Abstract
In this paper, an encryption model for the grayscale and color images based on novel magic square, and differential encoding technique along with chaotic map has been proposed. The coordinate positions of the plain image have been randomized by implementing the 2D Arnold scrambling algorithm in confusion phase. The magic square constructed by a novel approach has been used to alter the pixel values of the original image. The differential encoding technique has been introduced in the model to raise the bit-level security. Further, the piece-wise linear chaotic map has been utilized in the diffusion phase to increase randomization for increasing the complexity. The visual analysis as well as histogram and correlation coefficient analysis has been performed to test the resistance of the proposed model against different kinds of statistical, entropy, and cropping attacks. The effect of information loss of the plain image hidden in the encrypted image has been investigated by trimming the one-third and one-fourth portion of the encrypted image. The proposed model has also been tested against the differential attacks by examining the NPCR and UACI scores. A comparison of the propounded model with the other existing encryption models has also been made for validation. The results show that the proposed model is advantageous and feasible for the image encryption-related applications.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
The recent advancements in networking and communication technologies raises the demand to store and transmit data over the network which requires improvement in the application areas concerning cryptography, cybersecurity, etc. [72]. The data transmitted and stored using open network are prone to information leakage. With the increase in volume, velocity, and veracity of the multimedia data, it becomes necessary to enhance the security, confidentiality, and privacy of the information [38, 57]. The requirement of confidentiality and authenticity of the information being downloaded, uploaded, and stored is one of the major issues in cloud data storage and encryption related applications. Thus, the need for securing the information from illegal and unlicensed access becomes a necessity [8]. Cryptography is a vital technique which guarantees the privacy of secret data by converting it to an unrecognizable form. Both images and text are converted to an unreadable form using the process of encryption [53].
Images play a significant role as an essential multimedia resource in the modern big data era which constitutes a large amount of information [30, 70]. Henceforth, the maintenance of integrity and security of images have become a major concern in many fields such as military, internet communication, multimedia systems, telemedicine, e-commerce, e-learning, banking, etc. [13, 56, 60]. The modern cryptographic applications offer a workable solution to the persisting issues of sharing images through internet.
In general, the image encryption model is divided into two parts: confusion and diffusion [17, 23]. The randomness in the pixels of plain image is introduced in the confusion process, whereas the pixel values of the image are altered in the diffusion process by using various methods [19].
Frequently, mathematics plays a vital role in various cryptographic models for enhancing the level of security [40, 44, 63, 67]. The researchers have utilized different techniques such as chaotic maps, matrix theory, wavelet theory, numerical techniques, magic cubes, transformation theory, elliptic curves, DNA encoding, etc., for encrypting images [10, 43, 50, 52, 64]. The matrix theory fulfills the requirement by using singular value decomposition, permutation, inverse of matrices, etc., in cryptographic models [43, 45, 68]. Most commonly, the special type of matrices named as magic squares raise the level of randomness in the encryption models to a higher extent [41]. In addition to matrix theory, the chaos maps have been widely used by the experimenters in the image encryption algorithms because of its unpredictability and sensitivity of initial state [25, 49]. The shuffling and altering of image pixels have been performed in the confusion and diffusion phases, respectively, of the encryption algorithms by using different chaotic maps [32, 37]. Despite this the sensitivity of chaotic maps to parameter initialization disturbs the stability of image encryption algorithms. Thus, the chaotic maps are required to be used in combination with other components to achieve the optimum extent of stability. Moreover, it is also necessary to introduce the new methods for construction of magic squares which are capable of raising the level of randomness in the image encryption models in comparison to the existing models.
In this work, a new approach for the generation of magic square has been instigated. The flexible structural features as well as complex arrangement of the elements of a novel magic square along with chaotic map and differential encoding enlighten the way toward the field of image encryption. The proposed model has been implemented on both color as well as grayscale images. The alteration in pixel values has been performed by taking advantage of elements and properties of newly constructed magic square which enhances the reliability and feasibility of the proposed model.
The rest of paper is outlined as under: The related work is outlined in Sect. 2. The motivation behind this work is elaborated in Sect. 3. The detailed description of all the phases of the proposed encryption and decryption model along with the construction of novel magic square is given in Sect. 4. The anatomization and detailed discussions of the proposed model are presented in Sect. 5. The conclusions procured from the work are delineated in Sect. 6.
2 Related work
A square matrix of order n, in which the elements alongside each row, each column, and each of the two main diagonals are sum up to a fixed constant is known as magic square [34]. The algebraic properties of magic squares enlighten the way toward different application areas illustrated as image processing, cryptography, game theory, graph theory, and appreciably more.
The researchers represented several methods for the construction of magic squares having fabulous mathematical characteristics. Li et al. showed the construction of pandiagonal magic squares of doubly even order using magic rectangles [29]. Lee et al. gave the necessary and sufficient condition for the non-singularity of regular magic squares by virtue of centro-skew matrices [28]. Chan et al. gave the method for the construction of singular and non-singular regular classical magic squares of odd order [6]. Liu et al. proved the non-singularity of the odd-order classical regular magic square generated using the centro-skew S-circulant matrix [31]. Miranda et al. gave a method for the generation of doubly even-order magic square along with the generalization of Durer\(^{\prime }\)s magic square [33]. The growing need of randomness in cryptographic models motivated the researchers to introduce reliable method for the construction of magic squares.
The various types of chaotic maps are used in combination with other components for the improvement in security of image encryption models in case of both grayscale and color images by the researchers. Shuangyuan et al. instigated the image encryption technique based on matrix transformation by locating the possible changed region [48]. Pappachan and Baby proposed image encryption model using combination of magic square and Tinkerbell maps [36]. Zhong et al. came forward with the concept of Good Lattice Point (GLP) for image encryption algorithms by modifying the pixel values using magic square operations [69]. Sowmiya et al. utilized the elements of pandiagonal magic squares in the model generated to encrypt images [51]. Farhan et al. [9] generated the keys using magic square for color image encryption. Rageed and Sadiq [39] introduced the composition of magic square along with 3D-chaotic map to encrypt and decrypt color images. Hua et al. [21] propounded a color image encryption algorithm using orthogonal Latin squares and 2D chaotic map. Wang and Liu [55] performed the image encryption by associating the octree diffusing and magic square scrambling with chaotic maps. Senthilnayaki et al. propounded a medical image encryption model based on magic square and particle swarm optimization (PSO) [47].
From the earlier work, it has been concluded that the erstwhile image encryption models lack in efficiency due to tight correlation, high redundancy, and big data stream. Also, it is necessary to introduce more mathematically rigorous method for the construction of large order magic squares. Moreover, the image encryption models based on single component along with either chaotic map or magic square are resilient in spite of the models based on combination of more than two components. Henceforth, in this paper the mathematically strong method for the generation of large order magic squares is formulated. Furthermore, this novel magic square is used in association with chaotic maps and differential encoding technique for encryption of both color as well as grayscale images. The differential encoding is utilized for the first time in encryption model to enhance the bit-level security and complexity.
3 Motivation
It has been observed from the literature that the mathematical approaches are capable of generating a more secure encryption models in comparison to any other techniques. Also, the less frequent availability of mathematically rigorous methods for the construction of large order magic squares has been noticed by us. Moreover, the magic squares are capable of generating a more secure encryption algorithm on combining with other components such as chaotic maps, scrambling techniques, DNA encoding, wavelet algorithms, etc. In addition, with growing demands it is necessary to pay attention to some techniques which are not explored yet. The differential encoding is one such technique which has not been utilized widely in spite of its great ability to provide the bit-level privacy to the encrypted data. Hence, these limitations of the benchmark models motivate us to propose an image encryption model by combining the concepts of magic square and differential encoding technique with the chaotic maps. The instigation of a novel magic square raises the level of complexity and security by making use of its elements. Also, the differential encoding technique is used to enhance the bit-level security of the proposed encryption model. Thus, the integration of chaotic map with the magic square and differential encoding in the propounded encryption model efficiently neglects all the major shortcomings of the image encryption models.
4 Proposed encryption/decryption model
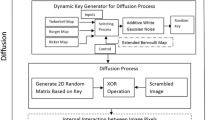
The proposed model for encryption and decryption of grayscale and color images has been instigated in this paper. Figure 1 shows the block diagram of the proposed encryption model. In the proposed model the encryption process comprises of two phases: confusion and diffusion. The scrambling technique has been used in the confusion phase to randomize the image pixels. Further, the diffusion phase has been accomplished using components: magic square, differential encoding technique, and chaotic map are explained in the following subsections.
4.1 Encryption model
All the phases of the encryption model have been explained in this subsection. The proposed model has been implemented on both grayscale and color images of different sizes. The systematic arrangement of all the components of the propounded image encryption model is shown in Fig. 1.
4.1.1 Confusion phase
In this phase, the initial locations of the pixels in the plain image are changed to any other random location to increase the haphazardness at the starting point of the encryption process [17]. In the proposed encryption model the scrambling has been performed by implementing 2D Arnold map given in Algorithm 1.

4.1.2 Diffusion phase
The diffusion phase of encryption model is essential to alter the pixel values of the plain image for generating an encrypted image. The propounded model contains components in the diffusion phase: magic square, differential encoding technique, and chaotic map are explained as follows:
4.1.0.1 Magic square
The \(n\times n\)-array of \(n^{2}\) numbers in which the sum of elements of each row, each column, main diagonal, and anti-diagonal is equal to a fixed constant is called as magic square and the fixed constant is termed as magic constant [42]. Mathematically, if \([a_{ij}] \) is a magic square of order n, then
The utilization of magic squares in the encryption model raises the level of complexity and security of the encrypted image. Moreover, the level of security in the proposed encryption model has been escalated by combining the concept of magic square with other components. The elements of magic squares have been used to change the pixel values of the plain image in the proposed model. The doubly even-order magic square of order sixteen has been harnessed in the propounded model generated by using following novel approach:
Let us consider two sets \(P=\{ p_{k} \;|\; \forall \; 1\le k\le \frac{n}{2}\}\) and \(Q=\{ q_{l}\; | \;\forall \; 1 \le l \le \frac{n}{2} \}\), where
for all \(0 \le s \le \frac{n}{4}-1.\) Thus, the elements of first row of \(A=[a_{ij}]_{n\times n}\) are given by
Now, define
The filling of remaining first \(\frac{n}{2}-1\) number of rows of A, starting from second row, is performed by using the following procedure:
Let \(s_{1}=\{ 1,2,5,6,\ldots \}=\{ x_{f}\; \vert \;\forall \;1 \le f \le \frac{n}{4} \}\) and \(s_{2}=\{ 3,4,7,8,\ldots \}=\{ y_{g}\; \vert \;\forall \;1 \le g \le \frac{n}{4}-1 \}\) be any two sets, where
for \(0\le h \le \Big \lfloor \frac{n}{8}-\frac{1}{2}\Big \rfloor \).
Therefore, the elements of all the remaining rows starting from the second row and up to \(\left( \frac{n}{2} \right) ^{th}\) row are given by
The elements of the lower half portion of matrix A, i.e., from \(\left( \frac{n}{2} +1 \right) ^{th}\) row to \(n^{th}\) row, are calculated by using the following expression
Therefore, the sum of elements of the first row (i.e. for \(i=1\)) is
The sum of elements of the \(i^{th}\) row, for \(2 \le i \le \frac{n}{2}\), evaluated by considering two cases is given by
Case-I: when \(r\in s_{1}\) then the row sum is
Case-II: when \(r\in s_{2}\) then the row sum is
Next, the sum of elements of each \(i^{th}\) row, for \(\frac{n}{2}+1 \le i \le n\), is
The main diagonal elements of the matrix A are defined by
and their sum is evaluated by
Similarly, the anti-diagonal elements of the matrix A are defined by
and their sum is
The column-wise definition of the above-constructed matrix \(A=[a_{ij}]_{n\times n}\) is given below:
For \(j=1,\) the elements of matrix A are given by
and their sum is
For \(2\le j \le \frac{n}{2}\), the elements of the matrix A are defined by
and \(s_{1},s_{2},P,Q,r\) are same as defined previously and their sum is evaluated as below:
Case-I: when \(r\in s_{1}\) then the sum of elements of each column is
Case-II: when \(r\in s_{2}\) then the sum of elements of each column is
Now, for \(\frac{n}{2}+1\le j \le n\), the elements of the above-generated matrix A are given by
and their sum is
Hence, the matrix A constructed above is a magic square with magic sum \(\frac{n(n^{2}+1)}{2}.\)
Algorithm 2 for the construction of above-introduced new class of doubly even-ordered magic square is as under:

4.1.0.2 Differential encoding technique
The differential encoding technique is implemented to impart unambiguous signal reception. In this technique, the previous reference bit is XOR with next bit in the sequence to hide the bit information of the plain image [73]. In this paper, it has been applied to encode the elements of the magic square which raises the level of security and complexity of the encrypted image. The encoding and decoding formulas used in implementation of this technique have been given below:
where \(d_{n},e_{n},\tilde{d_{n}}\) and \(\tilde{e_{n}}\) are the input, encoded, receiver and decoded sequences.
The block diagram of the differential encoding technique is depicted in Fig. 2. The examples of the sequence employed in the encryption and decryption model generated by this technique are demonstrated in Figs. 3 and 4.
4.1.0.3 Chaotic map
The random behavior, vulnerability, and susceptibility features of the chaotic maps increase their demand in the image encryption models [11]. The sequences generated using Piece-wise Linear Chaotic Map (PWLCM) alter the pixel values of the plain image to a high extent. Moreover, the chaotic maps generate different sequences each time for the same image which makes it hard for the intruders to fetch any information related to the plain image from the encrypted image. Two secret keys \(n_{0}\) (control parameters) and \(x_{0}\) (initial value) are used for the generation of chaotic sequences.
The complete utilization of the above components in the encryption model is outlined in Algorithm 3 as under:

4.2 Decryption model
The decryption has been accomplished by applying the encryption algorithm in reverse order. Starting with the conversion of 2D encrypted image to 1D array, the reverse circular shift and XOR operation have been applied to fetch the encoded magic square values using chaotic maps in binary form. The reverse differential encoding technique is used to extract the actual selected entries of the magic square which are further used to fetch the pixel values of the plain image. The reverse scrambling algorithm has been used to restore the original positions of the pixels in the plain image from the encrypted image. The reverse of the scrambling process is depicted with the help of Algorithm 4 as below:

5 Results and discussions
In this paper, the proposed encryption and decryption model based on the integration of magic square and differential encoding with chaotic maps has been analyzed. The model has been investigated in MATLAB 2021a platform, on Windows 10 Pro operating system with Intel\(\circledR \) Xenon\(\circledR \) CPU E5-2650 v3 (2.30 GHz) and 8GB of RAM. The 20 grayscale and 10 color images have been investigated using the proposed image encryption model while the results of only 17 images have been shown in the paper. The images available in USC-SIPI database have been utilized for the attestation of the propounded model [59]. The security, visual and statistical examination of the proposed model has been performed to confirm the resistance ability of the model against differential, entropy, visual, statistical, and cropping attacks. The grayscale and color images of resolution \(256\times 256\) pixels, \(512 \times 512\) pixels, and \(1024 \times 1024\) pixels have been considered for experimentation of the proposed model.
5.1 Visual analysis
The visual analysis is used to check the dissimilarity and similarity of the plain image with encrypted and decrypted image respectively. Figure 5 depicts the plain, encrypted, and decrypted grayscale and color images of different sizes using the proposed model. In case of color images, the component-wise encryption has been carried out using the proposed model. The encrypted images constitute the smooth distribution of the RGB and grayscale components. The visual inspection of the encrypted images shows that no information about structural outline of the plain image has been revealed. Also, a high visual similarity has been observed between decrypted and plain images.
5.2 Histogram analysis
The histograms invaded the demographic dissimilarity between the pixel values of the plain and encrypted images. The effectiveness of the resistance against statistical attacks of the encryption model is guaranteed by the even and smooth distribution plots [2].
In Figs. 6 and 7, the histograms of original and encrypted color and grayscale images are represented. The uneven distribution in the histogram of the plain images convey the useful information about the pixel values. The histograms of the encrypted images are uniformly distributed in the case of grayscale as well as color images which guarantee the strength of the proposed model to resist statistical attacks. The uniformity in the histograms is justified by using the chi-square test [17, 23, 35] to obtain the numerical results instead of visual spoofing and its values are calculated by the following formula:
where \(E_{i}=\frac{MN}{256}\) and \(P_{i}\) represents the expected and observed frequencies of each level in the image and \(i=1,2,3,\ldots ,255.\) Generally, for the different levels of significance the chi-square values are \(\chi ^{2}_{0.05}(255) =293.2478,\chi ^{2}_{0.01}(255)=310.4574\) and \(\chi ^{2}_{0.1}(255) =284.3359\).
In Table 1, the chi-square values of the encrypted image are less than the chi-square values of the plain image which proves the uniformity of histograms of encrypted images.
5.3 Key space analysis
The security of an image encryption model from the brute-force attacks is assured by the enough large size of key space. The required size of the key space must be greater than \(2^{128}\) to resist the brute-force attacks effectively [39, 46]. In the proposed image encryption model the key \(k=(k_{1},k_{2},k_{3},k_{4})\) is used for the decryption process at the receiver end. Here, the sub-keys \(k_{1},k_{2},k_{3},k_{4}\) represent the size of key of the 2D Arnold map used as scrambling technique, the size of key generated by magic square, the size of key produced by reference bits, and the size of key consisting of the parameters \(n_{0}=(n_{1},n_{2},n_{3})\) as well as initial values \(x_{0}=(x_{1},x_{2},x_{3})\) of the PWLCM map respectively. Further, if the size of each element of the magic square of order m is \(2^{b}\) bits then the size of the sub-key \(k_{2}\) is \((2^{b})^{m^{2}}\). Also, if the computer precision is \(10^{-15}\) then the size of key generated by each parameter and initial value in PWLCM is \(10^{15}\) which means the size of sub-key \(k_{4}\) is \((10^{15})^{3} \times (10^{15})^{3} \approx 2^{299}.\) Hence, the total size of the key space is calculated as
which is much larger than \(2^{128}\). This infers that the proposed model is capable of resisting brute-force attacks.
5.4 Key sensitivity analysis
The high sensitivity of the key in the encryption model guarantee the infeasibility of the brute force attack to decrypt the encrypted image. It means that the slightest changes made in the key used for decryption purpose do not allow the images to be get decrypted [4, 65]. In the proposed model, the change in only a single parameter of the key \(k=(k_{1},k_{2},k_{3},k_{4})\) do not allow the encrypted image to reveal any information related to the plain image. For instance, in case of RGB image if change the initial value \(x_{0}=(x_{1},x_{2},x_{3})\) of the PWLCM from \(x_{1}=0.157613081677548, x_{2}=0.970592781760616, x_{3}=0.957166948242946\) to \(x_{1}=0.157613081977548, x_{2}=0.970592781960616, x_{3}=0.957166948942946\) then this modified key do not generate the original plain image. Similarly, the intruder will never be able to obtain the original plain image if two or more parameters of the key are changed. The results of the decrypted images after changing one, two and three parameters in the key of the image 4.1.04 (RGB image) and 5.1.12 (gray image) are shown in Fig. 8 which ensures that the proposed model efficiently resists the brute force attacks.
5.5 Speed analysis
The time taken for the execution of an algorithm is also a significant factor, with respect to enhanced security level. The times taken by the encryption and decryption algorithms of the proposed model are given in Table 2, in case of both grayscale and color test images. The average times taken for the encryption of grayscale images of sizes \(256\times 256\), \(512\times 512\) and \(1024\times 1024\) pixels are 2.3 s, 9.5 s and 38.5 s respectively. In the same way, the encryption times of \(256\times 256\) and \(512\times 512\) pixels color images are 6.75 s and 27.7 s, respectively. Also, their corresponding average decryption times in case of both grayscale as well as color images are 3.66 s, 14.95 s, 60.31 s, 11.07 s and 45.23 s. It has been concluded that the proposed model is faster in comparison to some erstwhile models [3, 5, 16, 24, 54, 58, 66]. Also, the proposed image encryption model is slower in comparison to the other state-of-the-art models [22, 26, 62, 64]. The main reason is that in order to improve the encryption security of this encryption method the image is scrambled with complex chaotic map, and the alteration of image pixel values using the elements of proposed magic square, which greatly increases the encryption speed.
The comparative analysis of the average values of time taken for encryption and decryption of \(256 \times 256\) grayscale images is represented in Table 3. The bold values indicate that the proposed model has better speed efficiency in comparison to erstwhile image encryption models. The data used for comparison of the algorithms introduced by Hu et al. [16], Wang and Liu [58], Zhan et al. [65], Chai et al. [5] has been taken from Yan et al. [62].
5.6 Correlation coefficient analysis
The relation between the neighboring pixels of the plain and encrypted images is revealed by evaluating the correlation coefficients [12] horizontally, vertically and diagonally using the formula given below:
where N is the size of the image and u, v are adjacent pixel values of the grayscale image or RGB components.
The average horizontal, vertical and diagonal correlation coefficients have been evaluated for both plain and encrypted images in this work. The correlation between neighboring pixels of the plain and encrypted images has been performed by randomly choosing 3000 pairs of neighboring pixels in opposite directions. The pixels value \((x+1,y)\) with respect to the variable position (x, y) is considered for horizontal correlation. In the same way, the neighboring pixels \((x,y+1)\) and \((x+1,y+1)\) have been used for vertical and diagonal correlation respectively over the value (x, y).
In Fig. 9, the average horizontal, vertical, and diagonal correlation scatter plot of the color images have been depicted. The linear relationship has been followed in the plots of plain image which infers the strong correlation between the neighboring pixel values. On the other hand, the weak correlation between the neighboring pixel values of the encrypted image in the figure shows that the statistical attacks get weaker against the proposed model.
Figure 10 represents the correlation coefficient scatter plots of the grayscale images. The plots of plain images show that the points are closely placed along the diagonal line which implies high correlation between the neighboring pixels. While the symmetrically distributed points in the plots of encrypted images depict the low correlational among the neighboring pixels. Thus, the proposed model greatly minimizes the correlation between the neighboring pixels of the encrypted image which enhances the resisting power of the proposed model against statistical attack.
The average values of correlation coefficients of the plain and encrypted images are indicated in Table 4. The negative values of the correlation coefficient of the encrypted images obtained by using the proposed model depicts the weak relationship among the neighboring pixels. This implies that the proposed model is highly resistant to statistical-based attacks.
5.7 Information entropy analysis
The distribution and randomness in the pixels of an image is measured by entropy parameter and is calculated using the formula shown as follows:
where \(t_{i}\) is the pixel value and \(p(t_{i})\) is its probability of occurrence in the image.
Table 5 contains the entropy values of color and grayscale images. It has been delineated that the entropy values of the encrypted images procured using the proposed model lies between 7.9970 and 7.9999 which is near to 8. Hence, in the proposed model there are very less chances of information leakage. This implies that the proposed model is less prone to statistical and entropy attacks.
The comparison of the proposed model with the erstwhile models for the entropy values is shown in Table 6. The bold values indicate the better score obtained by the proposed model which proves that the proposed model is more secure to the entropy and statistical attacks as compared to the existing models.
5.8 Differential attack
The information transmitted through open network in the form of images is prone to the differential attacks. The performance of the model against differential attack is ensured by using the two widely used parameters: NPCR and UACI. The extent of percentage of distinct pixels in the two encrypted images is measured by using NPCR (number of pixels change rate). On the other hand, UACI metric (unified averaged changed intensity) depicts the average dissimilarity between the two encrypted images. The formulas used for finding the NPCR and UACI values are as follows:
where M and N represent the width and height of the plain image, \(C_{1}\) and \(C_{2}\) are two encrypted images encrypted before and after one pixel change, c is the difference between the corresponding pixel values of the encrypted images \(C_{1}\) and \(C_{2}\), and \(w\times h\) is the number of pixels in the plain image.
The NPCR and UACI values of the encrypted images using the proposed model are shown in Table 7. The values of NPCR and UACI have been analyzed for significance value at \(\alpha =0.05\). The proposed model pass the test results for all the images corresponding to the theoretical NPCR and UACI critical values which shows the resistance against the differential attacks.
In Table 8, juxtaposition of the proposed model with existing models is presented. The bold values of NPCR and UACI indicates the failure of the encryption models. It has been observed that the proposed model pass all the NPCR and UACI test results for the significant level at \(\alpha =0.05\). However, the existing encryption models proposed by [2, 27] and [18] do not give a test result of \(100\%\) which implies that these models can be prone to the differential attack than the rest of the models. However, the proposed scheme exhibits excellent performance by comparison, which proves the progress of this work.
5.9 Cropping attack
The anti-shearing aptness of the encryption model is verified by trimming some portions of the encrypted image. The trimming can spread the subtle changes in the plain image to the whole encrypted image in the encryption process. It also, tells about the effect of data loss in an encrypted image before decryption process [19].
The cropping attack has been applied on all the test images, but the results of only one grayscale and one color image are represented in Fig. 11. It has been observed that decryption process of the proposed model can still recover the plain image even after the loss of (1/3)rd and (1/4)th amount of data in the encrypted image [17]. The most of the information of the recovered images are easily recognizable even with addition of some noise. Therefore, when the encrypted image encounters cropping attack in the transmission, the proposed model has better security and can effectively resist the cropping attack.
5.10 SSIM
Structural Similarity Index Metric (SSIM) qualifies the degree of structural invariance between the two images [7]. It ranges from 0 to 1. The SSIM value 1 instigates that the images are completely indistinguishable, while its 0 value represents the characteristic dissimilarity between two images [14].
From Table 9 it has been analyzed that the plain versus decrypted images got the SSIM value equal to 1 which depicts the complete structural similarity between the plain and decrypted images. The SSIM values of the plain versus encrypted images ranges from 0.0043 to 0.0107 which means that the two images are completely distinct with respect to the image pixel values. Hence, the proposed image encryption model is effective and feasible against statistical attacks which implies that there are very few chances of information loss.
The experimental and statistical analysis conveys that the proposed image encryption and decryption model has better performance as compared to the existing models. The experimental results show that the proposed model resist statistical, entropy, differential, and cropping attacks in an efficient way.
6 Conclusion
This work propounds an image encryption and decryption model based on the scrambling algorithm, a novel magic square and differential encoding technique along with chaotic maps to enhance the level of security and privacy. The propounded model comprises two phases: confusion and diffusion. In the proposed model, the coordinate positions of the image pixels have been randomized by employing the scrambling algorithm which intensifies the degree of intricacy in the encrypted image before altering the pixel values. The elements of the magic square are utilized to change the image pixel values which reduce the plain image information hidden in the encrypted image. Further, the bit-level security of the proposed model has been improved by virtue of the implementation of the differential encoding technique on the magic square values. The XOR operation has been performed on the encoded and chaotic map values before applying the circular shift. Next, the complexity of the magic square values has been increased by using differential encoding and chaotic map. The in-depth security, structural, visual, and robustness anatomization of the propounded model have been performed to check the validity of the model against entropy, statistical, cropping, and differential attacks. The comparative inspection of the proposed model with the existing models reveals that the proposed model is more secure against different types of attacks. Henceforth, the proposed model is feasible and efficient for cryptographic application areas. In future, the researchers may work on the combination of algebraic properties of the magic square propounded in this paper along with wavelet transformations, numerical methods, DNA encoding technique, etc. These combinations might be able to generate the image encryption model with more enhanced level of security and complexity. Also, the proposed model will be tested for video and audio data encryption.
Data availability
The data that support the findings of the study are available in USC-SIPI [http://sipi.usc.edu/database].
References
Alawida, M., Samsudin, A., Teh, J.S., Alkhawaldeh, R.S.: A new hybrid digital chaotic system with applications in image encryption. Signal Process. 160, 45–58 (2019). https://doi.org/10.1016/j.sigpro.2019.02.016
Alawida, M., Teh, J.S., Samsudin, A., et al.: An image encryption scheme based on hybridizing digital chaos and finite state machine. Signal Process. 164, 249–266 (2019). https://doi.org/10.1016/j.sigpro.2019.06.013
Ayoup, A.M., Hussein, A.H., Attia, M.A.: Efficient selective image encryption. Multimed. Tools Appl. 75(24), 17171–17186 (2016). https://doi.org/10.1007/s11042-015-2985-7
Bao, L., Tang, J., Ding, H., He, M., Zhao, L.: The \(n\)-level (\(n\ge 4\)) logistic cascade homogenized mapping for image encryption. Nonlinear Dyn. 105, 1911–1935 (2021). https://doi.org/10.1007/s11071-021-06688-6
Chai, X., Gan, Z., Yuan, K., Chen, Y., Liu, X.: A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput. Appl. 31(1), 219–237 (2019). https://doi.org/10.1007/s00521-017-2993-9
Chan, C.Y.J., Mainkar, M.G., Narayan, S.K., Webster, J.D.: A construction of regular magic squares of odd order. Linear Algebra Appl. 457, 293–302 (2014). https://doi.org/10.1016/j.laa.2014.05.032
Deb, S., Biswas, B., Bhuyan, B.: Secure image encryption scheme using high efficiency word-oriented feedback shift register over finite field. Multimed. Tools Appl. 78(24), 34901–34925 (2019). https://doi.org/10.1007/s11042-019-08086-y
Faragallah, O.S., Afifi, A., El-Shafai, W., El-Sayed, H.S., Alzain, M.A., Al-Amri, J.F., Abd El-Samie, F.E.: Efficiently encrypting color images with few details based on rc6 and different operation modes for cybersecurity applications. IEEE Access 8, 103200–103218 (2020). https://doi.org/10.1109/ACCESS.2020.2994583
Farhan, A.S., Abed, S.H., Awad, F.H.: Color image encryption with a key generated by using magic square. J. Eng. Appl. Sci. 13(8), 2038–2041 (2018). https://doi.org/10.36478/jeasci.2018.2038.2041
Gaffar, A.F.O., Malani, R., Putra, A.B.W.: Magic cube puzzle approach for image encryption. Int. J. Adv. Intell. Inform. 6(3), 290–302 (2020). https://doi.org/10.26555/ijain.v6i3.422
Ghadirli, H.M., Nodehi, A., Enayatifar, R.: An overview of encryption algorithms in color images. Signal Process. 164, 163–185 (2019). https://doi.org/10.1016/j.sigpro.2019.06.010
Gupta, A., Singh, D., Kaur, M.: An efficient image encryption using non-dominated sorting genetic algorithm-iii based 4-d chaotic maps. J. Ambient. Intell. Humaniz. Comput. 11(3), 1309–1324 (2020). https://doi.org/10.1007/s12652-019-01493-x
Herzog, A., Shahmehri, N., Duma, C.: An ontology of information security. Int. J. Inf. Secur. Priv. (IJISP) 1(4), 1–23 (2007). https://doi.org/10.4018/jisp.2007100101
Hore, A., Ziou, D.: Image quality metrics: PSNR versus SSIM. In: 2010 20th International Conference on Pattern Recognition, pp. 2366–2369. IEEE (2010). https://doi.org/10.1109/ICPR.2010.579
Hu, G., Li, B.: A uniform chaotic system with extended parameter range for image encryption. Nonlinear Dyn. 103(3), 2819–2840 (2021). https://doi.org/10.1007/s11071-021-06228-2
Hu, T., Liu, Y., Gong, L.H., Ouyang, C.J.: An image encryption scheme combining chaos with cycle operation for DNA sequences. Nonlinear Dyn. 87(1), 51–66 (2017). https://doi.org/10.1007/s11071-016-3024-6
Hu, X., Wei, L., Chen, W., Chen, Q., Guo, Y.: Color image encryption algorithm based on dynamic chaos and matrix convolution. IEEE Access 8, 12452–12466 (2020). https://doi.org/10.1109/ACCESS.2020.2965740
Hua, Z., Zhou, Y.: Image encryption using 2D logistic-adjusted-sine map. Inf. Sci. 339, 237–253 (2016). https://doi.org/10.1016/j.ins.2016.01.017
Hua, Z., Zhou, Y., Pun, C.M., Chen, C.P.: 2D sine logistic modulation map for image encryption. Inf. Sci. 297, 80–94 (2015). https://doi.org/10.1016/j.ins.2014.11.018
Hua, Z., Zhou, Y., Huang, H.: Cosine-transform-based chaotic system for image encryption. Inf. Sci. 480, 403–419 (2019). https://doi.org/10.1016/j.ins.2018.12.048
Hua, Z., Zhu, Z., Chen, Y., Li, Y.: Color image encryption using orthogonal Latin squares and a new 2D chaotic system. Nonlinear Dyn. 104, 4505–4522 (2021). https://doi.org/10.1007/s11071-021-06472-6
Ibrahim, D.R., Abdullah, R., Teh, J.S.: An enhanced color visual cryptography scheme based on the binary dragonfly algorithm. Int. J. Comput. Appl. 44(7), 623–632 (2022). https://doi.org/10.1080/1206212X.2020.1859244
Khedr, W.I.: A new efficient and configurable image encryption structure for secure transmission. Multimed. Tools Appl. 79(23), 16797–16821 (2020). https://doi.org/10.1007/s11042-019-7235-y
Kumar, C.M., Vidhya, R., Brindha, M.: An efficient chaos based image encryption algorithm using enhanced thorp shuffle and chaotic convolution function. Appl. Intell. 52(3), 2556–2585 (2022). https://doi.org/10.1007/s10489-021-02508-x
Kumar, S., Srivastava, P.K., Srivastava, G.K., Singhal, P., Singh, D., Goyal, D.: Chaos based image encryption security in cloud computing. J. Discrete Math. Sci. Cryptogr. 25(4), 1041–1051 (2022). https://doi.org/10.1080/09720529.2022.2075085
Lai, Q., Zhang, H., Kuate, P.D.K., Xu, G., Zhao, X.W.: Analysis and implementation of no-equilibrium chaotic system with application in image encryption. Appl. Intell. 1–24 (2022). https://doi.org/10.1007/s10489-021-03071-1
Lan, R., He, J., Wang, S., Gu, T., Luo, X.: Integrated chaotic systems for image encryption. Signal Process. 147, 133–145 (2018). https://doi.org/10.1016/j.sigpro.2018.01.026
Lee, M.Z., Love, E., Narayan, S.K., Wascher, E., Webster, J.D.: On nonsingular regular magic squares of odd order. Linear Algebra Appl. 437(6), 1346–1355 (2012). https://doi.org/10.1016/j.laa.2012.04.004
Li, W., Wu, D., Pan, F.: A construction for doubly pandiagonal magic squares. Discret. Math. 312(2), 479–485 (2012). https://doi.org/10.1016/j.disc.2011.09.031
Liao, X., Yin, J., Chen, M., Qin, Z.: Adaptive payload distribution in multiple images steganography based on image texture features. IEEE Trans. Depend. Secure Comput. (2020). https://doi.org/10.1109/TDSC.2020.3004708
Liu, L., Gao, Z., Zhao, W.: On an open problem concerning regular magic squares of odd order. Linear Algebra Appl. 459, 1–12 (2014). https://doi.org/10.1016/j.laa.2014.06.046
Liu, Y., Zhang, J., Han, D., Wu, P., Sun, Y., Moon, Y.S.: A multidimensional chaotic image encryption algorithm based on the region of interest. Multimed. Tools Appl. 79, 17669–17705 (2020). https://doi.org/10.1007/s11042-020-08645-8
Miranda, D.O., Miranda, L., Bacelar, L.B.: Generalization of Dürer’s magic square and new methods for doubly even magic squares. J. Nepal Math. Soc. 3(2), 13–15 (2020). https://doi.org/10.3126/jnms.v3i2.33955
Nordgren, R.P.: On properties of special magic square matrices. Linear Algebra Appl. 437(8), 2009–2025 (2012). https://doi.org/10.1016/j.laa.2012.05.031
Norouzi, B., Seyedzadeh, S.M., Mirzakuchaki, S., Mosavi, M.R.: A novel image encryption based on hash function with only two-round diffusion process. Multimed. Syst. 20(1), 45–64 (2014). https://doi.org/10.1007/s00530-013-0314-4
Pappachan, J., Baby, J.: Tinkerbell maps based image encryption using magic square. Int. J. Adv. Res. Electric. Electron. Instrum. Eng. (IJAREEIE) 4, 6226–6232 (2015). https://doi.org/10.15662/ijareeie.2015.0407034
Patro, K.A.K., Acharya, B.: A novel multi-dimensional multiple image encryption technique. Multimed. Tools Appl. 79(19), 12959–12994 (2020). https://doi.org/10.1007/s11042-019-08470-8
Peng, F., Zhang, X., Lin, Z.X., Long, M.: A tunable selective encryption scheme for H. 265/HEVC based on chroma IPM and coefficient scrambling. IEEE Trans. Circuits Syst. Video Technol. 30(8), 2765–2780 (2019). https://doi.org/10.1109/TCSVT.2019.2924910
Rageed, H.A.H., Sadiq, A.M.: A new algorithm based on magic square and a novel chaotic system for image encryption. J. Intell. Syst. 29(1), 1202–1215 (2020). https://doi.org/10.1515/jisys-2018-0404
Raju, D., Eleswarapu, L., Pranav, M.S., Sinha, R.K.: Multi-level image security using elliptic curve and magic matrix with advanced encryption standard. Multimed. Tools Appl. 1–21 (2022). https://doi.org/10.1007/s11042-022-12993-y
Rani, N., Mishra, V.: Application of magic squares in cryptography. In: International Conference on Intelligent Vision and Computing, pp. 321–329. Springer (2021). https://doi.org/10.1007/978-3-030-97196-0_26
Rani, N., Mishra, V.: Behavior of powers of odd ordered special circulant magic squares. Int. J. Math. Educ. Sci. Technol. 53, 1044–1062 (2022). https://doi.org/10.1080/0020739X.2021.1890846
Rani, N., Sharma, S.R., Mishra, V.: Grayscale and colored image encryption model using a novel fused magic cube. Nonlinear Dyn. 108(2), 1773–1796 (2022). https://doi.org/10.1007/s11071-022-07276-y
Sadhukhan, D., Ray, S., Biswas, G., Khan, M.K., Dasgupta, M.: A lightweight remote user authentication scheme for IoT communication using elliptic curve cryptography. J. Supercomput. 77(2), 1114–1151 (2021). https://doi.org/10.1007/s11227-020-03318-7
Sahila, K., Thomas, B.: Secure digital image watermarking by using SVD and AES. In: Intelligent Data Communication Technologies and Internet of Things, pp. 805–818. Springer (2021). https://doi.org/10.1007/978-981-15-9509-7_65
Sasikaladevi, N., Geetha, K., Sriharshini, K., Aruna, M.D.: Radiant-hybrid multilayered chaotic image encryption system for color images. Multimed. Tools Appl. 78(9), 11675–11700 (2019). https://doi.org/10.1007/s11042-018-6711-0
Senthilnayaki, B., Venkatalakshami, K., Dharanyadevi, P., Nivetha, G., Devi, A. An efficient medical image encryption using magic square and PSO. In: 2022 International Conference on Smart Technologies and Systems for Next Generation Computing (ICSTSN), pp. 1–5. IEEE (2022)
Shuangyuan, Y., Zhengding, L., Shuihua, H.: An asymmetric image encryption based on matrix transformation. In: IEEE International Symposium on Communications and Information Technology, 2004. ISCIT 2004, vol. 1, pp. 66–69. IEEE, Sapporo, Japan (2004). https://doi.org/10.1109/ISCIT.2004.1412451
Singh, K.N., Singh, O.P., Baranwal, N., Singh, A.K.: An efficient chaos-based image encryption algorithm using real-time object detection for smart city applications. Sustain. Energy Technol. Assess. 53, 102566 (2022). https://doi.org/10.1016/j.seta.2022.102566
Sneha, P., Sankar, S., Kumar, A.S.: A chaotic colour image encryption scheme combining Walsh–Hadamard transform and Arnold–Tent maps. J. Ambient. Intell. Humaniz. Comput. 11(3), 1289–1308 (2020). https://doi.org/10.1007/s12652-019-01385-0
Sowmiya, S., Tresa, I.M., Chakkaravarthy, A.P.: Pixel based image encryption using magic square. In: 2017 International Conference on Algorithms, Methodology, Models and Applications in Emerging Technologies (ICAMMAET), pp. 1–4. IEEE, Chennai, India (2017). https://doi.org/10.1109/ICAMMAET.2017.8186634
Tedmori, S., Al-Najdawi, N.: Image cryptographic algorithm based on the Haar wavelet transform. Inf. Sci. 269, 21–34 (2014). https://doi.org/10.1016/j.ins.2014.02.004
Telem, A.N.K., Fotsin, H.B., Kengne, J.: Image encryption algorithm based on dynamic DNA coding operations and 3D chaotic systems. Multimed. Tools Appl. 80(12), 19011–19041 (2021). https://doi.org/10.1007/s11042-021-10549-0
Vidhya, R., Brindha, M., Gounden, N.A.: Analysis of zig–zag scan based modified feedback convolution algorithm against differential attacks and its application to image encryption. Appl. Intell. 50(10), 3101–3124 (2020). https://doi.org/10.1007/s10489-020-01697-1
Wang, J., Liu, L.: A novel chaos-based image encryption using magic square scrambling and octree diffusing. Mathematics 10(3), 457 (2022). https://doi.org/10.3390/math10030457
Wang, M., Yang, W.F., Xiong, X.W.: Application of information hiding technology based on matlab in military information security. In: Advanced Materials Research, vol. 546, 395–400. Trans Tech Publications Ltd (2012). https://doi.org/10.4028/www.scientific.net/AMR.546-547.395
Wang, S., Wang, C., Xu, C.: An image encryption algorithm based on a hidden attractor chaos system and the Knuth–Durstenfeld algorithm. Opt. Lasers Eng. 128, 105995 (2020). https://doi.org/10.1016/j.optlaseng.2019.105995
Wang, X., Liu, C.: A novel and effective image encryption algorithm based on chaos and DNA encoding. Multimed. Tools Appl. 76(5), 6229–6245 (2017). https://doi.org/10.1007/s11042-016-3311-8
Weber, G.: USC-SIPI image database: Version 4. dept elect eng-syst, univ southern california, los angeles, ca. Technical reports, USA, Tech Rep 244 (1993). http://sipi.usc.edu/database
Wootton, R.: Assessing telemedicine: a systematic review of the literature. BMJ 323(7312), 557–560 (2001). https://doi.org/10.1136/bmj.323.7312.557
Wu, Y., Zhou, Y., Saveriades, G., Agaian, S., Noonan, J.P., Natarajan, P.: Local Shannon entropy measure with statistical tests for image randomness. Inf. Sci. 222, 323–342 (2013). https://doi.org/10.1016/j.ins.2012.07.049
Yan X, Wang X, Xian Y (2021). Chaotic image encryption algorithm based on arithmetic sequence scrambling model and DNA encoding operation. Multimedia Tools Appl 80(7), 10949–10983. https://doi.org/10.1007/s11042-020-10218-8
Yavuz, E.: A novel chaotic image encryption algorithm based on content-sensitive dynamic function switching scheme. Opt. Laser Technol. 114, 224–239 (2019). https://doi.org/10.1016/j.optlastec.2019.01.043
Ye, G., Liu, M., Wu, M.: Double image encryption algorithm based on compressive sensing and elliptic curve. Alex. Eng. J. 61(9), 6785–6795 (2022). https://doi.org/10.1016/j.aej.2021.12.023
Yu, W., Liu, Y., Gong, L., Tian, M., Tu, L.: Double-image encryption based on spatiotemporal chaos and DNA operations. Multimed. Tools Appl. 78(14), 20037–20064 (2019). https://doi.org/10.1007/s11042-018-7110-2
Zhan, K., Wei, D., Shi, J., Yu, J.: Cross-utilizing hyperchaotic and DNA sequences for image encryption. J. Electron. Imaging 26(1), 013021 (2017). https://doi.org/10.1117/1.JEI.26.1.013021
Zhang, Y., Xiao, D., Shu, Y., Li, J.: A novel image encryption scheme based on a linear hyperbolic chaotic system of partial differential equations. Signal Process. Image Commun. 28(3), 292–300 (2013). https://doi.org/10.1016/j.image.2012.12.009
Zheng, F., Chen, C., Zheng, X., Zhu, M.: Towards secure and practical machine learning via secret sharing and random permutation. Knowl. Based Syst. 245, 108609 (2022). https://doi.org/10.1016/j.knosys.2022.108609
Zhong, W., Deng, Y.H., Fang, K.T.: Image encryption by using magic squares. In: 2016 9th International Congress on Image and Signal Processing, BioMedical Engineering and Informatics (CISP-BMEI), pp. 771–775. IEEE (2016). https://doi.org/10.1109/CISP-BMEI.2016.7852813
Zhou, M., Wang, C.: A novel image encryption scheme based on conservative hyperchaotic system and closed-loop diffusion between blocks. Signal Process. 171, 107484 (2020). https://doi.org/10.1016/j.sigpro.2020.107484
Zhou, Y., Bao, L., Chen, C.P.: Image encryption using a new parametric switching chaotic system. Signal Process. 93(11), 3039–3052 (2013). https://doi.org/10.1016/j.sigpro.2013.04.021
Zhou, Y., Li, C., Li, W., Li, H., Feng, W., Qian, K.: Image encryption algorithm with circle index table scrambling and partition diffusion. Nonlinear Dyn. 103(2), 2043–2061 (2021). https://doi.org/10.1007/s11071-021-06206-8
Ziemer, R.: Modulation. In: Meyers, R.A. (ed.) Encyclopedia of Physical Science and Technology, 3rd edn., pp. 97–112. Academic Press, New York (2002). https://doi.org/10.1016/B0-12-227410-5/00456-7
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rani, N., Mishra, V. & Sharma, S.R. Image encryption model based on novel magic square with differential encoding and chaotic map. Nonlinear Dyn 111, 2869–2893 (2023). https://doi.org/10.1007/s11071-022-07958-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-022-07958-7