Abstract
Steganography is one of the well-known data hiding methods, which is used in many security companies and government communications. In this technique, the various types of digital media can be used as a cover to hide secret information without impress the general form of them. Generally, key space and security are two important matters in most steganography methods, and they have the direct impact in proposed method’s security. Moreover, Chaotic maps have been used in many data hiding algorithms to increase the security and key space of proposed schemes. The main reasons of using chaotic maps in steganography methods are sensitivity to initial conditions and control parameters. This paper proposes a new steganography technique based on new 3d sine chaotic map. This map is used in embedding and extracting processes to increase the security of the proposed algorithm. Satisfactory performance, acceptable image distortion and stronger robustness against some attacks are the main features of proposed method, and they are shown in experimental results. Comparison with some existing method shows that the quality and performance of the proposed algorithm are good, and it has high security and acceptable robustness against cropping and salt & pepper attacks.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The most important issue in human’s life is extending the variety of digital data. This problem is significantly increased day by day. Generally, large amounts of data are used in government or private agencies, medical centers and military’s communications. On the other hand, each person has specific data, which include very important information about his/her private stuffs. However, it is a remarkable point to provide the security of these data as much as possible.
Usually, images, videos and audios are the most popular digital data, and more people use them. They are shared in many social networks and no one’s paying attention to their security [41]. Nevertheless, difference methods have been proposed to enhance the security of digital data. The categories of proposed methods are based on their applications and robustness against attacks. On the other hand, digital data are considered as a cover to hide important information or secret messages. For example, important messages hide inside the other data in military or security systems. This process did not change the quality of covers, and it is hard to detect actual messages by the others. Different types of methods have been proposed to hide important information which cryptography, watermarking and steganography are the most well-known methods. In cryptography techniques, data is usually shuffled with special keys, and only the sender and receiver are able to reconstruct the data with same keys [1, 45]. In these methods, data protects themselves from attacks. Many image encryption methods have been proposed [5, 12, 16, 24, 25] for digital data which some of them are discussed in the following. Zhang Leihong et al. proposed a high-performance cryptography for large images in [23]. In this method, the sender encrypted image with Fast Fourier Transform and then this image encrypted again by the system of compressive ghost imaging (CGI). Likewise, the receiver decrypted image by FFT and compressive sensing (CS). The results of simulation showed the performance, security and combination of CS, and FFT improved the security of proposed method against chosen-plain text attack, cipher-text attack and noise attack. In [20], Manish Kumar et al. suggested a new data encryption method based on position substitution, shuffling and a diffusion process. This method generated a 3D matrix for finding the position of a text symbol and then this position shuffled by encryption key. Matrix generation and position shuffling are done by logistic chaotic map. The integrity of cipher text checked by its parity in the encrypted form. Simulation results demonstrate remarkable robustness of the proposed scheme against statistical attacks. Ting Hu et al. proposed an image cryptography based on chaotic map and a DNA sequence in [15]. Proposed approach employed the Logistic-Sine system (LSS) in the coupled map lattice (CML) to generate sequences with better chaotic characteristics. This algorithm diffused images with unique chaotic key, and the insertion of DNA is used to confuse DNA encode. Experimental results demonstrated the acceptable speed of proposed method and good robustness against some recognized attacks. Akram Belazi et al. presented an image encryption scheme based on a chaotic map [4]. Proposed scheme used substitution-boxes, linear fractional transform and lifting wavelet transform to encrypt the sensitive parts of images. Proposed algorithm used dynamic keys instead of fixed key to control the encryption process and make any attacks impossible. Extensive experiments showed the high performance and great potential of proposed approach.
In watermarking methods, the watermarks are embedded inside digital media to protect them against many illegal manipulations. Usually, watermarks are the composition information of owners. Difference types of watermarking methods have been proposed in [3, 6, 34, 39, 40]. Chuan Qin et al. proposed a new fragile watermarking method based on overlapping strategy in [35]. This method used the block-wise mechanism and the pixel-wise for tampering localization and content recovery, respectively. This method embedded authentication bits into pixel’s least significant bits (LSB), then used these bits to find forged parts. The results of tests demonstrated the capability of proposed method in localizing forged areas. M. Moosazadeha and G. Ekbatanifard presented a digital image watermarking algorithm [28]. Proposed technique used YCoCg-R color space to increase the robustness of the suggested algorithm against various attacks. Proposed method also utilized discrete cosine transform and the coefficient of relationship in embedding process. In this method, the blocks’ complexities in the host image are calculated to select embedding blocks, and increased the resistance of the proposed scheme against JPEG compression. Comparison with similar techniques showed good performance of proposed method in imperceptibility, robustness and capacity of proposed approach. L. Chen and J. Zhao suggested a new blind watermarking scheme for depth-image-based rendering (DIBR) 3D images in [8]. They used contourlet transform in embedding and extracting processes. The simulation results illustrated that the proposed method has acceptable robustness against noise addition, image compression, geometric attacks and good performance in terms of depth image variation. Zhuhong Shao et al. presented a robust watermarking technique based on chaotic map and orthogonal Fourier-Mellin moments. This method contained ownership registration phase and verification phase. In this method, a binary future of image is calculated with orthogonal Fourier-Mellin moments, and chaotic map generated the verification of image. Experimental results illustrated acceptable validity and security of proposed method against difference attacks.
Steganography is the art of hiding a secure message inside different types of digital media. The actual challenge in this technique is hiding important data in a cover without destroy any parts of cover. Generally, many special steganography methods have been proposed for different messages and covers [21, 22, 26, 33, 44]. Images are the most popular covers in the steganography techniques. Generally, spatial domain and transform domain steganography are the most well-known techniques in image steganography methods. The spatial domain schemes embed the bits of secure message in cover bits directly [7, 30, 31]. Discrete Cosine Transform (DCT), Discrete Fourier Transform (DFT), and Discrete Wavelet Transform (DWT) are the most well-known transforms, that used in transform domain methods. These transforms apply on cover and stego images to improve the visual quality of methods in embedding and extracting processes. Generally, proposed approaches used difference way to enhance the robustness. For example, some schemes use transforms, chaos maps or combined methods. M. Ghebleh and A. Kanso introduced a steganography method based on 3D chaotic cat map and lifted discrete wavelet transforms [11]. This method used Sweldens lifting scheme to ensure integer-to-integer transform. The experimental results demonstrated the efficiency and flexibility of proposed method. Mehdi Hussain et al. presented a new data hiding method for digital images in [17]. Proposed method used the difference values between pixels in each block to determine the selection of parity-bit pixel value difference (PBPVD) and improved rightmost digit replacement (iRMDR). Experimental results determined good visual quality and high robustness against RS and histogram analysis attacks. R. González et al. suggested a new method for images steganography in [27]. This paper used Bernoulli chaotic maps and the least significant bit technique in embedding and extracting processes. In this method, secure message bits are encrypted, and they are embedded in random RGB channels. The experimental results showed good improvement in the image fidelity, and peak signal to noise ratio (PSNR).
The remaining part of this paper is organized as follows: The chaotic map is described in Section 2. Section 3 presents proposed steganography method. Performance evaluation and experimental results of the proposed method are presented in Section 4. The comparison results of proposed method with other algorithms are investigated in Section 5. Finally, Section 6 concludes this paper.
2 Extraction of 3D sine map
Sensitivity to initial conditions and control parameters are the main features of chaotic maps. These features have been used in many security systems and methods. Generally, to create chaotic behaviors the simple linear or non-linear equations are used. For example, logistic map is one of the well-known chaotic map. This map is very simple, fast and it has some unique properties. Sine map is another simple map that has chaotic behaviors and it is very similar to logistic map [14]. The classical form of this map is defined by:
where μ > 0 and it is control parameter, x0 is initial condition and it is in interval [0,1]. This map has a control keys and one dimension, so it isn’t good to use in color images. In order to increase the key space of this map and its dimension, this paper introduced a new three dimensional sine map. In the first steps, the ϕ1, ϕ2 and ϕ3 functions are defined by following equation:
In the next step, δ, η and κ control keys are added to increase the key space. New functions are calculated by:
Modulo operation is used in the next step to generate results in interval [0,1]. Finally, the main formula of new three dimensional sine map is defined by:
where x0,y0 and z0 are initial conditions and they are in interval [0,1]. δ, η and κ are control parameters and they are in interval [1,4]. The simulation results of map show that the power 3 of control keys generate better pseudo random numbers. Figure 1 illustrates the time series of xi, yi and zi (i = 1,…,150) sequences. The visual representation of attractor for 3d sine map is shown in Fig. 2. Histogram analysis and bifurcation diagram are shown in Fig. 3. These figures show the chaotic behavior of 3d sine map.
Cross correlation and auto correlation are the other tests which used to evaluate the generated sequences by 3d sine map. Cross correlation is the correlations between two sequences, and it shows the best interval for these sequences. The values of this test are between 1 and -1 in standard form. Auto correlation is the correlations between a sequence and itself. Figure 4 shows the results of cross correlation between sequences xi and yi, and auto correlation for sequence xi (i = 1,…,2000).
ENT, NIST and DIEHARD test suites are the most well-known statistical tests. These tests have been developed to show the randomness properties of pseudo-random number generators. This paper use these tests to investigate the randomness of 3d sine map. Three sequences are generated for xi, yi and zi (i = 10000000), separately. These sequences are saved as bin files and used in ENT, NIST and DIEHARD test suits. The results of these test suites are shown in Tables 1, 2, and 3.
3 Proposed steganography method
This section presents a new digital image steganography. The main processes of proposed steganography are embedding and extracting processes. Embedding process contains seven phases. In phase one, a cover image with size M × N × K and secure message with size a × b enter in the algorithm. Phase two applies integer wavelet transform on RGB channels of cover image and puts the LL sub bands on matrix I. Blocking process is started in phase three and algorithm divides matrix I into 16 × 16 non-overlapping blocks. The block-wise permutation is performed in phase four and then algorithm puts the permuted blocks in matrix P. Permutation process is used to increase the security of proposed approach. In phase five, 3d sine map uses keys 1 (x0,y0, z0, δ, η and κ) to generate random decimal numbers by (4) and algorithm changes these numbers to integer form by (5) and key 2 (ω,σ and 𝜃). In phase six, the output numbers of (5) are used as a coordinate and color channel in matrix P to embed the bits of secure message. These steps (phase five and phase six) are repeated until the proposed algorithm embeds all bits of hidden message. Proposed algorithm performs the inverse of block-wise permutation in phase seven and finally, algorithm applies the inverse of integer wavelet transform to generate stego image. The steps of embedding process are shown in Fig. 5. Proposed algorithm uses a mask matrix to prevent selecting pixels that have already been embedded.
Extracting process includes six phase, which in phase one, stego image enters in extracting algorithm. Phase two applies integer wavelet transform on RGB channels of stego image and puts the LL sub bands on matrix I. In phase three, extracting algorithm divides matrix I into 16 × 16 non-overlapping blocks. The block-wise permutation is performed in phase four and algorithm puts the permuted blocks in matrix P. Proposed scheme permute the blocks of stego image to find the exact location of embedded pixels. In phase five, 3d sine map uses keys 1 to generate random decimal numbers by (4) and changes these numbers to integer form by (5) and keys 2 (Keys 1 and Keys 2 are same in embedding and extracting processes). In phase six, the output numbers of (5) are used as a coordinate and color channel in matrix P to extract the bits of secure message. Phase five and phase six are repeated until all bits of the secure message extracted. The extracting process is finished by generating secure message. Figure 6 demonstrates the extracting process of proposed technique. Mask matrix is used in extracting algorithm to avoid selecting pixels that have already been extracted.
4 Experimental results
The important issues in proposing new methods are examining the results of tests and the robustness of proposed methods against attacks. This paper uses some standard pictures like Lena, Peppers and Baboon with different hiding messages to evaluate the proposed method in embedding processes. The results of tests are calculated by using AMD Phenom II x4 processor, 8GB RAM, Linux Ubuntu 16 x64 OS and MATLAB R2016b x64 software.
4.1 PSNR and SSIM measures
Peak Signal to Noise Ratio (PSNR) and structural similarity index (SSIM) are two well-known measures, which used to compare differences between original images and the changed form of them. The results of PSNR show the visual quality of cover images after embedding process. PSNR is calculated by following equation:
where MAXI is the value of possible pixel in the cover images. MSE is the mean square error and it is defined by:
where C and St are cover image and stego image, respectively. m and n are the size of cover image. SSIM predicts the perceived quality of images and measures the similarity of cover image and stego image. The results of SSIM are defined by:
where σx and σy are the mean intensities of x and y, \({\sigma _{x}^{2}}\) and \({\sigma _{y}^{2}}\) are the variances of x and y, σxy is the co-variance of x and y, respectively. The averages of x and y are μy and μx, C1 and C2 are the variables to stabilize the division with weak denominator. The results of PSNR and SSIM measures after embedding different size of messages are shown in Table 4. This table also demonstrates the number of channels (RGB) that used in embedding process. The sizes of channels are almost same and show the proposed technique uses all channels of cover image in embedding secure messages. Figure 7 illustrates the PSNR and SSIM measures of 100 cover images after embedding secure message.
4.2 Robustness against attacks
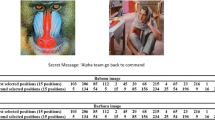
The considerable parameter of proposing a steganography method is robustness against attacks. Generally, steganography hides a secure message in cover image and it can happen that some parts of cover image destroyed accidentally or changed by the attackers. According to these problems, proposed method should be resisted against any destruction. To test the robustness of proposed method, this section first embeds Baboon (256 × 256) image as a secure message in Lena and Peppers images, then apply cropping attack and salt & peppers noise on stego images. Figure 8 shows the reconstructed secret message after these attacks. This paper uses SSIM, BER and NCC measures to calculate the destruction of secure message after extracting it from attacked stego images. The results of these measures are shown in Table 5. In this table cover images are 512 × 512 and message (Baboon) is 256 × 256. According to the results, proposed method can be resist against some image processing attacks.
Extracted Baboon secret message from stego images after Cropped and Salt & peppers noise attacks, a Lena 1024 × 1024, b Peppers 512 × 512, c Crop 100 × 100, d Extracted secure image after crop attack, e Salt & peppers noise (parameter = 0.02), f Extracted secure image after salt & peppers noise attack
4.3 Histogram analysis
Image histogram is an useful tool in image processing field that used to show the number of pixels in images and their intensity values. In images steganography, histogram is used to investigate cover images after embedding process and it shows the distribution of secure message in cover images’ channels. This paper embeds 77244 bits and 9744 bits in two different sizes of cover image to compare the results of histogram. The comparison results are shown in Fig. 9. This figure shows that the histograms of each cover image are very similar with their stego images and the distortion of Lena image is acceptable after embedding different size of secure messages.
4.4 Key space analysis
Key space is the important part of encryption methods and shows the capability of methods against brute force attack. The key space of proposed algorithm contains two different parts. First part is the keys which used in the new 3d sine map. The initial conditions of this map are three double keys (x0,y0,z0) and the size of each initial key is 10− 14. The computational precision of control parameters (δ,η and κ) are 3 × 10− 14. Therefore, the general key space of 3d sine map is 3 × 46 + 3 × 48 = 282 bits. Second part of key space is the control parameters (ω,σ and 𝜃) which used in (5). The total key space of these parameters is 138 bits. According to these parts, we can conclude the main key space of proposed steganography is 282 + 138 = 420 bits. This key length is large enough to defeat brute force attacks.
5 Comparison with similar methods
This article selects two types of existing method to compare with proposed steganography. First types of articles choose color images from Internet and public dataset like USC-SIPI-ID [9]. Table 6 demonstrates the comparison results of PSNR and SSIM between proposed method and existing method. In this table message size is 8 kb. Seconed types of methods have used transforms and gray scale images in embedding and extracting process. The grayscale images that used for comparison are in UCID database [37]. Table 7 illustrates the comparison results of PSNR, SSIM and NCC between proposed method and similar methods. This paper compares the key space of proposed methods with similar steganography methods in Table 8. The results of these tables show that the proposed method has good performance after embedding secure message in two types of images and key space of presented algorithm is higher than some existing methods.
6 Conclusion
This paper proposed a new transform domain image steganography method based on 3d sine chaotic map. The chaotic map enhances the security of proposed steganography and increases the key space. The pixels of cover image are selected by the outputs of chaotic map to embed secure message bits. Bifurcation diagram and histogram analysis show the chaotic behavior of 3d sine map and the results of statistical tests present the randomness of this map. Cross correlation and auto correlation show the best interval for generated sequences. However, proposed algorithm uses integer wavelet transforms in embedding and extracting processes, and it is applied on cover and stego images. This transform uses the integer coefficients to increase the capability of proposed method in extracting process. Experimental results show acceptable imperceptibility of proposed method based on PSNR and SSIM measures. Proposed scheme also has large key space and good robustness against some image-processing attacks. Comparison results between proposed algorithm and some existing schemes show that the proposed steganography has good performance and quality in embedding and extracting processes.
References
Akhavan A, Samsudin A, Akhshani A (2017) Cryptanalysis of an image encryption algorithm based on dna encoding. Opt Laser Technol 95:94–99
Bailey K, Curran K (2006) An evaluation of image based steganography methods. Multimed Tools Appl 30(1):55–88
Barani MJ, Ayubi P, Jalili F, Valandar MY, Azariyun E (2015) Image forgery detection in contourlet transform domain based on new chaotic cellular automata. Secur Commun Netw 8(18):4343–4361
Belazi A, El-Latif AAA, Diaconu A-V, Rhouma R, Belghith S (2017) Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms. Opt Lasers Eng 88:37–50
Chai X (2017) An image encryption algorithm based on bit level brownian motion and new chaotic systems. Multimed Tools Appl 76(1):1159–1175
Chakraborty S, Chatterjee S, Dey N, Ashour AS, Hassanien AE (2017) Comparative approach between singular value decomposition and randomized singular value decomposition-based watermarking. In: Intelligent techniques in signal processing for multimedia security. Springer, pp 133–149
Chen X, Gao G, Liu D, Xia Z (2016) Steganalysis of lsb matching using characteristic function moment of pixel differences. China Commun 13(7):66–73
Chen L, Zhao J (2017) Robust contourlet-based blind watermarking for depth-image-based rendering 3d images. Signal Process Image Commun 54:56–65
Cheng W-C, Pedram M (2004) Chromatic encoding: a low power encoding technique for digital visual interface. IEEE Trans Consum Electron 50(1):320–328
El Hennawy HM, Omar AE, Kholaif SM (2015) Lea: link encryption algorithm proposed stream cipher algorithm. Ain Shams Eng J 6(1):57–65
Ghebleh M, Kanso A (2014) A robust chaotic algorithm for digital image steganography. Commun Nonlinear Sci Numer Simul 19(6):1898–1907
Ghebleh M, Kanso A, Stevanović D (2017) A novel image encryption algorithm based on piecewise linear chaotic maps and least squares approximation. Multimedia Tools and Applications 77(6):7305–7326
Gutub AA-A, et al. (2010) Pixel indicator technique for rgb image steganography. J Emerg Technol Web Intell 2(1):56–64
Hilborn RC (2000) Chaos and nonlinear dynamics: an introduction for scientists and engineers, Oxford University Press on Demand, Oxford
Hu T, Liu Y, Gong L-H, Guo S-F, Yuan H-M (2017) Chaotic image cryptosystem using dna deletion and dna insertion. Signal Process 134:234–243
Hu T, Liu Y, Gong L-H, Ouyang C-J (2017) An image encryption scheme combining chaos with cycle operation for dna sequences. Nonlinear Dyn 87(1):51–66
Hussain M, Wahab AWA, Ho AT, Javed N, Jung K-H (2017) A data hiding scheme using parity-bit pixel value differencing and improved rightmost digit replacement. Signal Process Image Commun 50:44–57
Jassim FA A novel steganography algorithm for hiding text in image using five modulus method, arXiv:1307.0642
Kanan HR, Nazeri B (2014) A novel image steganography scheme with high embedding capacity and tunable visual image quality based on a genetic algorithm. Expert Syst Appl 41(14):6123– 6130
Kumar M, Kumar S, Budhiraja R, Das M, Singh S (2017) A cryptographic model based on logistic map and a 3-d matrix. J Inf Secur Appl 32:47–58
Lalitha R, Srinivasu PN (2017) An efficient data encryption through image via prime order symmetric key and bit shuffle technique. In: Computer communication, networking and internet security. Springer, pp 261–270
Lee C-F, Weng C-Y, Chen K-C (2017) An efficient reversible data hiding with reduplicated exploiting modification direction using image interpolation and edge detection. Multimed Tools Appl 76(7):9993–10016
Leihong Z, Zilan P, Luying W, Xiuhua M (2016) High-performance compression and double cryptography based on compressive ghost imaging with the fast fourier transform. Opt Lasers Eng 86:329–337
Li C, Luo G, Qin K, Li C (2017) An image encryption scheme based on chaotic tent map. Nonlinear Dyn 87(1):127–133
Li Y, Gai K, Qiu L, Qiu M, Zhao H (2017) Intelligent cryptography approach for secure distributed big data storage in cloud computing. Inf Sci 387:103–115
Malik A, Sikka G, Verma HK (2017) An image interpolation based reversible data hiding scheme using pixel value adjusting feature. Multimed Tools Appl 76(11):13025–13046
Martínez-González RF, Díaz-Méndez JA, Palacios-Luengas L, López-Hernández J, Vázquez-Medina R (2016) A steganographic method using bernoulli’s chaotic maps. Comput Electr Eng 54:435– 449
Moosazadeh M, Ekbatanifard G (2017) An improved robust image watermarking method using dct and ycocg-r color space. Optik-Int J Light Electron Opt 140:975–988
Muhammad K, Ahmad J, Sajjad M, Zubair M Secure image steganography using cryptography and image transposition, arXiv:1510.04413
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW (2016) A novel magic lsb substitution method (m-lsb-sm) using multi-level encryption and achromatic component of an image. Multimed Tools Appl 75(22):14867–14893
Muhammad K, Ahmad J, Rehman NU, Jan Z, Sajjad M (2017) Cisska-lsb: color image steganography using stego key-directed adaptive lsb substitution method. Multimed Tools Appl 76(6):8597–8626
Parah SA, Sheikh JA, Hafiz AM, Bhat GM (2014) Data hiding in scrambled images: a new double layer security data hiding technique. Comput Electr Eng 40 (1):70–82
Parah SA, Sheikh JA, Assad UI, Bhat GM (2017) Hiding in encrypted images: a three tier security data hiding technique. Multidim Syst Sign Process 28 (2):549–572
Parah SA, Sheikh JA, Loan NA, Bhat G (2017) A robust and computationally efficient digital watermarking technique using inter block pixel differencing. In: Multimedia forensics and security. Springer, pp 223–252
Qin C, Ji P, Zhang X, Dong J, Wang J (2017) Fragile image watermarking with pixel-wise recovery based on overlapping embedding strategy. Signal Process 138:280–293
Sajasi S, Moghadam A-ME (2015) An adaptive image steganographic scheme based on noise visibility function and an optimal chaotic based encryption method. Appl Soft Comput 30:375–389
Schaefer G, Stich M (2004) Ucid: an uncompressed color image database. Storage Retr Methods Appl Multimed 5307:472–480
Su Q, Niu Y, Zou H, Zhao Y, Yao T (2014) A blind double color image watermarking algorithm based on qr decomposition. Multimed Tools Appl 72 (1):987–1009
Su Q, Chen B (2017) Robust color image watermarking technique in the spatial domain. Soft Comput 22(1):91–106
Su Q, Wang G, Zhang X, Lv G, Chen B (2017) An improved color image watermarking algorithm based on qr decomposition. Multimed Tools Appl 76 (1):707–729
Subhedar MS, Mankar VH (2014) Current status and key issues in image steganography: a survey. Comput Sci Rev 13:95–113
Subhedar MS, Mankar VH (2016) Image steganography using redundant discrete wavelet transform and qr factorization. Comput Electr Eng 54:406–422
Thabit R, Khoo BE (2015) A new robust lossless data hiding scheme and its application to color medical images. Digit Signal Process 38:77–94
Valandar MY, Ayubi P, Barani MJ (2017) A new transform domain steganography based on modified logistic chaotic map for color images. J Inf Secur Appl 34:142–151
Xie EY, Li C, Yu S, Lü J (2017) On the cryptanalysis of fridrich’s chaotic image encryption scheme. Signal Process 132:150–154
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
All authors declare that they have no conflict of interest.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Valandar, M.Y., Barani, M.J., Ayubi, P. et al. An integer wavelet transform image steganography method based on 3D sine chaotic map. Multimed Tools Appl 78, 9971–9989 (2019). https://doi.org/10.1007/s11042-018-6584-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6584-2