Abstract
Numerous sensor network applications require accurate and rapid localization of randomly deployed sensor nodes. For wireless sensor network (WSN) localization, optimization methods can provide specific and reliable position estimates of a sensor node. The fixed density of beacons may be increase or decrease owing to various reasons, such as upkeep, lifespan, and breakdown. Because of its robustness, flexibility, and economic viability, the distance vector-hop (DV-Hop) algorithm is used to locate WSN nodes. Because of its high precision and fast computing speed, class topper optimization (CTO) is suitable to solve localization problems. This study proposes an orthogonal learning CTO-based DV-Hop localization algorithm for three-dimensional WSNs. Moreover, this study used a refined formula to calculate the minimum hop size of beacon nodes for reducing localization errors (LEs) in the approximated distance between the beacon and dumb nodes. Results revealed that our proposed method outperformed some existing algorithms in terms of reducing LEs (0.6%) and localization error variance (0.3%) and enhancing localization accuracy (0.4%) and coverage (0.7%).
Similar content being viewed by others

Avoid common mistakes on your manuscript.
1 Introduction
Wireless sensor networks (WSNs) have attracted considerable research attention. WSNs are composed of numerous small sensor devices called sensor nodes that gather and communicate data from the environment [1]. WSN localization of collected usable data is a critical problem. Furthermore, without determining actual location-related information within each sensor node, the obtained data are not useful [2]. Moreover, the location of a data-sensing sensor is as crucial as the data itself. Thus, the data and position-related information must be jointly communicated to determine the precise location of information collected by the sensor node. Several applications designed for use in extreme environments are increasingly using WSNs, such as those employed in battlegrounds, border patrols, and rain forests [3, 4] and those used for the remote control of hazardous areas and routing [5, 6]. Although the global positioning system is commonly used for sensor localization, it is not a viable choice because of the high cost of WSNs. Thus, researchers have proposed various WSN localization algorithms [7]. Numerous localization algorithms currently available are classified into two types: range based and range free [8].
To calculate a node’s location, range-free localization algorithms are used to estimate the distance within nodes and do not require external hardware. For these types of algorithms, the closest node whose position is known is used to localize dumb nodes. The centroid algorithm [9], DV-Hop [10, 11], amorphous [12], approximate point in triangulation test [13], and multidimensional scaling techniques [14] are some of the well-known range-free localization algorithms. However, the existing range-free localization algorithms have many limitations. For example, these algorithms are not resistant to environmental noise interference, require long computational time to determine sensor node positions, and provide only coarse-grained precision. Range-based localization algorithms require precise measurement methods that necessitate expensive equipment to determine the distance or angle between a node and its counterpart, providing highly accurate location-related information [15]. Received signal strength indicator [16], time of arrival [17], angle of arrival of signals packets [18], and time difference of arrival [19] are some examples of range-based localization algorithms. We focus on range-free algorithms in this study because they do not require additional devices.
Range-free localization techniques do not require any hardware, making them less expensive than range-based localization techniques. Furthermore, to reduce the localization error (LE), appropriate localization optimization methodologies must be developed in conjunction with a range-free localization algorithm. Although a localization method involving the use of a high percentage of localized nodes would be adequate for localization, it does not guarantee fine-grained precision. Thus, optimization algorithms should be applied to the results of localization techniques to reduce the LE. Optimization algorithms are useful in practical applications. However, with the availability of an increasing amount of information in the IoT era, many real-world problems include multiple decision parameters and evaluation indicators. Single-objective optimization algorithms cannot efficiently solve such problems. Thus, multiobjective optimization algorithms have been proposed and are used in diverse fields. Most studies have used single-objective optimization algorithms to solve localization problems [20]. However, numerous studies have demonstrated the importance of multiobjective optimization algorithms in solving multiobjective complex problems [21]. Although traditional studies have focused on two-dimensional space, most sensors have been deployed in three-dimensional space for various applications, necessitating further research to overcome complex challenges.
Several optimization techniques have been developed to solve real-time optimization problems. However, these techniques are not useful for solving large-scale, complex problems in WSNs. The class topper optimization (CTO) method is proposed in this study to overcome existing limitations. The CTO algorithm presented in [22] is a population-based meta-heuristic optimization technique. On the basis of students’ learning behaviors, a CTO is motivated to become the best student in the class (class topper). A class is divided into sections where students learn regarding various subjects. Exams are conducted each year to evaluate each student’s performance in a specific class. Section toppers are students who receive the highest marks in a section, whereas class toppers receive the highest marks in a class. Students are always striving to improve their knowledge to be the best student possible. To become a class topper, the CTO algorithm mimics students’ unique learning behaviors. During the process of becoming a class topper in CTO, students enhance their knowledge with the help of the knowledge of their respective section topper.
Contribution of this study:
- i:
-
We discovered a novel formula to optimize the average hop-distance calculation among nodes in a 3D wireless sensor network.
- ii:
-
An orthogonal learning–based CTO (OLCTO) focused on a DV-Hop localization algorithm was developed to reduce the LE in 3D WSNs.
- iii:
-
The efficiency and reliability of the algorithm were improved by implementing the optimization process by using the OLCTO approach.
- iv:
-
Simulation results revealed that our new multiobjective OLCTO method outperforms some existing approaches.
2 Associated works
Numerous optimization-based algorithms have been developed to solve localization problems. In [20], an NSGA-II-based multiobjective DV-Hop localization algorithm was proposed; this study applied an improved constraint strategy to all beacon nodes to improve DV-Hop location estimation precision. This algorithm exhibited greater accuracy with a small increase in computational costs. Kaur et al. [23] proposed Wolf algorithm–based optimization to accurately estimate the average hop distance for each beacon node. The algorithm provided precise results with a small increase in the computation cost. Another study [24] recommended using multiobjective functions to solve difficult problems involving several objects and track them in order to reduce the model’s size. However, that study measured the proportion of selection to determine the global optimum solution. The effect of radio irregularity was not examined in that study. Kanwar and Kumar [25] suggested a range-free localization approach using runner-root algorithms. They changed the average hop size of anchor nodes by refining a correction factor and optimized the hop size by using a line search algorithm. The precision of localization was improved using a runner-root method.
The genetic method was used in [26] to improve range-free localization. The authors introduced a correction factor to alter the hop size of anchor nodes, which was then further improved using a line search algorithm. However, holes, nonuniform node distribution, network sparsity, and irregular radio patterns may reduce the suggested algorithm’s performance. Using PSO, Singh and Sharma [27] proposed an improved DV-Hop localization algorithm. They measured the hop count and minimum hop size by using the proposed algorithm to determine the location and evaluate performance errors. The developed method utilized the hop size of the anchor from which the dumb node defined its reach. In addition, with the PSO strategy, the positions of unknown nodes can be determined. The dynamic-range average bisector approach was proposed in [26] to identify the location of nodes. In the system, each anchor node transmits data at two range levels. The correction factor was employed to prevent the overlapping of regions at the expense of increased computational costs.
A multipath routing scheme for homogeneous WSNs was presented in [28]. The proposed routing method was used to reduce energy consumption and balance load, resulting in increased network lifetime. We aim to reduce the packet loss rate in this work. Clustering network nodes, exploring paths between CHs, and maintaining paths are the three phases of the proposed routing method. A two-level routing algorithm with two phases, clustering and routing, was proposed in [29]. CHs are chosen during the clustering phase on the basis of residual energy, length from the BS, centrality, and the number of neighbors. BCHs and CHs are chosen during this phase. Each clustering setup phase has two clustering-steady phases, as determined by BCH selection. Thus, clustering’s overhead is minimized. Routing is the second phase, which has two levels: intra cluster and inter cluster. Each cluster is divided into four sections, each with a CH centrality, and nodes are located in these four sections in intra cluster routing. In inter cluster routing, CHs are layered in accordance with their distance from the BS.
A safe data aggregation scheme was described in [30]. The goal of data patterns is to reduce redundant data in the network, reduce sensor node energy consumption, and maintain data accuracy and precision. Intra cluster data aggregation, inter cluster data aggregation, and data transfer are the three phases of a secure data aggregation method. In [31], a binary tree was used to organize sensor nodes. Subsequently, data aggregation was conducted on the tree’s middle nodes, and analyzed data were sent to the root node. The data must first be approved to prevent unauthorized data aggregation requests. The aggregation process then begins, and an enhanced cyclic redundancy code is used hop by hop to ensure data aggregation accuracy and reliability. Meanwhile, data packets obtained from their offspring are subjected to cumulative functions imposed by intermediate nodes. As a result, the workload of sensors in the network is significantly reduced. This pattern continues, and aggregated data are eventually sent to the base station.
In [32], a secure combination data aggregation method called SHSDA was proposed; this method is based on a mixture of star and tree structures. The network is divided into four sections, each of which is geographically split into four equal components. A star structure is formed among nodes. The best node in terms of residual energy and centrality is chosen as the root of a star structure in each section. An energy-efficient layer routing protocol was proposed by Hajipour and Barati [33]. This technique divides the network into circles that are concentric. The circles are then divided into eight equal sectors at a 45∘ angle. For each section, an agent is chosen. Each section’s agent is in charge of gathering and aggregating data sensed by nodes in that section. When the agent receives data, it adds error detection and correction codes before sending the data to the lower layer of the same sector’s agent. The process is repeated until the arrival of all data at the base station.
In [34], a two-level energy-aware routing and a clustering method were proposed. The network is clustered, and the most suitable CHs are chosen on the basis of main factors related to energy consumption. A rendezvous region is then built to create a communication substructure between CHs, and nodes in this region are referred to as backbone nodes. In this area, a tree is created to send aggregated data to the sink through CHs. This tree provides an appropriate substructure for sending data to the sink, allowing CHs to send data to the sink with the least amount of overhead and energy and in a short amount of time. Because of the use of this microstructure, CHs do not need to use route discovery to send data to the sink. These findings indicate that range-free localization algorithms still need improvement in terms of localization accuracy (LA). Thus, we propose a new algorithm for 3D WSNs that employs the multiobjective OLCTO approach.
3 Conventional 3D DV-hop algorithm
The free localization technique is based on a protocol for distance routing. To determine the number of hops of beacon nodes and the minimum hop distance apart from WSNs, the distance between dumb nodes or unknown nodes and beacon nodes is calculated. Different paths form in a network topology among dumb and beacon nodes that are not linear due to nonuniform connectivity with wireless sensor nodes. The 3D DV-Hop localization algorithm is an extension of the classic DV-Hop technique. Therefore, some errors have been identified in the algorithm for node positioning [25].
- Step 1:
-
The minimum hop amount is defined for unknown and beacon nodes in step 1. By transmitting signals through beacon nodes through the vector protocol system, neighboring nodes can be shown their location. Information exists in the form of Hi, aj, bj, and cj in which id is the identity; aj, bj, and cj are coordinates; and Hi is the hop count for the i beacon node. First, 0 is set as the value of Hi [35]. The nodes obtain data from the broadcast and record the hop amount and localization of the vector’s beacon nodes. The Hi value must be increased by 1 through this process [26]. In this update process, if any node receives the same id group, the new received data will be compared with the original value of Hi. The nodes obtain broadcast data and track the hop amount and localization for the beacon nodes of the vector.
- Step 2:
-
The minimum hop count and average hop distance are determined to calculate the distance between unknown and beacon nodes. The average hop distance for the entire network is determined by obtaining the position and hop amount for beacon nodes, as described in the previous stage. Then, these data are transmitted to the entire network. Furthermore, most nodes require information on the average hop distance from a beacon node that is nearer to them [36]. The following equation provides the typical distance of the hop (jpi) and the hop range (pi) between the i(ai,bi,ci) beacon node and the other (beacon) node j(aj,bj,cj):
$$ j{{p}_{i}}=\frac{{\sum}_{i\ne j}{\sqrt{{{({{a}_{i}}-{{a}_{j}})}^{2}}+{{({{b}_{i}}-{{b}_{j}})}^{2}}+{{({{c}_{i}}-{{c}_{j}})}^{2}}}}}{{\sum}_{i\ne j}{h(ij)}}, $$(1)where jpi is the minimum hop distance and h(ij) is the number of hops from beacon nodes i and j. The following formula can be used to calculate the distance between beacon and dumb nodes.
$$ {{p}_{iU}}=j{{p}_{iU}}\times {{Hop}_{min}}, $$(2)where jpiU is the step distance, Hopmin is the step count between the i beacon nodes, and piU denotes the estimated distance between the dumb node U and the beacon node i.
- Step 3:
-
Let the coordinates of the U dumb node be (a,b,c), and the ith beacon node be (ai,bi,ci)(1 ≤ i ≤ n) in stage 3. Correspondingly, the distance between the ith beacon node and the unknown or dumb node U is pi(1 < i < n). The dumb node’s coordinates can been determined as follows:
$$ \begin{array}{@{}rcl@{}} && {{({{a}}-{{a}_{1}})}^{2}}+{{({{b}}-{{b}_{1}})}^{2}}+{{({{c}}-{{c}_{1}})}^{2}}={p_{1}^{2}} ;\\ && {{({{a}}-{{a}_{2}})}^{2}}+{{({{b}}-{{b}_{2}})}^{2}}+{{({{c}}-{{c}_{2}})}^{2}}={p_{2}^{2}} ;\\ && ....................................... \\ && {{({{a}}-{{a}_{n}})}^{2}}+{{(b-{{b}_{n}})}^{2}}+{{(c-{{c}_{n}})}^{2}}={p_{n}^{2}} ; \end{array} $$(3)$$ \begin{array}{@{}rcl@{}} && {a_{1}^{2}}-{a_{n}^{2}}-2({{a}_{1}}-{{a}_{n}})a+{b_{1}^{2}}-{b_{n}^{2}}-2({{b}_{1}}-{{b}_{n}})b \\ &&+ {c_{1}^{2}}-{c_{n}^{2}}-2({{c}_{1}}-{{c}_{n}})a ={p_{1}^{2}}-{p_{n}^{2}} ;\\ && ..................................................................... \\ && a_{n-1}^{2}-{a_{n}^{2}}-2({{a}_{n-1}}-{{a}_{n}})a+b_{n-1}^{2}-{b_{n}^{2}}-2({{b}_{n-1}} \\ &&-{{b}_{n}})b+c_{n-1}^{2}-{c_{n}^{2}}-2({{c}_{n-1}}-{{c}_{n}})c=p_{n-1}^{2}-{p_{n}^{2}}; \end{array} $$(4)(4) can be arranged in the matrix from as follows:
$$ SA = T , $$(5)where \(S=\begin {bmatrix} 2({{a}_{1}}-{{a}_{n}}) 2({{b}_{1}}-{{b}_{n}}) 2({{c}_{1}}-{{c}_{n}}) \\ 2({{a}_{2}}-{{a}_{n}}) 2({{b}_{1}}-{{b}_{n}}) 2({{c}_{1}}-{{c}_{n}}) \\ ................................. \\ 2({{a}_{n-1}}-{{a}_{n}}) 2({{b}_{1}}-{{b}_{n}}) 2({{c}_{1}}-{{c}_{n}}) \\ \end {bmatrix},\)
\(T=\begin {bmatrix} {a_{1}^{2}}-{a_{n}^{2}}+{b_{1}^{2}}-{b_{n}^{2}}+{c_{1}^{2}}-{c_{n}^{2}}+{p_{n}^{2}}-{p_{1}^{2}} \\ {a_{2}^{2}}-{a_{n}^{2}}+{b_{2}^{2}}-{b_{n}^{2}}+{c_{2}^{2}}-{c_{n}^{2}}+{p_{n}^{2}}-{p_{2}^{2}} \\ .......................................... \\ a_{n-1}^{2}-{a_{n}^{2}}-b_{n-1}^{2}-{b_{n}^{2}}-c_{n-1}^{2}-{c_{n}^{2}}+{p_{n}^{2}}-p_{n-1}^{2} \\ \end {bmatrix},\) \( A=\begin {bmatrix} a \\ b \\ c \\ \end {bmatrix},\)
Finally, the least square approximation is used to calculate the dumb node coordinates as given below:
$$ A={{({{S}^{T}}S)}^{-1}}{{S}^{T}}T. $$(6)
4 Methodology:
4.1 Mathematical formulation of localization in 3D WSNs
Let us consider an update to a 3-dimensional network. (a1,b1,c1),(a2,b2,c2),(a3,b3,c3),...........(an,bn,cn) are the positions of beacon nodes. The positions of dumb nodes are (as+ 1,bs+ 1,cs+ 1),(as+ 2,bs+ 2,cs+ 2), (as+ 3,bs+ 3,cs+ 3)...........(as+t,bs+t,cs+t)). The following formula can be used to calculate the distance between beacon nodes:
where (a,b,c) are the coordinate of the dumb node, (ai,bi,ci) are the coordinates of the ith beacon node position, and pi denotes the distance between dumb nodes and the ith beacon node. In general, localization systems work in two stages:
- Stage 1::
-
Internode distances can be estimated using the hop link (hop counting) or internode communication. In addition, measurements can be used to calculate the actual physical distance.
- Stage 2::
-
Distances are calculated and converted into the known coordinates of the network’s node. To estimate distance measurements, an optimization problem model that minimizes the total sensor position errors can be designed.
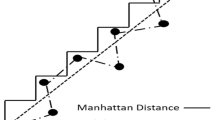
As presented in Fig. 1, the Pythagorean theorem can be utilized to calculate the distance between nodes. The Euclidean distance between the dumb and beacon nodes is given as follows:
where f(a,b,c) is the objective function that represents the distance error. The optimization problem defined by (9) can be solved using diverse optimization approaches. The chosen method should effectively minimize the LE and optimize derived locations to improve LA. To overcome the challenge of localization, many scholars have proposed employing popular heuristic methods.
4.2 OLCTO algorithm
Meta-heuristic optimization algorithms are frequently utilized in both experimental and industrial settings because of their versatility, simplicity, and robustness. CTO is among the most recent and widely used algorithms in this field [37]. A chaotic dynamic is introduced in CTO with an adjustable inertia weight factor to enrich the search behavior and prevent local optimum problems [38]. The following equation can be used to describe a chaotic search strategy:
The CTO approach includes the use of nonlinear dynamic acceleration coefficients to change the cognitive component C1 and the social component C2 as follows [39]:
The CTO algorithm has several flaws, including the ability to trap in local minima and other limitations when dealing with multiobjective problems. Thus, OLCTO is currently being used to overcome the limitations of CTO. The orthogonal diagonalization (OD) technique is used by the OLCTO algorithm. This technique can be used to derive orthogonal guidance vectors in the active group. The diagonal matrix can be obtained using the OD process by converting the multiplication of three matrices into the diagonal matrix (DM). DM is used to update the section topper, the class topper, and learn from vectors for all students in the class. To obtain DM, a square matrix P of size r × r is converted into a DM of size r × x × r as follows:
where R is a r × x × r-dimensional matrix composed of P′s eigenvector and DM′s diagonal elements. Because R is invertible, Eq. (13) can be defined as follows:
where B is an orthogonal matrix; thus, (14) can be written in the following form:
Figure 2 shows the OLCTO flowchart.
The OLCTO procedure steps are as follows:
- Step 1.:
-
Initialize the vectors of position (students) Si(0) at random and learn the form Li(0) for each student i. i = 1,2,..., m.
- Step 2.:
-
Calculate the performance index p(x) by using the position vector (students) Si(0).
- Step 3.:
-
Use the equation to initialize the section topper position vector of student i in the CTO algorithm:
$$ {{Q}_{{{S}_{t}},i}}={{S}_{i}}(0), $$(16)where \({{Q}_{{{S}_{t}},i}}\) denotes the section topper. To determine the section topper position vectors, use (16).
- Step 4.:
-
The m section topper position vectors can be ordered in ascending order by using the performance index value of p(x).
- Step 5.:
-
Create a matrix B with the size m × x × p. Each entry in this matrix corresponds to one of the m section topper position vectors in same order as in Step 4.
- Step 6.:
-
To transform matrix B into a symmetric matrix A with a dimension of m × x × p, use the CTO pseudo code [22].
- Step 7.:
-
Apply OD to matrix A to obtain a DM of size r × x × r.
- Step 8.:
-
The equations below can be used to update the vectors:
$$ {L_{i}^{t}}=L_{i}^{t-1}+C\times \phi \times [D{M_{i}^{t}}-S_{i}^{t-1}], $$(17)$$ {S_{i}^{t}}=S_{i}^{t-1}+{L_{i}^{t}}, $$(18)DMi is the diagonal of the matrix DM, and i = 1,2,..., r, C is the coefficient of nonlinear dynamic acceleration, ranging from [2.5 to 0.5].
- Step 9.:
-
Calculate \(Q_{{{S}_{t}},i}^{t}\) (section topper) from the m students by using the following Eq. (19):
$$ {Q_{{S}_{t},_{i}}^{t}}=\left\{\begin{array}{ll} {S_{i}^{t}}, & if\text{ }{{\text{h({S}}_{i}}^{t})}\text{ }\le {{\text{h({Q}}_{i}}^{t-1})}, \\ {Q_{{S}_{t},_{i}}^{t-1}} &\qquad~~ otherwise, \end{array}\right. $$(19)Then, calculate \(f(Q_{{{S}_{t}},i}^{t})\). i = 1,2,..., m.
- Step 10.:
-
The following method can be used to determine the class topper (best position). Choose \(Q_{{S}_{t}}\), which corresponds to the minimum of \(f(Q_{{S}_{t}}^{t})\). i = 1,2,..., m.
Assess p(x) to find \(Q_{{C}_{t}}^{t}\), which is the class topper (best position).
$$ Q_{{C}_{t}}^{t} = min Q_{{{S}_{t},i}}^{t}, $$(20) - Step 11.:
-
Finish the iterations, t = Niter
The following steps are included in the proposed algorithm:
- Step 1.:
-
Dumb node locations are determined using the minimum hop distance calculated by each beacon (i.e., one-hop-size) from another beacon in the network. The greater the precision of this estimated distance is, the more effective the approximate positions are.
- Step 2.:
-
Instead of using the conventional approach, we define and measure the average hop distance among beacons. Thus, we use the polynomial approximation to reduce the estimated LE and increase LA. The following polynomial is used to calculate the approximate hop distance from the ith beacons and other beacons m.
$$ {{r}_{im}}={{\kappa }_{0}}+{{\kappa }_{1}}{{p}_{im}}+{{\kappa }_{2}}p_{im}^{2}, $$(21)where κ0, κ1 and κ2 are the coefficients.
$$ \begin{bmatrix} & p_{i1}^{2} & {{p}_{i1}} & 1 \\ & p_{i2}^{2} & {{p}_{i2}} & 1 \\ & {\vdots} & {\vdots} & {\vdots} \\ & p_{ij}^{2} & {{p}_{ij}} & 1 \\ \end{bmatrix}\begin{bmatrix} {\kappa }_{2} \\ {\kappa }_{1} \\ {\kappa }_{0} \\ \end{bmatrix}=\begin{bmatrix} & {{r}_{i1}} \\ & {{r}_{i2}} \\ & {\vdots} \\ & {{r}_{ij}} \\ \end{bmatrix}, $$(22)We solve the following equation to determine the polynomial function estimate of the distance among nodes:
$$ \kappa ={{({{P}^{T}}P)}^{-1}}{{P}^{T}}R, $$(23)For each dumb node, the distance between itself and the beacon node is calculated as follows:
$$ {{r}_{ij}}={{\kappa }_{0}}+{{\kappa }_{1}}{{p}_{ij}}+{{\kappa }_{2}}p_{ij}^{2}, $$(24)where rij and pij represent the distance as well as minimum number of hops between the ith dumb node and the jth beacon node, respectively. Thus, we obtain the following matrix form:
$$ {{r}_{est}}=hop\times \kappa , $$(25)The actual distance between the ith and jth is calculated as
$$ {{r}_{true}}=\sqrt{{{({{a}_{i}}-{{a}_{j}})}^{2}}+{{({{b}_{i}}-{{b}_{j}})}^{2}}+{{({{c}_{i}}-{{c}_{j}})}^{2}}}. $$(26)The error between the ith and jth nodes of the beacon is determined as follows:
$$ {{r}_{error}}={{r}_{est}}-{{r}_{true}}. $$(27)We now add a rectification factor, which is defined as follows:
$$ \tau =\frac{r_{error}}{s}, $$(28)where s is the number of beacon nodes. The τ rectification factor is used by adding it to the previous hop size to change the hop size of the beacon node. The adjusted distance between the ith beacon nodes and the kth dumb node is determined as [40]:
$$ r_{ik}^{Mod}=(HopSize+\tau )\times {{H}_{ik}}. $$(29) - Step 3.:
-
To enhance the location accuracy between sensor nodes, we present an orthogonal learning DV-Hop localization approach based on CTO. In orthogonal learning optimization, the optimal solution for result comparison is indicated as the minimum of the sum of two goal values. We used four single-objective functions and two multiobjective (orthogonal learning) functions to develop our proposed technique. The following is a proposed algorithm that employs single-objective optimization functions:
$$ f_{1}(a,b,c)=\min\left( \sum\limits_{i=1,2....M}\left| \sqrt{{{(a-{{a}_{i}})}^{2}}+{{(b-{{b}_{i}})}^{2}}+{{(c-{{c}_{i}})}^{2}}}-{{r}_{ik}^{Mod}} \right|\right). $$(30)$$ f_{2}(a,b,c)=\min\left( \sum\limits_{i=1,2....M}\left| \sqrt{{{(a-{{a}_{i}})}^{2}}+{{(b-{{b}_{i}})}^{2}}+{{(c-{{c}_{i}})}^{2}}}-{{r}_{ik}^{Mod}} \right|\right)^{2}. $$(31)$$ f_{3}(a,b,c)=\min \left( \sum\limits_{i=1,2....M}\left| \sqrt{{{(a-{{a}_{i}})}^{2}}+{{(b-{{b}_{i}})}^{2}}+{{(c-{{c}_{i}})}^{2}}}-{{r}_{it}^{Mod}} \right|\right). $$(32)where \({{r}_{it}^{Mod}}=hop\times \kappa \), κ = (PTP)− 1PTR and rerror = rest − rtrue.
$$ f_{4}(a,b,c)=\min \left( \sum\limits_{i=1,2....M}\left| \sqrt{{{(a-{{a}_{i}})}^{2}}+{{(b-{{b}_{i}})}^{2}}+{{(c-{{c}_{i}})}^{2}}}-{{r}_{it}^{Mod}} \right|\right)^{2}. $$(33)
The proposed algorithm considers the following multiobjective (orthogonal learning) functions, where m1 is formulated by combining f1 and f2, and m1 and m1 is represented as follows:
m2 is the formulated by combining f3 and f4, and m2 is represented as follows:
5 Metrics of performance
LE, localization error variation (LEV), LA, and coverage are parameters used to evaluate the performance of the proposed OLCTO-based DV-Hop algorithm.
5.1 LE
The LE for a 3D WSN can be computed as follows:
5.2 LEV
Variance measures how far each number in a set deviates from the mean. LEV for a 3D WSN can be computed as follows:
5.3 LA and coverage
LA can be computed as follows:
Coverage can be computed as follows:
where t denotes the number of unknown or dumb nodes and \((a_{i}^{tr},b_{i}^{tr},c_{i}^{tr})\) is true positions of unknown or dumb node i. The estimated dumb node positions are ith is \((a_{i}^{est},b_{i}^{est},c_{i}^{est})\). R is the sensor node’s communication range.
6 Simulation and results analysis
In a 3D environment, the proposed approach is implemented. For our system, we used the OLCTO algorithm with C = 4, W = 2.5 to 0.05, Itermax = 20, as well as random variables between 0 and 1. For a 3D, the minimum transmission range of a node is 25 m2. The value of the communication range is dependent on node density. The greater the communication range is, the lower is the node density. The communication range of 3D space is larger than that of 2D space. Figure 3 depicts the typical distribution of 150 dumb nodes and 30 beacon nodes in 3D space. Table 1 lists parameters used in the simulation. For the scenario, we used uniformly dispersed dumb nodes and beacon nodes, and the results were assessed using the following parameters: (i) the total number of nodes, (ii) the total number of beacon nodes, and (iii) communication range of nodes.
6.1 Effects of beacon nodes on LE, LEV, LA, and coverage
Figures 4 and 5 present the effects of the beacon on LE and LEV, respectively. The number of beacon nodes varies from 20 to 160. As presented in Table 2, the m1 had less LEs and LEV. For example, when the total number of beacon nodes is set to 20, the multiobjective function m1 had approximately 0.6%, 8%, 8.8%, 15.2%,22.2%, and 30.2% less LEs in f1, f2, m [24], m2, f4, and f5, respectively, and 0.3%, 10.3%, 15.3%, 20.3%, 30.3%, and 70.3% less LEV in f1, f2, m [24], m2, f6, and f5, respectively. The proposed method has approximately 0.4%, 0.8%, and 0.9% less LEs in [30, 41] and [28], respectively, and 0.5%, 1.3%, and 1.9% less LEV in [30, 41] and [28], respectively.
Figures 6 and 7 present the effects of the beacon on LA and coverage, respectively, and Table 3 presents the analysis data. As indicated in Table 3, the multiobjective function m1 exhibited improved LA and coverage. For example, when the total number of beacon nodes was set to 20, the multiobjective function m1 had approximately 0.4%, 2%, 73.2%, 74.2%,78.3%, and 80.02% improved LA in m2, m [24], f1, f2, f4, and f3 and 0.7%, 9.8%, 47.8%, 49.8%, 69.8%, and 89.8% improved coverage in m2, m [24], f1, f2, f4, and f3, respectively. The proposed method had approximately 0.4%, 2%, and 8.02% improved LA in [30, 41] and [28], respectively, and 0.7%, 6.8%, and 9.8% improved coverage in [30, 41] and [28], respectively.
6.2 Effect the total number of nodes on localization errors, error variance, accuracy, and coverage
Figures 8 and 9 present the effect of number nodes on LE and LEV, respectively. As presented in Table 4, with an increase in the total number of nodes, the multiobjective function m1 had the lowest LE and LEV. For example, when the total number of nodes was set to 200, the multiobjective function m1 had approximately 1%, 4%, 6.7%, 8%,9.3%, and 11.9% less LEs in f1, m [24], f2 m2, f6, and f5, respectively, and 8%, 11%, 54%, 72%, 84%, and 84.6% less LEV in f1, m [24], f2 m2, f6, and f5, respectively. The proposed method had approximately 1.2%, 5%, and 6.9% less LEs in [30, 41] and [28], respectively, and 4%, 7%, and 8.6% less LEV in [30, 41] and [28], respectively.
Figures 10 and 11 present the effect of the total number of nodes on LA and coverage, respectively, and Table 5 presents the associated analysis of data. With an increase in the total number of nodes, the multiobjective function m1 exhibited improved LA and coverage. For example, when the total number of nodes was 200, the multiobjective function m1 exhibited approximately 0.2%, 3.2%, 65.2%, 72.2%,80.2%, and 88.2% improved LA in m [24], m2, f1, f2, f4, and f3, respectively, and 0.1%, 1%, 47%, 57%, 77%, and 97% improved coverage in m [24], m2, f1, f2, f4, and f3, respectively. The proposed method resulted in approximately 0.5%, 2.2%, and 8.2% improved LA in [30, 41] and [28], respectively, and 0.2%, 3%, and 7% improved coverage in [30, 41] and [28], respectively.
6.3 Effect of LE, LEV, LA, and coverage on the communication range
Figures 12 and 13 present the effect of the transmission range on LE and LEV, respectively, and Table 6 presents the associated analysis of data. For example, when the transmission range was 25, the multiobjective function m1 had approximately 2.8%, 5%, 15%, 19%,22%, and 26% less LEs in m [24], f1, f2 m2, f6, and f5 and 8%, 56%, 64%, 74%, 78%, and 83% less LEV in m [24], f1, f2 m2, f6, and f5, respectively. The proposed method had approximately 1.8%, 3%, and 6% less LEs in [30, 41] and [28], respectively, and 6%, 6.6%, and 8.3% less LEV in [30, 41] and [28], respectively.
Figures 14 and 15 present the effect of the total number of nodes on LA and coverage, respectively, and Table 7 presents the associated analysis of data. As indicated in Table 7 with an increase in the transmission range, the multiobjective function m1 exhibited improved LA and coverage. For example, when the total number of nodes was 25, the multiobjective function m1 had approximately 7%, 15%, 36%, 50%,78%, and 86% improved LA in m [24], m2, f1, f2, f4, and f3 and 9%, 14%, 94%, 95%, 96%, and 97% improved coverage in m [24], m2, f1, f2, f4, and f3, respectively. The proposed method exhibited approximately 7%, 7.8%, and 8.6% improved LA in [30, 41] and [28] and 9%, 9.5%, and 9.8% improved coverage in [30, 41] and [28].
7 Conclusion
In this study, we present a range-free DV-Hop localization method in 3D space by utilizing the OLCTO optimization. The suggested approach converts single-objective functions based on the DV-Hop localization algorithm into two multiobjective functions to reduce LEs. The goal of multiobjective localization is to reduce LEs while increasing positional precision. Among all the proposed objective functions, the multiobjective function m1 had the least LEs and LEV as well as improved LA. Simulation results revealed that the multiobjective function m1 had the highest placement accuracy among all single- and multiobjective functions and multiobjective PSO [24]. The proposed method’s main limitations are in terms of energy consumption, network lifetime, and network reliability. In our next study, we will focus on improving the convergence rate and reducing energy consumption to enhance LA. The following study focuses on reducing communication between dumb and beacon nodes by computing the hop size of all beacons at dumb nodes. This approach can reduce computational time while reducing node energy consumption. Future studies can develop circular and spiral beacon nodes for the deployment of the multi-hop-based approach in a 3D system and on a physical staging ground.
Data availability
Not applicable
Code availability
Not applicable
References
Dai H, Chen A, Gu X, He L (2011) Localisation algorithm for large-scale and low-density wireless sensor networks. Electr Lett 47(15):881–883
Najeh T, Sassi H, Liouane N (2018) A novel range free localization algorithm in wireless sensor networks based on connectivity and genetic algorithms. Int J Wireless Inf Netw 25(1):88–97
Joshi YK, Younis M (2016) Restoring connectivity in a resource constrained WSN. J Netw Comput Appl 66:151–165
Lee S-M, Cha H, Ha R (2007) Energy-aware location error handling for object tracking applications in wireless sensor networks. Comput Commun 30(7):1443–1450
Gavish B, Neuman I (1992) Routing in a network with unreliable components. IEEE Trans Commun 40(7):1248–1258
Liao W-H, Sheu J-P, Tseng Y-C (2001) Grid: a fully location-aware routing protocol for mobile ad hoc networks. Telecommun Syst 18(1):37–60
Song G, Tam D (2015) Two novel DV-Hop localization algorithms for randomly deployed wireless sensor networks. Int J Distr Sensor Netw 11(7):187670
Gao GQ, Lei L (2010) An improved node localization algorithm based on DV-Hop in WSN. In: 2010 2nd International conference on advanced computer control. IEEE, vol 4, pp 321–324
Bulusu N, Heidemann J, Estrin D (2000) GPS-less low-cost outdoor localization for very small devices. IEEE Personal Commun 7(5):28–34
Niculescu D, Nath B (2001) Ad hoc positioning system (APS). In: GLOBECOM’01. IEEE global telecommunications conference (Cat. No. 01CH37270). IEEE, vol 5, pp 2926–2931
Niculescu D (2003) DV based positioning in ad hoc networks. Telecommun Syst 22(1-4):267–280
Nagpal R et al (1999) Organizing a global coordinate system from local information on an amorphous computer
He T, Huang C, Blum BM, Stankovic JA, Abdelzaher T (2003) Range-free localization schemes for large scale sensor networks. In: Proceedings of the 9th annual international conference on Mobile computing and networking, pp 81–95
Shang Y, Ruml W, Zhang Y, Fromherz MP (2003) Localization from mere connectivity
Kaur A, Kumar P, Gupta GP (2019) A weighted centroid localization algorithm for randomly deployed wireless sensor networks. J King Saud Univ-Comput Inf Sci 31(1):82–91
Viani F, Lizzi L, Rocca P, Benedetti M, Donelli M, Massa A (2008) Object tracking through RSSI measurements in wireless sensor networks. Electron Lett 44(10):653–654
Girod L, Estrin D (2001) Robust range estimation using acoustic and multimodal sensing. In: Proceedings 2001 IEEE/RSJ international conference on intelligent robots and systems. Expanding the societal role of robotics in the the next millennium (Cat. No. 01CH37180). IEEE, vol 3, pp 1312–1320
Priyantha NB, Chakraborty A, Balakrishnan H (2000) The cricket location-support system. In: Proceedings of the 6th annual international conference on mobile computing and networking, pp 32–43
Niculescu D, Nath B (2003) Ad hoc positioning system (APS) using aoa. In: IEEE INFOCOM 2003. Twenty-second annual joint conference of the IEEE computer and communications societies (IEEE Cat. No. 03CH37428). Ieee, vol 3, pp 1734–1743
Wang P, Xue F, Li H, Cui Z, Xie L, Chen J (2019) A multi-objective DV-Hop localization algorithm based on NSGA-II in Internet of Things. Mathematics 7(2):184
Sun Z, Tao L, Wang X, Zhou Z (2015) Localization algorithm in wireless sensor networks based on multiobjective particle swarm optimization. Int J Distr Sensor Netw 11(8):716291
Das P, Das DK, Dey S (2018) A new class topper optimization algorithm with an application to data clustering. IEEE Trans Emerging Topics Comput
Kaur A, Kumar P, Gupta GP (2018) Nature inspired algorithm-based improved variants of DV-Hop algorithm for randomly deployed 2D and 3D wireless sensor networks. Wirel Pers Commun 101(1):567–582
Kanwar V, Kumar A (2021) Range free localization for three dimensional wireless sensor networks using multi objective particle swarm optimization. Wirel Pers Commun 117(2):901– 921
Kanwar V (2020) DV-Hop-based range-free localization algorithm for wireless sensor network using runner-root optimization. J Supercomput:1–18
Sharma G, Kumar A (2018) Improved DV-Hop localization algorithm using teaching learning based optimization for wireless sensor networks. Telecommun Syst 67(2):163–178
Singh SP, Sharma SC (2019) Implementation of a PSO based improved localization algorithm for wireless sensor networks. IETE J Res 65(4):502–514
Shahbaz AN, Barati H, Barati A (2021) Multipath routing through the firefly algorithm and fuzzy logic in wireless sensor networks. Peer-to-Peer Netw Appl 14(2):541–558
Mosavifard A, Barati H (2020) An energy-aware clustering and two-level routing method in wireless sensor networks. Computing 102(7):1653–1671
Yousefpoor E, Barati H, Barati A (2021) A hierarchical secure data aggregation method using the dragonfly algorithm in wireless sensor networks. Peer-to-Peer Netw Appl 14(4):1917– 1942
Hasheminejad E, Barati H (2021) A reliable tree-based data aggregation method in wireless sensor networks. Peer-to-Peer Netw Appl 14(2):873–887
Naghibi M, Barati H (2021) SHSDA: secure hybrid structure data aggregation method in wireless sensor networks. J Ambient Intell Humanized Comput 12(12):10769–10788
Hajipour Z, Barati H (2021) EELRP: energy efficient layered routing protocol in wireless sensor networks. Computing 103(12):2789–2809
Sharifi SS, Barati H (2021) A method for routing and data aggregating in cluster-based wireless sensor networks. Int J Commun Syst 34(7):e4754
Kumar S, Lobiyal D (2013) An advanced DV-Hop localization algorithm for wireless sensor networks. Wireless Personal Commun 71(2):1365–1385
Kanwar V, Kumar A (2020) Multiobjective optimization-based DV-Hop localization using NSGA-II algorithm for wireless sensor networks. Int J Commun Syst 33(11):e4431
Mohanta TK, Das DK (2021) Class topper optimization based improved localization algorithm in wireless sensor network. Wirel Pers Commun:1–20
Liu B, Wang L, Jin Y-H, Tang F, Huang D-X (2005) Improved particle swarm optimization combined with chaos. Chaos, Solitons Fractals 25(5):1261–1271
Tian D, Zhao X, Shi Z (2019) Chaotic particle swarm optimization with sigmoid-based acceleration coefficients for numerical function optimization. Swarm Evolution Computat 51:100573
Vesterstrom J, Thomsen R (2004) A comparative study of differential evolution, particle swarm optimization, and evolutionary algorithms on numerical benchmark problems. In: Proceedings of the 2004 congress on evolutionary computation (IEEE Cat. No. 04TH8753). IEEE, vol 2, pp 1980–1987
Mohanta TK, Das DK (2022) Advanced localization algorithm for wireless sensor networks using fractional order class topper optimization. J Supercomput:1–29
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Mohanta, T.K., Das, D.K. A three-dimensional wireless sensor network with an improved localization algorithm based on orthogonal learning class topper optimization. Ann. Telecommun. 78, 475–489 (2023). https://doi.org/10.1007/s12243-023-00944-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-023-00944-z