Abstract
The study of chaotic constructions and their associated cryptographic frameworks has sparked a lot of research interest in recent years. Latest advances in wireless technology and the proliferating limitations posed by open communication channels, biometric-enabled remote client authentication procedures with passwords have recently gained traction. In order to address this problem, this paper proposes a secure biometric-based remote user authentication procedure using convolution-Chebyshev chaotic maps with a key agreement procedure. The extended convolution-Chebyshev chaotic maps-based scheme was developed over the interval \(( - \infty , + \infty ),\) and the required properties for the procedure were verified rigorously. The proposed procedure provides a secure client authentication mechanism using biometrics. Additionally, the projected procedure provides a good key agreement feature with perfect forward secrecy while reducing the computation loads for smart cards. As a result, the proposed procedure outperforms related authentication procedures in terms of security and computational performance.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
There has been a lot of research interest in analyzing chaotic systems and their possible cryptographic structures in recent years [1,2,3]. Specific cryptographic primitives behave in a way that is fundamentally similar to chaotic frameworks, which are described by their sensitivity to random operations and initial conditions in the vicinity [4,5,6]. Many remote clients exchange their details with one another due to the relative ease of using the Internet, and the widespread popularity of the Internet of Things (IoT) [7]. The mechanism of remote user authentication ensures that a remote server verifies the legitimacy of a user over an insecure or open communication channel [8,9,10]. It is crucial to verify the identity of remote clients in this situation. In order to address this issue, Lamport [11] suggested the first authentication procedure for use in open network channels in 1981. However, it is worth mentioning that the Lamport system allows the server to keep a verification table for remote clients.
Consequently, hackers could be able to access sensitive information. The password-enabled authentication procedure is an important technique for determining the authenticity of a remote user in a client/server environment [12,13,14,15]. For instance, Sun et al. [16] posit that password-supported authentication procedures have a significant flaw because humans are not specialists at memorizing text strings. As a result, even though they know that their passwords could be insecure, most users would likely select easy-to-remember passwords.
Researchers have recently suggested several biometric-based remote client authentication procedures [17,18,19,20]. The work in [17] in particular presented an improved biometric-based authentication procedure for telecare medicine information systems (TMIS) based on an elliptic curve cryptosystem. By comparison, the work in [18] projected an improved and robust biometrics-based three-factor authentication procedure for applications in multi-server environments. In a similar fashion to work in [18], a robust biometrics-based authentication procedure for a multi-server setting has been presented [19]. Due to Odelu et al. [20], the work presented a secure biometrics-based multi-server authentication procedure using smart cards. Essentially, the biometric system, based on pattern recognition, collects biometric data from an individual. The system accomplishes this by extracting and comparing a feature set from the information to a database template set [21,22,23,24]. According to Das [25], biometric keys have several advantages listed as follows. Biometric keys cannot be lost or forgotten. They are complicated to share or copy. They are also tough to distribute or forge, not easy to break, and cannot be guessed easily.
Additionally, biometric-supported remote client authentication procedures are highly efficient and safer than predictable password-based remote client authentication procedures. In 2014, Chuang et al. [26] introduced a trust computing-based anonymous multi-server authentication with key agreement procedure, leveraging smartcards and biometrics. According to Chuang et al. [26], the procedure is quite simple to use and allows for multi-server authentication and user anonymity. Later, in 2014 and 2015, Mishra et al. [27] and Lin et al. [28] examined Chuang et al. [26] procedure and found several flaws. In order to address these issues, they suggested a stable anonymous three-factor authentication procedure with superior capabilities. In 2015, Lu et al. [29] demonstrated that Mishra et al.’s [27] approach is highly vulnerable to replay attacks and includes an insecure password altering process. For multi-server architecture, they suggested a robust biometric-based authentication procedure.
In 2015, Mir et al. [30] projected an authentication procedure using Elliptic Curve Cryptography (ECC) for telemedicine networks. Also, Chaudhry et al. [31] demonstrated that Mir et al.’s procedure [30] is vulnerable to a misplaced smart card attack and fails to provide the required user anonymity. In 2016, Zhu [32] proposed a multi-server procedure for privacy security focused on chaotic map operations. However, their procedure is limited due to their vulnerability to a privileged insider attack. This is because an RC system insider operating as an attacker can guess a client's password using stored information on the client's device and registration appeal information throughout the registration process.
In 2018, Qi et al. [33] showed that Chaudhry et al.’s [31] procedure could not achieve the perfect forward secrecy and failed a denial-of-service attack. Qi et al. [33] proposed a new procedure to address the limitations inherent in Chaudhry et al.’s procedure [31]. It is worthy of note that the scheme due to Qi et al. [33] can withstand various attacks. Recently, Sahoo et al. [34] presented remarkable results that show the limitations of Qi et al.’s procedure. Sahoo et al. [34] noted that Qi et al.’s procedure [33] could not protect against the key compromise impersonation attack, known session-specific temporary information attack, and offline password guessing attack. In order to address these issues, Sahoo et al. [34] advised an enhanced new procedure based on ECC and demonstrating the strengths to resist various attacks. A summary of some related works is given in Table 1.
The preceding works of literature demonstrate that current biometric-empowered remote client authentication with key agreement procedures has varying security strengths and lower computational overheads. However, when exposed to several high-level adversarial attacks, most of the existing schemes show limited existential unforgeability.
Additionally, remote user authentication using biometric applications with key agreement procedures is critical to the design of future security systems. However, the idea of employing convolution-Chebyshev chaotic maps for biometric-based remote user authentication has not been addressed adequately. Addressing this problem is critical to overcoming the vast limitations of current remote user authentication using biometric with key agreement procedures.
Also, modern cryptography focused on chaos theory, such as signature techniques [35,36,37,38], authentication [9, 39, 40], information hiding techniques [41,42,43], encryption techniques for cloud computing environments [44,45,46,47,48], mobile healthcare [49], secure and adaptive intelligent learning [50,51,52,53], and hash functions [54], which has received a lot of attention in recent years. Thus, the idea of using cryptographic-based chaotic maps to create a robust authentication scheme is not out of place.
Based on chaos theory, the projected procedure will allow a client to communicate with a server anonymously while providing mutual authentication among the client and the server. Thus, the current paper introduces an efficient convolution-Chebyshev chaotic maps-based remote client authentication with key agreement procedure using biometric to address the shortcomings of the related procedures in the literature.
1.1 Contributions
The following are the main contributions of this paper:
-
We projected an effective remote user authentication using biometric with a key agreement procedure, leveraging convolution-Chebyshev chaotic maps.
-
We demonstrated that the proposed remote user authentication using biometric with key agreement procedure has the lowest storage expense in contrast to other procedures in the literature.
-
We showed that our projected scheme gives high-level security. The key innovation in our proposed work is that while maintaining high performance, the proposed remote user authentication using biometric with key agreement procedure provides high-level security.
-
We demonstrate that the proposed remote user authentication using biometric with key agreement procedure can be easily implemented in various low-power and low-processing-power devices.
1.2 Roadmap
The remainder of this article is planned as follows. In Sect. 2, we introduce the definitions of Chebyshev chaotic maps and their extension. In Sect. 3, we developed the new version of chaotic maps and discussed their properties. Then, the projected procedure is presented in Sect. 4. In Sect. 5, we review the projected procedure and prove that it can withstand various sophisticated attacks. In Sect. 6, we examined the performance of the presented procedure. Finally, Sect. 7 concludes the paper and discusses future prospects.
2 Preliminaries
The Chebyshev polynomial and extended chaotic maps are discussed in this section. The symbolizations used in our projected procedure are presented in Table 2.
2.1 Chebyshev chaotic maps
This section looks at Chebyshev polynomials (CP) [55] and examines their functionalities, as shown in Fig. 1. The CP \({\mathtt{T}}_{r} \left( \chi \right)\) is a polynomial with degree n in the variant of \(\chi\). Let \(n\) be an integer, and \(\chi\) \(\in \left[ { - 1, 1} \right]\) be the version. The CP is defined as follows:
where \(\cos^{ - 1}\) and \(\cos \left( x \right)\) are trigonometric functions [56] considered as \(\cos^{ - 1} : \left[ { - 1, 1\left] { \to } \right[0, \pi } \right]\) and \(\cos : \text{R} \to \left[ { - 1, 1} \right].\) Figure 1 shows a few examples of CPs for \(n = 1,2,3,4,5\).
2.2 Properties of Chebyshev polynomials
Two significant properties characterize Chebyshev polynomials [38, 45, 49, 57]. These are the chaotic and semi-group properties.
-
(a)
The chaotic property:
The Chebyshev polynomial map defined as \({\mathtt{T}}_{r} : \left[ { - 1, 1\left] \to \right[ - 1, 1} \right]\) with degree \(n > 1\), is a chaotic map having its invariant density function given as \(f^{*} \left( \chi \right) = \frac{1}{{\left( {\pi \sqrt {1 - \chi^{2} } } \right)}}\) for some positive Lyapunov exponent \(\lambda = {\text{In }} n > 0\).
-
(b)
The semi-group property:
where \({\text{l}}\) and \({\text{w}}\) are positive integers and \(\chi \in \left[ { - 1, 1} \right].\)
2.3 Computational problems
Two challenges that are known to be quite hard to handle within polynomial time are observed in Chebyshev polynomials [35, 36, 38, 39, 45]. These are defined as follows:
-
(1)
Given two exponents \(\chi\) and Y, the task of the discrete Log (DL) is to estimate the integer \(w\) with the end goal \({\mathtt{T}}_{{\text{w}}} \left( \chi \right) = {\text{Y}}\).
-
(2)
Given three exponents \(\chi\), \({\mathtt{T}}_{{\text{w}}} \left( \chi \right)\), and \({\mathtt{T}}_{\ell } \left( \chi \right)\), the task of the Diffie–Hellman problem (DHP) is to estimate the exponent \({\mathtt{T}}_{{{\text{w}}\ell }} \left( \chi \right)\).
2.4 Extended chaotic maps
It was established by Zhang [58] that the above semigroup property holds for CPs within the interval \(\left( { - \infty , + \infty } \right)\). This can be strengthened by:
where \(\chi \in \left( { - \infty , + \infty } \right)\), \(\text{n} \ge 2\) and \(q_{1}\) is a large prime. Now, we reflect on the recurrence relations \({\mathtt{T}}_{\mathrm{n}} \left( \chi \right) = \left( {12{\mathtt{T}}_{\mathrm{n} - 1} \left( \chi \right) - {\mathtt{T}}_{\mathrm{n} - 2} \left( \chi \right)} \right) \left( {\bmod 13} \right)\) with \({\mathtt{T}}_{0} \left( \chi \right) = 1\) and \({\mathtt{T}}_{1} \left( \chi \right) = 6\), where \(q_{1} = 13.\) Then, \({\mathtt{T}}_{\mathrm{n}} \left( \chi \right)\) created by this recurrence is 1, 6, 6, 1, 6, 6, …… with \({\mathtt{T}}\) = 3 period [45, 59]. Obviously,
\({\mathtt{T}}_{{\text{w}}} \left( {{\mathtt{T}}_{{\text{l}}} \left( \chi \right)} \right) \equiv {\mathtt{T}}_{{{\text{lw}}}} \left( \chi \right) \equiv {\mathtt{T}}_{{\text{l}}} \left( {{\mathtt{T}}_{{\text{w}}} \left( \chi \right)} \right) \left( {\bmod \, q_{1} } \right)\),
As a result, the semigroup assets holds and the improved Chebyshev polynomials commute as well.
3 Main results for convolution-Chebyshev chaotic maps
In this section, we briefly familiarize the convolution-Chebyshev summation (CCS). Also, we developed a new version of Chebyshev chaotic maps, known as convolution-Chebyshev chaotic maps (CCCM).
3.1 Convolution-Chebyshev summation (CCS)
Convolution-Chebyshev summation (CCS) is a formula of several variations of any summation method for summing possibly divergent formal power series, introduced by Chebyshev summation.
3.1.1 Convolution-Chebyshev chaotic maps
Definition 1
For two power series in \(z\), the convolution product (Hadamard product) is defined as follows [60]:
where \(\phi \left( \varsigma \right) = \mathop \sum \nolimits_{n = 0}^{\infty } \phi_{n} \varsigma^{n}\) and \(\psi \left( \varsigma \right) = \mathop \sum \nolimits_{n = 0}^{\infty } \psi_{n} \varsigma^{n} .\)
We define a transform called convolution-Chebyshev summation (CCS) by using the convolution product and the summation formula of Chebyshev polynomials.
Note that
where
as follows:
Definition 2
Define a power series in \(\varsigma\)
Define the transform \({\mathcal{T}}_{\chi }\) of \(\phi\) by
Note that
and for all \(\chi ,\) The CCS \({\mathbf{T}}_{\chi } \left( \varsigma \right)\) satisfies the recurrent convolution
Finally, the dynamic plot of the suggested CCS is shown in Fig. 2.
Three-dimensional plot and the contour plot for the functions \({\mathbb{T}}_{\upchi } \left( z \right),\upphi \left( \varsigma \right) = \frac{\varsigma }{{\left( {1 - \text{x}\varsigma } \right)}},{\mathbb{T}}_{\chi } \left( \varsigma \right)*\upphi_{\chi } \left( \varsigma \right)\) of first order and \(\phi_{{\upchi }} \left( \varsigma \right) = \frac{\varsigma }{{(1 - {\text{x}}\varsigma )^{2} }}\) and \({\mathbb{T}}_{\upchi } \left( \varsigma \right),\phi_{\chi } \left( \varsigma \right)\) for the second order, respectively
3.1.2 Extended chaotic maps by using convolution product
Zhang [58] established that the above semigroup properties hold for Chebyshev polynomials defined on the \(\left( { - \infty , + \infty } \right)\) interval, which can improve the assets, as follows (see Sect. 2):
Obviously, \({\mathtt{T}}_{n} \left( {{\mathtt{T}}_{l} \left( \chi \right)} \right) \equiv {\mathtt{T}}_{nl} \left( \chi \right) \equiv {\mathtt{T}}_{l} \left( {{\mathtt{T}}_{n} \left( \chi \right)} \right)\) (mod \(q_{1} )\) , so the semigroup possessions hold and the enhanced Chebyshev polynomials commute under composition.
Using the convolution approach for all \(\chi \in \left( { - \infty , + \infty } \right)\), we get the following result:
Theorem 3.1
Consider the power series \(\phi \left( \varsigma \right) = \sum\nolimits_{n = 0}^{\infty } {\phi_{n} \varsigma^{n} }\) . The recurrent and semi-group relations for all \(\chi \in \left( { - \infty , + \infty } \right)\) are given by
-
(1)
$$\left( {{\mathbf{T}}_{\chi }^{m} \left( \varsigma \right)} \right) = {\mathbf{T}}_{\chi }^{m - 1} \left( {{\varvec{T}}_{\chi } \left( \varsigma \right)} \right) = {\varvec{T}}_{\chi }^{m - 2} \left( {{\varvec{T}}_{\chi }^{2} \left( \varsigma \right)} \right)$$
-
(2)
$${\mathbf{T}}_{\chi }^{k} \left( {{\mathbf{T}}_{\chi }^{m} \left( \varsigma \right)\,} \right) = {\mathbf{T}}_{\chi }^{km} \left( \varsigma \right).$$
Proof
For the first part, it is easy to verify the result directly from the convolution product. For the second part, we use the definition of the generalized formula, we get
4 The proposed procedure
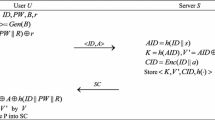
In this section, the proposed scheme using the convolution-Chebyshev chaotic maps is presented. The flowchart of authentication using biometric is shown in Fig. 3. The registration center \({\mathcal{R}\mathcal{C}}_{i}\) starts by picking a random number \(w\) and an arbitrary integer \(b\), then computing \(p{\mathtt{k}} \equiv {\varvec{T}}_{b} \left( w \right) \left( {\bmod \, q_{1} } \right)\). The master secret key \(b\) is held secretly by the registration center \({\mathcal{R}\mathcal{C}}_{i}\). The registration, authentication, login, and password change stages are all part of our presented scheme. The detailed steps of these stages will now be outlined in the subsections as follows.
4.1 Registration stage
The remote \({\mathcal{U}}_{i}\) user must follow the steps below to register and become new authorized users in the framework, as shown in Fig. 4.
-
(1)
The user enters their password \(pwd_{i}\), identity \(id_{i}\), a \({\text{n}}\) arbitrary number, and her/his personal biometric \({\varvec{B}}_{i}\) on a specific computer, then estimates \(\psi_{i} = {\mathcal{H}}\left( {{\varvec{B}}_{i} } \right)\). \({\mathcal{U}}_{i}\) then sends {\(id_{i}\), \(\psi_{i} = {\mathcal{H}}\left( {{\varvec{B}}_{i} } \right)\), \({\mathcal{H}}\left( {pwd_{i} \parallel {\varvec{B}}_{i} \parallel {\text{n}}} \right)\)} via a protected channel to the \({\mathcal{R}\mathcal{C}}_{i}\) registration center.
-
(2)
The registration center calculates the succeeding \({\mathcal{R}\mathcal{C}}_{i}\):
\(\begin{aligned} & \Omega_{i} = {\mathcal{H}}\left( {id_{i} \parallel b} \right), \\ & {\mathcal{W}}_{i} = {\mathcal{H}}\left( {pwd_{i} \parallel {\varvec{B}}_{i} \parallel \text{n}} \right) \oplus \psi_{i} , \\ & {\mathcal{Y}}_{i} = \Omega_{i} \oplus {\mathcal{W}}_{i} . \\ \end{aligned}\)
\({\mathcal{R}\mathcal{C}}_{i}\) embeds \(\left( {id_{i} , {\mathcal{H}}\left( . \right),{\mathcal{Y}}_{i} ,w,p{\mathtt{k}},q_{1} } \right)\) in the user's smart card (SC) and sends it over a protected channel to the user \({\mathcal{U}}_{i}\).
-
(3)
\({\mathcal{U}}_{i}\) calculates \({\varvec{B}}pwd = {\varvec{B}}_{i} \oplus {\mathcal{H}}\left( {pwd_{i} } \right)\) after obtaining the smart card and inserting \({\text{n}}\) and \({\varvec{B}}pwd\) into the SC to complete the registration.
4.2 Login stage
When a legal user \({\mathcal{U}}_{i}\) wishes to access the server \({\mathcal{S}}_{i}\) in this process, as shown in Fig. 5, they must do the following:
-
(1)
\({\mathcal{U}}_{i}\) inserts their SC into the card reader and select a specific device for their biometric template \({\varvec{B}}_{i}\) and password \(pwd_{i}\).
-
(2)
The values \({\varvec{B}}_{i} ^{\prime} = {\varvec{B}}pwd \oplus {\mathcal{H}}\left( {pwd_{i} } \right)\) is computed and \({\varvec{B}}_{i} = {\varvec{B}}_{i} ^{\prime}\) is checked by the SC. The smart card would refuse the request if \({\varvec{B}}_{i} \ne {\varvec{B}}_{i} ^{\prime}\).
-
(3)
The SC creates a \({\mathtt{u }}\) and calculates
\(\begin{aligned} & \psi_{i} = {\mathcal{H}}\left( {{\varvec{B}}_{i} } \right), \\ & {\mathcal{W}}_{i} ^{\prime} = {\mathcal{H}}\left( {pwd_{i} \parallel {\varvec{B}}_{i} \parallel {\text{n}}} \right) \oplus \psi_{i} \\ & \Omega_{i} ^{\prime} = {\mathcal{Y}}_{i} \oplus {\mathcal{W}}_{i} ^{\prime}, \\ & {\mathfrak{W}}_{1} \equiv {\varvec{T}}_{\mathrm{u}} \left( w \right) \left( {\bmod \, q_{1} } \right), \\ & {\mathfrak{W}}_{2} \equiv {\varvec{T}}_{\mathrm{u}} \left( {p{\mathtt{k}}} \right) \left( {\bmod \, q_{1} } \right), \\ & {\text{n}}id_{i} = id_{i} \oplus {\mathcal{H}}\left( {{\mathfrak{W}}_{1} \parallel {\mathfrak{W}}_{2} } \right) \\ & \gamma = {\mathcal{H}}\left( {id_{i} \parallel {\text{n}}id_{i} \parallel \Omega_{i} ^{\prime}\parallel {\mathfrak{W}}_{1} \parallel {\mathfrak{W}}_{2} \parallel \tau_{1} } \right). \\ \end{aligned}\)
-
(4)
The user \({\mathcal{U}}_{i}\) sends {\({\text{n}}id_{i}\), \({\mathfrak{W}}_{1}\), \(\gamma\), \(\tau_{1}\)} to \({\mathcal{S}}_{i}\).
4.3 Authentication stage
The server \({\mathcal{S}}_{i}\) carries out the following phases to access mutual authentication after receiving the login appeal messages, as shown in Fig. 6.
-
(1)
Upon receiving {\({\text{n}}id_{i}\), \({\mathfrak{W}}_{1}\), \(\gamma\), \(\tau_{1}\)}, \({\mathcal{S}}_{i}\) tests the legitimacy of \(\tau_{1}\) by the examination, if the equation \(\tau^{\prime} - \tau_{1} > \Delta \tau\) holds, where \(\tau^{\prime}\) is the time when the server obtains the messages from \({\mathcal{U}}_{i}\) and \(\Delta \tau\) represents the predetermined permissible time period of transmission delay. \({\mathcal{S}}_{i}\) rejects \({\mathcal{U}}_{i}\) if the equation holds.
-
(2)
\({\mathcal{S}}_{i}\) calculates \({\mathfrak{W}}_{2}^{^{\prime}} \equiv {\varvec{T}}_{b} \left( {{\mathfrak{W}}_{1} } \right) \left( {\bmod \, q_{1} } \right)\), \(id_{i} ^{\prime} = {\text{n}}id_{i} \oplus {\mathcal{H}}\left( {{\mathfrak{W}}_{1} \parallel {\mathfrak{W}}_{2} ^{\prime}} \right)\) and checks the legitimacy of \(id_{i} ^{\prime}\).
-
(3)
\({\mathcal{S}}_{i}\) calculates \(\Omega_{i} ^{\prime\prime} = {\mathcal{H}}\left( {id_{i} ^{\prime}\parallel b} \right)\) and \(\gamma ^{\prime} = {\mathcal{H}}\left( {id_{i} ^{\prime}\parallel {\text{n}}id_{i} \parallel \Omega_{i} ^{\prime\prime}\parallel {\mathfrak{W}}_{1} \parallel {\mathfrak{W}}_{2} ^{\prime}\parallel \tau_{1} } \right)\).
-
(4)
Then, \({\mathcal{S}}_{i}\) verifies whether \(\gamma ^{\prime}\) equals to \(\gamma\). If \(\gamma ^{\prime} \ne \gamma\), \({\mathcal{S}}_{i}\) stops the session.
-
(5)
If \(\gamma^{\prime} = \gamma\), \({\mathcal{S}}_{i}\) arbitrarily selects an integer \({\mathtt{v}}\) and calculates \({\mathfrak{W}}_{3} \equiv {\varvec{T}}_{{\mathtt{v}}} \left( w \right) \left( {\bmod \, q_{1} } \right)\) and \(\mu = {\mathcal{H}}\left( {id_{i} ^{\prime}\parallel \Omega_{i} ^{\prime\prime}\parallel {\mathfrak{W}}_{2} ^{\prime}\parallel {\mathfrak{W}}_{3} \parallel \tau_{2} } \right)\). Then, \({\mathcal{S}}_{i}\) sends {\({\mathfrak{W}}_{3}\), \(\mu\), \(\tau_{2}\)} to \({\mathcal{U}}_{i}\).
-
(6)
\({\mathcal{U}}_{i}\) tests the validity of \(\tau_{2}\) by testing, if the equation \(\tau^{\prime} - \tau_{2} > \Delta \tau\) holds after obtaining {\(\mathfrak{W}_{3}\), \(\mu\), \(\tau_{2}\)}. \({\mathcal{U}}_{i}\) rejects \({\mathcal{S}}_{i}\) if the equation holds.
-
(7)
\({\mathcal{U}}_{i}\) checks whether \(\mu^{\prime}? = \mu\) by computing \(\mu ^{\prime} = {\mathcal{H}}\left( {id_{i} \parallel \Omega_{i} ^{\prime}\parallel {\mathfrak{W}}_{2} \parallel {\mathfrak{W}}_{3} \parallel \tau_{2} } \right)\). \({\mathcal{U}}_{i}\) will terminate the session if they are not equal. Otherwise, \({\mathcal{U}}_{i}\) computes \({\mathfrak{W}}_{4} \equiv {\varvec{T}}_{{\mathtt{u}}} \left( {{\mathfrak{W}}_{3} } \right) \equiv {\varvec{T}}_{{{\text{uv}}}} \left( w \right) \left( {\bmod \, q_{1} } \right)\) and \(\xi = {\mathcal{H}}\left( {id_{i} \parallel \Omega_{i} ^{\prime}\parallel {\mathfrak{W}}_{2} \parallel {\mathfrak{W}}_{4} \parallel \tau_{3} } \right)\). Then, \({\mathcal{U}}_{i}\) sends {\(\xi\), \(\tau_{3}\)} to \({\mathcal{S}}_{i}\).
-
(8)
\({\mathcal{S}}_{i}\) tests the validity of \(\tau_{3}\) by testing, if the equation \(\tau^{\prime} - \tau_{3} > \Delta \tau\) holds as it receives {\(\xi\), \(\tau_{3}\)}. \({\mathcal{S}}_{i}\) rejects \({\mathcal{U}}_{i}\) if the equation holds. Otherwise, \({\mathcal{S}}_{i}\) computes \({\mathfrak{W}}_{4}^{^{\prime}} \equiv {\varvec{T}}_{{\mathtt{v}}} \left( {{\mathfrak{W}}_{1} } \right) \equiv {\varvec{T}}_{{{\text{uv}}}} \left( w \right) \left( {\bmod \, q_{1} } \right)\) and \(\xi ^{\prime} = {\mathcal{H}}\left( {id_{i} ^{\prime}\parallel \Omega_{i} ^{\prime\prime}\parallel {\mathfrak{W}}_{2} ^{\prime}\parallel {\mathfrak{W}}_{4} ^{\prime}\parallel \tau_{3} } \right)\) and tests if \(\xi^{\prime}? = \xi\).
-
(9)
\({\mathcal{S}}_{i}\) approves \({\mathcal{U}}_{i}\)’s login appeal if it holds, and the verification is complete. Then, using a symmetric cryptosystem, both \({\mathcal{U}}_{i}\) and \({\mathcal{S}}_{i}\) will connect with each other using the session key \({\mathfrak{W}}_{4}\) and \({\mathfrak{W}}_{4}^{^{\prime}}\).
Subsequently \(p{\mathtt{k}} \equiv {\varvec{T}}_{b} \left( w \right) \left( {\bmod \, q_{1} } \right)\), \({\mathfrak{W}}_{1} \equiv {\varvec{T}}_{{\mathtt{u}}} \left( w \right) \left( {\bmod \, q_{1} } \right)\), \({\mathfrak{W}}_{2} \equiv {\varvec{T}}_{{\mathtt{u}}} \left( {p{\mathtt{k}}} \right) \left( {\bmod \, q_{1} } \right)\), and \({\mathfrak{W}}_{3} \equiv {\varvec{T}}_{{\mathtt{v}}} \left( w \right) \left( {\bmod \, q_{1} } \right)\) so that we can originate
and
\({\mathfrak{W}}_{4}^{^{\prime}} \equiv {\varvec{T}}_{{\mathtt{u}}} \left( {{\mathfrak{W}}_{3} } \right) \equiv {\varvec{T}}_{{\mathtt{u}}} \left( {{\varvec{T}}_{{\mathtt{v}}} \left( w \right)} \right) \equiv {\varvec{T}}_{{\mathtt{v}}} \left( {{\varvec{T}}_{{\mathtt{u}}} \left( w \right)} \right) \equiv {\varvec{T}}_{{\mathtt{v}}} \left( {{\mathfrak{W}}_{1} } \right) \equiv {\mathfrak{W}}_{4} \left( {\bmod \, q_{1} } \right)\).
As a result, the correctness of the scheme is established.
4.4 Password change stage
The smart card confirms the user's previously entered password before updating the newly updated password during this process. The user \({\mathcal{U}}_{i}\) goes through the following steps to update the password:
-
(1)
Inserts the SC and suggestions both the \({\varvec{B}}_{i}\) biometric template and \(pwd_{i}\) old password.
-
(2)
\({\varvec{B}}_{i} ^{\prime} = {\varvec{B}}pwd \oplus {\mathcal{H}}\left( {pwd_{i} } \right)\) is computed by the smart card, and \({\varvec{B}}_{i} = {\varvec{B}}_{i} ^{\prime}\) is checked. If \({\varvec{B}}_{i} \ne {\varvec{B}}_{i} ^{\prime}\) is true, \({\mathcal{U}}_{i}\) has entered the incorrect old password or biometric template. The SC then declines the order.
-
(3)
\({\mathcal{U}}_{i}\) enters their new password \(pwd_{i}^{new}\), if the biometric verification is effective.
-
(4)
The smart card is capable of computing the following:
\(\begin{aligned} & \psi_{i} = {\mathcal{H}}\left( {{\varvec{B}}_{i} } \right), \\ & {\mathcal{W}}_{i} \,^{\prime} = {\mathcal{H}}\left( {pwd_{i} \parallel {\varvec{B}}_{i} \parallel {\text{n}}} \right) \oplus \psi_{i} , \\ & {\mathcal{W}}_{i} \,^{\prime\prime} = {\mathcal{H}}\left( {pwd_{i}\,^{new} \parallel {\varvec{B}}_{i} \parallel {\text{n}}} \right) \oplus \psi_{i} , \\ & \Omega_{i} \,^{\prime} = {\mathcal{Y}}_{i} \oplus {\mathcal{W}}_{i} ^{\prime}, \\ & {\mathcal{Y}}_{i} \,^{\prime} = \Omega_{i}\, ^{\prime} \oplus {\mathcal{W}}_{i} \,^{\prime\prime}. \\ \end{aligned}\)
-
(5)
Finally, replaces \({\mathcal{Y}}_{i}\) with \({\mathcal{Y}}_{i} ^{\prime}\) on the smart card.
5 Security Analysis and Discussion
This segment contains a check to ensure that the procedure under consideration supports mutual authentication, perfect forward secrecy, and user anonymity. Furthermore, we tested the proposed protocol against a variety of attacks, including privileged insider attack, replay attack, offline password guessing attack, perfect forward secrecy, stolen-verifier attack, known-plaintext attack, and Bergamo et alattack.'s [56].
Proposition 1
The proposed procedure can achieves privileged insider attacks.
Proof
The remote user \({\mathcal{U}}_{i}\) sends \({\mathcal{H}}\left( {pwd_{i} \parallel {\varvec{B}}_{i} \parallel {\text{n}}} \right)\) to the registration center \({\mathcal{R}\mathcal{C}}_{i}\) during the registration procedure of the presented scheme. Without \({\varvec{B}}_{i}\) and \({\text{n}}\), the privileged insider cannot deduce the password \(pwd_{i}\). As a result, our system will withstand a privileged insider attack.
Proposition 2
The presented procedure can achieve user anonymity.
Proof
The attacker can listen in on a user \({\mathcal{U}}_{i}\)'s communication with a server \({\mathcal{S}}_{i}\) and attempt to track down the user's true identity to obtain info about the user. The real identity \(id_{i}\) is secured in our scheme by \({\mathfrak{W}}_{2} \equiv {\mathfrak{W}}_{2}^{^{\prime}} \equiv {\varvec{T}}_{b} \left( {{\varvec{T}}_{{\mathtt{u}}} \left( w \right)} \right) \left( {\bmod \, q_{1} } \right)\) from \(p{\mathtt{k}} \equiv {\varvec{T}}_{b} \left( w \right) \left( {\bmod \, q_{1} } \right)\) and \({\mathfrak{W}}_{1} \equiv {\varvec{T}}_{{\mathtt{u}}} \left( w \right) \left( {\bmod \, q_{1} } \right)\). The attacker would need to deal with the convolution-Chebyshev chaotic maps-based DHP to compute \(\mathfrak{m}_{2}\). As a result, our presented scheme will guarantee user anonymity.
Proposition 3
The proposed procedure can achieves mutual authentication.
Proof
The mutual authentication among the user \({\mathcal{U}}_{i}\) and server \({\mathcal{S}}_{i}\) is possible with our presented scheme. To authenticate \({\mathcal{U}}_{i}\), server \({\mathcal{S}}_{i}\) must check the validity of \(\gamma\) and \(\xi\) during the authentication process of our presented scheme. To authenticate \({\mathcal{S}}_{i}\), the user \({\mathcal{U}}_{i}\)'s smart card must also check the validity of \(\mu\). If an attacker attempts to forge messages, she/he will be faced with the convolution-Chebyshev chaotic maps-based DLP and the convolution-Chebyshev chaotic maps-based DHP. As a result, both the server and the user will authenticate, resulting in mutual authentication.
Proposition 4
The presented procedure can achieve an off-line password guessing attack.
Proof
The messages {\({\text{n}}id_{i}\), \({\mathfrak{W}}_{1}\), \(\gamma\), \(\tau_{1}\)} and {\({\mathfrak{W}}_{3}\), \(\mu\), \(\tau_{2}\)} may be intercepted by the attacker. The attacker can also gain access to the smart card's \({\mathcal{Y}}_{i}\). Then, she/he will try to guess the \(pwd_{i} ^{\prime}\) password. However, since the attacker lacks knowledge of the elements \({\mathcal{W}}_{i}\), \(\psi_{i}\), \({\varvec{B}}_{i}\) and \(\Omega_{i}\), the attacker is unable to check the correctness of the password \(pwd_{i} ^{\prime}\). The attacker will also have to deal with the convolution-Chebyshev chaotic maps-based DHP if he tries to derive the random integers \({\mathtt{u}}\) and \({\mathtt{v}}\). As a result, our system can withstand an offline password guessing attack.
Proposition 5
The presented procedure can achieve replay attacks.
Proof
In the next run, the attacker might intercept contact messages from \({\mathcal{U}}_{i}\) and replay them to the server \({\mathcal{S}}_{i}\). With the wrong timestamps, however, the intruder is unable to pass the verification. So, by using the timestamps \(\tau_{1}\), \(\tau_{2}\), and \(\tau_{3}\), our presented procedure is safe against the replay attack.
Proposition 6
The proposed procedure can achieves a stolen-verifier attack.
Proof
The stolen-verifier attack occurs when an intruder good deals with the server's security-sensitive verification table and uses it to impersonate a genuine user during the authentication process. In our presented system, the server does not need to keep any security-subtle verification tables. As a result, our procedure is immune to the stolen-verifier attack.
Proposition 7
The projected procedure can achieve perfect forward secrecy.
Proof
According to perfect forward secrecy, even if a session key or long-term key is compromised in some way, the foe will be unable to extract all other session keys from the cracked one [61, 62]. In our proposed procedure, the smart card and server \({\mathcal{S}}_{j}\) compute the existing session key \(\xi = {\mathcal{H}}\left( {id_{i} \parallel \Omega_{i} ^{\prime}\parallel {\mathfrak{W}}_{2} \parallel {\mathfrak{W}}_{4} \parallel \tau_{3} } \right)\), where \({\mathfrak{W}}_{3} \equiv {\varvec{T}}_{{\mathtt{v}}} \left( w \right) \left( {\bmod \, q_{1} } \right)\), and \({\mathfrak{W}}_{4} \equiv {\varvec{T}}_{{\mathtt{u}}} \left( {\mathfrak{m}_{3} } \right) \left( {\bmod \, q_{1} } \right)\) use random numbers \({\mathtt{v}}\) and \({\mathtt{u}}\) and \(\Omega_{i} ^{\prime} = {\mathcal{Y}}_{i} \oplus {\mathcal{W}}_{i} ^{\prime}\), where \({\mathcal{W}}_{i} ^{\prime} = {\mathcal{H}}\left( {pwd_{i} \parallel {\varvec{B}}_{i} \parallel {\text{n}}} \right) \oplus \psi_{i}\). Even if a foe knew the current session key, they would be unable to use it to calculate any of the other valid session keys because the random numbers in each contact session are unique. With our presented procedure, this procedure aids in maintaining complete forward confidentiality.
Proposition 8
The projected procedure can achieves lost smart card attacks.
Proof
Assume that a side-channel attack will remove all of the data from the smart card [63, 64]. The attacker may attempt to deduce the password from the data, but the elements protect the password \({\mathcal{W}}_{i}\), \(\psi_{i}\), \({\varvec{B}}_{i}\), and \(\Omega_{i}\), which the attacker does not have access to it. Furthermore, if the biometric template of the user \({\varvec{B}}_{i}\), is not provided, the attacker is unable to pass biometric authentication. As a result, our presented procedure is impervious to smart card theft.
Proposition 9
The presented procedure can achieves Bergamo et al.’s attack [56].
Proof
Bergamo et al.’s attack [56] is predicated on a foe being able to obtain the related variables \(b\), w, \({\mathfrak{W}}_{1}\), and \({\mathfrak{W}}_{3}\) and derive u and v from them. The adversary may be able to quickly obtain \(b\), w, \({\mathfrak{W}}_{1}\), and \({\mathfrak{W}}_{3}\), but there is no way in our presented procedure to extract \({\mathtt{u}}\) and \({\mathtt{v}}\) from those values. Convolution-Chebyshev chaotic maps encrypt the elements, which can only be identified by the client and server. In addition, we use enhanced convolution-Chebyshev chaotic maps to avoid the periodicity of the cosine function by extending the \({\mathcal{Y}}\) interval to \(\left( { - \infty , + \infty } \right)\). As a result, Bergamo et al. attack’s [56] have no bearing on our proposed procedure.
6 Performance analysis and discussion
We demonstrate how well the proposed procedure works in this section of the paper. Table 3 compares the security futures of our projected procedure to those of Lee et al. [65], He et al. [61], Lee and Hsu [66], Fan et al. [67], Qi and Chen [33], and Sahoo et al. [34] existing procedures. Under critical considerations, our proposed procedure provides more security than the other existing procedures. Furthermore, we compared the computational primitives used in our proposed procedure for positioning the user and server to those used in other related procedures. We assume that the hash output of \(h\left( . \right)\) is 160 bits (if we use the SHA-1 hash algorithm [68]) and that both the clear identity \(\varvec{id}_{i}^{^{\prime}}\) and the check value are 160 bits. As a result, a sensor node's total storage requirement is 480 bits.
In this comparison, we used the four-time complexity notations: \({\mathtt{t}}_{ch} ,\;{\mathtt{t}}_{s}\),\({\mathtt{t}}_{h} ,\) and \({\mathtt{t}}_{{{\text{ec}}}}\) which described the performance time for a Chebyshev chaotic map operation, one elliptic curve scale multiplication, a one-way hash function, and a symmetric encryption/decryption operation, respectively. Several works [35,36,37, 69] have recognized the relationships between \({\mathtt{t}}_{{\text{h}}} ,{\mathtt{t}}_{{{\text{ch}}}} ,{\mathtt{t}}_{{\text{s}}}\) and \({\mathtt{t}}_{{{\text{ec}}}}\) with respect to \({\mathtt{t}}_{{\text{h}}}\) \(\left( {{\mathtt{t}}_{{\text{h}}} = 0.32\,{\text{ms}}} \right)\). The relationship and order of computational complexity among the metrics are as follows: \({\mathtt{t}}_{s} \approx {\mathtt{t}}_{h} , {\mathtt{t}}_{{{\text{ch}}}} \approx {\mathtt{t}}_{{\text{h}}} ,{\mathtt{t}}_{{{\text{ec}}}} \approx 72.5{\mathtt{t}}_{{\text{h}}} ,\) and \({\mathtt{t}}_{ch} \approx {\mathtt{t}}_{{\text{h}}} \approx {\mathtt{t}}_{{\text{s}}} < {\mathtt{t}}_{{{\text{ec}}}}\). Table 4 shows the proposed procedure as well as the most time-consuming operations of the existing procedures. Figure 7 also compares total processing costs in milliseconds (ms).
By comparison, due to the use of Chebyshev chaotic maps and hash functions, our proposed procedure can provide comprehensive security assurance at a very low computation cost while demonstrating very high efficiency.
Remote user authentication is an essential part of accessing valuable services or resources in healthcare, the Internet of Things (IoT), multi-server environments, and cloud applications. Remote user authentication [70] is an essential part of any security architecture. Authorization grants identity-based privileges, and audit trails are not transparent without authentication. The presented procedure is lightweight; therefore, it is very useful for the development of lightweight authentication protocols for Internet of Things (IoT), multi-server environments, and cloud applications.
The convolution is a mathematical operation on two functions, formulas (polynomials, expressions, etc.) (X and Y) that yields a third function X*Y = Z) that states how the outline of one is improved by the other. The term convolution indicates to both the consequence function and to the procedure of calculating it. Understanding discrete convolution as polynomial multiplication, which is a necessary operation in digital signal and image processing. The summation on k-times is known as a periodic summation of the function X with respect to Y. The proposed procedure is based on the convolution-Chebyshev chaotic maps and its security is based on the hardness of convolution-Chebyshev chaotic maps.
7 Conclusions
This article projected an efficient convolution-Chebyshev chaotic maps-enabled remote user authentication with key agreement procedure using biometric. We developed the extended convolution-Chebyshev chaotic maps over the interval \(\left( { - \infty , + \infty } \right)\) and derived the required properties to establish the proposed procedure. The procedure shows significant biometric authentication without verification tables, enhances user anonymity, gives perfect forward secrecy, and has less computational and communication costs. Finally, formal and informal security and performance analyses revealed that the proposed procedure performs better than related procedures in the literature. Future work would focus on harnessing the potentials of the proposed procedure to provide a secure biometric authenticated key agreement for telemedicine-based information systems.
Data availability
No data was used in this article.
References
Meshram C, Ibrahim RW, Meshram SG, Jamal SS, Imoize AL (2021) An efficient authentication with key agreement procedure using Mittag–Leffler–Chebyshev summation chaotic map under the multi-server architecture. J Supercomput. https://doi.org/10.1007/s11227-021-04039-1
Meshram C, Obaidat MS, Hsiao K-F, Imoize AL, Meshram A (2021) An effective fair off-line electronic cash protocol using extended chaotic maps with anonymity revoking trustee. In: 2021 International Conference on Communications, Computing, Cybersecurity, and Informatics, pp 1–5. https://doi.org/10.1109/ccci52664.2021.9583217
Lin C-H et al (2021) Intelligent symmetric cryptography with chaotic map and quantum based key generator for medical images infosecurity. IEEE Access 9:118624–118639
Kocarev L (2002) Chaos-based cryptography: a brief overview. IEEE Circ Syst Mag 1(3):6–21
Aydın Y, Özkaynak F (2021) Eligibility analysis of different chaotic systems derived from logistic map for design of cryptographic components. In: 2021 International Conference Engineering Technologies and Computer Science (EnT), pp 27–31
Munir N, Khan M, Hazzazi MM, Aijaedi A, Alharbi AR, Hussain I (2021) Cryptanalysis of internet of health things encryption scheme based on chaotic maps. IEEE Access 9:105678–105685
Imoize AL, Adedeji O, Tandiya N, Shetty S (2021) 6G enabled smart infrastructure for sustainable society: opportunities, challenges, and research roadmap. Sensors 21(5):1–58. https://doi.org/10.3390/s21051709
Li C-T, Hwang M-S (2010) An efficient biometrics-based remote user authentication scheme using smart cards. J Netw Comput Appl 33(1):1–5
Meshram C, Obaidat MS, Meshram A (2020) An efficient robust lightweight remote user authentication protocol using extended chaotic maps. In: Proceedings of the 2020 International Conference on Computer, Information, and Telecommunication Systems, CITS 2020, pp 8–13. https://doi.org/10.1109/CITS49457.2020.9232622
Sun Q, Moon J, Choi Y, Won D (2016) An improved dynamic ID based remote user authentication scheme for multi-server environment. In: Green, Pervasive, and Cloud Computing, pp 229–242
Lamport L (1981) Password authentication with insecure communication. Commun ACM 24(11):770–772
Fan L, Li J-H, Zhu H-W (2002) An enhancement of timestamp-based password authentication scheme. Comput Secur 21(7):665–667
Lee C-C (2009) On security of an efficient nonce-based authentication scheme for SIP. Int J Netw Secur 9(3):201–203
Shen J-J, Lin C-W, Hwang M-S (2003) Security enhancement for the timestamp-based password authentication scheme using smart cards. Comput Secur 22(7):591–595
Sarohi HK, Khan FU (2013) Graphical password authentication schemes: current status and key issues. Int J Comput Sci Issues 10(2 Part 1):437
Sun H-M, Chen Y-H, Lin Y-H (2011) oPass: a user authentication protocol resistant to password stealing and password reuse attacks. IEEE Trans Inf Forensics Secur 7(2):651–663
Lu Y, Li L, Peng H, Yang Y (2015) An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J Med Syst 39(3):1–8
Chaudhry SA, Naqvi H, Farash MS, Shon T, Sher M (2018) An improved and robust biometrics-based three factor authentication scheme for multiserver environments. J Supercomput 74(8):3504–3520
He D, Wang D (2014) Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst J 9(3):816–823
Odelu V, Das AK, Goswami A (2015) A secure biometrics-based multi-server authentication protocol using smart cards. IEEE Trans Inf Forensics Secur 10(9):1953–1966
Jain AK, Ross A, Prabhakar S (2004) An introduction to biometric recognition. IEEE Trans Circuits Syst Video Technol 14(1):4–20
Li C-T, Hwang M-S (2010) An online biometrics-based secret sharing scheme for multiparty cryptosystem using smart cards. Network 3(4):5
Maltoni D, Maio D, Jain AK, Prabhakar S (2009) Handbook of fingerprint recognition. Springer
Prabhakar S, Pankanti S, Jain AK (2003) Biometric recognition: security and privacy concerns. IEEE Secur Priv 1(2):33–42
Das AK (2011) Analysis and improvement on an efficient biometric-based remote user authentication scheme using smart cards. IET Inf Secur 5(3):145–151
Chuang M-C, Chen MC (2014) An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst Appl 41(4):1411–1418
Mishra D, Das AK, Mukhopadhyay S (2014) A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst Appl 41(18):8129–8143
Lin H, Wen F, Du C (2015) An improved anonymous multi-server authenticated key agreement scheme using smart cards and biometrics. Wirel Pers Commun 84(4):2351–2362
Lu Y, Li L, Yang X, Yang Y (2015) Robust biometrics based authentication and key agreement scheme for multi-server environments using smart cards. PLoS ONE 10(5):e1026323
Mir O, Nikooghadam M (2015) A secure biometrics based authentication with key agreement scheme in telemedicine networks for e-health services. Wirel Pers Commun 83(4):2439–2461
Chaudhry SA, Naqvi H, Khan MK (2018) An enhanced lightweight anonymous biometric based authentication scheme for TMIS. Multimed Tools Appl 77(5):5503–5524
Zhu H, Zhang Y, Sun Y (2016) Provably secure multi-server privacy-protection system based on Chebyshev chaotic maps without using symmetric cryptography. Int J Netw Secur 18(5):803–815
Qi M, Chen J (2018) New robust biometrics-based mutual authentication scheme with key agreement using elliptic curve cryptography. Multimed Tools Appl 77(18):23335–23351
Sahoo SS, Mohanty S, Majhi B (2020) Improved biometric-based mutual authentication and key agreement scheme using ECC. Wirel Pers Commun 111(2):991–1017
Meshram C, Obaidat MS, Tembhurne JV, Shende SW, Kalare KW, Meshram SG (2020) A lightweight provably secure digital short-signature technique using extended chaotic maps for human-centered IoT systems. IEEE Syst J. https://doi.org/10.1109/JSYST.2020.3043358
Meshram C, Ibrahim RW, Obaid AJ, Meshram SG, Meshram A, Abd El-Latif AM (2021) Fractional chaotic maps based short signature scheme under human-centered IoT environments. J Adv Res 32:139–148
Meshram C, Lee CC, Meshram SG, Meshram A (2020) OOS-SSS: an efficient online/offline subtree-based short signature scheme using Chebyshev chaotic maps for wireless sensor network. IEEE Access 8:80063–80073. https://doi.org/10.1109/ACCESS.2020.2991348
Meshram C, Li C-T, Meshram SG (2019) An efficient online/offline ID-based short signature procedure using extended chaotic maps. Soft Comput 23(3):747–753. https://doi.org/10.1007/s00500-018-3112-2
Meshram C, Ibrahim RW, Deng L, Shende SW, Meshram SG, Barve SK (2021) A robust smart card and remote user password-based authentication protocol using extended chaotic maps under smart cities environment. Soft Comput 25(15):10037–10051. https://doi.org/10.1007/s00500-021-05929-5
Meshram C, Obaidat MS, Meshram A (2020) An efficient robust lightweight remote user authentication protocol using extended chaotic maps. In: 2020 International Conference on Computer, Information and Telecommunication Systems (CITS), pp 1–6. https://doi.org/10.1109/CITS49457.2020.9232622
Zou L, Sun J, Gao M, Wan W, Gupta BB (2019) A novel coverless information hiding method based on the average pixel value of the sub-images. Multimed Tools Appl 78(7):7965–7980
Yu Z, Gao C, Jing Z, Gupta BB, Cai Q (2018) A practical public key encryption scheme based on learning parity with noise. IEEE Access 6:31918–31923
Yu C, Li J, Li X, Ren X, Gupta BB (2018) Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimed Tools Appl 77(4):4585–4608
Meshram C, Lee CC, Ranadive AS, Li CT, Meshram SG, Tembhurne JV (2020) A subtree-based transformation model for cryptosystem using chaotic maps under cloud computing environment for fuzzy user data sharing. Int J Commun Syst 33(7):1–15. https://doi.org/10.1002/dac.4307
Meshram C, Lee C-C, Meshram SG, Li C-T (2019) An efficient ID-based cryptographic transformation model for extended chaotic-map-based cryptosystem. Soft Comput 23(16):6937–6946. https://doi.org/10.1007/s00500-018-3332-5
Premkamal PK, Pasupuleti SK, Alphonse PJA (2020) Efficient escrow-free CP-ABE with constant size ciphertext and secret key for big data storage in cloud. Int J Cloud Appl Comput 10(1):28–45
Zheng Q, Wang X, Khan MK, Zhang W, Gupta BB, Guo W (2017) A lightweight authenticated encryption scheme based on chaotic SCML for railway cloud service. IEEE Access 6:711–722
Kumar A (2019) Design of secure image fusion technique using cloud for privacy-preserving and copyright protection. Int J Cloud Appl Comput 9(3):22–36
Meshram C, Ibrahim RW, Obaidat MS, Sadoun B, Meshram SG, Tembhurne JV (2021) An effective mobile-healthcare emerging emergency medical system using conformable chaotic maps. Soft Comput 25(14):8905–8920. https://doi.org/10.1007/s00500-021-05781-7
Poongodi M, Malviya M, Hamdi M, Vijayakumar V, Mohammed MA, Rauf HT, Al-Dhlan KA (2021) 5G based Blockchain network for authentic and ethical keyword search engine. IET Commun. https://doi.org/10.1049/cmu2.12251
Mohammed MA, Ibrahim DA, Salman AO (2021) Adaptive intelligent learning approach based on visual anti-spam email model for multi-natural language. J Intell Syst 30(1):774–792
Awan MJ et al (2021) Image-based malware classification using VGG19 network and spatial convolutional attention. Electronics 10(19):2444
Li Z, Zhao M, Jiang H, Xu Q (2019) Keyword guessing on multi-user searchable encryption. Int J High Perform Comput Netw 14(1):60–68
Gaikwad VP, Tembhurne JV, Meshram C, Lee C-C (2021) Provably secure lightweight client authentication scheme with anonymity for TMIS using chaotic hash function. J Supercomput. https://doi.org/10.1007/s11227-020-03553-y
Mason JC, Handscomb DC (2002) Chebyshev polynomials. CRC Press
Bergamo P, D’Arco P, De Santis A, Kocarev L (2005) Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans Circuits Syst I Regul Pap 52(7):1382–1393. https://doi.org/10.1109/TCSI.2005.851701
Han S, Chang E (2009) Chaotic map based key agreement with/out clock synchronization. Chaos Solitons Fract 39(3):1283–1289. https://doi.org/10.1016/j.chaos.2007.06.030
Zhang L (2008) Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fract 37(3):669–674. https://doi.org/10.1016/j.chaos.2006.09.047
Chen F, Liao X, Wong K, Han Q, Li Y (2012) Period distribution analysis of some linear maps. Commun Nonlinear Sci Numer Simul 17(10):3848–3856
Laine TP (1980) The product formula and convolution structure for the generalized Chebyshev polynomials. SIAM J Math Anal 11(1):133–146
He D, Chen Y, Chen J (2012) Cryptanalysis and improvement of an extended chaotic maps-based key agreement protocol. Nonlinear Dyn 69(3):1149–1157. https://doi.org/10.1007/s11071-012-0335-0
He D, Ma M, Zhang Y, Chen C, Bu J (2011) A strong user authentication scheme with smart cards for wireless communications. Comput Commun 34(3):367–374. https://doi.org/10.1016/j.comcom.2010.02.031
Kocher P, Jaffe J, Jun B (1999) Differential power analysis. In: Annual International Cryptology Conference, pp 388–397
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. IEEE Trans Comput 51(5):541–552
Lee C-C, Chen C-L, Wu C-Y, Huang S-Y (2012) An extended chaotic maps-based key agreement protocol with user anonymity. Nonlinear Dyn 69(1):79–87. https://doi.org/10.1007/s11071-011-0247-4
Lee C-C, Hsu C-W (2013) A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dyn 71(1):201–211. https://doi.org/10.1007/s11071-012-0652-3
Wu F, Xu L, Kumari S, Li X (2015) A novel and provably secure biometrics-based three-factor remote authentication scheme for mobile client–server networks. Comput Electr Eng 45:274–285
Secure Hash Standard, National Institute of Standards and Technology (NIST), Federal Information Processing Standards Publication. FIPS 180-4, 2015
Ibrahim MH, Kumari S, Das AK, Wazid M, Odelu V (2016) Secure anonymous mutual authentication for star two-tier wireless body area networks. Comput Methods Programs Biomed 135:37–50
Park Y, Park K, Lee K, Song H, Park Y (2017) Security analysis and enhancements of an improved multi-factor biometric authentication scheme. Int J Distrib Sens Netw 13(8):1–12
Acknowledgements
The authors would like to thank anonymous reviewers of The Journal of Supercomputing for their careful and helpful comments and extend their gratitude to the Deanship of Scientific Research at King Khalid University for funding this work through the research groups program under Grant Number R. G. P. 2/150/42. The work of Agbotiname Lucky Imoize is supported by the Nigerian Petroleum Technology Development Fund (PTDF) and the German Academic Exchange Service (DAAD) through the Nigerian-German Postgraduate Program under Grant 57473408.
Author information
Authors and Affiliations
Contributions
Conceptualization was done by CM and RWI; Formal analysis was carried out by ALI; Investigation was done by CM; RWI; and ALI; Methodology was done by CM; RWI; and SSJ; Resources were done by CM; Software was done by SGM; ALI; and SKB; Supervision was done by CM; RWI; and ALI; Validation/Visualization were carried out by CM; SSJ; and RWI; Writing—original draft were done by CM; RWI; and SSJ; Writing—review and editing were carried out by CM; RWI; SSJ; SGM; ALI; and SKB.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Meshram, C., Ibrahim, R.W., Meshram, S.G. et al. An efficient remote user authentication with key agreement procedure based on convolution-Chebyshev chaotic maps using biometric. J Supercomput 78, 12792–12814 (2022). https://doi.org/10.1007/s11227-021-04280-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-021-04280-8