparently recognizable in different types of watermarked images.
Difference images between host image and watermarked image by embedding logo of Fig. 4e
Finally, an objective measurement called normalized energy (NE) is designed to evaluate the watermark visibility and it can be computed based on the difference image E as follows.
Where e (x, y) denotes the pixel value of difference image E.
We test the normalized energy of difference image of different methods when the PSNR values of watermarked images generated by different methods are roughly the same. Comparisons of watermark visibility are provided in Table 2. The proposed RVWBCM scheme can achieve 47 % higher normalized energy than Yip et al.’s PVMA method [22]. From the table we can observe that the RVWBCM method has better watermark visibility than PVMA scheme [22] for different types of images.
4.3 Comparison of unmarked image quality
In this RVWBCM scheme, given the watermarked image and secret keys, one can remove successfully the visibly embedded watermark pattern from the watermarked image. The visible watermark removal and high-quality restoration of the host image are only dependent on the secret key, and visible watermark removal do not resort to original watermark. This is because that authorized users can extract the binary watermark from the watermarked image before visible watermark removal. In order to evaluate effectively the removability of this proposed visible watermarking scheme, we compare the performance of the proposed algorithm with that of Yang et al. algorithm [19] in terms of PSNR values of unmarked images and the comparison results are listed in Table 3. Note that the RVWBCM scheme uses logo 1 as the watermark pattern and Yang et al. scheme embedded the gray-level version of logo 1 into host images in comparison experiments. From Table 3, we find that the unmarked images legally recovered by the proposed algorithm with the correct secret keys, have 8.20 dB higher PSNR values than those of Yang et al. algorithm on average. This shows that the proposed RVWBCM algorithm is superior to Yang et al. method in terms of the unmarked image quality.
4.4 Robustness
An excellent visible watermarking scheme demands that the visible watermarks overlaid on host images be hard to remove illegally. Figure 7 gives some robustness experimental results by visibly embedding logo1 of Fig. 4e into Lena BTC compressed image. The visible watermark on the attacked images is clearly recognizable. This implies that the watermark component is still in these images. So from Fig. 7 we can see that the proposed algorithm is robust against common image processing attacks such as image enhancement, image filtering, collusion attack, and image compression.
Robustness against image processing attacks. The watermarked images (a), (b), (c), (d), (e) and (f) are generated by histogram equalization, 5 × 5 mean filtering, Laplacian sharpening, averaging 20 different watermarked image versions, JPEG compression with quality factor 10 and JPEG2000 compression with compression ratio 60:1, respectively
4.5 Security analysis
The proposed RVW algorithm has two different combinations of secret key. If each key is a floating-point number of 15 digits, then there are 15 + 15 = 30 uncertain digits. So the possible key space is 1030. The RVW algorithm with such a large key space is sufficient for reliable practical use and has the ability to resist brute-force attack. Figure 8 demonstrates that authorized users with correct keys can remove effectively the embedded visible watermark on the watermarked image. However, illegally recovered image with incorrect user keys contains much too energy residue of the visible watermark, and has low PSNR value of 18.8457 dB. In addition, we compare the proposed algorithm with existing reversible visible watermarking schemes such as Yang et al.’s scheme and Hu et al.’s scheme [6] in order to verify the security against illegal removal, and the comparison experimental results are also listed in Table 4. From Table 4, the average PSNR value of the recovered images by illegal visible watermark removal with the proposed RVWBCM algorithm are about 18.30 dB, and is much lower than that of Yang et al.’s method (about 32.98 dB) and Hu et al.’s approach (about 38.08). This indicates that the proposed RVWBCM algorithm is superior to previous RVW schemes in terms of illegal watermark removal.
Moreover, as we all know, computational complexity of BTC coding is much less than DCT, DWT and VQ. Generally, BTC-based visible watermarking schemes can achieve less time cost than existing schemes based on common image coding standards. Perhaps visible watermarking schemes based on BTC are expected to provide real-time copyright protection via internet.
5 Conclusion
This paper presented a removable visible watermarking scheme applicable for BTC compressed images. The visible watermark strength is adaptive to host image content by exploiting image features in BTC compressed domain. To prevent unauthorized users from recovering the original pixels in the watermarked region, this method invisibly embeds the binary watermark sequence in the visibly watermarked image. This ensures that only authorized user can succeed in remove the visible watermark and obtain high quality unmarked image. The key space is large enough to be able to resist brute-force attack. Moreover, the visible watermark removal doesn’t need the information of original binary watermark, and watermark embedding and watermark removal operate in BTC compressed domain. In a word, the proposed RVWBCM scheme is secure and has low computational cost, and it can provide real-time copyright protection and secure access control of digital media via internet or mobile terminals. In the future, to achieve broader applicability of RVW schemes, we will develop RVW scheme applicable for common compression standard such as JPEG.
References
Chang C-C, Lin C-C, Li K-M (2010) A removable visible watermark for digital images. J Comput 21(3):37–49
Farrugia RA (2010, 26–28 April) A Reversible Visible Watermarking Scheme for Compressed Images. In: Proc. 15th IEEE Mediterranean Electrotechnical Conference (MELECON 2010), Valletta, Malta, pp. 212–217
Fränti P, Nevalainen O, Kaukoranta T (1994) Compression of digital images by block truncation coding: a survey. Comput J 37(4):308–332
Hong W, Chen TS, Shiu CW ( 2008, 27–30 May) Lossless Steganography for AMBTC-Compressed Images. In Proc. 2008 Congress on Image and Signal Processing, vol. 2. Sanya, Hainan, China, pp. 13–17
Hu Y, Jeon B (2006) Reversible visible watermarking and lossless recovery of original images. IEEE Trans Circ Syst Video Technol 16(11):1423–1429
Hu YJ, Kwong S, Huang J (2006) An algorithm for removable visible watermarking. IEEE Trans Circ Syst Video Technol 16(1):129–133
Huang BB, Tang SX (2006) A contrast-sensitive visible watermarking scheme. IEEE Multimedia 13(2):60–67
Lian S (2009) Quasi-commutative watermarking and encryption for secure media content distribution. Multimed Tools Appl 43(1):91–107
Liu TY, Tsai WH (2010) Generic lossless visible watermarking - a new approach. IEEE Trans Image Process 19(5):1224–1234
Liu Y, Zheng D, Zhao J (2007) An image rectification scheme and its applications in RST invariant digital image watermarking. Multimed Tools Appl 34(1):57–84
Luo Y, Zhao Y, Cheng L, Wang J, Liu X (2012) Lossless visible three-dimensional watermark of digital elevation model data. LNCS T Edutainment 7220(8):138–147
Mitchell OR, Delp EJ, Carlton SG (1978, June 4–7) Block truncation coding: a new approach to image compression. In: Proc. the IEEE International Conference on Communications, vol. 1. Toronto, Ontario, Canada, pp. 12B.1.1–12B.1.4
Mohanty SP, Ramakrishnan KR, Kankanhalli MS (2000) A DCT domain visible watermarking technique for images. In: Proc. IEEE Int. Conf. Multimedia and Expo., vol. 2. New York City, NY, USA, pp. 1029–1032
Pareek NK, Vinod Patidar, Sud KK (2006) Image encryption using chaotic logistic map. Image Vis Comput 24(9):926–934
Shie S-C, Lin SD (2008) Improving robustness of visible image watermarks. Imaging Sci J 56(1):23–28
Tsai M-J (2009) A visible watermarking algorithm based on the content and contrast aware (COCOA) technique. J Vis Commun Image Represent 20(5):323–338
Tsai H-M, Chang L-W (2007, 2–5 July) A High Secure Reversible Visible Watermarking Scheme. In: Proc. 2007 I.E. International Conference on Multimedia and Expo. Beijing, China, pp. 2106–2109
Tsaia HM, Chang LW (2010) Secure reversible visible image watermarking with authentication. Signal Process Image Commun 25(1):10–17
Yang Y, Sun X, Yang H, Li CT (2008) Removable visible image watermarking algorithm in the discrete cosine transform domain. J Electron Imaging 17(3):033008-1–033008-11
Yang Y, Sun X, Yang H, Li CT, Xiao R (2009) A contrast-sensitive reversible visible image watermarking technique. IEEE Trans Circ Syst Video Technol 19(5):659–667
Yeh FH, Lee GC, Lin YT (2008, 9–12 Dec) Removable Visible Watermarking in JPEG Compression Domain. In: Proc. 2008 I.E. Asia-Pacific Services Computing Conference (APSCC ‘08), Yilan, Taiwan, China, pp. 1328–1331
Yip SK, Au OC, Ho CW, Wong HM (2006) Lossless visible watermarking. In: Proc. Int. Conf. Multimedia and Expo. Toronto, Ontario, Canada, pp. 853–856
Zhang X, Wang S, Feng G (2011) Reversible visible watermarking with lossless data embedding based on difference value shift. Intell Autom Soft Comput 17(2):233–243
Acknowledgments
This work was supported in part by the National Natural Science Foundation of China under Grant No. 61073191, 61170287 and 61232016, Hunan Provincial Natural Science Foundation of China under Grant No. 10JJ6090, Scientific Research Fund of Hunan Provincial Science and Technology Department of China under Grant No. 2011GK3140, 2010GK3049 and 2011GK3139, Key Program of Hunan Provincial Education Department of China under Grant no. 12A029, Research Program of Humanities and Social Sciences of Chinese Ministry of Education under Grant No. 12YJAZH065, Science and Technology Innovative Research Team in Higher Educational Institutions of Hunan Province under Grant No. [2010]212.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yang, H., Yin, J. A secure removable visible watermarking for BTC compressed images. Multimed Tools Appl 74, 1725–1739 (2015). https://doi.org/10.1007/s11042-013-1714-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-013-1714-3