Abstract
When the channel fading is assumed to be fast fading and the transient variation of the channel gain is considered, the signal-to-interference noise ratio (SINR, Signal to Interference plus Noise Ratio) of the secondary user changes with the channel gain. This will cause some secondary users to fail to get the SINR, required for normal communication if the secondary user transmit power is enhanced, although it meets the secondary user communication requirements, at the same time, the interference to the primary user exceeds the interference threshold. Affects the normal communication of the primary user. In order to solve this problem, a robust power control algorithm based on probabilistic constraints is proposed. In this paper, the average SINR model is transformed into the uncertain distribution model by introducing the uncertain parameters satisfying the exponential distribution. In this paper, the SINR probability density functions of primary and secondary users are given, and the probabilistic constraints are transformed into deterministic constraints. In order to solve the secondary user transmit power, the interference temperature of the primary user is taken as the constraint condition, and the complete iterative algorithm is used to realize the fast convergence of the secondary user transmit power. Since the protection of the primary user will lead to the damage of the interests of some secondary users, this chapter introduces the admission control, according to the highest degree of dissatisfaction first eliminate the mode of the sub-users who do not meet the requirements of communication to implement admission control. The number of secondary users meeting the communication condition in the system is increased. The simulation results show that the algorithm can quickly identify the secondary users who do not meet the communication conditions, and avoid the excessive elimination of the secondary users, increase the number of secondary users who can communicate normally, and increase the total throughput of the system.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- Cognitive radio
- Underlay spectrum sharing
- Distributed power control
- Probabilistic constraints
- Robust power control
1 Introduction
There are many factors affecting the wireless channel, and the channel state is also time-varying and stochastic. At present, most researches only consider the accurate known channel state and ignore the influence of channel uncertainty, which leads to the failure to guarantee the communication quality of each user [1]. The instability of the wireless signal is caused by the variability of the wireless channel, so the channel gain from the signal transmitter to the signal receiver is also variable. Wireless signals are generally divided into three kinds of fading: free space fading, shadow slow fading and multipath fast fading.
The uncertainty of channel parameters is an important problem in wireless communication. Some scholars consider the influence of the transient change of channel gain on the system, and adopt remedial measures to reduce the influence of the system. This method can be regarded as a “compensation method” [2]. In reference [3], the problem of distributed robust transmission scheduling and power control in cognitive space-time division multiple access (STDMA) networks is studied. By considering the uncertainty of channel gain, the QoS conflict caused by the transient channel gain is avoided, and a distributed two-level algorithm for distributed column generation is proposed. At the same time, the bound of signal-to-noise ratio (SINR) constraint violation probability and the expected number of additional time slots needed to meet the needs of the user’s link traffic are derived. Reference [4] considers cognitive radio networks where a single primary user and multiple secondary users coexist. According to the channel conditions, the SNR is dynamically adjusted under the given BER requirement, and the admission control is adopted to eliminate the SINR secondary users. In reference [5], a robust ergodic resource allocation scheme (ERA, Ergodic Resource Allocation),) is proposed under the framework of underlying heterogeneous networks based on orthogonal frequency division multiple access (OFDMA). This scheme not only guarantees the interference requirement of macro network, but also improves the average and speed of the network. The previously proposed ERA schemes are assumed to satisfy the average constraint value, but in heterogeneous networks, the instantaneous interference threshold for macro users is not guaranteed [6]. In this paper, the scheme can solve the above problems very well. In the cognitive radio environment, SU and PU share the same spectrum. Since PU has higher channel access priority than SU, it is necessary to study more SU access systems when all primary users satisfy their own SINR. Each primary user tracks its target SINR. by adopting a traditional TPC algorithm. As long as the total reception power at the main receiver is lower than the given threshold, each transmit SU adopts TPC, otherwise, it reduces its transmission power according to the ratio of the given threshold to the total received power at the main receiver. The algorithm proposed in this paper can increase the number of SU in the access system under the condition that all PU’s SINR are guaranteed.
2 System Model
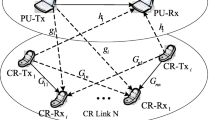
In this paper, the underlay spectrum access mode is considered, so it is unnecessary to consider the communication situation of the primary user, and the time of sensing and judging the primary user’s activity is reduced indirectly. This paper considers the underlay multi-user distributed cognitive radio scene, as shown in Fig. 1. Primary and secondary users coexist in the network, including \( M \) for secondary users, \( N \) for primary users. The secondary user is represented by the set \( {\text{A}} = \left\{ {1,2, \cdots ,M} \right\} \) and the primary user by the set \( {\text{B}} = \left\{ {1,2, \cdots ,N} \right\} \). Order \( \forall i,j \in {\text{A}} \), \( \forall k \in {\text{B}} \).
Assuming that the channel is flat fading, the average SINR of \( SU_{i} \) can be expressed as:
Which is
\( g_{i,i} \), Instantaneous link gain from \( SU_{i} \) to \( SBS_{i} \); \( g_{i,j} \), Instantaneous link gain from \( SU_{i} \) to \( PBS \); \( g_{p,i} \), Instantaneous link gain from \( SU_{i} \) to \( PBS \); \( g_{p,p} \), Instantaneous link gain from \( PU \) to \( PBS \); \( g_{i,p} \), Instantaneous link gain from \( PU \) to \( SBS_{i} \); \( p_{i} \), the \( i \)th secondary user transmit power; \( p_{i}^{\hbox{max} } \), Secondary user maximum transmit power; \( p^{total} \), Total interference power from \( SU_{i} \) to primary user; \( p^{th} \), Main user’s interference threshold; \( N_{S} \), Other secondary user interference; \( N_{P} \), Primary user interference; \( \delta^{2} \), Background noise; \( \gamma_{i}^{th} \), The SINR value for the \( i \)th secondary user when the QoS requirement is satisfied.
In order to ensure the normal communication of the primary user, the interference power cannot exceed the interference threshold of the primary user. Therefore, in order to meet the interference threshold, the total interference power of the secondary user must be met
In a cognitive system, in order to ensure a secondary user’s QoS requirements, each secondary user’s receiving SINR needs to meet a certain threshold value:
3 Mathematical Model
The average SINR can not reflect the instantaneous performance, so this paper mainly studies the instantaneous SINR of the secondary users. The receiver SINR has the characteristics of fast fading with channel fading. In order to reflect the instantaneous characteristics of SINR, we transform the average SINR model into the instantaneous characteristic model:
Among them, the \( E \) clothing is exponentially distributed with a mean value of 1, and the probability density equation is \( f_{E} \left( \chi \right) = e^{ - \chi } \).
By using the method of [7] transformation, the robust optimization problem is transformed into:
4 Robust Optimal Control Algorithm
For the robust optimization problem of formula (5), a power control algorithm is proposed in this section, which not only realizes the power allocation to secondary users, but also ensures that the primary users are not disturbed. Due to the interference threshold of the primary user and the minimum communication SINR requirement of the secondary user, some \( SU \) SINR can not meet the communication requirements in the actual process. Therefore, this section introduces admission control to realize the optimal utilization of network resources.
4.1 Robust Power Iterative Mathematical Model
For the robust optimization problem (5), considering the Qos constraint of \( SU \), we can obtain,
Which, \( \bar{N}_{i} = \sum\limits_{j = 1,j \ne i}^{N} {\bar{g}_{i,j} p_{j} } \).
Considering the threshold constraint \( 0 \le p_{i} \le p_{i,\hbox{max} } \) of \( SU_{i} \) transmission power, the following power iterations can be obtained:
which, \( \left[ \chi \right]^{ + } = \hbox{max} \left[ {\chi ,0} \right] \).
According to the power iteration formula in formula (7), when the maximum power threshold \( p_{i}^{\hbox{max} } \gg p_{i}^{opt} \), the \( p_{i}^{\hbox{max} } \) has little constraint on the transmitting power of \( SU_{i} \), whereas the maximum power threshold \( p_{i}^{\hbox{max} } \) has a very strong constraint on the transmission power of \( SU_{i} \). It can avoid the interference of \( SU_{i} \) transmit power to PU.
4.2 Complete Iterative Robust Power Control Algorithm
Formula (7) mainly uses \( p_{i}^{\hbox{max} } \) to constrain the power of the secondary user in the iteration process, and does not protect against the interference threshold of the primary user. Next, we give the protection strategy of the PU.
All SU interference with PU is \( \bar{I}_{p} \). Its size directly affects the communication quality of PU. With the decrease of \( \bar{I}_{p} \), the communication quality of PU becomes better and better. When the limit condition is \( \bar{I}_{p} = 0 \), the communication quality of PU is the best, which becomes a non-cognitive radio model. The reason for the decrease of \( \bar{I}_{p} \) is, on the one hand, the decrease in the transmitting power of SU, on the other hand, the decrease in the number of SU. In order to improve the communication quality of PU, the number of SU will decrease. To take into account both the quality of PU communication and the number of SU, we select the following interference thresholds:
\( I_{th} \) is the largest interference PU can tolerate. In order to limit the transmission power of SU and guarantee the Qos of PU, we give the following formula:
\( \hat{p}_{i} \) is the transmission power of \( SU_{i} \) after stabilization \( \hat{p}_{i} = \hbox{min} \left\{ {p_{i}^{opt} ,p_{i}^{\hbox{max} } } \right\} \). \( \hat{I}_{p} \) indicates the interference to PU caused by the final transmit power of \( SU_{i} \).
Since \( p_{i}^{\hbox{max} } \) can limit the transmission power of \( SU_{i} \), we propose a robust power control algorithm for maximum power regulation.
First set the minimum transmit power of the SU is \( p_{{}}^{\left( 1 \right)\hbox{min} } = \left\{ {p_{1}^{\left( 1 \right)\hbox{min} } ,p_{2}^{\left( 1 \right)\hbox{min} } , \cdots ,p_{N}^{\left( 1 \right)\hbox{min} } } \right\} \), then, adequate evaluation of interference threshold \( I_{th} \) by SU. Estimate the maximum transmit Power \( p_{{}}^{\left( 1 \right)\hbox{max} } = \left\{ {p_{1}^{\left( 1 \right)\hbox{max} } ,p_{2}^{\left( 1 \right)\hbox{max} } , \cdots ,p_{N}^{\left( 1 \right)\hbox{max} } } \right\} \) of all SU based on \( I_{th} \). Determination of power renewal step size \( \Delta p^{{\left( {\text{n}} \right)}} = \frac{{p_{{}}^{\left( 1 \right)\hbox{max} } - p_{{}}^{{\left( {\text{n}} \right)\hbox{min} }} }}{2} \) by dichotomy, which \( \Delta p^{\left( 1\right)} = \frac{{p_{{}}^{\left( 1 \right)\hbox{max} } - p_{{}}^{\left( 1\right)\hbox{min} } }}{2} \). Since all SU have the same transmit priority, all SU iterate simultaneously according to the minimum transmit power. The following flow steps of the minimum power regulation algorithm are given.
-
1.
Initialization: the number of adjustments is \( n = 1 \), The number of iterations per adjustment is \( t = 1 \), The initial minimum transmit power is \( p_{{}}^{\left( 1 \right)\hbox{min} } = \rho \).
-
2.
For \( i = 1,2, \cdots ,N \), Iterative formula based on power of SU
Repeat 2 steps to update power, order \( t = t + 1 \), power eventually converges to \( \hat{p}_{i}^{\left( n \right)} \).
-
3.
Using \( \hat{p}_{i}^{\left( n \right)} \), to calculate the interference \( \hat{I}_{p}^{\left( n \right)} \) of PU, which \( \hat{I}_{p}^{\left( n \right)} = \sum\limits_{i = 1}^{N} {\hat{p}_{i}^{\left( n \right)} \bar{g}_{p,i} } \).
-
4.
\( \hat{I}_{p}^{\left( n \right)} \) was compared with \( I_{th} \). If \( \hat{I}_{p}^{\left( n \right)} < I_{th} \), order \( n = n + 1 \), synchronously increase the transmit power of SU, \( p_{{}}^{{\left( {{\text{n}} + 1} \right)\hbox{min} }} = p_{{}}^{{\left( {\text{n}} \right)\hbox{min} }} + \Delta p^{{\left( {\text{n}} \right)}} \), start over from step 2. If \( I_{th} - \hat{I}_{p}^{\left( n \right)} < \omega \left( {\omega > 0} \right) \), then \( \hat{p}_{i} = \hat{p}_{i}^{\left( n \right)} \).
According to the above iterative algorithm, the communication quality of SU is guaranteed by limiting the maximum transmit power of PU. However, it is likely that some \( SU_{i} \) transmit power can not meet its own SINR requirements. If these cognitive users continue to communicate, it will only cause a waste of resources and cause more interference. Therefore, in order to optimize resource utilization, admission control is introduced. The implementation process is as follows.
4.3 Admission Control Algorithms
-
1.
SU calculation average SINR \( \hat{\gamma }_{i} \) based on the formula \( \hat{\gamma }_{i} = \frac{{\bar{g}_{i,i} \hat{p}_{i} }}{{\sum\limits_{j = 1,j \ne i}^{N} {\bar{g}_{i,j} \hat{p}_{j} + \bar{g}_{i,p} p_{p} + \delta^{2} } }} \), the \( \hat{\gamma }_{i} \) is compared with the optimal average SINR \( \bar{\gamma }_{i} \), which \( \bar{\gamma }_{i} = \frac{1}{{ - \ln \left( {1 - \varepsilon } \right)}}\overset{\lower0.5em\hbox{$\smash{\scriptscriptstyle\smile}$}}{\gamma }_{i} \). If \( \hat{\gamma }_{i} < \bar{\gamma }_{i} \), the \( SU_{i} \) enters the queue to be removed.
-
2.
In the removal queue, the \( SU_{i} \) corresponding to the smallest \( \hat{\gamma }_{i} \) is removed from the communication cognitive user by ordering the \( \hat{\gamma }_{i} \) according to the size.
-
3.
The remaining SU is updated according to the iterative algorithm. If all SU meets \( \bar{\gamma }_{i} > \hat{\gamma }_{i} \), admission control ends, otherwise, step 1 is returned.
Each secondary user is updated iteratively until the utility function in (4) is maximized. An automatic non-cooperative power control algorithm designed in this paper (APCGA, Automatic Power Control Game Algorithms) The process is as follows:
Step 1: Initialization power vector \( p_{i} (0) \) and \( p_{0} \), count \( \gamma_{i} (0) \).
Step 2: If \( \bar{\gamma }_{i} < \gamma_{i}^{th} \), \( \beta_{i} \) remain unchanged; otherwise automatically adjust \( \beta_{i} \) through \( \beta_{i + 1} = \beta_{i} \bar{\gamma }_{i} /\gamma_{i}^{th} \).
Step 3: Order \( m = m + 1 \), recalculate power \( p_{i}^{(m + 1)} \) using.
If \( p_{i}^{(m + 1)} \) meet (2), go on, otherwise the iteration stops.
Step 4: The \( i \)th secondary user, \( |U_{i}^{(m + 1)} - U_{i}^{(m)} | < \omega \) (precision \( \omega > 0 \)), the iteration stops; Otherwise, return to step 2.
5 Simulation Results and Analysis
In this section, the proposed power control algorithm and admission control algorithm are simulated and verified, and the network performance under these two algorithms is evaluated. The following are some of the simulation parameters in this chapter: \( R_{p} = 450\,{\text{m}} \), \( \delta^{2} = 10^{ - 10} \), \( p^{\hbox{max} } = 50\,{\text{mW}} \), \( p_{p} = 100\,{\text{mW}} \); which \( i = 1,2, \cdots ,N \), \( \overset{\lower0.5em\hbox{$\smash{\scriptscriptstyle\smile}$}}{\gamma }_{p} = 5\,{\text{dB}} \), \( \overset{\lower0.5em\hbox{$\smash{\scriptscriptstyle\smile}$}}{\gamma }_{i} = 15\,{\text{dB}} \); \( \rho = 5 \times 10^{ - 15} \,{\text{w}} \), \( \omega = 10^{ - 15} \). Assuming 30 SU users, we randomly selected 20 cognitive system (\( N = 20 \)) to verify the algorithm. Probability threshold \( \varepsilon = \varphi = 0.1 \).
5.1 Algorithm Convergence
Figure 2 shows the power iteration process of SU. The convergence of the complete iterative algorithm can be clearly seen in the diagram. At the same time, all SU have completed convergence within 15 steps, and most SU have completed convergence in 10 steps.
5.2 Admission Control Algorithm
According to the final transmission power of SU, the average SINR \( \hat{\gamma }_{i} \), of \( SU_{i} \) can be obtained as shown in Fig. 3(a). The average SINR of four SU is lower than the target SNR, so the four SU users can not meet their own communication SINR requirements. In addition, the figure shows that the average SINR of \( SU_{20} \) is the lowest. According to the execution process of admission control, the \( SU_{20} \) is removed from the network, and the power of the remaining 19 SU is recalculated using the complete iterative algorithm.
As shown in Fig. 3(b), after \( SU_{20} \) is eliminated, the average SINR of both \( SU_{4} \) and \( SU_{8} \) meets the communication requirements, and the SNR of the remaining cognitive users exceeds the target SNR requirement, and the performance is significantly improved than that before admission control. This is because the function of admission control is to eliminate the secondary users whose performance is poor and can not meet the requirements of communication, which indirectly reduces the interference of the remaining users, so the signal-to-noise ratio is increased. Figure 3(b) shows that the average SINR of \( SU_{13} \) still cannot meet the communication requirements and needs to be eliminated.
As shown in Fig. 3(c), the average SINR of the remaining 18 SU meets the requirements after \( SU_{13} \) is removed. The purpose of adopting admission control is to find the users farthest from the average SINR in the system and eliminate the unnecessary interference from other users, and to make it possible for the users with small average SINR deviation to realize the communication requirements. If the simulation results mentioned above, there are 4 SU users who can not meet the normal communication requirements. After adopting admission control, two SU users are eliminated, and the normal communication of the other 2 SU users is realized. The number of normal communication SU has changed from 16 to 18. At the same time, the system interference is reduced. This also fully reflects the effect of the admission control algorithm proposed in this chapter.
It can be seen from Fig. 4 that the average SINR of cognitive users is larger under admission control than without admission control in the case of fixed channel gain and fixed interrupt probability. Because a part of the secondary users who can not complete the communication normally is eliminated under the admission control algorithm, the total interference of the primary users is reduced, which indirectly improves the signal-to-noise ratio of the primary users. As can be seen from Figs. 3(c) and 4, the introduction of admission control can improve the overall performance of cognitive systems. However, with the increase of uncertain parameter \( \varepsilon \), the average SINR of secondary users decreases. This is because the normal communication of the secondary users is affected with the increase of the bad channel environment, resulting in the decrease of the average SINR of the secondary users.
5.3 Complete Iterative Algorithm
Figure 5 shows the curve of cognitive user interrupt probability when the target SNR is different. The probability of outage is defined as the ratio of the number of users to the total number of users. It can be seen from Fig. 5 that the outage probability increases with the increase of SINR.
In this paper, the power control algorithm (the complete iterative algorithm) is used to determine how to eliminate the cognitive users who can not communicate normally when each power iteration converges to a stable value, which will result in a high overall interruption probability. This is because cognitive users who can not communicate normally have been in the system for a long time as interference sources. This method is used to filter out the secondary users’ nonconformance caused by transient, although the outage probability is increased, the total number of secondary users who can communicate normally is also increased, and the total throughput of cognitive system is improved. The increase in the number of secondary users that can communicate normally, as shown in Fig. 6, also increases system energy consumption. If the interference temperature is detected at all times in the iterative process and the algorithm (discontinuous iteration algorithm) is used to verify the Qos requirement of the cognitive user, it is found that the dissatisfied cognitive user can be eliminated in order to reduce the outage probability. However, this method will amplify the transient state, cause excessive elimination of secondary users, reduce the number of secondary users who can communicate normally, and reduce the throughput of cognitive systems.
6 Conclusion
In this chapter, the objective of the instantaneous SINR, is to minimize the energy consumption, and the robust power allocation of SU is realized by the interference management of PU. First, assuming the exponential distribution of the user’s instantaneous SINR service, the probabilistic constraint equations of SU and PU are given respectively. The probabilistic constraints are solved by the distribution function of SINR, and the optimal SINR and PU interference constraint expressions of SU are obtained. Based on the interference constraints of PU, a robust power control algorithm based on complete iteration is proposed. The algorithm can effectively ensure the fast convergence of SU power in the range of PU interference constraints. Therefore, this paper adopts admission control to eliminate these SU and make rational use of network resources. The simulation results show the effectiveness of the algorithm and the practicability of the overall solution.
References
Han, S., Liang, Y.-C., Soong, B.-H.: Robust joint resource allocation for OFDMA-CDMA spectrum refarming system. IEEE Trans. Commun. 64(3), 1291–1302 (2016)
Bao, Y., Chen, H.: Design of robust broadband beamformers using worst-case performance optimization: a semidefinite programming approach. IEEE/ACM Trans. AudioSpeech Lang. Process. 25(4), 895–907 (2017)
Phunchongharm, P., Hossain, E.: Distributed robust scheduling and power control for cognitive spatial-reuse TDMA networks. IEEE J. Sel. Areas Commun. 30(10), 1934–1946 (2012)
Du, H., Ratnarajah, T.: Robust utility maximization and admission control for a MIMO cognitive radio network. IEEE Trans. Veh. Technol. 62(4), 1707–1718 (2013)
Mokari, N., Saeedi, H., Azmi, P.: Quantized ergodic radio resource allocation in cognitive femto networks with controlled collision and power outage probabilities. IEEE J. Sel. Areas Commun. 32(11), 2090–2104 (2014)
Rasti, M., Hasan, M., Le, L.B., Hossain, E.: Distributed uplink power control for multi-cell cognitive radio networks. IEEE Trans. Commun. 63(3), 628–642 (2015)
Xu, Y.J., Zhao, X.H.: Robust probabilistic distributed power control algorithm for underlay cognitive radio networks under channel uncertainties. Wirel. Pers. Commun. 78(2), 1297–1312 (2014)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 ICST Institute for Computer Sciences, Social Informatics and Telecommunications Engineering
About this paper
Cite this paper
Yang, G., Tan, X., Wang, X. (2019). Robust Power Control Algorithm Based on Probabilistic Constraints in Cognitive Radio Networks. In: Jin, J., Li, P., Fan, L. (eds) Green Energy and Networking. GreeNets 2019. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 282. Springer, Cham. https://doi.org/10.1007/978-3-030-21730-3_3
Download citation
DOI: https://doi.org/10.1007/978-3-030-21730-3_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-21729-7
Online ISBN: 978-3-030-21730-3
eBook Packages: Computer ScienceComputer Science (R0)