Abstract
Time Slotted Channel Hopping (TSCH) is one of the Medium Access Control methods proposed in the IEEE 802.15.4e standard to deal with the requirements of the industrial Wireless Sensor Networks (WSNs), especially in terms of high reliability and low latency. The key feature of the TSCH method is the combination between a time slotted access with a channel hopping, while considering both shared and dedicated links. The latter are essential for ensuring transmissions without loss and additional delays. Therefore, the objective we are seeking to reach in this paper is to demonstrate the benefit use of dedicated links on industrial WSNs-based 802.15.4e TSCH method. To this end, we propose an analytical model-based Markov chains for the TSCH method taking into account the dedicated links, and we estimate the transmission probability \(\tau \) of a data packet. The latter will be then used to develop others analytical models, in order to derive a number of performance metrics, namely the average access delay, the reliability, the throughput, and the energy consumption. Furthermore, to validate the analytical model, we perform extensive simulations-based Monte-Carlo. Finally, to give credibility to the obtained simulation results, we compute \(95\%\) confidence intervals. Numerical results show that increasing the number of dedicated links reduces significantly the retransmission probability offering best network performances in terms of average access delay, reliability and throughput.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Wireless Sensor Networks (WSNs) have grown in the current era due to their extended scopes. They are widely used in the environmental field for monitoring disasters, such as earthquakes and volcanoes. Another critical application field of WSNs is medical security for remote monitoring of patients. Nowadays, WSNs are integrated in industrial environments for performing control/command tasks, like in factory automation [1] and process automation [2]. Such industrial processes are time-critical and require high reliability, robustness and low latency [3]. These strict demands on the communication protocols have been discussed by proposing revisions to the IEEE 802.15.4 standard, where the most important is characterized by the emergence of the IEEE 802.15.4e amendment. The IEEE Institute released the IEEE 802.15.4e amendment in the fall of 2012, which is aimed at improving and expanding the functionality of the IEEE 802.15.4-2011 standard. In IEEE 802.15.4e amendment, five different Medium Access Control (MAC) methods has been proposed and incorporated, namely: Radio Frequency Identification (RFID), Asynchronous Multi Channel Adaptation (AMCA), Deterministic Synchronous Multichannel Extension (DSME), Low Latency and Deterministic Networks (LLDN) and, Time Synchronous Channel Hopping (TSCH).
TSCH is a MAC method that combines between a time slotted access and the ability of channel hopping. In other words, it is an hyprid of Time Division Multiple Access (TDMA) [4] and Frequency Division Multiple Access (FDMA) [5]. That is why, TSCH provides high reliability and low latency compared to the other IEEE 802.15.4e MAC methods. The most important feature of the TSCH method is its ability to be enabled whether on shared or dedicated links. The shared links are special channels assigned to more than one transmitter, leading collisions and transmissions failures. To remedy the problems of repeated collisions in the packet retransmission, the IEEE 802.15.4e amendment implemented a retransmission algorithm called TSCH-CA (TSCH Carrier Sense). The retransmission of a data packet can take place on a next link to the destination, so the next transmission can be done either on shared links or on dedicated links.
The main goal of the present work is to highlight the new features provided by the IEEE 802.15.4e TSCH mode, such as the use of dedicated links. More precisely, we take into account the transmissions and the retransmissions on the two types of links of the TSCH mechanism, namely shared and dedicated links, unlike the proposed work in the literature considering only the shared link.
To achieve the above goal, we propose an enhanced Markov chain model describing the functioning of a single device in IEEE 802.15.4e TSCH, enabling transmissions and the retransmissions on both shared and dedicated links. The mathematical model allows to compute the average access delay, the reliability, the energy consumption and the throughput of the IEEE 802.15.4e TSCH network. Then, we provide a performance analysis in order to demonstrate the effect of the network size and the number of available dedicated links on the TSCH network performances. Furthermore, Monte Carlo simulations are conducted in order to validate the accuracy of the proposed model. We will also compute a 95% confidence interval for each simulation result in order to consolidate the simulation results. Finally, we give a comparative study between the case where the transmissions and the retransmissions are occurring only on shared links and the case where they are occurring by combining shared links with dedicated links, in order to illustrate the improvements provided by the use of dedicated links.
The rest of this paper is organized as follows: In Sects. 2 and 3, we respectively present a functioning and the existing work on the 802.15.4e TSCH mode. In Sects. 4 and 5, we respectively provide the mathematical modeling and the derivation of the performance metrics of the IEEE 802.15.4e TSCH network. The performance analysis of the 802.15.4e TSCH network is provided is Sect. 6. In Sect. 7 we validate the accuracy of our analytical results. In Sect. 8 we provide a comparative study. Finally, Sect. 9 concludes this paper.
2 Overview of the IEEE 802.15.4e TSCH
In this section, we provide an overview of the TSCH mechanism defined in the IEEE 802.15.4e standard. We describe the most important functionalities provided by TSCH.
2.1 Slotframe structure
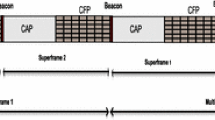
In TSCH mecanism, the notion of superframe employed in DSME, LLDN and its parent standard IEEE 802.15.4 has been replaced by the concept of slotframe. A slotframe consists of defined periods of communication between devices called time slots. A slotframe automatically repeats over the time, hence forming a communication schedule. Figure 1 illustrates an example of a TSCH superframe structure with three time slots [6].
Each time slot is long enough for a pair of devices to exchange a maximum-length data frame and a possible acknowledgment. If the latter is not received within a predetermined time, the retransmission will only occur in the next time slot dedicated to the same pair of devices, and this on any slotframe [7, 8].
2.2 Channel hopping
One of the main features of TSCH is multi-channel communication, built on channel hopping, where the device can periodically switch channel.
According to the IEEE 802.15.4e standard, there are 16 channels operating at a frequency of 2.4 GHz. Each frequency channel is identified by a channelOffset, which is an integer value in the interval [0; 15]. Nevertheless, some of these frequencies could be blacklisted due to poor communication quality [7, 8]. In TSCH, the link between two devices is defined by the coupled [Timeslot, channelOffset]. This is a pairwise assignment of the time slot where the two nodes communicate and their respective channelOffset [6, 7]. The physical CH channel used in a given link is derived as follows:
where ASN is a counter which represents the total number of slots elapsed since the network was deployed. It increments after each time slot and is shared by all the devices of the network. \(N_{ch}\) is the length of the HoppingSequenceList table which contains all the available channels; in other words, \(N_{ch}\) is the number of available frequencies. Finally, F can be implemented as a lookup table.
Two types of links can be established in TSCH mode, they are shared links and dedicated links. When the link is dedicated, only a pair of devices can communicate. In the case of a shared link, several devices can transmit data.
Figure 2 shows an example of a TSCH schedule with three timeslots in each slotframe and four channelOffset. The link (\(T_{2},3\)) is assigned to the devices F and G in order to transmit data packets to the device B; this link is shared between the devices F and G, while the link (\(T_{1},0\)) is assigned to the device I in order to transmit data packets to the device C; it is a dedicated link for the device I.
2.3 PAN formation
TSCH mode can be used with any network topology (eg, star, tree, mesh) and it supports two types of devices as in the IEEE 802.15.4 standard: Reduced-Function Device RFD and Full-Function Device FFD.
When a network is established, the PAN coordinator broadcasts an Enhanced Beacon (EB) in response to an MLME BEACON.request from an upper layer. Devices that wish to connect with the PAN coordinator must be in broadcast scope. The Enhanced Beacon contains information about time, channel hopping, time slots, and initial links. The node wishing to join the network performs an active or passive scan after receiving an MLME-SCAN.request from a higher layer. Once the device hears an Enhance Beacon, it generates an MLME-BEACON NOTIFY.indication at a higher layer. Thus, the latter initializes the slotframe and the information of the initial links available in the Enhanced Beacon(EB). Once the device is synchronized to the network, the upper layer schedules the device in TSCH mode by sending a TSCH MODE.request [7].
2.4 Transmission and acknowledgment process
In TSCH mode, when a device has a data frame to transmit, it must reach its own time slot. If the CCA is enabled, it must wait for macTsCCAOffset \(\mu s\) and then run the CCA. At time macTsTxOffset \(\mu s \), the node starts transmitting the data frame. If an ACK is expected, the device will wait for macTsRxAckDelay \(\mu s \), and then allow the receiver to wait for the ACK. If the ACK is not received after macTsAckWait \(\mu s \), the device can idle the radio and consider the transmission to have failed. If no ACK is expected, the transmitter can idle the radio after sending the frame. As for the receiver, it waits for macTsRxOffset \(\mu s \) then switches to receive mode for macTsRxWait \(\mu s \) . If the frame has not started at this time, it may idle the receiver. Otherwise, once the frame is received, the receiver waits for macTsTxAckDelay \( \mu s \) then sends an ACK [7]. Figure 3 illustrates an example of the transmission process with acknowledgment.
Transmission process diagram with acknowledgment [7]
2.5 TSCH CSMA-CA algorithm
As we have mentioned previously, in the TSCH method, the transmission can be on a shared or dedicated links. Shared link is assigned to more than one device, which leads to collisions and transmission failures. So, in the case where the shared link was utilised and the transmission was unsuccessful, the TSCH Collision avoidance retransmission algorithm (TSCH-CA) should be performed for shared links, in order to reduce the repeated collisions when the packet is retransmitted. As the retransmission may happen in the next link to the destination, the subsequent transmission may be in either shared links or dedicated links. The TSCH-CA retransmission backoff algorithm illustrated in Fig. 4 has the following properties:
-
The retransmission backoff wait is applied just to the transmission on shared link. The transmission is immediate on a dedicated link, i.e. there is no waiting time.
-
The retransmission backoff is calculated in the number of shared transmission links.
-
The backoff window increases for each consecutive transmission failure on a shared link, and it is resets to the minimum value after a successful transmission on a shared link.
-
The backoff window remains unchanged after a failed transmission in a dedicated link.
When a device encounters a failed transmission on a shared link, it shall perform the following steps: First, the Beacon Exponent and the number of retransmissions carried out are initialized \((BE =MAcMinBE )\) and \((NB =0)\) (step 1). The MAC sublayer delays for a random number uniformly generated in the range \([0, 2^{BE-1}]\) shared links (on any slotframe) before retransmitting on a shared link. Retransmission on a dedicated link may happen at any time (step 2). If the retransmission is successful on a shared link (step 3), BE is reset to macMinBE and the algorithm terminates. If the retransmission is failed on a shared link (step 4), NB and BE are incremented, (e.i.\(NB= NB+1\) and \(BE = min(BE + 1; macMaxBE)\)). If NB exceeds macMaxFrameRetries (the default value of the number of retransmissions allowed), e.i. \((NB >macMaxFrameRetries )\) (step 5), the MAC sublayer reports a failure to the higher layer. Otherwise, the algorithm goes back to (step 2).
3 Related work
IEEE 802.15.4e has received significant attention from the scientific community since its advent. Researches have focused on the three MAC mechanisms: LLDN [9,10,11,12,13,14], DSME [15,16,17,18,19] and TSCH [20,21,22,23,24,25,26,27,28,29,30,31,32,33].
In this section, we provide a literature review of the main research regarding the TSCH mechanism. In fact, we identify in this research field two categories of papers: the research that improves the TSCH mechanism and the research focusing on his performance evaluation. As part of the TSCH mechanism improvement, the authors of [20,21,22, 34] are interested on how building an optimal schedule to plan the distribution of time slots and channels in a network-based TSCH method. The approaches proposed in [20] and [34] are centralized and those proposed in [21] and [22] are distributed. The authors of [24, 29, 35] have studied the network association process. In [25], the authors have addressed the blind channel hopping problem. The authors of [36] have proposed algorithms which allow to reduce collisions on shared links.
In the field of performance evaluation, the authors of [27, 30, 37, 38] have analyzed the performances of the TSCH method using simulation and experimentation. In [37], the authors have analyzed the performances of the IEEE 802.15.4e TSCH mode using the NS2 simulation tool, and have presented some results, such as: Delivery ratio, latency and energy per packet. The obtained results have been compared to the legacy IEEE 802.15.4 in order to show the performance enhancements approved by the new amendment. In [27], the authors have analyzed the performances of IEEE 802.15.4e TSCH mode in terms of delivery rate, latency and time to association using a real implementation in emulated environment. The authors of [30] have implemented a full link-layer security on multiple platforms using different hardware/software policies, in order to investigate the security on the link-layer of TSCH. In [38], the authors have evaluated experimentally the communication quality made by TSCH in a setup that includes real motes exposed to a realistic interfering traffic.
On the other hand, the authors of [29, 31,32,33, 39] were interested to the performance evaluation of the TSCH mode using mathematical modeling. The authors of [32] have used Markov chain model in order to analyse the transmission on the shared link. They have derived the expressions of the packet loss rate, normalized throughput, energy consumption, and average access delay. In [29], the authors have presented a Markov chain model to determine the parameters that affect mobile node association process. In [33], the authors have developed a Markov chain model of the TSCH-CA Algorithm in shared links taking into account the capture effect parameter. The authors of [31] have presented an enhanced Markov chain model to evaluate the impact of the number of devices sharing the same link on the performances of the network under saturated and unsaturated conditions. Finally, the authors of [39] have proposed a performance analysis of the TSCH-CA Algorithm under a noisy environment and when only shared links are used.
All the previous work did not highlight the retransmissions on the dedicated links provided by the IEEE 802.15.4e TSCH mode, in order to show their impact on the TSCH network performances. In this paper, we present an extension of the Markov Chain model proposed in [39], taking into account the transmissions and the retransmissions under both noisy shared and dedicated links. In addition, we conduct a comparative study between the case where the transmissions and the retransmissions are carried out only on shared links and the case where they are carried out by combining shared links with dedicated links.
4 Modeling 802.15.4e TSCH method inabling both shared and dedicated links
In this section, we develop a tow-dimensional discrete time Markov chain for modeling the operation of a 802.15.4e TSCH device, which uses specially both shared and dedicated links for communicating. More precisely, we take into account the transmission failure on a dedicated link. We determine the transmission probability \(\tau \) by solving the stationary probabilities equations of the proposed Markov chain model. Then, we use this probability to develop mathematical models in order to obtain some performance metrics, which are: average access delay, reliability, energy consumption and throughput.
4.1 Model hypotheses, parameters and probabilities
We present below the principal hypotheses used for the development of the proposed Markov chain model of the TSCH scheme. The list of all probabilities and parameters required for modeling are given respectively in the Tables 1 and 2.
-
1.
The network consists of a fixed number of devices;
-
2.
There are dedicated channels and shared channels, i.e., the devices can transmit/retransmit their packets on either dedicated link or shared link;
-
3.
The wireless channel is disturbed and noise errors may happen on the transmitted data packets, this means that a transmission failure of a packet may be caused by a noisy channel;
-
4.
The Capture effect is ignored;
-
5.
The ACK is taken into account.
4.2 Transmission probability \(\tau \) of a data packet
Now, we study the functioning of un individual TSCH device by a Markov chain, in order to estimate the transmission probability \(\tau \) that the device transmits its data packet at a given time slot. This probability is then used to compute the considered performance metrics.
Knowing that a device may be in one of the three states: the state where the device is in the process of decrementing its backoff time counter, the state where the device is in the process of retransmitting its data packet using shared or dedicated link and in the idle state.
Let R(t) be the stochastic process modeling, at a given time t, the backoff stage i for a given device.
Let B(t) be the stochastic process modeling, at a given time t, either the backoff time counter when transmitting on a shared link, the transmission on a dedicated link or the idle state.
We can summarize the possible states of a given device as follows:
-
The idle state \(\{R(t)= i, B(t)= -1\}\), \(i\in (0,m)\): in this case, the device will obtain a dedicated link with the probability \(P_{Dt}\) or a shared link with the probability \(P_{Sht}\) and moves to the transmission step.
-
The backoff state \(\{R(t)= i, B(t)= j\}\), \(i\in (0,m)\) and \(j\in (0,W_{i}-1)\): in this case, the device has obtained a shared link and before transmitting, it must decrement a random number drawn in the contention window \([0, W_{i}]\). After reaching the value 0, the device transmits its packet.
-
The transmission state on a dedicated link \(\{R(t)= i, B(t)= -2\}\), \(i\in (0,m)\): in this case, the device has obtained a dedicated link and will transmit its data packet without delay. If the transmission failed, the device will retransmit its data packet with the probability \(P_{e}\). If the data packet is transmitted successfully, the device moves to a new transmission with the probability \(1-P_{e}\).
-
The transmission state on a shared link \(\{R(t)= i, B(t)= 0\}\), \(i\in (0,m)\): in this case, the device is in the transmission stage on a shared link. If the transmission failed, the device will retransmit its data packet with the probability \(P_{r}\). If the transmission is successful, the device will proceed to a new transmission with the probability \(1-P_{r}\).
The backoff window size \(W_{i}\) for a given device in backoff stage i is determined using Eq. (2):
Where \(W_{0} = 2^{macMinBE}\) and \(m=macMaxFrameRetries\).
The two-dimensional process \(\{R(t),B(t)\}\) may be modeled by the discrete-time Markov chain illustrated in Fig. 5.
In the following, we give the list of all transition probabilities of the proposed Markov chain and their descriptions:
-
The transition probability \(P\{i,j/i,j+1\}\) from the state \((i,j+1)\) to the state (i, j) models the decrementation of the backoff counter at each slot time. It is expressed by Eq. (3).
$$\begin{aligned} P\{i,j/i,j+1\}=1, i\in (0,m), j\in (0,W_{i}-1) \end{aligned}$$(3) -
The transition probability \(P\{i,j/i,-1\}\) from the state \((i,-1)\) to the state (i, j) models the transmission on a shared Link at stage i with the choose of the backoff time counter in the contention window \((W_{i})\). It is given by Eq. (4).
$$\begin{aligned} P\{i,j/i,-1\}=PSht/W_{i}, i\in (0,m), j\in (0,W_{i}-1) \end{aligned}$$(4) -
The transition probability \(P\{i,-2/i,-1\}\) from the state \((i,-1)\) to the state \((i,-2)\) models the transmission on a dedicated Link at stage i. It is given by Eq. (5).
$$\begin{aligned} P\{i,-2/i,-1\}=P_{Dt}, i\in (0,m), \end{aligned}$$(5) -
The transition probability \(P\{i,-1/i-1,0\}\) from the state \((i-1,0)\) to the state \((i,-1)\) models back to the idle state after a unsuccessful transmission on a shared link. It is expressed by Eq. (6).
$$\begin{aligned} P\{i,-1/i-1,0\}=P_{r}, i\in (0,m). \end{aligned}$$(6) -
The transition probability \(P\{0,-1/i,0\}\) from the state (i, 0) to the state \((0,-1)\) models back to the idle state after a successful transmission on a shared link. It is expressed by Eq. (7).
$$\begin{aligned} P\{0,-1/i,0\}=1-P_{r}, i\in (0,m). \end{aligned}$$(7) -
The transition probability \(P\{i,-1/i,-2\}\) from the state \((i,-2)\) to the state \((i,-1)\) models back to the idle state after a unsuccessful transmission on a dedicated link. It is given by Eq. (8).
$$\begin{aligned} P\{i,-1/i,-2\}=P_{e}, i\in (0,m). \end{aligned}$$(8) -
The transition probability \(P\{0,-1/i,-2\}\) from the state \((i,-2)\) to the state \((0,-1)\) models back to the idle state after a successful transmission on a dedicated link. It is given by Eq. (9).
$$\begin{aligned} P\{0,-1/i,-2\}=1-P_{e}, i\in (0,m). \end{aligned}$$(9)
where
Now, we will proceed to the calculation of the stationary probability \(\pi _{i,j}\) for each state (i, j) of our Markov chain, with: \(i\in (0,m)\) and \(j\in (-2,W_{i})\) . Indeed, the proposed Markov chain model has a finite state space, and it is irreducible and aperiodic so we can conclude that this stationary distribution is unique. The mathematical formula of the stationary probability distribution is expressed by Eq. (12).
For the calculation of the stationary probabilities, we have applied the Balance Equation [40] provided by Eq. 13.
Where,
S is the state space of the Markov chain, \(\pi _{i}\) is the stationary probability of being in state i and \(P_{i,k}\) is the probability of transition from the state i to the state k.
Hence, we have achieved the following equations:
-
$$\begin{aligned} \pi _{i,-1}=\lambda ^{i}\pi _{0,-1}, i\in (0,m). \end{aligned}$$(14)
-
$$\begin{aligned} \pi _{i,-2}=P_{Dt} \lambda ^{i}\pi _{0,-1}, i\in (0,m). \end{aligned}$$(15)
-
$$\begin{aligned} \pi _{i,0}= P_{Sht}\lambda ^{i}\pi _{0,-1}, i\in (0,m). \end{aligned}$$(16)
-
$$\begin{aligned} \pi _{i,j}= \frac{W_{i}-j}{Wi}\pi _{i,0}, i\in (0,m),j\in (0,W_{i}-1). \end{aligned}$$(17)
Where \(\lambda =\frac{PrP_{Sht}}{P_{Dt}+P_{Sht}+PeP_{Dt}}\)
According to the Eqs. (14), (15), (16) and (17), the values of \(\pi _{i,j}\) are expressed as a function of the probabilities \(P_{r},P_{Dt},P_{Sht},P_{e}\) and the stationary probability \(\pi _{0,-1}\). Now, by imposing the normalization condition on the proposed Markov chain, we obtain the expression of \(\pi _{0,-1}\) as follows:
Hence, we have:
Finally, we can give the expression of the transmission probability \(\tau \) of a data packet. Knowing that a TSCH device can transmits/retransmits its data packet using shared or dedicated link, the transmission probability \(\tau \) may be expressed as the sum of stationary probabilities of transmission states (i, j) on shared links (given by Eq. (22)) and the stationary probabilities of transmission states (i, j) on dedicated links (given by Eq. (23)). Finally \(\tau \) is given by Eq. (21):
Where
4.3 Collision and retransmission probabilities
The collision probability Pc, is the probability that a transmission of a data packet is considered as unsuccessful because of a collision at a given time slot. This probability is expressed as the probability that at least one other device among the remaining \((n-1)\) devices of the TSCH network transmits at the same timeslot on the same shared link. It is given as follows:
As was mentioned in the hypothesis, the channel in not ideal, this means that a data packet may undergo transmission errors. Therefor a transmission of a data packet on a shared link is a failure and needs to be retransmitted if it experiences a collision or transmission errors. Hence, Pr is expressed as function of Pc and Pe as follows:
Equations (20) and (25) form a nonlinear system that can be solved by means of numerical techniques, and we can finally achieve the numerical values of the transition probabilities and stationary probabilities.
5 Performance metrics
Using the defined Markov chain, we are able to derive the mathematical expressions of TSCH method performance metrics, namely: average access delay, energy consumption, reliability and throughput.
5.1 Average access delay
The average access delay of a successful transmission of a data packet is the time interval from which the packet is in the MAC queue ready to be transmitted, until an ACK is received. We only consider the delay of a successful transmission, i.e., the delay of the discarded data packet after reaching the maximum number of attempts is not taken into account. To determine the latter, we first develop the expressions of the average delay spent on a shared link and on a dedicated link. Let \(E[D_{sh_{i}}]\) the average delay of a successful transmission on a shared link at the backoff stage i.
Where,
\(T_{s}\) is the time duration of a successful transmission of the data packet at the backoff stage i.
\(i.T_{c}\) is the time duration of i unsuccessful transmissions of the data packet due to collision and/or transmission errors on a shared link at stages \(0,1,2,...i-1\).
\(E(T_{h})\) is the average backoff delay
Let \(A_{i}\) the event that a device has transmitted the data packet successfully on a shared link at the backoff stage \(i+1\) after i failures.
Let \(A_{m}\) the event that a device has transmitted the data packet successfully on a shared link after m attempts.
Hence, the probability of a successful transmission at the backoff stage \(i+1\) after i failures is given as follows:
Now, using the expression of the average delay of a successful transmission \(E[D_{sh_{i}}]\) at the backoff stage i and the expression of a successful transmission probability \(P(A_{i}/A_{m})\) at the backoff stage i, we can get the expression of the average delay of a successful transmission of a data packet on a shared link as follows:
Let \(E[D_{d_{i}}]\) the average delay of a successful transmission on a dedicated link at the backoff stage i.
Where,
\(T_{s}\) is the time duration of a successful transmission of the data packet at the backoff stage i.
\(i.T_{c}\) is the time duration of i unsuccessful transmissions of the data packet on a shared link at backoff stages \(0,1,2,...i-1\).
\(E(T_{h})\) is the average backoff delay
Let \(B_{i}\) the event that a device has transmitted the data packet successfully on a dedicated link at the backoff stage \(i+1\) after i failures.
Let \(B_{m}\) the event that a device has transmitted the data packet successfully on a dedicated link after m attempts.
Hence, the probability of a successful transmission at the backoff stage \(i+1\) after i failures is given as follows:
Now, using the expression of the average delay of a successful transmission \(E[D_{d_{i}}]\) at the backoff stage i and the expression of a successful transmission probability at the backoff stage i, we can get the expression of the average delay of a successful transmission of a data packet on a dedicated link as follows:
Finally, the avarege delay of a successful transmission of a data packet is given as follows:
5.2 Energy consumption
In this subsection, we give the expression of the average energy consumption of a TSCH device to communicate. Knowing that the device consumes energy during the transmission and the reception states and does not consumes it during backoff stage, the average energy consumption of one device is defined as follow:
where \(E_{trans}\) is the energy consumption in the transmission state and it is given by Eq. (36). \(E_{recep}\) is the energy consumption in the reception state and it is expressed by Eq. (37). Finally, \(E_{idle}\) is the energy consumption in the idle state, it is given by Eq. (38).
\(P_{trans}\), \(P_{recep}\) and \(P_{idle}\) represent respectively the average energy consumption in transmission, reception and idle states.
5.3 Reliability
We will now proceed to the reliability calculation. Reliability is defined as the probability of successful transmission of a data packet. In the TSCH mode, if the transmission of a data packet on a shared link fails after m attempts, it will be considered lost. Therefore, the probability of packet loss is expressed as follows:
Finally, the reliability is given by the following equation:
5.4 Throughput
The throughput TH which can be reached in a TSCH network is determined as a function of the various events which can occur on the transmission channel during a time slot, and this on a shared link and a dedicated link.
First, we will develop the expression of the achievable throughput on a shared link \(Th_{sh}\). The fundamental parameters for the calculation of said throughput are as follows:
-
Let \(P_{tSh}\) the probability that there is at least one transmission on a shared link in a given slot time, i.e., the channel is busy. Given that there are n devices competing for the channel, and each device transmits with the probability \(\tau _ {Sh}\), then:
$$\begin{aligned} P_{tSh}= 1-(1-\tau _{Sh})^{n }. \end{aligned}$$(41) -
Let \(\tilde{P}_{ts}\) the probability of a successful transmission of a data packet. In other words, it is the probability that there is exactly one node transmitting on a shared link, with no noise errors. This probability is also conditioned by the fact that the channel is busy. It is given as follows:
$$\begin{aligned} \tilde{P}_{ts}= \frac{n \tau _{Sh}(1-\tau _{Sh})^{n -1}(1-P_{e})}{P_{tSh}}. \end{aligned}$$(42) -
Let \(T_{s}\) the time duration of a successful transmission of a data packet:
$$\begin{aligned} T_{s}= T_{p}+T_{h}+t_{ack}+T_{ack}; \end{aligned}$$(43)Where,
-
\(T_{p}\) is the time duration of payload transmission.
-
\(T_{h}\) is the time duration of PHY and MAC headers transmission.
-
\(t_{ack}\) is the waiting time for an ACK.
-
\(T_{ack}\) is the time duration of ACK transmission.
Let \(T_{c}\) the time duration of a unsuccessful transmission of a data packet:
$$\begin{aligned} T_{c}= T_{p}+T_{h}+t_{ack-to}; \end{aligned}$$(44)Where, \(t_{ack-to}\) is the timeout of an ACK.
-
Finally, the throughput \( TH_ {sh} \) achievable on a shared link is calculated as follows:
Where,
-
\(L_{p}\) is the payload of a data packet.
-
\((1-P_{tSh})\) is the probability that the transmission channel is free. Hence, \(((1-P_{tSh})\sigma )\) expresses the average duration of a free time slot.
-
\((P_{{tSh}}\tilde{P}_{ts})\) is the probability of a successful transmission on a shared link. Hence, \((P_{{tSh}}\tilde{P}_{ts}T_{s})\) expresses the average duration of a successful transmission on a shared link.
-
\((P_{{tSh}} (1-\tilde{P}_{ts}))\) is the probability of an unsuccessful transmission on a shared link. Hence, \((P_{{tSh}} (1-\tilde{P}_{ts})Tc)\) expresses the average duration of an unsuccessful transmission.
We will now proceed to the calculation of the throughput that can be reached on a dedicated link THd
-
Let \(P_{td}\) the probability that the dedicated link is occupied by a transmission in a given time slot.
$$\begin{aligned} P_{td}= 1-(1-\tau _{D})^{n }. \end{aligned}$$(46) -
Let P sd the probability of a successful transmission of a data packet on a dedicated link.
$$\begin{aligned} P_{sd}= 1-P_{e}. \end{aligned}$$(47) -
Let \(T_{s}\) the duration of a successful transmission of a data packet on a dedicated link:
$$\begin{aligned} T_{s}= T_{p}+T_{h}+t_{ack}+T_{ack}; \end{aligned}$$(48) -
Let \(T_{e}\) the duration of an unsuccessful transmission of a data packet on a dedicated link\(::\)
$$\begin{aligned} T_{e}= T_{p}+T_{h}+t_{ack-to}; \end{aligned}$$(49)
Hence, the throughput \(TH_{d}\) achievable on a dedicated link is given as follows:
Where,
-
\((1-P_{td})\) is the probability that the transmission channel is free. Hence, \(((1-P_{td})\sigma )\) expresses the average duration of a free time slot.
-
\((P_{{td}}{P}_{sd})\) is the probability of a successful transmission on a dedicated link. Hence, \((P_{{td}}{P}_{sd}T_{s})\) expresses the average duration of a successful transmission on a dedicated link.
-
\((P_{{td}} (1-{P}_{sd}))\) is the probability of a successful transmission on a dedicated link. Hence, \((P_{{td}} (1-{P}_{sd})T_{e})\) expresses the average duration of an unsuccessful transmission.
Finally, the overall throughput achievable in a TSCH network is given as follows:
6 Performance evaluation
In this section, we analyze the numerical results obtained from the implementation under Matlab of the mathematical model presented in the Sect. 4. The values of the parameters used in this analysis are presented in the Table 3. The main objective of this part is to show the impact of the number of dedicated channels and the number of devices on the TSCH network performances.
6.1 Impact of the dedicated channels number on the performances of the IEEE 802.15.4e TSCH network
In this part, we analyze the variations of the TSCH performance metrics, namely, the probability of retransmission, the average delay, energy consumption, reliability and throughput according to the number of dedicated channels and for different number of devices in the network. The purpose of this analysis is to see the impact of the number of dedicated channels on the TSCH network performances.
In Fig. 6, we illustrate the variation of the retransmission probability due to collisions or transmission errors, as a function of the dedicated channels number. We note that the retransmission probability decreases with the increase in the number of dedicated channels regardless of the network size. Indeed, by increasing the number of dedicated channels, the probability of transmitting a data packet on a dedicated channel increases, which means that the number of nodes competing to transmit a data packet on a shared link decreases, and then collisions are reduced. Therefore, the retransmission probability is decreased.
Figure 7 shows that by increasing the number of dedicated channels, the average delay decreases. This decrease can be explained by the fact that, the transmission on a dedicated channel does not require a waiting time. And also, as we illustrated in the previous figure, by increasing the number of dedicated channels, collisions are reduced, thus decreasing the probability of retransmission. As a result, the device spends less time in the backoff state and the delay is therefore reduced.
In Fig. 8, we observe that the energy consumption increases by increasing the number of dedicated channels. In fact, this is because the probability of transmission increases and collisions are reduced (as explained previously), so thus the device stays more in the transmission and reception states, thus consuming more energy.
The Fig. 9 indicates that the reliability increases with the increase in the number of dedicated channels, regardless of the number of devices in the network.
Indeed, as the probability of retransmission decreases, the probability that the data packets are discarded decreases when the retransmission attempts exceeded the maximum retry limit value. This increases the reliability of the network.
We observe in the Fig. 10 that the throughput increases with the increase in the number of dedicated channels whatever the number the network size, and this because the bandwidth is used more. We also notice that when the number of devices is greater than that of the channels (up to 5 channels), the throughput obtained with a reduced number of devices (N = 6) is greater than that obtained with an average number (N = 10) and a higher number (N = 14). Indeed, when the number of devices is large, the number of devices competing for access to the transmission channel increases. As a result, the probability of retransmission increases, and the channel is not used for successful transmission. On the other hand, when the number of dedicated channels is greater than the number of devices, we notice the opposite effect. And this because collisions are reduced, so the bandwidth is better used.
6.2 Impact of the network size on the performances of the IEEE 802.15.4e TSCH network
Now, we analyze the variations of the retransmission probability, the average delay, the energy consumption, the reliability and the throughput as a function of the number of devices for different number of dedicated channels. The purpose of this analysis is to show the impact of network size on TSCH network performances.
We note in the Fig. 11 that the probability of retransmission increases with the increase in the number of devices in the network. Indeed, the increase in the number of nodes generates an increase in collisions on the shared links, and thus an increase in retransmissions.
The Fig. 12 shows that the average delay increases with the increase in the number of devices in the network. This is due to the increase in retransmissions caused by collisions on shared links. Therefore, the device spends a lot of time in the backoff state, which causes longer delays. (doubler la fenetre)
We notice in the Fig. 13 that the energy consumption decreases when the number of devices in the network increases.
This is explained by the fact that the devices are not requested to transmit the data. Thus a device spends more time in idle and backoff states than the other states (transmission and reception), and thus consumes less energy.
In Fig. 14, we observe that the reliability decreases by increasing the network syze. In fact, as the probability of retransmission increases, the probability that packets are lost after exceeding a maximum number of retransmission attempts increases, thereby reducing the reliability.
We show in Fig. 15 that, when the number of dedicated channels is equal to 4 and 8, the throughput increases respectively to 6 and 10 devices then decreases. On the other hand, when the number of dedicated channels is equal to 12, the throughput increases with the increase in the number of devices in the network and then stabilizes. As a result, it can be concluded that the throughput is affected by the collisions which generate the retransmissions, and which are reduced when the number of dedicated channels is large. In other words, the throughput becomes important when the collisions are low.
7 Validation
In order to validate the accuracy of the proposed mathematical model and the analytical results obtained in Sect. 4, we have developed a simulation program based on Monte Carlo simulations, using the Matlab programming language. In addition, to consolidate the results obtained, we calculated a 95% confidence interval for each simulation result.
In Figs. 16, 17, 18, 19 and 20, we respectively illustrate the numerical results of the retransmission probability, the average delay, the energy consumed, the reliability and the throughput, in order to compare the results of the analytical expressions obtained in Sect. 4 with their corresponding Monte Carlo simulation results. In all the figures, we notice a good correlation between the analytical results and those of the Monte Carlo simulations.
In Tables 4, 5, 6, 7, 8, we will provide the numerical results of the performance metrics considered. We observe a good correlation between the analytical results and those of Monte Cartlo simulation. Tables 4, 5, 6, 7 and 8 also show the confidence intervals calculated for each simulation result. Finally, according to the Figs. 16, 17, 18, 19, 20 and Tables 4, 5, 6, 7 and 8, we can conclude that the proposed mathematical model is validated by the Monte Carlo simulation results with a good correlation.
8 Comparison
In the following, we present a comparison between our results and the results presented in [32], which considers only the communications on a shared link. Indeed, we will provide a comparative study between the results generated by the analytical model provided in Sect. 4 and those generated by the analytical model presented in [32]. We analyse the variation of the retransmission probability, the average access delay, the energy consumption, the packet loss and the throughput according to the number of devices with 08 dedicated channels for our model.
In Fig. 21, we study the variation of the retransmission probability obtained from our analytical model and that obtained from the model proposed in [32]. We notice that the retransmission probability increases by increasing the number of devices in both cases. However, the retransmission probability obtained from our model is less important than that obtained from the model proposed in [32].
The main reason is that our model takes into account the transmissions on both dedicated and shared links, thus the number of devices sharing a link is limited. Whereas, the model proposed in [32] takes into account only the transmissions on the shared links, so all the devices content the channel for transmission.
Figure 22 shows the data packet loss rate as a function of the number of devices. The behaviour of this figure is similar to that of Fig. 21 for both models, because the data packet loss rate is strongly related to collisions and transmission errors.
We illustrate in Fig. 23 that, the average access delay increases with the increase of the number of devices. Indeed, when the number of retransmissions increases, the device tries more times for transmitting one data packet and spends much time in the backoff state. However, the average delay generated from our model is significantly smaller. The reason is the retransmission on the dedicated links.
We note in Fig. 24 that the energy consumption for a successful transmission of one bit per device increases with the increase in the number of devices. Because, the device tries more times to transmit the data packet, consuming more energy. Nevertheless, the energy consumption obtained from the model presented in [32] is significantly high.
We show in Fig. 25 that the throughput obtained from our model is higher than the one obtained from the model proposed in [32]. We explain this by the fact that the throughput is affected by collisions and transmission errors which are minimized when using the dedicated links.
9 Conclusion
The main goal of this paper is to highlight the benefit use of dedicated links on 802.15.4.e TSCH performances. To do this, we have proposed an analytical model based on a two-dimensional discrete-time Markov chain for the modeling of the IEEE 802.15.4e TSCH method. The proposed model takes into account the transmissions on the two types of links, such as shared and dedicated links. We have studied in more detail the transmission rules of the TSCH-CA protocol, that is to say the successful and unsuccessful transmissions on the two types of links. Solving the stationary probability equations of the proposed Markov chain model has allowed us to estimate the data packet transmission probability. The latter has been used to derive the expressions of the performance metrics, namely: average access delay, energy consumed, reliability and throughput. Monte Carlo simulations for which we have attached confidence intervals were also carried out in order to validate the proposed model. We have analyzed the influence of the number of dedicated links and the number of devices on the TSCH network performances. The results obtained have shown the important gains of dedicated channels. They have proven that increasing the number of dedicated channels improves network performances. This is made by decreasing the retransmission probability, which leads to reduce the average access delay, to increase the reliability and the throughput. All this improvements are important for industrial applications in WSNs.
References
Wu J, Guo S, Li J, Zeng D (2016) Big data meet green challenges: greening big data. IEEE Syst J 10(3):873
Miorandi D, Uhlemann E, Vitturi S, Willig A (2007) Guest Editorial: Special section on wireless technologies in factory and industrial automation. IEEE Trans Ind Inform 3(2):95
Platt G, Blyde M, Curtin S, Ward J (2005) Distributed wireless sensor networks and industrial control systems-a new partnership. In: The second IEEE workshop on embedded networked sensors, EmNetS-II. IEEE, pp 157–158. https://doi.org/10.1109/EMNETS.2005.1469112
Sikandar A, Kumar S (2014) Performance analysis of interference aware power control scheme for TDMA in wireless sensor networks. In: Kumar K, Malay, Mohapatra, Durga P, Konar, Amit, Chakraborty, Aruna (eds) Advanced computing, networking and informatics, vol 2. Springer, pp 95–101
Accettura N, Piro G (2014) Optimal and secure protocols in the IETF 6TiSCH communication stack. In: IEEE 23rd international symposium on industrial electronics (ISIE). IEEE, pp 1469–1474. https://doi.org/10.1109/ISIE.2014.6864831
Kurunathan H, Severino R, Koubaa A, Tovar E (2018) IEEE 802.15.4e in a Nutshell: Survey and Performance Evaluation. IEEE Commun Surv Tutor 20(3):1989–2010. https://doi.org/10.1109/COMST.2018.2800898
IEEE Standard for Local and metropolitan area networks–Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs) Amendment 1: MAC sublayer. IEEE, pp 1–225 (2012)
Guglielmo DD, Nahas BA, Duquennoy S, Voigt T, Anastasi G (2017) Analysis and experimental evaluation of IEEE 802.15.4e TSCH CSMA-CA algorithm. IEEE Trans Veh Technol 66(2):1573. https://doi.org/10.1109/TVT.2016.2553176
Dariz L, Ruggeri M, Malaguti G (2013) A proposal for enhancement towards bidirectional quasi-deterministic communications using IEEE 802.15.4. In: 21st Telecommunications Forum Telfor (TELFOR), pp 353–356. https://doi.org/10.1109/TELFOR.2013.6716242
Berger A, Pichler M, Haselmayr W, Springer A (2014) Energy-efficient and reliable wireless sensor networks: an extension to IEEE 802.15.4e. EURASIP J Wirel Commun Netw 1:126. https://doi.org/10.1186/1687-1499-2014-126
Anwar M, Xia Y (2014) IEEE 802.15.4e LLDN: superframe configuration for networked control systems. In: Proceedings of the 33rd Chinese control conference, pp 5568–5573. https://doi.org/10.1109/ChiCC.2014.6895891
Ouanteur C, Aïssani D, Bouallouche-Medjkoune L, Yazid M, Castel-Taleb H (2017) Modeling and performance evaluation of the IEEE 802.15.4e LLDN mechanism designed for industrial applications in WSNs. Wirel Netw 23(5):1343. https://doi.org/10.1007/s11276-016-1226-y
Sahoo PK, Pattanaik SR, Wu SL (2017) Design and analysis of a low latency deterministic network MAC for wireless sensor networks. Sensors 17(10):2185. https://doi.org/10.3390/s17102185
Willig A, Matusovsky Y, Kind A (2017) Relayer-enabled retransmission scheduling in 802.15.4e LLDN—exploring a reinforcement learning approach. J Sens Actuator Netw 6(2):6. https://doi.org/10.3390/jsan6020006
Jeong WC, Lee J (2012) Performance evaluation of IEEE 802.15.4e DSME MAC protocol for wireless sensor networks. In: First IEEE workshop on enabling technologies for smartphone and internet of things (ETSIoT). IEEE, pp 7–12. https://doi.org/10.1109/ETSIoT.2012.6311258
Lee J, Jeong WC (2012) Performance analysis of IEEE 802.15.4e DSME MAC protocol under WLAN interference. In: International conference on ICT convergence (ICTC), pp 741–746. https://doi.org/10.1109/ICTC.2012.6387133
Capone S, Brama R, Ricciato F, Boggia G, Malvasi A (2014) Modeling and simulation of energy efficient enhancements for IEEE 802.15.4e DSME. In: Wireless telecommunications symposium (WTS). IEEE, pp 1–6. https://doi.org/10.1109/WTS.2014.6835017
Lee YS, Chung SH (2016) An efficient distributed scheduling algorithm for mobility support in IEEE 802.15.4e DSME-based industrial wireless sensor networks. Int J Distrib Sens Netw 12(2):9837625. https://doi.org/10.1155/2016/9837625
Vallati C, Brienza S, Palmieri M, Anastasi G (2017) Improving network formation in IEEE 802.15.4e DSME. Comput Commun 114:1. https://doi.org/10.1016/j.comcom.2017.09.016
Palattella MR, Accettura N, Dohler M, Grieco LA, Boggia G (2012) Traffic aware scheduling algorithm for reliable low-power multi-hop IEEE 802.15.4e networks. In: IEEE 23rd international symposium on personal, indoor and mobile radio communications (PIMRC), pp 327–332. https://doi.org/10.1109/PIMRC.2012.6362805
Accettura N, Vogli E, Palattella MR, Grieco LA, Boggia G, Dohler M (2015) Decentralized traffic aware scheduling in 6TiSCH networks: design and experimental evaluation. IEEE Internet Things J 2(6):455. https://doi.org/10.1109/JIOT.2015.2476915
Duy TP, Dinh T, Kim Y (2017) Distributed cell selection for scheduling function in 6TiSCH networks. Comput Stand Interfaces 53:80. https://doi.org/10.1016/j.csi.2017.03.008
Guglielmo DD, Seghetti A, Anastasi G, Conti M (2014) A performance analysis of the network formation process in IEEE 802.15.4e TSCH wireless sensor/actuator networks. In: IEEE symposium on computers and communications (ISCC), pp 1–6. https://doi.org/10.1109/ISCC.2014.6912607
Vogli E, Ribezzo G, Grieco LA, Boggia G (2015) Fast join and synchronization schema in the IEEE 802.15.4e MAC. In: IEEE wireless communications and networking conference workshops (WCNCW). IEEE, pp 85–90
Du P, Roussos G (2012) Adaptive time slotted channel hopping for wireless sensor networks. In: 4th Computer science and electronic engineering conference (CEEC). IEEE, pp 29–34. https://doi.org/10.1109/CEEC.2012.6375374
De Guglielmo D, Anastasi G, Seghetti A (2014) Advances onto the internet of things. Springer, Berlin, pp 135–152
Alves RCA, Margi CB (2016) IEEE 802.15.4e TSCH mode performance analysis. In: IEEE 13th international conference on mobile ad hoc and sensor systems (MASS), pp 361–362. https://doi.org/10.1109/MASS.2016.054
Vilajosana X, Wang Q, Chraim F, Watteyne T, Chang T, Pister K (2014) A realistic energy consumption model for TSCH networks. IEEE Sens J 14(2):482. https://doi.org/10.1109/JSEN.2013.2285411
Al-Nidawi Y, Kemp AH (2015) Mobility aware framework for timeslotted channel hopping IEEE 802.15.4e sensor networks. IEEE Sens J 15(12):7112. https://doi.org/10.1109/JSEN.2015.2472276
Sciancalepore S, Vučinić M, Piro G, Boggia G, Watteyne T (2017) Link-layer security in TSCH networks: effect on slot duration. Trans Emerg Telecommun Technol 28(1):e3089. https://doi.org/10.1002/ett.3089
Ouanteur C, Bouallouche-Medjkoune L, Aïssani D (2017) An enhanced analytical model and performance evaluation of the IEEE 802.15.4e TSCH CA. Wirel Pers Commun 96(1):1355. https://doi.org/10.1007/s11277-017-4241-0
Chen S, Sun T, Yuan J, Geng X, Li C, Ullah S, Abdullah Alnuem M (2013) Performance analysis of IEEE 802.15.4e time slotted channel hopping for low-rate wireless networks. KSII Trans Internet Inf Syst 7(1):1. https://doi.org/10.3837/tiis.2013.01.001
Guglielmo D, Nahas BA, Duquennoy S, Voigt T, Anastasi G (2017) Analysis and experimental evaluation of IEEE 802.15.4e TSCH CSMA-CA algorithm. IEEE Trans Veh Technol 66(2):1573. https://doi.org/10.1109/TVT.2016.2553176
Martin KM, Seetha Ramanjaneyulu B (2020) Priority Based Centralized Scheduling for Time Slotted Channel Hopping Based Multihop IEEE 802. 15. 4 Networks. J Comput Theor Nanosci 17(1):363–372
Mohamadi M, Djamaa B, Senouci MR, Mellouk A (2021) FAN: fast and active network formation in IEEE 802.15.4 TSCH networks. J Netw Comput Appl 183—-184:103026. https://doi.org/10.1016/j.jnca.2021.103026
Hammoudi S, Harous S, Aliouat Z, Louail L (2018) Time slotted channel hopping with collision avoidance. Int J Ad Hoc Ubiquitous Comput 29(1–2):85–102
De Guglielmo D, Anastasi G, Seghetti A (2014) Advances onto the internet of things. Springer, Berlin, pp 135–152. https://doi.org/10.1007/978-3-319-03992-3
Cena G, Demartini CG, Ghazi Vakili M, Scanzio S, Valenzano A, Zunino C (2020) Evaluating and modeling IEEE 802.15.4 TSCH resilience against Wi-Fi interference in new-generation highly-dependable wireless sensor networks. Ad Hoc Netw 106:102199. https://doi.org/10.1016/j.adhoc.2020.102199
Touloum S, Bouallouche-Medjkoune L, Aïssani D, Ouanteur C (2020) Performance analysis of the IEEE 802.15.4e TSCH-CA algorithm under a non-ideal channel. IJWMC 18(1):1. https://doi.org/10.1504/IJWMC.2020.104765
Gardiner C (2009) Stochastic methods, vol 4. Springer, Berlin
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Touloum, S., Bouallouche-Medjkoune, L., Yazid, M. et al. Performance modeling of the IEEE 802.15.4e TSCH enabling both shared and dedicated links in industrial WSNs. Computing 104, 859–891 (2022). https://doi.org/10.1007/s00607-021-00990-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00607-021-00990-2
Keywords
- Industrial WSNs
- IEEE 802.15.4e standard
- TSCH method
- Dedicated links
- Modeling and analysis
- Simulation and validation