Abstract
Design for values addresses the challenge of making technology accessible, effective, and appropriate for diverse groups of users. Older adult users represent a highly heterogenous, diaphanous, and evolving group of users. The ETHOS project used an extended iterative design process informed by theories of late life. One goal of elder-sensitive design for values is integrated systems that truly support independent living. These designs capitalize on older adults’ capabilities and minimize their limitations, are sensitive and responsive to changing functional/cognitive status, and are respectful of the privacy and dignity of elders and their caregivers.
Access provided by CONRICYT-eBooks. Download reference work entry PDF
Similar content being viewed by others
Keywords
Introduction
Technologies in the home embed the choices of the designer. Even when the individual living with the technology has a choice, the constraints of those choices are determined by the designer. For example, our most common sensor platform is the cell phone. Modern smartphones have accelerometers, cameras, video cameras, GPS, more detailed location using wireless, and a wide array of client connections to centralized servers (e.g., Facebook, Google, Snapchat). How those are accessed, activated, or on by default is not decided by the person holding the phone, but by the designer. Such sensors are embedded not only in our lives but increasingly in our homes and even our bodies. Unlike phones, which can be updated (depending on the model and thus the designers choice), devices embedded in homes, cars, and humans have a very different update cycle and costs. Thus evaluating the values and choices embedded becomes correspondingly more important.
We begin our article by introducing the concept of value-sensitive design (also known as design for values). We point to the specific design for privacy model from Ann Cauvoukian. We consider these models through the lens of psychosocial motivational theories of late life. We describe the implementation of a design for values approach for home-based technologies as used in the Ethical Technology in the Homes of Seniors (ETHOS) Laboratory. Specifically we discuss both those choices that were made implicitly in design and those choices where we empowered the elder (and potential subject of sensor surveillance) to choose for him or herself.
Design for Values
Design for values (DfV also known as Values In Design or VID and as value-sensitive design or VSD) has focused on a wide range of problems, including accessibility (Shneiderman and Hochheiser 2001), privacy (Golberg 2001), security (Gollmann 2010), inclusion of all stakeholders’ viewpoints (Friedman et al. 2002), and digital rights management (Camp 2003; Knobel and Bowker 2011). DfV methods have been used to encourage business ethics by information system design (Stahl 2008) and enable ethical game design as well analysis of the values embedded in traditionally designed games (Belman et al. 2011).
DfV is an iterative design method that begins by identifying the parties that will be directly impinged by a design should a system be successful. The simple act of envisioning the use of the technology and its context of use can make designers more aware of potential impacts. DfV draws from Computer-Supported Cooperative Work, HCI, and participatory design.
Design for Privacy
The DfV approach is related to the Privacy by Design (PbD) framework. The two approaches were developed simultaneously, one in academy with a more generalized approach to various values and one with a tight focus on privacy by the Ontario’s Information and Privacy Commissioner, Dr. Ann Cavoukian (Cavoukian 2009).
In the PbD framework the similarity is that there is an initial statement about data from the concept level. Yet rather than adding additional iteration of design, the goal is to evaluate privacy impact at each stage of the design. Cavoukian identifies each stage and the questions to be asked during each stage: development, design, production, and marketing.
Cavoukian provides a set of examples of the end result of the application of the DfV principles. A common theme is the recognition that data compilation has costs but often no value. Data that are compiled create risks as well as the costs of compilation and disclosure. For any data that are compiled, the creation of a plan in the situation that the data are leaked, contaminated, or lost is an important component of PbD. The ability to understand the costs of data decisions as privacy decisions is the core of PbD.
Privacy cannot be isolated from other system design concerns. For example, there are serious privacy concerns if tracking is done on a server. However, consider if there is no server but only a local device. In that case, power is a significant concern and lack of service may be undetectable as there is not a server check-in. In terms of not sharing information, lack of shared data can prevent long-term learning.
Design for Values: The Senior Edition
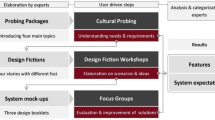
Designing for smart homes for independent living requires an iterative participatory design process beginning with familiarization. Older adults have little familiarity with functionality of home-based technologies. Potential end users need to first develop a mental model of these technologies, speculate upon their potential usefulness, and then consider what needs these technologies might conceivably meet for themselves or their peers. This process is best accomplished over a series of design meetings to accommodate novice users and the typically slower cognitive processes of later life. Once there is some consistency among participants of potential uses for in-home technologies, the actual design, test, evaluation, and redesign process may begin. For very old potential end user groups, there may need to be several iterations of the process.
Common user-centered design employs processes such as interviews, focus groups, contextual observations, shadowing, participatory design sessions, and in situ evaluations. The processes, and the analyses of the resulting data, are often elder-blind, completely uninformed by biopsychosocial theories of aging. The United States, vis-a-vis western Europe, is a relatively young country. The psychology of old age, particularly late old age, is not present in the collective consciousness of designers in the United States. Concepts including socio-emotional selectivity theory, passive mastery, tolerance, and transcendence, often reflected in western European paradigms, are not adequately represented in most US user studies. The blended nature of decision making, i.e., a carefully negotiated ever changing dance between elders and their caregivers, is often overlooked as well.
Psychosocial Motivation in Late Old Age . We began our user-centered design with an initial privacy values statement from the literature and with an awareness that this statement was unlikely to reflect the actual privacy perceptions of older adults. As we collected and analyzed data through multiple steps described below, we began to build on psychosocial motivational theories and a concept that could serve as a foundation to an elder-sensitive design for values framework and technological prototypes that reflected the principles of the framework. These theories informed our analyses of user study data and resulted in a framework with four essential constructs: control over data flow, type of data, role of caregiver recipient, and data transparency.
Socio-emotional Selectivity Theory. First, the constructs of data flow and role of caregiver recipient were based on socio-emotional selectivity theory. Carstensen and others (Carstensen et al. 2003) posit that older adults place primary importance on important relationships. While the concept of privacy has been shown to hold some interest (Beach et al 2008; Wild et al. 2008; Kwasny et al. 2008), it is the maintenance of key relationships that is the primary motivation for behaviors of cognitively intact people in late life – those we identified as likely early adopters for this study. “If it helps my son to feel better about taking care of me, I don’t care what he wants to install,” stated an octogenarian. Controlling data flow to selected caregiving recipients helps older adults maintain the primacy of relationships over technology. It can also empower caregivers in blended decision making and data management.
Dignity and Independence. The construct type of data is based on theory concerning dignity and independence. Along with a primary focus on important relationships, people in most western civilizations covet a sense of independence, self-worth, and dignity as they age, even into very late life. Sixsmith (1986) suggests that these perceptions are composed of more than one component (p. 341):
-
1.
Being able to look after one’s self; not being dependent on others for domestic, physical, or personal care – physical independence.
-
2.
Capacity for self-direction, free to choose what to do, free from interference, and free from being told what to do – autonomy.
-
3.
Not being under an obligation to anyone and not having to rely on charity.
-
4.
Independence is not threatened if support is based on reciprocity or interdependence.
Independence, self-worth, and dignity are fragile possessions as the old navigate the difficult terrain of very late life. A septuagenarian noted, “How much control do you want to give up? It’s going to be hard enough when you’re older to keep what little sense of self-dignity (you have).” Faced with the threats of institutionalization, the ravages of disease, and well-meaning but overbearing caregivers, older adults may choose in-home technologies as a way to maintain autonomy and dignity or, as a last resort, a way to avoid institutionalization. This choice should not lead to becoming the passive subject of constant monitoring. Thus, in addition to providing control over data flow and caregiving recipients of data as mentioned above, ethical design for elders provides appropriate levels of control over what type and granularity of data is collected and transmitted by technologies in the home. It is imperative that the data control mechanism be designed for and adjustable to the changing physical and cognitive needs of the aging adult.
Passive Mastery. The contract transparency is based on the concept of passive mastery. Contemporary discourse about privacy, and even technology, has the tone of “us against the machine.” Older adults, particularly those in late life, are happy to let others fight this fight. They win through accepting what is, with whatever grace may be mustered (Missinne 2013). There is no place in the very tenets of user studies, at least in the United States, that inculcates the transcendent nature of the psychology and ethos of a good old age. What appears to be naivety, or even ignorance, may well be the tolerant, transcendent nature of someone who has aged long and well.
Although older adults in very late life may be relatively unconcerned or simply transcendent about privacy, they may also lack awareness of the amount of data that is collected through interaction with numerous technologies. Thus, an ethical approach in design for old age is data transparency . It is not enough for elders to know monitoring technologies are installed in the home. Because of likely limited awareness of data aggregation in addition to deliberate tolerance, we suggest that data must be visible and comprehensible for an older adult user for true transparency.
Case Study
Ethical Technology in the Homes of Seniors (ETHOS)
To facilitate an elder-sensitive design for values/privacy approach to smart home technologies, we created a highly interdisciplinary research team: a technologist, a privacy and security specialist, an informatics ethicist, a psychologist with expertise in human-centered design, and a social gerontologist. Using a design for values/design for privacy approach informed by psychosocial theories of late old age, we used an extended iterative user-centered design model. At each step we provided feedback to a focused, yet group of potential end users – likely early adopters and their caregivers.
The user-centered design approach followed by the ETHOS research team was as follows:
-
1.
Initial privacy values statement
-
2.
Delphi method with aging experts to develop focus group protocol
-
3.
Alpha focus groups
-
4.
Data analysis and revision of initial values statement
-
5.
Preliminary prototype design
-
6.
Beta focus groups
-
7.
Prototype redesign
-
8.
Survey
-
9.
Prototype and values statement redesign
-
10.
User studies
-
11.
Final prototype design
-
12.
In situ study
-
13.
Values statement and prototype design review
-
14.
Survey
-
15.
Final values statement and prototype design review
Results from each segment of the study illuminate and clarify the multiple perspectives, interests, and values critical to a design for values and privacy (Caine et al. 2011; Lorenzen-Huber et al. 2011; Shankar et al. 2012). Our initial values statement evolved from an individual perception of privacy to a privacy framework of a densely contextualized, relationship-dependent perception of the multiple meanings of privacy (Lorenzen-Huber et al. 2011). This is design for values, the senior version: multiple stakeholders are affected by smart home technologies, and the key players and contexts change rapidly in very late life.
After the initial values statement, we engaged in a more targeted literature review to identify the specific threats and activities of daily living which would be the focus of the designs as well as theories of late life as a lens through which to better understand older adults’ perceptions of threats and values. The early alpha and beta focus groups, averaging about 12 participants, and the survey (n = 48) took place over the course of about 6 months and included overlapping groups of participants. During this time, the participants had the opportunity to develop mental models of smart home technologies and were able to identify threats and values statements which enabled quick prototyping.
We initially had four prototypes, each of which had its carefully evaluated data footprint Duncan et al (2009). The ability to pause data compilation was made on a per-device basis. During these early studies, some projects were rejected. The Mirror Motive (Fig. 1) was designed to provide pop-up reminders on a large touch screen that doubled as a mirror, an effort to blend the technology into everyday objects. The Mirror Motive (was rejected by focus group participants for these very design efforts: they did not like the mirror and touch screen, and they were concerned that reminders (such as medication reminders) might pop-up in the living room when there were guests).
Results from these first studies showed that participants were interested in knowing what data was collected, who was accessing it, and being able to control the data flow. The types of control desired were (a) the ability to turn off monitoring, (b) an automatic restart after devices were turned off, and (c) the ability to hide device status from family caregivers. In terms of usability, participants wanted a simple interface for control over personal data. Conscious of the cognitive demand of new technologies, participants suggested several features that would improve usability.
Based on the findings from these early studies, we designed a single device to control the suite of technologies and the resulting data flow. The final prototype design included a single point of control that we named the DigiSwitch (Figs. 2 and 3), reminiscent of a telephone switchboard. The DigiSwitch is a touch screen computer integrated into a digital picture frame. It allows users to turn individual monitoring technologies on and off and allows them to see what data are being collected and transmitted. It thus provides an easy-to-use intuitive interface that allows elders to control their own digital footprints. It provides the ability to mute or pause data (Fig. 4) from leaving the house and a reminder that devices would automatically turn back on after 30 min (Fig. 5). The “Friend’s View” can be selected from the main screen (Fig. 6) providing the ability to see the data that did left the house (Fig. 7). We choose the form of a digital touch screen picture frame for the DigiSwitch to eliminate a panoply of cords and peripherals and to blend this technology into the background of everyday objects in a typical older adult’s home.
The DigiSwitch provides data transparency through “Friend’s View,” a compilation of data received by a chosen friend/caregiver. Older adults were most interested in the “Friend’s View” of the video feed. In our in situ study, we included up to two video cameras, placed in locations chosen by the older adult participants, to explore perceptions of the collection and transmission of highly granular data. Cameras were typically placed in front hallways or living rooms, and the older adults were fascinated with the views of their lives as transmitted to a friend/caregiver. Their interest in actual data flow corroborated the importance of design for transparency.
The DigiSwitch provides control by enabling on/off of all or selected technologies with a simple tap on the touch screen. In response to comments from the focus groups and surveys, we incorporated an innovative feature unique to the DigiSwitch, “Me Time.” Me Time was designed for device state privacy, the ability to control information about whether the device was on or off. Thus the DigiSwitch enabled older participants to start or stop devices that transmitted data, but also to control information provided to their caregiver about if and when they choose to turn off the devices.
An elder-sensitive approach to design for values and design for privacy must take into account the constant, sometimes rapid, changes in elders’ functional ability, the unique complexities of caregiver networks, the elders’ often rudimentary conceptualizations of data and privacy, and the preference for passive rather than active mastery. We propose that the oldest olds’ perceptions of the need for privacy are highly contextual, individualized, and dependent upon the recipient of the data, the sensitivity of the activity being monitored, and the granularity of the data. Generic values for design is an important, but inadequate, starting point for design for elders and those who care for them.
References
Beach S, Schulz R, De Bruine W, Downs J, Musa D, Matthews J (2008) Privacy attitudes and quality of life technology in disabled and non-disabled baby boomers and older adults. Gerontologist 48(2):46
Belman J, Flanagan M, Nissenbaum H, Diamond J (2011). Grow-a-game: a tool for values conscious design and analysis of digital games. Paper presented at the proceedings of DiGRA 2011 conference, Think Design Play, Hilversum, The Netherlands
Caine K, Zimmerman C, Schall-Zimmerman Z, Hazlewood W, Camp LJ, Connelly K, Shankar K (2011) DigiSwitch: a device to allow older adults to monitor and direct the collection and transmission of health information collected at home. J Med Syst 35(5):1181–1195
Camp LJ (2003) First principles of copyright for DRM design. IEEE Pervasive Comput 7(3):59–65
Carstensen LL, Fung HH, Charles ST (2003) Socioemotional selectivity theory and the regulation of emotion in the second half of life. Motivation Emotion 27(2):103–123
Cavoukian A (2009) Privacy by design: take the challenge. http://www.privacybydesign.ca/. Retrieved 17 Feb 2014
Duncan J, Camp LJ, Hazlewood W (2009) The portal monitor: a privacy-enhanced event-driven system for elder care. Paper presented at the Persuasive 2009, Claremont
Friedman B, Kahn P, Borning A (2002) Value sensitive design: theory and methods University of Washington technical report, University of Washington, pp 02–12
Golberg H (2001) Shostack. Privacy ethics and trust. Boston U Law Rev 81(2):407–422
Gollmann D (2010) Computer security. In: Wiley Interdisciplinary Reviews: Computational Statistics. 2.5, pp 544–554, September/October 2010
Knobel C, Bowker G (2011) Values in design. Commun ACM 54(7):26–28
Kwasny M, Caine K, Rogers WA, Fisk AD (2008) Privacy and technology: folk definitions and perspectives. Paper presented at the CHI ‘08 extended abstracts on human factors in computing systems, Florence
Lorenzen-Huber L, Boutain M, Camp LJ, Shankar K, Connelly KH (2011) Privacy, technology, and aging: a proposed framework. Ageing Int 36(2):232–252
Missinne L (2013) In this life: spiritual growth and aging. Liguori Publications, Liguori
Shankar K, Jean Camp LJ, Connelly K, Huber LL (2012) Aging, privacy, and home-based computing: development of a framework for design. IEEE Pervasive Comput 11(4):46–54
Shneiderman B, Hochheiser H (2001) Universal usability as a stimulus to advanced interface design. Behav Informa Technol 20(5):367–376
Sixsmith A (1986) Independence and home in later life. In C. Phillipson, M. Bernard, & P. Strang (Eds.), Dependency and interdependency in old age— Theoretical perspectives and policy alternatives (pp. 338–347). London, UK: Croom Helm in Association with The British Society of Gerontology
Stahl BC (2008) Ethical issues of information and business: a critical perspective. In: Himma KE, Tavani HT (eds) The handbook of information and computer ethics. Wiley, Hoboken, pp 311–335
Wild K, Boise L, Lundell J, Foucek A (2008) Unobtrusive in-home monitoring of cognitive and physical health: reactions and perceptions of older adults. J Appl Gerontol 27(2):181
Acknowledgments
This material is based upon work supported by the National Science Foundation under award number 0705676. Any opinions, findings, and conclusions or recommendations expressed in this presentation are those of the authors and do not necessarily reflect the views of the National Science Foundation.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing Switzerland
About this entry
Cite this entry
Huber, L., Camp, L.J. (2017). User-Driven Design in Smart Homes: Ethical Aspects. In: van Hoof, J., Demiris, G., Wouters, E. (eds) Handbook of Smart Homes, Health Care and Well-Being. Springer, Cham. https://doi.org/10.1007/978-3-319-01583-5_7
Download citation
DOI: https://doi.org/10.1007/978-3-319-01583-5_7
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-01582-8
Online ISBN: 978-3-319-01583-5
eBook Packages: EngineeringReference Module Computer Science and Engineering