Abstract
It’s easy to access Internet resources in the cloud environment. And it’s important to protect the legal users’ privacy and confidentiality. Recently, Hou and Wang proposed a robust and efficient user authentication scheme based on elliptic curve cryptosystem. Their scheme was practical and easy to implement. They claimed that their scheme could against off-line password guessing, DoS, server spoofing, replay, parallel session and impersonation attacks. In this article, we will show that Hou-Wang’s scheme is vulnerable to the guessing attack with smart card. In this article, we also propose an improved Hou-Wang’s user authentication scheme to withstand the vulnerability in their scheme.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
It’s easy to access Internet resources in the cloud environment. In order to protect the users could have the access right to obtain the resources provided by the remote server, the remote user authentication schemes were proposed [1,2,3,4,5,6,7,8,9,10,11]. Furthermore, it’s also important to protect the legal users’ privacy and confidentiality. To authenticate a user from Internet, many user authentication schemes had been proposed in past decades. Many schemes were applied a smart card to authenticate the legal users [12,13,14,15,16,17,18,19,20,21]. One of these schemes was developed for multi-servers [22,23,24,25,26,27]. One of these schemes was developed for biometrics [28,29,30]. One of these schemes was applied passwords for generating session key [31, 32].
In 2012, Li, Liu, and Wu proposed a secure remote user authentication to withstand the spoofing attack, forgery attack, and password guessing attack [33]. Unfortunately, Feng, Chao, and Hwang found the security of Li-Liu-Wu’s scheme was vulnerable to password guessing attacks [34]. In 2012, Yoon et al. proposed an efficient remote user authentication scheme [35]. Unfortunately, Chen, Liang, and Hwang found their scheme is insecure to against the password guessing attack [36]. In 2014, Huang, Chang, Yu proposed a user authentication scheme which is based on timestamp [37]. Huabg et al. claimed their scheme could withstand the impersonated attack and more secure than other schemes. However, Feng, Liang, Hwang found that their scheme was vulnerable to the legal user’s smart card and password guessing attack [38].
Recently, Hou and Wang proposed a robust and efficient user authentication scheme based on elliptic curve cryptosystem [39]. Hou-Wang’s scheme is practical. They claimed that their scheme could against the off-line password guessing, DoS, spoofing, replay, parallel session, and impersonation attacks. In this article, we will show that Hou-Wang’s scheme is vulnerable to the guessing attack with smart card. In this article, we also propose an improved Hou-Wang’s user authentication scheme to withstand the vulnerability in their scheme.
2 Review of Hou-Wang Scheme
There are two main participants in Hou-Wang’s scheme: a user Ui and server S [39]. We briefly describe Hou-Wang’s scheme as follows.
The Registration Phase. In this registration phase, a new user (Ui) needs to apply to the server for as a legal user. After the phase, the server will make and issue a smart card for the new user (Ui). The smart card contains the following five parameters: {Bi, H(), G, Ek(), and Dk()}, here Bi = EAi(H(x || ni) || niG); Ai = H(IDi || PWi); where H() denotes a hash function; IDi and PWi denote an identity and password of the new user, respectively. x and ni denote a server’s master secret key and a random number for Ui, respectively. G denotes a public base point of elliptic curve; Ek() and Dk() denote an enciphering and deciphering algorithms with the secret key k, respectively. The server S maintains and keeps a registration table with two columns: H(IDi ⊕ x)G and ni.
The Login Phase. In this phase, when the user (Ui) wants to have the access right to obtain the resources provided by the remote server, Ui keys in his/her identity (IDi) and password (PWi) to the client devise with smart card. The smart card sends {Ci, Di} to the server S: Ai = H(IDi || PWi); Bi = EAi(H(x || ni) || niG); H(x || ni) || niG = DAi(Bi); Ci = t G; Ki = t Pubs; Di = EKi(IDi || H(x || ni)), where t denotes a random nonce in Zp*. Pubs is the server’s public key, Pubs = x G.
The Authentication and Session Key Exchange Phase. In this authentication and session key exchange phase, the server (S) verifies Ui as follows.
-
(1)
After receiving {Ci, Di}, the server calculates and obtains the deciphering key Ki, Ui, and H(x || ni) as follows: K’i = x Ci; ID’i || H(x’ || n’i) = DK’i(Di). Next, S computes H(ID’i ⊕ x)G and retrieves the random number ni of Ui from the registration table.
-
(2)
S computes H(x || ni) and then verifies H(x || ni) is whether or not equal to H(x’ || n’i). If it is not holds, S terminates this phase. Next, S sends {Ei, Fi} to Ui, where Ei = s G; Fi = s Ci + niG, where s denotes a random nonce in Zp*.
-
(3)
The smart card checks Ei and Fi. The server also authenticates the legal user. Finally, the server and smart card share the session key SK = stG.
3 The Weakness and the Improved of Hou-Wang Scheme
In this section, we show the weakness of Hou-Wang’s remote user authentication scheme [39]. The main weakness of Hou-Wang’s scheme is that their scheme could not against the on-line password guessing attack with user’s smart card (SC for short). A user Ui’s smart card may be lost or stolen by an adversary. The adversary could try to guess the user’s password.
-
(1)
The adversary inserts the user Ui’s smart card to his/her client device. Next, the adversary keys in the identity of the user Ui and guesses a password PW’i.
-
(2)
SC sends {Ci, Di} to the server S: A’i = H(IDi || PW’i); Bi = EAi(H(x || ni) || niG); H’(x || ni) || n’iG = DA’i(Bi); Ci = t G; Ki = t Pubs; Di = EKi(IDi || H’(x || ni)).
-
3)
The server performs Steps (1) and (2) in the authentication and session key exchange phase to verify the user (adversary) legally. If the guessing password by the adversary is correct, the adversary will receive {Ei, Fi} from the server. Otherwise, the adversary guesses the other password PW’i and repeats Step (1).
In order to improve the weakness of Hou-Wang’s remote user authentication scheme, we propose an improvement of Hou-Wang’s scheme in this section. The password changing and the smart revocation phases are the same as that in Hou-Wang’s scheme.
The Registration Phase. In this phase, a new user (Ui) needs to apply to the server for as a legal user. After the phase, the server will make and issue a smart card for Ui. The smart card contains {Bi, H(), G, Ek(), and Dk()}, where Bi = EAi(H(x || ni) || niG); Ai = H(IDi || PWi). The server S maintains and keeps a registration table with three columns: H(IDi ⊕ x)G, ni, and counter (see Table 1). The counter is used to record the times of failing to login the server.
The Login Phase. This phase is similar to that of Hou-Wang scheme. In this phase, when Ui wants to have the access right to obtain the resources provided by the remote server, Ui keys in his/her identity (IDi) and inputs his/her password (PWi) to the client devise with smart card. The smart card sends {Ci, Di} to the server S: Ai = H(IDi || PWi); H(x || ni) || niG = DAi(Bi); Ci = t G; Ki = t Pubs; Di = EKi(IDi || H(x || ni)).
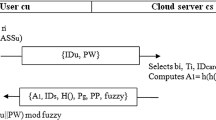
The Authentication and Session Key Exchange Phase. In this authentication and session key exchange phase, S verifies Ui as follows (see Fig. 1).
-
(1)
After receiving {Ci, Di}, the server calculates and obtains the deciphering key Ki, the Ui identity, and H(x || ni) as follows: K’i = x Ci; ID’i || H(x’ || n’i) = DK’i(Di).
-
(2)
S computes H(ID’i ⊕ x)G and retrieves the random number ni of Ui from Table 1.
-
(3)
S computes H(x || ni) and then verifies H(x || ni) is whether or not equal to H(x’ || n’i). If it is not holds, the server stops this procedure and adds 1 to the counter in Table 1. If the counter is greater than 3, the server removes the user’s information from registration table. The user needs to re-makes a registration for sharing the server’s resource.
-
(4)
The server S sends {Ei, Fi} to the user Ui, where Ei = s G; Fi = s Ci + ni G, where s denotes a random nonce in Zp*.
-
(5)
The smart card computes F’i = tEi + ni and then checks F’i is whether or not equal to Fi. If it holds, computes and sends the verification message Ri to the server: Ri = H(tEi || Ei || Ci).
-
(6)
The server computes R’i = H(sCi || Ei || Ci) and checks R’i whether equal to Ri. If it holds, S thus authenticates the legal user.
-
(7)
The server and the smart card share the session key SK = stG.
Subsequent paragraphs, however, are indented.
4 Conclusions
In summary, we have shown that the weakness of Hou-Wang’s remote user authentication scheme. Hou-Wang’s scheme could not against the on-line password guessing attack with smart card. In this article, we also proposed an improvement of Hou-Wang’s remote user authentication scheme to improve the weakness in Hou-Wang’s scheme.
References
Tsai CS, Lee CC, Hwang MS (2006) Password authentication schemes: current status and key issues. Int J Netw Secur 3:101–115
Yang CC, Chang TY, Hwang MS (2003) The security of the improvement on the methods for protecting password transmission. Informatica 14:551–558
Zhuang X, Chang CC, Wang ZH, Zhu Y (2014) A simple password authentication scheme based on geometric hashing function. Int J Netw Secur 16:271–277
Ling CH, Chao WY, Chen SM, Hwang MS (2015) Cryptanalysis of dynamic identity based on a remote user authentication scheme for a multi-server environment. In: Advances in engineering research, vol 15. Atlantis Press, pp 981–986
Liu Y, Chang CC, Chang SC (2017) An efficient and secure smart card based password authentication scheme. Int J Netw Secur 19(1):1–10
Liu CW, Tsai CY, Hwang MS (2017) Cryptanalysis of an efficient and secure smart card based password authentication scheme. In: Advances in intelligent systems and computing, recent developments in intelligent systems and interactive applications, vol 541. Springer, pp 188–193 (2017)
Wei J, Liu W, Hu X (2016) Secure and efficient smart card based remote user password authentication scheme. Int J Netw Secur 18(4):782–792
Tsai CY, Pan CS, Hwang MS (2017) An improved password authentication scheme for smart card. In: Advances in intelligent systems and computing, recent developments in intelligent systems and interactive applications, vol 541. Springer, pp 194–199
Thandra PK, Rajan J, Satya Murty SAV (2016) Cryptanalysis of an efficient password authentication scheme. Int J Netw Secur 18(2):362–368
Pan CS, Tsai CY, Tsaur SC, Hwang MS (2016) Cryptanalysis of an efficient password authentication scheme. In: The 3rd IEEE international conference on systems and informatics, Shaihai, pp 732–737
Pan HT, Pan, CS, Tsaur, SC, Hwang, MS (2017) Cryptanalysis of efficient dynamic ID based remote user authentication scheme in multi-server environment using smart card. In: 12th international conference on computational intelligence and security, Wuxi, China, pp 590–593
He D, Chen J, Hu J (2011) Weaknesses of a remote user password authentication scheme using smart card. Int J Netw Secur 13:58–60
Hwang MS, Chong SK, Chen TY (2000) Dos-resistant ID-based password authentication scheme using smart cards. J Syst Softw 83:163–172
Hwang MS, Li LH (2000) A new remote user authentication scheme using smart cards. IEEE Trans Consum Electron 46:28–30
Kumar M, Gupta MK, Kumari S (2011) An improved efficient remote password authentication scheme with smart card over insecure networks. Int J Netw Secur 13:167–177
Ramasamy R, Muniyandi AP (2012) An efficient password authentication scheme for smart card. Int J Netw Secur 14:180–186
Shen JJ, Lin CW, Hwang MS (2003) Security enhancement for the timestamp-based password authentication scheme using smart cards. Comput Secur 22:591–595
Shen JJ, Lin CW, Hwang MS (2003) A modified remote user authentication scheme using smart cards. IEEE Trans Consum Electron 49:414–416
Tang H, Liu X, Jiang L (2013) A robust and efficient timestamp-based remote user authentication scheme with smart card lost attack resistance. Int J Netw Secur 15:446–454
Yang L, Ma JF, Jiang Q (2012) Mutual authentication scheme with smart cards and password under trusted computing. Int J Netw Secur 14:156–163
Ghosh D, Li C, Yang C (2018) A lightweight authentication protocol in smart grid. Int J Netw Secur 20(3):414–422
Feng TH, Ling CH, Hwang MS (2014) Cryptanalysis of Tan’s improvement on a password authentication scheme for multi-server environments. Int J Netw Secur 16:318–321
He D, Zhao W, Wu S (2013) Security analysis of a dynamic id-based authentication scheme for multi-server environment using smart cards. Int J Netw Secur 15:282–292
Li LH, Lin IC, Hwang MS (2001) A remote password authentication scheme for multi-server architecture using neural networks. IEEE Trans Neural Netw 12:1498–1504
Lin IC, Hwang MS, Li LH (2003) A new remote user authentication scheme for multi-server architecture. Futur Gener Comput Syst 19:13–22
Amin R (2016) Cryptanalysis and efficient dynamic ID based remote user authentication scheme in multi-server environment using smart card. Int J Netw Secur 18(1):172–181
Mohan NBM, Chakravarthy ASN, Ravindranath C (2018) Cryptanalysis of design and analysis of a provably secure multi-server authentication scheme. Int J Netw Secur 20(2):217–224
Li CT, Hwang MS (2010) An online biometrics-based secret sharing scheme for multiparty cryptosystem using smart cards. Int J Innov Comput Inf Control 6:2181–2188
Li CT, Hwang MS (2010) An efficient biometrics-based remote user authentication scheme using smart cards. J Netw Comput Appl 33:1–5
Prakash A (2014) A biometric approach for continuous user authentication by fusing hard and soft traits. Int J Netw Secur 16:65–70
Zhu H, Zhang Y (2017) An improved two-party password-authenticated key agreement protocol with privacy protection based on chaotic maps. Int J Netw Secur 19(4):487–497
Wu M, Chen J, Wang R (2017) An enhanced anonymous password-based authenticated key agreement scheme with formal proof. Int J Netw Secur 19(5):785–793
Li J, Liu S, Wu S (2012) Cryptanalysis and improvement of a YS-like user authentication scheme. Int J Digit Conten Technol Appl 7(1):828–836
Feng TH, Chao WY, Hwang MS (2014) Cryptanalysis and improvement of the Li-Liu-Wu user authentication scheme. In: International conference on future communication technology and engineering, Shenzhen, China, pp 103–106
Yoon EJ, Kim SH, Yoo KY (2012) A security enhanced remote user authentication scheme using smart cards. Int J Innov Comput, Inf Control 8(5):3661–3675
Chen TY, Ling CH, Hwang MS (2014) Weaknesses of the Yoon-Kim-Yoo remote user authentication scheme using smart cards. In: IEEE workshop on electronics, computer and applications, Ottawa, Canada, pp 771–774
Huang HF, Chang HW, Yu PK (2014) Enhancement of timestamp-based user authentication scheme with smart card. Int J Netw Secur 16:463–467
Feng TH, Ling CH, Hwang MS (2014) An improved timestamp-based user authentication scheme with smart card. In: The 2nd congress on computer science and application, Sanya, China, pp 111–117 (2014)
Hou G, Wang Z (2017) A robust and efficient remote authentication scheme from elliptic curve cryptosystem. Int J Netw Secur 19(6):904–911
Acknowledgements
This work was partially supported by the Ministry of Science and Technology, Taiwan, under grant MOST 106-2221-E-468-002.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Hwang, MS., Yang, HW., Yang, CY. (2019). An Improved Hou-Wang’s User Authentication Scheme. In: Kim, K., Baek, N. (eds) Information Science and Applications 2018. ICISA 2018. Lecture Notes in Electrical Engineering, vol 514. Springer, Singapore. https://doi.org/10.1007/978-981-13-1056-0_31
Download citation
DOI: https://doi.org/10.1007/978-981-13-1056-0_31
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-13-1055-3
Online ISBN: 978-981-13-1056-0
eBook Packages: EngineeringEngineering (R0)