Abstract
Identifying intruders using data mining approach in recent trend provides better detection rate when compared with other classical systems. In this paper we introduced Oppositional based Laplacian grey wolf optimization algorithm for clustering the class of attacks based on the similarity and active learning of SVM classification using this optimization algorithm. The results of the proposed algorithm have been evaluated with standard metrics and compared with the recent algorithms to prove its significance. The results of the proposed algorithm show its significance when compared with the existing methodologies.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
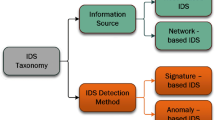
The vital role of intrusion detection system is to defend the computer system or a network system from the hackers or they are called as intruders. IDS use well classified classifiers to distinguish between normal users and potential hackers. IDS also use clustering techniques for grouping the users based on their similarities. Under two basic considerations the IDS can work efficiently identify the intruders among the legible users: (1) auditing of log data from the computer systems are possible for IDS and (2) there will be distinct difference among the legible users and intruders.
IDS have been addressed by many researchers with different models. However, the implemented IDS cannot work efficiently without periodical updates and in case if it fails to do so then the IDS cannot compete with new type of attacks. IDS can be updated by both manually and using networks. However, updating IDS is a time and energy consuming process. IDS can analyse the network automatically via the data log files of the system. There are different phases in IDS and they are:
-
1.
Analysing the packets over the network.
-
2.
Feature extraction from the captures packets to list out the details of the connection or regarding the host.
-
3.
Developing a model to analyse the features which can further be extended to distinguish the normal and abnormal behaviour among the users.
-
4.
With the use of learnt model to develop the intrusion detection mechanism.
Chung and Wahid (2012) proposed a novel fusion intrusion detection system by adopting the usage of intelligent dynamic swarm. It is merged with rough set for carrying the process of feature selection. It comprises of simplified swarm optimization for carrying the intrusion data classification strategy as discussed in Jaganathan and Palaniswami (2014). IDS-RS is proposed to handle the most appropriate features, which can easily denote the network traffic pattern. The main theme of the proposed algorithm is to improvise the performance of SSO classifier, the integration of novel weighted local search (NWLS) approach is merged with SSO. The objective of novel local search strategy is to look for optimized and best results from the closest of the current solution formed by SSO. The KDDC up 99 dataset is adopted for checking the performance of the proposed hybrid system and the evaluation of results are compared with particle swarm optimization (PSO) and two other most popular benchmark classifiers. The testing results illustrates that the proposed hybrid system can attain high level of classification accuracy than others with 93.3% and it can be one of the competitive classifier for the intrusion detection system.
Horng et al. (2011) discussed the advancement of using an SVM-based intrusion detection system, and it also discloses the information about the process of hierarchical clustering algorithm. The integration of simple feature selection process added with SVM technique provides high level of security and act as a perfect system for protecting the data. The hierarchical clustering algorithm with the SVM provide accuracy with fewer, abstracted, and higher-qualified training instances that are obtained from the KDD Cup 1999 training set. The entire process completes by consuming less training time, but parallel it enhances the performance of outcome SVM. The unassuming feature selection technique was functional to eradicate insignificant features from the training set. The attained SVM model can categorize the data of network traffic more accurately. The KDD Cup 1999 dataset was consumed to check the stability of the proposed system. The comparison process takes place with other traditional intrusion detection systems which uses same dataset, this system displayed improved performance by quickly identifying DoS and Probe attacks, and the beset performance in overall accuracy.
Eesa et al. (2015) presented an effective feature-selection scheme which is completely based on cuttlefish optimization algorithm. This effective strategy mainly focused on providing accurate solution for intrusion detection systems (IDSs). It mainly focuses on IDSs with a huge amount of data; one of the critical tasks of IDSs is to retain the finest quality of features that denote the entire data. It also has the ability to eradicate the redundant and inappropriate features. The proposed model adopts the cuttlefish algorithm (CFA) which acts as a search strategy to discover the optimal subset of features. The proposed model fetch help of decision tree (DT) classifier as a verdict on the nominated features that evolves by the CFA. The KDD Cup 99 dataset is used to estimate the proposed model. The outcome displays the feature subset attained by importing CFA. It generates higher detection rate and level of accuracy rate is high with a lower false alarm rate, when compared with the obtained results using all features.
Thaseen and Kumar (2017) proposed an intrusion detection model using Chi-square feature selection. The multi class support vector machine (SVM) uses a parameter for carrying the tuning method by integrating the optimization. It fetches the parameter known as radial basis function kernel such as gamma represented by ‘!’ and over fitting constant ‘C’. These parameters are considered has two significant parameters which helps SVM to attain more accuracy and also helps to construct a multi class SVM which has not been assumed for IDS. It also provides decreases the time consumed by training and testing process. The increase of the individual classification accuracy while there is an interference of network attacks. The tentative outcomes on NSL-KDD dataset which is an improved variety of KDDC up 1999 dataset displays that our proposed method outcomes indicate better detection rate and with minimized false alarm rate. An investigation on the computational time essential for training and testing is also supported out for procedure in time critical applications.
Lin et al. (2012) explained an intelligent algorithm with feature selection process and the technique makes a set of decision rules which can be easily applied, in order to check the anomaly intrusion detection. The significant theme is to make use of support vector machine (SVM), decision tree (DT), and simulated annealing (SA), to detect abnormal circumstances. In the proposed algorithm, the role of adopting SVM and SA is to identify the best nominated features to uplift the exactness of anomaly intrusion detection. The evaluation of the information from using KDD’99 dataset was carried by getting the data derived from DT and SA and it can acquire decision rules for new attacks and can improve accuracy of classification. By considering the requirements for the DT and SVM the finest parameter settings are automatically accustomed by SA. The proposed algorithm outclasses other prevailing methods. The simulation results establish that the proposed algorithm is effective in detecting anomaly intrusion detection. Various optimization problems that are addressed using evolutionary concepts can be found in Smys and Kumar (2016); Anguraj and Smys (2019), Raghav et al. (2017a, b), Mubarakali et al. (2019), Raghav and Ponnurangam (2017), Abiramy et al. (2018), Thirugnanasambandam et al.(2017), Raghav et al. (2019), Thirugnanasambandam et al. (2019).
Oppositional based learning (OBL) is integrated with basic GWO algorithm. The reason behind choosing the opposition based learning (OBL) is that it does not depend on the specific algorithm used to speed up the convergence rate of different optimization techniques. For finding a better candidate solution, the simultaneous consideration of an estimated and its corresponding opposite estimated which is closer to the global optimum than a random candidate solution. In a very short period, OBL, a new concept in computational intelligence, has been utilized in different soft computing areas.
The following section of the paper is organized as follows: Sect. 2 deals with the problem definition of IDS, Sect. 3 discusses on SVM classification model. Section four explains the proposed model along with the drawbacks in the existing GWO. Section 5 deals with the experimental evaluation and finally Sect. 6 concludes the paper.
2 Problem definition
In this section a brief view on data mining approach in intrusion detection mechanism using machine learning models are given along with the background knowledge on network security. This section will also describe how the log data is mapped with SVM and optimization model for classification and clustering respectively.
2.1 Network security
Communication model through networks plays a vital role in carrying sensational information for a wide range of purposes, hackers are attracted towards the network to snip away the information or to disrupt the system. In today’s trending grows with online trading and the domination of e-market and e-commerce, the necessity of network security is high in securing the communication model. In network stream, information security comes with three major concerns Froehlich and Kent (1998):
-
Confidentiality: Securing the data from unauthorized persons either through copying or through reading it.
-
Integrity: Protecting the information from unauthorized persons so that they cannot modify the it.
-
Availability: Safeguarding the information from unauthorized persons in such a way it should not be wiped out or erased from the memory location.
The above-mentioned points state that the information has to be protected in these ways. Following are the methods to be followed to protect the confidential data from the hackers Froehlich and Kent (1998).
-
Authentication: Acknowledging the authorized persons using identical record and providing the facility to claim the same. Through passwords, pins, patterns, etc. authentication can be done.
-
Authorization: The level of access that the authorized persons can be taken to. For example, a customer and a merchant in e-commerce site.
-
Non-Repudiation: Providing protection to the information who tries to access it by trying to violate the above-mentioned points.
2.2 Network intrusion detection
Intrusion detection is the process of identifying the course of actions that are attempted to compromise any of the three measures of data (confidentiality, integrity and availability) as described by Axelsson (1998), Debar et al. (2000). Detection of these attacks can be done by examining the log records of the system and the network. The system records are called as host-based data and the network records can be referred as network-based data as discussed in Freeman et al. (2002), Marchette (1999) (i.e. tcpdump). From different research aspects IDS has been addressed which includes statistical, predictive, neural networks as discussed by Lunt (1993), Ryan et al. (1998), Teng et al. (1990). expert systems as described by Denning (1987), keystrokes as formulated in Monrose and Rubin (1997), model-based IDS Garvey and Lunt (1991), Kumar (1995), Network Security Monitor Mukherjee et al. (1994), autonomous as described in Spafford and Zamboni (2000), fuzzy as described by Klawonn and Höppner (2003) and data mining as discussed in Han et al. (2011), Hand et al. (2001), Kantardzic (2003).
In traditional approaches, the identification of intruder in a network is a real-time process. A system with equipped IDS is placed in a system and when a new node comes to access the piece of information the node is subject to come through the IDS where the authentication and authorization privilege will be approved as discussed in Besharati et al. (2019). The implementation of IDS in a network or system requires two major concerns. (1) Cost of deployment and (2) updating the IDS. IDS is a standalone system where the module is built completely along with predefined data regarding identification mechanism and process of identifying the intruder as discussed in Bi et al. (2016). When a new instruction needs to be added to IDS, in traditional approaches the whole system is expected to reboot. In recent approaches, the system must undergo training process for updating the new information. In machine learning approach, the IDS system posses the capability to update the information without any pre-requisite training process. This system is explained below with a sample model.
2.3 Example of IDS using machine learning approach
Here is a sample procedure to describe the course of action taken to identify the intruder using machine learning model. Let us consider, a dataset \(\chi\) consists of the log data after pre-processing is done. Let \(\psi\) be the training step of the machine learning model. As it is a show Fig. 1. Each data point \(d \in \chi\) is given to searching function \(\varphi\) to find the data points selected to undergo training process in \(\psi\). And \(\delta\) is the classifying function decides which class of user they belongs to.
In this approach when a new data point is received it undergo training in appropriate manner using the search function \(\varphi\) to obtain the proper training procedure from \(\psi\). This approach does not require any rebooting mechanism or rebuilt or retraining of whole dataset. Two different approaches are to be expected to fulfil the process namely clustering and classification. Classification is the process of labelling the data to which class it belongs to. Clustering is the process of identifying the similarity among the data points. These two approaches are the basic blocks of machine learning based IDS. In our approach we used support vector machine for classification and oppositional based Laplacian grey wolf optimization algorithm for clustering.
3 SVM classification mechanism
Support vector machine (SVM) is a classic algorithm used for classification mechanism in machine learning. In this section, a brief introduction on the working procedure of SVM in data classification is given. This SVM is explained by considering the active log data of intrusion detection as it input for classification.
Let us consider \(d \in \chi\) is the data which belongs to either Class A (Intruder) or Class B (Legible user). Every data in \(\chi\) can be labelled with \(y_{i} \in \left[ { - 1,\; 1} \right]\) such that
Entire training set can be stated as
Using the given dataset a hyperplane \({\mathcal{H}}\) needs to be derived which separates both the classes. Initially two hyperplanes \({\mathcal{H}}_{1}\) and \({\mathcal{H}}_{2}\) is plotted based on the closest points among − 1 and + 1 from \({\mathcal{H}}\) respectively.
where \(w\) stands for the normal and \(b\) denotes distance from \({\mathcal{H}}\) to origin. Figure 2 shows the initial process of constructing hyperplane \({\mathcal{H}}\).
SVM is also used as multi-level classifier whereas in our example we used binary classifier since in our approach we used binary SVM. The classification process requires clustering mechanism to label the data though which group it should gets trained. At this phase optimization comes into picture where a better clustering model is promising through the literature.
4 Oppositional based Laplacian grey wolf optimization algorithm
In this phase, the proposed oppositional based Laplacian grey wolf optimization Algorithm is explained in detail which is used for clustering purpose in IDS. Initially the standard grey wolf algorithm working process is explained along with its drawbacks. Then the proposed algorithm is given in the form of pseudo code.
4.1 Grey wolf optimization algorithm
Grey wolf optimizer is an optimization algorithm proposed by Mirjalili et al. (2014) inspired from the socio behaviour of wolves and their hunting proceeding. Based on the hunting strategy of grey wolves they are categorised into three forms namely:
-
\(\alpha\)—Deciding authority to instruct other wolves where to sleep, hunt, etc.
-
\(\beta\)—Advisor for \(\alpha\) wolves in decision making procedure and takes the position of \(\alpha\) wolves in their absence
-
\(\delta\)—Subordinate wolves follow the instructions of \(\alpha\) and \(\beta\) wolves.
There are two phases in GWO namely encircling and hunting phase. Encircling phase identifies the location of the prey and instructs the other wolves to round it. Hence the other wolves are subject to update its location based on the instruction. It is mathematically represented as
where \(t\) denotes the iteration, \(\vec{A}\;and\;\vec{C}\) represents the coefficient vectors, \(\xi\) position of the wolf and \(\xi_{c}\) is the position of prey.
The vector \(\vec{A}\;{\text{and}}\;\vec{C}\) are computed as follows:
where varies from 2 to 0, and \(\vec{r}\) is a random vector in [0, 1].
In hunting phase, the \(\alpha ,\;\beta\) and \(\delta\) wolves (solutions) are considered as the first, second and third solution based on the ranking of the fitness values. The hunting procedure can be represented mathematically as follows.
where, \(\overrightarrow {\varGamma }_{\alpha }\), \(\overrightarrow {\varGamma }_{\beta } , \overrightarrow {\;\varGamma }_{\delta }\) refers the adjusted distance vectors of \(\alpha ,\beta\) and \(\delta\) wolves, \(\vec{C}_{1} , \vec{C}_{2} , \vec{C}_{3}\) are the coefficient vectors.
where, \(\vec{\xi }_{1} , \;\vec{\xi }_{2}\) and \(\vec{\xi }_{3}\) are the updated positions of \(\alpha ,\;\beta\) and \(\delta\) wolves.
where \(\vec{\xi }\;\left( {t + 1} \right)\) is the new updated position. The parameter A and C guides GWO algorithm to identify the optimum solutions in a global search space. Figure 3 shows the algorithmic flows of GWO.
4.2 Drawbacks of GWO
In Fig. 4, Initially GWO’s performs better in finding the new solution in both exploration and exploitation. Later, in a course of iteration the new solutions which generated are from specific regions due to struck in local optima and thereafter it lags in exploration. In addition, with that it lags in balancing exploitation and exploration process.
4.3 Oppositional learning
Oppositional based learning is a population search technique which generates the opposite of the generated solutions that diverts the searching process. It is also evident that using oppositional search leads to higher convergence rate towards optimal solutions as discussed in Rahnamayan et al. (2008).
The opposition-based learning can be defined as follows.
Definition
Oppositional learning is the process of generating opposite solutions of the current solution thus diverge the searching process in the given solution search space.
If \(\xi\) is an individual in the solution space bounded with the region [\(u^{\prime } ,v^{\prime }\)], the new individual can be generated as follows:
And this \(\xi^{ *}\) is generated for single dimensional cases.
For multi-dimensional problems the solution can be generated as where \(i\) defines the dimension, which can range from 1 to \(D\).

4.4 Laplace distribution
Evolutionary Algorithms comes with the random initialization process that then converges towards optimal solution. The standard distribution probability of Laplace transform Ahandani and Alavi-Rad (2012) using the probability density function is given by
Such that \(\xi\) range between \(\left( { - \;\infty ,\; + \;\infty } \right)\) and the distribution function of Laplace is given as
where \(x\) and \(y\) are the local parameters and the values of \(x\) ranges between \(\left( { - \infty , + \infty } \right)\) and \(y \ge 0\).
The above-mentioned distribution is the actual form of Laplacian distribution on any mathematical model and the results of the distribution with local parameters set to 1 and 2 respectively will result the distributed values as shows in Fig. 5 Based on the mathematical and simulation evidence found in the literature as well as form Fig. 5 the proposed schema can be introduced in GWO.
The pseudo code for Laplacian distribution algorithm is given in algorithm 2.

The pseudo code for oppositional based Laplacian grey wolf optimization algorithm is given in algorithm 3.

4.5 SVM and OLGWO on IDS
With the discussions stated above, the proposed algorithm OLGWO along with SVM is used to address the intrusion detection in the following manner (algorithm 4). Figure 4 shows the Block Diagram of SVM-OLGWO on IDS.

5 Experimental evaluation
The proposed methodology has been implemented in MATLAB Version 9.6 on KDD99 dataset. In total KDD dataset has 23 different types of attacks where all the attacks come under four major class of attacks namely: DoS, R2L, U2R, and Probing. Since KDD has large dataset and we use learning using SVM classifier, we trained and tested our algorithm using the following samples mentioned in Table 1.
The performance measures we used for evaluating the proposed algorithm are training time, detection rate, false positive and false negative. The existing algorithms we used for comparison are classical SVM, ASOACN Feng et al. (2014) and CSVAC Feng et al. (2014). The results of the classified datasets are clearly given in the form of confusion matrix in Table 2 for SVM, Table 3 for CSOACN, Table 4 for CSAVC and Table 5 for SVM & OLGWO. Table 6 for SVM-OLGWO vs existing methods, Table 7 For data set T2 tested by SVM-OLGWO and Table 8 for SVM-OLGWO and KDD99 Winner. The confusion matrix shows the proper classification that it has to be classified. For example, the row of the table shows the actual dataset that is classified, and the column refers the predicted set. If both correlates with same value, then it is termed as properly detected.
Figure 6 shows the parameter tuning of \(A\) and \(c\) with different values ranges from 0 to 2 with the interval. As the result the value that having high detection rate was used for implementation of our proposed algorithm.
6 Conclusion
In this paper, a learning-based approach for detecting intruders using log files of the computer system is proposed. A structure for clustering the users via improvised grey wolf algorithm with Laplacian distribution and oppositional learning is proposed along with SVM for classification. In the proposed approach clustering and classification are the base systems for identifying the intruders in computer systems. The proposed approach is evaluated with standard metrics and compared with the existing methodologies. The proposed methodology acquires better detection rate than the other existing approaches. An empirical test has been followed to tune the parameters of grey wolf optimization algorithm. The significance of the proposed algorithm is higher than the existing approach which can be found in Table (6). The future scope of this model can also be used to solve other engineering optimization problems in the near future.
Change history
23 May 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s12652-022-03931-9
References
Abiramy NV, Smilarubavathy G, Nidhya R, Kumar D (2018) A secure and energy efficient resource allocation scheme for wireless body area network. In: International conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC) I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), 2018 2nd International Conference, pp 729–732
Ahandani MA, Alavi-Rad H (2012) Opposition-based learning in the shuffled differential evolution algorithm. Soft Comput 16(8):1303–1337
Anguraj DK, Smys S (2019) Trust-based intrusion detection and clustering approach for wireless body area networks. Wirel Pers Commun 104(1):1–20
Axelsson S (1998) Research in intrusion-detection systems: a survey—technical report. Department of Computer Engineering, Chalmers University of Technology, Göteborg, pp 1–93
Besharati E, Naderan M, Namjoo E (2019) LR-HIDS: logistic regression host-based intrusion detection system for cloud environments. J Ambient Intell Humaniz Comput 10(9):3669–3692
Bi M, Xu J, Wang M, Zhou F (2016) Anomaly detection model of user behavior based on principal component analysis. J Ambient Intell Humaniz Comput 7(4):547–554
Chung YY, Wahid N (2012) A hybrid network intrusion detection system using simplified swarm optimization (SSO). Appl Soft Comput 12(9):3014–3022
Debar H, Dacier M, Wespi A (2000) A revised taxonomy for intrusion-detection systems. Ann Telecommun 55(7–8):361–378
Denning DE (1987) An intrusion detection model. IEEE Trans Softw Eng 13(2):222–232
Eesa AS, Orman Z, Brifcani AMA (2015) A novel feature-selection approach based on the cuttlefish optimization algorithm for intrusion detection systems. Expert Syst Appl 42(5):2670–2679
Feng W, Zhang Q, Hu G, Huang JX (2014) Mining network data for intrusion detection through combining SVMs with ant colony networks. Future Gener Comput Syst 37:127–140
Freeman S, Bivens A, Branch J, Szymanski B (2002) Host-based intrusion detection using user signatures. In: Proceedings of the research conference, pp 1–6
Froehlich FE, Kent A (1998) The Froehlich/Kent encyclopedia of telecommunications: Volume 17-Television Technology, vol. 17. CRC Press
Garvey TD, Lunt TF (1991) Model-based intrusion detection. In: Proceedings of the 1st national computer security conference, vol 17, pp 372–385
Han J, Kamber M, Pei J (2011) Data mining concepts and techniques third edition. The Morgan Kaufmann Series in Data Management Systems, pp 83–124
Hand D, Mannila H, Smyth P (2001) Principles of data mining. MIT Press, Sections, Cambridge, pp 2–6
Horng SJ, Su MY, Chen YH, Kao TW, Chen RJ, Lai JL, Perkasa CD (2011) A novel intrusion detection system based on hierarchical clustering and support vector machines. Expert Syst Appl 38(1):306–313
Jaganathan S, Palaniswami S (2014) Control of voltage profile with optimal control and placement of distributed generation using the refined bacterial foraging algorithm. J Vib Control 20(13):1–14
Kantardzic M (2003) Data mining concepts, models, methods, and algorithms. John Wiley, New York, pp 1–529
Klawonn F, Höppner F (2003) What is fuzzy about fuzzy clustering? Understanding and improving the concept of the fuzzifier. In: International symposium on intelligent data analysis, pp 254–264
Kumar S (1995) Classification and detection of computer intrusions. Doctoral dissertation, PhD thesis, Purdue University, pp 1–180
Lin SW, Ying KC, Lee CY, Lee ZJ (2012) An intelligent algorithm with feature selection and decision rules applied to anomaly intrusion detection. Appl Soft Comput 12(10):3285–3290
Lunt TF (1993) A survey of intrusion detection techniques. Comput Secur 12(4):405–418
Marchette DJ (1999) A statistical method for profiling network traffic. In: Workshop on intrusion detection and network monitoring, pp 119–128
Mirjalili S, Mirjalili SM, Lewis A (2014) Grey wolf optimizer. Adv Eng Softw 69:46–61
Monrose F, Rubin A (1997) Authentication via keystroke dynamics. In: Proceedings of the ACM conference on computer and communications security, pp 48–56
Mubarakali A, Ashwin M, Mavaluru D, Kumar AD (2019) Design an attribute based health record protection algorithm for healthcare services in cloud environment. Multimed Tools Appl. https://doi.org/10.1007/s11042-019-7494-7
Mukherjee B, Heberlein LT, Levitt KN (1994) Network intrusion detection. IEEE Netw 8(3):26–41
Raghav RS, Ponnurangam D (2017) Reconstruction of topology using RABC algorithm in wireless sensor networks. Int J Mech Eng Technol 8(8):148–157
Raghav RS, Amudhavel J, Dhavachelvan P (2017a) Artificial immune optimization on minimum energy broadcasting in wireless sensor networks. Adv Appl Math Sci 17(1):79–94
Raghav RS, Sujatha P, Ponnurangam D (2017b) An enriched artificial bee colony (EABC) algorithm for detection of sinkhole attacks in Wireless Sensor Network. Int J Mech Eng Technol 8(8):193–202
Raghav RS, Kalaipriyan T, Chandraprabha K, Janakiraman S, Saravanan D, Venkatesan S (2019) Augmented powell-based krill herd optimization for roadside unit deployment in vehicular ad hoc networks. J Test Eval 47(6):1–23
Rahnamayan S, Tizhoosh HR, Salama MM (2008) Opposition versus randomness in soft computing techniques. Appl Soft Comput 8(2):906–918
Ryan J, Lin MJ, Miikkulainen R (1998) Intrusion detection with neural networks. Advances in neural information processing systems, pp 943–949
Smys S, Kumar AD (2016) Secured WBANs for pervasive m-healthcare social networks. In: IEEE international conference on intelligent systems and control (ISCO), pp 1–4
Spafford EH, Zamboni D (2000) Intrusion detection using autonomous agents. Comput Netw 34(4):547–570
Teng HS, Chen K, Lu SC (1990) Security audit trail analysis using inductively generated predictive rules. In: IEEE sixth conference on artificial intelligence for applications, pp 24–29
Thaseen IS, Kumar CA (2017) Intrusion detection model using fusion of Chi-square feature selection and multi class SVM. J King Saud Univ Comput Inform Sci 29(4):462–472
Thirugnanasambandam K, Amudhavel J, Pothula S (2017) Oppositional cuckoo search for solving economic power dispatch. IIOABJ 8(2):199–207
Thirugnanasambandam K, Prakash S, Subramanian V, Pothula S, Thirumal V (2019) Reinforced cuckoo search algorithm-based multimodal optimization. Appl Intell 49:1–25
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article has been retracted. Please see the retraction notice for more detail:https://doi.org/10.1007/s12652-022-03931-9
About this article
Cite this article
Anitha, P., Kaarthick, B. RETRACTED ARTICLE: Oppositional based Laplacian grey wolf optimization algorithm with SVM for data mining in intrusion detection system. J Ambient Intell Human Comput 12, 3589–3600 (2021). https://doi.org/10.1007/s12652-019-01606-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-019-01606-6