Abstract
The Time Slotted Channel Hopping (TSCH) mechanism is created in the IEEE 802.15.4e amendment, to meet the need of Industrial Wireless Sensor Networks. It combines time slotted access and channel hopping with deterministic behavior. The mechanism offers two types of links: dedicated links and shared links. In order to reduce the probability of repeated collisions in shared links, the mechanism implemented a retransmission backoff algorithm, named TSCH Collision Avoidance (TSCH CA). In this article, we develop a two dimensional Markov chain model for the IEEE 802.15.4e TSCH CA mechanism, we take into account the deterministic behavior of this mechanism. In order to evaluate its performances, we estimate the stationary distribution of this chain. Then, we derive theoretical expressions of: collision probability, data packet loss rate, reliability, energy consumption, throughput, delay and jitter. Then, we analyze the impact of the number of devices sharing the link for a fixed network size under different traffic conditions. Finally, the accuracy of our theoretical analysis is validated by Monte Carlo simulation. It is shown that the performances of the IEEE 802.15.4e TSCH parameters are strongly related to the number of devices sharing the link.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Wireless Sensor Networks (WSNs) were used for the first time by soldiers, in the military domain, to detect intrusions and tracking threats [1]. Since, they were widely extended to other applications, such as: medical [2, 3], and environment applications [4]. Nowadays, by the development of the sensor devices and the arrival of actuators, WSNs increasingly attract the industrial communities [5, 6]. They are used in factory automation and process control [7, 8].
In order to support the Wireless Local Area Networks (WLAN) requirements, the standardization efforts have led to the development of several technologies, namely: IEEE 802.15.1 [9] (Bluetooth), IEEE 802.11 [12] (WiFi), wireless Hart [10], ISA100a [11] and IEEE 802.15.4 [13] (ZigBee).
Although the IEEE 802.15.4 standard is the most used technology for WLANs, the use of this latter for industrial applications became limited [14]. Since 2012, the need to overcome these limitations has given birth to the new IEEE 802.15.4e standard [15].
The IEEE 802.15.4e standard defines Medium Access Control (MAC) enhancements to better support the critical industrial requirements. It introduces new mechanisms, such as: Low Latency Deterministic Networks (LLDN), Distributed Synchronous Multi-Channel Extension (DSME) and Time Slotted Multi-Channel Extension (TSCH). In order to create the IEEE 802.15.4e TSCH amendment, the IEEE standardization has integrated the existing concept of Time Synchronized Mesh Protocol (TSMP) [16] ratified wireless Hart in the IEEE 802.15.4e amendment. This TSCH amendment combines time slotted access and channel hopping [15], or in other words, it combines the Time Division Multiple Access (TDMA) with Frequency Division Multiple Access (FDMA) [17]. The TDMA scheme [18] appears by dividing the time into slot frames repeating over the time. Whereas, the FDMA scheme [19] appears by the possibility for many couples of devices to exchange their data packets in the same timeslot, using different channel offsets. In addition, in a given timeslot, the TSCH mechanism offers two types of links : dedicated links and shared links. More than one device can be assigned to a link (shared group link). In this case, collisions may occur and result transmission failure detected by no receiving an acknowledgment. To reduce the probability of repeated collisions, the IEEE 802.15.4e standard [15] implemented a retransmission backoff algorithm, named TSCH Collision Avoidance (TSCH CA). The TSCH has a deterministic behavior, i.e., all the actions that will occur at each timeslot are well known, even when the actions are assigned to have occurred in a shared link. This means that the number of devices sharing the link is well known. So, intuitively, it is not the whole number of devices in network that are assigned to transmit in a given shared link, but a restricted number of devices.
Since the apparition of the new IEEE 802.15.4e amendment, various researches have been conducted. Some authors were interested to present the MAC mechanisms of the standard [20]. Other, to enhance the proposed mechanisms [21,22,23,24,25,26,27,28], or to define secure protocols [17]. The rest of the authors were interested to the performance evaluation of the IEEE 802.15.4e standard [29,30,31,32,33,34]. The performance analysis is based either by mathematical modeling or by simulation. When it is based on mathematical modeling, the Markov chain models are often used, it is inspired from the existing works on IEEE 802.11 [35,36,37,38,39,40,41] and IEEE 802.15.4 for both slotted CSMA/CA [42,43,44,45,46,47,48,49,50,51,52,53,54] and unslotted CSMA/CA [55, 56]. In [33], authors analyzed the transmission in the shared link using TSCH CA algorithm. However, the authors have not taken into account the deterministic behavior of the TSCH mechanism in a shared link, they supposed that all devices of the network share the given link.
In this paper, we present an enhancement analytical study of the transmission in the shared link using TSCH CA algorithm. We take into account the deterministic behavior of the TSCH mechanism. We study the impact of the number of devices sharing the same link on the performances of the network, under saturated and non saturated conditions. The results are validated by Monte Carlo simulations.
The remainder of this paper is organized as follows. Section 2 presents related works about IEEE 802.15.4e standard. Section 3 describes IEEE 802.15.4e standard and summarizes its main MAC enhancements. Section 4 gives a detailed Markov chain model of TSCH/CA mechanism, and derives the theoretical expressions of collision probability, data packet loss rate, reliability, energy consumption, throughput, delay and jitter. Section 5 presents the impact of the number of devices sharing the link variation on the network performances under different traffic conditions. We validate our analysis by Monte Carlo simulations. Section 6 concludes this paper.
2 Related Works
To meet the need of the industrial applications, the new IEEE 802.15.4e standard has been created. Since, the scientific community were interested in its brought enhancements. Some works addressed the LLDN [24,25,26, 29, 61] and the DSME mechanisms [23, 30,31,32]. When others were interested in TSCH. Those works done on TSCH are various.
On the one hand, some of them addressed the enhancement of the TSCH mechanism, where authors proposed scheduling algorithms to allow devices to transmit in their assigned timeslots. In [21] a novel Traffic Aware Scheduling Algorithm for TSCH (TASA) is proposed to support the emerging industrial applications, which require low latency at low duty cycle and power consumption. This algorithm is a centralized algorithm, it extends the theoretically graph theory methods of matching and coloring by means of an innovative approach based on network topology and traffic load. Distributed scheduling algorithms for TSCH are presented in [22, 57]. In [27], authors presented an Adaptive TSCH (A-TSCH) algorithm in order to improve the reliability of the existing TSCH. They proposed to use the blacklisting technic, which consists to use a selected subset of channels considered “Reliable”, unlike the IEEE 802.15.4e TSCH which indiscriminately uses all 16 channels in the 2.4 GHz band. In [28], the authors adopted mechanisms for learning the spectral condition and blacklisting to the A-TSCH.
On the other hand, some other works were done on the performances evaluation. The authors of [14] evaluated the performances of the IEEE 802.15.4e TSCH in terms of latency, delivery ratio and energy per packet. They compared their results to the existing IEEE 802.15.4 by simulation. In [34], authors were interested to the formation process of TSCH network. They, firstly, proposed a random advertisement algorithm. Then, they evaluated the joining time performance metric, which is the total time taken by a new device to join the network. Results showed that the parameter depends on the number of channels used for advertisement. In [33], authors analyzed the transmission in the shared link using TSCH CA algorithm. They used the Markov chain modeling to estimate the distribution probability. Then, they derived theoretical expressions of the following performance metrics: data packet loss probability, normalized throughput, delay and energy consumption. Results showed that the TSCH CA can guarantee low energy consumption and relative reliability, for a given device transmitting in a shared timeslot.
In addition, the authors of [17] and [60], presented respectively the new 6TiSCH stack (IPv6 over the TSCH mode of IEEE 802.15.4e) and the 6LoWPAN stack. Both the works addressed the security mechanisms for the IEEE 802.15.4e TSCH. The authors of [59] and [58] were interested to the construction of energy consumption models for IEEE 802.15.4e TSCH. Models are obtained by slot-based “step-by-step” modeling.
3 IEEE 802.15.4e Description
IEEE 802.15.4e [15] amends the IEEE 802.15.4-2011 Standard [13] to specify additional MAC behaviors, that allow devices to better support the industrial and commercial applications. The IEEE 802.15.4e standard defines the following three modes:
-
Deterministic and Synchronous Multi-Channel Extension (DSME);
-
Low Latency Deterministic Networks (LLDN);
-
Time Slotted Channel Hopping (TSCH).
3.1 DSME
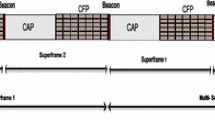
The IEEE 802.15.4 supports only up to 7 Guaranteed Timeslots (GTSs) and these GTSs are restricted to use a single channel [13, 15]. The IEEE 802.15.4e DSME enhances the IEEE 802.15.4 standard by extending the number of GTS timeslots, and adopting a channel hopping to ensure that GTSs can be used in more channels. DSME [31, 31] employs a multi-superframes structure defined by coordinators that periodically transmit an Enhanced Beacon (EB). A multi-superframes is a cycle of repeated superframes, each of which consists of a beacon frame, Contention Access Period (CAP) and Contention Free Period (CFP). An example of a multi-superframes structure is shown in Fig. 1. Additional energy-saving is obtained using CAP reduction. When CAP reduction is applied, all CAPs except the one in the first superframe of the multi-superframes are substituted with DSME-GTSs as shown in Fig. 2.
3.2 LLDN
The IEEE 802.15.4e LLDN mechanism [15] operates only in a star topology, and all the devices are connected to the LLDN coordinator. The time is divided in cycles called LLDN superframes, as shown in Fig. 3.
The meaning or the usage of the timeslots in the superframe are as follows:
-
Beacon: the first timeslot of each superframe contains a beacon frame. It is used for synchronization with the superframe structure;
-
Management timeslots: management timeslots are optional, they provide a mechanism for bidirectional transmission of management data in downlink and uplink direction;
-
Nand M: are respectively the number of timeslots allowed for data transmission, and retransmission, N + M defines the total number of timeslots available for uplink transmission. IEEE 802.15.4e standard allows a maximum of 254 timeslots excluding the beacon and management timeslots;
-
GACK: is the Group ACKnowledgment, it contains N bits bitmap to indicate successful and failed uplink transmissions, in the same order as the uplink transmission. It is used to facilitate retransmission of failed transmission within the same superframe;
-
Bidirectional timeslots: used for the transmission of device data to the LLDN PAN coordinator (uplink) as well as of data from the LLDN PAN coordinator to the LLDN device (downlink).
In the LLDN superframe, there are two types of timeslots: dedicated timeslots and shared timeslots. More than one device can be assigned to a timeslot (shared group timeslots). In this case, the devices use simplified CSMA/CA (a contention-based access method).
3.3 Time Slotted Channel Hopping (TSCH) Mechanism
The IEEE 802.15.4e TSCH owes its creation to the integration of the existing TSMP into the IEEE 802.15.4e amendment [17]. Unlike DSME and LLDN, TSCH is a non beacon mechanism. It combines time slotted access and channel hopping [15].
3.3.1 Time Slotted Access Synchronization
In TSCH mechanism, like in TDMA scheme, devices are synchronized through a periodic slotframe. A slotframe is a collection of timeslots repeating over the time. Figure 4 shows a slotframe with four timeslots. Multiple slotframes are used for a given network to define different communication schedule for various devices.
3.3.2 Channel Hopping
TSCH supports the use of multi channels based on channel hopping technic. The channel hopping is defined in [15] as the periodically switching of the channel. It uses a known sequence to both sending and receiving devices.
In TSCH a link is defined as the pairwise assignment of a directed communication between devices in a given timeslot, on a certain channel offset [14, 14, 34]. Hence, a link between two devices can be represented by a couple (ASN, channelOffset), where Absolute Slot Number (ASN) is the total number of timeslots that has elapsed since the start of the network. It increments globally in the network every tiemslot. In principle 16 different channels are available for communication. Each channel is identified by a channelOffset i.e., an integer value in the range [0…15] [14].
Physical channel, CH, in a link is made according to the following formula:
where HSL is the Hopping Sequence List and HSL is the Hopping Sequence Length.
The channel hopping technic improves the network capacity. However, it is considered as a blind channel hopping [62]. So, a blacklisting technic is proposed in [27, 28] to overcome this problem.
In TSCH, there are two types of links. Dedicated and shared links. We can give an example in Fig. 5 of a possible schedule, supporting dedicated and shared links with four channel offsets. The link (2, 2) is assigned to the device H in order to transmit to the device D, i.e., it’s a dedicate link for the device H. Whereas, the link (1, 3) is assigned to devices I and H, i.e., this link is a shared link between devices I and H.
3.3.3 Network Topology
The TSCH mechanism is an independent topology. It can be used to form any topology, from a star to a full mesh [15]. Like in IEEE 802.15.4, the IEEE 802.15.4e TSCH network supports two types of devices:
-
Full Function Device (FFD): device that can operate as either a network coordinator or as a simple network device;
-
Reduced Function Device (RFD): device that can operate only as a network device.
3.3.4 Transmission Process
When a given device is operating in TSCH mode, Contention Channel Access (CCA) may be used as shown in Fig. 6. So, when a device has a packet to transmit, it shall wait for a link to the destination device. Then, the transmitter waits for macTsCCAOffset, and performs CCA. At macTsTxOffset, the device begins transmitting the frame.
3.3.5 Acknowledgment Process
If an acknowledgment is expected, the device waits for macTsRxAckDelay, and then enables the receiver to await the acknowledgment. If the acknowledgment does not arrive within macTsAckWait, the device may idle the radio and consider the transmission failed.
The Fig. 6 summarizes the transmission process with expected acknowledgment.
Where the default values of the MAC parameters are given in Table 1.
3.3.6 Retransmission Process in Dedicated Links
In the case where the retransmission is assigned to be in dedicated link, if an acknowledgment is not received within the appropriate time-out, the device shall conclude that the single transmission attempt has failed. So, the device shall repeat the process of transmitting the data and waiting for an acknowledgment, up to a maximum of macMaxFrameRetries times. If an acknowledgment is still not received after the number of macMaxFrameRetries retransmissions, the MAC sublayer shall assume the transmission has definitively failed and notify the next higher layer of the failure.
3.3.7 TSCH Collision Avoidance Retransmission Algorithm (TSCH CA) in Shared Links
In the case where the transmission was made on a shared link, assigned to more than one device, collisions may occur and result a transmission failure. To reduce the probability of repeated collisions, a retransmission backoff algorithm has been implemented for shared links.
The retransmission backoff is applied only to the transmission on shared links. There is no waiting for transmission on dedicated links. The retransmission backoff is calculated in the number of shared transmission links.
The TSCH CA algorithm has the following characteristics:
-
The backoff window increases after each consecutive failed transmission in a shared link;
-
The backoff window is reset to the minimum value if the transmission is successful in a shared link;
-
The backoff window is reset to the minimum value if the transmission in a dedicated link is successful and the transmit queue is then empty.
-
The backoff window does not change when a transmission has failed in a dedicated link;
-
The backoff window does not change when a transmission is successful in a dedicated link and the transmission queue is still not empty;
The TSCH CA algorithm presented in IEEE 802.15.4e is analogous to that of CSMA/CA described in IEEE 802.15.4 [13], except that the backoff is calculated in shared links, so the CSMA-CA aUnitBackoffPeriod is not used.
A device upon encountering a transmission failure in a shared link shall initialize the Backoff Exponent (BE) to macMinBE (the minimum value of the BE whose default value is one). The MAC sublayer shall delay for a random number in the range \([0,2^{BE} - 1]\) shared link. For each successive failure on a shared link, the device should increase the backoff exponent until the backoff exponent is equal to macMaxBE (which default value is seven). Successful transmission on a shared link resets the backoff exponent to macMinBE. If an acknowledgment is still not received after a maximum retransmissions retry limit macMaxFrameRetries (which default value is three), the MAC sublayer shall assume that the transmission has definitively failed and notify the next higher layer of the failure.
4 Modeling of the IEEE 802.15.4e TSCH CA Mechanism
In this section, we propose a two dimensional Markov chain model for the IEEE 802.15.4e TSCH CA mechanism. Then, we resolve the stationary probabilities equations, in order to compute the packet transmission probability \(\tau\). This probability will be used to develop mathematical models, in order to derive the following performance metrics, namely: data packet loss probability, reliability, energy consumption, throughput, average delay and jitter.
4.1 Hypothesis
The following list depict the considered hypothesis in the construction of our analytical model for IEEE 802.15.4e TSCH CA mechanism.
-
1.
There are N devices disposed on a star topology around an FFD device;
-
2.
There are K devices sharing their data in a shared link (\(K\le N\));
-
3.
The wireless channel is ideal, the capture effect and noise errors are neglected;
-
5.
The frames which have undergone a collision are retransmitted in shared links using TSCH CA algorithm;
-
6.
The possible retransmission in a dedicated link is not taken into account;
-
7.
The ACK is taken into account.
Table 2 defines the probabilities used in our Markov chain model.
4.2 Data Packet Transmission Probability (\(\tau\))
In this subsection, in order to study the behavior of a single device transmitting its data packet in a shared link, we use a two dimensional Markov chain model. This modeling allows us to compute the probability \(\tau\) that a device transmits its data packet in a chosen link.
Our Markov chain of IEEE 802.15.4e TSCH CA mechanism is defined by a graph transition G illustrated in Fig. 7, and its set of states \(E=\{s(t), c(t)\}\), where
-
s(t) is the stochastic process representing at a given time t the backoff stage;
-
c(t) is the stochastic process representing at a given time t the backoff time counter.
-
The state \(\{s(t)=-1, c(t)=0\}\) is the idle state;
-
The state \(\{s(t)=0, c(t)=-1\}\) is the transmission state;
-
The state \(\{s(t)=i, c(t)=-1\}\) is the retransmission state, where \(i\in (1,m)\). m is the macMaxFrameRetries.
-
4.3 Transition Probabilities
The state transition probabilities associated with our Markov chain are given as follows:
-
The backoff counter decreases with the probability expressed in Eq. (2).
-
When the backoff counter reaches to zeros, the device starts transmission immediately, from where Eq. (3).
-
When the transmission has undergone a collision, a new initial backoff value is uniformly chosen at the backoff stage i from the range \([0, W_{i}]\), as in Eq. (4), where
$$\begin{aligned} W_{i} =\left\{ \begin{array}{ll} 2^{i}W_{0}, &{} \quad i\le m_{b}-m_{0}; \\ 2^{m_{b}-m_{0}}W_{0}, &{} \quad m_{b}-m_{0}<i\le m.\\ \end{array} \right. \end{aligned}$$(9)where \(m_{b}={\textit{macMaxBE}}\), \(m_{0}={\textit{macMinBE}}\) and \(m={\textit{macMaxCSMA}}\).
-
After a succesful transmission:
-
If the transmission has undergone a collision at backoff stage m:
As we can see in the graph transition G illustrated by Fig. (7), our Markov chain is irreducible, so the stationary distribution exists. Particulary, this stationary distribution is unique because our Markov chain is ergodic.
Let \(\pi _{i,j}= \lim _{t\rightarrow \infty } (P(s(t)=i, c(t)=k)), i\in (-1,m), k\in (-1,W_{i}-1)\) be the stationary distribution of the proposed Markov chain model. From Eqs. (2)–(8), the closed-form solution for this Markov chain is given by Eq. (10).
According to the normalization condition, we obtain:
Now, we can express each term of Eq. (11) as a function of \(\pi _{0, -1}\).
-
1.
Expression of \(\pi _{-1,0}\) as a function of \(\pi _{0, -1}\):
From our Markov chain, we obtain:
$$\begin{aligned} \pi _{-1,0}&= \lambda \cdot \pi _{-1,0}+ \lambda (1-Pc)\sum _{i=0}^{m}\pi _{i,-1} + \lambda \cdot Pc \cdot \pi _{m,-1}\nonumber \\&= \frac{\lambda }{1-\lambda } \cdot \pi _{0, -1} \end{aligned}$$(12) -
2.
Expression of \(\sum _{i=0}^{m}\sum _{k=0}^{W_{i}-1}\pi _{i,k}\) as a function of \(\pi _{0, -1}\):
From Eq. (10), we have:
$$\begin{aligned} \sum _{i=0}^{m}\sum _{k=0}^{W_{i}-1}\pi _{i,k}&= \sum _{i=0}^{m}\sum _{k=0}^{W_{i}-1} \frac{W_{i}-k}{W_{i}} \pi _{i,-1}\nonumber \\&= \left\{ \begin{array}{llll} \frac{\pi _{0,-1}}{2}\left( \frac{1-Pc^{m+1}}{1-Pc}+W_{0}\frac{1-\left( 2\cdot Pc\right) ^{m+1}}{1-2\cdot Pc}\right) , &{} \\ \quad if\quad m \le m_{b}-m_{0}, &{} \\ \\ \frac{\pi _{0,-1}}{2}\left( \frac{1-Pc^{m+1}}{1-Pc}+W_{0}\frac{1-\left( 2\cdot Pc\right) ^{\acute{m}+1}}{1-2 \cdot Pc}\right) ,&{}\\ else.&{} \\ \end{array} \right. \end{aligned}$$(13) -
3.
Expression of \(\sum _{i=0}^{m}\pi _{i,-1}\) as a function of \(\pi _{0, -1}\):
We use Eq. (10), and we obtain:
$$\begin{aligned} \sum _{i=0}^{m}\pi _{i,-1}= \pi _{0,-1}\left( \frac{1-Pc^{m+1}}{1-Pc}\right) . \end{aligned}$$(14)
Now, we replace Eqs. (12), (13) and (14) in Eq. (11), and we obtain the following expression of \(\pi _{0, -1}\):
The probability \(\tau\) that a device starts transmission, according to our Markov Chain, is the probability to be in the transmission state. i.e. \(\{s(t)=i, c(t)=-1\}\), \(i=1 - m\). It is given by Eq. (16):
This probability is the key to derive the expressions of the performances metrics of IEEE 802.15.4e TSCH/ CA mechanism. However, this probability, \(\tau\), depends on the collision probability Pc that at least one of the remaining devices among those sharing the given link (\(k-1\)) transmits at the same timeslot. We assume that those devices transmit with probability \(\tau\). Then, the collision probability Pc is given as follows:
The non linear system formed by Eqs. (16) and (17) can be solved using a numerical method.
4.4 Data Packets Loss Probability
The data packets are discarded after the maximum retry limit achievement. If a device tries to transmit after m attempts, the data packet will be lost. Then, the data packet loss probability, \(P_{loss}\), is given as follows:
4.5 Reliability
The reliability is defined as the probability of successful data packet transmission. It is expressed as the opposite event of data packet loss probability. So, the reliability R is given by Eq. (19).
4.6 Energy Consumption
The average energy consumption of a device is given as the sum of the average energies consumption in the idle state \(E_{idle}\), the transmission state \(E_{trans}\) and the reception state \(E_{recep}\). It is expressed as follows:
where
\(P_{idle}, P_{trans}\) and \(P_{recep}\) are respectively, the average energy consumption in idle, transmission and reception states.
4.7 Throughput
The throughput is defined as the quantity of successful data packet transmission with the ratio of channel time. The channel time includes channel free time \(\sigma\) and channel busy time.
-
Let Pr be the probability that the channel is busy (there is at least one transmission in the considered timeslot):
$$\begin{aligned} Pr=1-(1-\tau )^{N}. \end{aligned}$$(24) -
Let Ps be the probability of successful data transmission probability conditioned by the fact that the channel is busy:
$$\begin{aligned} Ps=\frac{N \cdot \tau (1-\tau )^{N-1}}{Pr}. \end{aligned}$$(25) -
Let Ts be time duration for successful data packet transmission:
$$\begin{aligned} Ts= L + t_{ack}+ T_{ack}. \end{aligned}$$(26) -
Let Tc be the time duration for collided data packet transmission:
$$\begin{aligned} Tc= L + timeout_{ack}. \end{aligned}$$(27)where L, \(t_{ack}\), \(T_{ack}\) and \(timeout_{ack}\) are respectively the time duration for the data packet transmission (including payload, PHY header and MAC header), waiting time for an ACK, time duration of transmitting an ACK and the timeout of an ACK.
Now, we can give the theoretical expression of throughput as follows:
4.8 Delay
The average delay, E(D), of a successfully sending data packet is the time interval from the data packet is ready to be transmitted, until an ACK is received. Without loss of generalities, we only consider the delay of successful transmission.
-
Let \(D_{i}\) be the average delay that the device transmits a successfully data packet at the ith stage:
$$\begin{aligned} E(D_{i})= t_{s}+ i\cdot t_{c} + \sum _{k=0}^{i} \frac{W_{k}-1}{2} \sigma . \end{aligned}$$(29)where \(\frac{W_{k}-1}{2}\) is the average number of timeslots that a station decrements in the stage i.
-
Let \(Q_{i}\) be the probability that a data packet is successfully transmitted from the stage i:
$$\begin{aligned} Q_{i}= \frac{(1-Pc) Pc^{i}}{1-Pc^{m+1}}. \end{aligned}$$(30)where \((1-Pc)\) is the probability that a data packet is successfully transmitted after previous i failed attempts \((Pc^{i})\), provided that the packet is not dropped \((1 - Pc^{m+1})\).
The expression of average delay is given as follows:
4.9 Jitter
The delay jitter, J, is defined as the possible variation of the data packet delay values from the mean value. We compute the jitter of the data packet as follows:
where the average squared delays \(E(D^{2})\) is calculated by Eq. (33).
5 Performance Evaluation
In this section, we will analyze the IEEE 802.15.4e TSCH in a shared link, under saturated and non saturated conditions \(\lambda =0, 0.5, 0.9\). To see the impact of the number of devices sharing the same link on the performances of the network, we will variate the number of devices sharing the link, at a fixed network size. A Monte Carlo simulations of IEEE 802.15.4e TSCH are presented to complete our analysis. The list of parameters used in our analysis is depicted in Table 3.
Figure 8 shows the collision probability obtained by our analytical expression in Eq. (17) and Monte Carlo simulation. On the one hand, we variate the number of devices sharing the link (K) at a given number of devices in the network (fixed at \(N=50\)). On the other hand, we variate the traffic conditions \(\lambda = 0, 0.5, 0.9\). We observe that the analytical results match the simulation results well whatever the traffic conditions and the number of devices sharing the link in the network are. The collision probability grows up as a function of the number of devices in the network. And, for a given network size, it also grows up as a function of the number of devices sharing the link. For example, for the network size equal to 50, the collisions are lower when the number of devices sharing the network is equal to 10, it grows up until the number of devices sharing the link is equal to 50. The reason is that when the number of devices increases the number of devices trying to transmit becomes important and then causes collisions. In addition, we remark that the curves under saturated traffic condition (\(\lambda =0\)) are above those under non saturated traffic condition (\(\lambda =0.9\)) and medium traffic condition (\(\lambda =0.5\)). Moreover, when \(\lambda =0\) means that the transmission queue is not empty, at each time there is a data packet to transmit. This engenders a higher collision probability.
Figure 9 illustrates the data packet loss rate as a function of the number of devices sharing the link, this figure follows the same behavior of Fig. 8, because the data packet loss rate is strongly related to collisions. So, similarly to collisions, both results of analytical expression in Eq. (18) and simulation are close.
In Fig. 10, we report the reliability as a function of the number of devices sharing the link for \(N=50\) under saturated (\(\lambda =0\)), non saturated (\(\lambda =0.9\)) and medium traffic conditions (\(\lambda =0.5\)) for both analytical expression given in Eq. (19) and simulation. As we have described in previous section, the reliability is the opposite event of the data packet loss rate. So, the curves in Fig. 10 are symmetrical to the curves in Fig. 9 by the asymptote \(x = y\). Simulation results and analytical expression are well matched.
In Fig. 11, we observe the energy consumption according to the number of devices sharing the link for \(N=50\), under saturated (\(\lambda =0\)), non saturated (\(\lambda =0.9\)) and medium traffic conditions (\(\lambda =0.5\)). On the one hand, we notice that the energy consumption decreases under saturated and medium traffic condition as the number of devices sharing the link increases at a given network size. Because, the more the number of devices sharing the link increases under saturated and medium traffic condition, the more collisions are important. So, the more time the device stays in the backoff state than in other states (transmitting and receiving states) and consumes less energy. On the other hand, we remark that the energy consumption increases under non saturated condition (\(\lambda =0.9\)) as the number of devices sharing the link increases at a given network size. Because, under no saturated condition collisions are lower, and the device has more chance to be in a transmitting or receiving state, so it consumes more energy.
It is important to observe that the energy consumption is really dependent on the number of devices sharing the link and the traffic conditions. Like previous curves, the simulations results and analytical expression in Eq. (21) of energy consumption are very close.
Figure 12 illustrates the Throughput as achieved by analytical expression in Eq. (28) and Monte Carlo simulation. We variate the number of devices sharing the link when the network size is 50. We remark that the throughput under non saturated condition increases from 5 to 10 devices and then it decreases until 50 devices. For saturated and medium traffic conditions, the throughput decreases. It is clear that the throughput is affected by collisions. The throughput is higher when the collisions are lower.
Figure 13 shows the delay variation according to the number of devices sharing the link. We notice that the delay increases with the increase of the devices sharing the link. Because, when the number of devices increases, the given device undergoes more collisions, then it spends much time in backoff state and causes long delay.
In Fig. 14, the jitter increases when the size of the network becomes increasingly important meaning that the variation of the data packet delay values from the mean value grows up when the number of devices is greater. The analytical expressions of both delay in Eq. (31) and jitter in Eq. (32) well match with Monte Carlo simulations.
6 Conclusion
In this article, we have modeled and analyzed the performances of IEEE 802.15.4e TSCH. We have derived theoretical expressions of collision probability, data packet loss rate, reliability, energy consumption, throughput, delay and jitter. We have seen that the performances of the TSCH mechanism are strongly related to the number of devices sharing the link and the traffic conditions. The Monte Carlo simulations well matches with our analytical results.
References
Chong, C. Y., & Kumar, S. P. (2003). Sensor networks: Evolution. Proceedings of the IEEE Opportunities and Challenges, 91(8), 1247–1256.
Yuce, Mehmet R., Ng, Peng Choong, & Khan, Jamil Y. (2008). Monitoring of physiological parameters from multiple patients using wireless sensor network. Journal of Medical Systems, 32(5), 433–441.
Davenport, D. M., Ross, F. J., & Deb, B. (2009). Wireless propagation and coexistence of medical body sensor networks for ambulatory patient monitoring. In Sixth international workshop on wearable and implantable body sensor networks (pp. 41–45).
Manes, G., Fantacci, R., Chiti, F., Ciabatti,M., Collodi, G., Di Palma,D., & Manes, A. (2007). Enhanced system design solutions for wireless sensor networks applied to distributed environmental monitoring. In 32nd IEEE conference on local computer networks (pp. 807–814).
Willig, A. (2008). Recent and emerging topics in wireless industrial communications: A selection. IEEE Transactions on Industrial Informatics, 4(2), 102–124.
Tiab, A., & Bouallouche, L. (2014). Routing in industrial wireless sensor networks: A survey. Chinese Journal of Engineering, 2014, 1–7.
Miorandi, D., Uhlemann, E., Vitturi, S., & Willig, A. (2007). Guest editorial: Special section on wireless technologies in factory and industrial automation, part I. IEEE Transactions on Industrial Informatics, 3(2), 95–98.
Platt, G., Blyde, M., Curtin, S., & Ward, J. (2005). Distributed wireless sensor networks and industrial control systems—A new partnership. In The second IEEE workshop on embedded networked sensors EmNetS-II (pp. 157, 158).
IEEE Standard for Information technology—Telecommunications and information exchange between systems—Local and metropolitan area networks—Specific requirements. Part 15.1: Wireless medium access control (MAC) and physical layer (PHY) specifications for wireless personal area networks (WPANs), IEEE Std., Rev. 2005, 14 June 2005.
HART Field Communication Protocol Specifications. (2008). Revision 7.1, DDL Specifications, HART Communication Foundation Std.
ISA. (2009). ISA100.11a: Wireless systems for industrial automation: Process control and related applications, International Society of Automation Std.
IEEE. (1999). Part 11: Wireless LAN medium access control (MAC) and physical layer (PHY) specifications. IEEE Std 802.11.
IEEE Std 802.15.4. IEEE standard for local and metropolitan area networks Part 15.4: low-rate wireless personal area networks (LR-WPANs), (2011) (revision of IEEE std 802.15.4-2006)
De Guglielmo, D., Anastasi, G., & Seghetti, A. (2014). Advances onto the internet of things, from IEEE 802.15.4 to IEEE 802.15.4e: A step towards the internet of things. Berlin: Springer International Publishing.
IEEE Std 802:15:4e. (2012). (Amendment to IEEE Std 802.15.4-2011)
Pister K. S. J., & Doherty, P. L. (2008). TSMP: Time synchronized mesh protocol. In International symposium on distributed sensor networks, DSN.
Accettura, N., & Piro, G. (2014). Optimal and secure protocols in the IETF 6TiSCH communication stack. In Industrial electronics (ISIE), 2014 IEEE 23rd international symposium on (pp. 1469–1474).
Sikandar, A., & Kumar, S. (2014). Performance analysis of interference aware power control scheme for TDMA in wireless sensor networks. Advanced Computing, Networking and Informatics, V(2), 95–101.
Gagliardi, Robert M. (1991). Satellite communications: Frequency-division multiple access. Dordrecht: Springer.
Joo, S. S., Kim, B.S., Jun, J. A., & Pyo, C. S. (2010). Enhanced MAC for the bounded access delay. In International conference on information and communication technology convergence (ICTC) (pp. 423, 424).
Palattella, M., Accettura, N., Dohler, M., Grieco, L., & Boggia, G. (2012). Trafic aware scheduling for reliable low-power multi-hop IEEE 802.15.4e networks. In IEEE 23rd International symposium on personal indoor and mobile radio communications (PIMRC), international symposium (pp. 327–332).
Accettura, N., Palattella, M. R., Boggia, G., Grieco, L. A., & Dohler, M. (2013). Decentralized traffic aware scheduling for multi-hop low power Lossy networks in the internet of things. In IEEE 14th International symposium and workshops in world of wireless, mobile and multimedia networks (WoWMoM) (pp. 1–6).
Capone, S., Brama, R., Ricciato, F., Boggia, G., & Malvasi, A. (2014). Modeling and simulation of energy efficient enhancements for IEEE 802.15. 4e DSME. In IEEE Wireless Telecommunications Symposium (WTS) (pp. 1–6).
Dariz, L., Ruggeri, M., & Malaguti, G. (2013). A proposal for enhancement towards bidirectional quasi-deterministic communications using IEEE 802.15.4. In 21st Telecommunications Forum (TELFOR) (pp. 353–356).
Reinhold, R., & Kays, R. (2013). Improvement of IEEE 802.15. 4a IR-UWB for time-critical industrial wireless sensor networks. In IEEE Wireless Days (WD), IFIP (pp. 1–4).
Berger, A., Pichler, M., Haselmayr, W., & Springer, A. (2014). Energy efficient and reliable wireless sensor networks—An extension to IEEE 802.15.4e. EURASIP Journal on Wireless Communications and Networking, 2014(1), 1–26.
Du, P., & Roussos, G. (2012). Adaptive time slotted channel hopping for wireless sensor networks. In Computer science and electronic engineering conference (CEEC) (pp. 29–34).
Du, P., & Roussos, G. (2013). Spectrum-aware wireless sensor networks. In IEEE 24th International symposium on personal indoor and mobile radio communications (PIMRC) (pp. 2321–2325).
Ouanteur, C., Aïssani, D., Bouallouche-Medjkoune, L., Yazid, M., & Castel-Taleb, H. (2016). Modeling and performance evaluation of the IEEE 802.15. 4e LLDN mechanism designed for industrial applications in WSNs. Wireless Networks, 1–16.
Lee, J., & Jeong, W. C. (2012). Performance analysis of IEEE 802.15.4e DSME MAC protocol under WLAN interference. In IEEE International conference on ICT Convergence (ICTC) (pp. 741–746).
Jeong, W. C., & Lee, J. (2012). Performance evaluation of IEEE 802.15.4e DSME MAC protocol for wireless sensor networks. In First IEEE workshop on enabling technologies for smartphone and internet of things (ETSIoT) (pp. 7–12).
Paso, T., Haapola, J., & Linatti, J. (2013). Feasibility study of IEEE 802.15.4e DSME utilising IR-UWB and S-ALOHA. In IEEE 24th international symposium on personal indoor and mobile radio communications (PIMRC), international symposium (pp. 1863–1867).
Chen, S., Sun, T., Yuan, J., Geng, X., Li, C., Ullah, S., et al. (2013). Performance analysis of IEEE 802.15.4e time slotted channel hopping for low- rate wireless networks. KSII Transactions on Internet and Information Systems (TIIS), 7(1), 1–21.
De Guglielmo, D., Seghetti, A., Anastasi, G., & Conti, M. (2014). A performance analysis of the network formation process in IEEE 802.15. 4e TSCH wireless sensor/actuator networks. In IEEE symposium on computers and communication (ISCC) (pp. 1–6).
Bianchi, G. (2000). Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal on Selected Areas in Communications, 18(3), 535–547.
Chatzimisios, P., Vitsas, V., & Boucouvalas, A. C. (2002).Throughput and delay analysis of IEEE 802.11 protocol. In IEEE 5th international workshop on networked appliances (pp. 168–174).
Chatzimisios, P., Boucouvalas, A. C., & Vitsas, V. (2003). IEEE 802.11 packet delay-a finite retry limit analysis. In IEEE global telecommunications conference GLOBECOM ’03 (Vol. 2, pp. 950–954).
Raptis, P., Banchs, A., & Paparrizos, K. (2006). A-simple-and-effective-delay-distribution-analysis-for-IEEE-802.11. In IEEE 17th international symposium on personal indoor and mobile radio communications (pp. 1–5).
Yazid, M., Bouallouche-Medjkoune, L., Aïssani, D., & Ziane-Khodja, L. (2014). Analytical analysis of applying packet fragmentation mechanism on IEEE 802.11b DCF network in non ideal channel with infinite load conditions. Wireless Networks, 20(5), 917–934.
Yazid, M., Ksentini, A., Bouallouche-Medjkoune, L., & Aïssani, D. (2014). Performance analysis of the TXOP sharing mechanism in the VHT IEEE 802.11 ac WLANs. IEEE Communications Letters, 18(9), 1599–1602.
Yazid, M., Aïssani, D., Bouallouche-Medjkoune, L., Amrouche, N., & Bakli, K. (2015). Modeling and enhancement of the IEEE 802.11 RTS/CTS scheme in an error-prone channel. Formal Aspects of Computing, 27(1), 33–52.
Park, T. R., Kim, T. H., Choi, J. Y., Choi, S., & Kwon, W. H. (2005). Throughput and energy consumption analysis of IEEE 802.15.4 slotted CSMA/CA. IEEE Electronics Leters, 41(18), 1017–1019.
Mišić, J., Shafi, S., & Mišić, V. B. (2006). Performance of a beacon enabled IEEE 802.15.4 cluster with downlink and uplink traffic. IEEE Transactions on Parallel and Distributed Systems, 17(4), 361–376.
Pollin, S., Ergen, M., Ergen, S. C., Bougard, B., Van Der Perre, L., Catthoor, F., Moerman, I., Bahai, A., & Varaiya, P. (2006). Performance analysis of slotted carrier sense IEEE 802.15.4 medium access layer. In Proceedings of GLOBECOM.
Patro, R. K., Raina, M., Ganapathy, V., Shamaiah, M., & Thejaswi, C. (2007). Analysis and improvement of contention access protocol in IEEE 802.15.4 star network. In IEEE internatonal conference on mobile adhoc and sensor systems MASS (pp. 1–8).
Shu, F., Sakurai, T., Zukerman, M., & Vu, H. L. (2007). Packet loss analysis of the IEEE 802.15.4 mac without acknowledgements. IEEE Communications Letters, 11(1), 79–81.
Pollin, S., Ergen, M., Ergen, S. C., Bougard, B., Van der Perre, L., Moerman, I., et al. (2008). Performance analysis of slotted carrier sense IEEE 802.15.4 medium access layer. IEEE Transactions on Wireless Communications, 7(9), 3359–3371.
Sahoo, P. K., & Sheu, J. P. (2008). Modeling IEEE 802.15.4 based wireless sensor network with packet retry limits. In 5th ACM symposium on performance evaluation of wireless ad hoc sensor and ubiquitous networks (pp. 63–70).
Wen, H., Chen, Z. J., & Dutkiewicz, E. (2009). An improved Markov model for IEEE 802.15.4 slotted CSMA/CA mechanism. Journal of Computer Science and Technology, 24(3), 495–504.
Park, P., Di Marco, P., Soldati, P., Fischione, C., & Johansson, K. H. (2009). A generalized Markov chain model for effective analysis of slotted IEEE 802.15.4. In IEEE 6th international conference on mobile adhoc and sensor systems MASS (pp. 130–139).
Wang, F., Li, D., & Zhao, Y. (2011). Analysis of CSMA/CA in IEEE 802.15.4, The Institution of Engineering and Technology. Communications, 5(15), 2187–2195.
Wang, F., Li, D., & Zhao, Y. (2012). On analysis of the contention access period of IEEE 802.15.4 MAC and its improvement. Wireless Personal Communications, 65(4), 955–975.
Li, X., & Hunter, D. K. (2012). Four-dimensional Markov chain model of single-hop data aggregation with IEEE 802.15.4 in wireless sensor networks. Wireless Networks, 18(5), 469–479.
Park, P., Di Marco, P., Fischione, C., & Johansson, K. H. (2013). Modeling and optimization of the IEEE 802.15.4 protocol for reliable and timely communications. IEEE Transactions on Parallel and Distributed Systems, 24(3), 550–564.
Buratti, C., & Verdone, R. (2008). A mathematical model for performance analysis of IEEE 802.15.4 non-beacon enabled mode. In Wireless conference, 14th European IEE (pp. 1–7).
Lauwens, B., Scheers, B., & Van de Capelle, A. (2010). Performance analysis of unslotted CSMA/CA in wireless networks. Telecommunication Systems, 44(1–2), 109–123.
Tinka, A., Watteyne, T., & Pister, K. (2010). A decentralized scheduling algorithm for time synchronized channel hopping. Ad Hoc Networks (pp. 201–216).
Vilajosana, X., Wang, Q., Chraim, F., Watteyne, T., Chang, T., & Pister, K. (2014). A realistic energy consumption model for TSCH. Networks, 14(2), 482–489.
Martinez, B., Vilajosana, X., Chraim, F., Vilajosana, I., & Pister, K. S. (2015). When scavengers meet industrial wireless. IEEE Transactions on Industrial Electronics, 62(5), 2994–3003.
Hennebert, C., & Dos Santos, J. (2014). Security protocols and privacy issues into 6LoWPAN stack: a synthesis. IEEE Internet of Things Journal, 1(5), 384–398.
Anwar, M., & Xia, Y. (2014). IEEE 802.15. 4e LLDN: Superframe configuration for networked control systems. In IEEE 33rd Chinese Control Conference (CCC) (pp. 5568–5573).
Watteyne, T., Mehta, A., & Pister, K. (2009). Reliability through frequency diversity: why channel hopping makes sense. In Proceedings of the 6th ACM symposium on Performance evaluation of wireless ad hoc, sensor, and ubiquitous networks (pp. 116–123).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ouanteur, C., Bouallouche-Medjkoune, L. & Aïssani, D. An Enhanced Analytical Model and Performance Evaluation of the IEEE 802.15.4e TSCH CA. Wireless Pers Commun 96, 1355–1376 (2017). https://doi.org/10.1007/s11277-017-4241-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4241-0