Abstract
In this paper, a novel image encryption algorithm based on the fractional-order chaotic system and compression sensing algorithm is proposed. Firstly, the dynamical characteristics of the fractional-order chaotic system are analyzed. The hardware circuit is designed in and realized on the DSP. Secondly, the block feedback diffusion algorithm is applied to this encryption scheme. The elements of the cipher block are decided by the front of the cipher block and the plain-text block. In this algorithm, it needs to be emphasized that the scrambling calculation and the diffusion operation are carried out simultaneously. The simulation results show that the algorithm can effectively encrypt digital images. Finally, the security analysis demonstrates the security and the effectiveness of the proposed encryption algorithm.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Because of the wide application of the streaming media, many multimedia data are delivered in the two different terminals. Those multimedia data include the image, video, and audio. Especially, the image data is an important data format in militarily, medical, and industrial areas. For example, a personal picture can illustrate the secret information of this person like health condition and personal habit [18, 46]. Therefore, the image files have the risk of unauthorized access. The protection scheme of the image files has become a serious problem. The image files are different with the text message. It is a typical two-dimensional data. Therefore, the data capacity of image is huge and the spatial distribution is complex. It is a disputed question that the encryption standard of text message is whether suitable to protect image data [5, 6, 18]. Besides, the image files without compression operation can occupy a huge resource of communication channels. These situations make the encryption algorithm needs to improve the security level of multimedia data transmission.
The chaotic systems have the properties of unpredictability, ergodicity, and sensitivity to their parameters. Therefore, chaotic systems have been widely used in different applications. In the security application area, most research objects are adopted different kinds of chaotic systems. These encryption schemes have wonderful security performance with a low calculation complexity [1, 4, 18, 23, 26, 27, 45]. Moreover, the DNA encode theory is applied to the chaotic-based encryption scheme [2, 22, 24, 39, 43]. The fractional-order chaotic system has more complex dynamical characteristics compared with the integer-order chaotic system [11, 16, 17, 25, 31, 32]. In the encryption algorithm, the order of the system can expend the key space of the algorithm. Also, the chaotic sequences of fractional-order chaotic system are random and the high-randomness sequence can cover the plain-text information more effectively. The related research can prove the fractional-order chaotic system has flexible and good characteristics in the encryption algorithm [21, 22, 34,35,36, 43].
The other problem is the size of the multimedia files. Firstly, the number of multimedia files in real-time transmitting is large. Secondly, it has to strictly comply with the law of sampling for the uncompressed multimedia data. Therefore, the resource of the signal channel is short and the transmitting cost is huge. The compression sensing technology is a new approach in the signal sampling theory. This scheme can generate the measured result by the measurement matrix. The size of the result is less than the original signal. It can save the storage space in the signal channel and reduce the transmitting cost. Moreover, the chaotic system is applied to build the measured matrix in the compressive sensing algorithm. This method can improve the security of transmission and compress the image file at the same time [7, 13, 30, 38, 40].
Based on the advantages of compression sensing, an image encryption algorithm based on the fractional-order chaotic system and compression sensing is proposed. The encryption algorithm is a combination of compression and encryption, the discrete chaotic system is applied to compress the image. The encryption scheme depends on the fractional-order chaotic system. The sequences of the fractional-order chaotic system are obtained by the CADM algorithm [15, 20, 25]. The contributions of this algorithm are listed as follows
-
1.
Two different and independent chaotic systems are applied into the flow of compression and encryption. The final cipher image cannot be decoded without the complete initial condition.
-
2.
The scrambling operation and diffusion calculation are carried out simultaneously. The purpose of this structure is to cover the statistical information of the plain-text image and change the arrangement of the pixel at the one round operation.
-
3.
The secret key has two parts: the public key and the private key. The compression rate (CR) is public in the processing of transmission. The parameters of the chaotic system are the private key in this algorithm.
-
4.
The new critical scores of the difference attack analyses are adopted in the security analyses [3, 10, 14, 42, 44].
The rest parts of this paper are structured as follows. The basic theory of compression sensing and the dynamical characteristics analyses of a fractional-order chaotic system are carried out in Sect. 2. The detail of the encryption algorithm and decryption workflow is described in Sect. 3. The encryption and decryption image is shown in Sect. 4. The results of performance analyses are given in Sect. 4 too. The important conclusion is given in Sect. 5.
2 Preliminaries
2.1 The basic theory of compression sensing
The basic structure of the compression sensing includes the three parts: the measurement matrix, the method of sparse signal, and the reconstruction algorithm. The complete flow of compression sensing can be presented as
where x represents the original signal. The matrix \(\psi \) is the orthogonal transform matrix. This matrix is applied to the sparse the original signal matrix. Therefore, this matrix can be called the sparse base matrix. The common sparse method includes the discrete cosine transform (DCT) algorithm and the discrete wavelet transform (DWT) algorithm. The matrix \(\phi \) is called the measurement matrix. The size of the measurement matrix is \(M \times N\) and M is less than the pixel amount N in the row or column.
The reconstruction algorithm can present the solution of the optimization \(l_{0}\) problem. This problem can be denoted as
where \(\Theta =\phi \cdot \psi \). The common reconstruction algorithms are orthogonal matching pursuit (OMP) algorithm, subspace pursuit (SP) algorithm and smoothed \(\ell _{0}\) norm (SL0) algorithm. The smoothed \(\ell _{0}\) (SL0) algorithm is applied in this encryption algorithm. The sparsest solutions are obtained by an under determined system of linear equations \(As = x\). Moreover, this algorithm tries to directly minimize the \(\ell _{0}\) norm [28, 29].
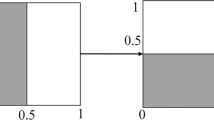
In this encryption algorithm, the sparse method is adopted the DWT scheme. The measurement matrix is constructed by the discrete chaotic system. To reduce the relevance among the column vectors, the first element of column vector is set \(\hat{\Phi (i,1)}=\lambda \cdot \Phi (i-1,1)\). The final measurement matrix is generated by
2.2 The dynamical characteristics of fractional-order chaotic system
The design concept of random-number generator in this encryption algorithm is based on the fractional-order Jerk chaotic system. The chaotic sequences are obtained by the CADM algorithm. Firstly, the integer-order Jerk chaotic system is present in Eq. (4)
Based on the Caputo definition [15], the fractional-order system can be rewritten as
At the first, Eq. (5) needs to be divided into the two blocks: the linear terms and the nonlinear terms
According to the calculation flow of CADM, the first five Adomian polynomials of the nonlinear term are calculated as follows:
The initial conditions \(x_0\) is equal to [\(x_1(t^+_ 0)\) \(x_2(t^+_ 0)\) \(x_3(t^+_ 0)\)]. Therefore, the first item is:
Letting \(x^0= c^0 = [c^0_ 1 c^0_ 2 c^0_ 3\)]. The second term is:
where the step size \(h=t-t_0\). Setting
then \(x^1\) will be represented as \(x^1_ i = \frac{c^1h^q}{q}\) (\(i=1,2,3\)). Similarly, the other four coefficients of the rest terms are:
So, the numerical solution of the FONJCS with six terms is
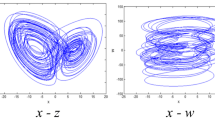
The system initial conditions are [1.9,0,0]; the system parameters are [a c d k q] = [1,0.5,\(2.72165*10^{-4}\),1,0.9]. The phase diagrams are shown in Fig. 1. Set the system parameters as \(a=1\), \(c=0.5\), \(k=1\), \(q=0.9\). The variable \(b\in [0.85,2.85]\). The Lyapunov exponent spectrum and the bifurcation diagram are shown in Fig. 2. This system suddenly transforms into two coexisting attractors when the parameter b = 0.965. Therefore, the curves of the max Lyapunov exponent and bifurcation diagram show the properties of two coexisting attractors. The widely chaotic range can be illustrated by Fig. 2a. Figure 2b can prove that this system has widely chaotic range from the max Lyapunov direction.
The DSP development board is selected as hardware platform to implement the fractional-order system in this paper. The parameters of six different type attractors are listed in Table 1. The experiment suit and the application environment are shown in Fig. 3. The simulation results are shown in Fig. 4.
2.3 The dynamical characteristics of the discrete chaotic system
The measurement matrix is obtained by the discrete chaotic system. Firstly, the size of the measurement matrix needs to control in a certain size. This measure can save the resource of the signal channel. The discrete chaotic system has low calculation cost and complex dynamical behaviors. It can satisfy this request. Moreover, the sequences of the discrete chaotic system have uniform distribution and zero correlation. Therefore, the discrete chaotic system has good promising applications in the encryption algorithm [4, 9, 44].
The 3D-SIMM system is a high-dimension (HD) discrete chaotic system. The mathematical model is
The phase diagram is shown in Fig. 5a. When the system parameters [a, b, c]=[1,\(2 \pi \),11.5], this system is in chaotic state. The 3D-SIMM has a wide hyper-chaotic range when variable \(a \in [0.33,5]\). The Lyapunov spectrum and bifurcation diagram are shown in Fig. 5b, c. It is obvious that this system has complex dynamical characteristics and a wide chaotic range [23]. Firstly, the hyper-chaotic state can maintain in the whole parameter range. This property is illustrated by Fig. 5c. Secondly, Fig. 5b can prove that this assumption is correct from other side. Therefore, the sequences of this system are applied to construct the measurement matrix.
3 The description of encryption algorithm
The discussion point of this section is the concrete steps of the encryption algorithm. The flow is shown in Fig. 6.
The order of encryption is subject to the compression–encryption. In the encryption operation, the scrambling operation and the diffusion calculation are going at the same time. Besides, the encryption algorithm is based on the block cipher theory. Therefore, the length of the secret sequence is certain. It can reduce the time cost in chaotic sequences calculation. Moreover, the elements of the cipher block are dependent on the front of the cipher block, the plain-text block, and the chaotic sequences.
3.1 The flow of encryption algorithm
-
1.
Sparse the image matrix. The sparse signal matrix is come from the plain-text image by DWT algorithm. The size of sparse signal matrix is equal to \(H \times W\), where H presents the number of rows, W is the number of columns.
-
2.
Set the compression rate (CR). The measurement matrix is generated by the discrete chaotic system. The size of the measurement matrix is subject to the number of CR. The final measurement matrix is obtained by Eq. (3). This equation is used to reduce the relevance among the column vectors.
-
3.
Compress the image matrix. The size of the new image matrix is equal to \(M \times W\), where the number of M is equal to \(CR \times H\). The elements of the new image matrix need to uniformization. The method of uniformization is
$$\begin{aligned} {\left\{ \begin{array}{ll} Max = max(max(P) \\ Min = min(min(P)) \\ Q = round(255 * (P - Min) / (Max - Min)) \\ \end{array}\right. }\qquad \end{aligned}$$(17)where P is the new image matrix, Q is the compressed image.
-
4.
The secret sequence is generated by the fractional-order Jerk chaotic system. The length of sequence is equal to the row vectors. The secret sequence is obtained by
$$\begin{aligned} S=\lfloor (pow2(16)*Y) \rfloor \bmod L, \end{aligned}$$(18)where the L is present for the max gray level in the image matrix. Y is a chaotic sequence obtained by the fractional-order Jerk chaotic system. Besides, the scrambling matrix is generated by a sort chaotic sequence.
-
5.
The size of cipher image is equal to \(H1 \times W1\). The encryption operation contains two directions: the blockchain diffusion and the elements scrambling in the group. These directions can be presented by one equation group as follows
$$\begin{aligned} {\left\{ \begin{array}{ll} MDF(i) = P(Index1(i)) + S1(i) + S2(i)\\ MDF(i) = MDF(i) \bmod L\\ Cipher image(n,:) = MDF \qquad n = 1 \end{array}\right. }. \end{aligned}$$(19)The front matrix of diffusion (MDF) is start block in the chain diffusion. The secret sequences S1 and S2 respond to the change value of the pixel. The Index1 is generated by sorting the chaotic sequence. This sequence is applied to disorder the arrangement of pixel in group. The final results of MDF are embed into the first row of cipher image.
$$\begin{aligned} {\left\{ \begin{array}{ll} MD(i)=MD1(Index1(i))+MD2(Index2(i)) \\ MD(i)=MD(i)+4*S1(i)+5*S2(i) \\ MD(i)=MD(i) \bmod L \\ Cipher image(n,:) = MD \qquad n \in [2, \cdots , H1] \end{array}\right. }. \end{aligned}$$(20)The matrix of diffusion (MD) is a basic unit in the encryption operation. The size of MD is equal to the column vector of plain-text image. The plain-text sequences P are named as MD1. The front cipher blocks C are named as MD2. Therefore, the value of the cipher group depends on the plain-text block, the secret sequence, and the front block of cipher image. The pixel of plain-text and the front cipher sequence are selected randomly. The select principle is subject to the Index matrix.
3.2 The flow of decryption algorithm
The decryption algorithm is inverse flow compare with the encryption algorithm. The flow is shown in Fig. 7.
Firstly, the value and order of the cipher matrix are recovered by the block diffusion and the elements scrambling. The recovered matrix is regrouped by the divide algorithm. The reconstructed image is obtained by the smoothed \(\ell _{0}\) algorithm and the inverse DWT transform.
-
1.
Recover the value of pixel. The principle of recovery is subject to Eqs. (21–22).
$$\begin{aligned} {\left\{ \begin{array}{ll} MRF(Index1(i))=MDF(i)-S1(i)-S2(i)\\ MRF(Index1(i))=MRF(Index1(i)) \bmod L\\ \end{array}\right. }, \end{aligned}$$(21)Equation (21) is inverse algorithm of Eq. (19). The inverse algorithm of Eq. (20) as follows
$$\begin{aligned} {\left\{ \begin{array}{ll} MR(Index1(i))=MR1(i)-MR2(Index2(i)) \\ -(4*S1(i)+5*S2(i)) \\ MR(Index1(j))=MR(Index1(j)) \bmod L\\ \end{array}\right. }. \end{aligned}$$(22) -
2.
Inverse uniformization of image matrix. The method of inverse uniformization as follows
$$\begin{aligned} R=(Q*(Max-Min))/255 + Min, \end{aligned}$$(23)where the matrix R is recover image matrix.
-
3.
Reconstruct the original image pixel. The smoothed \(\ell _{0}\) (SL0) algorithm is applied to reconstruct pixel of image matrix.
-
4.
Inverse the DWT and obtain the final decrypted image.
4 The performance analysis
4.1 Simulation result
This section to test the decoded image is similar to the plain-text image, where some classical images are selected as the test images. The encryption parameters contain two parts: (1) the parameters of the chaotic system; (2) the initial parameters of the chaotic system. The structure of the secret key is listed in Table 2. The encryption and decryption results are shown in Fig. 8.
4.2 The key analyses
The secret key is decided the decoded image is correct. Also, the secret key can affect the security of the cipher image. Therefore, the security of secret key is an important character of encryption algorithm. This subsection has two directions need to discuss.
4.2.1 The key space analysis
The first discussion point is the key space. The space of secret key should approach or larger than \(2^{100}\) [5, 8, 12]. The large key space makes sure the cipher image has the ability to resist the brute-force attack. The key space of the proposed algorithm can approach \(2^{448}\). This result is satisfied with the request for key space. Table 3 demonstrates that the comparison result with another encryption scheme. Firstly, the proposed algorithm has enough key space to resist the brute-force attack. Secondly, compared with other algorithms, the key space of the proposed algorithm is large.
4.2.2 The key sensitivity analysis
The second discussion point is the sensitivity of the secret key. The image applied to test key sensitivity is Lena (\(256 \times 256\)). Set the change value \(\Delta \) equal to \(\pm 10^{-15}\); the new parameters encode the plain-text image. The test result is shown in Fig. 9. The difference between the two cipher images can be calculated by the number of pixels change rate (NPCR). The calculation method is shown as follows
Equation 25 is represented the symbolic function \(D( i , j )\).
where C (\( i \), \( j \)) is the original cipher matrix and C1 (\( i \), \( j \)) is the new cipher matrix. The size of image matrix can be considered as \(W \times H\). Besides, the new cipher matrix has come from the different parameters of encryption algorithm.
Table 4 shows the test results of NPCR with difference cipher image. It is obviously that the new cipher image is a different image compare with the original cipher image. The error key can’t recover the cipher image. In the encryption phase, the little change of secret key can obtain the difference cipher image.
4.3 The anti-statistical attack ability analyses
The discussion point in this subsection is the anti-statistical attack ability. The discussion direction has three indexes, the histogram, the information entropy, and the adjacent point correlation analysis. These indexes can present the randomness of cipher image.
4.3.1 The histogram analysis
The purpose of histogram analysis proves that the distribution of pixels is the uniform distribution. This hypothesis can be illustrated by \(\chi ^{2}\)-value. The different critical values with 10%, 5%, and 1% probability are 284.3360, 293.2478, and 310.4574, respectively. The analysis result is listed in Table 5. The values of \(\chi ^{2}\) can prove that the distribution cipher image is uniform. The histogram of the cipher image and the plain-text image is shown in Fig. 10.
4.3.2 Correlation analysis
The correlation analysis is aim to measure the correlation of adjacent pixel in different directions. The calculation equation of correlation coefficients is shown in Eq. (26–29).
This equation group has calculated the value of correlation coefficients of the image. The correlation coefficients of the cipher image are close to 0. It can prove that the adjacent pixel is not correlated. The adjacent pixel point distribution is shown in Fig. 11. The correlation coefficient results are listed in Table 6. The comparison results are shown in Table 7
The analysis result of pixel point distribution: a plain-text horizontal direction, b plain-text vertical direction correlation, c plain-text diagonal direction correlation, d ciphertext horizontal direction correlation, e ciphertext vertical direction correlation, and f ciphertext diagonal direction correlation
Figure 11d–f illustrates that the correlation of adjacent pixels is reduced. The correlation coefficient with different directions can prove that the assumption is correct.
4.4 The compression ratio analyses
In this subsection, the mean structural similarity (MSSIM) and peak signal-to-noise ratio (PSNR) are applied to measure the quality of decode image with difference compression ratios.
4.4.1 The mean structural similarity (MSSIM) analysis
The structural similarity (SSIM) is used to measure the similarity between two images. The mean structural similarity (MSSIM) is applied to evaluate the performance of the encryption algorithm. The calculation method is defined as
where \(\mu _{x}\) and \(\mu _{y}\) represent the average values of plain image X and the decode image Y. \(\sigma _{x}\) and \(\sigma _{y}\) denote the variance values of X and Y. \(\sigma _{xy}\) is the covariance of X and Y. C1, C2 and \(C3=[(K_{1} \times 255)^{2},(K_{2} \times 255)^{2}, \frac{C_{2}}{2}\)] are constants, where \(k_{1}=0.01\) and \(k_{2}=0.03\). The total number of image blocks M is equal to 64. Table 8 lists the different images at the different compression.
The bigger MSSIM value can prove two different images have a good similarity. For the decrypted image, the value of MSSIM is bigger than 0.9. The analysis results illustrated that the decrypted image is similar to the plain-text image.
4.4.2 The peak signal-to-noise ratio (PSNR) analysis
The anti-noise attack ability is discussion point in this section. The cipher image might be disturbed by noise signal during transmission. Mean squared error (MSE) and peak signal-to-noise ratio (PSNR) are adopted to calculate the quality of decrypted image. The formula of MSE and PSNR is as follows:
where \(x_{i}\) and \(y_{i}\) are the pixel value of plain-text image and decrypted image, respectively. The high score of PSNR can illustrate the high quality of decode image. On the contrary, the value of MSE has a low degree. The diagrams of MSE and PSNR are shown in Fig. 12a, b. The simulation condition is that the encrypted image is attacked by Gaussian white noise with the variance within the range of (\(10^{-7}\), \(10^{-5}\)). The distribution of MSE and PSNR displays that the noise signal could affect the quality of the decrypted image.
The other function of PSNR is to judge the quality of the recovered image. The Lean (\(256 \times 256\)) image is selected as the test image in this section. The comparison result is shown in Table 9.
The other index about image quality is cosine similarity. This index is applied to calculate the similarity between the decrypted image and the original image. The equation of cosine similarity is
where \(x_{i}\) and \(y_{i}\) are present for the decrypted image with Gaussian noise signal and plain-text image, respectively. In the ideal conditions, the result of cosine similarity should be 1. The value of cosine similarity decrease when the cipher image is affected by the noise signal. The results of cosine similarity are shown in Fig. 12c.
The analysis results can prove that the encryption algorithm can resist the effect of the noise signal. The quality of the decrypted image is shown clearly. The similarity of cosine can prove that the cipher image is similar to the plain-text image.
4.5 The anti-difference attack ability
The NPCR (number of pixels change rate) and UACI (unified average changing intensity) are important index for measuring the ability for anti-difference attack. The equation of NPCR is present in Eq. (24–25). The calculation method of UACI is shown as follows
where C (\( i \), \( j \)) is the cipher matrix and C1 (\( i \), \( j \)) is the new cipher matrix. In this subsection, the pixel original plain-text image is changed randomly. The new plain-text image is obtained. Therefore, the new plain image is applied to encryption and obtained the new cipher image C1.
The criteria values of NPCR and UACI are applied to test the encryption algorithm. The critical score of NPCR is
where \( G \) is the number of pixel points or coordinates in a plain matrix, L indicates the value of the gray level. Setting the significance level \(\alpha \), the NPCR value of the cipher image is greater than \(N_{*}^{a}\). It means that the encryption scheme can resist difference attack effectively. The critical range of UACI is obtained from Eq. (35)
where
and
The UACI score of cipher images should fall into the interval of (\(u_{a}^{*-},u_{a}^{*+}\)). It can prove that the encryption algorithm passes the UACI test. The test results of NPCR and UACI are listed in Tables 10 and 11.
The test results can prove that the encryption algorithm has a high sensitivity of pixels change. It means that the encryption algorithm can resist the difference attack. The comparison result of other encryption schemes is shown in Table 12.
4.6 The anti-choose plain-text and Known plain-text attack analysis
In this section, the known plain-text attack and chosen plain-text attack are used to evaluate the security performance of the encryption algorithm. Based on the description in Ref. [14], the attacker can choose the random matrix to obtain the corresponding cipher and speculate the construction of the secret key. For measuring the algorithm performance of resisting the known plain-text attack and chosen plain-text attack, all-white and all-black pictures are selected as encryption object. The performance of anti-known plain-text and chosen plain-text attacks ability are shown in Fig. 13 and Table 13.
The encryption result and histogram are shown in Fig. 13a–c. Figure 13c can illustrate that the cipher picture is the uniform distribution. Besides, the \(\chi ^{2}\) value is 251.0833. It is satisfied with the critical stander of different freedom. It can prove that the proposed algorithm can resist known plain-text attack and chosen plain-text attack more effectively.
5 Conclusion
This paper provided a novel image encryption algorithm. This algorithm is based on the fractional-order Jerk system, the discrete chaotic system and compression sensing theory. Firstly, the analysis of the dynamical characteristics shows that this chaotic system has a wide chaotic range. Therefore, the analysis results can prove that this system is suitable to apply to the encryption algorithm. Secondly, the block cipher theory is applied to the encryption algorithm. Therefore, the size of secret code sequences is small. It can reduce the time cost of chaotic sequences calculation. In the encryption operation, the value of the plain-text matrix and the arrangement of pixels are changed simultaneously. It can permute the pixels arrangement more effectively. Moreover, the current elements of the cipher block are based on the front cipher block and plain-text block. At the end, the security analyses show that this algorithm has good performance in resisting common attacks such as statistical, brute-force, and anti-differential attacks. Therefore, this encryption algorithm has good encryption properties and protects the plain information more effectively. Also, this algorithm provided another realization way for image security.
However, this algorithm still has few questions that need to be improved. The limitations of this algorithm are summarized as follows,
-
1.
The one-dimensional measurement matrix is applied in the current algorithm. Therefore, the image size is only reduced in the row direction. The channel resource occupied problem cannot be overcome completely.
-
2.
The two chaotic system can expend key space of secret key. Besides, these systems can provide different chaotic sequences. However, the calculation cost is bigger than the encryption algorithm based on the one chaotic system.
Therefore, the measurement matrix is two-dimensional in compression operation in the future. It can reduce the image size from two directions. The performance of compression has improved. On the other hand, the new chaotic sequence generator scheme is a new focus point in the future. The time cost of chaotic sequences calculation needs to decrease in the new scheme. This is an important index of new encryption algorithm.
References
Alvarez, G., Li, S.: Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurcat. Chaos 16(08), 2129–2151 (2006)
Aqeelurrehman, L.X., Hahsmi, M.A., Haider, R.: An efficient mixed inter-intra pixels substitution at 2bits-level for image encryption technique using dna and chaos. Optik 153, 117–134 (2018)
Belazi, A., El-Latif, A.A.A., Belghith, S.: A novel image encryption scheme based on substitution-permutation network and chaos. Sig. Process. 128, 155–170 (2016)
Cao, C., Sun, K., Liu, W.: A novel bit-level image encryption algorithm based on 2d-licm hyperchaotic map. Sig. Process. 143, 122–133 (2018). https://doi.org/10.1016/j.sigpro.2017.08.020
Chai, X., Chen, Y., Broyde, L.: A novel chaos-based image encryption algorithm using dna sequence operations. Opt. Lasers Eng. (2017a). (88(Complete):197–213)
Chai, X., Gan, Z., Lu, Y., Chen, Y., Han, D.: A novel image encryption algorithm based on the chaotic system and dna computing. Int. J. Mod. Phys. C 28(05), 1750069 (2017b)
Chai, X., Zheng, X., Gan, Z., Han, D., Chen, Y.: An image encryption algorithm based on chaotic system and compressive sensing. Sig. Process. 148, 124–144 (2018). https://doi.org/10.1016/j.sigpro.2018.02.007
Chai, X., Wu, H., Gan, Z., Zhang, Y., Chen, Y.: Hiding cipher-images generated by 2-d compressive sensing with a multi-embedding strategy. Sig. Process. (2020). https://doi.org/10.1016/j.sigpro.2020.107525
Chen, C., Sun, K., He, S.: A class of higher-dimensional hyperchaotic maps. Eur. Phys. J. Plus (2019). https://doi.org/10.1140/epjp/i2019-12776-9
Chen, C., Sun, K., He, S.: An improved image encryption algorithm with finite computing precision. Sig. Process. (2019b). https://doi.org/10.1016/j.sigpro.2019.107340
Chen, L.P., Yin, H., Yuan, L.G., Lopes, A.M., Machado, J.T., Wu, R.C.: A novel color image encryption algorithm based on a fractional-order discrete chaotic neural network and dna sequence operations. Front. Inf. Technol. Electron. Eng. 21(6), 866–879 (2020)
Gan, Z., Chai, X.L., Han, D.J., Chen, Y.R.: A chaotic image encryption algorithm based on 3-d bit-plane permutation. Neural Comput. Appl. 31(11), 7111–7130 (2018). https://doi.org/10.1007/s00521-018-3541-y
Gong, L., Deng, C., Pan, S., Zhou, N.: Image compression-encryption algorithms by combining hyper-chaotic system with discrete fractional random transform. Opt. Laser Technol. 103, 48–58 (2018). https://doi.org/10.1016/j.optlastec.2018.01.007
Gong, L., Qiu, K., Deng, C., Zhou, N.: An optical image compression and encryption scheme based on compressive sensing and rsa algorithm. Opt. Lasers Eng. 121, 169–180 (2019). https://doi.org/10.1016/j.optlaseng.2019.03.006
He, S., Sun, K., Banerjee, S.: Dynamical properties and complexity in fractional-order diffusionless Lorenz system. Eur. Phys. J. Plus 131(8), 254 (2016)
He, S., Sun, K., Mei, X., Yan, B., Xu, S.: Numerical analysis of a fractional-order chaotic system based on conformable fractional-order derivative. Eur. Phys. J. Plus (2017a). https://doi.org/10.1140/epjp/i2017-11306-3
He, S., Sun, K., Wang, H., Mei, X., Sun, Y.: Generalized synchronization of fractional-order hyperchaotic systems and its dsp implementation. Nonlinear Dyn. 92(1), 85–96 (2017b). https://doi.org/10.1007/s11071-017-3907-1
Hua, Z., Zhou, Y.: Image encryption using 2d logistic-adjusted-sine map. Inf. Sci. 339, 237–253 (2016). https://doi.org/10.1016/j.ins.2016.01.017
Jin, X., Wu, Z., Song, C., Zhang, C., Li, X.: 3d point cloud encryption through chaotic mapping. In: Pacific Rim Conference on Multimedia, pp. 119–129. Springer (2016)
Khalil, R., Al Horani, M., Yousef, A., Sababheh, M.: A new definition of fractional derivative. J. Comput. Appl. Math. 264, 65–70 (2014)
Li, G., Wang, L.I.: Double chaotic image encryption algorithm based on optimal sequence solution and fractional transform. Vis. Comput. 35(9), 1267–1277 (2019)
Li, P., Xu, J., Mou, J., Yang, F.: Fractional-order 4d hyperchaotic memristive system and application in color image encryption. Eur. J. Image Video Process. 1, 22 (2019)
Liu, W., Sun, K., He, S.: Sf-simm high-dimensional hyperchaotic map and its performance analysis. Nonlinear Dyn. 89, 2521–2532 (2017a)
Liu, W., Sun, K., He, Y., Yu, M.: Color image encryption using three-dimensional sine icmic modulation map and dna sequence operations. Int. J. Bifurcat. Chaos 27(11), 1750171 (2017b)
Ma, C., Jun, M., Cao, Y., Liu, T., Wang, J.: Multistability analysis of a conformable fractional-order chaotic system. Phys. Scr. 95(7), (2020)
Matthews, R.: On the derivation of a chaotic encryption algorithm. Cryptologia 8(8), 29–41 (1989)
Millerioux, G., Amigo, J.M., Daafouz, J.: A connection between chaotic and conventional cryptography. IEEE Trans. Circuits Syst. Regul. Pap. 55(6), 1695–1703 (2008)
Mohimani, G.H., Babaie-Zadeh, M., Jutten, C.: Fast sparse representation based on smoothed l0 norm. In: International Conference on Independent Component Analysis and Signal Separation, pp 389–396. Springer (2007)
Mohimani, H., Babaie-Zadeh, M., Jutten, C.: A fast approach for overcomplete sparse decomposition based on smoothed l0 norm. IEEE Trans. Signal Process. 57(1), 289–301 (2008)
Mou, J., Yang, F., Chu, R., Cao, Y.: Image compression and encryption algorithm based on hyper-chaotic map. Mobile Netw. Appl. (2019). https://doi.org/10.1007/s11036-019-01293-9
Peng, D., Sun, K.H., Alamodi, A.O.A.: Dynamics analysis of fractional-order permanent magnet synchronous motor and its dsp implementation. Int. J. Mod. Phys. B (2019a). https://doi.org/10.1142/s0217979219500310
Peng, Y., Sun, K., He, S., Peng, D.: Parameter identification of fractional-order discrete chaotic systems. Entropy 21(1), 27 (2019b)
Rey, A.M.D.: A method to encrypt 3d solid objects based on three-dimensional cellular automata. In: Hybrid Artificial Intelligence Systems, pp. 427–438 (2015)
Sayed, W.S., Radwan, A.G.: Generalized switched synchronization and dependent image encryption using dynamically rotating fractional-order chaotic systems. AEU Int. J. Electron. Commun. 123, (2020)
Talhaoui, M.Z., Wang, X., Midoun, M.A.: A new one-dimensional cosine polynomial chaotic map and its use in image encryption. Vis, Comput (2020a)
Talhaoui, M.Z., Wang, X., Talhaoui, A.: A new one-dimensional chaotic map and its application in a novel permutation-less image encryption scheme. Vis, Comput (2020b)
Wang, X., Xu, M., Li, Y.: Fast encryption scheme for 3d models based on chaos system. Multimed. Tools Appl. 78(23), 33865–33884 (2019)
Xu, Q., Sun, K., Cao, C., Zhu, C.: A fast image encryption algorithm based on compressive sensing and hyperchaotic map. Opt. Lasers Eng. 121, 203–214 (2019). https://doi.org/10.1016/j.optlaseng.2019.04.011
Yang, F., Mou, J., Luo, C., Cao, Y.: An improved color image encryption scheme and cryptanalysis based on hyperchaotic sequence. Phys. Scr. 94 (2019a)
Yang, F., Mou, J., Sun, K., Cao, Y., Jin, J.: Color image compression-encryption algorithm based on fractional-order memristor chaotic circuit. IEEE Access (2019b). https://doi.org/10.1109/ACCESS.2019.2914722
Yang, F., Mou, J., Liu, J., Ma, C., Yan, H.: Characteristic analysis of the fractional-order hyperchaotic complex system and its image encryption application. Signal Process. 169, (2020)
Yu, S.S., Zhou, N.R., Gong, L.H., Nie, Z.: Optical image encryption algorithm based on phase-truncated short-time fractional Fourier transform and hyper-chaotic system. Opt. Lasers Eng. (2020). https://doi.org/10.1016/j.optlaseng.2019.105816
Zhang, L.M., Sun, K.H., Liu, W.H., He, S.B.: A novel color image encryption scheme using fractional-order hyperchaotic system and dna sequence operations. Chin. Phys. B 26, 10 (2017)
Zhongyun, H., Zhou, Y., Huang, H.: Cosine-transform-based chaotic system for image encryption. Inf. Sci. 480, 403–419 (2019). https://doi.org/10.1016/j.ins.2018.12.048
Zhou, S., Wei, Z., Wang, B., Zheng, X., Zhou, C., Zhang, Q.: Encryption method based on a new secret key algorithm for color images. AEU Int. J. Electron. Commun. 70(1), 1–7 (2016)
Zhu, C., Gan, Z., Lu, Y., Chai, X.: An image encryption algorithm based on 3-d dna level permutation and substitution scheme. Multimed. Tools Appl. (2019). https://doi.org/10.1007/s11042-019-08226-4
Acknowledgements
This subject is supported by the Natural Science Foundation of Liaoning Province (2020-MS-274) and the National Nature Science Foundation of China (No.61773010).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
No conflicts of interests in the publication by all authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The Natural Science Foundation of Liaoning Province (2020-MS-274) and the National Nature Science Foundation of China (No. 61773010).
Rights and permissions
About this article
Cite this article
Xu, J., Mou, J., Liu, J. et al. The image compression–encryption algorithm based on the compression sensing and fractional-order chaotic system. Vis Comput 38, 1509–1526 (2022). https://doi.org/10.1007/s00371-021-02085-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00371-021-02085-7