Abstract
Study of pipeline networks which are used to transfer gas and oil from the production sites to consumers has widened all over the globe. On the other hand, there is a colossal loss of resources due to spills and leakages caused by natural disasters, human sabotage, and wear and tear of pipeline infrastructure. Serious economic losses can be faced in transportation of fluid through these anomalies that may incur additional costs for the final consumer. Nuclear fluids may also damage infrastructure and cause health risks to both humans and marine life. This issue is very critical to fulfill the energy demands of population in the entire world. For this purpose, a comprehensive study of recent pipeline anomalies detection techniques was performed. We proposed an effective solution to monitor pipelines and provided a framework for anomaly localization using Cooja simulator and geographical information systems that can also be used in pre-disaster management scenarios, i.e. pipelines can be maintained prior to actual leaks and spills. Timely precautionary measures can thus be taken during the pre-disaster, disaster and post disaster stages, thereby minimizing wastage of natural resources. We also compare localization accuracy with two detection and localization techniques namely: negative pressure wave and pressure point analysis.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Large amounts of fluids are transported through pipelines which are the dominant source to cover long distances. Thus, anomalies in pipelines is a critical problem that may lead to huge environmental pollution and economic losses which must be controlled in order to enhance efficiency to supply fluids from one place to another (Ostfeld et al. 2008; Sheltami et al. 2016). The main causes for pipeline leakages could be human carelessness, natural accidents or pipeline material and infrastructure. Most of the methods used for leak detection consist of some maintenance personnel who monitors the pipeline on periodic basis, but one main disadvantage of this method is slow response. Due to aforementioned problem, the fluid transportation system can face more economic losses.
The novel advancements in wireless and control technology instigated us to work on WSNs (Liu et al. 2013). Wireless sensor networks (WSNs) based applications are continuously improving with rapid technological advancements in micro electro mechanical systems (MEMS) (Katiyar et al. 2010). Internet of Things (IoT) which is also based on WSNs is a hot area nowadays for the researchers (Belli et al. 2016; Sun et al. 2016). They play significant role in achieving goals of IoT by gathering environmental context and surrounding information for different applications in IoT.
This paper aims to: (1) address the issues of sensing and detecting pipeline network leaks through WSNs. (2) Make a comparative study between current detection and localization algorithms to assess localization accuracy. (3) Propose an effective solution to monitor pipelines and develop a framework for anomaly localization in pipelines. (4) Compare localization accuracy with existing techniques.
We have developed our own framework for anomaly localization using Cooja simulator. The focus of this paper is on the accuracy of localization protocols.
The paper outline is organized as follows: Sect. 2 has an extensive literature review, with the classification of different anomaly detection techniques, hardware and software based anomaly detection methods. Section 3 defines our framework. Section 4 presents implementation and evaluation of negative pressure wave (NPW) and pressure point analysis (PPA) methods. In Sect. 5, invasive sensor with time stamps (ISTS) localization technique is proposed and implemented using the developed framework. In Sect. 6, NPW, PPA and ISTS are evaluated based on localization accuracy with conclusion, future work and recommendations. Section 7 concludes with ISTS design considerations.
2 Literature review
Design and deployment of WSNs in pipeline leak detection depends upon fluid type and the environment in which the pipeline is going to be placed (Sportiello 2013). Generally, fluids transported through pipelines are thermal fluids, sewage, gas, oil and water. Pipelines are usually placed either inside or outside water, or underground or above ground on soil (Maglaras and Katsaros 2012). The surrounding environment and fluid type in pipelines are important factors that guide the decision of whether the WSNs are to be placed inside or outside the pipe for leak detection (Abdallah 2011). WSNs for leak detection are broadly classified based on the communication mechanism they adopt with one another as well as with fluid itself (Mustafa and Chou 2012). The sensors that are in contact with fluid are called invasive while those that are not in contact are called noninvasive sensors. Vibration and acoustic sensors are non-invasive while velocity, flow and pressure transients are invasive (Sheltami et al. 2017).
2.1 Classifying leak detection techniques
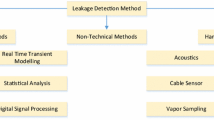
In the literature, leak detection techniques are classified into various categories as per different criteria. These criterion include: level of human dependence, number of sensors required and technological structure (Murvay and Silea 2012). If classification is based on the level of human dependence, the system can be classified into manual, semi-automatic and fully automatic based on number of humans involved. Based on the type of instrumentation, researchers who use optical instruments for leak detection classify into optical and non-optical methods (Sivathanu 2003). However some of the researchers categorize these methods into inferential, direct and indirect (Folga 2007). Direct methods deal with leak detection and pipeline monitoring based on visual inspection and hand held devices to measure gas diffusion, whereas inferential or indirect methods deal with leak detection based on variation of certain parameters of a particular pipeline such as pressure and flow rate.Two other categories of pipeline leak detection include software and hardware based methods, where the hardware based method is very effective in leak detection and localization with the help of specially designed precise instruments. Hardware based methods can be further classified based on the use of detection equipment. These methods include ultrasonic flow meters, soil monitoring, optical, vapor sampling, cable sensor and acoustic. But these methods are expensive and difficult to install, therefore, their usage is limited in places with high possibility of risk such as natural disaster areas, rivers or pipelines with dangerous materials (Murvay and Silea 2012).
In software based methods, algorithms are used to detect leaks by continuously monitoring the state of pipeline parameters such as pressure, temperature, flow rate etc. Based on their technical nature, leak detection methods are classified as software based methods, hardware based methods and non-technical methods. While non-technical methods do not contain any kind of technical device rather they rely more on human or animal senses (Murvay and Silea 2012).
2.1.1 Hardware based leak detection
This section explores the hardware based method in more detail and also includes recent research works and a generic discussion considering the advantages and disadvantages of the method.
2.1.1.1 Fiber optic sensing
In this method, a fiber optic cable is installed throughout the pipeline to monitor leak detection. According to this method, the material in the pipeline gets physically connected with the fiber cable in case of leak occurrence. When material is touched with the fiber cable, the cable temperature changes from where the leak can be detected.
The method works on the principle of optical time domain reflectometry (OTDR) or Raman effect in which the light of laser is dispersed when laser pulse is expanded throughout the fiber due to molecular vibrations. In this way, the information about change in temperature is carried through dispersed light along the pipeline. There are two methods: (1) Raman based. (2) Brillion based. For long term perspective, Brillion based method is more stable and accurate (Rajeev et al. 2013).
The major advantage of fiber optics is its resistance to the interference of electromagnetic waves. However, it also has certain drawbacks that include maintenance and installation costs as well as its insensitivity towards a variety of heterogeneous applications for pipeline monitoring. This method is also not suitable for existing underground pipelines because of the need of an extra excavation to find a suitable place for its installation (Murvay and Silea 2012).
2.1.1.2 Soil monitoring
Soil monitoring uses a nonhazardous and low cost gas tracer to be sent into the pipeline. The tracer consists of high quality volatile gas that escapes from the exact leakage point. Outer soil of pipeline is examined in case of any possible leak and its location can also be found out (Lowry et al. 2000). The method becomes reliable if more alarms are associated with the detection of small leaks but the one major disadvantage of this method is the pipeline must be fed with a gas tracer continuously along with the material to be transported which makes it much costly. Furthermore, this method is also not suitable for uncovered pipelines without surrounding soil.
2.1.1.3 Acoustic detection
In this method, sensors are placed at both edges of pipes where the leak is likely to occur. The deployment of sensors can be carried out directly on suspected points or over road surfaces like fire hydrants.
Leak location could be found through velocity of sound propagation, sensing points distance and lagging time. Leak location could be detected through the equation below (Geiger et al. 2003):
where d is the distance among sensors, d1 represents the distance from leak to sensor S1. c represents the velocity of propagation of sound waves and tpeak represents difference of time among same frequencies in each sensor.
Acoustic detection technique has one major advantage in terms of feasibility of continuous monitoring of pipeline for leakage detection. A real time leak detection system was proposed by Avelino et al. (2009) which did not offer leak localization in contrast with Murvay and Silea (2012) where leak’s size and location can also be determined. On the other hand, vehicular pump and valve noises affect efficiency of this method as they will also be detected at sensor ends. In terms of cost, large numbers of sensors need to be installed on pipelines which also limit its feasibility to cover long distance pipelines. It is useful for pipelines up to 100 m long. Its efficiency also depends upon the skills and proficiency of operator (Ghazali 2012).
2.1.1.4 Liquid or vapor sensing tubes
In this method, a vapor or liquid sensing tube is installed along the whole pipeline for leakage detection. This tube is filled with air while being in atmospheric pressure. Whenever the leak occurs the liquid inside the pipeline gets in contact with the tube and then penetrates inside. An electrolyte cell is deployed along the detected line. An accurate gas volume is transmitted into the tube through electrolyte cell. The gas and air travel from the entire length of sensing tube. The level of gas concentration increases with increase in leak substance which indicates the size of leak. The test gas generates an end peak when it passes from the detector. End peak indicates the entire length of sensing tube. Leak localization can be determined by computing ratio of end peak arrival and leak peak arrival (Geiger et al. 2006).
The disadvantage of this method is its slow response time for leak detection. Also, the cost of installation in long pipelines is very high due to which it is not suitable in terms of practical implementations. This method is also very complex to be adopted for above ground applications as well as for deep sites.
2.1.1.5 Liquid sensing cables
Along with pipelines, these cables are installed to show changes in energy pulses. The changes occur because of impedance differentials and the energy pulses that are safe are sent via cables. As energy pulses pass through the cable, reflected energy map is saved in the memory and reflections are turned back to the monitoring unit. The electrical properties are changed when the liquid inside the pipeline, in the case of sufficient leakage, makes the sensor cable wet. This variation would become the cause for reflection at that point and the leak is localized through this variation. The lag between reflected pulse and input pulse is used to calculate time of localization (Geiger et al. 2006). This method is suitable for short pipelines and for multiple leakage detection and localization.
2.1.2 Software based methods
Software based methods are briefly explained. General discussion, merits and demerits of recent research work for these methods is also described in this section.
2.1.2.1 Negative pressure wave method
In NPW method, pressure is dropped when the leak occurs. This is because of the unexpected reduction in the density of the liquid at the leakage site. Consequently, the source of pressure waves travels outwards from leakage point in the opposite direction of leak. The fluid pressure is noted down after and before the leak occurs and the wave generated by this leakage is named as negative pressure wave. The signal of pressure reduction is measured by pressure sensors that are deployed in terminal ends. Various negative pressure time differences are obtained at the terminal ends because the leak can occur at any point on the pipeline. With the help of measured time differences obtained through pressure sensors deployed on the two sides, the point of leak, negative pressure wave velocity and length of pipeline section can be determined (Ge et al. 2008; Ma et al. 2010).
In Fig. 1, the distance is considered as L, negative pressure wave velocity is represented as v, natural gas velocity in pipeline is depicted as u, the distance between upstream sensor and leak location is x and time is represented as t1 and t2 for the detection of wave through two sensors.
Distance x between sensor and leak point can be determined through Eq. 1 (Hou et al. 2013).
Equation 2 is known as formula for general leak localization. Hou et al. (2013) and Shuqing et al. (2009) demonstrated a customized form of general leak localization.
High false alarm rate is a challenge in NPWM that occurs because of pressure drops at transducers due to normal transient of pipelines. Sometimes larger pressure drops may occur due to these transients (that include opening and closing of pump valves) than drops caused due to leakage. Flow balance method can be integrated to solve the problem of high rates of false alarms in NPWM (Ma et al. 2010; Peng et al. 2011; Tian et al. 2012).
Accuracy of leak localization is also affected by inefficient time synchronization of upstream and downstream sensors that are used for monitoring purposes. Small time deviations in monitoring may come up with a large error of localization (Ma et al. 2010) Non-sudden leaks go undetected by the sensors deployed at terminal ends due to the low intensity of negative pressure waves (El-Shiekh 2010).
2.1.2.2 Mass balance method
The mass balance method is considered very simple and is based on the process of mass conservation (Burgmayer and Durham 2000; Martins and Seleghim 2010). When the volume of fluid entering and leaving the pipeline exceeds a threshold level, an alarm is raised. Liu (2008) addressed the difficulties in implementations. The mass balance method hybridized with probabilistic method (Rougier 2005) offers low cost implementation by giving the advantage of using already available instrumentation over the pipeline (Murvay and Silea 2012; Wan et al. 2011).
Performance of the mass balance method depends on measuring instrument accuracy and frequency to obtain balance measurements and leak size. The major drawback of the mass balance method is that it cannot perform real time small leaks detection which results in the loss of plenty of fluid before an alarm is raised. One more disadvantage of the mass balance method is that it is much more sensitive and likely to be affected by random dynamics and disturbances that typically occur in pipelines from time to time. Hence, to avoid high rates of false alarms during transient period of pipeline, threshold values are necessary to be adaptive. This method needs an additional localization method to localize the leak which it cannot perform alone.
2.1.2.3 Pressure point analysis
Pressure point analysis (PPA) is one of the significant methods to detect leakages in pipelines (Wan et al. 2011). It requires continuous pressure measurement throughout the whole pipeline at different locations. Whenever a mean pressure value is recorded to be below a threshold level, a decision for raising an alarm is made through statistical analyses of measurements. One of the methods uses a pressure gradient model. Fluid mechanics state that, due to frictional losses steady state pressure drops linearly in a straight horizontal pipe (Mysorewala et al. 2015). When an anomaly occurs, we see noticeable increase in slope of the line before leak and decrease in slope of the line after leak. Anomalies can be localized by finding the intersection of two slopes.
This method offers low cost and is easy to maintain because it only needs pressure signals that are delivered through detection points. This method is also suitable for underwater and cold environments. It also has the ability to detect small leaks which other methods cannot (Murvay and Silea 2012; Wan et al. 2011). On the other hand, it is unreliable for leak detection and localization in transient flows which limits its functionality in several applications.
3 Methodology
Cooja is an open source Java based WSN simulator. It is not specialized for pipeline monitoring purposes. We developed our own framework for anomaly localization in pipelines. It provides not only an elucidation for pipeline monitoring but also a framework for anomaly localization with geographical information systems (GIS). The first step was to conduct an extensive literature survey of recent leak detection and localization techniques. Then, we proposed an effective solution for pipeline monitoring. The next phase was to simulate the proposed solution. We used Cooja simulator as a part of our framework, but any other simulator can be used. External script support (ESS) and external modular support (EMS) are used to give support for pipeline monitoring. ESS and EMS act as an external aid for simulator e.g. external mobility plugin was used as EMS to aid in node mobility. Several python Scripts were used as ESS to generate node positions. ESS was also used for controlling simulations i.e. repetitions, stop at specific time etc. After successful simulation, data is sent to middleware application (MAP) for further processing and calculation. MAP can do memory intense calculations for final localization results. MAP has the capability to generate GIS compatible data to transform anomalies and pipeline data to a real time GIS. Python scripts were written for final data projection using various coordinated systems. With GIS, there are two main coordinate systems: (1) geographical coordinate system (GCS). (2) Projected coordinate systems (PCS). Both coordinates provide a framework for defining real world locations. GCS mainly refers with the use of latitude and longitudes i.e. spherical coordinate system whereas PCS provides mechanism to project maps’ spherical surface to a two-dimensional Cartesian coordinate plane. There are hundreds of GCS and thousands of PCS available with varying parameters like units of measurement, datum, central median, spheroid of reference, shifts in − x − y directions, measurement framework (geographic/plain metric) etc. Data can thus be projected to any of GCS and PCS. Figure 2 shows the workflow followed to achieve our goals. Note: the path for google API is not followed in this thesis. It was plan B, in case GIS integration fails.
4 Implementation
Most of the pipeline anomaly detection techniques proposed can detect leaks but are not able to localize properly. Among the limited number of localization techniques, we chose two state of art techniques NPW and PPA which are able to detect and localize leaks and compare against our proposed ISTS technique.
4.1 NPW implementation
4.1.1 Topology
NPW method is implemented on Cooja network simulator using Contiki OS. The topology is defined such that there is a pipeline of 5 km. Every 1000 m a sensor is deployed including the start and end. The network deployment area for NPW is 1 × 5000 m.
Each sensor acts as upstream and downstream sensors depending on the scenario. The distribution is six upstream/downstream sensors and an anomaly sensor (an emulator for anomalies). Anomalies can be tested at several locations in the study area.
4.1.2 Evaluation
NPW method is evaluated by analyzing the difference between the actual anomaly location and the localization accuracy achieved by the implemented algorithm as shown in Fig. 3.
NPW is analyzed and tested at 50 different locations. It can be further concluded that negative pressure wave method is not suitable for longer distances. Due to large differences in ∆t, its accuracy is highly affected. Figure 4 shows variance of NPW method with the ideal. Zero is taken as the reference/ideal point. Least variance is better.
It can be further analyzed from Fig. 3 that accuracy is worst up to the scale of approximately ± 500 m when the anomaly is felt close to upstream or downstream sensors. Figure 5 shows percentage accuracy over 5 km.
NPW is also evaluated in terms of accuracy w.r.t to varying oil viscosities. Several types of oil samples are taken with varying gravities and viscosities. See Table 1.
It is noted that overall behavior of the curves remains the same. But noticeable differences in accuracy can be seen between different grades, especially between low grade having specific gravity 0.81, viscosity − 4 cSt and extra heavy having specific gravity 0.88, viscosity 337 cSt. See Fig. 6.
Figure 6 shows variance comparison of accuracy between light and extra heavy grade oil with zero as a reference point.
4.2 PPA implementation
Pressure point analysis (PPA) is one of the novel methods for anomaly detection and localization. Generally, it requires continuous pressure measurement in whole pipeline at different locations. Whenever a mean pressure value is recorded to be below threshold level, a decision for raising an alarm is made through statistical analyses of measurements. One of the methods is using pressure gradient model. Fluid mechanics state that, due to frictional losses steady state pressure drops linearly in a straight horizontal pipe (Mysorewala et al. 2015). When an anomaly occurs, we see a noticeable increase in the slope of the line before leak and a decrease in slope of the line after the leak. Anomalies can be localized by finding the intersection of two slopes.
4.2.1 Topology
PPA method is implemented on Cooja network simulator using Contiki OS. The topology is defined such that there is a pipeline of 5 km. Every 1000 m a sensor is deployed including the start and end. The network deployment area for NPW is 1 × 5000 m. The distribution is six sensors and an anomaly sensor (emulator for anomalies). Anomalies can be tested at several locations in the study area.
Data is then sent to MAP for further analysis, calculations and finalized results. MAP acts as a statistical analyzer and a display device. Gradient model is also implemented in MAP and compared with data collected from Cooja.
4.2.2 Evaluation
PPA method is evaluated by analyzing the difference between the actual anomaly location and the localization accuracy achieved by the implemented technique as shown in Fig. 7.
It is analyzed and tested at 50 different locations with 160 simulations. Figure 8 shows variance of the PPA method with the actual anomaly location. Zero is taken as the reference/ideal point. Least variance is better. It can be concluded that the points where anomalies occur near pressure transducers have less error in localization. This is because the effect of pressure drops due to leaks is more accurately heard nearby as compared with the pressure drops away from pressure transducers. It is observed that this method gives accuracy up to ± 112.38 m. Figure 9 shows percentage accuracy of PPA over 5 km.
5 Invasive sensors with time stamps (ISTS) algorithm implementation
5.1 Algorithm description
In this section, we propose invasive sensors with time stamps (ISTS) algorithm, a novel technique for anomaly detection and localization following our own framework defined in Sect. 3. ISTS technique is implemented on Cooja simulator. It localizes anomalies not only after an anomaly or a group of anomalies has occurred but also works well in pre-disaster management scenarios. Careful precautionary measures can thus be taken before the actual disaster occurs. Anomalies (∆1, ∆2, ∆3, … ∆n) are localized by using special type of invasive sensor (IS) attached along with a depth gauge. Several sensors are installed on various fixed locations on a pipeline known as FP’s i.e. FP1, FP2, FP3, …, FPn. These sensors can communicate at the backend server. Data is continuously being updated. Anomalies are localized by using reference of FP’s. IS moves from one FP to another. During its journey, it maintains its clock and takes pipeline thickness readings using the depth gauge. Wherever the thickness drops below preset threshold, it registers its first clock (T∆1) and average accelerometer reading (V∆1) in its memory element. Similarly, for second and third drops up to jth drop {T∆2V∆2, T∆3V∆3, …, T∆jV∆j} are registered. When it passes any FP, FP sensor shares its respective location id (L1, L2, L3, …, Ln). On receiving location id’s, IS replies back with data collected during the last interval with the current clock readings (Tn, Tn+1, Tn+2, …, Tn+k) and average accelerometer readings (Vn, Vn+1, Vn+2, …, Vn+k). See Fig. 10.
First anomaly location (∆1) is calculated as
where
K is the total number data exchanges at a specific FP
Similarly, for second anomaly location ∆2
where
\(\Delta {T_2}=\left( {\frac{{\mathop \sum \nolimits_{{i=0}}^{{k - 1}} {T_{n+i}}~}}{k}} \right) - {T_{\Delta 2}}\)
For jth anomaly location ∆j
where
\(j \in \{ (1),~(1,2),(1,2,3),~ \ldots \;{\text{maximum}}\;{\text{number}}\;{\text{of}}\;{\text{feasible}}\;{\text{anomalies}}\} .\)
ISTS is capable to localize multiple anomalies. Three test scenarios were run on 1 × 5000 m pipeline in Cooja. These are as follows:
-
Scenario 1: When there is single anomaly.
-
Scenario 2: When there are multiple anomalies between different pairs of FP’s.
-
Scenario 3: When there are multiple anomalies between single pair of FP’s.
5.2 GIS integration
GIS technology is a system of software and hardware that supports capture, manipulation, management, analysis and display of geographic information. It is an enormous technology that maximizes the efficiency of decision making and planning similarly like today ERP systems are for Business. It provides a platform for extensive spatial analysis for researchers and decision makers with new flexibilities and research directions. GIS plugin in our MAP application can be used to project sensors, pipeline and anomaly data to a real time GIS for further analysis. GIS compatible files are generated. Then using python scripts point and line features are created and projected using specified projection system. For details about projection systems refer to Sect. 3. Currently this MAP version supports locations only in decimal degrees. To generate GIS compatible anomaly data, any of the three algorithms must be run once. The block diagram of the framework followed to attain integration is shown in Fig. 11.
It shows that GIS area of MAP requires field coordinates of sensor or pipeline, with localization data as an input to the system using any of the techniques (NPW, PPA, ISTS). Sensors’ point features and pipeline line features are generated using ‘GIS compatible data’ button. Similarly, anomaly point features are generated using ‘generate GIS anomaly data’ button under the condition that at least any of the three algorithms must be run once. With the help of python scripts, data is then projected to GIS technology. Figure 12 shows the sample GIS output for ISTS scenario 1 discussed in Sect. 5.1, where the anomaly was localized at 2688 m from start. Black point features are the sensor locations. Red point feature is an anomaly location in real time geographical location.
Similarly, GIS Outputs for ISTS scenarios 2 and 3 discussed in previous Sect. 5.1 are also shown in Figs. 13 and 14.
5.3 Evaluation
ISTS algorithm is evaluated by analyzing the difference between the actual anomaly location and the localization accuracy achieved by the implemented algorithm as shown in Figs. 15 and 16.
It is tested at 50 different locations. Figure 17 shows variances of ISTS algorithm with the actual anomaly location. Zero is taken as the reference/ideal point. Least variance is better. It is observed that this method gives accuracy up to ± 46.8 m.
After several experiments, it was observed that errors in localization were shifts with a constant value. Thus, localization accuracy can be improved further by introducing a constant recalibration factor (RF). Hence, final equations of algorithm become as in Eqs. 7 and 8.
For a specific implementation, RF will be calculated after experiments. Figure 18 shows the improved version of ISTS where overall localization accuracy is increased by 50%
Figure 19 shows comparative variances of ISTS with RF and without RF. It is observed that, localization error in the vicinity of sensors is increased in contrast with the older version. But overall localization accuracy is improved from ± 46.8 to ± 23.4 m.
Figure 20 shows percentage accuracy of ISTS over a distance of 5 km.
6 Results
Negative pressure wave, PPA and ISTS combined variances are compared. Figure 21 shows the comparison of ISTS algorithm without RF against the other two techniques—NPW and PPA.
Figure 22 shows the comparison of ISTS algorithm with RF against the other two techniques—NPW and PPA.
Figure 23 shows the average accuracy of the ISTS, PPA, NPW algorithms with light and extra heavy grade. PM with R.F outperforms all with the average accuracy of 11.976 m.
Figure 24 shows the confidence intervals for ISTS, PPA and NPW. These confidence intervals are calculated based on the difference in accuracies on the data set of 50 samples. With 95% confidence, it can be concluded from the figure that accuracy results of techniques will never overlap each other. NPW results may overlap because NPW light and NPW heavy belong to same class with difference in grade of oil. Area of NPW heavy grade oil overlapped by light grade oil light is 10.25%. It means there is probability of 0.1 that results of NPW heavy will match with the results of NPW light. Similarly, there is a 0.13 probability of getting better results than NPW light. On other hand, most of the area of NPW heavy is higher than NPW light. It can be concluded that there are 73% chances of getting bad localization results when using heavy grade oil as compared with light grade oil. This also demonstrates that for NPW, the type of the material is an important factor that affects localization accuracies.
7 Conclusion and future work
This work simulated and evaluated NPW and PPA in terms of accuracy and compared them against our proposed technique. ISTS algorithm supersedes the other two. Its accuracy is not affected by pipeline transient flows and type of material. Time synchronization is also not an issue as the clock is maintained by IS. Moreover, with scheduled monitoring, preventive measures can be taken before an actual anomaly/disaster occurs with zero fluid loss. This is not possible with the other two techniques. However, it incurs high implementation costs on existing pipeline infrastructure. The whole pipeline infrastructure needs to be redefined. In addition, design of IS sensor is also a challenge, which is left for future work.
On the other hand, PPA and NPW incur low implementation cost but are unreliable in anomaly localization and detection for transient flows. With PPA, occurrence of multiple anomalies at different locations at the same time instant cannot be detected or localized. However, at different time instants, localization is possible under the condition that system should be re-stabilized and starts adhering pressure gradient profile. Pipeline gradient profile is also affected by the natural curves and turns of the pipe. Pipelines should be straight and horizontal. With NPW, time synchronization is also a critical factor because only a little deviation in time may come up with a large localization error. It cannot localize multiple anomalies that occur at the same time. Multiple anomalies occurring at different locations within a range of single pair of upstream and downstream sensors cannot also be detected. However, multiple anomalies occurring at different locations within a range of different upstream and downstream sensor pairs can be detected and localized. If negative wave is somehow missed or not able to reach the end sensors, there is no way to detect this anomaly later on. With the ISTS method, occurrence of multiple anomalies at different locations at the same or different instants of time can be detected and localized.
8 Design considerations
The design of IS and pipeline infrastructure should be such that it can be deployed and evacuated from several locations along the pipeline. These are called as deployment units. The distance between two deployment units depends on the energy capabilities of IS i.e. how far it can move. IS is also supposed to be moved at a constant speed. Small variations in speed will not affect localization accuracy due to averaging accelerometer reading parameters taken at anomaly locations. In case of failure due to huge variations in speed between two FP’s, ISTS will still be able to detect anomalies but with the increase in localization error. The maximum realizable localization error is the area of pipeline between two consecutive FPs—FPn and FPn+1. ISTS is flexible enough to handle such situations and re-localize itself when it crosses any FP. The localization accuracy of anomalies will not be affected for upcoming anomalies after FPn+1. However, hybrid detection and localization techniques can be used in case ISTS fails. The other design requirements that IS should have is a clock. Depending on the design of IS, if stepper motors are used for motion, clock ticks can be updated with the ticks of stepper motor. Memory elements are also required to store anomaly data. An accelerometer unit, that can measure meter per second dimensional quantities like speed, velocity with capability of taking averages since last reset. Depth gauge unit should be capable of sensing pipeline thickness readings continuously throughout pipeline infrastructure. Finally, design of IS should be flexible enough to support varying pipe sizes.
References
Abdallah S (2011) Generalizing unweighted network measures to capture the focus in interactions. Soc Netw Anal Min 1(4):255–269
Avelino AM, de Paiva JA, da Silva RE, de Araujo GJ, de Azevedo FM, Quintaes FdO, Salazar AO (2009) Real time leak detection system applied to oil pipelines using sonic technology and neural networks. In: Paper presented at the industrial electronics, 2009. IECON’09. 35th annual conference of IEEE
Belli L, Cirani S, Davoli L, Ferrari G, Melegari L, Picone M (2016) Applying security to a big stream cloud architecture for the internet of things. Int J Distrib Syst Technol (IJDST) 7(1):37–58
Burgmayer PR, Durham VE (2000) Effective recovery boiler leak detection with mass balance methods. In: Paper presented at the Proceedings of TAPPI engineering conference
El-Shiekh T (2010) Leak detection methods in transmission pipelines. Energy Sources Part A Recov Utili Environ Eff 32(8):715–726
Folga SM (2007) Natural gas pipeline technology overview (No. ANL/EVS/TM/08-5). Argonne National Laboratory (ANL), Argonne, IL, United States
Ge C, Wang G, Ye H (2008) Analysis of the smallest detectable leakage flow rate of negative pressure wave-based leak detection systems for liquid pipelines. Comput Chem Eng 32(8):1669–1680
Geiger G, Werner T, Matko D (2003) Leak detection and locating—a survey. In: Paper presented at the PSIG annual meeting
Geiger G, Vogt D, Tetzner R (2006) State-of-the-art in leak detection and localization. Oil Gas Eur Mag 32(4):193
Ghazali MF (2012) Leak detection using instantaneous frequency analysis. University of Sheffield, Sheffield
Hou Q, Ren L, Jiao W, Zou P, Song G (2013) An improved negative pressure wave method for natural gas pipeline leak location using FBG based strain sensor and wavelet transform. Math Probl Eng 2013(2013):278794. https://doi.org/10.1155/2013/278794
Katiyar V, Chand N, Soni S (2010) Clustering algorithms for heterogeneous wireless sensor network: a survey. Int J Appl Eng Res 1(2):273
Liu A (2008) Overview: pipeline accounting and leak detection by mass balance, theory and hardware implementation. Quantum Dynamics Inc., Woodland Hills
Liu Y, He Y, Li M, Wang J, Liu K, Li X (2013) Does wireless sensor network scale? A measurement study on GreenOrbs. IEEE Trans Parallel Distrib Syst 24(10):1983–1993
Lowry WE, Dunn SD, Walsh R, Merewether D, Rao DV (2000) Method and system to locate leaks in subsurface containment structures using tracer gases. Google Patents
Ma C, Yu S, Huo J (2010) Negative pressure wave-flow testing gas pipeline leak based on wavelet transform. In: 2010 international conference on paper presented at the computer, mechatronics, control and electronic engineering (CMCE)
Maglaras LA, Katsaros D (2012) New measures for characterizing the significance of nodes in wireless ad hoc networks via localized path-based neighborhood analysis. Soc Netw Anal Min 2(2):97–106
Martins JC, Seleghim P (2010) Assessment of the performance of acoustic and mass balance methods for leak detection in pipelines for transporting liquids. J Fluids Eng 132(1):011401
Murvay P-S, Silea I (2012) A survey on gas leak detection and localization techniques. J Loss Prev Process Ind 25(6):966–973
Mustafa H, Chou PH (2012) Embedded damage detection in water pipelines using wireless sensor networks. In: 2012 IEEE 14th international conference on paper presented at the high performance computing and communication and 2012 IEEE 9th international conference on embedded software and systems (HPCC-ICESS)
Mysorewala M, Sabih M, Cheded L, Nasir MT, Ismail M (2015) A novel energy-aware approach for locating leaks in water pipeline using a wireless sensor network and noisy pressure sensor data. Int J Distrib Sens Netw 11(10):675454. https://doi.org/10.1155/2015/675454
Ostfeld A, Uber JG, Salomons E, Berry JW, Hart WE, Phillips CA,.. . Kapelan Z (2008) The battle of the water sensor networks (BWSN): a design challenge for engineers and algorithms. J Water Resour Plan Manag 134(6):556–568
Peng Z, Wang J, Han X (2011) A study of negative pressure wave method based on haar wavelet transform in ship piping leakage detection system. In: 2011 IEEE 2nd international conference on paper presented at the computing, control and industrial engineering (CCIE)
Rajeev P, Kodikara J, Chiu WK, Kuen T (2013) Distributed optical fibre sensors and their applications in pipeline monitoring. In: Paper presented at the key engineering materials
Rougier J (2005) Probabilistic leak detection in pipelines using the mass imbalance approach. J Hydraul Res 43(5):556–566
Sheltami TR, Bala A, Shakshuki EM (2016) Wireless sensor networks for leak detection in pipelines: a survey. J Ambient Intell Hum Comput 7(3):347–356
Sheltami TR, Shahra EQ, Shakshuki EM (2017) Perfomance comparison of three localization protocols in WSN using Cooja. J Ambient Intell Hum Comput 8(3):373–382
Shuqing Z, Tianye G, Hong X, Guangpu H, Zhongdong W (2009) Study on new methods of improving the accuracy of leak detection and location of natural gas pipeline. In: Paper presented at the 2009 international conference on measuring technology and mechatronics automation
Sivathanu Y (2003) Natural gas leak detection in pipelines. Technology Status Report, En’Urga Inc., West Lafayette
Sportiello L (2013) A methodology for designing robust and efficient hybrid monitoring systems. Int J Crit Infrastruct Prot 6(3):132–146
Sun X, Liu P, Ma Y, Liu D, Sun Y (2016) Streaming remote sensing data processing for the future smart cities: state of the art and future challenges. Int J Distrib Syst Technol (IJDST) 7(1):1–14
Tian CH, Yan JC, Huang J, Wang Y, Kim D-S, Yi T (2012) Negative pressure wave based pipeline leak detection: challenges and algorithms. In: 2012 IEEE international conference on paper presented at the service operations and logistics, and informatics (SOLI)
Wan J, Yu Y, Wu Y, Feng R, Yu N (2011) Hierarchical leak detection and localization method in natural gas pipeline monitoring sensor networks. Sensors 12(1):189–214
Acknowledgements
The authors would acknowledge the support of King Fahd University of Petroleum and Minerals for this research.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Anwar, S., Sheltami, T., Shakshuki, E. et al. A framework for single and multiple anomalies localization in pipelines. J Ambient Intell Human Comput 10, 2563–2575 (2019). https://doi.org/10.1007/s12652-018-0733-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-018-0733-3