Abstract
When a new event occurs, the nodes in the neighborhood of the event sense and then send many packets to the sink node. Such circumstances need their networks to be simultaneously reliable and event-driven. Moreover, it should be remove redundant packets in order to lower the average energy consumption. A data fusion algorithm based on event-driven and Dempster–Shafer evidence theory is proposed in this paper to reduce data packet quantities and reserve energy for wireless sensor networks upon detecting abnormal data. Sampling data is compared against the set threshold, and the nodes enter the relevant state only when there are abnormal datum; at this point, cluster formation begins. All cluster members incorporate a local forwarding history to decide whether to forward or to drop recent sampling data. Dempster–Shafer evidence theory is exploited to process the data. The basic belief assignment function, with which the output of each cluster member is characterized as a weighted-evidence, is constructed. Then, the synthetic rule is subsequently applied to each cluster head to fuse the evidences gathered from cluster member nodes to obtain the final fusion result. Simulation results demonstrate that the proposed algorithm can effectively ensure fusion result accuracy while saving energy.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Wireless sensor networks (WSNs) play an indispensable role in many applications due to its low cost, easy deployment, dynamic networking capability, and easy expansion. WSNs are utilized in environmental monitoring, military, and real-time target tracking systems among others [1, 2]. WSNs are composed of many small volumes and low power sensor nodes which are deployed in the monitored area to form a network which facilitates wireless communication. The main source of power to a sensor node is a limited and non-rechargeable battery, so it is crucial to design WSNs with special focus on energy constraints [3].
A large number of nodes are distributed in the area to gather comprehensive information from the monitoring network. Some of this data has similarity or consistency with each other, which results in a large number of redundant packets [4, 5]. According to the respective data acquisition method, WSNs can be divided into continuous acquisition, event-driven acquisition, and periodic acquisition categories [6]. The event-driven model can be used in fire monitoring, pollution monitoring, medical rescue, and other similar applications. In these applications, when a new event occurs, nodes within the event area upload vital change data which may cause congestion [7]. Once an event of interest is detected, nodes may enter a high working frequency. In monitoring based on an event-driven report, clustering can reduce the energy consumption compared to the unscheduled systems by reducing collisions, idle listening, or overhearing at the cost of coordination messages during the cluster formation period [6].
WSNs mainly expend energy in data communication, transmission, and processing. Data transmission is especially energy-consumptive [8]. Transmission energy consumption is also closely related to transmission quantity. Data fusion is a technique which utilizes in-network processing to remove incorrect and redundant data from sensor node measurements so as to efficiently return information upon the user’s request. Fusing the data effectively helps not only to minimize communication collisions, but also to reduce energy costs as the amount of data transmitted is reduced [9]. In practical application, all fusion methods encounter issues with various uncertainties. However, Dempster–Shafer evidence theory (or D–S evidence theory) provides a natural and powerful method for illumination and synthesis of uncertain information and is commonly used to fuse data [10].
In this work, we concentrated on event-driven data fusion to group nodes within the event area into clusters to reduce the amount of data packets. This paper presents a data fusion algorithm based on event-driven and D–S evidence theory (EDDS). The network forms clusters dependent on a given threshold only when an event occurs, which prevents excessive energy consumption under normal circumstances. After the data is transferred from cluster heads (CHs) to the sink node, weighted data fusion is performed with reasonable confidence and composition rules. This process reduces the influence of anomaly monitored data while increasing the proportion of similar data to help the system determine whether an event has or has not truly occurred.
The remainder of this paper is organized as follows. Section 2 discusses the related work. Section 3 reviews the D–S evidence theory concept, and Sect. 4 explains the proposed scheme and its specifications. Simulation results are presented and discussed in Sect. 5. Section 6 provides a brief summary and conclusion.
2 Related Works
LEACH [11] is one of the clustering algorithms most commonly used to conserve WSN energy. It assumes that all nodes have uniform energy consumption. In actuality, nodes consume uneven amounts of energy and thus, it is unreasonable to select CHs in an equally distributed manner. Some researchers [12,13,14] proposed clustering methods based on event-driven data acquisition. Manjeshwar et al. [12] worked under the assumption that clustering plays the same role as LEACH and that nodes use a given threshold to determine whether data is necessary to forward. Ozger et al. [13] proposed an event-driven spectrum-aware clustering protocol which forms clusters after event detection and maintains them until the end of the event. After an event is detected, CHs are selected among appropriate nodes to form clusters between the event and the sink node; the one-hop member is selected to maximize the number of available two-hop neighbors. After the event, the cluster is no longer available to reduce the energy consumption due to unnecessary clustering and maintenance costs. An energy-aware clustering technique based on event-driven data reporting in WSN called EET was presented by Adulyasas et al. [14] for data monitoring. In EET, when the data changes beyond a given threshold, sensor nodes upload only necessary data. To this effect, clusters are created only in specific locations where such necessary data changes occur. Clusters are operated as long as the ambient situation continues to change. Once the situation becomes stable, the clusters are reset and each sensor node in the clusters switches to sleep mode to conserve the energy otherwise consumed by cluster heads and members. Hou et al. [15] proposed a data fusion algorithm dependent on an event-driven dynamic clustering scheme and neural network, where dynamic cluster and cluster head election processes are based on the severity of the event and the node residual energy. The BP neural network model is used to fuse large amounts of data and extract them.
D–S evidence theory transforms subjective, uncertain, and conflicting information into objective decision-making results [16]. There are two main reasons that D–S evidence theory does not readily satisfy the necessary accuracy for fusion. First, it is difficult to ensure a reasonable and accurate basic belief assignment function (BBAF). Second, it is highly challenging to make decisions with the unified BBAF [17]. Many researchers have attempted to resolve these problems [17,18,19]. Shen et al. [17] proposed an integrated model based on D–S evidence theory and extreme learning machine. Reasonable basic belief assignments are established. Comprehensive basic belief assignments can be obtained via evidence synthesis from several mass functions; the final decision is made based on an extreme learning machine to secure reliable multi-sensor data fusion results. Wang et al. [18] divided sensor node data into several groups depending on the deviation, then applied basic probability assignment to generate a discrimination framework. The mass function of combined evidence is considered the weight distribution function of the evidence. Finally, a unified result can be obtained by a weighted summation rule. Liu et al. [19] introduced a D–S evidence theory-based fault-tolerant event detection algorithm which can be used to analyze the impact of the spatial correlation between nodes at different distances and the node status on event detection performance. The output of each sensor node is characterized as weighted evidences instead of crisp values, where neighboring node status values are reasonably fused according to their individual contribution to the detection.
3 Preliminaries of D–S Evidence Theory
The basic idea of D–S evidence theory is to establish a discernment framework, to determine the degree of support for each set of evidence, and then to apply an evidence synthesis formula to calculate the support for all propositions. Under D–S evidence theory, the set of possible outcomes for a decision problem of all pairs of mutually exclusive pairs defines the discernment framework, Θ = {θ1, θ2,…, θ n }.
3.1 Basic Concepts
Several belief functions in D–S evidence theory are described below.
If a function m: 2Θ → [0, 1],∀ A ⊆ Θ, 0 ≤ m(A) ≤ 1 which satisfies
where Φ denotes the null set and m(A) is the BBAF subset A. The BBAF reflects the degree of evidence support for each subset. Subset A with non-zero mass is called a focal element; (A, m(A)) is a piece of evidence.
Let m be a function of the discernment framework Θ, where the impact of evidences on a given element A of Θ has two points: belief and plausibility. They are denoted as Bel(A) and Pl(A), as shown in the following equation:
where \(\bar{A}\) is the supplement of A, Bel(A) indicates the degree of confidence that the evidence is true for A, and Pl(A) indicates that the trustworthiness of A is not false. For any focal element in Θ, the corresponding BBAF contributes a belief interval [Bel(A), Pl(A)], where the lower and upper probabilities represent the belief and plausibility.
3.2 Combinational Rule
Let m1, m2, …, m n be n independent values in Θ. For a given element A belonging to Θ, the generalized rule for combining n number of evidences is:
if K = 1, the evidences are completely conflicting.
4 Data Fusion Based on Event Driven and D–S Evidence Theory
4.1 Network Model
The network described in this paper monitors events, then transforms and processes the monitored data of the events. The network system consists of stationary and energy-limited sensor nodes as well as one sink node. All sensor nodes are distributed randomly in the monitored area and have a unique ID. Each sensor node learns relevant information, such as location and ID, for itself and its one-hop neighbors. The clustering process is driven by an event. The node that becomes the CH can adjust the transmission power according to the communication distance.
4.2 Threshold Definition
Definition 1
Stimulation Hard Threshold (SHT): Whenever the sampling value of one node exceeds a threshold SHT, abnormal phenomena can be confirmed.
Definition 2
Biased Threshold (BT): The initial value at which nodes detect the necessary changes in data within the region area.
Definition 3
The cluster head election value (P): The possibility that a node becomes a CH.
where Ti is a sampling value of one node at the current time, E s is the surplus energy of nodes, d toS is the distance from a node to the sink node, and α is the coefficient of event severity.
Definition 4
Cluster Lifetime (CL): Used to judge the existence time of the cluster. Over CL + t, there are no abnormal monitored data and the cluster is disbanded. t is the time at which the node is selected as a CH.
4.3 Node States
There are three node states of EDDS which merit description here. We also explain how the threshold definition provided above functions specifically.
-
1.
Sleep state This state represents the nodes’ situations before they begin to work. The nodes do not communicate with each other during this time so as to conserve energy. The active state is triggered at regular time intervals. The node also returns to this state whenever its energy is depleted or the cluster is disbanded.
-
2.
Active state The main tasks of the node in this state are data gathering and identifying abnormal data with significantly changes (\(|T_{i} - A_{i - 1} | > {\text{BT}}\), where Ai−1 is the last data uploaded to the CH). The nodes now seek a CH as they find abnormal data, and also receive cluster-forming messages from the CH. The node transmits the data to the CH as a member.
-
3.
Excited state Once the node finds an event (T i > SHT), it enters an excited state in which it carries out several tasks such as data collection, data transmission, and high-frequency data processing. The node also may become a CH if its P value is maximal among neighbor nodes in excited states.
4.4 Cluster Formation Based on Event-Driven
When the node receives cluster formation from different CHs, it joins the cluster whose CH has greater surplus energy. To prevent creating an excessive number of clusters, which would lead to redundancy, the nodes do not join a new cluster or become CHs if those labeled as cluster members are stimulated again. The cluster formation process upon abnormal data detection is illustrated in Fig. 1.
4.5 Event-Driven Data Fusion Under D–S Evidence Theory
4.5.1 Cluster Members Preprocess
The sensor node compares its own data in the current time T i with the threshold SHT and the data most recently uploaded to the CH Ai−1. If T i > SHT or \(|T_{i} - A_{i - 1} | \ge {\text{BT}}\), T i should be transferred to the CH; otherwise, T i should be disregarded. In general, non-events comprise large portions of the monitoring period (i.e., data changes are small), so that the nodes are sleepy most of the time. This reduces the amount of transmitted data packets and saves energy.
4.5.2 Data Fusion Under D–S Evidence Theory
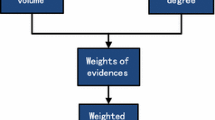
The data set T = {T1, T2, … T j }, monitored by nodes that belong to the same cluster at time t, is regarded as the discernment framework. Each cluster is considered to be evidence of the discernment framework. The CH first combines the BBAF generated by the nodes within the cluster. The BBAF of each data value in the combination of evidences is considered the weighting coefficient of the fusion. Weighted data fusion results are obtained accordingly.
Under statistical theory, effective monitored values fall within a specific neighborhood of true values. Values outside this neighborhood are affected by environmental noise, human disturbances, or systematic errors. The assigned BBAF of T i belonging to the kth set can be obtained as follows:
where β is a trust coefficient which can be altered to adjust the discrimination degree of the obtained BBAF, j is the total quantity of data in a set, and \(T_{M}^{k}\) is the median monitored value in the kth set. m k (T i ) is used to reduce the impact of outliers. The closer T i gets to the median, the higher the BBAF of T i will be.
The BBAF function k can be calculated as follows:
The fusion result of the kth set of data is:
The results of each set are reassigned before the final fusion result is obtained.
For effective event-driven WSN monitoring, it is necessary to consider the distance from the event center: nodes closer to the event center yield more valuable monitored data. Because the event center cannot accurately be determined, here, we use the data set representing the earliest timepoint as a fuzzy event center.
According to our references [20], the distance of evidence \(d_{mass} (m_{1} ,m_{2} )\) can be used to estimate the similarity of the evidence involved in the combination:
where m1 and m2 are evidence vectors. D is a positively defined matrix which can be calculated as follows:
In order to transform the reliability of a function to an appropriate metric, we define the credibility of a BBAF for the kth set as:
where \(\eta_{k}\) indicates that the closer the cluster is to the event source, the greater the credibility of its evidence. m0 represents the trust allocation of the first set of data at the time the event is marked. It is necessary to assign a weight for fused result of each data set to further improve the reliability of monitored data and reduce the conflict among evidences.
The average belief weight \(\bar{\eta }_{k}\) is as follows:
The n − 1 fused results are weighted to yield a final result:
Figure 2 summarizes the data fusion process of the proposed EDDS algorithm.
5 Simulation Results and Analysis
This section discusses our performance evaluation for the proposed EDDS algorithm in MATLAB. We set up the average energy consumption, end-to-end delay, and fractional error as performance evaluation indicators for the EDDS algorithm. To analyze node energy consumption, we adopted an energy consumption model similar to LEACH [11]. The simulation parameter values are summarized in Table 1.
5.1 Energy Consumption Analysis
Average energy consumption is one of the most important parameters reflecting the performance of the network. In order to test the performance of our event-driven scheme under different ranges of events and event rates, we assumed that LEACH, EBPDF, and EDDS are adopted to run for 600 epochs.
Figure 3 shows the average energy consumption under various scale event occurrence regions where events occur 30 times per hour. In EDDS, the average energy consumption is 19.6 and 15% lower on average than that of LEACH and EBPDF, respectively, at an event region of 200 × 200 m2. As shown in Fig. 4, the average energy consumption of LEACH is consistently largest and EBPDF second-largest among the three algorithms. At 60 times per hour, the average energy consumption of EDDS is 23.3 and 14.4% lower, respectively, than LEACH and EBPDF. Average energy consumption consistently increases in EDDS and EBPDF but stabilizes in LEACH. LEACH functions are irrelevant to event occurrence, and the LEACH network is continuously exciting over the network’s whole lifetime, so its average energy consumption is higher than the other algorithms. Clustering in EDDS and EBPDF are connected to event occurrence, so costs increase as more events occur. The nodes participating in cluster formation are limited to the region where events occur and to the event rate. However, the nodes remain asleep during calm monitoring periods, which enables significant energy conservation compared to LEACH.
The proposed algorithm is based on an association between D–S evidence theory and an event-driven clustering scheme. The network generates large amounts of data when an event occurs, but the amount of data is reduced after data processing through D–S evidence theory. EDDS requires somewhat costly fusion of the data in clusters, but the amount of communication data in the node is fairly low; in short, it works under a reasonable energy constraint.
The average energy consumption of nodes under the same three algorithms with events occurring 60 times per hour in a 200 × 200 m2 region is shown in Fig. 5. EDDS showed the lowest energy consumption throughout the simulation period. The energy depletion of LEACH and EBPDF are at 620th and 843rd epoch, respectively. EDDS maintains surplus energy until epoch 1000.
EDDS markedly differs from the other two algorithms mainly in regards to its minimal amount of transmitted data. EDDS uses given thresholds to sift the sampling data while LEACH does not exploit the threshold mechanism. If there is no abnormal data that exceeds the thresholds mentioned above, the data is not uploaded. Nodes in non-event regions stay asleep, thus minimizing the overall network energy consumption. EBPDF, conversely, continually transfers data after cluster formation without consideration of any given threshold.
5.2 End-to-End Delay Analysis
End-to-End latency defined as the time from when a packet is received by the CH to when it is delivered to the sink node. Figure 6 shows different event rate versus average end-to-end delay, where the network can generate data packets at a rate of 24 kbps. The latency of EDDS increases slowly when the event rate is lower than 20 times per hour, but after that the latency increases quickly. When event rate is less than 20 times per hour, the nodes sleep for a regular time and packets are delivered in a specified unit time. As the increasing of event rate,the nodes are switched between a sleep state and active/excited state frequently, and packets are delivered continuously in specified unit time which is shorter than no events. The packets increased with increasing of event rate, lead to network congestion and incur long delays [21], which is why the latency of EDDS is consistently growing. At the same time, CHs need more time to fuse received packets.
5.3 Fractional Error Analysis
In this experiment, we used a data set for fire temperature distribution (Fire Dynamic Simulator [22]) to evaluate EDDS. The sampling data of the node closest to the ignition source serves as the blank data and β = 0.27. Figure 7 shows the fusion results of EDDS and EBPDF, where the results of EDDS and the blank data show a similar trend as the epochs progress.
To measure fused data accuracy, we computed the fractional error in the achieved results as follows:
We randomly selected five sets of fusion results to calculate the fractional error as shown in Table 2. EDDS outperformed EBPDF in processing data and showed a consistently lower fractional error, indicating that it is indeed feasible and effective.
6 Conclusions
This paper presented a data fusion algorithm based on event-driven and D–S evidence theory which yields high-precision fusion results with low control energy overhead. Nodes share similar data for most of the monitoring time. Thresholds are applied to nodes to ensure they transmit only necessary data and clustering based on event-driven, so the nodes transmit very little data when the network situation is stable to reserve energy. Clusters are created only in areas with abnormal data which persists over a certain time period. Multiple data sources are combined into coordinated results through D–S evidence theory. Data from the same cluster serves as evidence of the framework, and data closer to the event source is given greater credibility. Compared to two other classical algorithms, EDDS is more energy efficient and yields more accurate data fusion for the detection of abnormal WSN data. In future, the research directions include the utilization of multi-source data or multi-path fusion and the optimization of other EDDS parameters such as quality of fusion and latency.
References
Xia, X., Chen, Z., Li, D., & Li, W. (2014). Proposal for efficient routing protocol for wireless sensor network in coal mine goaf. Wireless Personal Communications, 77(3), 1699–1711.
Owojaiye, G., & Sun, Y. (2013). Focal design issues affecting the deployment of wireless sensor networks for pipeline monitoring. Ad Hoc Networks, 11(3), 1237–1253.
Tsai, C. W., Hong, T. P., & Shiu, G. N. (2016). Metaheuristics for the lifetime of WSN: A review. IEEE Sensors Journal, 16(9), 2812–2831.
Dauwe, S., Renterghem, T. V., Botteldooren, D., & Dhoedt, B. (2012). Multiagent-based data fusion in environmental monitoring networks. International Journal of Distributed Sensor Networks, 2012, (2012-6-5), 2012(1–2), 15.
Huy, D. V., & Viet, N. D. (2015). DF-AMS: Proposed solutions for multi-sensor data fusion in wireless sensor networks. In International conference on knowledge and systems engineering (pp. 1–6). IEEE.
Bouabdallah, N., Rivero-Angeles, M. E., & Sericola, B. (2009). Continuous monitoring using event-driven reporting for cluster-based wireless sensor networks. IEEE Transactions on Vehicular Technology, 58(7), 3460–3479.
Kamarei, M., Hajimohammadi, M., Patooghy, A., & Fazeli, M. (2015). An efficient data aggregation method for event-driven WSNs: A modeling and evaluation approach. Wireless Personal Communications, 84(1), 1–20.
Bahrami, S., Yousefi, H., & Movaghar, A. (2012). DACA: Data-aware clustering and aggregation in query-driven wireless sensor networks. In International Conference on Computer Communications and Networks (Vol. 7204, pp. 1–7). IEEE.
Izadi, D., Abawajy, J. H., Ghanavati, S., & Herawan, T. (2015). A data fusion method in wireless sensor networks. Sensors, 15(2), 2964.
Yager, R. R., Kacprzyk, J., & Fedrizzi, M. (1994). Advances in the Dempster–Shafer theory of evidence. New York: Wiley.
Heinzelman, W. R., Chandrakasan, A., & Balakrishnan, H. (2000). Energy-efficient communication protocol for wireless microsensor networks. In Hawaii International Conference on System Sciences (Vol. 18, p. 8020). IEEE Computer Society.
Manjeshwar, A., & Agrawal, D. P. (2002). APTEEN: A hybrid protocol for efficient routing and comprehensive information retrieval in wireless. In Parallel and Distributed Processing Symposium. Proceedings International, IPDPS 2002, Abstracts and CD-ROM (p. 8). IEEE.
Ozger, M., & Akan, O. B. (2013). Event-driven spectrum-aware clustering in cognitive radio sensor networks. In IEEE INFOCOM (Vol. 12, pp. 1483–1491). IEEE.
Adulyasas, A., Sun, Z., & Wang, N. (2013). An event-driven clustering-based technique for data monitoring in wireless sensor networks. In Consumer Communications and NETWORKING Conference (Vol. 14, pp. 653–656). IEEE.
Hou, X., Zhang, D., & Zhong, M. (2014). Data aggregation of wireless sensor network based on event-driven and neural network. Chinese Journal of Sensors and Actuators, 27(1), 142–148.
Shafer, G. (1978). A mathematical theory of evidence. Technometrics, 20(1), 242.
Shen, B., Liu, Y., & Fu, J. S. (2014). An integrated model for robust multisensor data fusion. Sensors, 14(10), 19669–19686.
Wang, W. Q., Yang, Y. L., & Yang, C. J. (2013). A data fusion algorithm based on evidence theory. Kongzhi Yu Juece/Control and Decision, 28(9), 1427–1430.
Liu, K., Yang, T., Ma, J., & Cheng, Z. (2015). Fault-tolerant event detection in wireless sensor networks using evidence theory. KSII Transactions on Internet & Information Systems, 9(10), 3965–3982.
Jousselme, A. L., Grenier, D., & Bossé, É. (2001). A new distance between two bodies of evidence. Information Fusion, 2(2), 91–101.
Hong, C., Xiong, Z., & Zhang, Y. (2016). A hybrid beaconless geographic routing for different packets in WSN. New York: Springer.
Mcgrattan, K. B., Hostikka, S., & Floyd, J. E. (2007). Fire dynamics simulator (version 5): User’s guide. NIST Special Publication, 4(4), 206–207.
Acknowledgements
This work was in part supported by the State Key Laboratory of Safety and Health for Metal Mines (2016-JSKSSYS-04); the Key Scientific Projects of Hunan Education Committee (15A161).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yu, X., Zhang, F., Zhou, L. et al. Novel Data Fusion Algorithm Based on Event-Driven and Dempster–Shafer Evidence Theory. Wireless Pers Commun 100, 1377–1391 (2018). https://doi.org/10.1007/s11277-018-5644-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5644-2