Abstract
Routing protocols plays a key role in coherent use of resources in Internet of Things (IoT). The more efficient routing scheme is, the more efficiently will nodes communicate with each other. In this paper, we present presents an efficient cluster based routing protocol for IoT. The protocol aims at increasing lifetime and stability of networks. The paper introduces a new routing scheme Modified-Percentage LEACH Protocol based on existing protocol namely Percentage LEACH. Extra amount of energy wastage is alleviated by reducing communication between Cluster Heads (CHs) and sink. Thus, it increases the lifetime of sensor nodes in IoT communication networks. It is achieved by introducing threshold calculation on each CH, which is used as basic criteria for CH election and selection. The protocol also takes into account distance parameter of nodes from sink. This protocol helps plummeting energy wastage which results in more lifetime and high throughput. The depicted protocol is compared with its parent protocol and simulation results shows high throughput and outperforms its parent protocols.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
IoT envisaged a system comprising of large number of everyday objects connected with each other. These objects are smart and intelligent to communicate and share information with other nodes and with the Internet [1]. Technological advancement in field of Micro-Electric Mechanical Systems has enabled scientists to design various type of sensors. These sensors possesses capabilities to sense its environment, gather data about events of interest from its environment depending upon its application, process gathered data and then transfer it to sink [2]. These sensors are cheap, tiny in size and are equipped with sensing, processing, communication components to carry out these tasks with confined resources. WSNs is merely a type of IoT networks that incorporates large number of such tiny and smart sensors. Therefore, the integration of WSN plays an important role in optimizing the use of sensors technology in various fields such as IoT, Cyber Physical Systems, Machine to Machine communication, etc. [3]. WSN are also proposed to be integrated with Cloud [4]. It will enable a wide range of applications such as data integrity, provenance usage and efficient data access across heterogeneous resources in WSN domain [5,6,7].
Due to its small size and applications these nodes are deployed in dense areas and terrains. The mode of deployment may be deterministic or nondeterministic [8]. In deterministic approach large numbers of nodes are distributed in field with proper placement. It is also known as controlled placement technique as nodes are placed according to a specific criterion in field of interest. This type of deployment occurs, when nodes are in reach of humans. In non-deterministic scheme nodes are placed without specific criteria. The deployment usually occurs in area where human interaction is not possible. It is also known as random deployment [9].
Sensor nodes after deployment in an environment organize itself and communicate with other nodes and sink to establish WSN [10]. This communication is based on signal strength, available resources and lifetime of nodes [11]. Sensors are battery powered, which is neither rechargeable nor replaceable because of its deployment [12]. There is no fixed or pre-defined structure/topology of the network because nodes re-organize itself according to environment and application. Network structure changes when nodes move from one location to another [13].
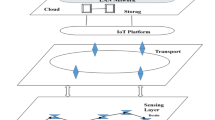
Objective of network is to forward sensed information to base station/sink directly or via other nodes. Sink is the final destination of data in WSNs. It has continuous power and control overall all network operations [14]. It identifies nodes by assigning a unique ID. This unique ID also helps in identification of malicious nodes in network. Figure 1 shows a typical WSN operation.
Communication of nodes with sink may be single-hop or multi-hop depending upon application and network area [15]. In single-hop communication, nodes or CHs directly communicate with sink. If distance is small, single-hop communication may be an option otherwise multi-hop communication scheme is used. In multi-hop communication node transfers data to sink via neighboring nodes. It uses distance as major parameter for data transfer. Each CH after data fusion sends data back to its nearest neighboring CH. The CH nearest to sink is hot-spot, as it receives data from all other CHs of the network.
In recent years, use of WSNs increases because of its usage in different critical applications. Different applications and its use are as follows:
- 1.
WSNs are widely used in Environmental Monitoring. Different environmental projects like Luster, SensorScope, Social Ecology and Volcanoes. In Volcanoes a WSN is deployed that sense seismic events, gather data about its frequency and then forward it to the sink.
- 2.
WSNs are used in Military systems. In Military it is used for border monitoring, intelligence gathering, surveillance, imaging, nuclear and explosives detector, force protection and battlefield awareness.
- 3.
Health-care is a major field in which WSNs is used. It is used in mass causality disasters, monitoring of hospitals, monitoring of patients in their illness, physical and physiological behavior.
Besides these usages WSNs have wide range of applications in areas like environment monitoring, military, smart homes, transport and telematics etc. [16].
With all these applications WSNs have major challenges like self-configuration, ad- hoc-communication and energy usage. Energy is one of key constraint that affects overall network lifetime and operation. This is because nodes are battery powered. If a node energy drains out, it is dead making network unstable and decreasing network lifetime. To increase this lifetime, energy usage may be reduced. To alleviate usage of energy and increase network lifetime efficient Operating System, MAC layer protocols and Routing protocols are required. Our research work focused on plummeting of energy usage using routing protocols.
Rest of paper is organized as, Sect. 2 explains related work. Section 3 describes motivation that provides base for this research. Section 4 describes different issues identified in PR-LEACH protocol. These issues are addressed in Sect. 5 with illustration of solutions to issues. Performance evaluation of the said protocol by comparing it with its parent protocol is explained in Sect. 6. Section 7 depicts conclusion and future work.
2 Related Work
Routing protocols can alleviate energy usage of nodes as it is used during data transfer among different nodes. It define scheme for en-routing data across network. These protocols are divided into four different categories to coup issues of data, location of nodes, scalability and multi-path protocols [17]. Different protocols define different level of hierarchy depending upon deployment environment and application requirement. Different routing protocols that provide base for our research work are as follows:
2.1 Low-Energy Adaptive Clustering Hierarchy (LEACH)
LEACH [18] is hierarchical cluster based routing protocol. It is core routing protocol and served as parent to today advanced routing protocols in WSNs. It divide network operation in rounds, where, each round lasts for specific amount of time depending upon different factors like rate of communication, residual energy etc. Each round has specific number of clusters headed by CHs. Sink define optimal number of CHs in a network depending upon number of nodes in a network. Each round uses two-step process to execute network operation. These steps are setup phase and steady-state phase. This protocol assumes that nodes are immovable and deployed randomly in limited area. Each node deployed in a network is identified by a unique ID. Sink identify nodes by node ID. Steps involved in network-creation and communication among nodes of network are described below:
- 1.
Setup phase: This phase is concerned with formation of cluster, selection of CHs and establishment of network among nodes. Homogeneous nodes in respect of energy are deployed randomly in network field. These nodes re-organize themselves to start process of CH election and selection. Each node elects itself as a candidate for CH. This protocol uses random probabilistic approach to select CHs. To simplify the selection of CHs, a set say G is defined which consists of all nodes that have not become CHs in previous rounds. Candidates for CHs select a random number between 0 and 1. A value of 0 indicate that the node remains CH in previous round and cannot be CH in current round while 1 indicates that it did not remained as CH. The probability of number with 1 is more than that of 0. The selected random value is compared with the equation below.
$$ T\left( n \right) = \left\{ {\begin{array}{ll} {\frac{p}{{1 - p*\left( {r \bmod \left( {\frac{1}{p}} \right)} \right)}},} & {if\;n \in G} \\ {0,} & {otherwise} \\ \end{array} } \right. $$(1)where G = set of nodes that are not selected as CHs, P = optimal number of CHs in network, r = current round.
If selected value of node is less than the specified threshold value, it can become candidate for CH. After selection of CHs, each CH now has to group-up its nearest nodes and create cluster. To create clusters, each selected CH broadcasts an advertisement message about its selection and demands other nodes to become its members. One node may receive message from many CHs. Each node calculate Received signal strength index (RSSI) for different CHs and sends their join request with its unique ID to CHs with highest RSSI. The node now becomes member of the specified CH. The CH will now act as a local controller for its members. Each node will forward their sensed data to CH for further action. Figure 2 shows a set-up process of network. Nodes after completing its session as CH are transferred to a set of node say A which holds all nodes that cannot become CHs in next round. This method allows even distribution of energy across the network because each node get full chance to become CH.
- 2.
Steady-state phase: This phase describes intra-cluster communication among nodes and their CHs. CHs uses contention-free protocol CSMA to communicate with nodes. CH defines time slots for each of its member and forwards it to the nodes. Nodes now use its specific time slot to transfer data to CH. This reduces chances of collision of data and its corruption. Figure 3 shows a set-up process of network. Number of members associated with a single CH is dependent on energy of nodes. The protocol first version is single-hop means each CH directly communicates with sink. The protocol is further extende to multi-hop LEACH, which allow CHs to communicate data to sink via other CHs. Centralized-LEACH is another extension of LEACH protocol that uses centralized approach for selection of CH and establishment of clusters. In this protocol each node sends its status and position to sink. Sink define CHs and its associated members. Communication of nodes with CHs and sink remains same as in LEACH protocol. Different issues in LEACH protocol are overhead involved in change of CH at start of each round which consumes extra energy. Each round repeats the same procedure of set-up and steady-state phase in each round. Each node can become CH because nodes selection is random. There is no defined threshold for selection of CH.
2.2 Vice-LEACH Protocol (V-LEACH)
To overcome the process of CH change which wastes energy, V-LEACH [19], a new protocol is proposed that introduces vice CHs in network. Each cluster is now supported by two CHs. One is known as primary CH and second is known as secondary CH. Primary CH remains CH for cluster until its energy is greater than secondary CH. After drain out of energy from primary CH, Secondary CH takes its part. All members of clusters know about their primary and secondary CH. They automatically switch their sending destination to secondary CH after fall of primary CH. The network operation is divided into rounds with each round composed of two steps. First step is set-up phase which is related with selection of CHs and formation of clusters. In V-LEACH two CHs are selected on basis of distance and energy of nodes. Primary and secondary CH has highest energy in current cluster. Secondary round is steady-state phase which is related to data communication between nodes and its CH. The protocol uses multi-hop approach for sending its data to sink. The protocol decreases energy wastage by reducing overhead of CH change.
2.3 Modified-LEACH Protocol (mod-LEACH)
Mod-LEACH [20] protocol enhances the core LEACH protocol by changing placement mechanism of CH and introducing soft and hard thresholds. The protocol operates in rounds. Each round is divided into set-up phase and steady-state phase. Limited numbers of immovable nodes are deployed randomly in field. These nodes organize itself and elect itself as a candidate for CH. It uses distribution mechanism for selection of CHs. Each node uses probabilistic approach to consider itself for CH. This protocol changes placement mechanism by removing CHs only when their energy is lesser than other nodes of cluster. The protocol uses two type amplification approaches for communication with CHs and with sink. As node require lesser energy to communicate with CH so, nodes adjust their amplification power according to its destination. This removes extra energy wastage during communication. The protocol uses soft and hard threshold to limit number of data transmission to sink. The defined thresholds assist nodes in removal of redundant data. If node senses a specific value and its value is greater than hard threshold, then data is transmitted immediately. In case of soft threshold data sensed is compared with previous data and if its value is found different from the previous one, data is transmitted. The protocol changes core LEACH protocol in two places, one in selection of CHs and second in introducing soft and hard thresholds.
2.4 Percentage-LEACH Protocol (PR-LEACH)
PR-LEACH [21] protocol is variation of LEACH protocol that limits number of CHs in network. It introduces threshold for selection of CHs. If a node value is greater than defined threshold it can become CH otherwise it cannot. The protocol operates in rounds such that each round has two steps. These steps akin to its core LEACH protocol. The steps are Set-up phase and Steady-state phase. First round of PR-LEACH protocol is similar to LEACH protocol because nodes deployed are similar in terms of energy. In second round, nodes energy changes because of their usage in communication. Nodes send their energies to CHs. CHs forward it to sink via other CHs as inter-cluster communication and intra-cluster communication. Both these communications are multi-hop in the said protocol. Sink receives energies from all CHs of network and calculate range from these energies. Sink broadcast this range to all CHs which forward it to their cluster members. Each member of cluster now uses this range to calculate threshold for itself. If energy of node is greater than calculated threshold the node is eligible for CH otherwise the node does not participate in election of CHs. The threshold is calculated using the following formula:-
where PR = Fractional value from 0 to 1, NER = Network energy range.
The protocol repeats this procedure in all rounds of network except first round. The results show extension in stability period of network and increase in number of alive nodes.
2.5 Comparative Analysis
Different Protocols that leads to our research work description are compared with each other using different properties. These properties are Energy Usage, CH Selection procedure, Hop-Count, Scalability and Distribution. The listed properties are different for different protocols. These properties are marked from 1 to 4 according to its strength and capability in specific protocol as shown in Table 1. Marking values are supported by different emphasis. Bold values represents highest mark i-e a protocol whose property is marked 4 has addressed the property at highest level. Italic values makes a specific property in average range while bolditalic values represents property with less strength. Figure 4 illustrate graphical display of marking of protocols with its properties.
3 Motivation
In WSNs lifetime of network depends upon node lifetime [22]. As nodes are battery powered so efficient schemes are required to extend node life by efficiently using its resources because nodes are limited in its resources. Majority of nodes energy wastage is during their communication with other nodes and sink. Primary basis of our motivation is distance of nodes among each other in network. As distance is directly proportional to amount of energy dissipated by a node so if a node communicate with other nodes having higher distances more energy will be lost and nodes will drain out its energy quickly [23]. This issue of distance among nodes requires different strategies during deployment and also during their communication with other nodes and sink. Secondary basis of our motivation is to alleviate extra communication of nodes with nodes/sink. To achieve this we calculate threshold value on CH level rather on sink level. PR-LEACH is a hierarchical protocol that enhances LEACH protocol to make it more efficient.
The protocol calculates Network Energy Range (NER) which is used to calculate threshold for each node during selection of CHs. The protocol estimates clustering mechanism regardless of distance from sink. If distance of node from sink is low, direct communication may be possibility instead of cluster creation which is an overhead. This issue is addressed in our defined protocol. Our proposed protocol MPR-LEACH extends the protocol and takes into account threshold that each node calculates and distance among these nodes. This threshold is based on network energy range calculated by CH of the concerned cluster. In this way nodes with higher energy in specific cluster may become CH reducing energy usage of nodes with lesser energies by preventing it from becoming CHs and node. Contributions of this research work are as follows:
This paper proposed a new hierarchical protocol known as Modified Percentage LEACH (MPR-LEACH). The protocol introduces local threshold calculation mechanism by reducing communication with sink and increasing local control of CH.
This paper takes into account different scenarios occurred during deployment of nodes in a network. It then defines different communication mechanisms for these nodes based on its placement during deployment.
The protocol is compared with its parent protocol and simulation results show its efficiency. Protocols are compared on basis of energy usage, packets sent to sink and number of alive nodes.
The protocol considers a limited area with nodes and the sink. Nodes are battery powered while sink has continuous power. Nodes are deployed randomly in field. These nodes are immovable are homogeneous with respect to energy.
4 Problem Statement
Different issues in PR-LEACH protocol that will serve as our motivation for MPR-LEACH protocol are as follows. As nodes deployed in network area are random so there are different strictures of network based on positions of nodes. Different structures that we considered are as follows:
- 1.
A structure of network in which all nodes deployed are nearer to sink. Distance between nodes and sink are very small and each node can directly communicate with sink.
- 2.
Nodes are deployed in such a way that there distance from sink is high. To communicate with sink large amount of energy is required.
Figure 5 demonstrate two different structures of network after deployment of nodes. In Fig. 5a nodes deployed are very near to sink and hence there distances from the sink are very small. While in Fig. 5b nodes distance from sink is high. As distance is directly proportional to amount of energy usage so large amount of energy is used during communication making drain-out of energy quickly. In PR-LEACH protocol threshold is used as a parameter for selection of node as CH. This threshold is calculated by each node after it get network energy range from sink. Each node in a particular cluster sends its residual energy to CH. CH forward this energy to sink via other CHs. Sink calculate network energy range (NER) and broadcast it to all nodes of the network. The nodes now use this NER to calculate threshold and if its minimum energy is lower than the prescribed threshold it is not capable for becoming CH.
Issue with this procedure is that each node has different amount of residual energy depending upon its participation in data gathering and forwarding. Some nodes may have high energy while some may have less amount of energy. Sink after receiving all these energies calculate NER. This NER is used both for nodes with high energy and nodes with lower energy. After calculation of threshold by each node to consider itself for CH many nodes are deprived from becoming CH. This decrease number of CHs in network increasing number of associated members with each CH making it loaded.
5 Proposed Protocol (Modified-PRLEACH)
In this section we present a new protocol namely Modified-Percentage LEACH Protocol (MPR-LEACH) to overcome the different issues illustrated above. The protocol addresses the above mentioned issues and makes it more efficient in number of alive nodes, total energy consumption and number of packets sent to sink. Following sections give brief overview of MPR-LEACH protocol.
5.1 Introduction
MPR-LEACH protocol is a hierarchical cluster based routing protocol that enhances its parent protocol PR-LEACH. It introduces different mechanism for communication with sink depending upon its structure and also reduce the extra amount communication which takes place during CH election and selection. The protocol outperforms its parent protocol.
5.2 Radio Model
To communicate with nodes and sink, nodes deployed uses first-order radio model. In the said model amount of energy used during communication is dependent on environment and distance. Free space model is type of model used when there is no extra obstacle between the communicating nodes while multi-path model is used when there is obstacle among the nodes that want to communicate with each other. The mathematical form of energy dissipated in both models is as follows:
where ETX = Energy consumed during transmission of data, Eel = Energy required to transmit a message of length l, Efs = Energy loss in free space model, Emp = Energy loss in multi-path routing, ERX = Energy consumed during receiving of data, d = Distance among nodes in which communication occurs, d0 = Threshold value that determine type of first order radio model to be followed: it is calculated as:
5.3 Deployment
Nodes are randomly deployed in network area. Nodes have different structure in network after its deployment depending upon environment and application. If all nodes are nearer to the sink and distance among them is very small. Then nodes communicate directly with the sink irrespective of any clustering mechanism. This is because very small amount of distance exists between sink which is a continuous power source and node [24]. If nodes deployment forms a structure where distance among nodes and sink is larger than multihop communication is used. In case of multi-hop communication clusters are create. Each cluster has a CH which transfer its data to sink via other CHs. Figure 6a represents communication of nodes when nodes deployed are closed to sink while 6b illustrate scenario when nodes are far away from sink.
5.4 Network Operation
Network operation in WSNs uses a round based approach with each round comprises of two main phases. First phase is initialization phase. This phase is concerned with establishment of network, selection of CHs and creation of clusters. In this phase nodes are deployed in network. These nodes organize itself to create clusters. Each cluster is headed by a CH. Second phase is communication phase which define intra-cluster communication among nodes. Number of rounds depends upon application and lifetime of network. The protocol assumes that continuous powered sink and nodes with same software and limited hardware capabilities are deployed randomly in limited area. These nodes are immovable. Each node has a specific ID. Sink identify node from its ID. After deployment of nodes, network procedure starts. Each node reorganizes and re-configures itself to communicate with its nearest neighbor and create a network. It enters into its first phase i-e initialization phase. Figure 7 shows operation of WSNs using MPR-LEACH protocol.
5.4.1 Initialization Phase
Initialization is the first phase of network operation. It is related with election and selection of CHs and establishment of clusters. Sink define optimal number of CHs in network. It is depended on size of network and nodes deployed into it. In first step, CHs are selected on basis of probability and energy. Each node considers itself as a candidate for CH by selecting a value between 0 and 1. The selected value by the node is then compared with the following equation:
where G = set of nodes that are not selected as CHs, P = optimal number of CHs in network, r = current round.
If selected value of the node is smaller than the calculated threshold. It can be a CH or otherwise it is normal node. Probability 0 means that node has never been a CH and it is capable for becoming CH while probability 1 means that is remain as CH in previous rounds. The protocol give even chance to each node to become CH and therefore a node that has already become a CH cannot be CH again in the same round. Optimal numbers of nodes are selected as CHs.
After selection of CHs, each CH broadcast its selection in network. Each normal node get signals from different CH nodes. These nodes after receiving join request from different CHs calculate Received Signal Strength Index (RSSI) and then compare RSSI of different CHs with each other. The normal nodes than sends its join request to CH with highest RSSI. In this way clusters are created.
In second round as network become heterogeneous because of communication across it. Each node sends its residual energy to its specified CH. The CH after getting energies from all nodes calculate specific NER given as
and broadcast it in its own cluster. Each member of the cluster now uses this XER to calculate threshold for CH selection. It is calculated as follows:
where PR = Fractional value from 0 to 1, NER = Network energy range.
Each node of a cluster now compare its residual energy with the threshold calculate for a specific cluster and consider whether it can be a candidate for CH of the said cluster. If its residual energy is low from threshold it cannot be CH otherwise it can be selected as CH.
5.4.2 Communication Phase
This phase is related with communication of nodes with its CH and then CH with sink. MPR-LEACH protocol uses single-hop scheme during intra-cluster communication and multi-hop scheme during inter-cluster communication. After creation of CH selection, it is considered as local controller of the cluster. Nodes join cluster by using RSSI. CH after getting information from different nodes define cluster and intimate it to all its members. Each member node sense data from its environment and deliver it to CH for data fusion. To avoid any kind of collision among data send by nodes to CH. CH uses CSMA time-slot approach. In this approach, CH based on number of members defines time-slots. Each time-slot belongs to specific node. This time frame is shared with all node members. Each node now delivers its data in its specific time-slot. This method reduces collision among data of different nodes. The flowchart in Fig. 8 illustrates working of the said protocol. After nodes deployment, system configuration and initial set-up nodes communicate with each other to establish a network. In set-up phase CHs are selected, this selection in first round is similar to LEACH protocol, because nodes deployed are homogeneous with respect to energy. As nodes become heterogeneous, range is calculated on CH level, which is used for threshold calculation when nodes consider itself for CH election. If energy is lower than threshold, the node becomes member of another cluster. After cluster creation, nodes send their data to CH which forwards it to sink via other CHs.
6 Performance Evaluation
MPR-LEACH protocol and its parent protocol are compared on basis of three basic parameters. These parameters show efficiency of our depicted protocol over its parent. These parameters are number of alive nodes, energy conservation and packet delivery ratio.
- 1.
Number of Alive Nodes
Network lifetime is dependent on lifetime of nodes in network. If nodes remain alive for longer period of time. They will gather data for longer period and hence forward it to the sink for further processing.
- 2.
Energy consumed
Nodes in WSNs are limited in terms of energy. They are battery powered. Change or renewal of batteries in WSNs is almost nil because of its deployment. To prolong network lifetime, nodes lifetime should be prolonged, which is achieved by efficient consumption of energy.
- 3.
Data sent to Sink
The primal objective of nodes gathering data is to forward it to sink. If more data is gathered by the nodes, data sent to sink will be more.
6.1 Results and Discussion
The proposed protocol i.e. MPR-LEACH is compared with its parent protocol PR-LEACH using same parameters. The comparison is conducted using Matlab simulator. Different parameters of environment in which simulation study takes place is described below in Table 2: xm,ym represents x and y axis of network area.
Nodes are deployed in an area of xm*ym such that sink is in the center having 600 × 600. Maximum numbers of rounds are 1500. Total number of nodes that are deployed in network is 100. P represents optimal probability of CHs. Nodes are homogeneous when deployed, as round takes place it become heterogeneous because of its rate of communication and its usage in operation. Energies provided to nodes in the said network are as follows in Table 3:
Simulation study of PR-LEACH protocol and MPR-LEACH protocol is taken on basis of above mentioned parameters. Results of this simulation are shown using comparison graphs. These graphs and their descriptions are as follows:
- 1.
Number of alive nodes
Network lifetime is dependent on number of alive nodes in a network. If nodes survive for greater amount of time, data gathering will be more time as a result of which network operation will continue for more time increases data deliverance to the sink. Figure 9 represents a comparison of the number of alive nodes of PR-LEACH and MPR-LEACH. Overall, graph shows that MPR-LEACH is more efficient that PR-LEACH protocol, this is because more number of alive nodes remained in MPRLEACH protocol. The figure clearly shows that due to reason of lower energy usage because of threshold calculation at CH level and awareness of distance during communication with sink and other nodes prevent excess amount of energy usage which increase alive nodes which results in increased lifetime of nodes. According to figure which shows simulation up to 1500 rounds, first node death in PR-LEACH protocol occurs earlier than MPR-LEACH. The graph of MPR-LEACH significantly shows its efficiency after 500 rounds where 20 nodes remains alive contrary to PRLEACH where all nodes die and network operation stops. Number of alive nodes is raised in MPR-LEACH protocol in comparison to PR-LEACH protocol.
-
2.
Energy Conservation of Nodes
Energy of nodes in a network defines its lifetime. Energy consumption being the key parameter of nodes to operate is required for carrying out various tasks. Figure 10 depicts a graph showing comparison of PR-LEACH and MPR-LEACH protocol using energy conservation as base parameter. According to graph both protocols consumption of energy is same in start, but gradually because of threshold calculation in MPR-LEACH energy consumption decreases. This energy of nodes in PR-LEACH drain out in 700 round when all alive nodes die, while in network using MPR-LEACH protocol, there still remains alive nodes, continuing network operations.
-
3.
Packets Delivery Ratio
Major aim of WSNs is to collect data by using nodes and then forward this data to sink for further processing. As energy consumption of nodes decreases, the lifetime of network increases with increasing number of alive nodes. This increase in network lifetime increases network operations of data gathering and forwarding. Figure 8 illustrates PRLEACH and MPR-LEACH protocol in terms of packets delivery ratio. A total of 3500 are delivered to sink by MPR-LEACH protocol which is larger than PR-LEACH protocol which delivers about 2300 packets in the same round. The packets delivery ratio shows that MPR-LEACH protocol has more throughput than PR-LEACH protocol (Fig. 11).
6.2 Comparative Analysis
In this section MPR-LEACH protocol is compared with its previous protocols using the same properties and marking. The table and graph representing performance of MPR-LEACH as compared to its earlier versions are shown in Table 4.
Figure 12 shows graphical representation of the said table. Table clearly depicts that MPR-LEACH protocol outperform its parent PR-LEACH protocol in number of alive nodes, data sent to sink and energy consumption.
7 Conclusion
The proposed protocol has shown a significant improvement over its parent protocols. The major difference among our proposed protocol and its parent protocol is that our protocol transforms global threshold calculation mechanism to local threshold calculation. This extension improves the selected protocol and makes it more energy efficient. The modified protocol plays a significant role in IoT networks by reducing the amount of energy required for communication between the sensor nodes and outside world such as hubs connected to Cloud. The protocol considers nodes to be immovable in the network. The protocol takes into account only two main schemes of nodes deployment i.e. free space and multi-path schemes. In future we will work on improvement of clustering mechanism and different deployment strategies to make it more efficient.
References
Wortmann, F., Flüchter, K.: Internet of things. Bus. Inform. Syst. Engineering 57(3), 221 (2015)
Carlos-Mancilla, M., López—Mellado, E., Siller, M.: Wireless sensor networks formation: approaches and techniques. J. Sens. 2016, 1 (2016)
Gubbi, J., Buyya, R., Marusic, S., Palaniswami, M.: Internet of things (IoT): a vision, architectural elements, and future directions. Future Gener. Comput. Syst. 29(7), 1645 (2013)
Ahmed, K., Gregory, M.: In: 2011 Seventh International Conference on Mobile Ad hoc and Sensor Networks (MSN), IEEE, pp. 364–366 (2011)
Imran, M., Hlavacs, H., Haq, I.U., Jan, B., Khan, F.A., Ahmad, A.: Provenance based data integrity checking and verification in cloud environments. PLoS ONE 12(5), e0177576 (2017)
Imran, M., Hlavacs, H., Khan, F.A., Jabeen, S., Khan, F.G., Shah, S., Alharbi, M.: Aggregated provenance and its implications in clouds. Future Gener. Comput. Syst. 81, 348 (2018)
Khan, F.A., Ahmad, A., Imran, M., Alharbi, M., Jan, B., et al.: Efficient data access and performance improvement model for virtual data warehouse. Sustain. Cities Soc. 35, 232 (2017)
Jiaying, D., Tianyun, S., Xiaojun, L., Zhi, L.: In: 2016 Chinese Control and Decision Conference (CCDC), IEEE, pp. 6529–6534 (2016)
Sharma, V., Patel, R., Bhadauria, H., Prasad, D.: Deployment schemes in wireless sensor network to achieve blanket coverage in large-scale open area: a review. Egypt. Inform. J. 17(1), 45 (2016). https://doi.org/10.1016/j.eij.2015.08.003
El Emary, I.M., Ramakrishnan, S.: Wireless Sensor Networks: From Theory to Applications. CRC Press, Boca Raton (2013)
Obaidat, M., Misra, S.: Principles of Wireless Sensor Networks. Cambridge University Press, Cambridge (2014)
Liu, X.: A deployment strategy for multiple types of requirements in wireless sensor networks. IEEE Trans. Cybern. 45(10), 2364 (2015)
Thulasiraman, P., White, K.A.: Topology control of tactical wireless sensor networks using energy efficient zone routing. Digit. Commun. Netw. 2(1), 1 (2016)
Agrawal, D.P., Zeng, Q.A.: Introduction to wireless and mobile systems. Cengage Learning, Boston (2015)
Rani, S., Ahmed, S.H.: Multi-hop Routing in Wireless Sensor Networks: An Overview, Taxonomy, and Research Challenges. Springer, Berlin (2015)
Preethichandra, D.: In: 2015 9th International Conference on Sensing Technology (ICST), IEEE, pp. 50–53 (2015)
Kumari, J. et al.: In: 2015 2nd International Conference on Computing for Sustainable Global Development (INDIACom), IEEE, pp. 325–330 (2015)
Heinzelman, W.R., Chandrakasan, A., Balakrishnan, H.: In: Proceedings of the 33rd Annual Hawaii International Conference On System Sciences, IEEE (2000)
Sindhwani, N., Vaid, R.: V LEACH: an energy efficient communication protocol for WSN. Mech. Confab 2(2), 79 (2013)
Mahmood, D., Javaid, N., Mahmood, S., Qureshi, S., Memon, A., Zaman, T.: In: 2013 Eighth International Conference on Broadband and Wireless Computing, Communication and Applications (BWCCA), IEEE, pp. 158–163 (2013)
Salim, M.M., Elsayed, H.A., El Ramly, S.H.: In: 2014 31st National Radio Science Conference (NRSC), IEEE, pp. 252–259 (2014)
Pourazarm, S., Cassandras, C.G.: Optimal routing for lifetime maximization of wireless-sensor networks with a mobile source node. IEEE Trans. Control. Netw. Syst. 4(4), 793–804 (2017)
Pourazarm, S., Cassandras, C.G., Zaman, N., Low, T.J., Alghamdi, T.: In: 2015 17th International Conference on Advanced Communication Technology (ICACT), IEEE, pp. 587–595 (2015)
Iyengar, S.S., Brooks, R.R.: Distributed Sensor Networks: Sensor Networking and Applications. CRC Press, Boca Raton (2016)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Khan, F.A., Ahmad, A. & Imran, M. Energy Optimization of PR-LEACH Routing Scheme Using Distance Awareness in Internet of Things Networks. Int J Parallel Prog 48, 244–263 (2020). https://doi.org/10.1007/s10766-018-0586-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10766-018-0586-6