Abstract
Telecare medicine information system (TMIS) is recognized as an important tool for improving the quality and protection of healthcare services. In addition to protecting the privacy of patients, many authentication techniques are being introduced in TMIS. After investigations, it is observed that many authentication techniques have security breaches. In this article, we propose an efficient, secure and lightweight authentication scheme for TMIS using chaotic hash function to achieve user anonymity. Chaotic hash function constitutes potential security a set in modern cryptography with its random behavior. Also, we provide the security proof in the random oracle (RO) model and proof of correctness of algorithm is presented using (Burrows–Abadi–Needham) BAN logic for proposed scheme. The comprehensive formal and informal security review demonstrate that the security of our scheme is resistive against known potential attacks. Additionally, our presented authentication scheme performs significantly better as compared to other existing schemes in the literature and also it is efficient on the basis on high security and low cost for computational and communication.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
With the advent of various computing resources and storage media, the large amount of data is generated by the different applications over the public communication network. Today, variety of data is available on our finger tips such as social media, stock market, finance, medical and healthcare, etc. All these data are very crucial and vital for any organization. Therefore, the challenge is to keep these data protected since the data movement is over the public network. In this article, we target the security and privacy of data generated by e-healthcare which is maintained on TMIS. The TMIS is designed to make it easier for patients to provide different healthcare services effortlessly. The main objective of TMIS is to store the medical data such as patient information, disease information, medical history and very important electronic medical records (EMRs) of patients, etc. This health information is vital to the patients, physicians, medical practitioner and hospitals. Using TMIS, patient at remote or distant location can post and get healthcare data or services over the public network. So, this system facilitates the patients in saving time and related expenses incurred in attaining the hospital physically. But, preserving patient’s security and privacy over public network is the challenging task. Also, physicians or doctors can monitor the patients to investigate or suggest healthcare services on need or demand. Due to superior facilities in telecommunication, wireless and mobile communication enriches the quality services in medical domain. Thus, we need strong mechanism to prevent unauthorized access of data, protection against EMRs confidentiality, and better availability of medical system. The efficient authentication mechanism is desired to protect against integrity, security, and authenticity of data transmitted over public network for TMIS. Hence, the main objective of this work is to propose a secure authentication scheme to preserve the user anonymity over public communication channel for TMIS. Moreover, detailed security analysis and security proofs is investigated to verify the security of propose scheme for different types of attacks.
In the literature, various authentication schemes are presented to ensure integrity, security, authenticity, and confidentiality. The early smart card and password authentication scheme has several advantages, i.e., smart card design protects against tamper resistance which is demonstrated in [1,2,3,4,5,6,7,8]. An authentication scheme based on passwords for TMIS is presented [9] wherein the scheme is efficient because of avoiding costlier computation of exponentiation as well as protects against a variety of attacks includes; stolen-verifier, guessing off-line/on-line password attack, and replay attack, etc. Furthermore, an impersonation attack is identified in [9], to overcome this attack for mobile devices (low power) in TMIS environment is illustrated in [10]. In [11], an authentication technique using dynamic ID for TMIS is proposed which suffers from user anonymity and password stolen attacks. Thus, improved dynamic ID-based schemes are designed [12,13,14] which is prevailing the attacks in [11].
Lee et al. in 2013 presented a secure authentication scheme based on password for smart cards in integrated electronic patient record (EPR) system [15]. Later, [16, 17] identified the security breach in [15], i.e., replay attack, stolen verifier attack, stolen smart card attack, impersonation attack, and presented more secure authentication schemes to resolve all the issues in [15]. In 2014, He et al. [2] formulated new authentication technique based on elliptic curve cryptography (ECC) and RFID using ID verifier wherein it overcomes the drawbacks of previous schemes. Moreover, performance measures are analyzed based on storage needed, and computation and communication cost. Similarly, ECC-based RFID [18] authentication review is presented to analyze the security and performance in healthcare environment using Internet of Things (IoTs).
1.1 Contribution
From the above findings and investigation, we need a robust and secure authentication scheme for TMIS. Hence, we present the various targeted contributions in this article for the proposal of new authentication scheme. The contributions are listed as follows:
-
1.
To propose an efficient scheme for lightweight and secure client authentication for TMIS using subtree under fuzzy user’s data sharing environments with anonymity. The proposed scheme utilizes one-way chaotic hash function which is secure and collision-resistant, and bitwise XOR operation.
-
2.
To present security proofs in RO model and proof of correctness using BAN logic.
-
3.
Our new scheme is client-friendly, i.e., it provides the client with the power to directly modify/update their password and personal biometric key without contacting to base station.
-
4.
To present thorough security examinations which includes: formal analysis and an informal investigation. Hence, the verification of proposed scheme is investigated for different attacks.
1.2 Road map of the article
In Sect. 2, we present the literature review related to authentication schemes in TMIS. In Sect. 3, we present the background material, concept of chaotic hash function, and attacker model. Section 4 demonstrates the complete details of proposed scheme for TMIS. The analysis of security for proposed scheme in TMIS is discussed in Sect. 5. Section 6 shows the performance comparison, and conclusions are highlighted in Sect. 7.
2 Related Works
Security and privacy of patient is the main concern in TMIS environment. To access healthcare services remotely, authentication of TMIS server and verification of patient is required. Lu et al. [19] presented a three-factor authentication method using biometric for TMIS, but after investigations it is found that the method is vulnerable to different attacks. In addition, patient untraceability is also not supported by the proposed method. In [20,21,22], vulnerabilities pointed in Lu et al. [19] are addressed and an improved biometric authentication schemes using ECC is implemented which is efficient against various attacks. Moreover, various techniques have been adopted in the literature to propose a robust and efficient authentication scheme that utilizes symmetric key [23], RSA [24], and key agreement [25] for TMIS.
Subsequently, numerous schemes were proposed to work against different attacks on TMIS. Maintaining the secrecy, authentication, and secure access to healthcare data is the challenging task in public network. A survey presented in [26] enriches to understand the applicability of authentication schemes toward security and respective vulnerabilities against various attacks. The authentication is needed in various systems wherein important data are stored via public network. Hence, the two-factor authentication [27] method used for healthcare under wireless medical sensor networks, three-factor authentication [28] in smart city and multi-server setting [29], password-based [30] and certificateless aggregate signature [31] authentication for vehicular ad hoc network (VANET), end-to-end authentication [32] in wearable devices for monitoring health, key agreement [33] authentication in cloud for cyber-physical systems, and 3-factor authentication [34] for satellite communications were proposed.
In recent, secure and efficient authentication schemes are proposed to address the various attacks in TMIS. Wei et al. [35] highlighted that how 3-factor authentication preserves the privacy and maintain the security. In [36], another 3-factor authentication for preserving user anonymity using extended ECC is proposed; moreover, the verification of security for proposed scheme is presented using formal and informal ways. Authentication scheme using smart card to overcome an attack such as mutual authentication, user anonymity and secrecy is illustrated by Radhakrishnan et al. [37]. The authors fixed the shortcomings of Lee et al. [15] scheme for TMIS. Furthermore, an authentication based on TMIS developed in [38] is adopted to remove the drawbacks of [39], the vulnerabilities pointed to resolves are guessing password, server spoofing, and extraction of biometric parameter. Nevertheless, the more improved 3-factor authentication [40, 41] and authentication using key agreement [42, 43] are the major breakthrough witnessed in the field of TMIS authentication.
Most recently, in 2020, Dharminder et al. [44] proposed a RSA-based TMIS authentication scheme which targets to resolve the shortcomings of Radhakrishnan et al., and provide the generalized authentication scheme. Lastly, Lo et al. [45] performed the security analysis toward to facilitate the scheme to allow off-line password change. Herein, author has overcome the issues identified in [46].
The above literature review motivates to design new authentication scheme for TMIS to offer various security features. After investigating the existing schemes for TMIS, we found that the TMIS is vulnerable to different security attacks and health information can be stolen. So, to protect the health information from different attacks, we need secure and lightweight authentication scheme for TMIS. In this paper, we present a secure authentication scheme for subtree-based fuzzy user environment, adopting the concept of chaotic hash function to accomplish user anonymity.
3 Background material
In this section, we briefly familiarizes the notations used in our propose authentication scheme, attacker model and the basic concept of Chaotic hash function as well as some related mathematical points.
3.1 Notations
A client authentication scheme with anonymity for TMIS is a novel cryptographic primitive for fuzzy-entity data sharing. Let us see how some notations are defined, because these notations will be used in our new scheme.
For simplicity, we use [x, y] for the shorthand of \(\left\{x, x+1, \ldots,y \right\}\) and [x] for [1, x]. For every \(\fancyscript{i}\fancyscript{d} =({\fancyscript{i}\fancyscript{d}}_{1},{\fancyscript{i}\fancyscript{d}}_{2},\ldots,{\fancyscript{i}\fancyscript{d}}_{\fancyscript{k}})\), where \(\fancyscript{i}\fancyscript{d}\) is an identity vector, let \({S}_{\fancyscript{i}\fancyscript{d}}=\{{\fancyscript{i}\fancyscript{d}}_{1},\ldots,{\fancyscript{i}\fancyscript{d}}_{\fancyscript{k}}\}\) is the set of \((\fancyscript{i}\fancyscript{d})\). The \(\fancyscript{i}\fancyscript{d}\)’s location record in a tree is defined by \({I}_{\fancyscript{i}\fancyscript{d}} =\left\{i; {\fancyscript{i}\fancyscript{d}}_{i} \in {S}_{\fancyscript{i}\fancyscript{d}}\right\}\). Identified receivers formulate a subtree which is related to tree-based encryption technique [47,48,49,50]. The \(\fancyscript{i}\fancyscript{d}\) and respective places of receivers are joined into \({\mathbb{T}}\). The legitimate \({\mathbb{T}}\) must cover the root node. From this, we depict that the structure is managed by PKG. Similarly, identity set of \({\mathbb{T}}\) and location indices of \({\mathbb{T}}\) are expressed by \({S}_{\mathbb{T}}={\cup}_{\fancyscript{i}\fancyscript{d}\in {\mathbb{T}}}{S}_{\fancyscript{i}\fancyscript{d}}\) and \({I}_{\fancyscript{i}\fancyscript{d}} =\{i; {\fancyscript{i}\fancyscript{d}}_{i} \in {S}_{\mathbb{T}}\}\), respectively. The symbolizations here can be expressed as \({\rm Sup}(\fancyscript{i}\fancyscript{d})=\{({\fancyscript{i}\fancyscript{d}}_{1},{\fancyscript{i}\fancyscript{d}}_{2},\ldots,{\fancyscript{i}\fancyscript{d}}_{{\fancyscript{k}}^{\prime}}); {\fancyscript{k}}^{\prime} \le \fancyscript{k}\}\) to indicate the superiority of \(\fancyscript{i}\fancyscript{d} =({\fancyscript{i}\fancyscript{d}}_{1},{\fancyscript{i}\fancyscript{d}}_{2},\ldots,{\fancyscript{i}\fancyscript{d}}_{\fancyscript{k}})\). Subtree, \({\mathbb{T}}\)'s predictable receivers are categorized as \({\rm Sup} ({\mathbb{T}})= {\cup}_{\fancyscript{i}\fancyscript{d}\in {\mathbb{T}}} {\rm Sup} (\fancyscript{i}\fancyscript{d})\).
The presented symbolizations are found to be appropriate for proposed client authentication scheme based on subtree. Suppose that the users are structured as shown in Fig. 1 in a tree structure. The \({S}_{\fancyscript{i}\fancyscript{d}} =\left\{\mathcal{B},\mathcal{F}\right\}\) and \({I}_{\fancyscript{i}\fancyscript{d}} =\left\{2, 6\right\}\) are used to specify a known user with \(\fancyscript{i}\fancyscript{d} =\left(\mathcal{B},\mathcal{F}\right)\). The \({\rm Sup} \left(\fancyscript{i}\fancyscript{d}\right)=\left\{\left(\mathcal{B}\right), \left(\mathcal{B},\mathcal{F}\right)\right\}\), a set is created by the user involving superiors of him/her. When message is send by the data owner to the receivers set in a subtree, i.e., \({\mathbb{T}} =\left\{\left(\mathcal{A}\right)\left(\mathcal{B},\mathcal{F}\right), \left(\mathcal{B},\mathcal{G}\right)\right\}\), then \({\mathbb{T}}\)'s identity set is denoted by \({S}_{\mathbb{T}} =\left\{\mathcal{A},\mathcal{B},\mathcal{F},\mathcal{G}\right\}\), and \({\mathbb{T}}\)'s position indices are represented by \({I}_{\mathbb{T}}=\{1, 2, 6, 7\}\), whereas superiors of \({\mathbb{T}}\)'s are expressed by \({\rm Sup}({\mathbb{T}}) = \{\left(\mathcal{A}\right), \left(\mathcal{B}\right),\left(\mathcal{B},\mathcal{F}\right), \left(\mathcal{B}, \mathcal{G}\right) \}\), we see user agreement toward data owner is conveyed.
3.2 Chaotic hash function
Chaotic hash function is a one-dimensional and piece-wise linear map [47,48,49,50,51,52], expressed as follows:
where the control parameter are \({\fancyscript{y}}_{i}\in [0, 1]\) and \(\gamma \in (0, 0.5)\). The parameter \(\gamma \) in \({\fancyscript{y}}_{i+1}\) guarantees the operation of map under chaotic state on utilizing \(0<\gamma <0.5\). The self-transformation of map is performed at \({[}0, 1{]}\), containing only a parameter \(\gamma \). Chaining variables \({\fancyscript{y}}_{0}\) and \({\fancyscript{y}}_{i}\) are used initially for the transformation, these chaining variables are the indicators in an algorithm for one-way hash.
3.3 Model for attacker
The insecure channel is chosen for the experimentation of authentication scheme proposed in this article. We assume following capabilities an adversary can hold. The valid assumptions are listed as follows:
-
1.
An adversary can extract information from smart card by power consumption monitoring [53, 54], when smart card is lost or stolen.
-
2.
Messages transmitted among the entities through public channel can be eavesdropped by an adversary.
-
3.
Eavesdrop messages can be updated and resend, and reroute by an adversary (Table 1).
4 Proposed scheme
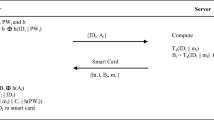
Here, we present an anonymity preserving efficient authentication scheme for TMIS. The scheme is protective against different security breaches, even though smart card is compromised. The identified phases of operations in the proposed scheme are similar to the related existing schemes, i.e., registration phase, login phase, verification phase, and password change phase. Detail description of proposed scheme is presented as follows and same is shown in Fig. 2.
4.1 Registration phase
Step 1: \({\mathcal{C}}_{\fancyscript{i}}\) chooses his identity, \({\fancyscript{i}\fancyscript{d}}_{i}\in {\rm Sup} \left({\mathbb{T}}\right)\), password \({\fancyscript{p}\fancyscript{w}}_{i}\), and random number \({\kappa}_{i}\), and computes \(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}= {\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right).{\mathcal{C}}_{\fancyscript{i}}\), sends the registration request \(\{{\fancyscript{i}\fancyscript{d}}_{i}, \overline{{\fancyscript{p}\fancyscript{w}}_{i}}\}\) over a secure channel.
Step 2: Once the registration request is received, \({\mathcal{S}}_{\fancyscript{j}}\) checks the \({\fancyscript{i}\fancyscript{d}}_{i}\)’s prescribed format and if \({\fancyscript{i}\fancyscript{d}}_{i}\) is invalid, registration request is aborted. Otherwise, \({\mathcal{S}}_{\fancyscript{j}}\) computes:
-
\({\mathcal{J}}_{i} = {\fancyscript{h}}_{\varsigma}(\fancyscript{s}\fancyscript{k}||{\fancyscript{i}\fancyscript{d}}_{i})\),
-
\({\mathcal{D}}_{i}= {\mathcal{J}}_{i} \oplus \overline{{\fancyscript{p}\fancyscript{w}}_{i}},\)
-
\(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} = {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||\overline{\fancyscript{p}\fancyscript{w}_i}||{\mathcal{J}}_{i}),\)
-
\({\mathcal{X}}_{i} = {\fancyscript{h}}_{\varsigma}(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||\fancyscript{s}\fancyscript{k}) \oplus \overline{{\fancyscript{p}\fancyscript{w}}_{i}}.\)
Finally, \({\mathcal{S}}_{\fancyscript{j}}\) stores \(({\mathcal{D}}_{i},\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime},{\fancyscript{h}}_{\varsigma}(.))\) on smart card and securely sends the smart card to \({\mathcal{C}}_{\fancyscript{i}}\). \({\mathcal{S}}_{\fancyscript{j}}\) stores \((\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime},{\mathcal{X}}_{i}, bit)\) bit \(0\backslash 1\). Whenever \(bit = 1\), which means the user is logged to the system, otherwise, \(bit = 0\).
Step 3: On an arrival of smart card \((SC)\), \(\mathcal{W} = {\kappa}_{i} \oplus {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||{\fancyscript{p}\fancyscript{w}}_{i})\) is computed by the user and \(\mathcal{W}\) is inserted on smart card. Lastly, \(\{{\mathcal{D}}_{i}, \mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}, {\fancyscript{h}}_{\varsigma}(.), \mathcal{W}\}\) is preserved on smart card.
4.2 Login phase
If \({\mathcal{C}}_{\fancyscript{i}}\) wants to access EMR data from TMIS system then \({\mathcal{C}}_{\fancyscript{i}}\) need to logon by inserting smart card into the authenticating device, and need to supply \({\fancyscript{i}\fancyscript{d}}_{i}\) and \({\fancyscript{p}\fancyscript{w}}_{i}\). The following computation is performed by the smart card at the time of login into the server. Figure 1 shows the steps of login phase as well as authentication phase.
-
\({\kappa}_{i} =\mathcal{W} \oplus {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||{\fancyscript{p}\fancyscript{w}}_{i})\),
-
\(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}= {\fancyscript{h}}_{\varsigma}({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i})\),
-
\({\mathcal{J}}_{i} ={\mathcal{D}}_{i}\oplus \overline{{\fancyscript{p}\fancyscript{w}}_{i}}= {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||\fancyscript{s}\fancyscript{k})\),
-
\(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime\prime} = {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{J}}_{i})\).
The SC compares \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime\prime}\) and \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}\). If \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{^{\prime\prime}}=\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}\) then inserted \({\fancyscript{i}\fancyscript{d}}_{i}\), and \({\fancyscript{p}\fancyscript{w}}_{i}\) are valid. Otherwise, session is terminated by SC. Therefore, computations performed by SC are
-
\({\mathcal{F}}_{i}= {\fancyscript{h}}_{\varsigma}({\mathcal{J}}_{i}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime})\),
-
\({\mathcal{Y}}_{i}= {\fancyscript{h}}_{\varsigma}(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}) \oplus {\fancyscript{i}\fancyscript{d}}_{i},\)
-
\({\mathcal{U}}_{i} = {\fancyscript{h}}_{\varsigma}(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{F}}_{i}||{\tau}_{1}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i})\).
The SC determined the current timestamp \({\tau}_{1}\) and \({\mathcal{C}}_{\fancyscript{i}}\) sends his/her login request \(\{{\tau}_{1}, {\mathcal{U}}_{i}, {\mathcal{Y}}_{i}\}\) to \({\mathcal{S}}_{\fancyscript{j}}\) (medical server) via public channel.
4.3 Verification phase
If \({\mathcal{C}}_{\fancyscript{i}}\)’s login request \(\{{\tau}_{1}, {\mathcal{U}}_{i}, {\mathcal{Y}}_{i}\}\) is received by \({\mathcal{S}}_{\fancyscript{j}}\), following steps are performed by \({\mathcal{C}}_{\fancyscript{i}}\) and \({\mathcal{S}}_{\fancyscript{j}}\) confirms agreement for session-key and mutual authentication.
Step 1: At timestamp \({\tau}_{2}\), \({\mathcal{S}}_{\fancyscript{j}}\) checks if \(({\tau}_{2}-{\tau}_{1})>\Delta \tau \), then login request is rejected by \({\mathcal{S}}_{\fancyscript{j}}\) otherwise it computes the following. Here, \(\Delta \tau \) represents transmission delay maximum time.
-
\(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}\) = \({\mathcal{X}}_{i}\) ⊕ \({\fancyscript{h}}_{\varsigma}(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime\prime}||\fancyscript{s}\fancyscript{k})\),
-
\({\fancyscript{i}\fancyscript{d}}_{i} = {\mathcal{Y}}_{i}\oplus {\fancyscript{h}}_{\varsigma}(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}),\)
-
\({\mathcal{J}}_{i} = {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||\fancyscript{s}\fancyscript{k}),\)
-
\({\mathcal{F}}_{i}^{\prime}= {\fancyscript{h}}_{\varsigma}({\mathcal{J}}_{i}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}),\)
-
\({\mathcal{U}}_{i}^{\prime} = {\fancyscript{h}}_{\varsigma}(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{F}}_{i}^{\prime}||{\tau}_{1}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i}).\)
\(\mathcal{S}\) compares \({\mathcal{U}}_{i}^{\prime}\) and \({\mathcal{U}}_{i}\), if \({\mathcal{U}}_{i}^{\prime}\ne {\mathcal{U}}_{i}\) then, session is terminated by \(\mathcal{S}\); otherwise, \(\mathcal{C}\) declare to be legitimate user.
Step 2: Random number \({\kappa}_{s}\) is generated by \(\mathcal{S}\) and perform the following computations.
-
\(\zeta = {\fancyscript{h}}_{\varsigma}({\kappa}_{s}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{F}}_{i}^{\prime})\),
-
\({\mathcal{H}}_{1} = {\fancyscript{h}}_{\varsigma}(\zeta ||{\kappa}_{s}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\tau}_{3})\),
-
\(\mu = {\kappa}_{s} \oplus {\mathcal{F}}_{i}^{\prime}\).
Step 3: Response message \(\{\mu, {\mathcal{H}}_{1}, {\tau}_{3}\}\) is sent to \({\mathcal{C}}_{\fancyscript{i}}\) by \(\mathcal{S}\) via public channel.
Step 4: After receiving response message \(\left\{\mu, {\mathcal{H}}_{1}, {\tau}_{3}\right\}\) from server \(\mathcal{S}\), \({\mathcal{C}}_{\fancyscript{i}}\) computes.
-
\({\kappa}_{s} = {\kappa}_{s} \oplus {\mathcal{F}}_{i}\oplus {\mathcal{F}}_{i}^{\prime},\)
-
\(\zeta = {\fancyscript{h}}_{\varsigma}({\kappa}_{s}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{F}}_{i}),\)
-
\({\mathcal{H}}_{1}^{\prime}={\fancyscript{h}}_{\varsigma}(\zeta ||{\kappa}_{s}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\tau}_{3}).\)
\({\mathcal{C}}_{\fancyscript{i}}\) compares \({\mathcal{H}}_{1}^{\prime}\) and \({\mathcal{H}}_{1}\). If \({\mathcal{H}}_{1}^{\prime}\) = \({\mathcal{H}}_{1}\) then, authentication of \(\mathcal{S}\) and \(\zeta \) is performed; Otherwise, session is terminated. \({\mathcal{C}}_{\fancyscript{i}}\) computes, \({\mathcal{H}}_{2} = {\fancyscript{h}}_{\varsigma}(\zeta)\) and \({\mathcal{H}}_{2}\) is sent to user.
Step 5: \(\mathcal{S}\) computes \({\mathcal{H}}_{2}^{\prime} = {\fancyscript{h}}_{\varsigma}(\zeta)\) and checks \({\mathcal{H}}_{2}^{\prime}= {\mathcal{H}}_{2}\), If valid session key is hold by \(\mathcal{S}\).
4.4 Password change phase
It is always a good practice that the client \({\mathcal{C}}_{\fancyscript{i}}\) should regularly change her/his password in order to improve protection. Assume that the client \({\mathcal{C}}_{\fancyscript{i}}\) wants to change her/his original password \({\fancyscript{p}\fancyscript{w}}_{i}\) by a new changed password \({\fancyscript{p}\fancyscript{w}}_{{i}_{{\rm new}}}\). To offer more security, password \({\fancyscript{p}\fancyscript{w}}_{i}\) change is allowed to \({\mathcal{C}}_{\fancyscript{i}}\) and new password \(({\fancyscript{p}\fancyscript{w}}_{{i}_{{\rm new}}})\) can be set. To do so, \({\mathcal{C}}_{\fancyscript{i}}\) inserts SC into an authenticating terminal, and then SC update password to \({\fancyscript{p}\fancyscript{w}}_{{i}_{{\rm new}}}\) by performing following steps.
-
1.
random number \({\kappa}_{i}\) as \({\kappa}_{i} =\mathcal{W} \oplus {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|{\fancyscript{p}\fancyscript{w}}_{i}\right)\) is retrieved by SC and computes
-
\(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}={\fancyscript{h}}_{\varsigma}({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}), \)
-
\({\mathcal{J}}_{i} ={\mathcal{D}}_{i}\oplus \overline{{\fancyscript{p}\fancyscript{w}}_{i}}= {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||\fancyscript{s}\fancyscript{k})\),
-
\(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime\prime} = {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{J}}_{i})\)
SC checks for the equality of \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}\boldsymbol{^{\prime}}}\) and \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}}\). If \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}\boldsymbol{^{\prime}}} \ne \mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}}\) then, no password update performed by SC. Otherwise, inserted \({\fancyscript{i}\fancyscript{d}}_{i}\) and \({\fancyscript{p}\fancyscript{w}}_{i}\) are correct and hence new password is entered by \({\mathcal{C}}_{\fancyscript{i}}\) on asking SC.
-
-
2.
\({\mathcal{C}}_{\fancyscript{i}}\) enters a new password \({\fancyscript{p}\fancyscript{w}}_{{i}_{{\rm new}}}\). Later, SC computes
-
\({\overline{\fancyscript{p}\fancyscript{w}}}_{{i}_{{\rm new}}}={\fancyscript{h}}_{\varsigma}({\fancyscript{p}\fancyscript{w}}_{{i}_{{\rm new}}}\oplus {\kappa}_{i})\),
-
\({\mathcal{N}\fancyscript{i}\fancyscript{d}}_{{i}_{{\rm new}}}^{\prime}= {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||{\overline{\fancyscript{p}\fancyscript{w}}}_{{i}_{{\rm new}}})\),
-
\({\mathcal{W}}_{{\rm new}} = {\kappa}_{i} \oplus {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||{\fancyscript{p}\fancyscript{w}}_{{i}_{{\rm new}}})\),
-
\({\mathcal{D}}_{{\rm new}}= {\mathcal{D}}_{i}\oplus {\overline{\fancyscript{p}\fancyscript{w}}}_{{i}_{{\rm new}}} \oplus \overline{\fancyscript{p}\fancyscript{w}_i}.\)
-
Finally, SC replaces \({\mathcal{D}}_{{\rm new}}\), \({\mathcal{W}}_{{\rm new}},\) and \({\mathcal{N}\fancyscript{i}\fancyscript{d}}_{{i}_{{\rm new}}}^{\prime}\) instead of \({\mathcal{D}}_{i}, \mathcal{W}\), and \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}}\), respectively. Here, random number \({\kappa}_{i}\) can be changed by \({\mathcal{C}}_{\fancyscript{i}}.\)
5 Security Analysis
This section is devoted to show the security proof of proposed scheme in RO model. Subsequently, the proof of correctness is also presented using BAN [55] logic for the same.
5.1 Formal security analysis
Here, RO model is utilized to propose the formal security analysis related to proposed scheme.
Definition 1
Secure and collision-resistant hash function based on chaotic maps [56].
It \({Adv}_{\mathcal{A}}^{CHASH}\left(t\right)\) denotes an adversary (attacker), then finding collision in chaotic hash function \({\fancyscript{h}}_{\varsigma}\left(.\right)\) is an advantage to adversary \(\mathcal{A}\) is as follows:
Probability of occurrence of \(E\) is \(Pr[E]\) in random space, and \((\fancyscript{z},{\fancyscript{z}}^{*})\Leftarrow A\) indicate that \((\fancyscript{z},{\fancyscript{z}}^{*})\) is chosen by \(\mathcal{A}\) randomly. If \(\varepsilon >0\) then chaotic hash function resists the collision, we have \({Adv}_{\mathcal{A}}^{CHASH}\left(t\right)\le \varepsilon \).
Following RO is chosen for formal security analysis of proposed scheme:
Reveal
String \(\fancyscript{z}\) is produced by the oracle unconditionally from the respective \(\fancyscript{y}={\fancyscript{h}}_{\varsigma}(\fancyscript{z})\) (chaotic hash value).
The formal security is offered by the Theorems 1 and 2, respectively, for proposed scheme which is protective against any adversary.
Theorem 1
One-way chaotic hash function \({\fancyscript{h}}_{\varsigma}\left(.\right)\) assumed to be an oracle, so proposed scheme is secure against the authenticate user’s (\({\mathcal{C}}_{\fancyscript{i}}\)) identity (\({\fancyscript{i}\fancyscript{d}}_{i}\)), server’s (\({\mathcal{S}}_{\fancyscript{j}}\)) private key (\(\fancyscript{s}\fancyscript{k}\)) and \({\mathcal{C}}_{\fancyscript{i}}\), \({\mathcal{S}}_{\fancyscript{j}}\) session key \(\zeta \).
Proof
We assume that \(\mathcal{A}\) has the capability to extract \({\fancyscript{i}\fancyscript{d}}_{i}\) of \({\mathcal{C}}_{\fancyscript{i}}\) (legitimate user), \(\fancyscript{s}\fancyscript{k}\) (private key) of \({\mathcal{S}}_{\fancyscript{j}}\) (server), and \(\zeta \) (session key) between \({\mathcal{C}}_{\fancyscript{i}}\) and \({\mathcal{S}}_{\fancyscript{j}}\). The \(\mathcal{A}\) utilizes Reveal oracle to execute \({\mathrm{EXP}1}_{\mathrm{SAKTMIS}}^{CHASH}\) (experimental algorithm) for proposed key agreement authentication based on biometric in multi-server environment, i.e., SAK-TMIS, which is presented in Algorithm 1.
Success probability, \({Succ1}_{\mathrm{SAKTMIS}}^{CHASH} =[\mathrm{Pr}[{\mathrm{EXP}1}_{\mathrm{SAKTMIS}}^{CHASH}=1]-1]\) is described for \({\mathrm{EXP}1}_{\mathrm{SAKTMIS}}^{CHASH}\). Then the advantage becomes \({Adv}_{\mathrm{SAKTMIS}}^{CHASH}\left({\fancyscript{t}}_{1},{\fancyscript{q}}_{\mathcal{R}}\right)= {max}_{A}\{{Succ1}_{\mathrm{SAKTMIS}}^{CHASH}\}\), Advantage function using \(\fancyscript{t}\) (execution time) and \({\fancyscript{q}}_{\mathcal{R}}\) (No. of RO reveal queries) is maximized on \(\mathcal{A}\). If \({Adv}_{\mathrm{SAKTMIS}}^{CHASH}\left({\fancyscript{t}}_{1},{\fancyscript{q}}_{\mathcal{R}}\right)<\varepsilon \), for smaller \(\varepsilon >0\) then we declare proposed scheme is protective to \(\mathcal{A}\) while trying to extract \({\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}\) , \(\fancyscript{s}\fancyscript{k}\) and \(\zeta \).
Experiment on Algorithm 1
If \(\mathcal{A}\) is capable to invert \({\fancyscript{h}}_{\varsigma}\left(.\right)\) (hash function), then \(\mathcal{A}\) wins the game by having \({\fancyscript{i}\fancyscript{d}}_{i}\), \(\fancyscript{s}\fancyscript{k}\) and \(\zeta \). However, it is hard to invert as per Definition 1, moreover, to invert \({\fancyscript{h}}_{\varsigma}\left(.\right)\) the problem is computationally not feasible. Since \({Adv}_{A}^{CHASH}\left(\fancyscript{t}\right)\le \varepsilon \), for smaller \(\varepsilon >0\), we have \({Adv}_{A}^{CHASH}\left({\fancyscript{t}}_{1},{\fancyscript{q}}_{\mathcal{R}}\right)\le \varepsilon \), which is does not depend on the earlier. Therefore, proposed scheme is fully protective against \(\mathcal{A}\) while extracting \({\fancyscript{i}\fancyscript{d}}_{i}\), \(\fancyscript{s}\fancyscript{k}\) and \(\zeta \).
Algorithm 1. \({\mathbf{E}\mathbf{X}\mathbf{P}1}_{\mathrm{SAKTMIS}}^{{\varvec{C}}{\varvec{H}}{\varvec{A}}{\varvec{S}}{\varvec{H}}}\) | |
|---|---|
1: Message of login request is eavesdropped \(\{{\tau }_{1}, {\mathcal{U}}_{i}, {\mathcal{Y}}_{i}\}\) at the time of login phase, here \({\mathcal{U}}_{i} = {\fancyscript{h}}_{\varsigma }(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{F}}_{i}||{\tau }_{1}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i}), {\mathcal{Y}}_{i}= {\fancyscript{h}}_{\varsigma }(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}) \oplus {\fancyscript{i}\fancyscript{d}}_{i}, \overline{{\fancyscript{p}\fancyscript{w}}_{i}}= {\fancyscript{h}}_{\varsigma }({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa }_{i}),{\mathcal{F}}_{i}= {\fancyscript{h}}_{\varsigma }({\mathcal{J}}_{i}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}), \mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime\prime} = {\fancyscript{h}}_{\varsigma }({\fancyscript{i}\fancyscript{d}}_{i}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{J}}_{i}),\) 2. Reveal oracle is called on input \({\mathcal{U}}_{i}\) to extract \({\fancyscript{i}\fancyscript{d}}_{i}\),\({\mathcal{F}}_{i}{\mathcal{Y}}_{i}\),\(\overline{{\fancyscript{p}\fancyscript{w}}_{i}},\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i},{\tau }_{1}\) as \((\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}\left|\left|{\overline{{\fancyscript{p}\fancyscript{w}}_{i}}}^{\prime}\right|\right|{\mathcal{F}}_{i}^{\prime}||{\tau }_{1}^{\prime}||{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\mathcal{Y}}_{i}^{\prime})\leftarrow reveal ({\mathcal{U}}_{i})\) 3. computes \({\mathcal{Y}}_{i}^{\prime}={{\fancyscript{i}\fancyscript{d}}_{i}}^{\prime}\oplus {\fancyscript{h}}_{\varsigma }\)(\({\overline{{\fancyscript{p}\fancyscript{w}}_{i}}}^{\prime}\)) 4. If \(({\mathcal{Y}}_{i}^{\prime}= {\mathcal{Y}}_{i})\) then 5. Accepted, \({\fancyscript{i}\fancyscript{d}}_{i}^{\prime}\) is the correct \({\fancyscript{i}\fancyscript{d}}_{i}\) of user 6. Authentication message is eavesdropped \((\mu , {\mathcal{H}}_{1}, {\tau }_{3})\) during the authentication phase, where \({\mathcal{H}}_{1} = {\fancyscript{h}}_{\varsigma }(\zeta ||{\kappa }_{s}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\tau }_{3}),\mu = {\kappa }_{s} \oplus {\mathcal{F}}_{i}^{\prime},{\mathcal{J}}_{i} = {\fancyscript{h}}_{\varsigma }({\fancyscript{i}\fancyscript{d}}_{i}||\mathcal{s}\fancyscript{k})\) 7. Reveal oracle is called on input \({\mathcal{H}}_{2}\) to extract \(\zeta \), \({\kappa }_{s}\),\(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}\), \({\fancyscript{i}\fancyscript{d}}_{i}\),\({\mathcal{J}}_{i}\), \({\tau }_{3}\) as \(({\zeta }^{\prime}||{{\kappa }_{s}}^{\prime}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\mathcal{J}}_{i}^{\prime}||{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\tau }_{3}^{\prime})\leftarrow reveal ({\mathcal{H}}_{1})\) 8. Reveal oracle is called on input \(\mathcal{b}\) to extract \(\mathcal{s}\fancyscript{k}\)(private key) of \(\mathcal{S}\) (server) as \(({\fancyscript{i}\fancyscript{d}}_{i}|\mathcal{s}\fancyscript{k})\leftarrow {\bf reveal} ({\mathcal{J}}_{i})\) 9. Calculates \({\zeta }^{\prime\prime}= {\fancyscript{h}}_{\varsigma }\)(\({\kappa }_{s}^{\prime}||{\mathcal{J}}_{i}^{\prime}||{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\mathcal{F}}_{i}^{\prime}\)), \({\mathcal{H}}_{1}^{\prime\prime}\) = \({\fancyscript{h}}_{\varsigma }\) (\({\zeta }^{\prime}||{\kappa }_{s}^{\prime}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}|{\mathcal{J}}_{i}^{\prime}||{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\tau }_{3}^{\prime}\)) 10. If \(({\mathcal{H}}_{1}^{\prime}= {\mathcal{H}}_{1}^{\prime\prime})\) than 11. Correct identity \({\fancyscript{i}\fancyscript{d}}_{i}\) (user) is accepted as \({\fancyscript{i}\fancyscript{d}}_{i}\) , \(\fancyscript{z}\), and \(\zeta \) , \(\mathcal{s}\fancyscript{k}\) (private key) of \(\mathcal{S}\) (server), and \(\zeta \) (session key) among \({\mathcal{C}}_{\fancyscript{i}}\) and \({\mathcal{S}}_{\mathcal{j}}\) , respectively. return 1 (i.e., Success) 12: else 13: return 0 (i.e., Failure) 14: end if 15: else 16: return 0 (i.e., Failure) | |
Theorem 2
One-way chaotic hash function \({\fancyscript{h}}_{\varsigma}\left(.\right)\) assumed to be an oracle, the proposed scheme stands protective against \(\mathcal{A}\) for extracting \({\fancyscript{p}\fancyscript{w}}_{i}\) (password) of \({\mathcal{C}}_{\fancyscript{i}}\) (user), in the situation of smart card (\({\mathcal{C}}_{\fancyscript{i}}^{\prime}s\)) lost or stolen by \(\mathcal{A}\).
Proof
We assume that \(\mathcal{A}\) has the capability to extract \({\fancyscript{p}\fancyscript{w}}_{i}\) of \({\mathcal{C}}_{\fancyscript{i}}\) (user), the extracted information is stored on smart card of \({\mathcal{C}}_{\fancyscript{i}}\). So, experiment \({\mathrm{EXP}2}_{\mathrm{SAKTMIS}}^{CHASH}\) is executed by \(\mathcal{A}\) presented in Algorithm 2.
The \({Succ2}_{\mathrm{SAKTMIS}}^{CHASH} =[\mathrm{Pr}\left[{\mathrm{EXP}2}_{\mathrm{SAKTMIS}}^{CHASH}=1\right]-1]\) is the success probability to execute \({\mathrm{EXP}2}_{\mathrm{SAKTMIS}}^{CHASH}\) and \({Adv2}_{\mathrm{SAKTMIS}}^{CHASH}\left({\fancyscript{t}}_{2},{\fancyscript{q}}_{\mathcal{R}}\right)= {max}_{A}\{{Succ2}_{\mathrm{SAKTMIS}}^{CHASH}\}\), advantage of \({\mathrm{EXP}2}_{\mathrm{SAKTMIS}}^{CHASH}\), where advantage function using \(\fancyscript{t}\) (execution time) and \({\fancyscript{q}}_{\mathcal{R}}\) (No. of RO reveal queries) is maximized on \(\mathcal{A}\). If \({Adv2}_{\mathrm{SAKTMIS}}^{CHASH}\left({\fancyscript{t}}_{2},{\fancyscript{q}}_{\mathcal{R}}\right)<\varepsilon \), and \(\varepsilon \) > 0 is sufficiently smaller than our scheme offers security against \(\mathcal{A}\) for extracting \({\fancyscript{p}\fancyscript{w}}_{i}\) of \({\mathcal{C}}_{\fancyscript{i}}\).
Assuming, all secrets {\({\mathcal{D}}_{i}\), \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}\), \({\fancyscript{h}}_{\varsigma}\left(.\right)\), \(\mathcal{W}\)} retrieved by \(\mathcal{A}\) from \({\mathcal{C}}_{\fancyscript{i}}\)'s smart card.
Experiment on Algorithm 2
If \(\mathcal{A}\) is capable to invert \({\fancyscript{h}}_{\varsigma}\left(.\right)\) (hash function), by deriving \({\fancyscript{p}\fancyscript{w}}_{i}\) of \({\mathcal{C}}_{\fancyscript{i}}\), \(\mathcal{A}\) wins the game. By the definition of chaotic hash function, \({Adv}_{A}^{CHASH}\left(\fancyscript{t}\right)\le \varepsilon \), with smaller \(\varepsilon \) > 0. We have \({Adv}_{A}^{CHASH}\left({\fancyscript{t}}_{2},{\fancyscript{q}}_{\mathcal{R}}\right)\le \varepsilon \), as it is dependent on \({Adv}_{\mathcal{A}}^{CHASH}\left(\fancyscript{t}\right)\). So, computationally it’s impractical to invert \({\fancyscript{h}}_{\varsigma}\left(.\right)\). Hence, our scheme is protective against \(\mathcal{A}\) for extracting \({\fancyscript{p}\fancyscript{w}}_{i}\) of \({\mathcal{C}}_{\fancyscript{i}}\) from smart card under lost or stolen scenario.
Algorithm 2. \({\mathbf{E}\mathbf{X}\mathbf{P}2}_{{\varvec{B}}{\varvec{A}}{\varvec{K}}{\varvec{A}}{\varvec{T}}{\varvec{N}}}^{{\varvec{H}}{\varvec{A}}{\varvec{S}}{\varvec{H}}}\) | |
|---|---|
1. Secret information is extracted {\({\mathcal{D}}_{i}\),\(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}\),\({\fancyscript{h}}_{\varsigma }\left(.\right)\),\(\mathcal{W}\)} from smart card SCi of \({\mathcal{C}}_{\fancyscript{i}}\) when lost or stolen based on attacks described in [47, 48]. Where \({\mathcal{D}}_{i}= {\mathcal{J}}_{i} \oplus \overline{{\fancyscript{p}\fancyscript{w}}_{i}},\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} = {\fancyscript{h}}_{\varsigma }({\fancyscript{i}\fancyscript{d}}_{i}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{J}}_{i}),\mathcal{W}={\kappa }_{i} \oplus {\fancyscript{h}}_{\varsigma }({\fancyscript{i}\fancyscript{d}}_{i}||{\fancyscript{p}\fancyscript{w}}_{i})\). 2. Reveal oracle is called on input \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}\), to extract \(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}\) ,\({\mathcal{J}}_{i}\) and \({\fancyscript{i}\fancyscript{d}}_{i}\) as \(\left({\fancyscript{i}\fancyscript{d}}_{i}\left|\left|\overline{{\fancyscript{p}\fancyscript{w}}_{i}}\right|\right|{\mathcal{J}}_{i}\right)\leftarrow {\bf reveal} ({M}_{i})\), 3. Reveal oracle is called on input \(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}\) to extract \({\fancyscript{p}\fancyscript{w}}_{i}\),\({\kappa }_{i}\) and \({\fancyscript{i}\fancyscript{d}}_{i}\) as \(({\fancyscript{p}\fancyscript{w}}_{i},{\kappa }_{i})\leftarrow {\bf reveal} (\overline{{\fancyscript{p}\fancyscript{w}}_{i}})\), 4. Computes \(\mathcal{W}\) * = \({\kappa }_{i} \oplus {\fancyscript{h}}_{\varsigma }({\fancyscript{i}\fancyscript{d}}_{i}||{\fancyscript{p}\fancyscript{w}}_{i})\) 5. if (\(\mathcal{W}\) * = \(\mathcal{W}\)) then 6. \({\fancyscript{p}\fancyscript{w}}_{i}\) is correct password of \({\mathcal{C}}_{\fancyscript{i}}\). 7: return 1 (i.e., Success) 8: else 9: return 0 (i.e., Failure) 10: end if | |
5.2 BAN logic for authentication proof
The authentication scheme or protocol can be analyzed using the BAN [55] logic. Generally, BAN logic is adapted to validate the authentication protocols as well as protocols for key establishment. Table 2 shows the various notations used and logical rules applied in BAN logic.
Idealized form of protocol messages is as follows:
Message 1. \({\mathcal{C}}_{\fancyscript{i}}\) → \(\mathcal{S}\): (\({\left({\fancyscript{i}\fancyscript{d}}_{i}\right)}_{{\fancyscript{h}}_{\varsigma}({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i})},{({\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\tau}_{1})}_{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||{\fancyscript{h}}_{\varsigma}({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i})}\), \({\tau}_{1}\))
Message 2. \(\mathcal{S}\) → \({\mathcal{C}}_{\fancyscript{i}}\): \({\left(\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}\right)}_{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||{\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right))},{({\mathcal{C}}_{\fancyscript{i}}\stackrel{\zeta}{\longleftrightarrow}\mathcal{S}||\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\fancyscript{i}\fancyscript{d}}_{i}||{\tau}_{3})}_{\zeta}\)
Message 3. \(\mathcal{S}\) → \({\mathcal{C}}_{\fancyscript{i}}\): \({({\kappa}_{s}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{F}}_{i}^{\prime})}_{\zeta}\)
5.2.1 Assumption
Following assumption are adapted in BAN logic to perform formal analysis:
A1) \({\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv \) #(\({\tau}_{1}\)).
A2) \({\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv \) (\({\mathcal{C}}_{\fancyscript{i}}\stackrel{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||{\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right))}{\longleftrightarrow}\mathcal{S}\)).
A3) \(\mathcal{S}\) |\(\equiv \) (\({\mathcal{C}}_{\fancyscript{i}}\stackrel{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||{\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right))}{\longleftrightarrow}\mathcal{S}\)).
A4) \({\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv \) (\({\mathcal{C}}_{\fancyscript{i}}\stackrel{{\fancyscript{h}}_{\varsigma}({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i})}{\longleftrightarrow}\mathcal{S}\)).
A5) \(\mathcal{S}\) |\(\equiv \) (\({\mathcal{C}}_{\fancyscript{i}}\stackrel{{\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right))}{\longleftrightarrow}\mathcal{S}\)).
A6) \({\mathcal{S}}_{\fancyscript{j}}\) |\(\equiv \) #(\({\tau}_{3}\)).
A7) \({\mathcal{S}}_{\fancyscript{j}}\) |\(\equiv {\mathcal{C}}_{\fancyscript{i}}|\equiv {\mathcal{C}}_{\fancyscript{i}}\stackrel{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||{\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right))}{\longleftrightarrow}\mathcal{S}\)
A8) \({\mathcal{C}}_{\fancyscript{i}}|\equiv {\mathcal{S}}_{\fancyscript{j}}|\equiv {\mathcal{C}}_{\fancyscript{i}}\stackrel{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||{\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right))}{\longleftrightarrow}\mathcal{S}\)
5.2.2 Analysis
Proposed scheme’s verification can be performed based on above assumptions and rules given in Table 3 related to BAN logic.
Lemma 1
The authenticity of login message of \({\mathcal{C}}_{\fancyscript{i}}\) could be correctly verified by \(\mathcal{S}\) (server).
Proof
Login message send by \({\mathcal{C}}_{\fancyscript{i}}\) to \(\mathcal{S}\). Then, timestamp and other values are received by \(\mathcal{S}\) and message source’s correctness can be proved as follows:
Message 1. \({\mathcal{C}}_{\fancyscript{i}}\) → \(\mathcal{S}\): (\({\left({\fancyscript{i}\fancyscript{d}}_{i}\right)}_{{\fancyscript{h}}_{\varsigma}({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i})},{({\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\tau}_{1})}_{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||\fancyscript{h}({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i})}\), \({\tau}_{1}\))
S1) \(\mathcal{S}\lhd \): \(\left({\fancyscript{i}\fancyscript{d}}_{i}\right),({\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\tau}_{1}),{\tau}_{1}\)// According to seeing rule.
S2) \(\mathcal{S}\) |\(\equiv {\mathcal{C}}_{\fancyscript{i}}|\sim \left({\fancyscript{i}\fancyscript{d}}_{i}\right),({\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\tau}_{1}),{\tau}_{1}\)// According to A3, A5, S1, message-meaning rule.
S3) \(\mathcal{S}\) |\(\equiv {\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv \left({\fancyscript{i}\fancyscript{d}}_{i}\right),({\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\tau}_{1}),{\tau}_{1}\)// According to A1, the freshness-conjuncatenation rule to S2.
S4) \(\mathcal{S}\) |≡ \({\tau}_{1}\)// According to A1, S3.
The fresh timestamp corresponding to the message is considered by \(\mathcal{S}\) (server). Hence, message source is correct is proved.
Lemma 2
The correctness of message responded by \(\mathcal{S}\) (server) can be verified by \({\mathcal{C}}_{\fancyscript{i}}\) (user).
Proof
Once the correctness of authenticate \({\mathcal{C}}_{\fancyscript{i}}\)’s (user’s) login message is confirmed, which consist of \(\mathcal{S}\)’s timestamp. Then, authenticity of \(\mathcal{S}\)’s message can be proved by \({\mathcal{C}}_{\fancyscript{i}}\) is shown as follows:
Message 2: \(\mathcal{S}\) → \({\mathcal{C}}_{\fancyscript{i}}\): \({\left(\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}\right)}_{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||{\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right))},{({\mathcal{C}}_{\fancyscript{i}}\stackrel{\zeta}{\longleftrightarrow}\mathcal{S}||\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\fancyscript{i}\fancyscript{d}}_{i}||{\tau}_{3})}_{\zeta}\)
S5) \({\mathcal{C}}_{\fancyscript{i}}\lhd {\left(\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}\right)}_{{\fancyscript{h}}_{\varsigma}({\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|\fancyscript{s}\fancyscript{k}\right)||{\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right))},{({\mathcal{C}}_{\fancyscript{i}}\stackrel{\zeta}{\longleftrightarrow}\mathcal{S}||\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\fancyscript{i}\fancyscript{d}}_{i}||{\tau}_{3})}_{\zeta}\)
S6) Based on assumption A3, S5 message meaning rule is applied hence we get.
\({\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv \mathcal{S}|\sim \left(\mathcal{S} \stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}\right),{({\mathcal{C}}_{\fancyscript{i}}\stackrel{\zeta}{\longleftrightarrow}\mathcal{S}||\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||{\fancyscript{i}\fancyscript{d}}_{i}||{\tau}_{3})}_{\zeta}\)
S7) Based on assumption A2, freshness rule is applied hence we get.
\({\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv \mathcal{S} |\equiv \left(\mathcal{S} \stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}\right),{({\mathcal{C}}_{\fancyscript{i}}\stackrel{\zeta}{\longleftrightarrow}\mathcal{S}||\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||{\fancyscript{i}\fancyscript{d}}_{i}||{\tau}_{3})}_{\zeta}\) .
S8) By using A3, A6 and S7, jurisdiction rule is applied hence we get \(\mathcal{S} |\equiv \mathcal{S} \stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}\), \({\tau}_{3}\).
This shows that correct verification of message source as well as its freshness could be done by \({\mathcal{C}}_{\fancyscript{i}}\).
Lemma 3
If authentication for message holds then common session key is computed by \({\mathcal{C}}_{\fancyscript{i}}\) and \(\mathcal{S}\) .
Proof
As per proposed scheme, after verifying timestamps and freshness of random number, \({\mathcal{C}}_{\fancyscript{i}}\) and \(\mathcal{S}\) can compute \(\zeta = {\fancyscript{h}}_{\varsigma}({\kappa}_{s}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{F}}_{i}^{\prime})\) (session key). By utilizing Lemmas 1 and 2, authenticity of \({\mathcal{C}}_{\fancyscript{i}}\) and \(\mathcal{S}\) among them is correctly verified. So, the unique session key generated using random number or fresh timestamps ensures the utilization of fresh session key for new session. The correct computation of negotiated session key is generated is believed by \({\mathcal{C}}_{\fancyscript{i}}\) and \(\mathcal{S}\) shown as follows:
S9) By using \(\zeta = {\fancyscript{h}}_{\varsigma}({\kappa}_{s}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}|\left|{\mathcal{F}}_{i}^{\prime}\right)\) we could get \({\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv {\mathcal{C}}_{\fancyscript{i}}\stackrel{\zeta}{\longleftrightarrow}{\mathcal{S}}_{\fancyscript{j}}\).
S10) As per message 3 we get \(\mathcal{S}\lhd {(\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{F}}_{i}^{\prime})}_{\zeta}\) .
S11) \(\mathcal{S}\) |\(\equiv {\mathcal{C}}_{\fancyscript{i}}|\sim {(\mathcal{S}\stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{F}}_{i}^{\prime})}_{\zeta}\)// According to S10, A3.
S12) \(\mathcal{S}\) |\(\equiv {\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv (\mathcal{S} \stackrel{{\kappa}_{s}}{\longleftrightarrow}{\mathcal{C}}_{\fancyscript{i}}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{F}}_{i}^{\prime})\).
S13) According to the \(\zeta = {\fancyscript{h}}_{\varsigma}({\kappa}_{s}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}|\left|{\mathcal{F}}_{i}^{\prime}\right)\) we could get \({\mathcal{C}}_{\fancyscript{i}}\) |\(\equiv {\mathcal{C}}_{\fancyscript{i}}\stackrel{\zeta}{\longleftrightarrow}{\mathcal{S}}_{\fancyscript{j}}\).
5.3 Discussions on attacks
5.3.1 Stolen smart card attack
Assume that the client \({\mathcal{C}}_{\fancyscript{i}}\)’s smart card is lost or stolen. As described in threat model [53]. Here, by using attacks described in [17, 53, 54], however, if the attacker uses the found smart card in order to login to the server \({\mathcal{S}}_{\fancyscript{j}}\), the attacker has to obtain/guess the correct password \({\fancyscript{p}\fancyscript{w}}_{i}\) of the client \({\mathcal{C}}_{\fancyscript{i}}\). Attacker extract stored information on the smart card \(\{{\mathcal{D}}_{i}, \mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime},{\fancyscript{h}}_{\varsigma}(.),\mathcal{W}\}\), once he/she find or stolen the smart card. Attacker deduce correct \({\fancyscript{p}\fancyscript{w}}_{i}\) of \({\mathcal{C}}_{\fancyscript{i}}\) to login to \({\mathcal{S}}_{\fancyscript{j}}\). However, we prove that valid \({\fancyscript{p}\fancyscript{w}}_{i}\) and \({\fancyscript{i}\fancyscript{d}}_{i}\) is cannot be computed by attacker. As a result, the attacker is unable to obtain the correct password of the client \({\mathcal{C}}_{\fancyscript{i}}\) and hence, our presented authentication protocol protects stolen smart card attacks.
5.3.1.1 Offline password guessing attack
In offline mode, to find user’s password, attacker must have random number \({\kappa}_{i}\), \({\fancyscript{i}\fancyscript{d}}_{i}\) and secret key d. The user’s \({\fancyscript{p}\fancyscript{w}}_{i}\) can be used only inside \({\mathcal{Y}}_{i}= {\fancyscript{h}}_{\varsigma}(\overline{{\fancyscript{p}\fancyscript{w}}_{i}})\oplus {\fancyscript{i}\fancyscript{d}}_{i}\) and \({\mathcal{U}}_{i} = {\fancyscript{h}}_{\varsigma}(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||\overline{\fancyscript{p}\fancyscript{w}_i} ||{\mathcal{F}}_{i}||{\tau}_{1}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{Y}}_{i})\). We observe that the guessing of correct password by an adversary need to find correct values \({\fancyscript{i}\fancyscript{d}}_{i}\) and \({\fancyscript{p}\fancyscript{w}}_{i}\) simultaneously but finding correct \({\fancyscript{i}\fancyscript{d}}_{i}\) with exact \({\fancyscript{l}}_{1}\) bits length and \({\fancyscript{p}\fancyscript{w}}_{i}\) with exact \({\fancyscript{l}}_{2}\) characters length concurrently is the probability is \({2}^{-{\fancyscript{l}}_{1}-6{\fancyscript{l}}_{2}}\). So, with probability \({2}^{-{\fancyscript{l}}_{1}-6{\fancyscript{l}}_{2}}\), the guessing is negligible and also finding in polynomial time [57] is not possible. Hence, we conclude the proposed scheme is protective for offline password guessing attack.
5.3.1.2 User’s stolen/lost smart card is untraceable
While login and authentication phase, messages are transmitted such as \(\{{\tau}_{1},{\mathcal{U}}_{i},{\mathcal{Y}}_{i}\}, \{\mu,{\mathcal{H}}_{1}, {\tau}_{3}\}\) and \(\{{\mathcal{H}}_{2}\}\), and can be intercepted by adversary and \(\{{\mathcal{D}}_{i}, \mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime},{\fancyscript{h}}_{\varsigma}(.),\mathcal{W}\}\) can be extracted from SC. The user’s identity can be found inside \({\mathcal{Y}}_{i}={\fancyscript{h}}_{\varsigma}(\overline{{\fancyscript{p}\fancyscript{w}}_{i}})\oplus {\fancyscript{i}\fancyscript{d}}_{i}\). Moreover, without \({\fancyscript{i}\fancyscript{d}}_{i}\) and \({\fancyscript{p}\fancyscript{w}}_{i}\), it is not possible for attacker to obtain user’s identity correctly. Thus, it is impossible to do in polynomial time [57]. Eventually, holder’s plaintext identity is not stored in SC. So, holder’s tracing based on smart card is not allowed by the proposed scheme.
5.3.2 Denial-of-service attack
When \({\mathcal{C}}_{\fancyscript{i}}\) inserts his identity \({\fancyscript{i}\fancyscript{d}}_{i}\) and password \({\fancyscript{p}\fancyscript{w}}_{i}\), the login message is not computed instantly by SC in proposed scheme. The correctness of \({\fancyscript{i}\fancyscript{d}}_{i}\) and \({\fancyscript{p}\fancyscript{w}}_{i}\) which is inserted is firstly checked. SC retrieves the random number \({\kappa}_{i} =\mathcal{W} \oplus {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}|\left|{\fancyscript{p}\fancyscript{w}}_{i}\right)\) and computes \(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}= {\fancyscript{h}}_{\varsigma}({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i})\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime\prime} = {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{J}}_{i})\) and compares \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime\prime}\) with \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}}\) which is stored on SC. The password is correct, if \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}\boldsymbol{^{\prime}}} = \mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}}\). Otherwise, incorrect password is identified and session is epilogue by SC. So, by using wrong password, the legitimate user is also not able to activate his/her SC. This works as a prevention mechanism for user not to insert false identifiers by mistake. Now, healthcare services can be accessed by the user without facing any problem of denial-of-service. Therefore, denial-of-service attack is easily handled by proposed scheme.
5.3.3 Replaying attack
The protection against replaying attack by the adversary is tackle by using timestamps, when login message is replays to \(\mathcal{S}\). Invalid timestamp \({\tau}_{i}\) (resp. \({\tau}_{\mathcal{S}}\)) is detected by \(\mathcal{S}\) (resp. \({\mathcal{C}}_{\fancyscript{i}}\)) when an adversary replays \({\fancyscript{l}}_{1}\) (resp. \({\fancyscript{l}}_{1}^{\prime}\)).
5.3.4 Stolen verifier attack
The cipher-text (\(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{{\varvec{i}}}^{\boldsymbol{^{\prime}}}\), \({\mathcal{X}}_{i}\), bit) with \({\mathcal{X}}_{i} = {\fancyscript{h}}_{\varsigma}(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} ||\fancyscript{s}\fancyscript{k}) \oplus \overline{{\fancyscript{p}\fancyscript{w}}_{i}}\) and \(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime} = {\fancyscript{h}}_{\varsigma}({\fancyscript{i}\fancyscript{d}}_{i}||\overline{\fancyscript{p}\fancyscript{w}_i}||{\mathcal{J}}_{i})\) is stored by the server on its database. Secret key \(\fancyscript{s}\fancyscript{k}\) and \(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}\) is only known to \({\mathcal{S}}_{\fancyscript{j}}\); hence, storing the values into the database is the sole responsibility of \({\mathcal{S}}_{\fancyscript{j}}\). Thus, stolen verifier attack in not vulnerable to proposed scheme.
5.3.5 Impersonation attack
The \({\mathcal{S}}_{\fancyscript{j}}\) or \({\mathcal{C}}_{\fancyscript{i}}\) are impersonated by the attacker under impersonate attack. To do so, the valid login request \(\{{\tau}_{1}, {\mathcal{U}}_{i}, {\mathcal{Y}}_{i}\}\) is forges by an adversary, where \({\mathcal{U}}_{i} = {\fancyscript{h}}_{\varsigma}(\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}||\overline{{\fancyscript{p}\fancyscript{w}}_{i}}||{\mathcal{F}}_{i}||{\tau}_{1}||{\fancyscript{i}\fancyscript{d}}_{i}|\left|{\mathcal{Y}}_{i}\right)\) and \({\mathcal{Y}}_{i}= {\fancyscript{h}}_{\varsigma}(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}) \oplus {\fancyscript{i}\fancyscript{d}}_{i}\). However, without the values of \(\fancyscript{i}\fancyscript{d}\) and \(\fancyscript{p}\fancyscript{w}\), \({\mathcal{U}}_{i}\) is not able to computed by an adversary, similar to Sect. 3.3.1.1, user’s correct password guess is fails here by the adversary. So, login request says to be correct cannot be generated by an adversary in the scenario when \({\mathcal{C}}_{\fancyscript{i}}\)’s smart card secret information \(\{{\mathcal{D}}_{i}, \mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime},{\fancyscript{h}}_{\varsigma}(.),\mathcal{W}\}\) is extracted by an adversary. Hence, proposed scheme smartly prevents from impersonation attack.
If \({\mathcal{S}}_{\fancyscript{j}}\) (server) is impersonated by the attacker. To do so, correct response message \(\left\{\mu, {\mathcal{H}}_{1}, {\tau}_{3}\right\}\) where \({\mathcal{H}}_{1} = {\fancyscript{h}}_{\varsigma}(\zeta ||{\kappa}_{s}||\mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime}|\left|{\mathcal{J}}_{i}\left|\left|{\fancyscript{i}\fancyscript{d}}_{i}\right|\right|{\tau}_{3}\right)\) and \(\mu = {\kappa}_{s} \oplus {\mathcal{F}}_{i}^{\prime}\) is forged by the attacker. Here, attacker must have the secret key \(\fancyscript{z}\) belongs to \(\mathcal{S}\). So, generation of valid response message by the attacker is not possible. Therefore, impersonation attack is prevented by proposed scheme.
5.3.6 Privileged insider attack
There is no provision of sending password in the form of plaintext by \({\mathcal{C}}_{\fancyscript{i}}\) in proposed scheme. Random number \({\kappa}_{i}\) is utilized to send \(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}= {\fancyscript{h}}_{\varsigma}\left({\fancyscript{p}\fancyscript{w}}_{i}\oplus {\kappa}_{i}\right)\) by \({\mathcal{C}}_{\fancyscript{i}}\). Hence, no insider at \(\mathcal{S}\) side obtains \({\fancyscript{p}\fancyscript{w}}_{i}\) at the time of registration phase. Moreover, \({\fancyscript{p}\fancyscript{w}}_{i}\) from \(\overline{{\fancyscript{p}\fancyscript{w}}_{i}}\) cannot be retrieved; therefore, privileged insider attack is resisted by proposed scheme.
5.3.7 Forward secrecy
On leakage of \(\fancyscript{z}\) (secret key) of server. Still, the session key (\(\zeta \)) cannot be computed by an adversary, because user’s identity is not known to the adversary to obtain \(\zeta = {\fancyscript{h}}_{\varsigma}({\kappa}_{s}||{\mathcal{J}}_{i}||{\fancyscript{i}\fancyscript{d}}_{i}||{\mathcal{F}}_{i}^{\prime})\). Hence, due to the lack of session key, proposed scheme maintain forward secrecy.
5.3.8 Many logged-in users’ attacks
The attack under title signifies that other user knows the \({\fancyscript{i}\fancyscript{d}}_{i}\) (identity) and \({\fancyscript{p}\fancyscript{w}}_{i}\) (password) in the scenario when user’s SC is lost or stolen. Then, everyone having SC and \({\fancyscript{p}\fancyscript{w}}_{i}\) (password for same SC) can simultaneously logged to \(\mathcal{S}\) [58, 59]. However, \(\mathcal{S}\) will not allow more users to access account of a legal user simultaneously. Here, under the assumption that non-registered users know the \({\mathcal{C}}_{\fancyscript{i}}\) ’s identity \({\fancyscript{i}\fancyscript{d}}_{i}\), password \({\fancyscript{p}\fancyscript{w}}_{i}\) and parameters \(\{{\mathcal{D}}_{i}, \mathcal{N}{\fancyscript{i}\fancyscript{d}}_{i}^{\prime},{\fancyscript{h}}_{\varsigma}(.),\mathcal{W}\}\). However, \(\mathcal{S}\) is maintaining field called “status-bit” in identity table, which restrict the simultaneously login on \(\mathcal{S}\). For example, when first user login into \(\mathcal{S}\). Then, status-bit is set to 1 by \(\mathcal{S}\). Now, the request of login by second user on \(\mathcal{S}\) is rejected, because the status-bit is already set to 1, indicates that someone is already login on the server. Thus, our scheme is also secured when many logged-in users attacks are performed on the system.
6 Performance comparison
The performance analysis and comparative study related to the security and functionality features supported by the proposed scheme presented in this section. In addition, proposed signature scheme’s efficiency is compared to the current schemes described in Chiou et al. [60], Ravanbakhsh and Nazari [63], and Ostad et al. [65]. The proposed scheme has capability to address the problem of stolen smart card attack and offline password guessing attack, etc. Table 3 shows the comparison based on various security features supported by the proposed scheme. Table 3 also demonstrates that the proposed scheme is effective in handling various attacks discussed in Sect. 5. The comparison has been made based on computational time. The comparative analysis used the notations mentioned in Table 4. The study uses the computational cost given in He et al. [63], and moreover the time required by each operation is presented in Table 4. The computational cost for modular exponentiation operation and one bilinear pairing operation is taken as 192 ms, and 496 ms, respectively. The computational cost for chaotic hash function is taken as equal to general hash function. The signing stage and the verification stage are influencing the overall performance of the scheme. Therefore, in this study, we compared the computational cost for signing stage and the verification stage, because it is the most dominating factor. Table 5 presents an overview execution time for each operation of our scheme in this research work over the state-of-the-art schemes mentioned in the literature.
Table 6 demonstrates that our scheme is more efficient than Chiou et al. [60], Ravanbakhsh and Nazari [61], and Ostad et al. [62] based on the time required for the various phases. It is seen from Table 6 that the proposed scheme requires only 52.58 ms for the registration stage, 70.64 ms for the login stage, 70.64 ms for the verification stage, and 104.52 ms for the password change stage. The total computational cost for the proposed scheme is 298.38 ms which is very less as compared to the counterparts. In addition, Fig. 3 shows the pictorial representation of comparative analysis and highlights the better performance of proposed scheme in comparison to current schemes.
7 Conclusions
In this article, we proposed an efficient lightweight and provably secure authentication scheme for client with anonymity for TMIS using chaotic hash function. We also, showed that the presented scheme is secure against very potential attacks such as stolen smart card attack, denial-of-service attack, replaying attack, stolen verifier attack, impersonation attack, privileged insider attack, forward secrecy, and many logged-in users’ attacks. Moreover, this new system is secure via structured security verification. The formal and informal security analysis is performed on the proposed scheme to ensure no security breaches. In addition, BAN logic is employed to show the completeness of the scheme. After experimenting the proposed scheme, we observed that the less overheads are incurred in terms of costs required for communication and computation related to existing schemes. Lastly, we conclude that our client authentication scheme is offering more features than existing sachems.
References
Sood SK, Sarjee AK, Singh K (2010) Anjour improvement of Liao et al.’s authentication scheme using smart card. In: 2010 IEEE 2nd International Advance Computing Conference (IACC2010), pp 240–245
He D, Kumar N, Chilamkurti N, Lee JH (2014) Lightweight ECC based RFID authentication integrated with an ID verifier transfer protocol. J Med Syst 38(10):1–6
Hwang MS, Li LH (2000) A new remote user authentication scheme using smart cards. IEEE Trans Consum Electron 46(1):28–30
Lee TF, Chang JB, Chan CW, Liu HC (2010) Password-based mutual authentication scheme using smart cards. In: The E-learning and Information Technology Symposium (EITS 2010)
Li CT, Lee CC, Weng CY (2014) A secure chaotic maps and smart cards based password authentication and key agreement scheme with user anonymity for telecaremedicine information systems. J Med Syst 38(9):77
He D, Kumar N, Chilamkurti N (2015) A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf Sci. https://doi.org/10.1016/j.ins.2015.02.010
He D, Zeadally S (2015) Authentication protocol for ambient assisted living system. IEEE Commun Mag 35(1):71–77
Chen CL, Yang TT, Chiang ML, Shih TF (2014) A privacy authentication scheme based on cloud for medical environment. J Med Syst 38(11):143
Wu ZY, Lee YC, Lai F, Lee HC, Chung Y (2012) A secure authentication scheme for telecare medicine information systems. J Med Syst 36(3):1529–1535
He DB, Chen JH, Zhang R (2012) A more secure authentication scheme for telecare medicine information systems. J Med Syst 36:1989–1995
Chen C, He D, Chan S, Bu SJ, Gao Y, Fan R (2011) Lightweight and provably secure user authentication with anonymity for the global mobility network. Int J Commun Syst 24(3):347–362
Lin HY (2013) On the security of adynamic ID-based authentication scheme for telecaremedical information systems. J Med Syst 37:9929
Cao T, Zhai J (2013) Improved dynamic ID-based authentication scheme for telecare medical information systems. J Med Syst 37:9912
Khan MK, Kumari S (2014) Cryptanalysis and improvement of “An efficient and secure dynamic ID-based authentication scheme for telecare medical information systems.” Secur Commun Netw 7(2):399–408
Lee T-F, Chang I-P, Lin T-H, Wang C-C (2013) A secure and efficient password-based user authentication scheme using smart cards for the integrated EPR information system. J Med Syst 37(3):9941
Wen F (2014) A more secure anonymous user authentication scheme for the integrated EPR information system. J Med Syst 38(5):42
Das A (2015) A secure and robust password-based remote user authentication scheme using smart cards for the integrated EPR information system. J Med Syst 39:25
He D, Zeadally S (2015) An analysis of RFID authentication schemes for internet of things in healthcare environment using elliptic curve cryptography. IEEE Internet Things J 2(1):72–83
Lu Y, Li L, Peng H, Yang Y (2015) An enhanced biometric based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J Med Syst 39(3):1–8
Abdellaoui A, Khamlichi YI, Chaoui H (2016) A robust authentication scheme for telecare medicine information system. Proc Comput Sci 98:584–589
Chaudhry SA, Mahmood K, Naqvi H, Khan MK (2015) An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography. J Med Syst 39:175. https://doi.org/10.1007/s10916-015-0335-y
Chaudhry SA, Khan MT, Khan MK, Shon T (2016) A multiserver biometric authentication scheme for TMIS using elliptic curve cryptography. J Med Syst 40:230. https://doi.org/10.1007/s10916-016-0592-4
Chaudhry SA, Naqvi H, Khan MK (2018) An enhanced lightweight anonymous biometric based authentication scheme for TMIS. Multimed Tools Appl 77:5503–5524. https://doi.org/10.1007/s11042-017-4464-9
Sutrala AK, Das AK, Odelu V, Wazid M, Kumari S (2016) Secure anonymity-preserving password-based user authentication and session key agreement scheme for telecare medicine information systems. Comput Methods Prog Biomed 135:167–185
Liu W, Xie Qi, Wang S, Bin Hu (2016) An improved authenticated key agreement protocol for telecare medicine information system. Springer Plus 5:555. https://doi.org/10.1186/s40064-016-2018-7
Masdari M, Ahmadzadeh S (2017) A survey and taxonomy of the authentication schemes in telecare medicine information systems. J Netw Comput Appl 87:1–19
Fan Wu, Li X, Sangaiah AK, Lili Xu, Kumari S, Liuxi Wu, Shen J (2018) A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Future Gener Comput Syst 82:727–737
Li X, Niub J, Kumaric S, Wud F, Chooe K-K (2018) A robust biometrics based three-factor authentication scheme for global mobility networks in smart city. Future Gener Comput Syst 83:607–618
Chandrakar P, Om H (2017) A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC. Comput Commun. https://doi.org/10.1016/j.comcom.2017.05.009
Hafizul Islam SK, Obaidat MS, Vijayakumar P, Abdulhay E, Fagen Li M, Reddy KC (2018) A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs. Future Gener Comput Syst 84:216–227
Cui J, Zhang J, Zhong H, Shi R, Yan Xu (2018) An efficient certificate less aggregate signature without pairings for vehicular ad hoc networks. Inf Sci. https://doi.org/10.1016/j.ins.2018.03.060
Jiang Qi, Ma J, Yang C, Ma X, Shen J, Chaudhry SA (2017) Efficient end-to-end authentication protocol for wearable health monitoring systems. Comput Electr Eng 63:182–195
Challa S, Das AK, Gope P, Kumar N, Wu F, Vasilakos AV (2018) Design and analysis of authenticated key agreement scheme in cloud-assisted cyber-physical systems. Future Gener Comput Syst. https://doi.org/10.1016/j.future.2018.04.019
Ostad-Sharif A, Abbasinezhad-Mood D, Nikooghadam M (2019) Efficient utilization of elliptic curve cryptography in design of a three-factor authentication protocol for satellite communications. Comput Commun 147:85–97
Wei J, Liu W, Hu X (2018) On the security and improvement of privacy-preserving 3-factor authentication scheme for TMIS. Int J Commun Syst. e3767
Chandrakar P, Om H (2018) An extended ECC-based anonymity-preserving 3-factor remote authentication scheme usable in TMIS. Int J Commun Syst e3540
Radhakrishnan N, Karuppiah M (2018) An efficient and secure remote user mutual authentication scheme using smart cards for Telecare medical information systems. Inform Med Unlocked. https://doi.org/10.1016/j.imu.2018.02.003
Alzahrani BA, Irshad A (2018) A secure and efficient TMIS-based authentication scheme improved against Zhang et al’.s scheme. Arab J Sci Eng 43:8239–8253. https://doi.org/10.1007/s13369-018-3494-6
Zhang LP, Zhu SH (2015) Robust ECC-based authenticated key agreement scheme with privacy protection for telecare medicine information systems. J Med Syst 39(5):1–13
Soni P, Pal AK, Hafizul Islam SK (2019) An improved three-factor authentication scheme for patient monitoring using WSN in remote health-care system. Comput Methods Progr Biomed 182:105054
Renuka KM, Kumari S, Li S (2019) Design of a secure three-factor authentication scheme for smart healthcare. J Med Syst 43:133. https://doi.org/10.1007/s10916-019-1251-3
Qiao H, Dong X, Shen Y (2019) Authenticated key agreement scheme with strong anonymity for multi-server environment in TMIS. J Med Syst 43:321. https://doi.org/10.1007/s10916-019-1442-y
Ostad-Sharif A, Abbasinezhad-Mood D, Nikooghadam M (2019) An enhanced anonymous and unlinkable user authentication and key agreement protocol for TMIS by utilization of ECC. Int J Commun Syst 2019:e3913. https://doi.org/10.1002/dac.3913
Dharminder D, Mishra D, Li X (2020) Construction of RSA-based authentication scheme in authorized access to healthcare services. J Med Syst 44:6. https://doi.org/10.1007/s10916-019-1471-6
Lo J-W, Chun-Yueh Wu, Chiou S-F (2020) A lightweight authentication and key agreement scheme for telecare medicine information system. J Internet Technol 21(1):263–272
Arshad H, Rasoolzadegan A (2016) Design of a secure authentication and key agreement scheme preserving user privacy usable in telecare medicine information systems. J Med Syst 40:237
Liu W, Liu J, Wu Q, Qin B, Naccache D, Ferradi H (2018) Efficient subtree-based encryption for fuzzy-entity data sharing. Soft Comput 22(23):7961–7976
Meshram C, Lee CC, Meshram SG, Meshram A (2020) OOS-SSS: an efficient online/offline subtree-based short signature scheme using Chebyshev chaotic maps for wireless sensor network. IEEE Access 8(1):80063–80073
Meshram C, Lee CC, Ranadive AS, Li CT, Meshram SG, Tembhurne JV (2020) A subtree-based transformation model for cryptosystem using chaotic maps under cloud computing environment for fuzzy user data sharing. Int J Commun Syst 33(7):e4307
Meshram C, Lee CC, Meshram SG, Khan MK (2019) An identity-based encryption technique using subtree for fuzzy user data sharing under cloud computing environment. Soft Comput 23(24):13127–13138
Xiao D, Liao X, Deng S (2005) One-way hash function construction based on the chaotic map with changeable-parameter. Chaos Solitons Fract 241:65–71
Das AK, Goswami A (2014) An enhanced biometric authentication scheme for telecare medicine information systems with nonce using chaotic hash function. J Med Syst 38:27
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. IEEE Trans Comput 51(5):541–552
Witteman M (2002) Advances in smartcard security. Inf Secur Bull 7:11–22
Burrows M, Abadi M, Needham R (1990) A logic of authentication. ACM Trans Comput Syst 8(1):18–36
Sarkar P (2010) A simple and generic construction of authenticated encryption with associated data. ACM Trans Inf Syst Secur 13(4):33
Chang YF, Yu SH, Shiao DR (2013) An uniqueness-andanonymitypreserving remote user authentication scheme for connected health care. J Med Syst 37:9902
Li CT, Lee CC, Weng CY, Fan CI (2013) An extended multi-server-based user authentication and key agreement scheme with user anonymity. KSII Trans Int Inform Syst 7:119–131
Li CT (2013) A new password authentication and user anonymity scheme based on elliptic curve cryptography and smart card. IET Inform Secur 7:3–10
Shin-Yan C, Ying Z, Liu J (2016) Improvement of a privacy authentication scheme based on cloud for medical environment. J Med Syst 40:101
Niloofar R, Nazari M (2018) An efficient improvement remote user mutual authentication and session key agreement scheme for E-health care systems. Multimed Tools Appl 77:55–88
Arezou O-S, Abbasinezhad-Mood D, Nikooghadam M (2019) An enhanced anonymous and unlinkable user authentication and key agreement protocol for TMIS by utilization of ECC. Int J Commun Syst 32:e3913
He D, Kumar N, Lee JH, Sherratt RS (2014) Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans Consum Electron 60(1):30–37
Acknowledgements
Supported by Visvesvaraya PhD Scheme, MeitY, Govt. of India. No. MEITY-PHD-3039.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest.
Human and animal rights
The paper does not contain any studies with human participants or animals performed by any of the authors.
Informed consent
Informed consent was obtained from all individual participants included in the study.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gaikwad, V.P., Tembhurne, J.V., Meshram, C. et al. Provably secure lightweight client authentication scheme with anonymity for TMIS using chaotic hash function. J Supercomput 77, 8281–8304 (2021). https://doi.org/10.1007/s11227-020-03553-y
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-020-03553-y