Abstract
We propose a novel opto-digital method of color image encryption which utilizes compound chaotic mappings, the reality preserving fractional Hartley transformation and piecewise linear chaotic map for substitution, optical processing and permutation of image pixels, respectively. The image to be encrypted initially undergoes a chaos-based substitution in the spatial domain through the compound chaotic maps followed by a transformation to the combined time–frequency domain using the fractional Hartley transform. A reality preserving version of the fractional Hartley transform is used to eliminate the complexity associated with transform coefficients. Optical transformation of the image, in the fractional Hartley domain, is followed by a permutation through piecewise linear chaotic maps. Due to the intertwined application of optical transformation and chaos-based substitution and permutation processes, the proposed image encryption scheme possesses higher security. The input parameters (initial conditions, control parameters, and number of iterations) of chaotic maps along with fractional orders of the fractional Hartley transform collectively form the secret keys for encryption/decryption. The proposed scheme is a lossless and symmetric encryption scheme. The level of security provided in terms of high sensitivity to keys, resistivity to brute-force attack, classical attacks, differential attacks, entropy attack, noise and occlusion attack along with the elimination of complex coefficients proves its better efficacy as compared to other similar state-of-the-art schemes.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Digital information has evolved through decades with extensive growth in its capabilities. In particular, the past 10 years have seen a massive increase in usage of digital data accompanied with day-to-day advancing electronic devices such as smartphones, robotic devices, electronic readers, etc. Such devices ascertain fast processing, immense data storage and computational capabilities. The security concern related to data dissemination, especially images and videos, is still an active area of research. As compared to advancements in technology, most of the security measures such as encryption schemes are based on methodologies that were followed 10 years ago. The classical methods that include data encryption standards (DES), advanced encryption standards (AES), blowfish, etc. are not suitable for bulk data [1, 2] such as image and video. This prompted researchers to come up with some alternative methods for bulk data encryption rather than relying on pure number theory.
For image encryption, there are numerous methods proposed in the literature that include dynamical chaos-based ciphers [3,4,5] and their hybridization with finite state machine [6], with optimized S-Box generation [7], cascade coupling [8, 9], higher dimensional chaos with DNA [10], parallel with compressive sensing [11]. On the other hand, optical transforms-based image encryption is an active area of research due to the inherent property of high speed and massive parallelism. The transform orders that provide an extra degree of freedom to the encryption scheme serve as secret keys. The transform-based image encryption is inspired from the classical double random phase encoding scheme (DRPE) [12,13,14] which is implemented with an optical setup comprising of lenses, spatial light modulators (SLM) and charged coupled devices (CCD). Most commonly used optical image encryption schemes include Fractional Fourier transform (FrFT) [15,16,17,18], Fresnel transform [19, 20], Gyrator transform [21, 22], Mellin transform [23, 24], Hartley transform [25,26,27], etc.
According to a recent survey reported by Ghadirili et al. [28], 32.03% of total published works on image encryption are based on chaos and only 8.65% are based on transform domain-based encryption schemes. Although the optical transform-based algorithms offer high speed, parallel data processing and thus for image encryption, provide greater flexibility for manipulating parameters such as wavelength, polarization, amplitude or phase but still their usage in practical implementation is less preferred owing to drawback related to complex domain outcome and smaller keyspace. Various researches on cryptanalysis have shown that these algorithms are vulnerable to chosen-plaintext attack (CPA), known-plaintext attack (KPA) and some heuristic attacks [29,30,31]. Chen et al. [29] suggested that a larger keyspace is required to avoid blind decryption. The reuse of keys should also be avoided [31] following a one-time pad approach.
As mentioned by Ghadirili et al. [28], chaos-based image encryption is preferred owing to its inherent characteristics of high sensitivity to seed values, randomness and ergodicity. The chaotic maps are broadly classified as 1D or higher dimensional maps, whereas 1D maps are simple in hardware implementation but due to certain flaws such as the existence of blank windows in bifurcations, smaller keyspace, etc., lead to their vulnerability to potential attacks [5, 32]. On the other hand, higher dimensional chaotic maps are complex and have larger keyspace but are not cost-effective in hardware implementation [33, 34]. Hybridization of chaotic maps is looked upon as one of the solutions to overcome these limitations [28, 35]. Working toward hybridization, there are number of schemes recently proposed [27, 36,37,38,39] that combine chaos with transform domain encryption. Such schemes are based on combination of chaos-dependent permutation along with a particular transform for making the image unintelligible where the order of their application may vary. Either permutation is followed by transform or permutation is performed in the spatial domain prior to transform. However, such schemes are unable to provide enough security although their immunity to noise and data occlusion attacks is fairly good [39, 40]. Moreover, many such schemes fail to provide testimony against most of the classical attacks and differential attacks [29, 30, 41, 42]. Some of the most recently proposed schemes [18, 22, 26, 40, 43,44,45,46] lack such analysis.
Keeping into consideration all above-stated limitations in the transform and chaos-based encryption schemes, we propose a novel opto-digital method of color image encryption in which the image to be encrypted is initially processed nonlinearly in the spatial domain with the help of a compound chaotic mapping followed by a reality preserving 2D fractional Hartley transform operation to convert the processed image in the optical domain. The transform coefficients obtained are further scrambled with the help of a piecewise linear chaotic map to enhance the security. The input parameters of chaotic maps thus used and the fractional-order of the fractional Hartley transform serve as the secret symmetric keys for encryption/decryption. The performance and security analyses prove that the proposed scheme is robust and efficient for the secure transmission of images. The proposed scheme is highly sensitive to the keys and has a larger keyspace and thus can withstand various cryptanalytic attacks. Its distinct feature of the complete elimination of the complex coefficient terms makes it suitable for real-time image transmission.
This paper is organized as follows: Introduction in Sect. 1 is followed by Sect. 2 that describes the preliminaries such as fractional transform, reality preserving methodology, chaotic maps, compound mapping, etc., used in the proposed image encryption method. Section 3 elaborates the step-by-step procedure used for the proposed image encryption/decryption, and Section 4 gives the results of performance and security analyses of the proposed scheme. A comparative analysis is included in Sect. 5. Finally, the work is concluded in Sect. 6.
2 Preliminaries
2.1 Fractional integral transform
Fractional transforms have found many applications in the field of engineering and science ever since the advent [16, 47, 48] and later for applications in optics [15, 49, 50]. With the evolution of the digital era, the fractional transforms were studied for their digital representations [17, 51, 52]. The ordinary Fourier transform is the generalized form of fractional-order transforms where the transform order is unity. The integer orders when replaced with fractional orders expand the application area of these transforms. Particularly in optical processing, these transforms are useful in digital holography, as means of modeling speckle fields propagating through apertured optical systems, in quantum optics, in optical encryption by means of random phase encoding (DRPE), in wave field theory to describe the reflection of coherent light from a non-uniform surface which is beneficial in meteorology. The basic form of the integral transform is the Fourier transform. Fourier is obtained following integral representations for \(f\left(x\right)\) and its nth integral as:
where \(\xi \) depicts the frequency. Replacing ‘\(n\)’ by an arbitrary fractional number ‘\(\alpha \)’ gives the fractional-order equivalent transform of the function \(f\left(x\right).\) The arbitrary angle \(\alpha \) corresponds to the angle of rotation in the time–frequency domain. It is also understood as the Wigner rotation as explained in position–momentum paradigm [15]. The fractional transform integral is said to be in purely time domain for \(\alpha \) = 0 and in purely frequency domain if \(\alpha \) = 1. Thus, a fractional order corresponds to the collective time–frequency domain which gives an extra degree of freedom for its application to image encryption. The Fourier transform and Hartley transform are closely related [25, 52] as the eigenvalues of the DFT are also the eigenvalues of the Hartley transform. Thus, a fractional Hartley transform can also be represented by a fractional Fourier transform [5, 7]. Hartley transform of a function \(f\left(x\right)\) is given by
where radian frequency variable \(\zeta =2\pi f\) and \(\mathrm{cas}\) function is defined as \(\mathrm{cas}\left(\zeta {x}\right)=\mathrm{cos}\left({\zeta x}\right)+\mathrm{sin}\left({\zeta x}\right)\). The fractional Hartley transform of a time-domain signal is defined as:
where the fractional Hartley kernel is defined as:
In the discrete domain, the eigenvectors of discrete fractional Fourier transform (DFrFT) are also the eigenvectors of discrete fractional Hartley transform (DFrHT). Thus, in terms of the Fourier transform, FrHT for a 2D signal can be represented as:
where \({F}^{\alpha ,\beta }\) corresponds to the fractional Fourier transform coefficient, \({\phi }_{1 }=\frac{\alpha \pi }{2}\), \({\phi }_{2}=\frac{\beta \pi }{2}\), \(\left|{\phi }_{1}\right|,\left|{\phi }_{2}\right|< \pi \), \(\left(u,v\right)\) represent the transform domain.
Therefore, fractional Hartley transform is the real part of fractional Fourier transform plus the negative of the imaginary part of the fractional Fourier transform [27]. The DFrHT possesses all the basic properties that are required in a fractional integral transform. The optical realization of fractional Hartley is described in [53]. However, the transform coefficients of a fractional Hartley transform are complex. These complex values need a holographic technique to record two images, one for spectrum and another for phase. This makes the storage and transmission less efficient due to double memory space requirements. Moreover, the computation complexity also increases during inverse operation.
2.2 Reality preserving method
The reality preserving concept was first introduced by Venturini and Duhamel [54] to overcome the complexity issue in the transform domain, where a reality preserving alternative to the complex fractional cosine and sine transforms was proposed. The reality preserving algorithm maintains most of the desired properties of the transform. As the resulting transform can have continuously increasing decorrelation power as the fractional order varies from ‘0’ to ‘1’ with an order of ‘0’ corresponding to no decorrelation and order of ‘1’ corresponding to a base transform with maximum decorrelation. This decorrelation power is used in various signal processing applications. Reality preserving can be employed where an orthogonal reality preserving transform is required and the de-correlating power is to be controlled by some parameter. The steps for deriving a reality preserving equivalent of FrHT are as follows:
Step 1 For a 1D FrHT of length, \({\rm M}\): Let \({\mathcal{H}}_{\mathcal{a},\frac{M}{2}}\) be a complex-valued fractional Hartley transform matrix with size \(M/2\)(\(M\) is even). The real input signal is represented by \(y= {\left\{{y}_{0},{y}_{1},{y}_{2},\dots {y}_{M-2},{y}_{M-1}\right\}}^{t}\) from which a permutation matrix (P) is obtained as, \({y}^{{\prime}}= {\left\{ {y}_{0}^{{\prime}},{y}_{1}^{{\prime}},{ y }_{2}^{{\prime}}, {\dots y}_{M-2}^{\prime} {{y}_{M-1}^{{\prime}}}\right\}}^{t}\) denoted as \({y}^{{\prime}}=Py\),
Step 2 \( \widehat{y}=\left\{{y}_{0}^{{\prime}}+\left.j{y}_\frac{M^{\prime}}{2}\right| \left.{y}_{1}^{\prime}+{y}_{{\frac{M}{2}+1}}^{\prime}\right|\ldots \left.{y}_{\frac{M}{2}-1}^{\prime}+jy_{2}^{\prime}\right|\left.y^{\prime}+jy_{M-1}^{\prime}\right|\right\}^{t}\) is the complex vector built from \(y\). Further, a transform output is obtained from this complex vector such that,
Step 3 The Reality preserving equivalent of transform is obtained as \({z}^{{\prime}}=\left\{\left(Re\, \widehat{z}\right), \left(Im \,\widehat{z}\right)\right\} ; z= {P}^{-1}({{z}^{{\prime}})}^{t}\), t represents transpose. Thus, \(z= {P}^{-1}{\mathrm{RPFrHT}}_{\mathcal{a}}Py\)
2.3 Chaotic maps
Dynamical chaos, observed in many nonlinear dynamical systems, is a deterministic, bounded, aperiodic behavior possessing sensitivity on initial conditions/system parameters. Along with the crucial feature of sensitivity on the initial condition, chaotic systems possess many other interesting and universal features like ergodicity, mixing, invariant density measure, positive metric entropy (KS-entropy), etc. These features make them suitable for use in secure communication. During the last two–three decades, the use of chaotic systems has been explored extensively and a well-defined close relationship between chaotic systems and ideal cryptographic systems has emerged [33]. According to Shannon [55], in order to attain a perfect secrecy, a combination of diffusion and confusion is essential in a cryptographic system. For images, which are characterized by the bulk of data, high correlation and redundancies, the chaotic systems have been found most suitable for achieving the desired level of permutation and substitution [4, 34]. In the proposed image encryption, we use chaotic systems as the source for introducing confusion and diffusion in conjunction with the optical process governed by the reality preserving fractional Hartley transform. The purpose of using transform is to bring the data from the spatial domain to the combined time–frequency domain so that the chaos-based analysis may not be feasible for the intruder. In the following paragraph, we briefly describe the chaotic systems being used in the proposed image encryption scheme.
2.3.1 For permutation/scrambling stage: Piecewise linear chaotic map (PWLCM)/Zhao map
The mathematical form of PWLCM [56] used for diffusion in the proposed image encryption scheme is as follows:
where \(\varepsilon \) (\(0<\varepsilon <1/2)\) is the control/system parameter. If \(Y \in \left[\mathrm{0,1}\right]\), it is known as normalized PWLCM. In this paper, we are using a normalized PWLCM [57] that can be expressed using a simple affine transformation:
2.3.2 For substitution: Compound chaotic maps
Due to some inherent weaknesses in one-dimensional maps for cryptographic applications [41] and to enhance the robustness in the complete parameter range, researchers have used a combination of chaotic systems, i.e., compound chaotic map [3, 8, 58]. In the proposed work, we use a similar nonlinear combination of three seed maps, \(F\left({x}_{n}\right),G\left({x}_{n}\right)\) and \(H({x}_{n})\). A compound chaos is defined by, \({x}_{n+1}=\left(F\left(G\left({x}_{n}\right)\right)+ H\left({x}_{n}\right)\right)\mathrm{mod}\,1\). The mod operation is to ensure that the output sequence is restricted in the range [0, 1]. The combination of the two maps improves the chaotic behavior [8]. Further, the addition of the third map (modulo 1) enhances the mixing and results in enhanced complexity.
In the proposed image encryption scheme, logistic map (L), tent map (T), and sine map (S) are used for compound mapping.
-
(a)
Logistic map: It is originally introduced as a demographic model [59] and is mathematically defined as:
$${x}_{n+1}=L\left({x}_{n}\right)=\mu {x}_{n}\left(1-{x}_{n}\right)=4r{x}_{n}\left(1-{x}_{n}\right) , 0<{x}_{n}<1$$(8)where \(\mu \in \left[\mathrm{0,4}\right]\) or \(r\in [\mathrm{0,1}]\) is the control parameter, also known as the bifurcation parameter. The 1D logistic map is chaotic for its control parameter range as \(0.9\le r <1\).
-
(b)
Tent map: It is the simplest piecewise linear chaotic map and is a topological conjugate of logistic map [60] defined in the interval [0, 1] and mathematically described as:
$$ x_{n + 1} = T\left( {x_{n} } \right) = \left\{ {\begin{array}{*{20}l} {2rx_{n} ,} \hfill & {{\text{if}}\,0 \le x_{n} \le 0.5} \hfill \\ {2r\left( {1 - x_{n} } \right) , } \hfill & {{\text{if}}\,0.5 < x_{n} \le 1 } \hfill \\ \end{array} } \right. $$(10)where \(0<r\le 1\). The chaotic behavior is observed for \(0.61<r<1\)
-
(c)
Sine map: Sine map is another simplest 1D nonlinear map [32], mathematically described as:
$${x}_{n+1}=S\left({x}_{n}\right)=r{{\rm sin}}\left(\pi {x}_{n}\right).$$(11)
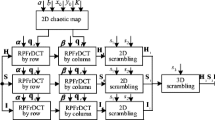
The chaotic behavior in this map is observed for \(r\in \left[0.87, 1\right]\). It is qualitatively identical to the logistic map as the topological entropy of the sine map is equal to that of the logistic map at \(r=1.\) Figure 1 illustrates the complete schematics of developing these three compound chaotic maps (CCM), CCM1, CCM2, and CCM3. The mathematical representation of each CCM is given in Table 1.
3 Encryption and decryption procedure
In this section, we describe the processes of encryption and decryption in detail. The proposed encryption process is based on three different stages. A chaos-based substitution/confusion in the spatial domain is the first stage followed by optical processing using reality preserving fractional Hartley transform and finally the third stage of chaos-based diffusion /scrambling in the transform domain. There are a total of 24 keys used in the encryption process that includes nine keys for confusion (first stage), six keys for optical transform and then nine keys for scrambling in the transform domain.
Encryption
3.1 Stage 1: Substitution based on compound chaos (CCM)
The input image ‘P’ of size \(M\times N\times 3\) is decomposed into its red (R), green (G) and blue (B) component images each of size \(M\times N\). The first level of encryption is based on compound chaotic maps described in Sect. 2.3.2. For example, the CCM used for the red component \({(R)}_{M\times N}\) is \(\left({T}\left({L}\right)+{L}\right) {\rm mod}\,1\) compound chaotic map (CCM1) with parameters \(\{{c1}_{0},u1,i1\}\) where \({\mathrm{c}1}_{0}\) denotes the initial value, \(u1\) is the bifurcation parameter and \(\mathrm{i}1\) is the number of iterations to be discarded as transient. For CCM1, a chaotic sequence is iterated for \(i1+MN\) different values, i.e., {\({c1}_{i1+M\times N}\}\). The initial \(i1\) iterations are discarded in order to avoid any computational error and also to increase the security. A similar process is followed for other CCMs. The values of sequence thus obtained are in floating point. These are converted to integer form as:
The integer sequence is then reshaped to a 2D image of size \(M\times N\) and is used for the substitution of each color component of the input image, \({P}^{{\prime}}\in [R,G,B]\) as:
3.2 Stage 2: Reality preserving 2D fractional Hartley transform
The outcome from Stage 1 in the spatial domain is then transformed via a fractional Hartley transform with a reality preserving algorithm. The transformation results in the complex coefficients which in optical processing require special holographic techniques for recording. In the digital domain, it becomes difficult to store and transmit the complex coefficients as it leads to increased complexity and memory requirements. To overcome such issues, a reality preserving algorithm [54] is used to obtain transform in the real domain as explained in Sect. 2.2. The substituted outcome of Stage 1 is transformed using the steps explained in Sect. 2.2. It is likely to mention that 1D transformation has to be extended to 2D for image data. The 1D RPFrHT can be easily extended to 2D by cascading two transforms, one along rows of the image and another along with the columns. This requires two different transform orders \((\alpha ,\beta )\) for both directions. For the sake of brevity, the individual steps of transformation are not again illustrated here. However, to correlate with explanation given in Sect. 2.2, final outcome of 1D RPFrHT for input as substituted image of Stage 1 is represented as:
This 1D \(\mathrm{RPDFrHT}\) can be extended to 2D by following the same procedure as shown above but in y-direction. For that, each column is treated as a different array and the values are wrapped to half along each column to obtain a matrix of dimensions \(M/2\times N\). The transform order along y-direction, i.e., along each column, is denoted by \(\beta .\) Hence, a \(2\mathrm{DRPDFrHT}\) can be described as a cascaded operation of two \(1\mathrm{D RPDFrHT}\)’s as:
where \(\left(M,N\right)\) represents the size of the image, (\(\alpha ,\beta )\) are the transform orders, \({S}_{\left(M,N\right)}\) is the substituted image of Stage 1. The above-stated procedure is repeated for each color component image with a different set of transform orders.
3.3 Single-bit phase modulation
The transformed image, obtained after reality preserving 2D fractional Hartley transform, in its coefficient has both positive and negative values which are not suitable for optical detection by CCD camera if an optical setup is used. In the digital domain, negative values cannot be realized while storing and retrieving. This issue needs to be handled for the complete recovery of data during the reverse process. A phase modulation method is used with a single bit of the data representing it as either a negative or positive value. This can be termed as a single-bit phase modulation method. In this method, we use a variable \({P}_{b}(u,v)\) which is assigned a bit ‘0’ for positive value and bit ‘1’ for negative value corresponding to the transform coefficients \({h}_{\left(k+1\right)}(u,v)\):
This single bit value is extracted for each color component and then is concatenated into a single image. This matrix of size \(M\times N\times 3\) can be used as a public key as it does not reveal any intuitive information about the encrypted data. Moreover, as it is a single-bit matrix, storage and transmission will not be an issue of concern. During the decryption process, the original transform coefficients are obtained as:
3.4 Stage 3: Chaotic scrambling using PWLCM
As explained in Sect. 2.3.1, a PWLCM map is used for generating a chaotic sequence owing to its LE (Lyapunov exponent) being positive over the entire range of its control parameters. Three different PWLCM or W-maps are used each for red, green and blue components of the transform coefficients obtained in Stage 2. For the transform coefficients of size \(\mathrm{M}\times \mathrm{N}\) corresponding to each color component, the PWLCM with parameters \(\left\{{x}_{0},u,t\right\}\) is iterated for (\(t+M\times N\)) number of iterations and a sequence of \(M\times N\) is generated by discarding first \(t\) terms to avoid any computational error of transients.
Step 1 The chaotic sequence generated by each PWLCM can be represented as:
Step 2 The chaotic sequence is then sorted in ascending/descending order into a vector, and the index of the vector is stored as the address into another vector as: \(\left[\mathrm{ind},{P}_{s}\right]=\mathrm{sort}({P}_{l})\). This changes the positions of the elements. Record the new index of \({P}_{s}\), i.e., mth element of \({P}_{s}\) corresponds to \(\mathrm{ind}\left\{m\mathrm{th}\right\}\) element of \({P}_{l}\).
Step 3 The 2D transform matrix of Stage 2 is reshaped into the 1D sequence of size \(MN\times 1\). Vectorization is performed to convert \(M\times N\) transform coefficients to a matrix of size \(M\times N\times 1\) by extracting the values column by column.
Step 4 Now, the recorded index of the sorted vector \(\mathrm{ind}\) is used to reorder (permute/scramble) the 1D transform vector as \(\mathrm{RPFrHT}\left(\mathrm{ind}\right).\) Finally, this 1D matrix is converted into 2D image format by reconverting it into \(M\times N\) vector.
In this stage, the initial value, control parameter and number of iterations to be discarded \(\left\{{x}_{0},u,t\right\}\) are used as the secret keys. Therefore, there are a total of nine keys for scrambling (three each for R, G and B individually). The scrambled transform coefficients give a final encrypted image which can now be transmitted over a public channel. The complete encryption process is shown in Fig. 2.
Decryption
The decryption procedure is illustrated in Fig. 3. Decryption is exactly the reverse of that of encryption. Exactly the same keys (all 24 keys) are required in each stage of decryption to completely recover the original image, thus making it a symmetric key cryptographic process.
The output of Stage 3 of the encryption process which is scrambled transform coefficients is descrambled using the same PWLCM’s with parameters \(\left\{{x}_{0},u,t\right\}\) as used during encryption. The descrambled image components are then inverse transformed with (\({\mathrm{RPFrHT})}^{-1}\) which is similar to the forward transform with the same transform orders but with negative values (six keys). The next step is the generation of the CCMs with nine keys of Stage 1. The generated CCMs need to be exactly same as used during the forward procedure, for them to be substituted with the inverse transform coefficients to retrieve the original image components.
4 Simulation results
The proposed scheme is realized in MATLAB 9.0, on a personal computer with Intel(R) Core (TM) i5 8250U CPU (3.45 GHz), 8 GB RAM, and 1 TB hard disk capacity. Two standard images (Lena, Baboon) taken from the SIPI dataset [61] are considered as test images for visual analysis and statistical analysis. The simulation results for numerical analysis are evaluated for a number of other images taken from the same dataset. The secret keys used in this simulation are randomly generated using a random number generator in MATLAB. The simulations are done with the same set of secret keys throughout this work. The distribution of keys and their corresponding values are given in Table 2.
4.1 Experimental analysis
Figure 4 shows encryption at each stage from left to right. Figure 4a, f shows the original standard color test images (Lena and Baboon). The first stage of encryption is the substitution with compound chaotic maps as described in Sect. 3.1, and the results obtained for this stage using the secret keys (Table 2) for red, green and blue channels, respectively, are shown in Fig. 4b, g. In order to enhance the security, a plain image-dependent session key is generated for each color channel (δr, δg, δb). Also, the session keys are added either to the initial condition or to control parameter alternatively to further create more confusion for any intruder. The next stage is to obtain the reality preserving fractional Hartley transform (RPFrHT) of the image by following the procedure described in Sect. 3.2. The secret keys at the transform stage are basically the pairs of fractional transform orders along the rows and columns of red, green and blue channels, respectively, as shown in Table 2. The resultant transformed images are shown in Fig. 4c, h. The transform output also has certain negative-valued coefficients which are stored in a single-bit phase modulation matrix by storing a bit ‘0’ for positive value and bit ‘1’ for negative value of the coefficients, and the resultant matrix in the form of an image is shown in Fig. 4d, i. It can be seen that transform output has some visual patterns which need to be removed. Therefore, the third and final stage is to permute the transformed image obtained after the second stage with the piecewise linear chaotic map as described in Sect. 3.4. The set of secret keys (Table 2) are used to permute each component image to make it a random noise-like image. The resultant images after the permutation are shown in Fig. 4e, j. This is the final encrypted image that is transmitted over the public channel along with the single-bit phase modulation matrix.
The decryption is exactly the reverse of that of the encryption procedure. If the same sets of keys (as used during encryption) are supplied at all stages of decryption, the original image can be recovered without any loss of data. The complete process of decryption of encrypted images is shown in Fig. 5. Figure 5a, f shows encrypted images of Lena and Baboon, respectively. The encrypted image will be first processed for descrambling/inverse permutation using PWLCM with the same set of secret keys as used for Stage 3 of encryption. The resultant images after the inverse permutation are shown in Fig. 5c, h. This transformed image (which carries the magnitude of transform coefficients) along with the single-bit phase modulation matrix as shown in Fig. 5b, g collectively represents the exact transform coefficients to be processed for the next stage of decryption, i.e., inverse reality preserving Hartley transformation. This combination (images in Fig. 5b, g along with Fig. 5c, h) is processed for inverse RPFrHT with the same pairs of fractional orders as supplied in Stage 2 of the encryption but with negative sign (as explained in Sect. 3). The resultant images after the inverse transform are shown in Fig. 5d, i. Now the third stage of decryption is executed on the image shown in Fig. 5d, i by following the procedure explained in Sect. 3.1 based on the compound chaotic maps (described in Sect. 2.3.2) and subject to the same set of secret keys for the red, green and blue channels as used in Stage 1 of encryption. The resulting images are the final decrypted/recovered images which are shown in Fig. 5e, j.
We have also experimented with a lot of other images having widely different contents using several combinations of secret keys and analyzed the corresponding encrypted and decrypted images with all intermediated images. We observe that the proposed method completely converts the images into visually obfuscated data and gives a lossless recovery in decryption.
4.2 Security analysis
The major concern of any cryptosystem lies in the level of security it provides. In other words, a good encryption technique should be robust against all sorts of cryptanalytics, statistical and brute-force attacks. In this section, we attempt to provide a complete investigation on the security of the proposed encryption technique.
4.2.1 Brute-force attack
In cryptographic applications, the most important part is the selection of keys. The keyspace should be large enough to counter any brute-force attack. This type of attack is based on exhaustive key searching where the adversary gets capability of recovering the original information by searching all possible keys in the keyspace until a correct key is found. The resistance to brute-force attack is the measure of the keyspace. A larger keyspace ensures better resistance. The keyspace should be > 2120 to preclude any eavesdropping [33, 62].
In this scheme, 24 keys are used with different precision levels. There are 12 keys with a precision of 10–15, six keys with the precision of 10–4, six keys with integer values (4 digits). Therefore, the total keyspace can be evaluated as
which is sufficiently larger than 2120 to resist any brute-force attack.
4.2.2 Perceptual security analysis
Perceptual security analysis determines the measure of dissimilarity between plain and encrypted images.
The utmost requirement of encryption is to make the information unintelligible and obfuscate the pixels in such a way that it appears as random white noise. It is evident from Fig. 4 that the final encrypted images are completely random and thus are visually unrecognizable.
Apart from visual quality, the perceptual security analysis results are numerically represented in terms of certain parameters, viz. peak signal-to-noise ratio (PSNR), mean square error (MSE) and spectral similarity index (SSIM). For a pair of original and encrypted images represented as \({o}_{i,j}\) and \({e}_{i,j}\), respectively, these parameters are defined as:
where \([M,N]\) is the image size, \(L\) is the highest intensity value (256 for an 8-bit image), \({\mu }_{o},{\mu }_{e},{\sigma }_{o},{\sigma }_{e},{\sigma }_{oe}\) are mean, variance and covariance of original and encrypted images. \({{C}}_{1},{{C}}_{2}\) are constants that are used to stabilize division with a weak denominator.
Mean square error (MSE) is an error metric that allows to compare pixel values of original with that of the encrypted image. Thus, a high value of MSE is desirable during encryption and in the decryption process, MSE should be ideally ‘0′ for lossless image recovery. PSNR is used as a metric for spectral information measure and is an error metric that is used as quality measure statistics of an image with respect to a reference image. The higher the value of PSNR, the better is its quality. Thus, two similar images will have infinite PSNR. However, a \(\mathrm{PSNR}\ge \) 28 is considered satisfactory for a reconstructed image. The purpose of evaluating PSNR is to show that the PSNR of the encrypted image with respect to the original image is very low (\(\ll 28)\) which indicates a significant difference between the original and encrypted image. However, there is a limitation of just relying on the MSE and PSNR values as these measures utilize only numeric values of pixels and do not consider other factors of the human visual system (HVS). Wang et al. [63] proposed Structural Similarity Index (SSIM) as another metric that considers three main biological factors, viz. luminance, contrast and structure comparison between an image and a reference image, and is a method of subjective evaluation for quantifying the visual image quality. \({{\rm SSIM}} \in [-\mathrm{1,1}]\) with a value of ‘1’ for ideally similar images.
Different images along with test images are simulated for these parameters’ evaluation. The simulated results are given in Table 3. As is evident from the results, the PSNR of encrypted images is very low (\(\ll 28)\) with MSE values ( \(\cong {10}^{4}\)) very high. SSIM of encrypted images is near to ‘zero’. All these parameters indicate that the encrypted images have high perceptual security.
During decryption, it is recommended to have decryption error negligibly low [66] for applications such as biometrics and secure military communications. The decryption error of decrypted image, \(\mathrm{De}(i,j)\) corresponding to plain image \(\mathrm{Pl}(i,j)\) of size \(M\times N\) is evaluated [67] as
where \({ }Q\left( {i,j} \right) = \left\{ {\begin{array}{*{20}l} {1,} \hfill & {{\rm Pl}\left( {i,j} \right) = {\rm De}\left( {i,j} \right) } \hfill \\ {0,} \hfill & {{\text{otherwise}}} \hfill \\ \end{array} } \right.\)
The decryption error of all the images is ‘zero’ in the proposed scheme. We have also checked the objective metrics for the same to validate our claim. The objective metrics are the same for all test images and are listed in Table 4.
4.2.3 Statistical analysis
4.2.3.1 Histogram analysis
An image histogram depicts the intensity value distribution of image pixels against each gray level. This statistical data can reveal some crucial information for an intruder to decrypt image by analyzing its histogram. Also, this information can be used to mount more statistical attacks. Thus, it becomes necessary to investigate the histograms of the encrypted image. The histogram of an encrypted image should be different from that of the actual image and also independent of the content of the actual image. As shown in Fig. 6, the first and third rows are the RGB channel histograms of plain image Lena and Baboon respectively. The second and fourth rows depict corresponding histograms of encrypted images. It is evident from Fig. 6 that the histograms of the encrypted image are quite different from that of the original image. One more important point worth mentioning here is that the histograms of the final encrypted image are always independent of the original image and hence, do not reveal any information about the original image.
4.2.3.2 Correlation analysis
The adjacent pixels in an ordinary image with definite visual content are highly correlated in horizontal, vertical and diagonal directions. A good encryption scheme should be capable to make the correlation sufficiently low in order to resist the statistical attacks. To analyze and compare the correlations of adjacent pixels in the plain and encrypted image, correlation analysis of the proposed scheme is done.
We have randomly selected \(100\times 100\) pixels of the red channel from each image. (For brevity, only red channel for both the test images is shown.) Figure 7a–c shows the horizontal, vertical and diagonally shifted pixels of plain image Lena, and Fig. 7d–f shows corresponding correlation plots in encrypted image. Similarly, Fig. 7g–i shows the horizontal, vertical and diagonally shifted pixels of plain image Baboon, and Fig. 7j–l shows corresponding correlation plots in encrypted Baboon. In order to quantify the adjacent pixel correlation in the encrypted image, correlation coefficients are computed through Eq. (23) where \({x}_{k}\) and \({y}_{k}\) are gray values for \(kth\) pair of selected adjacent pixels.
where \(D\left(x\right)=\frac{1}{M}\sum_{k=1}^{M}{({x}_{k}-E(x))}^{2}\), \(D\left(y\right)=\frac{1}{M}\sum_{k=1}^{M}{({y}_{k}-E(y))}^{2}\)
The correlation analysis is done for all the images in the horizontal, vertical and diagonal directions. We observe that the adjacent pixels are highly correlated in the plain images. However, this correlation is completely removed after the encryption of the images using the proposed image encryption technique. The quantitative results of the correlation coefficients between the horizontally, vertically and diagonally adjacent pixels distributions are given in Table 5 for the encrypted images only (for all three color components). A very low value (\(\approx \) 0) of the correlation coefficients for encrypted images proves no correlation and hence resistance to statistical attacks.
4.2.4 Key sensitivity analysis
A cryptosystem is evaluated for its effectiveness in terms of key sensitivity. Therefore, the sensitivity of the keys should be as high as possible. There are two aspects of evaluation for key sensitivity: (1) During encryption, a completely different ciphertext should be generated with a very minute change in key, and (2) During decryption, there should be incorrect recovery (almost a random noise-like) with wrong keys. A key sensitivity parameter (KS) is introduced in [72] which should be ideally 100% for two completely dissimilar images.
However, in practical terms, KS should be as close to 100%. For each key, KS is evaluated in the encryption stage corresponding to each wrong key. For example, the value for the key (K1) gives ciphered image (\({C}_{1})\), and for altered key with very minute variation \(\left({K}_{1}^{{\prime}}\right)\) another ciphered image \(\left({C}_{2}\right)\) is obtained. Therefore, KS parameter for two ciphered images, \({C}_{1}\) and \({C}_{2}\) is as:
where \({C}_{1}\) and \({C}_{2}\) are two different ciphered images with the difference in any one of the keys,
The KS value for each key in all three stages of encryption is evaluated (for image Lena) as shown in Tables 6 (for Stage 1), 7 (for Stage 2), 8 (for Stage 3). The KS values are very close to 100% which clearly indicates that key sensitivity is extremely high at the encryption side. It has also been observed that the key sensitivity of Stage 2 (transform stage) is evaluated at different precisions. The KS is a little less when a precision of 10–4 is used. This depicts that using only transform for decorrelating the pixels cannot provide optimum security and hence the addition of other security layers is essential.
At decryption, key sensitivity is measured in terms of MSE plots corresponding to deviation in each key over a range in close proximity. For this, each key value is little deviated by infinitesimally small values and the decrypted image is evaluated for its MSE with reference to the original image. It is observed while simulation that the recovery with each wrong key gives a completely random image. For avoiding any redundancy in results, the MSE plots for wrong keys are generated corresponding to each stage for the Red channel only (\({K}_{1}\)–\({K}_{3}\): Stage 1,\( {K}_{10}\)–\({K}_{11}\): Stage 2, \({K}_{16}\)–\({K}_{18}\): Stage 3). The reader may refer to Table 2 for the description of keys.
The MSE plots depict high sensitivity as there is an error of order of 104 with a deviation of as minute as an order of 10–15 in the key values for chaotic maps (keys \({K}_{1}\)–\({K}_{3}\)) as shown in Fig. 8a–c. For MSE plots of keys at stage 2, the values are deviated by 10–4 in transform order along x-direction (\({K}_{10}\)) in Fig. 8d, along y-direction (\({K}_{11}\)) in Fig. 8e and collectively for both (\({K}_{10}\),\( {K}_{11}\)) in Fig. 8f . For MSE plots corresponding to keys at stage 3, deviation in key values (\({K}_{16}\), \({K}_{17}\), \({K}_{18}\)) of an order of 10–15 is plotted and shown in Fig. 8g–i, respectively. It is observed that MSE plots of other channels are similar.
4.2.5 Information entropy analysis
Entropy refers to the measure of amount of information in any signal. For image, the amount of information entropy/Shannon entropy depends on the probability of occurrence of particular pixel intensity in the histogram. For a flat image, entropy is \(zero\) and for an encrypted image, its entropy is defined as the amount of uncertainty associated with the random image. The random variable can be a quantitative measure of any one of the pixel entities such as color, luminance, saturation, etc. Entropy is thus a statistical measure of randomness. For an image R with pixel values \({\mathrm{r}}_{\mathrm{i}}\), its entropy is explicitly defined as:
where \(p\) is the probability of occurrence of \({r}_{i}\mathrm{th}\) pixel; \(b\) is the base of log which can be \(\mathrm{e},10\,\mathrm{ or \,}2\). In an image with maximum \(n\, \mathrm{bit}s, M={2}^{n}\), b = 2.
Recently, another measure for image randomness is introduced [73] which is coined as local entropy measure. It is based on Shannon entropy measure over local image pixels. Local entropy measure is able to overcome certain weaknesses of Shannon entropy measure. Some of proved weaknesses in [73] are unfair randomness comparisons for images of variant sizes, failure to distinguish image randomness before and after shuffling, inaccurate values in the case of synthesized images, etc.
Local entropy is the mean entropy of several nonoverlapping image blocks that are randomly selected from the source image. In order to differentiate from local entropy, Shannon entropy is termed as global entropy. Local entropy is evaluated over a certain number of nonoverlapping blocks (k) of image pixels (TB), therefore termed as (k, TB)-local entropy as:
where Si are randomly selected nonoverlapping image blocks as S1, S2, S3 … Sk and TB are the number of pixels in each block, Sk. For image intensity level, L = 2 (binary image), \({ T}_{B}^{L=2}=2\). Similarly, for L = 256 \({T}_{B}^{L=256}=1936\) and the total number of nonoverlapping blocks should not be less than 30 \((k\ge 30)\).
The entropy analysis results of a few test plain images and their corresponding encrypted images are given in Table 9. The values of information entropy for the encrypted images are almost converging to a value of 7.9999, i.e., the highest possible value of information entropy for an 8-bit random image. The local entropy values are also evaluated, and it is observed that local entropy is close to global entropy. This ensures that the proposed scheme gives randomness in encrypted domain indicating a negligible information leakage and thus is secure against entropy attack.
4.2.6 Differential attack analysis
A differential attack is successful when an intruder is able to retrieve some clue about secret keys by slightly changing the plain image and comparing it with the encrypted image. In order to ensure robustness to such attack, it is required that a minute change in the plain image should be able to generate a huge difference in encrypted image. In other words, the diffusion of the system should be able to spread the difference over the entire image. There are two indicators that are used to quantify robustness to differential attack, NPCR (number of pixel change rate) and UACI (unified average change in intensity) [76, 77]. For a plain image with width W and height H,, let there be two ciphertexts generated (C1, C2) corresponding to the plain image and another with altered value at pixel location (i, j). These measures are mathematically defined as:
where \(D\left( {i,j} \right) = \left\{ {\begin{array}{*{20}l} {1,} \hfill & { C_{1} \left( {i,j} \right) \ne C_{2} \left( {i,j} \right) } \hfill \\ {0,} \hfill & {\text{ otherwise}} \hfill \\ \end{array} } \right.\)
where L = 256 for an 8-bit image. For a 256 Gy-level image encryption, the expected value of NPCR is 99.6094%, whereas that of UACI is 33.4635%. In the proposed scheme, we have modified a randomly selected pixel location (126, 137) for evaluating these parameters. The corresponding NPCR, UACI values are given in Table 10.
4.2.7 Classical attack analysis
There are four types of such attacks that include ciphertext only attack where it is assumed that the adversary has access to few ciphertext only [42], plaintext attack where it is assumed to have access to set of plaintext only, known-plaintext attack where knowledge of a set of plaintexts and corresponding ciphertext is available to the adversary and fourth is a chosen-plaintext attack where it is assumed that the adversary has access to set of plaintexts to be encrypted to obtain ciphertexts. As known ciphertext attack provides more information to an adversary, it is believed that if a ciphertext can resist a chosen ciphertext attack, it can also resist other types of attacks [78]. The proposed scheme is designed such that it is highly sensitive to keys. Moreover, the ciphertext is dependent on plaintexts as the initial conditions of the chaotic maps that are used in Stage 1 of encryption strongly depend on the plain input. Therefore, a unique ciphertext is generated corresponding to each plaintext. Hence, the proposed scheme is robust to the chosen ciphertext attack.
4.2.8 Data occlusion attack
There is a possibility of data loss while communicating images over heavy traffic channels or due to insecure channels. An effective encryption scheme should be able to recover the image even after occlusion attack if the data are uniformly diffused over the entire image. Post-processing techniques can be further used to recover the losses. To check the tolerance of the proposed scheme, encrypted data are subjected to varying amounts of data loss and corresponding decrypted images are checked for perceptual security. In Fig. 9, the first and third rows depict cropping in encrypted data (Lena image), whereas in the second and fourth rows corresponding decrypted images are shown. It is observed that image contour is still recoverable with up to 50% of data loss. The average values for data loss up to 12.5%, 25% and 50% are recorded in Table 11. The numerical values clearly indicate that the proposed scheme can resist data loss for recovery of the image which can be further improved by applying data post-processing techniques.
4.3 Noise attack analysis
Robustness against noise is an important index to check for the encryption scheme as distortion, degradation and corrupted data (coding error) are common in communication channels. The proposed scheme is checked for the addition of Gaussian noise with zero mean and varying variances to get data corresponding to different SNR (signal-to-noise ratio) between noisy and noise-free encrypted images. This can be mathematically explained as:
where \({{I}_{e}}^{{\prime}}\) is noisy image \({I}_{e}\) is the encrypted image, \(G\) represents the Gaussian noise with \(\sigma \) as its standard deviation. Figure 10 shows decrypted images when the encrypted images are distorted with different noise levels. The noise levels are quantified according to the SNR of noisy image with reference to encrypted image. MSE values are plotted for different SNR values. The plot clearly shows that error is proportional to the amount of noise in the encrypted domain. It is evident from Fig. 10 that image contour is detectable with as low as SNR of 1 dB, thereby giving testimony to the fact that the proposed scheme performs fair enough in a noisy environment and thus can resist noise attack.
4.3.1 Speed analysis
The run time of an encryption algorithm is an important issue for real-time applications. Optical transforms have an inherent property of fast and parallel processing. This is due to the optical setup that comprises SLM (for processing complex coefficients) and CCD (for storage). However, in the digital domain, the run time of an algorithm depends on the complexity associated with it. Therefore, a compromise between speed and complexity is highly desirable. The proposed scheme has multiple security layers for attaining substitution, transformation and permutation. The average encryption and decryption times are recorded in Table 12. It is likely to mention that run time can be further improved by optimization methods.
5 Comparative analysis
This section gives a brief summary on various comparisons of the proposed scheme with other similar state-of-the-art schemes. Firstly, by using a reality preserving algorithm [54], the complex computation is eliminated completely which is inherited in all DRPE and other optical transform domain-based encryption schemes [19, 21, 31, 36, 80, 81]. Another limitation in such similar schemes is the shorter key space, thereby leading to possibility of brute-force attack [28, 29, 82]. Table 13 lists some of the recent schemes with their key space for comparison with that of the proposed scheme.
On the bases of histogram analysis, the histogram in the encrypted domain with the proposed scheme is nearly uniform as compared to other similar schemes with optical transform domain [18, 19, 23, 40, 45, 64, 87]. The uniform histogram gives higher security against entropy attacks. A comparison of entropy values for RGB of image Lena is listed in Table 9.
Any encryption algorithm can be characterized by its decorrelating ability. For a comparison on this, Table 14 lists some of the recent published works in terms of their averaged correlation coefficients (with reference to Lena image).
Another important parameter for comparison is the decrypted image quality. To check, we have evaluated decryption error (DErr) as explained at the end of Sect. 4.2.2. DErr is ‘zero’ for all test images which clearly depicts that proposed scheme is lossless unlike some other recent schemes that are either fixed/single transform order-based [23, 40, 46, 65, 67, 86, 88] or others that are based on multiple parameters [43, 64, 74, 79, 89]. The PSNR of the decrypted image with reference to the original image (Lena image) is listed in Table 4. The proposed scheme is also robust to differential attacks as is evident from the analysis for NPCR and UACI values (Table 10).
6 Conclusion
Recently, many researchers have come up with image encryption schemes based on the optical transform domain. To overcome the limitations of shorter keyspace with the only transform-based approach, researchers have intertwined chaos and fractional transform domain in some way or other to get the benefit of both. Most of the schemes are focused on decorrelation based on fractional transform and chaos-based scrambling with different orders of their operation to improve security and also to enlarge the keyspace. However, these schemes fail to provide enough security due to certain limitations of the transform domain. The proposed scheme is based on three security layers with compound chaos-based substitution followed by decorrelation of pixels with a reality preserving fractional Hartley transform and another chaos-based permutation, thereby facilitating a lossless recovery at decryption. The proposed scheme is a novel method that not only enlarges the keyspace but also provides better robustness to most of the possible attacks. Security analysis and comparative analysis collectively give testimony to the efficacy of the scheme.
References
Chen, G., Mao, Y., Chui, C.K.: A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Solitons Fractals 21(3), 749–761 (2004). https://doi.org/10.1016/j.chaos.2003.12.022
Chiaraluce, F., Ciccarelli, L., Gambi, E., Pierleoni, P., Reginelli, M.: A new chaotic algorithm for video encryption. IEEE Trans. Consum. Electron. 48(4), 838–844 (2002). https://doi.org/10.1109/TCE.2003.1196410
Behnia, S., Akhshani, A., Mahmodi, H., Akhavan, A.: A novel algorithm for image encryption based on mixture of chaotic maps. Chaos Solitons Fractals 35(2), 408–419 (2008). https://doi.org/10.1016/j.chaos.2006.05.011
Patidar, V., Pareek, N.K., Purohit, G., Sud, K.K.: A robust and secure chaotic standard map based pseudorandom permutation–substitution scheme for image encryption. Opt. Commun. 284(19), 4331–4339 (2011). https://doi.org/10.1016/j.optcom.2011.05.028
Arroyo, D., Rhouma, R., Alvarez, G., Li, S., Fernandez, V.: On the security of a new image encryption scheme based on chaotic map lattices. Chaos Interdiscip. J. Nonlinear Sci. 18(3), 033112 (2008). https://doi.org/10.1063/1.2959102
Alawida, M., Teh, J.S., Samsudin, A.: An image encryption scheme based on hybridizing digital chaos and finite state machine. Signal Process. 164, 249–266 (2019). https://doi.org/10.1016/j.sigpro.2019.06.013
Alzaidi, A.A., Ahmad, M., Doja, M.N., Al Solami, E., Beg, M.S.: A new 1D chaotic map and β-Hill climbing for generating substitution-boxes. IEEE Access 6, 55405–55418 (2018). https://doi.org/10.1109/ACCESS.2018.2871557
Zhou, Y., Hua, Z., Pun, C.M., Chen, C.P.: Cascade chaotic system with applications. IEEE Trans. Cybern. 45(9), 2001–2012 (2015). https://doi.org/10.1109/ACCESS.2018.2871557
Lan, R., He, J., Wang, S., Gu, T., Luo, X.: Integrated chaotic systems for image encryption. Signal Process. 147, 133–145 (2018). https://doi.org/10.1016/j.sigpro.2018.01.026
Zhang, Y.Q., Wang, X.Y., Liu, J., Chi, Z.L.: An image encryption scheme based on the MLNCML system using DNA sequences. Opt. Lasers Eng. 82, 95–103 (2016). https://doi.org/10.1016/j.optlaseng.2016.02.002
Chai, X., Gan, Z., Chen, Y., Zhang, Y.: A visually secure image encryption scheme based on compressive sensing. Signal Process. 134, 35–51 (2017). https://doi.org/10.1016/j.sigpro.2016.11.016
Refreiger, P., Javidi, B.: Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 20(7), 767–769 (1995). https://doi.org/10.1364/OL.20.000767
Unnikrishnan, G., Singh, K.: Double random fractional Fourier domain encoding for optical security. Opt. Eng. 39(11), 2853–2860 (2000). https://doi.org/10.1117/1.1313498
Wang, Q., Guo, Q., Lei, L., Zhou, J.: Iterative partial phase encoding based on joint fractional Fourier transform correlator adopting phase-shifting digital holography. Opt. Commun. 313, 1–8 (2014). https://doi.org/10.1016/j.optcom.2013.09.058
Mendlovic, D., Ozaktas, H.M.: Fractional Fourier transforms and their optical implementation: I. JOSA 10(9), 1875–1881 (1993). https://doi.org/10.1364/JOSAA.10.001875
Namias, V.: The fractional order fourier transform and its application to quantum mechanics. IMA J. Appl. Math. 25(3), 241–265 (1980). https://doi.org/10.1093/imamat/25.3.241
Ozaktas, H.M., Arikan, O., Kutay, M.A., Bozdagt, G.: Digital computation of the fractional Fourier transform. IEEE Trans. Signal Process. 44(9), 2141–2150 (1996). https://doi.org/10.1109/78.536672
Mishra, D.C., Sharma, R.K., Suman, S., Prasad, A.: Multi-layer security of color image based on chaotic system combined with RP2DFRFT and Arnold transform. J. Inf. Secur. Appl. 37, 65–90 (2017). https://doi.org/10.1016/j.jisa.2017.09.006
Hwang, H.: Optical color image encryption based on the wavelength multiplexing using cascaded phase-only masks in Fresnel transform domain. Opt. Commun. 285(5), 567–573 (2012). https://doi.org/10.1016/j.optcom.2011.11.007
Wang, Y., Quan, C., Tay, C.J.: Optical color image encryption without information disclosure using phase-truncated Fresnel transform and a random amplitude mask. Opt. Commun. 344, 147–155 (2015). https://doi.org/10.1016/j.optcom.2015.01.045
Sui, L., Liu, B., Wang, Q., Li, Y., Liang, J.: Color image encryption by using Yang-Gu mixture amplitude-phase retrieval algorithm in gyrator transform domain and two-dimensional Sine logistic modulation map. Opt. Lasers Eng. 75, 17–26 (2015). https://doi.org/10.1016/j.optlaseng.2015.06.005
Abuturab, M.: Securing color image using discrete cosine transform in gyrator transform domain structured-phase encoding. Opt. Lasers Eng. 50(10), 1383–1390 (2012). https://doi.org/10.1016/j.optlaseng.2012.04.011
Zhou, N., Wang, Y., Gong, L.: Novel optical image encryption scheme based on fractional Mellin transform. Opt. Commun. 284(13), 3234–3242 (2011). https://doi.org/10.1016/j.optcom.2011.02.065
Vashisth, S., Singh, H., Yadav, A.K., Singh, K.: Image encryption using fractional Mellin transform, structured phase filters, and phase retrieval. Optik 125(18), 5309–5315 (2014). https://doi.org/10.1007/978-981-13-1642-5_29
Bracewell, R.N.: Aspects of the Hartley transform. Proc. IEEE 82(3), 381–387 (1994). https://doi.org/10.1109/5.272142
Liu, Z., Zhang, Y., Liu, W., Meng, F., Wu, Q., Liu, S.: Optical color image hiding scheme based on chaotic mapping and Hartley transform. Opt. Lasers Eng. 51(8), 967–972 (2013). https://doi.org/10.1016/j.optlaseng.2013.02.015
Singh, N., Sinha, A.: Optical image encryption using improper Hartley transforms and chaos. Optik 121(10), 918–925 (2010). https://doi.org/10.1016/j.ijleo.2008.09.049
Ghadirli, H.M., Nodehi, A., Enayatifar, R.: An overview of encryption algorithms in color images. Signal Process. 164, 163–185 (2019). https://doi.org/10.1016/j.sigpro.2019.06.010
Chen, J., Bao, N., Li, J., Zhu, Z.L., Zhang, L.Y.: Cryptanalysis of optical ciphers integrating double random phase encoding with permutation. IEEE Access 5, 16124–16129 (2017). https://doi.org/10.1109/ACCESS.2017.2735420
Singh, P., Yadav, A.K., Singh, K.: Known-Plaintext attack on cryptosystem based on fractional hartley transform using particle swarm optimization algorithm. In: Engineering Vibration, Communication and Information Processing, Singapore, pp. 317–327 (2019). https://doi.org/10.1007/978-981-13-1642-5_29
Kumar, P., Joseph, J. and Singh, K.: Double random phase encoding based optical encryption systems using some linear canonical transforms: weaknesses and countermeasures. In: Linear Canonical Transforms, pp. 367–396. Springer, New York (2016). https://doi.org/10.1007/978-1-4939-3028-9_13
Kathleen, T., Tim, D. and James, A.: Chaos: an introduction to dynamical systems. Physics Today, vol. 50, pp. 67–68. Publisher: Springer-Verlag, New York (1997). ISBN 3-540-78036-x
Alvarez, G., Li, S.: Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 16(8), 2129–2151 (2006). https://doi.org/10.1142/S0218127406015970
Huang, C.K., Nien, H.H.: Multi chaotic systems based pixel shuffle for image encryption. Opt. Commun. 282(11), 2123–2127 (2009). https://doi.org/10.1016/j.optcom.2009.02.044
Teh, J.S., Alawida, M., Sii, Y.C.: Implementation and practical problems of chaos-based cryptography revisited. J. Inf. Secur. Appl. 50, 102421 (2020). https://doi.org/10.1016/j.jisa.2019.102421
Zhang, Y., Xiao, D.: Double optical image encryption using discrete Chirikov standard map and chaos-based fractional random transform. Opt. Lasers Eng. 51(4), 472–480 (2013). https://doi.org/10.1016/j.optlaseng.2012.11.001
Li, H., Wang, Y.: Double-image encryption based on discrete fractional random transform and chaotic maps. Opt. Lasers Eng. 49(7), 753–757 (2011). https://doi.org/10.1016/j.optlaseng.2011.03.017
Singh, N., Sinha, A.: Gyrator transform-based optical image encryption, using chaos. Opt. Lasers Eng. 47(5), 539–546 (2009). https://doi.org/10.1016/j.optlaseng.2008.10.013
Wu, J., Guo, F., Liang, Y., Zhou, N.: Triple color images encryption algorithm based on scrambling and the reality-preserving fractional discrete cosine transform. Optik 125(16), 4474–4479 (2014). https://doi.org/10.1016/j.ijleo.2014.02.026
Singh, P., Yadav, A.K., Singh, K.: Phase image encryption in the fractional Hartley domain using Arnold transform and singular value decomposition. Opt. Lasers Eng. 91, 187–195 (2017). https://doi.org/10.1016/j.optlaseng.2016.11.022
Li, C., Li, S., Asim, M., Nunez, J., Alvarez, G., Chen, G.: On the security defects ofan image encryption scheme. Image Vis. Comput. 27(9), 1371–1381 (2009). https://doi.org/10.1016/j.imavis.2008.12.008
Chang, X., Yan, A., Zhang, H.: Ciphertext-only attack on optical scanning cryptography. Opt. Lasers Eng. 126, 105901 (2020). https://doi.org/10.1016/j.optlaseng.2019.105901
Lang, J.: Image encryption based on the reality-preserving multiple-parameter fractional Fourier transform and chaos permutation. Opt. Lasers Eng. 50(7), 929–937 (2012). https://doi.org/10.1016/j.optlaseng.2012.02.012
Sui, L., Duan, K., Liang, J., Zhang, Z., Meng, H.: Asymmetric multiple-image encryption based on coupled logistic maps in fractional Fourier transform domain. Opt. Lasers Eng. 62, 139–152 (2014). https://doi.org/10.1016/j.optlaseng.2014.06.003
Ran, Q., Yuan, L., Zhao, T.: Image encryption based on nonseparable fractional Fourier transform and chaotic map. Opt. Commun. 348, 43–49 (2015). https://doi.org/10.1016/j.optcom.2015.03.016
Kaur, G., Agarwal, R., Patidar, V.: Multiple image encryption with fractional Hartley transform and robust chaotic mapping. In: 6th International Conference on Signal Processing and Integrated Networks (SPIN), pp. 399–403. IEEE (2019). https://doi.org/10.1109/SPIN.2019.8711777
McBride, A.C., Kerr, F.H.: On Namias’s fractional Fourier transforms. IMA J. Appl. Math. 39(2), 159–175 (1987). https://doi.org/10.1093/imamat/39.2.159
Condon, E.: Theories of optical rotatory power. Rev. Mod. Phys. 9(4), 432 (1937). https://doi.org/10.1103/RevModPhys.9.432
Ozaktas, H.M., Mendlovic, D.: Fractional Fourier transforms and their optical implementation II. JOSA A 10(12), 2522–2531 (1993). https://doi.org/10.1364/JOSAA.10.002522
Almeida, L.B.: The fractional Fourier transform and time-frequency representations. IEEE Trans. Signal Process. 42(11), 3084–3091 (1994). https://doi.org/10.1109/78.330368
Pei, S.C., Tseng, C.C., Yeh, M.H., Shyu, J.J.: Discrete fractional Hartley and Fourier transforms. IEEE Trans. Circuits Syst. II Analog Digit. Signal Process. 45(6), 665–675 (1998). https://doi.org/10.1109/82.686685
Pei, S.C., Ding, J.J.: Fractional cosine, sine, and Hartley transforms. IEEE Trans. Signal Process. 50(7), 1661–1680 (2002). https://doi.org/10.1109/TSP.2002.1011207
Zhao, D., Li, X., Chen, L.: Optical image encryption with redefined fractional Hartley transform. Opt. Commun. 281(21), 5326–5329 (2008). https://doi.org/10.1016/j.optcom.2008.07.049
Venturini, I., Duhamel, P.: Reality preserving fractional transforms [signal processing applications]. In: Acoustics, Speech, and Signal Processing 5(V-205), France (2004). https://doi.org/10.1109/ICASSP.2004.1327083
Shannon, C.E.: Communication theory of secrecy systems. Bell Syst. Tech. J. 28(4), 656–715 (1949). https://doi.org/10.1002/j.1538-7305.1949.tb00928.x
Zhou, L.H., Feng, Z.J.: A new idea of using one-dimensional PWL map in digital secure communications-dual-resolution approach. IEEE Trans. Circuits Syst. II Analog Digit. Signal Process. 47(10), 1107–1111 (2000). https://doi.org/10.1109/82.877154
Li, S., Chen, G., Mou, X.: On the dynamical degradation of digital piecewise linear chaotic maps. Int. J. Bifurc. Chaos 15(10), 3119–3151 (2005). https://doi.org/10.1142/S0218127405014052
Zhou, Y., Bao, L., Chen, C.P.: A new 1D chaotic system for image encryption. Signal Process. 97, 172–182 (2014). https://doi.org/10.1016/j.sigpro.2013.10.034
May, R.M.: Simple mathematical models with very complicated dynamic. Nature 261(5560), 459 (1976)
Al-Shameri, W.F.H., Mahiub, M.A.: Some dynamical properties of the family of tent maps. Int. J. Math. Anal. 7(29), 1433–1449 (2013). https://doi.org/10.12988/ijma.2013.3361
Weber, A.G.: The USC-SIPI image database version 5. USC-SIPI Report, 315(1) (1997)
Talhaoui, M.Z., Wang, X., Talhaoui, A.: A new one-dimensional chaotic map and its application in a novel permutation-less image encryption scheme. Vis. Comput. (2020). https://doi.org/10.1007/s00371-020-01936-z
Wang, Z., Bovik, A.C., Sheikh, H.R., Simoncelli, E.P.: Image quality assessment: from error visibility to structural similarity. IEEE Trans. Image Process. 13(4), 600–612 (2004). https://doi.org/10.1109/TIP.2003.819861
Azoug, S.E., Bouguezel, S.: A non-linear preprocessing for opto-digital image encryption using multiple-parameter discrete fractional Fourier transform. Opt. Commun. 359, 85–94 (2016). https://doi.org/10.1016/j.optcom.2015.09.054
Faragallah, O.S., Alzain, M.A., El-Sayed, H.S., Al-Amri, J.F., El-Shafai, W., Afifi, A., Naeem, E.A., Soh, B.: Block-based optical color image encryption based on double random phase encoding. IEEE Access 7, 4184–4194 (2019). https://doi.org/10.1109/ACCESS.2018.2879857
Murillo-Escobar, M.A., Cruz-Hernández, C., Abundiz-Pérez, F., López-Gutiérrez, R.M., Del Campo, O.A.: A RGB image encryption algorithm based on total plain image characteristics and chaos. Signal Process. 109, 119–131 (2015). https://doi.org/10.1016/j.sigpro.2014.10.033
Souyah, A., Faraoun, K.M.: An image encryption scheme combining chaos-memory cellular automata and weighted histogram. Nonlinear Dyn. 86(1), 639–653 (2016). https://doi.org/10.1007/s11071-016-2912-0
Jain, R., Sharma, J.B.: Symmetric color image encryption algorithm using fractional DRPM and chaotic baker map. In: IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT) (2016). https://doi.org/10.1109/RTEICT.2016.7808152
Farah, M.B., Guesmi, R., Kachouri, A., Samet, M.: A novel chaos based optical image encryption using fractional Fourier transform and DNA sequence operation. Opt. Laser Technol. 121, 105777 (2020). https://doi.org/10.1016/j.optlastec.2019.105777
Li, G.: Double chaotic image encryption algorithm based on optimal sequence solution and fractional transform. Vis. Comput. 35(9), 1267–1277 (2019). https://doi.org/10.1007/s00371-018-1574-y
Kang, X., Ming, A., Tao, R.: Reality-preserving multiple parameter discrete fractional angular transform and its application to color image encryption. IEEE Trans. Circuits Syst. Video Technol. 29(6), 1595–1607 (2018). https://doi.org/10.1109/TCSVT.2018.2851983
Lian, S.: Multimedia content encryption: techniques and applications. Auerbach Publication, Taylor & Francis Group (2008). ISBN-13: 978-1-4200-6527-5
Wu, Y., Zhou, Y., Saveriades, G., Agaian, S., Noonan, J.P., Natarajan, P.: Local Shannon entropy measure with statistical tests for image randomness. Inf. Sci. 222, 323–342 (2013). https://doi.org/10.1016/j.ins.2012.07.049
Kaur, G., Agarwal, R., Patidar, V.: Chaos based multiple order optical transform for 2D image encryption. Eng. Sci. Technol. Int. J. 23(5), 998–1014 (2020). https://doi.org/10.1016/j.jestch.2020.02.007
Liu, H., Kadir, A.: Asymmetric color image encryption scheme using 2D discrete-time map. Signal Process. 113, 104–112 (2015). https://doi.org/10.1016/j.aeue.2014.02.002
Wu, Y., Noonan, J.P., Agaian, S.: NPCR and UACI randomness tests for image encryption. Cyber J. Multidiscip. J. Sci. Technol. J. Sel. Areas Telecommun. (JSAT) 1(2), 31–38 (2011)
Tong, X.J., Zhang, M., Wang, Z., Liu, Y., Xu, H., Ma, J.: A fast encryption algorithm of color image based on four-dimensional chaotic system. J. Vis. Commun. Image Represent. 33, 219–234 (2015). https://doi.org/10.1016/j.jvcir.2015.09.014
Wang, X.Y., Li, P., Zhang, Y.Q., Liu, L.Y., Zhang, H., Wang, X.: A novel color image encryption scheme using DNA permutation based on the Lorenz system. Multimed. Tools Appl. 77(5), 6243–6265 (2018). https://doi.org/10.1007/s11042-017-4534-z
Kang, X., Tao, R., Zhang, F.: Multiple-parameter discrete fractional transform and its applications. IEEE Trans. Signal Process. 64(13), 3402–3417 (2016). https://doi.org/10.1109/TSP.2016.2544740
Liu, Z., Xu, L., Lin, C., Dai, J., Liu, S.: Image encryption scheme by using iterative random phase encoding in gyrator transform domains. Opt. Lasers Eng. 49(4), 542–546 (2011). https://doi.org/10.1016/j.optlaseng.2010.12.005
Zhou, N., Li, H., Wang, D., Pan, S., Zhou, Z.: Image compression and encryption scheme based on 2D compressive sensing and fractional Mellin transform. Opt. Commun. 343, 10–21 (2015). https://doi.org/10.1016/j.optcom.2014.12.084
Ran, Q., Zhang, H., Zhang, J., Tan, L., Ma, J.: Deficiencies of the cryptography based on multiple-parameter fractional Fourier transform. Opt. Lett. 34(11), 1729–1731 (2009). https://doi.org/10.1364/OL.34.001729
Liu, H., Kadir, A., Niu, Y.: Chaos-based color image block encryption scheme using S-box. AEU-Int. J. Electron. Commun. 68(7), 676–686 (2014). https://doi.org/10.1016/j.sigpro.2015.01.016
Wu, X., Kan, H., Kurths, J.: A new color image encryption scheme based on DNA sequences and multiple improved 1D chaotic maps. Appl. Soft Comput. 37, 24–39 (2015). https://doi.org/10.1016/j.asoc.2015.08.008
Enayatifar, R., Sadaei, H.J., Abdullah, A.H., Lee, M., Isnin, I.F.: A novel chaotic based image encryption using a hybrid model of deoxyribonucleic acid and cellular automata. Opt. Lasers Eng. 71, 33–41 (2015). https://doi.org/10.1016/j.optlaseng.2015.03.007
Hu, G., Kang, X., Guo, Z., Luo, X.: A novel image encryption scheme based on hidden random disturbance and feistel RPMPFrHT network. In: Chinese Conference on Image and Graphics Technologies. Springer, Singapore (2018). https://doi.org/10.1007/978-981-13-1702-6_25
Hennelly, B., Sheridan, J.T.: Optical image encryption by random shifting in fractional Fourier domains. Opt. Lett. 28(4), 269–271 (2003). https://doi.org/10.1364/OL.28.000269
Sui, L., Gao, B.: Single-channel color image encryption based on iterative fractional Fourier transform and chaos. Opt. Laser Technol. 48, 117–127 (2013). https://doi.org/10.1016/j.optlastec.2012.10.016
Shan, M., Chang, J., Zhong, Z., Hao, B.: Double image encryption based on discrete multiple-parameter fractional Fourier transform and chaotic maps. Opt. Commun. 285(21–22), 4227–4234 (2012). https://doi.org/10.1016/j.optcom.2012.06.023
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kaur, G., Agarwal, R. & Patidar, V. Color image encryption scheme based on fractional Hartley transform and chaotic substitution–permutation. Vis Comput 38, 1027–1050 (2022). https://doi.org/10.1007/s00371-021-02066-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00371-021-02066-w